#Laravel Security
Explore tagged Tumblr posts
Text
Answers To The Important Laravel Security Questions
Introduction

Laravel is a powerful PHP framework known for its elegant syntax and robust features, making it a popular choice for web developers. However, like any web development framework, security is a critical concern. Ensuring that your Laravel applications are secure is essential to protect sensitive data and maintain user trust. Security is the most common concern for many businesses. This is well justified because of the growing concern about an increase in cyberattacks. In this article, we address vital security questions related to Laravel. It provides insights and tips on Laravel security best practices to help safeguard the applications.
Significance of Application Security

Application security is a critical aspect of Laravel development (and any software development) that ensures the protection of data and systems. It protects users from various threats and vulnerabilities. Here are a few key reasons why application security needs to be a high priority:
Data Breaches: Securing applications helps prevent unauthorized access to sensitive data, such as personal information, financial details, and confidential business data.
Reputation Management: Users are more likely to trust and engage with applications that prioritize security. A single security breach can severely damage a company’s reputation and erode user trust.
Prevents Financial Loss: Data breaches can result in significant financial losses due to legal fees, fines, and remediation costs. Security incidents can lead to loss of business, decreased customer confidence, and long-term damage to brand equity.
Data Integrity: Application security helps ensure that data is not tampered with or altered by unauthorized entities.
Common Threats: Laravel security measures protect against various cyber threats, including SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and more.
Advanced Threats: Security practices also help defend against more sophisticated attacks, such as zero-day exploits and Advanced Persistent Threats (APTs).
Application security cannot be overstated. It is essential for protecting sensitive data and maintaining user trust. It also helps prevent financial losses, ensure application integrity, and mitigate cyber risks.
It plays a big role in enhancing development processes, supporting business continuity, and facilitating compliance with legal requirements. Prioritizing security is crucial for the success and longevity of any business operating in this digital age.
Here are a few relevant facts and statistics:
The application security market is expected to generate $6.97 Billion in 2024.
According to Statista's forecast, the size of the security market in 2028 will be $11.83 billion.
Application breaches account for 25% of all breaches.
Over 75% of applications will have at least one flaw.
As per a report by IBM, the costliest data breach was $4.25 Million.
An average ransomware attack costs $4.54 million.
Vital Laravel Security Questions

How Does Laravel Handle Authentication?
Laravel offers an out-of-the-box comprehensive authentication system that simplifies the implementation of user login and registration. The Auth facade provides an easy way to manage authentication, including features such as:
User registration and login
Password reset functionality
Authentication guards
User roles and permissions
Use Strong Password Policies
Two-factor authentication (2FA)
Secure Password Storage
How Can You Prevent SQL Injection in Laravel?
Laravel uses Eloquent ORM and the query builder, which automatically protects against SQL injection. By using parameter binding, Laravel ensures that user input is safely escaped before executing SQL queries.
Always prefer Eloquent ORM for database interactions, as it inherently protects against SQL injection. When using raw SQL queries, always use parameter binding to ensure inputs are correctly escaped.
How Does Laravel Protect Against Cross-Site Scripting (XSS)?
Laravel provides built-in protection against XSS by automatically escaping output. This means that any data retrieved from the database and displayed in views is escaped to prevent script injection. Always escape output using Laravel’s {{ }} syntax for variables.
How Can You Prevent Cross-Site Request Forgery (CSRF) in Laravel?
Laravel automatically generates a CSRF token for each active user session. This token is embedded in forms and must be included in any request that modifies data. Laravel then verifies the token to ensure the request is legitimate. Ensure all forms include the CSRF token.
How Can You Secure Laravel Routes and Controllers?
Laravel middleware provides a mechanism for filtering HTTP requests entering your application. Use authentication and authorization middleware to protect routes. Apply appropriate access controls to routes to ensure only authorized users can access certain parts of the application. Controllers handle the business logic of your application and should also be secured. Always validate user inputs in controllers to prevent invalid data from being processed. Laravel’s authorization policies provide a way to manage user permissions for accessing specific actions.
