#Network security service
Explore tagged Tumblr posts
Text
Ha már ISMS auditor lennék
Az ember eljön egy viszonylag méretes szállodaláncba és naívan rákérdez, hogy mi is a Wifi? Flegma recepciós odavágja, hogy csak a közös területen van Wifi. Ha a szobába is akarok a akkor, leszek szíves 7 fontot leszúrni a kasszánál és 24 órára kapok valamit.
Aha, hát kösz nem. Nézzük a Wifi-t a biztonságos gépről, amin nincs olyan adat amiben kárt tenne valami fosadék net. Már ott elbukik, hogy a security rendszer óbégat, hogy nem biztonságos, nyilván wiresharkkal látnám az összes forgalmat. Mutatom bárisnyának a recepciónál, hogy látod nyuszika, itt óbégat a riasztás, hogy fosadék a hálózatotok. Erre ő, hogy meg kall adni az email címet, majd akkor kapcsolódhatók rendesen. Kapott eldobható email címet szórakozzanak azzal. Kapcsolódtam, de továbbra sem biztonságos a net. Mucikának mondom, hogy így sem jó, egy kalap fos a hálózatotok, erre ő, hogy lehet netezni nem? Különben sem kötelező használni.
Na itt triggerelt be. Most gyűjtöm ki az összes evidenciát, hogy milyen minősítésük van, milyen policyket adtak ki, milyen certificate-jeik vannak és minek nem felel meg a kurva hálózatuk. Kapnak olyan review-t, hogy a fal adja a másikat. Szarjanak aprószöget és beizzítom a hordozható hálózatot majd használom azon keresztül.
Ha tehetném befizetnék ide @muszeresz részére egy pár napos tanulmányutat, szerintem lubickolna.
20 notes
·
View notes
Text
IMPORTANT QUESTIONS OF ELECTRONICS FOR COMPETITIVE TEST PREP. ❤️
Impact of Semiconductor Technology on Everyday Life Discuss the influence of semiconductors on modern communication and connectivity. Explain how they power artificial intelligence and machine learning. Highlight the role of semiconductors in the development of advanced medical technologies. The primary knoledge you nee to know about curcuits , diode , register and transister , also know about , how does it works?

LEARN ABOUT NETWORKING WITH SEMI-CONDUCTOR 👈
The most used semiconductor material is silicon, which is widely used in producing integrated circuits (ICs), also known as microchips. These chips contain multiple transistors, which act as switches that allow the flow of electricity to be controlled, enabling complex electronic functions.
Current in a Parallel Circuit
Problem:vA 24V battery is connected to three resistors in parallel: R₁ = 4Ω, R₂ = 6Ω, and R₃ = 12Ω. Find the current through R₂.
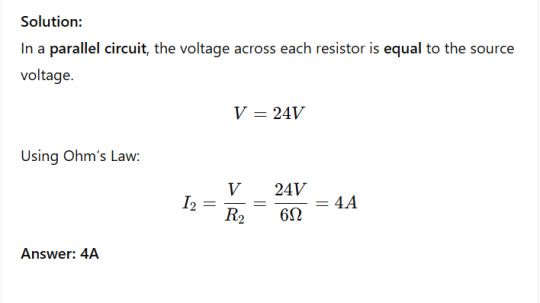
JOIN US WITH US FOR FREE VIDEO TUTORIAL 👈
#electronics components#electronics store#electronics manufacturing#electronics industry#appliances#surfaces#semiconductor#technologie#electricalsafety#network marketing#network security#services#online tutoring#online education#online courses#digital learning
3 notes
·
View notes
Text
Top Cybersecurity Solutions Providers in Delhi-NCR: Wish Geeks Techserve
Cybersecurity services in India have become an essential investment for businesses looking to safeguard their digital infrastructure from rising cyber threats. With an increasing number of data breaches, phishing attacks, and malware infiltrations, organizations cannot afford to overlook the importance of strong IT security frameworks. Companies in Delhi-NCR, in particular, need to prioritize security due to the region's rapid technological growth and evolving cyber risk landscape.
Finding the top cybersecurity solutions provider in India is crucial for ensuring business continuity, regulatory compliance, and data integrity. Among the top contenders offering robust security solutions is Wish Geeks Techserve, a trusted IT security services India provider known for its innovative and customized cybersecurity strategies.
The Growing Cybersecurity Challenges in India
As the digital economy expands, businesses face a multitude of security threats ranging from ransomware attacks to sophisticated hacking attempts. The emergence of remote working models and cloud computing has further increased the vulnerability of organizations, making network security services in India a necessity rather than an option. The cyber threat landscape includes:
Phishing and Social Engineering Attacks: Cybercriminals exploit human vulnerabilities through fraudulent emails and deceptive practices to gain unauthorized access to sensitive information.
Malware and Ransomware Infections: Malicious software infiltrates systems, encrypting or corrupting critical business data, often leading to significant financial losses.
Insider Threats and Human Errors: Employees, either maliciously or unintentionally, can cause security breaches through weak passwords, mishandling of data, or lack of security awareness.
