#Computer Technical Support
Explore tagged Tumblr posts
Text
Trusted Home Computer Repair Services by Mobile Computer Repair

Mobile Computer Repair offers reliable and efficient Home Computer Repair Services tailored to meet your everyday tech needs. Whether it’s a slow PC, virus issues, hardware upgrades, or software troubleshooting, our certified technicians come directly to your home for fast and friendly service. We handle all major computer brands and ensure your system runs smoothly with minimal downtime. No need to disconnect or carry anything—we provide onsite solutions you can trust. Serving both urgent fixes and regular maintenance, Mobile Computer Repair is your go-to choice for professional and affordable home computer repairs. Backed by years of experience and customer satisfaction, we make technology stress-free right at your doorstep. Get expert service today with the personal touch you deserve.
#Home Computer Repair Services#Desktop Computer Repair#Computer Technical Support#Affordable Computer Repair
0 notes
Text

Nerdcore Computers offers onsite computer repairs to businesses around Australia. Our team of data recovery experts, Business it experts, networking engineers, it business consultants are ready to assist your staff with any it issues your business is faced with.
The Nerdcore Group technicians have the right training and experience to handle all networking issues, no matter how big or small. We can consult with your business to set up a local, national or global network, or we can come to your home to get your computer talking to your smart tv and your TV talking to your smart fridge – if it’s one of those Jazzy ones
#nerdcore computers#nerdcore pc sytems#computer repairs#onsite compute repairs#home compuer repairs#nerdcore pc#local computer repairs#data recovery#computer technical support
0 notes
Text
I wonder if Half Life is so slow on my netbook because of Wine or because of the shitty GPU. It is slower on software rendering mode, but when in OpenGL mode it's not using 100% CPU.
#half life#wine#Linux#i am aware that there is a native linux version of HL#and i actually own it#but its the steam version#and theres no retail linux version#and steam doesnt support 32 bit computers#i mean it technically does#but no matter what it still tries to install 64 bit libraries and erroring out#so im playing the GOTY edition i found online
7 notes
·
View notes
Photo

(via GIPHY)
#giphy#cat#kitty#kitten#support#cyberpunk#work in progress#computers#keep calm#cable#mischief#international cat day#servers#g5 games#cat day#technical difficulties#please stand by#log in#hidden city#technical issues#working on the fix
7 notes
·
View notes
Text
NeedTechAdvice Blog - Latest Tech Tips, Gadgets Reviews & Expert Tech Advice
Welcome to the NeedTechAdvice Blog, your go-to source for the latest tech tips, gadget reviews, and expert insights. Whether you’re exploring the newest gadgets, upgrading your devices, or seeking tech solutions, our blog offers valuable advice and in-depth reviews to keep you informed. From everyday electronics to car tech, dive into a world of smarter digital living with us. https://www.needtechadvice.com/index.php/our-blog/

#online shopping#latest gadget tips#expert tech advice#latest gadgets#technology reviews#gadget shopping tips#tech expert#car tech products#computer electronics tips#gadget tips#technical advice for latest gadgets#expert tech support#electronics tips#gadgets expert
2 notes
·
View notes
Text
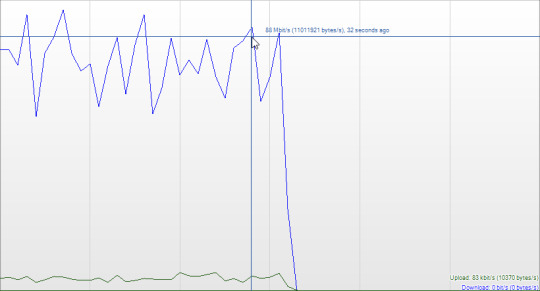
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
129K notes
·
View notes
Text
Commercial Underwriter (Fully Remote or Hybrid-Working) - Leeds
Job title: Commercial Underwriter (Fully Remote or Hybrid-Working) – Leeds Company: Aston Charles Job description: enquiries from a wide variety of brokers throughout the UK, using your sound technical and negotiation skills to secure…, collaborating with the Claims team, as well as developing and maintaining excellent working relationships with the Technical… Expected salary: Location: Leeds Job…
#Automotive#Azure#Backend#Bioinformatics#Blockchain#Broadcast#cloud-computing#Crypto#CTO#Cybersecurity#data-privacy#data-science#dotnet#fintech#Frontend#GIS#HPC#iot#it-support#Java#mobile-development#Networking#NLP#prompt-engineering#regtech#remote-jobs#Salesforce#system-administration#Technical Writer
0 notes
Text
Empower Your Business with Dedicated IT Resources from Quarec Resources Pvt. Ltd.

