#Access Control Software
Explore tagged Tumblr posts
Text
Public Safety and Security Market to Reach $514.1 Billion by 2031
Meticulous Research®—a leading global market research company, published a research report titled, ‘Public Safety and Security Market by Offering (Safety Devices, Safety Software, Safety Services), Technology (IoT, AI, Cloud Computing, ML), Application (Data Gathering, Mapping, and 3D Imaging), End Use (Warehouses & Depots, Workplaces, Shopping Malls & Retail Stores) and Geography - Global Forecast to 2031.’
According to this latest publication from Meticulous Research®, the global public safety and security market is expected to reach $514.1 billion by 2031 from an estimated $234.2 billion in 2024, at a CAGR of 11.9% during the forecast period. The growth of the public safety and security market is driven by the growing utilization of AI, ML, and analytics technologies in public safety and security applications, increasing awareness and initiatives for public safety and security, and government focus on managing the needs of the rising urban population. However, the significant initial investments required to implement public safety and security solutions restrain the growth of this market. The integration of cloud computing and big data analytics in public safety and security solutions and the rising incidence of terrorism and security breaches are expected to generate market growth opportunities. However, the complexities in implementing advanced public safety and security systems and the rising cases of data theft are major challenges for market stakeholders.
The global public safety and security market is segmented by offering, technology, application, end use, and geography. The study also evaluates industry competitors and analyses the country and regional-level markets.
Based on offering, the global public safety and security market is segmented into safety devices, safety software, and safety services. In 2024, the safety services segment is expected to account for the largest share of the global public safety and security market. The large market share of this segment is attributed to the increasing demand for specialized safety services to address specific safety and security challenges. Safety services such as critical infrastructure security, emergency medical, firefighting, and disaster management services are critical in ensuring the safety and well-being of citizens and critical assets. Moreover, the safety services segment is projected to register the highest CAGR during the forecast period.
Based on technology, the global public safety and security market is segmented into the Internet of Things, artificial intelligence, cloud computing, machine learning, cybersecurity, and other technologies. In 2024, the Internet of Things segment is expected to account for the largest share of the global public safety and security market. The large share of the segment is attributed to the rising demand for real-time data insights and improved situational awareness. Moreover, the Internet of Things segment is projected to register the highest CAGR during the forecast period.
Based on application, the global public safety and security market is segmented into data gathering, mapping and 3D imaging, threat detection, security and incident management, monitoring, fire and explosion examination, network security, and other applications. In 2024, the security and incident management segment is expected to account for the largest share of the global public safety and security market. The large market share of this segment is attributed to the need to respond effectively to emergencies, the increasing adoption of smart city technologies, and the integration of IoT devices. Moreover, the security and incident management segment is projected to register the highest CAGR during the forecast period.
Based on end use, the global public safety and security market is segmented into warehouses depots, workplaces, shopping malls & retail stores, schools & universities, hospitals & healthcare, residential, transportation, and other end uses. In 2024, the transportation segment is expected to account for the largest share of the global public safety and security market. The large share of this segment is attributed to the growing concern of terrorist threats and passenger safety. Advances in contactless ticketing and facial recognition for identity verification are driving the adoption of modern transportation security solutions. Furthermore, the implementation of AI-based video analytics for crowd monitoring contributes to the growth of this segment. However, the hospitals and healthcare segment is projected to register the highest CAGR during the forecast period.
Based on geography, the public safety and security market is segmented into North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. In 2024, North America is expected to account for the largest share of the global public safety and security market. The large share of this region is attributed to the rising adoption of digital technology and data due to the growing need for improving decision-making, promoting digital inclusivity and equity, creating a collaborative ecosystem, prioritizing citizen safety and health, establishing trust and transparency, and developing resilience and adaptability to manage change effectively. However, Europe is slated to register the highest growth at a CAGR during the forecast period.
Key Players
The key players operating in the global public safety and security market are Hexagon AB (Sweden), Fujitsu Ltd. (Japan), Robert Bosch GmbH (Germany), Atos SE (France), Cisco Systems, Inc. (U.S.) Saab AB (Sweden), Airbus SE (Netherlands), Siemens AG (Germany), Intel Corporation (U.S.), Fotokite AG (Switzerland), CityShob (Israel), 3xLOGIC (U.S.), L3Harris Technologies, Inc. (U.S.), OnSolve (U.S.) and Haystax (U.S.).
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=5661
Key Questions Answered in the Report:
Which are the high-growth market segments in terms of offering, technology, application, end use, and geography?
What is the historical market size for the public safety and security market across the globe?
What are the market forecasts and estimates for the period 2024–2031?
What are the major drivers, restraints, opportunities, and challenges in the global public safety and security market?
Who are the major players in the market, and what are their market shares?
How is the competitive landscape for the global public safety and security market?
What are the recent developments in the global public safety and security market?
What are the different strategies adopted by the major players in the market?
What are the key geographic trends, and which are the high-growth countries?
Who are the local emerging players in the global public safety and security market, and how do they compete with other players?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Public Safety and Security Market#Surveillance Cameras#Sensors#Biometric and Authentication Devices#Safety Alarms#Intruder Detection Devices#Critical Communication Devices#Geographic Information Systems#Access Control Software#Building Management Software#Vehicle Recognition Software#Behavior analytics software#Disaster Management Services#Critical Infrastructure Security Services#Emergency Medical Services#Firefighting Services
0 notes
Text

new sensation
#homie just got access to the newest emotion ‘exclossia’ via software update. take care of that wetware baby mwah#don’t look too closely bc this one is a mess. but I’m trying to practice making more use of the CRT in a controlled format or in collage#but I didn’t rlly have a plan here so it’s got moderately rough edges#my art#glitch art#aesthetic#art#artwork#webcore#internetcore#glitchcore#abstract#artists on tumblr#glitch aesthetic#tech aesthetic#cyberpunk#crt
175 notes
·
View notes
Text
Well shit. I walk back what I said. that works for my spouse's phone too. Wth. Thanks for solving that for me.