DDoS (Distributed Denial-of-Service) Attacks: Hackers overwhelm business networks with excessive traffic, leading to downtime and operational disruptions.
Cloud Security Risks: With increasing cloud adoption, businesses must ensure secure cloud storage, access management and data encryption practices to prevent unauthorized intrusions.
Why Choose Wish Geeks Techserve as the Best Cybersecurity Company in India?
Wish Geeks Techserve stands out among cybersecurity solutions providers in India, offering state-of-the-art security services tailored to businesses of all sizes. Their comprehensive approach ensures complete protection from internal and external threats. Here’s what makes them the ideal IT security services India provider:
1. Advanced Cybersecurity Solutions for End-to-End Protection
Wish Geeks Techserve provides holistic security solutions that cover all aspects of IT security. Their expertise spans across:
Threat Intelligence & Risk Assessment: Proactively identify vulnerabilities and strengthen weak points before attacks occur.
Endpoint Protection & Malware Defense: Implementing security measures that shield endpoints like computers, mobile devices and IoT systems from cyber threats.
Firewall & Intrusion Prevention Systems (IPS): Ensuring that network boundaries remain impervious to unauthorized access attempts.
Incident Response & Forensics: Swift action in the event of a cyberattack, minimizing damage and preventing future breaches.
2. Comprehensive Network Security Services in India
As a leading cybersecurity solutions provider in India, Wish Geeks Techserve specializes in network security services in India, ensuring robust defense mechanisms against cyber threats. Their network security offerings include:
Secure VPN Implementations: Allowing safe and encrypted remote access for employees working from different locations.
DDoS Protection & Mitigation: Preventing large-scale cyberattacks that aim to disrupt operations.
Zero Trust Security Frameworks: Adopting a ‘never trust, always verify’ approach to user authentication and access control.
3. 24/7 Cybersecurity Monitoring & Incident Response
Cyber threats do not operate within business hours, which is why Wish Geeks Techserve provides round-the-clock monitoring and support. Their dedicated Security Operations Center (SOC) continuously tracks anomalies, preventing attacks before they escalate.
4. Regulatory Compliance & Data Privacy Solutions
With stringent data protection regulations like GDPR and India’s upcoming Personal Data Protection Bill, businesses must comply with legal security mandates. Wish Geeks Techserve helps companies meet these requirements by implementing industry-leading compliance strategies and ensuring secure handling of customer and business data.
5. Customized Cybersecurity Strategies for Businesses
Recognizing that no two businesses have the same security needs, Wish Geeks Techserve delivers customized cybersecurity services in India based on industry-specific challenges. Whether it's securing financial transactions, protecting healthcare records, or preventing e-commerce fraud, their team crafts personalized solutions to fit organizational requirements.
How Businesses Can Benefit from Strong Cybersecurity Measures
Adopting best-in-class IT security services India offers multiple benefits beyond just data protection. Businesses that invest in top-tier security measures experience:
Improved Customer Trust: Demonstrating commitment to data privacy enhances brand credibility.
Reduced Financial Losses: Preventing cyberattacks reduces the risk of hefty ransom payments, fines and revenue losses due to downtime.
Operational Efficiency: Secure IT environments enable seamless business operations without disruptions from malware or unauthorized access.
Competitive Advantage: Businesses that prioritize cybersecurity gain an edge over competitors who fail to implement robust security strategies.
Conclusion
Cybersecurity is no longer a choice but a necessity for businesses in Delhi-NCR and across India. Choosing the right cybersecurity solutions provider in India can make all the difference in ensuring business continuity and protection against cyber threats. Wish Geeks Techserve emerges as one of the best cybersecurity companies in India, offering cutting-edge IT security services in India that cater to businesses of all sizes. Their expertise in network security services in India ensures that organizations remain resilient against evolving cyber risks.
If you’re looking for a trusted partner to fortify your cybersecurity infrastructure, Wish Geeks Techserve is the go-to provider, ensuring that your business stays secure in the ever-changing digital landscape. Invest in strong security measures today and safeguard your business’s future!
#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Network Security Services in India
4 notes
·
View notes
Text
The Evolving Threat of AI in the Public Housing Sector

The Evolving Threat of AI in the Public Housing Sector: How to Protect Your Organization
Read Blog:https://centurygroup.net/the-evolving-threat-of-ai-in-the-public-housing-sector-how-to-protect-your-organization/
#artificialintelligence #ai #machinelearning #technology #cyberthreats #cybersecurity #cyberattack #cybercrime #ransomware #networksecurity #technology #dataprivacy #hackers #cybersecurityexpert #itsecurity #threatintelligence #cybersecuritytraining #hacked
#artificial intelligence#ai generated#Machinelearning#Cyberthreats#Cyberattack#managed it services#ransomware#network security#dataprotection
2 notes
·
View notes
Text
Always On VPN Security Updates October 2024
Microsoft has released the October 2024 security updates, and numerous issues may impact Always On VPN administrators. Although many CVEs affect Always On VPN-related services that are Remote Code Execution (RCE) vulnerabilities, none are critical this cycle. RRAS Updates This month, Microsoft has provided 12 updates for the Windows Server Routing and Remote Access Service (RRAS), commonly…
#Always On VPN#AOVPN#CVE#enterprise mobility#hotfix#Microsoft#Mobility#NDES#Network Device Enrollment Service#Patch Tuesday#RAS#Remote Access#Routing and Remote Access#routing and remote access service#RRAS#SCEP#security#Simple Certificate Enrollment Protocol#update#VPN#Windows#Windows Server
1 note
·
View note
Text

Smart Home Solutions at Palm Beach Audio Visions
At Palm Beach Audio Visions (PBAV), we are passionate about delivering exceptional audio visual, home automation, lighting, and technology integration solutions for residential and commercial projects. From the initial concept to the final system deployment, we are dedicated to ensuring that projects are completed on time and within budget while exceeding industry standards for quality. Our team of experienced professionals brings a wealth of expertise in the high-end market and a strong focus on building lasting relationships with our clients. Feel free to visit us!