How Can You Secure Laravel’s File Uploads?
Ensure that only allowed file types and sizes are uploaded with the help of validation techniques. Store uploaded files outside the public directory to prevent direct access.
How Can You Implement a Secure Password Reset in Laravel?
Laravel provides a robust password reset feature out of the box, including generating secure tokens and sending password reset emails. It uses a secure token generation mechanism, ensuring that tokens are unique and hard to guess. Limiting the number of password reset requests from a single IP address prevents brute-force attacks.
How Can You Secure Laravel APIs?
Secure your APIs with tokens using Laravel Passport or Laravel Sanctum. Implement rate limiting on API endpoints to prevent abuse. Encrypt data in transit using HTTPS and ensure that sensitive data is never transmitted in plain text.
How Can You Keep Laravel Dependencies Secure?
Only use packages from trusted sources and review their security practices before including them in your project. Use tools like snyk or npm audit to scan your dependencies for known vulnerabilities.
How Can You Implement Logging and Monitoring in Laravel?
Logging and monitoring are essential for detecting and responding to security incidents. They provide insights into application activity and help identify potential security issues. Laravel provides a robust logging system based on Monolog. Configure logging to capture important events and errors. Review logs regularly for suspicious activity and respond promptly to any potential security threats.
Most common security threats faced by Laravel applications?
Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages viewed by other users.
SQL Injection: Malicious SQL statements are insert into an entry field for execution.
Cross-Site Request Forgery (CSRF): Unauthorized commands are transmit from a user that the web application trusts.
Unauthorized Access: Improper authentication and authorization checks can allow users to access restricted areas.
Data Leakage: Sensitive information is exposed due to improper handling of data.
What are some common misconfigurations that can lead to security vulnerabilities in Laravel applications?
Debug Mode: Never run your application in debug mode in a production environment. Debug mode can expose sensitive information about your application's configuration.
Environment Variables: Ensure that sensitive information in the .env file is not expose and is securely manage.
Server Configurations: Ensure the server is configure correctly to prevent directory listing and other exposures. Use .htaccess or server configurations to secure directories.
Some advanced security features provided by Laravel 11?
Argon2id Support: Enhanced password hashing with support for Argon2id, providing better resistance against side-channel attacks.
Native Two-Factor Authentication (2FA): Built-in support for adding a layer of security to user accounts.
Automatic HTTPS Enforcement: Easier enforcement of HTTPS across all routes, ensuring data encryption during transmission.
What role does Laravel Telescope play in application security?
Real-Time Monitoring: Telescope provides real-time monitoring and logging of security-related events such as failed login attempts, CSRF token mismatches, and more.
Alerting: Enhanced alerting and notification features to keep developers informed of potential security issues, allowing for swift action.
Secure Your Laravel Application
Securing a Laravel application involves a multifaceted approach that includes secure authentication and protection against common vulnerabilities. No one can help better with secure Laravel development, than an official Laravel partner.
Acquaint Softtech is one such software development outsourcing company in India. We have over 10 years of experience delivering cutting-edge solutions.
Security requires ongoing attention and diligence. Always stay informed about Laravel's security features and adhere to best practices. Make the most of the available resources to reduce the risk. Hire remote developers from Acquaint Softtech and gain an upper edge.
A secure application protects your users. At the same time, it enhances the credibility and reliability of your work as a developer. Make a smart business decision to choose between outsourcing and **IT staff augmentation.**
FAQ
What are the most common security threats to Laravel applications?
Cross-Site Scripting (XSS), SQL Injection, Cross-Site Request Forgery (CSRF), unauthorized access, and data leakage.
How does Laravel prevent Cross-Site Scripting (XSS) attacks?
Laravel's Blade templating engine automatically escapes output to prevent malicious scripts from being execute.
How does Laravel mitigate SQL Injection?
Mitigating SQL Injection: Eloquent ORM and Query Builder use PDO parameter binding to safely handle user inputs, preventing direct insertion into SQL queries.