yknow what would be a fucked up phone feature
#dystopia#capitalist hell#late stage capitalism#techblr#phones#technology#consumer rights#digital dystopia#forced obsolescence#anti consumer design#planned obsolescence#right to repair#tech industry greed#digital autonomy#loss of control#tech frustration#privacy concerns#tech monopoly#corporate greed#unethical design#hardware restrictions#tech criticism#corporate overreach#dystopian tech#firmware locks#software paywalls#anti consumerism#modern inconvenience#user rights#tech accessibility
116K notes
·
View notes
Text

Is your HR team still chasing attendance records? It’s time to switch to a system that updates in real-time and syncs across locations. With Spintly, attendance management gets smarter and simpler - just the way it should be: https://spintly.com/time-and-attendance-management-system/
#attendance management#time and attendance software#attendance system#biometric attendance#spintly#accesscontrol#mobile access#smartacess#biometrics#smartbuilding#visitor management system#access control system#access control solutions
0 notes
Text
Smart Parking Management Software | Parkomax Streamline your parking operations with Parkomax's advanced parking management software. Real-time monitoring, automated access, and seamless reporting in one platform.
#Parking Management Software#Smart Parking System#Automated Parking Software#Parking Control System#Parking Lot Management Software#Cloud-based Parking Software#Parking Garage Management System#Parking Access Control#Parking Operations Software#Digital Parking Solutions#Parkomax parking software#IoT-enabled parking system#Parking analytics and reporting tool#Multi-location parking management solution#Parking ticketing and billing automation
0 notes
Text
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. For educational institutions, ensuring FERPA compliance is not just a legal obligation; it's a crucial aspect of building trust with parents and students. Choosing the right school management software can significantly simplify the process of maintaining compliance and safeguarding sensitive student data.
Understanding FERPA Compliance
FERPA grants parents and eligible students certain rights regarding their education records. These rights include:
The right to inspect and review their education records.
The right to request amendments to their education records.
The right to control the disclosure of personally identifiable information (PII) from their education records.
Non-compliance with FERPA can lead to severe penalties, including loss of federal funding. Therefore, selecting a school management system with robust security features and a commitment to data privacy is paramount.
MeraSkool: A FERPA-Compliant Solution
MeraSkool.com offers a comprehensive school management solution designed with FERPA compliance in mind. Our platform incorporates multiple layers of security to protect student data, including:
Data Encryption: MeraSkool employs advanced encryption techniques to protect student data both in transit and at rest.
Access Control: Our system uses role-based access control (RBAC), ensuring that only authorized personnel have access to sensitive information. This prevents unauthorized access and maintains data integrity.
Regular Security Audits: We conduct regular security audits and penetration testing to identify and address any potential vulnerabilities.
Data Backup and Recovery: MeraSkool provides robust data backup and recovery mechanisms to ensure data availability in case of any unforeseen circumstances. This safeguards against data loss and ensures business continuity.
Compliance Certifications: We are actively pursuing relevant compliance certifications to further demonstrate our commitment to data security and privacy. (Note: Specific certifications should be listed here if available).
AI-Powered Insights and Data Security: MeraSkool leverages AI to optimize tasks and provide insights for operational efficiency, while robust data security protocols ensure privacy and regulatory compliance. (Learn More)
Key Features for FERPA Compliance
Several features within MeraSkool directly contribute to FERPA compliance:
1. Secure Student Management:
MeraSkool's student management module (learn more) allows schools to manage student enrollment, maintain detailed profiles, track attendance, and generate grade reports securely. The system ensures only authorized personnel can access sensitive student information, maintaining confidentiality.
2. Controlled Access to Records:
Our platform provides granular control over access to student records, ensuring that only authorized individuals—parents, teachers, and administrators—can view the appropriate information. This prevents unauthorized disclosure of PII.
3. Secure Fee Management:
MeraSkool's fee management module (learn more) supports creating fee structures, generating invoices, and enabling secure online payments. This functionality maintains financial transparency while securing sensitive financial data.
4. Robust Reporting and Analytics:
MeraSkool's reporting and analytics capabilities provide valuable insights into student performance, attendance, and other key metrics. This data is accessed through secure channels, adhering to FERPA guidelines.
5. Audit Trails:
(Note: If available, mention the existence and functionality of audit trails in MeraSkool. Audit trails record all actions performed on student data, providing a valuable tool for monitoring and ensuring accountability.)
6. Powerful Printable system:
MeraSkool offers a powerful printable system (learn more) allowing for secure downloading and printing of marksheets, results, ID cards, fee receipts, and other essential documents. This functionality helps maintain accurate records while ensuring data remains secure.
Additional Benefits of MeraSkool
Beyond FERPA compliance, MeraSkool provides numerous other benefits for schools:
Exam & Assignment Management: Create, schedule, and manage exams with different question formats. (Learn More)
Timetable and Attendance Management: Automated attendance tracking and timetable creation. (Learn More)
Realtime Notification: Realtime notifications powered by WhatsApp bot. (Learn More)
World-Class Support: 24/7 support and a 7-day new feature delivery commitment. (Learn More)
Simple to Use UI & UX: Intuitive design and seamless user experience. (Learn More)
Easy Onboarding with Excel Upload: Effortless integration and seamless transition. (Learn More)
MeraSkool's Commitment to Data Privacy
MeraSkool is committed to providing a secure and compliant platform for schools. We understand the importance of protecting student data and are dedicated to continually improving our security measures to meet the evolving demands of FERPA and other relevant regulations.
Contact us today to learn more about how MeraSkool can help your school maintain FERPA compliance and streamline its operations.
Note: This information is for general guidance only and does not constitute legal advice. Consult with legal counsel to ensure your school's full compliance with FERPA.
#FERPA compliance#school management software#student privacy#data security#MeraSkool#educational software#online learning#school administration#data encryption#access control#security audits#FERPA regulations#data protection
0 notes
Text
Why Your Business Needs Centralized Document Management Software: Discover PDQ Docs
In the digital age, businesses face an ever-growing need to manage an increasing volume of documents and data. From contracts and invoices to internal memos and client files, organizing and storing these documents efficiently is crucial for maintaining smooth operations. This is where centralized document management software, such as PDQ Docs, can make a significant difference. By offering a centralized system for storing and managing documents, PDQ Docs can help businesses reduce inefficiencies, enhance collaboration, and improve security.
