#Cybersecurity Testing
Explore tagged Tumblr posts
Text
Boost Your Digital Success: Why Performance and Security Testing Are Essential
The Importance of Performance and Security Testing for Your Digital Success
In the current rapid digital space, organizations increasingly depend on their applications and websites to connect with customers, manage processes, and generate revenue. When a digital platform is poorly developed with respect to performance or security, it can negatively impact missed opportunities, reputation, and substantial monetary losses. This is where the important processes of performance and security testing fit in. They are important processes that can help ensure your digital resources are strong, dependable, and secure, with a competitive advantage for your organization. In this blog, we will discuss why performance and security testing are essential complete processes, areas of advantage, and what role they play in your digital success.
What is Performance Testing?
Performance testing is the method of assessing how well a system, application, or website performs under various conditions. More precisely, performance testing should encompass speed, response time, scalability, and stability to ensure that, regardless of the platform, it can effectively handle user demand. Performance testing ensures that applications are still efficient and easy to use during any sudden spikes in traffic or when performing complex computational tasks.
There are several important types of performance testing:
Load Testing: Assesses how the system performs when it is under what is expected user load.
Stress Testing: Assesses how the system performs by overloading the system in extreme conditions to assess its breaking point.
Scalability Testing: Solves whether the system can grow or shrink in its ability to meet user demands.
Endurance Testing: Measures and screens performance for long durations to identify social issues like memory leaks.
Performance testing assists businesses in identifying their bottlenecks and weaknesses, which then provides their users with a seamless user experience at all times, especially during peak usage.
Why Security Testing is Essential
In a world where cyber threats are becoming more commonplace, security testing is the first step in protecting sensitive information and maintaining user trust. Security testing exposes vulnerabilities inherent in your application or system that may be exploited by a malicious actor. A weakness in security could lead to catastrophic consequences, such as data breaches or ransomware attacks.
Key Aspects of Security Testing
Vulnerability Assessment: Discovers possible weaknesses in the system, like software that incorporates outdated libraries or systems that are poorly configured.
Penetration Testing: Enables testers to be hostile and review exploitable vulnerabilities in web applications or systems.
Security Audit: Reviews code, frameworks, and configurations concerning an industry's benchmark.
Risk Assessment: Assesses possible threats to a business.
The results of security testing will help in the increased discovery of vulnerabilities and the reduction of financial losses, lawsuits, and damaged reputations for businesses.
The Importance of Performance and Security Testing
1. Improved User Experience
Users will not tolerate a site or app that takes too long to load. Slow and inconsistent performance can lead to high bounce rates and lost conversions. Performance testing can improve the speed, reliability, and consistency of your web platform, which increases both the likelihood of use and overall user experience.
2. Safeguarding Against Cyber Attack
Cyber threats are not just a concern for larger enterprises; small businesses are also now being targeted by attack vectors that previously affected larger enterprises. As threats become more advanced, security testing is a key tool for spotting weaknesses, mitigating them before hackers can exploit them, and ultimately safeguarding your data, as well as your customers’.
3. Reduce Overall Costs
Performance and security problems that come after deployment are expensive problems to fix. Early detection through testing minimizes expensive fixes that will ultimately hurt your bottom line and minimize the risk of downtime or breaches to your application.
4. Compliance
There are strict guidelines and regulations in place in certain industries, particularly finance, healthcare, and e-commerce (also GDPR and PCI DSS). Security testing can help provide evidence of compliance and save you from fines or legal formalities.
5. Scalability
There are growth concerns depending on the accuracy of your report and the possible hurdles of growth your web service could face. Performance testing helps avoid any issues that can arise from suddenly increased numbers of traffic or usage.
Best Practices for Effective Testing
Test early, test often - Each stage of the development lifecycle lends itself to testing to find issues as early as possible.
Test realistic user behaviours - Take advantage of user behaviours that are as realistic as you can for testing, along with their attack behaviours, as testing will give more realistic outputs.
Automate your testing - Automated testing tools will help you save time and improve precision in repeatable tasks.