What measures does Laravel take to prevent Cross-Site Request Forgery (CSRF)?
Laravel generates a CSRF token for each user session, which is verified by middleware for all state-changing requests to ensure they are legitimate.
What are the best practices for authentication and authorization in Laravel?
Use Laravel’s built-in authentication system and implement policies and gates to effectively manage user permissions.
0 notes
Text
Securing Your Laravel App: Latest Best Practices and Threat Protection
In the ever-evolving world of web development, Laravel has emerged as one of the most popular PHP frameworks. Its elegant syntax, robust features, and vibrant community make it a top choice for many developers. However, as with any technology, ensuring the security of your Laravel application is paramount. In this blog post, we will delve into the latest best practices for securing your Laravel app and protecting it against threats.

Why Security Matters in Laravel Development
Before we dive into the specifics, let’s take a moment to understand why security is so crucial in Laravel development. As the digital landscape expands, so does the potential for security breaches. These breaches can lead to data loss, unauthorized access, and even severe financial implications. Therefore, whether you’re a seasoned Laravel developer or a business looking to hire a Laravel developer, understanding and implementing security best practices is non-negotiable.
Laravel Security Best Practices
1. Keep Your Laravel Version Updated
One of the simplest yet most effective ways to secure your Laravel app is by keeping your Laravel version updated. Each new version of Laravel comes with security patches and updates that fix known vulnerabilities.
2. Use HTTPS
Using HTTPS instead of HTTP ensures that all communication between your server and your users is encrypted. This encryption makes it much harder for attackers to access sensitive information.
3. Validate and Sanitize Data
Always validate and sanitize data coming from users or third-party sources. Laravel provides several ways to validate data, including form request validation, manual validation, and even validation rules.
4. Use Laravel’s Built-In Authentication
Laravel comes with built-in authentication scaffolding, which provides a secure way to handle user authentication. Using this feature can save you from the potential security risks of building your own authentication system.
5. Limit and Monitor Access
Implement role-based access control (RBAC) to limit who can access what resources in your application. Also, monitor your application for any unusual activity.
Threat Protection in Laravel
Protecting your Laravel app from threats involves being aware of the common types of attacks and knowing how to prevent them. Here are a few threats you should be aware of:
1. SQL Injection
SQL injection involves an attacker manipulating your SQL queries to gain unauthorized access or make unauthorized changes to your database. Laravel’s Eloquent ORM uses PDO parameter binding, which protects your application from SQL injection.
2. Cross-Site Scripting (XSS)
XSS attacks involve an attacker injecting malicious scripts into your web pages, which are then run by your users’ browsers. Laravel’s Blade templating engine automatically escapes output, protecting your application from XSS attacks.
3. Cross-Site Request Forgery (CSRF)
CSRF attacks trick your users into performing actions without their knowledge or consent. Laravel includes built-in protection against CSRF attacks.
Conclusion
Securing your Laravel application involves a combination of staying updated with the latest Laravel version, using built-in Laravel features, and being aware of common threats. Whether you’re a Laravel developer or a Laravel development company, following these best practices will go a long way in ensuring the security of your Laravel application.
Remember, security is not a one-time task but an ongoing process. Stay vigilant, stay updated, and most importantly, stay secure.
FAQs on Securing Your Laravel App: Latest Best Practices and Threat Protection**
Q: Why is securing my Laravel app important?
- A: Securing your Laravel app is crucial to protect sensitive data, prevent unauthorized access, and safeguard against potential cyber threats. It ensures the integrity and reliability of your application.
Q: What are the latest best practices for securing a Laravel app?
- A: Some best practices include keeping Laravel and its dependencies up-to-date, implementing strong authentication mechanisms, securing sensitive routes, using HTTPS, and regularly auditing and monitoring your application for potential vulnerabilities.
Q: How can I keep my Laravel framework and dependencies updated?
- A: Use Composer to manage your project dependencies and regularly update Laravel by running `composer update`. Stay informed about security releases and apply them promptly.