Key Benefits of PDQ Docs as Centralized Document Management Software
PDQ Docs provides several features that make it an ideal choice for businesses seeking to improve their document management processes. One of the primary advantages of using centralized document management software like PDQ Docs is its advanced search functionality. Employees can find any document within seconds, even if it’s buried deep within a large archive. With powerful filtering and keyword search options, PDQ Docs ensures that no time is wasted on manual searches, allowing teams to stay focused on their core tasks.
Another benefit of PDQ Docs is its secure storage system. The software employs encryption protocols to protect sensitive information, ensuring that only authorized users can access specific documents. With the rise in cybersecurity threats, securing company data has never been more critical. PDQ Docs gives businesses peace of mind, knowing that their files are safe from unauthorized access or loss.
Furthermore, PDQ Docs promotes seamless collaboration. In a modern workplace, team members often need to work together on documents regardless of their location. PDQ Docs allows multiple users to access and edit documents simultaneously, fostering real-time collaboration among teams. This feature is particularly useful for businesses with remote or hybrid workforces, as it allows employees to stay connected and productive even when they aren’t in the same office.
How PDQ Docs Improves Efficiency Across Teams
Implementing centralized document management software like PDQ Docs has a direct impact on the efficiency of a business. By centralizing all files into one platform, the need for redundant document versions is eliminated. With PDQ Docs’ version control features, users can track changes, view previous versions, and ensure that everyone is working on the most up-to-date version of a document.
In addition to improving efficiency, PDQ Docs also simplifies compliance management. For businesses in regulated industries, such as healthcare or finance, keeping accurate records is vital. PDQ Docs helps ensure that documents are stored and tracked in accordance with industry standards, reducing the risk of compliance violations.
Conclusion: Why PDQ Docs is Essential for Your Business
In conclusion, centralized document management software like PDQ Docs is an essential tool for modern businesses looking to stay competitive and organized. By centralizing all your documents in one secure, easy-to-use platform, PDQ Docs improves access, collaboration, security, and compliance. Whether you’re a small business or a large enterprise, investing in PDQ Docs can significantly improve the efficiency of your document management processes, ultimately saving you time and money while boosting productivity.
#centralized document management software#document collaboration#file version control#document security#electronic document management#workflow automation#document indexing#digital document organization#document archiving#secure file management#document access control
0 notes
Text
Real-Time Biometric Software: A Solution to Attendance Management for UPSC Coaching

In an era where efficiency and precision are paramount, real-time biometric software is emerging as a game-changer in attendance management systems. Particularly for UPSC coaching centers, where punctuality and discipline are critical, leveraging such technology ensures accuracy, saves time, and enhances overall management. Institutions like NIALabs are paving the way with advanced solutions like their finger biometric systems that streamline operations seamlessly.
Why UPSC Coaching Centers Need Biometric Attendance Solutions
It is a great challenge to manage attendance of so many students in UPSC coaching centers especially with large groups. Not only are these methods exacting in time, but they are also quite imprecise. Biometric software can be viewed as offering a more powerful solution altogether: it monitors the process in real time and does not contain human mistakes. Here's why it is indispensable:
Accuracy and Transparency: Another advantage is where biometric systems are put in place in order to keep attendances for example the biometric solution providers NIALabs eliminate falsified records.
Time-Saving: Computerized processes save the time that would be taken on roll calls and manual recordation.
Efficiency in Management: The use of real-time data enhances ways through which attendance patterns are monitored and controlled by the administrators hence enhancing the operational efficiency of the system.
Enhanced Accountability: In biometric systems students as well as staff is made responsible for the presence.
How Real-Time Biometric Software Works
Biometric attendance system incorporates physical characteristics of a person for instance fingerprints or face recognition. In ID authentication mode, any student or staff member who approaches the system undergoes a match making process with a previously stored database to ensure the best identification. Availability of attendance records is possible in real-time where changes may be made immediately depending on an administrator’s request.
Key Features of Biometric Systems
Instant Authentication: These systems give fast identification, with little time being wasted, as is the case with NIALabs’ finger biometric software.
Cloud Integration: Numerous solutions available provide cloud storage, and therefore information is protected and can be accessed remotely.
Customizable Reports: School authorities can be able to produce customized attendance reports to suit their needs.
Scalability: Biometric systems can be easily custom made in regards to the size and type of coaching centre; whether it is a small ‘coaching classes’ or a large coaching institute.
Benefits of NIALabs Finger Biometric Software for UPSC Coaching Centers
NIALabs has been established as an important player in biometric solutions and has its finger biometric systems in high technology. Here’s what sets their software apart:
User-Friendly Interface: A tool for utilization by anyone who does not have the technical know-how to put it down themselves.
Advanced Security: Secure data processing protects specific information through high grade encryption.
Custom Solutions: Given the specificity, in terms of the nature of its accomplishments, to the needs of education institutions.
Real-Time Updates: Recording of attendees per meeting and preparation of reports on the same at real-time.
Cost-Effectiveness: Free from the high costs of many models without the need to have low standard or fewer functionalities.
Implementing Biometric Software: A Step-by-Step Guide
For UPSC coaching centers considering this transformation, here’s how to get started:
Assess Your Requirements
Consider the needs of the students, your institution, and the size as well as the quantity of students in your institution. This will help in choosing the right system.
Choose a Reliable Provider
Choose a reliable provider of such solutions as NIALabs offers durable and effective biometric systems.
Installation and Setup
The installation and configuration of the system should be done in accordance to the various guidelines. We have completed the high-priority tasks of federating NIALabs with other industry laboratories and establishing its strategic targets; however, we are still seeking ways to open additional doors and expand our opportunities, with help from experts for this procedure.
Train Staff and Students
To ensure that the users of the system embrace the system, have some level of training done on the system. This reduces resistance and increases acceptance.