Work with a provider - Using a provider of testing services, like GQAT Tech, will give you reliable results and clear issue identification.
Monitor continuously - Continuous testing and monitoring will allow the systems to always remain secure and performant as they relate to new threats and demands.
Why Choose Professional Testing Services?
Internal testing is important, while using a testing provider will provide expertise, available and advanced tools, and insight from both sides of the testing process. A provider like GQAT Tech will provide testing services in either performance or security testing and can work to your needs. Our teams are very experienced and perform established methodologies that will identify and then remediate existing issues found on your digital platforms or websites to ensure they work correctly, are performant, and secure.
Conclusion
In a time of increasing user expectations and continuous risk, we should view performance and security testing as a need instead of an option. When companies perform continuous performance and security testing, they can produce a great user experience, protect sensitive content from prying eyes, and create a great opportunity for success at scale. The sooner performance and security testing are utilized, the sooner your platform can thrive, whether you are developing a new application or scaling an existing one.
Do you think you are ready to elevate your digital platforms? Start with GQAT Tech's professional testing to take your first step towards a faster, safer, and more reliable digital footprint.
#Performance Testing#Security Testing#Load Testing#Software Optimization#Application Security#QA Performance#Cybersecurity Testing#Stress Testing#GQATTECH
0 notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
2 notes
·
View notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

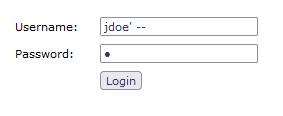
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
2 notes
·
View notes
Text
Staying Relevant: Balancing Learning and Life as an Ethical Hacker
Have you experienced burnout while trying to develop your skills and you just don't have the time to do everything? Finding balance is the key to improving your skills in a healthy way. In this article, I explore healthy habits to grow without burning out
You’ve heard it before – cybersecurity is a field that evolves at a blindingly fast pace. The tools, techniques, and technologies threatening networks transform rapidly. As an ethical hacker, your skills can become obsolete within months if you aren’t continuously upgrading your knowledge. Point #4 on our hacker roadmap deals with knowing the latest and greatest when it comes to the state of…

View On WordPress
#burnout#certifications#conference#continuous learning#Cyber Security#cybersecurity education#cybersecurity skills#Ethical Hacking#hacker skills#infosec community#leadership#learning plan#maintaining balance#microlearning#Penetration Testing#pentesting methodologies#personal development#podcast#red team operations#security news#security policies#security tools#time management#trends#vulnerability assessments#work-life balance
3 notes
·
View notes
Text
In today's digitally connected world, cyber security has become a paramount concern. It encompasses the practice of safeguarding systems, networks, and data from digital attacks, unauthorized access, or damage. With the rapid growth in online transactions, social media, and Internet of Things (IoT) devices, vulnerabilities have increased, making cyber security more critical than ever.
Attackers employ a variety of methods, such as malware, ransomware, phishing, and social engineering, to breach defenses. Individuals, businesses, and governments must stay vigilant by keeping software up to date, utilizing strong, unique passwords, and employing multi-factor authentication.
Investing in robust security measures not only protects sensitive information but also maintains trust and integrity in digital relationships. In an era where data breaches can lead to significant financial and reputational losses, cyber security is not just a technological concern but a fundamental aspect of modern life.
4 notes
·
View notes
Text
#Performance Testing#Security Testing#Load Testing#Software Optimization#Application Security#QA Performance#Cybersecurity Testing#Stress Testing#Mobile App Testing#Android Testing#iOS App Testing#Cross-Device Testing#Mobile QA#Mobile Automation Testing#App Performance Testing#Real Device Testing#Functional Testing#Software QA#Feature Validation#System Testing#Manual Testing#Automated Functional Testing#End-to-End Testing#Black Box Testing#ETL Testing#Data Validation#Data Warehouse Testing#BI Testing#Database QA#Data Quality Checks
0 notes
Text
the last time something like this happened it was in 2010, with a McAfee virus protection update:
and guess who was Chief Technology Officer at the time? a guy called George Kurtz, who went on to become the founder and CEO of CrowdStrike 🙃
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.