At Quarec Resources Pvt. Ltd., we provide top-tier Dedicated IT Resources to propel your business forward. Our skilled IT professionals seamlessly integrate with your team, offering expertise in software development, system administration, network management, and more. By choosing our dedicated resources, you gain flexibility, cost-efficiency, and the ability to swiftly adapt to evolving technological demands. Partner with Quarec to ensure your IT operations are robust, scalable, and aligned with your strategic goals.
#Dedicated IT Resources#IT Staff Augmentation#Dedicated IT#Software Development Team#System Administration Services#Network Management Solutions#IT Outsourcing#Remote IT Support#IT Consulting#Cloud Computing Services#Cybersecurity Solutions#Data Analytics Services#IT Project Management#Technical Support Services#IT Infrastructure Management
0 notes
Text
Support Computer Science Education: Technician/Senior Technician Opportunity at NUST! - March 2025
The National University of Science and Technology (NUST) is seeking a skilled and versatile Technician/Senior Technician to join their Department of Computer Science! If you’re passionate about providing technical support in a computer science environment, and have experience in software development, network administration, and desktop support, this is an excellent opportunity. About the…

View On WordPress
#ai#Bulawayo Jobs#Computer Science Jobs#Desktop Support Jobs#Hot Zimbabwe Jobs#IT Jobs#Job Opportunity#Linux#Network Administration Jobs#NUST Jobs#software#Software Development Jobs#Technical Support Jobs#Technician Jobs#technology#University Jobs#Windows#Zimbabwe Jobs
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text
Apple iPhone 16 Pro -NeedTechAdvice

The iPhone 16 Professional is Apple’s newest flagship, that includes a Grade 5 titanium design that makes it each sturdy and light-weight. It is available in two sizes: 6.3-inch and 6.9-inch Tremendous Retina XDR shows with thinner borders for a extra immersive expertise.
Some standout options embody:
A18 Professional chip for enhanced efficiency, particularly in high-intensity duties like gaming.
Superior digital camera system with a 48MP predominant sensor, 48MP ultra-wide, and telephoto lenses, able to 4K video at 120 fps.
Apple Intelligence for improved productiveness and privateness, providing instruments like writing help and picture creation.
New show expertise that routes information underneath energetic pixels, leading to thinner borders.
Enhanced sturdiness with splash, water, and dirt resistance, and a harder Ceramic Defend materials.