Monitor and Optimize
Attend meeting attendance data and formed a pattern for improving the usage of the system.
Addressing Concerns About Biometric Technology
However, one may argue that the use of biometric technology will bring issues of privacy and security data into the technology investment. To address these issues:
Data Encryption: Please go for systems with good encryption to enhance security of the information.
Compliance with Regulations: Make sure that the provider complies with particular legislation on the data protection.
Transparency: In order to gain the trust of the users, the informed and recounting ways of using and storing data should be made obvious.
Conclusion
Real time biometric software is not only a new fashion, but it has become a need in the modern world for institutions which seek to receive high results. To the UPSC coaching centers, importation of this technology means an improvement in the management, security around the learning institution and overall discipline. They are evident by the fact that today NIALabs, with its finger biometric solutions, remains as the most reliable partner in this transformational journey. By adopting these systems, coaching centers will remain relevant to their mission of preparing students for success, while leaving the issues of attendance management to other systems.
#al finger biometric#biometric software#face biometric#real time biometric#biometric attendance#access control system#biometric solutions#biometric munufacturers
0 notes
Text

Enjoy Seamless Gym Entry with Biometric Access - no keys, no hassle just effortless and secure access every time.
For a Free Demo Call us now at +91-8291682083
Read More: https://tinyurl.com/2s4j3xpn
#club management software#best gym management software#gym management system#fitness management software#gym software#fitness business#biometric access control#secure#gymex
0 notes
Text
PureCode software reviews | Avoid Redirects for Authentication Checks
Instead of using redirects to check if a user is authenticated, employ route guards or higher-order components (HOCs) to protect sensitive routes. This method also provides a more secure and centralized way of managing access control.
#Authentication Checks#Avoid Redirects#purecode ai company reviews#purecode#purecode ai reviews#purecode software reviews#purecode reviews#purecode company#managing access control.
0 notes
Text
Public Safety and Security Market Size, Share, Forecast, & Trends Analysis
Meticulous Research®—a leading global market research company, published a research report titled, ‘Public Safety and Security Market by Offering (Safety Devices, Safety Software, Safety Services), Technology (IoT, AI, Cloud Computing, ML), Application (Data Gathering, Mapping, and 3D Imaging), End Use (Warehouses & Depots, Workplaces, Shopping Malls & Retail Stores) and Geography - Global Forecast to 2031.’
According to this latest publication from Meticulous Research®, the global public safety and security market is expected to reach $514.1 billion by 2031 from an estimated $234.2 billion in 2024, at a CAGR of 11.9% during the forecast period. The growth of the public safety and security market is driven by the growing utilization of AI, ML, and analytics technologies in public safety and security applications, increasing awareness and initiatives for public safety and security, and government focus on managing the needs of the rising urban population. However, the significant initial investments required to implement public safety and security solutions restrain the growth of this market. The integration of cloud computing and big data analytics in public safety and security solutions and the rising incidence of terrorism and security breaches are expected to generate market growth opportunities. However, the complexities in implementing advanced public safety and security systems and the rising cases of data theft are major challenges for market stakeholders.
The global public safety and security market is segmented by offering, technology, application, end use, and geography. The study also evaluates industry competitors and analyses the country and regional-level markets.
Based on offering, the global public safety and security market is segmented into safety devices, safety software, and safety services. In 2024, the safety services segment is expected to account for the largest share of the global public safety and security market. The large market share of this segment is attributed to the increasing demand for specialized safety services to address specific safety and security challenges. Safety services such as critical infrastructure security, emergency medical, firefighting, and disaster management services are critical in ensuring the safety and well-being of citizens and critical assets. Moreover, the safety services segment is projected to register the highest CAGR during the forecast period.
Based on technology, the global public safety and security market is segmented into the Internet of Things, artificial intelligence, cloud computing, machine learning, cybersecurity, and other technologies. In 2024, the Internet of Things segment is expected to account for the largest share of the global public safety and security market. The large share of the segment is attributed to the rising demand for real-time data insights and improved situational awareness. Moreover, the Internet of Things segment is projected to register the highest CAGR during the forecast period.
Based on application, the global public safety and security market is segmented into data gathering, mapping and 3D imaging, threat detection, security and incident management, monitoring, fire and explosion examination, network security, and other applications. In 2024, the security and incident management segment is expected to account for the largest share of the global public safety and security market. The large market share of this segment is attributed to the need to respond effectively to emergencies, the increasing adoption of smart city technologies, and the integration of IoT devices. Moreover, the security and incident management segment is projected to register the highest CAGR during the forecast period.
Based on end use, the global public safety and security market is segmented into warehouses depots, workplaces, shopping malls & retail stores, schools & universities, hospitals & healthcare, residential, transportation, and other end uses. In 2024, the transportation segment is expected to account for the largest share of the global public safety and security market. The large share of this segment is attributed to the growing concern of terrorist threats and passenger safety. Advances in contactless ticketing and facial recognition for identity verification are driving the adoption of modern transportation security solutions. Furthermore, the implementation of AI-based video analytics for crowd monitoring contributes to the growth of this segment. However, the hospitals and healthcare segment is projected to register the highest CAGR during the forecast period.
Based on geography, the public safety and security market is segmented into North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa. In 2024, North America is expected to account for the largest share of the global public safety and security market. The large share of this region is attributed to the rising adoption of digital technology and data due to the growing need for improving decision-making, promoting digital inclusivity and equity, creating a collaborative ecosystem, prioritizing citizen safety and health, establishing trust and transparency, and developing resilience and adaptability to manage change effectively. However, Europe is slated to register the highest growth at a CAGR during the forecast period.
Key Players
The key players operating in the global public safety and security market are Hexagon AB (Sweden), Fujitsu Ltd. (Japan), Robert Bosch GmbH (Germany), Atos SE (France), Cisco Systems, Inc. (U.S.) Saab AB (Sweden), Airbus SE (Netherlands), Siemens AG (Germany), Intel Corporation (U.S.), Fotokite AG (Switzerland), CityShob (Israel), 3xLOGIC (U.S.), L3Harris Technologies, Inc. (U.S.), OnSolve (U.S.) and Haystax (U.S.).