Q: What authentication mechanisms should I use to secure my Laravel app?
- A: Laravel provides built-in authentication features. Implement multi-factor authentication (MFA), use strong password policies, and consider OAuth or social media logins for additional security layers.
Q: How do I secure sensitive data in my Laravel app?
- A: Employ encryption for sensitive data using Laravel's encryption features. Avoid storing sensitive information in plain text and utilize secure methods like Laravel's Eloquent ORM for database operations.
Q: Is HTTPS necessary for my Laravel app?
- A: Yes, using HTTPS is crucial. It encrypts data in transit, preventing eavesdropping and man-in-the-middle attacks. Obtain an SSL certificate and configure your Laravel app to use HTTPS.
Q: How can I protect against common web application security threats?
- A: Implement input validation, use Laravel's built-in protection against Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF), and sanitize user inputs to prevent SQL injection.
Q: Should I use Laravel's built-in security features or implement additional security packages?
- A: Laravel offers robust security features, but depending on your specific requirements, you may consider additional security packages like Laravel Security Package or Laravel Fortify for enhanced protection.
Q: How can I monitor my Laravel app for security vulnerabilities?
- A: Regularly conduct security audits, use security scanning tools, and implement logging and monitoring solutions to detect and respond to any suspicious activities or potential threats.
Q: What steps can I take to recover my Laravel app in case of a security breach?
- A: Have a well-defined incident response plan, regularly back up your data, and ensure you can quickly restore your application to a secure state. Additionally, notify users of any security incidents and prompt them to update passwords if necessary.
0 notes
Text
#laravel security#laravel security features#laravel development company#build laravel applications#laravel app development
0 notes
Text
Prevent HTTP Parameter Pollution in Laravel with Secure Coding
Understanding HTTP Parameter Pollution in Laravel
HTTP Parameter Pollution (HPP) is a web security vulnerability that occurs when an attacker manipulates multiple HTTP parameters with the same name to bypass security controls, exploit application logic, or perform malicious actions. Laravel, like many PHP frameworks, processes input parameters in a way that can be exploited if not handled correctly.

In this blog, we’ll explore how HPP works, how it affects Laravel applications, and how to secure your web application with practical examples.
How HTTP Parameter Pollution Works
HPP occurs when an application receives multiple parameters with the same name in an HTTP request. Depending on how the backend processes them, unexpected behavior can occur.
Example of HTTP Request with HPP:
GET /search?category=electronics&category=books HTTP/1.1 Host: example.com
Different frameworks handle duplicate parameters differently:
PHP (Laravel): Takes the last occurrence (category=books) unless explicitly handled as an array.
Express.js (Node.js): Stores multiple values as an array.
ASP.NET: Might take the first occurrence (category=electronics).
If the application isn’t designed to handle duplicate parameters, attackers can manipulate input data, bypass security checks, or exploit business logic flaws.
Impact of HTTP Parameter Pollution on Laravel Apps
HPP vulnerabilities can lead to:
✅ Security Bypasses: Attackers can override security parameters, such as authentication tokens or access controls. ✅ Business Logic Manipulation: Altering shopping cart data, search filters, or API inputs. ✅ WAF Evasion: Some Web Application Firewalls (WAFs) may fail to detect malicious input when parameters are duplicated.
How Laravel Handles HTTP Parameters
Laravel processes query string parameters using the request() helper or Input facade. Consider this example:
use Illuminate\Http\Request; Route::get('/search', function (Request $request) { return $request->input('category'); });
If accessed via:
GET /search?category=electronics&category=books
Laravel would return only the last parameter, category=books, unless explicitly handled as an array.
Exploiting HPP in Laravel (Vulnerable Example)
Imagine a Laravel-based authentication system that verifies user roles via query parameters:
Route::get('/dashboard', function (Request $request) { if ($request->input('role') === 'admin') { return "Welcome, Admin!"; } else { return "Access Denied!"; } });
An attacker could manipulate the request like this:
GET /dashboard?role=user&role=admin
If Laravel processes only the last parameter, the attacker gains admin access.