The iPhone 16 Professional gives spectacular battery life, because of its 3582 mAh battery and the ability effectivity of the A18 Professional chip. In checks, it lasted round 14 hours and seven minutes on a single cost. It is a vital enchancment over the iPhone 15 Professional, which managed about 10 hours and 53 minutes.
The bigger iPhone 16 Professional Max has an much more exceptional battery life, lasting as much as 18 hours and 6 minutes. This makes it one of many prime performers in its class.
The iPhone 16 Professional boasts a formidable digital camera system designed to raise your images and videography expertise:
48MP Primary Fusion Digital camera: This digital camera encompasses a second-generation sensor-shift optical picture stabilization and 100% Focus Pixels, making certain sharp and detailed pictures even in low gentle.
48MP Extremely Broad Digital camera: With a 120° subject of view and Hybrid Focus Pixels, this digital camera is ideal for capturing expansive landscapes and macro pictures.
12MP 5x Telephoto Digital camera: The telephoto lens gives a 5x optical zoom with a tetraprism design, permitting for high-quality close-ups with out shedding element.
4K Video Recording: The iPhone 16 Professional helps 4K video at 120 frames per second, offering easy and high-resolution video seize.
Subsequent-Technology Photographic Types: These permit you to modify colour, highlights, and shadows in real-time, providing you with extra artistic management over your pictures.
Evening Mode and Evening Mode Portraits: Enabled by the LiDAR Scanner, these options allow you to seize beautiful pictures in low-light situations.
Apple Intelligence: While still in beta, Apple Intelligence offers intriguing features like Visual Intelligence for object identification and advanced photo editing tools.
AI and Software Programs
The iPhone 16 Pro integrates advanced Apple Intelligence to enhance user experience across various tasks:
Writing Tools
Proofreading and Rewriting: AI-powered tools can proofread your text and rewrite it to match the desired tone and wording. These features are available in most writing apps, including third-party ones.
Summarization: You can record audio in the Notes or Phone app, and Apple Intelligence will generate summaries of your transcripts, highlighting the most important information.
Visual Creativity
Genmoji: Create personalized emojis directly from your keyboard by providing a description. This feature allows for fun and unique visual expressions.
Image Playground: Generate unique images based on descriptions, concepts, or even people from your Photos library. Experiment with different styles like animation, illustration, and sketch.
Clean Up: Easily remove distracting background objects from your photos with a single tap, helping you perfect your shots.
Siri Enhancements
Context Awareness: Siri can now assist you with tasks based on your personal context. For example, it can help you find your passport number while booking a flight, all while maintaining your privacy.
Productivity Boost
Priority Messages: Important messages in Mail are elevated to the top of your inbox, ensuring you don’t miss time-sensitive information.
Camera Control Button: The iPhone 16 Pro Max introduces a new customizable Camera Control button on the right side. This button not only provides instant access to the camera but also supports gesture recognition and haptic feedback, making it a versatile tool for photographers.
Apple Intelligence: While still in beta, Apple Intelligence offers intriguing features like Visual Intelligence for object identification and advanced photo editing tools.

We will be happy to hear your thoughts -NeedTechAdvice
For More Visit Our Website: https://needtechadvice.com/
#Apple iPhone 16 Pro#Apple iPhone 16 Pro NeedTechAdvice#Apple iPhone 16Pro#Apple iPhone#iPhone#Smart Phone#technical advice for electronics#latest gadgets#expert tech support#computer#electronics#car products#onine gaming#AppleiPhone16Pro#AppleiPhone16ProNeedTechAdvice#AppleiPhone#SmartPhone
1 note
·
View note
Text
my trying to get out of reading fmdm shouldn't be taken as an indicator that it's not good (it is) or that i don't rlly like it (i do) but instead as an indicator that i probably have undiagnosed adhd and can't read/watch/whatever long media without sprinkling in shorter media in the same medium bc i need the gratification of actually finishing something in order to keep going . fmdm is 42 hours and totono is 15 hrs (and a lot less if you're not a completionist which i am not in this regard bc i've already gone through it) . i'll probs throw at Least a saya no uta replay* (6hrs) in there as well before i'm done w fmdm
#(*technically i watched a playthrough on youtube bc this computer is new and my old one couldn't support most vns etc etc)#romeo.txt
1 note
·
View note
Text
Bruce should absolutely get dragged for being an overbearing control freak with boundary issues
Babs should absolutely NOT be the one to do it