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=5661
Key Questions Answered in the Report:
Which are the high-growth market segments in terms of offering, technology, application, end use, and geography?
What is the historical market size for the public safety and security market across the globe?
What are the market forecasts and estimates for the period 2024–2031?
What are the major drivers, restraints, opportunities, and challenges in the global public safety and security market?
Who are the major players in the market, and what are their market shares?
How is the competitive landscape for the global public safety and security market?
What are the recent developments in the global public safety and security market?
What are the different strategies adopted by the major players in the market?
What are the key geographic trends, and which are the high-growth countries?
Who are the local emerging players in the global public safety and security market, and how do they compete with other players?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Public Safety and Security Market#Surveillance Cameras#Sensors#Biometric and Authentication Devices#Safety Alarms#Intruder Detection Devices#Critical Communication Devices#Geographic Information Systems#Access Control Software#Building Management Software#Vehicle Recognition Software#Behavior analytics software#Disaster Management Services#Critical Infrastructure Security Services#Emergency Medical Services#Firefighting Services
0 notes
Text
MCA Requirements with SAP System | Toggle Now
It’s been almost a year since the Ministry of Corporate Affairs (MCA), India introduced a new set of guidelines to companies on April 1, 2023, aiming to bring transparency and restrict or reduce data manipulation of books within the company. This prompted SAP clients to initiate new processes such as enabling audit trails and change logs. However, many customers are still unsure about what they need to do.
A survey conducted by ToggleNow between September 2023 and March 2024 found that 7 out of 10 customers attempted to implement the rules, but they might not have completed all the necessary steps In conclusion, the management of audit logs such as SM19/SM20 presents challenges, as enabling them may consume significant storage space and affect system performance. Despite being a standard feature, users in SAP can still delete these logs, highlighting the necessity for enhanced security measures.

Many clients have not implemented additional safeguards, leaving the system vulnerable to unauthorized alterations. Furthermore, users with administrative privileges can easily disable or erase audit trails, while wider authorizations enable the posting of backdated entries. Debug authorizations are often overlooked, granting users access to SE16 with debug capabilities, compromising data integrity. Moreover, changes made through RFMs and in debug mode lack timestamp records, necessitating stricter controls. The deletion of change and edit logs underscores the imperative for robust authorization controls. To mitigate risks, RFMs and RFCs must be secured to prevent unauthorized access and alterations.
Absolutely! Evaluating your SAP system to ensure compliance with the Ministry of Corporate Affairs (MCA) requirements is crucial for maintaining transparency and data integrity within your organization. Our team of experts specializes in SAP systems and regulatory compliance, and we’re here to assist you every step of the way.
Read more: https://togglenow.com/blog/expert-tips-for-aligning-your-sap-system-with-mca-requirements/
#sap sod analysis#sap user management automation#GRC Access Control#sap grc access control#sap identity access management#sap governance risk and compliance#GRC Audit#ITGC Reports#sap grc risk management#SAP Risk management#sap risk management module#sap hana software#SAP Authorization#SAP IAG#SAP Redesign#SAP Cybersecurity
0 notes
Text
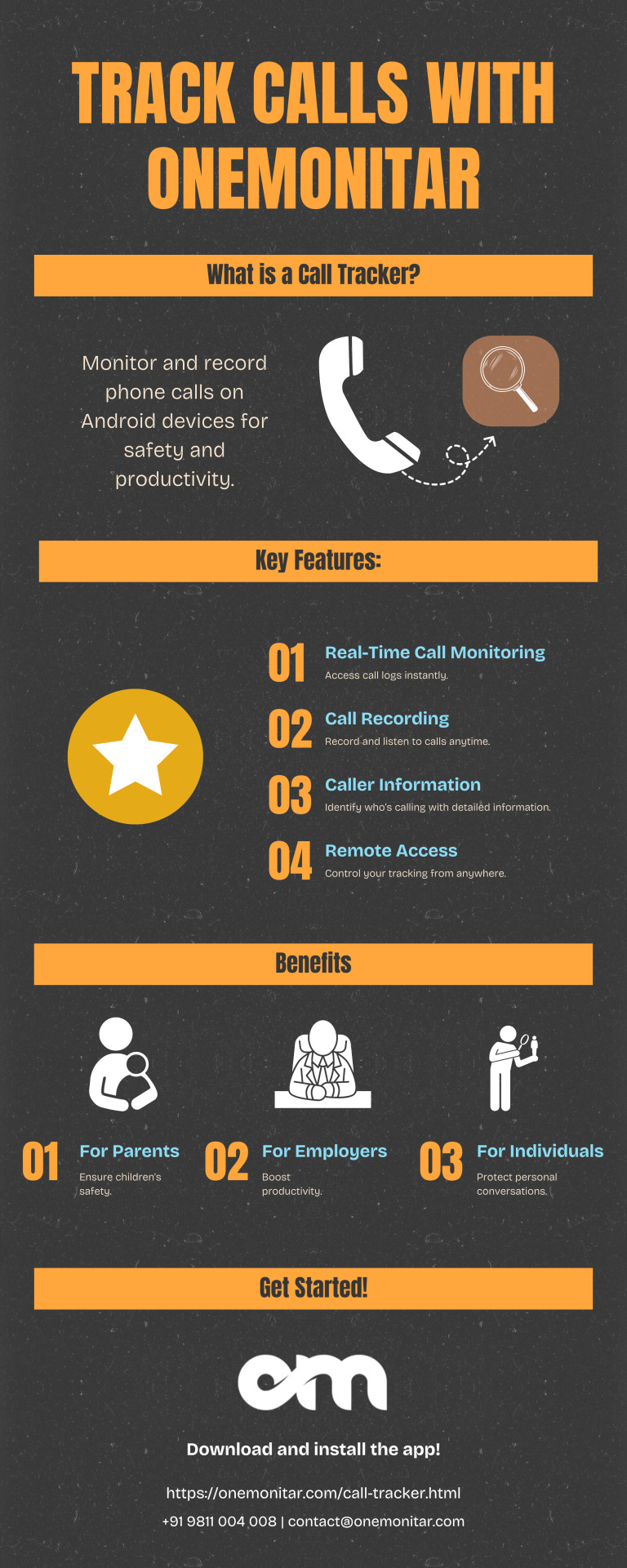
Discover the power of ONEMONITAR’s Call Tracker! Monitor and record phone calls on Android devices with real-time tracking, call recording, and caller details, all from anywhere. Whether you’re a parent ensuring your child’s safety, an employer boosting productivity, or an individual protecting your conversations, ONEMONITAR is your go-to solution. Easy to use, secure, and backed by 24/7 support—get started today!