#the connection might mean nothing and this is just something that happens every decade or so to very large cybersecurity software providers#but....it does seem to suggest the testing protocol has Problems#in the news#sign of the times#dove.txt
114K notes
·
View notes
Text
VirtualBox Guest Additions on Kali Linux Install Guide 2025
Installing VirtualBox Guest Additions on Kali Linux packages correctly is crucial for optimal virtual machine performance. Many users struggle with fullscreen display issues, shared folders, and clipboard functionality when running Kali Linux on VirtualBox. This comprehensive guide provides the definitive method for installing these essential packages in 2025. Check the 256MB Video memory and 4GB…
0 notes
Text

#information technology#software#software development#testing#automation#awscloud#cybersecurity#digitaltransformation
0 notes
Text
How effective is Red Teaming & Pen Testing?
In today’s digital landscape, ensuring cybersecurity is crucial for organizations of all sizes. One of the key approaches to identifying vulnerabilities in security systems is through Red Teaming and Penetration Testing (Pen Testing). But how effective are these strategies?
Evaluating the Effectiveness of Red Teaming
Through the simulation of real threats, red teaming evaluates an organization's defenses. Here’s how it proves effective:
Comprehensive Security Assessment: It offers an in-depth analysis of security measures and identifies weaknesses.
Realistic Scenarios: By mimicking actual threat actors, it provides a practical understanding of potential risks.
Team Improvement: The exercise fosters collaboration among security teams, enhancing their response strategies.
Assessing the Impact of Penetration Testing
Pen testing focuses on identifying vulnerabilities through controlled attacks. Its effectiveness can be summarized by:
Finding Weak Points: It draws attention to particular weaknesses that an attacker could take advantage of.
Prioritizing Threats: Helps organizations focus on critical areas needing protection.
Regulatory Compliance: Frequently necessary to adhere to rules and industry norms.
Both red teaming and pen testing play vital roles in strengthening an organization’s cybersecurity posture. By proactively identifying vulnerabilities, organizations can better defend against potential threats and ensure a safer digital environment.
0 notes
Text
Are You Prepared for 2025's Top Cyber Threats?
Cybercriminals are getting smarter—and no business is too small to be targeted. From phishing emails and ransomware attacks to insider threats and credential stuffing, understanding today’s most dangerous cyber risks is the first step to securing your systems and data.
0 notes
Text
Penetration testing isn't just about ethical hacking—it's a structured process that helps businesses discover and fix vulnerabilities before real attackers exploit them.
In cybersecurity, the penetration testing lifecycle is typically divided into five essential phases:
Planning & Reconnaissance
Scanning
Gaining Access
Maintaining Access
Analysis & Reporting
Each stage plays a vital role in identifying potential security gaps, especially for businesses in finance, healthcare, and technology sectors.
If you're managing sensitive data or infrastructure, understanding these phases helps you assess risk better and strengthen your defenses.
Dive deeper into the complete breakdown here: Read the Full Guide
1 note
·
View note
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
4 notes
·
View notes
Text
The Artificial Intelligence Role in Penetration Testing and Cyber Defense
Introduction
The internet is growing at a pace never seen before, and cyber attacks are also developing in tandem. Companies all over the world are investing in online cyber security training so that experts are equipped with the tools to protect their networks. Penetration testing, the most critical element of cybersecurity, is a preventive strategy to find out vulnerabilities before the attackers can exploit them. With the introduction of artificial intelligence (AI), penetration testing and cyber defense mechanisms are transforming and becoming better.
This is an article on how AI is revolutionizing penetration testing and cybersecurity, its advantages, disadvantages, and future directions. Understanding what AI is doing in cybersecurity will enable cybersecurity experts to utilize AI-powered tools to further fortify their defenses against constantly changing cyberattacks.
The Growing Importance of Penetration Testing in Cybersecurity
Penetration testing, or ethical hacking, involves the simulation of cyberattacks to test the security stance of a company. It's a common practice in online cyber security courses as well as cybersecurity training since it enables experts to identify vulnerabilities and implement robust countermeasures.