Mitigating HTTP Parameter Pollution in Laravel
1. Validate Incoming Requests Properly
Laravel provides request validation that can enforce strict input handling:
use Illuminate\Http\Request; use Illuminate\Support\Facades\Validator; Route::get('/dashboard', function (Request $request) { $validator = Validator::make($request->all(), [ 'role' => 'required|string|in:user,admin' ]); if ($validator->fails()) { return "Invalid Role!"; } return $request->input('role') === 'admin' ? "Welcome, Admin!" : "Access Denied!"; });
2. Use Laravel’s Input Array Handling
Explicitly retrieve parameters as an array using:
$categories = request()->input('category', []);
Then process them safely:
Route::get('/search', function (Request $request) { $categories = $request->input('category', []); if (is_array($categories)) { return "Selected categories: " . implode(', ', $categories); } return "Invalid input!"; });
3. Encode Query Parameters Properly
Use Laravel’s built-in security functions such as:
e($request->input('category'));
or
htmlspecialchars($request->input('category'), ENT_QUOTES, 'UTF-8');
4. Use Middleware to Filter Requests
Create middleware to sanitize HTTP parameters:
namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class SanitizeInputMiddleware { public function handle(Request $request, Closure $next) { $input = $request->all(); foreach ($input as $key => $value) { if (is_array($value)) { $input[$key] = array_unique($value); } } $request->replace($input); return $next($request); } }
Then, register it in Kernel.php:
protected $middleware = [ \App\Http\Middleware\SanitizeInputMiddleware::class, ];
Testing Your Laravel Application for HPP Vulnerabilities
To ensure your Laravel app is protected, scan your website using our free Website Security Scanner.

Screenshot of the free tools webpage where you can access security assessment tools.
You can also check the website vulnerability assessment report generated by our tool to check Website Vulnerability:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
HTTP Parameter Pollution can be a critical vulnerability if left unchecked in Laravel applications. By implementing proper validation, input handling, middleware sanitation, and secure encoding, you can safeguard your web applications from potential exploits.
🔍 Protect your website now! Use our free tool for a quick website security test and ensure your site is safe from security threats.
For more cybersecurity updates, stay tuned to Pentest Testing Corp. Blog! 🚀
3 notes
·
View notes
Text

Building Secure Video Streaming with Signed URLs
𝗤𝘂𝗶𝗰𝗸 𝗰𝗵𝗲𝗰𝗸: 𝗜𝘀 𝘆𝗼𝘂𝗿 𝘃𝗶𝗱𝗲𝗼 𝗰𝗼𝗻𝘁𝗲𝗻𝘁 𝗿𝗲𝗮𝗹𝗹𝘆 𝘀𝗲𝗰𝘂𝗿𝗲, 𝗼𝗿 𝗷𝘂𝘀𝘁 𝗼𝗻𝗲 𝗹𝗶𝗻𝗸 𝗮𝘄𝗮𝘆 𝗳𝗿𝗼𝗺 𝗯𝗲𝗶𝗻𝗴 𝘀𝗵𝗮𝗿𝗲𝗱 𝗲𝘃𝗲𝗿𝘆𝘄𝗵𝗲𝗿𝗲?
If you're building an OTT platform, an edtech portal, or even a private training hub, controlling access to your videos is a must, not a maybe.
At Brainstream, we recently implemented Signed URLs to help one of our clients lock down their video content ��. It’s like giving users a one-time key that works only under the right conditions and nowhere else.
We’ve written a short blog to break down:
What signed URLs actually are
When you should use them
How they can keep your content secure without breaking the user experience
Check it out here 👉 https://brainstreamtechnolabs.com/building-secure-video-streaming-with-signed-urls/
If you're building something video-driven, this might be worth a read. Curious to hear how others are approaching video security.
1 note
·
View note
Text
Authentication is a fundamental part of any web application, ensuring that users can securely log in and access protected content. While Laravel provides built-in authentication scaffolding, sometimes developers prefer manual authentication for better control and customization.