#Call tracker#Phone call monitoring#Call recording app#Android call tracker#Real-time call monitoring#Remote call access#Call spy app#Phone spy software#Parental control app#Employee monitoring app#Secure call tracker#Phone tracking app#ONEMONITAR call tracker#Monitor phone calls#Call tracker for Android
0 notes
Text
Infostealers: What are they & far-reaching effects on data security - CyberTalk
New Post has been published on https://thedigitalinsider.com/infostealers-what-are-they-far-reaching-effects-on-data-security-cybertalk/
Infostealers: What are they & far-reaching effects on data security - CyberTalk


By Hendrik De Bruin, Security Engineer, Check Point Software Technologies.
Infostealers…ransomware’s lesser-known cousin
When it comes to malware, ransomware usually steals the limelight, largely because of the direct, devastating impact that ransomware often causes. However, ransomware’s lesser-known cousin, the “infostealer,” is slowly but surely gaining ever-more attention.
Over the last few years, we have noticed a massive increase in the usage of infostealers. In fact, some research suggests as much as 5,900% growth since 2018. Statistics also indicate that during 2023, over 10 million devices were compromised by info stealing malware, reflecting an increase of 643% over the past three years.
An infostealer is a type of malware designed to infiltrate computer systems, not for purposes of data encryption like ransomware or data deletion like “wipers”, but specifically designed to steal sensitive information.
These malicious programs exfiltrate various data, including login credentials, session cookies, financial information, and personally identifiable information (PII). After harvesting and capturing the sensitive information, the infostealer sends it back to remote servers controlled by cyber criminals.
Once cyber criminals obtain the sensitive information, it is sold on the dark web to various nefarious actors, such as “Initial Access Brokers” who use the info to facilitate larger attacks, like ransomware attacks.
Infostealers…And their real-life impact
To showcase the impact that infostealers can have and to reinforce that infostealers deserve more attention, we can look at two recent incidents: a breach reported at Ticketmaster and at a major European bank.
In both cases, malicious actors gained access to information stored at a third-party service provider called Snowflake. Snowflake offers a cloud-based data storage and analytics service, often referred to as “data-as-a-service”.
During these breaches, attackers simply used credentials — which were most likely obtained through infostealers — to access associated Snowflake accounts, leading to the sale of information belonging to more than 550 million Ticketmaster customers on the dark web.
The info was sold by a group known as “ShinyHunters”, a known player in the infostealer business that’s notorious for using legitimate credentials to obtain initial access.
The ShinyHunters group also claims to have information related to 30 million customers and 28 million credit card numbers associated with the breached banking institution.
Although we focus on these two instances here, they reflect two of at least 165 Snowflake customer accounts that were accessed by this specific threat actor using credentials harvested through infostealers.
How can organisations protect themselves?
Although there may have been various security oversights involved with the two aforementioned breaches, I believe the following three factors played the biggest role:
Another factor that often plays a role when it comes to SaaS security is the popular misconception that the Cloud Service Provider is responsible for your data in the cloud. In reality, YOU as the customer remain responsible and accountable for the security of and access control to data in the cloud.
1. Lack of end user email and browser protection – Among cyber criminals, the most popular means of malware delivery are through email and internet downloads. Not having adequate email and browser security allowed for the initial delivery of the malware.
2. Lack of endpoint protection – Endpoint devices were not properly secured against malware such as infostealers, allowing the malware to be deployed on devices.
3. Lack of SaaS security – The absence of additional security controls, such as Multi-Factor Authentication, allowed for easy access using stolen credentials.
Let’s unpack the items listed above to get a better understanding of how each played a role in the mentioned breaches.
Email and browser protection
Infostealers are typically delivered through internet downloads, phishing emails and or other social engineering attacks.
Your first line of defense for the delivery of infostealers lies in the deployment of email security and anti-phishing solutions such as Harmony Email and Collaboration, which will prevent the delivery of phishing emails and emails containing malware.
Further, should a malicious email be delivered containing a malicious link, having adequate browser protection should prevent the browser from accessing the link and malware from being downloaded.
Internet access control and browser security solutions, such as Harmony SASE Internet Access, will prevent the download of malicious files and restrict corporate password re-use on non-corporate websites.
Corporate password re-use and other password best practices
Although passwords should NEVER be used as the only means of authentication, we often still find this to be the case for various organisations and applications. NIST and other similar institutions provide various guidelines and best practices related to passwords. However, it is also important to note that other than corporate password re-use restrictions, none of these password recommendations from NIST or other similar institutions would have really offered protection from infostealers; mainly because infostealers exfiltrate cleartext passwords.
If you still rely on passwords, the following guidelines from NIST may assist you:
Increase password length – Password length matters more than complexity.
Avoid corporate password re-use – Ensuring that corporate passwords aren’t re-used for other platforms, such as social media, will keep your corporate credentials and systems protected from external credential breaches.
Breached password protection – Ensure that attempted password updates do not contain known breached passwords
Password rotation – Contrary to popular beliefs, the NIST advises against rotating passwords too often and regards 30 to 60 days as too often. Ninety days may be a fair compromise.
Endpoint protection and response
From an endpoint perspective, Endpoint Detection and Response (EDR) remains as one of the primary defenses against malware such as infostealers. EDR solutions typically include both signature-based detection mechanisms as well as behaviour based detection mechanisms, which include analyses of data to detect suspicious activity, such as indicators of compromise (IOCs).