Legacy methods of penetration testing put a great reliance on human resources, which is labor and time-intensive. Ethical hackers have to scan manually for vulnerabilities, assess probable exploits, and emulate attacks. Although the process works, it is normally hindered by human mistake and the sheer amount of potential threats.
The Role of AI in Cybersecurity and Penetration Testing
1. Automated Threat Detection
AI security systems are capable of scanning huge volumes of data in real-time to detect vulnerabilities and potential threats. AI applies machine learning algorithms to detect patterns and anomalies that are indicative of security breaches. Automated threat detection reduces the process significantly, obviating the time required to identify and respond to cyber threats, thereby enhancing the overall security standing of an organization.
2. AI-Based Vulnerability Scanning
Artificial intelligence-based vulnerability scanners may be employed to scan networks, systems, and applications on a continuous basis to identify security vulnerabilities. These scanners employ machine learning to enhance precision, minimize false positives, and initiate only real threats for further investigation. This feature is especially useful for online cyber security training companies, as it enables students to gain hands-on experience in vulnerability scanning based on real-life scenarios.
3. Improved Threat Intelligence
Threat intelligence is an essential element of cyber security. AI is capable of collecting and analyzing information from various sources, such as dark web bulletin boards, threat repositories, and network logs, and providing actionable insights. Organizations can remain proactive against new threats and modify their security strategy accordingly with AI-powered cybersecurity.
4. Ethical Hacking with AI
Ethical hacking demands strong technical expertise and skill, which can be supplemented using AI tools. AI may automate reconnaissance, exploit development, and post-exploitation analysis for ethical hackers. With the addition of AI security tools in ethical hacking, penetration testers can discover vulnerabilities more effectively and create better mitigation plans.
5. Real-Time Incident Response
One of the strongest advantages of AI in cybersecurity is its real-time incident response capability. AI security systems can detect and respond to threats before they can do extensive harm. By analyzing the patterns of attacks and predicting future threats, AI enhances the ability of an organization to prevent cyber incidents proactively.
Benefits of AI Implementation in Cybersecurity Defense and Training
Increased Efficiency and Accuracy
Artificial intelligence -based cybersecurity solutions can process massive amounts of data at unprecedented rates, allowing threat detection and mitigation at an accelerated pace. This efficiency decreases the burden on cybersecurity experts so that they can concentrate on strategic decision-making and incident management.
Cost-Effectiveness
Penetration testing and cyber defense procedures can be greatly minimized in operational costs through automating them using AI. Companies can use their resources more efficiently, making their cybersecurity staff available for high-priority work.
Adaptive Learning
AI security systems learn from emerging threats and adjust their defenses in response. This ability to learn by themselves means that cybersecurity defenses stay current, even against changing cyber threats.
Increased Hands-On Training
Cybersecurity training sessions can incorporate AI-based simulation platforms to offer practical experience in penetration testing and cyber defense. These platforms use actual attack scenarios to enable students to gain practical experience and prepare for actual cybersecurity challenges.
Incorporating AI in Cyber Defense: Challenges
False Positives and False Negatives
While AI improves the efficiency of threat detection, it is not infallible. AI-powered security software sometimes triggers false alarms or fails to detect sophisticated cyber attacks. AI models need continuous monitoring and adjustment to make them more accurate.
Dependence on Data Quality
AI systems depend on large data sets in order to operate efficiently. Outdated or incorrect data can undermine the efficacy of AI-based security systems. Organizations have to make sure that their AI models are trained on current and extensive cybersecurity data sets.
Ethical and Legal Issues
The use of AI in penetration testing and cyber protection is regulated by legal and moral issues. The organizations must ensure that AI-based penetration testing solutions are used responsibly and comply with the regulatory requirements.
Future Trends in AI-Powered Cybersecurity
With advancing AI technology, so will its application in cybersecurity. Some of the future trends are:
AI-Powered Autonomous Security Systems: Emerging cybersecurity systems might utilize completely autonomous AI systems capable of identifying, analyzing, and eliminating threats on their own without any human interaction.