#Laravel12#ManualAuthentication#Laravel#Authentication#UserLogin#LaravelSecurity#PHP#LaravelApp#LaravelDevelopment#WebDevelopment#LaravelTutorial#UserAuthentication#LaravelAuth#PHPFramework#CustomAuthentication#LaravelProjects#WebAppSecurity#LaravelBestPractices#LaravelLogin#BackendDevelopment#Security#LaravelUserAuthentication#LaravelGuide#CustomAuth#LoginSystem#LaravelAppDevelopment
0 notes
Text
Laravel Security: Top 7 Mistakes Developers Make
I often see the question: “Is Laravel secure?”, and in this video, let’s take a look at what the framework offers, and how developers … source
0 notes
Text
Answers To The Important Laravel Security Questions
Introduction Laravel is a powerful PHP framework known for its elegant syntax and robust features, making it a popular choice for web developers. However, like any web development framework, security is a critical concern. Ensuring that your Laravel applications are secure is essential to protect sensitive data and maintain user trust. Security is the most common concern for many businesses.…
0 notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text

Learn about latest Laravel threats in 2024 how to protect your apps with best practices Keep your applications safe and stay ahead with expert tips techniques
0 notes
Text
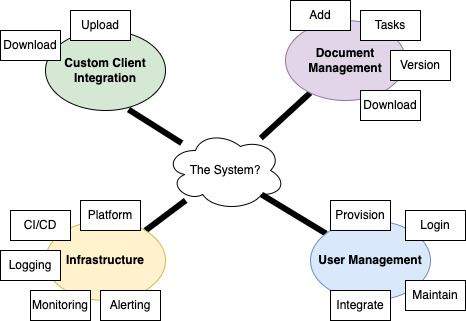
In interviewing for higher level architecture positions, you will be sometimes be asked to do design a new system to demonstrate your capabilities. The following is from such an interview around PHP, Laravel, Nuxt, MySQL, Redis, AWS, and K8s.
0 notes
Text
In any modern web application, user authentication is essential, and email verification and password reset are common features. Laravel 12 provides out-of-the-box solutions to handle both of these functionalities.
Email Verification allows you to ensure that the email provided by a user is valid and accessible. This improves the security of your application.
Password Reset allows users who have forgotten their password to reset it easily, maintaining the usability and security of your application.
In this tutorial, we will go over the steps to implement email verification and password reset in Laravel 12.
#Laravel12#EmailVerification#PasswordReset#Laravel#WebDevelopment#LaravelSecurity#Authentication#PHP#LaravelApp#PasswordRecovery#LaravelFeatures#UserAuthentication#LaravelDevelopment#LaravelTutorial#LaravelAuth#Security#LaravelProjects#UserVerification#ResetPassword#WebAppSecurity#BackendDevelopment#LaravelBestPractices#PHPFramework#LaravelAPI#LaravelLogin#AccountSecurity
0 notes
Text
RE: Password Security on Santae
We want to directly address a false and misleading claim circulating online.
No one on the Santae team — including administrators or management — can see your password. Passwords are never stored in plaintext. Like any secure platform, we use one-way encryption to protect your login credentials. We use Laravel’s built-in authentication system, which hashes (and salts) every password before it’s ever saved. This means your actual password is not visible or accessible to anyone, including Myself(CJ), Developers, Management or Administrators.
We can assist with password resets only in cases where the “Forgot Password” function fails. This is a standard fail-safe, allowing us to manually set a new password upon your request. However, we do not have access to your current or previous passwords, nor can we view any password you’ve set.
We always encourage you to use a unique password for Santae and for every other service you use.
Spreading misinformation like this causes unnecessary panic and undermines trust in the safety protocols we’ve put in place. We take your account security very seriously, and our systems are designed to uphold modern standards of user privacy and data protection.
If you have any concerns, please contact support through our support ticket system on-site or email [email protected]. Thank you for helping keep our community safe, informed, and respectful.