A solution like Check Point’s Harmony Endpoint leverages Check Point’s ThreatCloud; a dynamically updated service based on an innovative global network of threat sensors and organisations that share threat data. It collaboratively fights against modern malware by aggregating and analysing big data telemetry and millions of Indicators of Compromise (IoCs).
Over 50 AI-based engines analyze this data. These engines detect and neutralize novel threats, ensuring that both known and unknown threats are addressed and prevented.
Multi-factor authentication
Most Software as a Service (SaaS) offerings have multi-factor authentication available as a configurable option. If your organisation is making use of SaaS offerings, it is critical that multi-factor authentication is configured. Password authentication alone is NOT adequate and should never be used, especially not on publicly exposed SaaS applications.
Although multi-factor authentication may not have completely eliminated the chances of these breaches occurring, it would have at the very least forced far greater costs and efforts onto the attackers. These efforts would also have to involve additional threat vectors, thereby increasing the probability of detection.
The adoption of cloud services, in combination with the “hybrid workforce” has significantly increased organisations’ attack surfaces, leading to greater exposure, risk and complexities. To overcome this, organisations are looking at adopting solutions such as Zero-Trust and SASE.
Zero-Trust
Zero-Trust, at its core, revolves around the idea of NO ACCESS or ZERO ACCESS, unless we can explicitly identify the device, the individual using the device and the security posture associated with both the device and the user. Zero Trust also enforces further concepts such as “least privilege.”
Zero-Trust Network Access (ZTNA) is still often perceived as being a very costly, time consuming and difficult exercise. However, modern solutions, such as Secure Access Service Edge (SASE), really simplify the implementation of Zero Trust.
In this specific instance, SASE with Secure Internet Browsing would have prevented the download of malware or infostealers from the internet.
The deployment of SASE would also allow organisations to further secure their SaaS applications by enforcing IP address based access restrictions on the SaaS application itself.
This will ensure access to the SaaS application ONLY if the device adheres to corporate security posture restrictions and your identity have the appropriate permissions.
In Conclusion
The threat posed by infostealers deserves the same attention as that posed by ransomware, and perhaps even more so, as infostealers often serve as enablers for much larger cyber attacks and breaches.
In the past, we have observed credentials obtained from infostealers being used for initial access during other malicious activities. These stolen credentials open a broader exploitation landscape, which could include personal accounts, corporate accounts, and even infrastructure access through VPNs and cloud management interfaces.
Protection from the risks posed by infostealers require a holistic approach, bringing us back to “good ole” “defense-in-depth”.
First, prevent the initial delivery of infostealers by protecting end users from malicious emails, websites and malware via email and internet access security controls.
Secondly, should email and internet access security controls fail, having an endpoint detection and response solution deployed should prevent the infostealer from being installed on devices and/or prevent credentials from being exfiltrated.
Other controls, such as Zero-Trust frameworks and SASE, further support the concept of defense in depth by preventing access; even with adequate credentials should other factors such as geo-location, device posture and so forth not check out.
Professional services, such as penetration testing, external attack surface assessments and continuous threat exposure management can also assist in reducing the risk posed by infostealers, as they can highlight weak security controls, such as password-only authentication.
For more insights from Hendrik de Bruin, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2023#access control#Accounts#ai#analyses#Analytics#applications#approach#Articles#as a service#Attack surface#attackers#attention#authentication#banking#Big Data#breach#browser#Business#Check Point#Check Point Software#Cloud#Cloud Management#cloud service#cloud service provider#cloud services#Collaboration#complexity#compromise#computer
0 notes
Text
How Biometric Devices Improve Employee Time Tracking
In an era where organizations strive for efficiency, accuracy, and security, managing employee attendance has evolved from traditional punch cards and manual logbooks to high-tech solutions. Among the most transformative innovations is the biometric device, a software that has revolutionized how companies track and manage employee time.
Whether you're a small business or a large enterprise, ensuring accurate time tracking is essential for payroll, productivity, and workforce management. Biometric devices offer a modern solution by linking attendance to unique human characteristics such as fingerprints, facial recognition, or iris scans - making time fraud and buddy punching things of the past.

What Is a Biometric Device?
A biometric device is a piece of hardware used to identify individuals based on unique biological traits. In the context of workplace management, these devices are typically deployed for access control and attendance tracking. Unlike traditional systems that require ID cards or PINs, biometric systems ensure that only the actual individual can clock in or access a restricted area.
Biometric devices can come in various forms:
Fingerprint scanners
Facial recognition systems
Iris recognition devices
Voice recognition tools
The growing popularity of biometric technology is due to its speed, accuracy, and ease of integration with other HR and payroll systems.
Common Problems with Traditional Time Tracking Methods
Before diving into how biometric devices improve employee time tracking, it’s worth understanding the limitations of traditional systems:
Buddy punching: Employees clock in or out for each other, leading to time theft.
Manual errors: Human oversight when entering or correcting data can lead to payroll discrepancies.
Lost or stolen access cards: These can pose both a security and operational risk.
Lack of real-time data: Delayed updates make it difficult to monitor workforce performance.
These challenges not only impact payroll accuracy but also affect overall productivity and morale.
How Biometric Devices Transform Time Tracking
1. Accuracy and Reliability
Biometric devices are incredibly accurate. Because they rely on individual traits that cannot be duplicated or shared, they offer reliable verification each time an employee clocks in or out. This eliminates common issues like buddy punching or fraudulent time logging.
For instance, a facial recognition-based biometric device ensures that only the authorized individual can record attendance. This means more accurate payroll processing and fewer disputes between HR and employees.
2. Real-Time Attendance Monitoring
Biometric systems provide real-time data on employee attendance. This allows HR departments and team managers to monitor punctuality, break times, and absenteeism more effectively. Cloud-based biometric devices like those offered by Spintly offer real-time syncing across multiple locations, perfect for businesses with distributed teams or multiple branches.
This live data can be accessed through dashboards and reports, offering actionable insights that go beyond mere attendance tracking.