AI-Powered Security Orchestration:AI will be utilized to automate and orchestrate security solutions so that processes of threat response are made more efficient.
AI-Augmented Cybersecurity Training: AI-enabled virtual labs and simulation platforms will be a critical part of cybersecurity training programs, offering students interactive hands-on training.
Quantum Computing and AI Security: With the growth of quantum computing, AI will be at the center of the creation of quantum-resistant cybersecurity regulations.
Conclusion
The use of AI for penetration testing and cyber defense is transforming the landscape of cybersecurity. AI security tools improve threat detection, automate vulnerability scanning, and enhance incident response. Organisations are better positioned to enhance their cybersecurity positioning and remain ahead of new threats with the use of AI security tools.
For working professionals who want to enhance their cybersecurity skills, one must take online cyber security training. Online platforms such as Guruface provide detailed cybersecurity training courses, teaching and practical experience that is necessary to excel in this profession. Since cyber attacks are evolving continuously, investment in cybersecurity training and ethical hacking courses is essential so that one has a strong defense system against cyber attacks.
0 notes
Text
Code. Test. Evolve. How EDSPL Empowers Businesses Through Full-Spectrum Software Solutions

In today’s fast-paced digital ecosystem, businesses need more than just software—they need intelligent, full-spectrum software solutions that grow with them. From idea to execution and beyond, success depends on the ability to code smartly, test rigorously, and evolve continuously.
That’s exactly what EDSPL delivers.
With a commitment to excellence, innovation, and long-term business growth, EDSPL (Enrich Data Solutions Pvt. Ltd.) offers end-to-end software services that don't just meet current needs—they anticipate future demands. In this blog, we explore how EDSPL empowers enterprises at every stage of the software lifecycle, ensuring agility, security, scalability, and success.
From Vision to Reality: EDSPL’s Software Development Philosophy
At EDSPL, software development is not a project. It’s a partnership.
Businesses often approach us with a problem, a vision, or a spark of an idea. Our job is to transform that vision into reality, using cutting-edge technologies, deep domain expertise, and agile processes.
Code: Intelligent Architecture and Development
Our journey begins at the core—clean, efficient, and scalable code.
Whether you're building an internal enterprise tool, a consumer-facing mobile app, or a robust SaaS platform, we start by understanding your objectives, your users, and your long-term strategy. Then we:
Design the software architecture that supports current operations and future growth.
Choose the best-fit technologies—Java, .NET, Python, Angular, React, Node.js, or a customized stack.
Employ agile development cycles that ensure fast delivery and continuous feedback.
Every line of code we write is auditable, secure, and optimized for performance.
Test: Zero-Bug Tolerance Through Intelligent QA
At EDSPL, we believe great code deserves even greater testing. That’s why we embed Quality Assurance (QA) right from Day One.
Our testing methodology is multi-layered:
Unit Testing to ensure individual components function flawlessly.
Integration Testing to confirm all parts work together seamlessly.
System Testing to evaluate end-to-end performance.
User Acceptance Testing (UAT) to verify real-world usability.
Automated Regression Testing to catch bugs before they catch you.
We simulate real-world conditions, heavy traffic, and diverse user behaviors to test system robustness.
Result? Products that are reliable, bug-free, and ready to scale.
Evolve: Continuous Support and Future-Readiness
Unlike vendors who step away after deployment, EDSPL believes in long-term evolution. We provide:
Ongoing support and maintenance
Continuous monitoring and optimization
Feature upgrades and scalability planning
Whether your user base grows tenfold, compliance requirements change, or a new business opportunity arises, EDSPL ensures your software evolves with you.
Why Full-Spectrum Solutions Matter
Most businesses today juggle multiple vendors—developers, testers, cybersecurity experts, cloud consultants, and support teams. This fragmentation leads to:
Communication gaps
Slower delivery cycles
Higher costs
Increased risk of failure
EDSPL solves this.