CJ
~ The Santae Team
25 notes
·
View notes
Text
🎬 Entertainment App Development Services: Build the Future of Digital Entertainment
In a digital-first world where users stream, binge, listen, and share content 24/7, the demand for entertainment app development services is skyrocketing. Whether you're launching the next Netflix, Spotify, or a regional OTT platform, a powerful entertainment app can place your content at the fingertips of millions.
This blog explores everything you need to know about building a successful entertainment mobile app—features, tech stack, monetization models, and how the right development partner can turn your vision into a captivating, scalable reality.

📱 Why You Need an Entertainment App in 2025
The entertainment industry is undergoing a massive digital shift. With over 6.5 billion smartphone users globally, streaming content—whether video, music, or live performances—has become the new normal. Audiences demand convenience, personalization, and immersive experiences, all of which can be delivered through a well-developed mobile application.
From OTT platform development to podcast and music streaming apps, custom solutions are now essential for media brands, production houses, indie artists, and entertainment startups.
📈 Market Stats Worth Noting:
The global video streaming market is expected to surpass $920 billion by 2030.
Time spent on entertainment and media apps increased by 40% post-pandemic.
Subscription-based platforms like Netflix, Hotstar, and Gaana have seen record-breaking growth.
If you're in the business of content creation or distribution, now is the time to invest in expert entertainment app development services.
🛠️ Core Features of a Winning Entertainment App
To compete with giants like Netflix, Spotify, or Amazon Prime, your app must go beyond basic functionality. Here's what users expect from a top-tier entertainment mobile app:
1. Content Streaming (Video/Audio)
High-quality streaming with adaptive bitrate, low buffering, and seamless playback across devices.
2. User Profiles & Personalization
Smart algorithms that recommend content based on watch history, preferences, or listening habits.
3. Subscription & Monetization Models
Support for freemium access, in-app purchases, advertisements, and recurring subscriptions.
4. Search & Filter
Powerful content discovery with keyword search, genres, languages, trending content, and more.
5. Multi-Platform Access
Cross-platform compatibility (Android, iOS, smart TVs, tablets, etc.) with a unified user experience.
6. Offline Downloads
Let users enjoy content without internet access by enabling secure offline downloads.
7. Live Streaming
Incorporate live shows, concerts, or podcasts with real-time chat and engagement.
8. Push Notifications
Keep users engaged by notifying them about new releases, trending content, and personalized suggestions.
9. Social Sharing & Integration
Let users share what they watch or listen to on social media, enhancing app visibility and virality.
🧠 Choosing the Right Technology Stack
Behind every great entertainment app is a powerful and scalable tech architecture. Here's what a reliable entertainment app development company should offer:
➤ Frontend (Mobile App Development)
React Native / Flutter for cross-platform development
Swift (iOS) and Kotlin (Android) for native apps
Custom UI/UX based on Figma, XD, or Sketch
➤ Backend
Node.js, Laravel, or Django for scalable API architecture
MongoDB or PostgreSQL for content and user data
Real-time databases like Firebase for chat, notifications, and analytics
➤ Streaming & CDN
Integration with AWS CloudFront, Vimeo OTT, or Wowza
DRM support to prevent piracy
Adaptive Bitrate Streaming (HLS, MPEG-DASH)
➤ Analytics & Recommendation Engine
Firebase, Mixpanel, or Google Analytics for user behavior
AI-powered recommendation engine to boost engagement and retention
💰 Monetization Strategies for Entertainment Apps
Monetization is crucial. Your entertainment app can generate recurring revenue through several models:
🔒 Subscription (SVOD)
Offer access to premium content on a weekly, monthly, or annual basis.
🎯 Advertisement (AVOD)
Free content monetized through banner ads, interstitials, or video ads using Google AdMob or Facebook Audience Network.
📥 Pay-per-view
Ideal for exclusive concerts, movie releases, or premium shows.
💼 Freemium
Provide basic content for free while charging for access to premium features or shows.
🤝 Why Hire Expert Entertainment App Developers?