3. Integration with Payroll and HRMS
A modern biometric device does more than log time. Many advanced systems integrate seamlessly with Human Resource Management Systems (HRMS) and payroll software. This eliminates the need for manual data entry, ensuring timely and accurate salary processing, tax compliance, and leave management.
Solutions like Spintly’s biometric access control and attendance management platforms are built with open APIs, making it easy to integrate with third-party software - resulting in a streamlined workflow and reduced administrative burden.
4. Improved Compliance and Audit Trail
Maintaining proper records of working hours is essential to comply with labor laws and industry standards. Biometric devices automatically log every time an employee enters or exits the workplace, providing a secure and tamper-proof audit trail.
This data becomes especially useful during labor audits or legal disputes, ensuring organizations remain compliant without having to dig through manual records.
5. Contactless and Hygienic Options
In the post-pandemic world, hygiene has become a critical consideration in workplace technology. Modern biometric devices now offer touchless options, such as facial recognition and mobile-based check-ins, which minimize physical contact.
Cloud-enabled platforms like Spintly even offer mobile-based biometric attendance solutions, where employees can check in via their smartphones - reducing shared touchpoints while maintaining strict security protocols.
Industry Use Cases
1. Corporate Offices
Biometric time tracking helps monitor in-office attendance while integrating with access control systems to manage entry permissions.
2. Manufacturing & Industrial Units
These devices ensure workers clock in accurately despite working in high-volume shifts, often across different parts of the plant.
3. Healthcare Institutions
Hospitals benefit from biometric tracking to maintain 24/7 shift records and manage attendance in a critical-care environment where staffing is essential.
4. Educational Institutions
Schools and colleges use biometric devices to track faculty and staff attendance while maintaining secure access to restricted areas.
Advantages Over RFID and PIN Systems
While RFID cards and PINs offer basic functionality, they’re prone to misuse and loss. A biometric device offers a level of certainty and convenience that traditional systems can't match. Employees can’t forget or lose their fingerprint or face, making the system more dependable and reducing the cost and hassle of replacements.
Furthermore, combining biometric devices with access control solutions, such as those provided by Spintly, enhances building security. The system ensures that only verified individuals gain access to sensitive areas, creating a safer workplace.
Key Features to Look for in a Biometric Device
If you're considering investing in a biometric time tracking solution, keep the following features in mind:
Cloud connectivity for remote access and real-time syncing
Integration capabilities with HRMS and payroll systems
Touchless operation for post-COVID hygiene standards
Mobile authentication for flexible, remote check-ins
Data encryption to protect biometric data and ensure compliance
Providers like Spintly are paving the way for secure, scalable, and easy-to-deploy biometric solutions that fit businesses of all sizes.
Conclusion
In a digital-first world, managing your workforce with accuracy and efficiency isn’t just about technology - it’s about trust, compliance, and operational excellence. A biometric device simplifies employee time tracking while eliminating common pitfalls like buddy punching, manual errors, and data delays.
By integrating biometric attendance with access control and cloud-based dashboards, organizations get a holistic view of employee movement and performance. Solutions such as Spintly’s smart biometric access platform are leading this transformation by offering sleek, wireless systems that combine convenience with security.
Whether you're looking to tighten security, reduce administrative overhead, or simply improve the employee experience, adopting a biometric solution could be the smartest investment your business makes this year.
#biometric machine#biometric attendance#biometric access#mobile access#attendance management#time and attendance software#accesscontrol#spintly#smartacess#biometrics#smartbuilding#visitor management system#access control solutions
0 notes
Text
Streamlining Amusement Park Entry: Modern Solutions for Efficient Visitor Management
Efficient visitor entry management is crucial for amusement parks to enhance guest experiences, ensure safety, and optimize operations. With advancements in technology, parks can now implement systems that facilitate seamless entry processes.
The Importance of Efficient Entry Management
Long queues and manual ticket checks can detract from the visitor experience. Implementing streamlined entry systems not only improves guest satisfaction but also aids in crowd control and security.
Key Components of Modern Entry Management Systems
1. Online Ticketing and Pre-registration
Allowing guests to purchase tickets online and register in advance reduces wait times at entry points. This system can also provide valuable data on expected attendance, aiding in resource planning.
2. Contactless Entry Solutions
Utilizing QR codes or RFID-enabled wristbands enables quick and hygienic access to the park. These methods minimise physical contact and expedite the entry process.
3. Real-time Monitoring and Analytics
Implementing systems that monitor visitor flow in real-time allows for dynamic crowd management. Data analytics can help identify peak times and areas, facilitating better staff allocation and enhancing safety measures.
4. Customisable Access Permissions
Advanced systems can assign different access levels to various visitor categories, such as VIPs or group tours, ensuring a tailored experience and efficient movement within the park.
5. Automated Notifications and Alerts
Integrating alert systems that notify staff of large group arrivals or potential security concerns enables proactive management and swift response to situations.
Benefits of Implementing Advanced Entry Management
Enhanced Guest Experience: Reduced wait times and personalised services lead to higher satisfaction.
Improved Operational Efficiency: Automation reduces manual workload, allowing staff to focus on guest engagement.
Increased Security: Real-time monitoring and controlled access points bolster safety measures.
Data-driven Decisions: Analytics provide insights into visitor behavior, informing marketing and operational strategies.
Adopting modern visitor entry management systems for amusement parks is essential, aiming to provide exceptional guest experiences while maintaining efficient and secure operations. By embracing technological advancements, parks can ensure smooth entry processes, better crowd control, and enhanced overall satisfaction. Upgrade your amusement park with smart entry solutions – Contact Parkomax today for seamless, secure, and data-driven visitor management!
#Visitor Entry Management System#Amusement Park Entry Solutions#Entry Management for Theme Parks#Parkomax Entry Systems#Smart Access Control for Parks#Contactless Entry Systems#RFID Wristband Entry#QR Code Ticketing#Real-time Visitor Monitoring#Automated Park Entry#Secure park entry system#Online ticketing system for amusement parks#Park access control technology#Smart ticketing solutions for theme parks#Amusement park management software
0 notes