We are a one-stop technology partner, offering full-spectrum services under one roof:ServiceWhat It IncludesCustom Software DevelopmentTailored solutions for web, mobile, and desktopEnterprise ApplicationsERP, CRM, HRMS, and data management platformsAPI Development & IntegrationSecure, scalable, and fast integrationsDevOps ServicesCI/CD pipelines, automation, and cloud-native deploymentCloud EnablementCloud security, migration, and managementUI/UX DesignWireframes, prototypes, user testing, and design systemsQA & Testing ServicesManual, automated, and performance testingCybersecurity IntegrationApplication security, network security, and more
This 360° approach allows EDSPL to reduce go-to-market time, lower development cost, and maximize ROI.
Human-Centered Design: Because Users Matter
We don’t just build software—we build experiences.
Our dedicated UI/UX team places the user at the heart of every design decision. Through interviews, feedback loops, and testing, we ensure every click, scroll, and swipe adds value.
Because in a competitive market, experience is everything.
Security by Design: Your Peace of Mind
In an era of data breaches and digital espionage, software is only as strong as its weakest link. EDSPL integrates security at every level:
Secure coding practices
Role-based access controls (RBAC)
End-to-end encryption
OWASP top 10 mitigation
Regular VAPT (Vulnerability Assessment and Penetration Testing)
Security isn’t an add-on. It’s built into the foundation of every solution we deliver—from application security to network security.
Cloud-First, Future-Ready
As remote work, scalability, and real-time collaboration become non-negotiable, we help businesses go cloud-native with robust cloud security frameworks.
Our cloud solutions include:
Cloud migration (on-prem to AWS, Azure, GCP)
Cloud-native app development
Microservices architecture
Containerization with Docker & Kubernetes
Serverless computing for cost efficiency
We also provide hybrid and multi-cloud strategies, so you never compromise on performance or control.
Case Studies: Business Transformation, Powered by EDSPL
1. Retail Automation Platform
A major retail brand approached EDSPL to digitize its supply chain. We built a custom logistics management platform integrated with IoT sensors and predictive analytics.
Results:
40% faster dispatch cycles
Real-time tracking
Inventory shrinkage reduced by 25%
2. Financial CRM for a Fintech Startup
For a growing fintech firm, we developed a scalable CRM with advanced analytics, API integrations, and two-factor authentication.
Results:
Lead conversion up by 3.2x
Secure client communication
Seamless third-party data sync
3. Hospital Management System
EDSPL built a full-stack HMS, including OPD, billing, diagnostics, and reporting for a multi-city hospital chain.
Results:
Paperless operations
99.9% uptime
Reduced admin overhead by 60%
These aren’t just projects. They’re partnerships that evolved into long-term digital transformations.
Our Secret Sauce: People + Process + Passion
People
Our team comprises senior software architects, cloud engineers, ethical hackers, DevOps experts, and UI/UX designers—each committed to innovation and client success.
Process
We follow agile + DevSecOps practices, with daily stand-ups, sprints, demos, and retrospectives to stay aligned and adaptable.
Passion
We love solving complex problems. Every challenge is an opportunity to innovate, disrupt, and deliver impact.
Beyond Development: Infrastructure Services That Accelerate You
EDSPL’s capabilities extend into digital infrastructure—from routing and switching to enterprise mobility management.
We ensure that what we build doesn’t just work—it works seamlessly in your environment, for your users, under your conditions.
Why Leading Brands Choose EDSPL
✅ End-to-end services from design to deployment
✅ Scalable architecture for growing businesses
✅ Bulletproof security for enterprise peace of mind
✅ Future-proof solutions that adapt to change
✅ Human-first design for better user adoption
✅ Round-the-clock support and transparent communication
Whether you’re a startup building your MVP or an enterprise undergoing digital transformation, EDSPL is your growth partner.
Conclusion: Ready to Code. Test. Evolve?
In an age where software defines success, you need more than a vendor—you need a visionary.
EDSPL’s full-spectrum software services are built to empower businesses at every turn, from ideation to innovation, development to deployment, and testing to transformation.
We don’t just code. We don’t just test. We help you evolve.
Let’s build the future together.
Talk to our experts today. Your business deserves better. Visit us at www.edspl.net to get started.
0 notes