Entertainment apps are high-stakes projects. Performance issues, bugs, or poor user experience can lead to instant churn. Here’s why hiring a team with domain expertise in entertainment mobile app development is critical:
They understand media licensing, content management, and user behavior.
They can optimize infrastructure for millions of concurrent users.
They’re familiar with UI/UX best practices that align with binge-watching or continuous listening behaviors.
They offer post-launch support for updates, bug fixes, and user feedback handling.
A team like Kickass Developers, with expertise in custom mobile app development, OTT app development, and audio/video streaming, ensures your idea is executed with precision and long-term scalability.
🚀 Final Thoughts: Your Entertainment App Is the Future of Engagement
Whether you’re building a regional OTT app, a music discovery platform, or a niche video streaming service, your success hinges on the right blend of technology, UX, scalability, and speed to market.
Investing in experienced entertainment app development services is your first step toward captivating your audience, building loyalty, and driving recurring revenue.
📞 Ready to Build Your Entertainment App?
Looking for a team that understands the entertainment industry inside and out?
Kickass Developers specializes in designing custom, high-performance entertainment applications tailored to your audience, brand, and growth goals.
📧 Contact us today at [email protected] 🌐 Or visit us at kickassdevelopers.com
#Entertainment App Developers#OTT App Development#Video Streaming App Services#Music App Development#Android Entertainment App#iOS Video App#Podcast App Developers#Live Streaming App Development#Subscription App Development
3 notes
·
View notes
Text
A Behind-the-Scenes Look at a Laravel Security Audit
Introduction Laravel is one of the most popular PHP frameworks, and it is likely to continue to be that way for some time to come. There are many reasons why this is so, like its syntax, robust features, scalability, and, most of all, its high level of security. Security remains a paramount concern for developers and businesses alike, irrespective of the selection of technology. Laravel, like…
0 notes
Text
What is an open source platform used for?
Open Source Development
An open source platform is a type of software whose source code or the base code is freely available to the public and open in segments. This means anyone can view, use, modify, and share the code. Open source platforms are widely used across industries because they offer flexibility, cost savings, and community-driven innovation. Open source development has become an initial go-to approach and one of the ideal options for building scalable and secure digital solutions.
Common Uses of Open Source Platforms -
1. Web and App Development
Open source platforms like WordPress, Drupal, and Joomla are widely used for building websites. The coders working in open source development department can customize and personalize these platforms to meet specific and unique business needs. Similarly, common frameworks such as React, Angular, and Laravel facilitate the development of dynamic and feature-rich web applications with their implementation and usage.
2. Operating Systems and Servers
Linux is one of the most well-known open-source operating systems. Many companies use Linux-based servers for hosting websites and applications because they are secure, fast, and cost-effective. These platforms are maintained by communities that constantly improve performance and patch vulnerabilities.
3. Cloud Computing
While the additional tools like OpenStack and Kubernetes are open source platforms and mediums that support the cloud infrastructure. They help businesses to manage their storage, networking, and computing resources efficiently while keeping operating costs low through open-source development.
4. Software Testing and DevOps
Open source tool and the common resources such as Selenium (for test automation) and Jenkins (for continuous integration) are essential and most considered in DevOps environments and stiff settings. These tools support the automated testing process, faster deployments, and seamless collaboration.
5. Data Management and Analytics
Platforms like Hadoop, Apache Spark, and PostgreSQL facilitate the processing and management of large datasets. These open-source solutions are widely used and leveraged in industrial sectors such as healthcare, finance with e-commerce for better understanding.
Why Do Businesses Prefer Open Source?
Open source platforms are cost-effective, highly customizable, and backed by active communities. They reduce and lower down the dependency on single vendors and parties and offer a general transparency in security and performance with its adaptation into the system or the infrastructure. Trusted providers and professional experts like Suma Soft, IBM, and Cyntexa specialize in delivering tailored and custom solutions through open source development, helping businesses to stay flexible, secure, and future-ready in this digital age and competitive market.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
2 notes
·
View notes