Ha ha kick his ass babs
#Dick should probably be the one to drag them both#Tim should probably also be dragged for it#but the ones he's done it to the most have looped around to finding it endearing#he skates by on technicality#bruce wayne#barbara gordon#also hot take I'm hiding here in the tags#I find Babs and Dick as a couple less endearing as time goes on#I just want them to be friends at this point#and I want Babs to have friends who pull her away from the computer when she gets weird over his new partners#she should get to be a little toxic as a treat#with a support network ready with a spray bottle and a thousand yard stare
536 notes
·
View notes
Text
alex hirsch + friends charity draw-a-thon highlights
jason ritter (dipper's va) showing his almonds to the audience during the 40-60 minutes of technical issues at the start of the stream
kristen schaal (mabel's va) alternating between very sweet and heartfelt bits about how art and the joy you find in it should never leave you regardless of what you do and supporting all of the people around her and then being crabby about screens and technology to the point where they start a bit about her playing the unabomber
jason constantly switching out his hats
billford drawing
alex hirsch: "i don't know what a jerma is. how old do you think i am?"
jason's honestly amazing performance of chappell roan's pink pony club
alex explaining to kristen that people thirst for stanford pines, ft. matt braly (director on gravity falls, creator of amphibia, and resident tech support + artist on the stream) casually breaking down ford's appeal (j.k. simmon's recording immediately followed this bit)
kristen doing multiple bits lowkey involving doxxing alex hirsch
jason wearing a model wirt head
kristen's 'gravity falls musical' that she wrote an hour before the stream in the car
j.k. simmons' recording of ford reading thirst posts being labelled "INSANE MESSAGE.wav" on alex hirsch's computer
everyone drawing waddles
matt: "can i see nosferatu if i haven't seen nosfera-one?"
alex as grunkle stan and kristen as mabel singing defying gravity from wicked, ft. mabel calling stan a bitch and yelling "the FUCKING wizard"
cut pages from the book of bill, including a honestly really cool diagram of bill's 'anatomy' that was cut for time
the ship wheel begetting alex hirsch drawing walter white/wolverine
the really cute drawing of dipper and mabel as link and zelda
jason almost saying 'selfcest' cause of the chat (in reference to steve/steve) and just stopping at 'self' like four times
jason and kristen singing espresso by sabrina carpenter
alex casually mentioning that matt apparently keeps trying to trick him into reading the entire script of the iron giant in his grunkle stan voice
#gravity falls#it was honestly a very funny time#they were very clearly overwhelmed by the turnout + donations in the beginning#rené.txt#just adding like. there was a bunch of other very funny shit that i did not include just bc i didnt want to make the post long
2K notes
·
View notes
Text









Tech Support: Part 3
[1-2-3]
Yes, this was a real thing we had to help with once.
Even though he complains, Donnie feels a lot of pride being looked to as the family expert for these things, I’m sure. For all that Splinter probably doesn’t know the deep intricacies of computers, I’ll bet he knows the basics. Could there be a deeper meaning to his confusion?
I personally headcanon that Splinter is the one who introduced computers, phones, and appliances to his sons way back in the dumpster diving days, and probably showed Donnie how to fix his first toaster or something. However, the special interest kicked in hard and pretty soon Donnie could run circles around Splinter when it came to fixing and engineering stuff. Perhaps, this is a way Splinter can find time to partake in Donnie’s interests and boost his confidence despite being way out of his depth on technical know-how himself.
When you don’t have a lot, it’s important to be resourceful and handy with a quick fix. Donnie had to have started building stuff somewhere!
It makes it all the more bittersweet if they were really close only to have Splinter struggle to bond with Donnie when he’s a little older. Don’t worry though, they’ll figure it out :)
#rottmnt#rise of the teenage mutant ninja turtles#rise of the tmnt#rottmnt comic#rise donnie#rise mikey#rise raph#rise leo#rottmnt donnie#rise splinter#t*cest dni#let Splinter be a good dad#I think everybody could use a little heartwarming parental love in their lives#even if family can be really annoying sometimes lol
5K notes
·
View notes