#Lutron Homeworks Dealer Whole House Smart Lighting Consultant#Design#Installation#Manager Solutions#Smart Home Network Setup Wifi Installation#Smart Home Security Camera Installation#Lutron Smart Window Electric Shades#Outdoor Entertainment System Design Installation Solution with Pool Patio Surround Sound Speakers#Outdoor Patio TV speaker Solution with Surround Sound#Universal Remote Control Smart Touch Screen Solution Programming Installation in Frenchman's Creek Palm Beach Gardens#Samsung QLED#Sony OLED#LG OLED Smart TV Dealer Installation Service#Home Theater System Consultant#Design and Installation Services#Sonos Dealer and Speaker Installation#Surround Sound Setup with In-ceiling Invisible Speakers#Whole House Multi Room Home Audio Installation Services#Smart Home Technology Consultant#Whole Home Automation Expert Installation Company#Control4 Smart Home Dealer - Installer
3 notes
·
View notes
Text

Best Cyber Security Services- NewGig Secure Solutions
#firewall#security#network security services#network security solutions#network security market#antivirus
2 notes
·
View notes
Text
Navigating Tech Success: A Comprehensive Guide to Managed IT Services in Dallas
As we look into Managed IT Services, don't forget to look beyond Dallas. Managed IT Services Dallas provides a tight-knit group of solutions, meeting the tech needs of businesses in this lively Texan city.
Let's jump into our guide to see how Managed IT Services Dallas isn't just a support system; it helps businesses grow in the heart of Texas. Let's make the complicated world of IT simpler, making sure your business does well in the digital age.
Understanding Managed IT Services Dallas
Managed IT Services Dallas is similar to having a helpful friend for your business technology needs. They guide you through the tech challenges, ensuring everything runs smoothly while you focus on your business.
Tailored Tech Solutions
Imagine Managed IT Services Dallas as your tech expert. It doesn't just fix problems; but it also makes special solutions that fit your business perfectly. No more one-size-fits-all, just personalized tech support.
Local Touch: IT Solutions Dallas
Navigate the tech landscape with IT Solutions Dallas. However, discover how local businesses in Dallas fine-tune their tech game, moreover, find a solution that align perfectly with their unique needs and most importantly with their goals.
Guarding Your Digital Realm: Network Security Dallas
In the digital age, protecting your business is a top priority. Because Network Security Dallas acts as your digital bodyguard, ensuring your data stays safe and most importantly, more secure in the hustle of Dallas business life.
Strategic Outsourcing for Growth
Outsourcing IT services in Dallas isn’t just a cost-cutting move; it’s also a strategic play. So, let's explore how businesses leverage Managed IT Services Dallas to align with their growth and plans seamlessly.
Key Features of Managed IT Services
Managed IT Services Dallas isn't just tech support; it's also a game-changer for businesses. So, let's explore the key features that make it essential for your Dallas-based venture.
1. Proactive Issue Prevention
First, say goodbye to constant tech troubles. Managed IT Services Dallas takes a proactive approach, preventing more issues before they disrupt your operations.
2. Tailored Tech Solutions
Second, your business is unique, and so are its tech needs. Moreover, Managed IT Services Dallas crafts personalized solutions that align with your specific goals and challenges.
3. 24/7 Tech Support
Third, Managed IT Services Dallas ensures round-the-clock support, providing peace of mind whenever issues arise.
4. Scalability for Growth
Fourth, as your business expands, so do your tech needs. That is why Managed IT Services Dallas scales with you, adapting to the changing demands of your growing venture.
5. Robust Network Security
Fifth, protecting your digital assets is non-negotiable. That is why Managed IT Services Dallas strengthens your digital fortress, while safeguarding your data in the bustling business landscape.
6. Strategic Outsourcing Advantage
Sixth, outsourcing isn't just a cost-saving move; it's also strategic. Managed IT Services Dallas leverages this advantage, ensuring your tech aligns seamlessly with your growth and plans.
7. Seamless Integration with Fort Worth
Lastly, Managed IT Services Fort Worth provides continuity and also collaboration, while ensuring a smooth digital transition beyond city borders.
Beyond Dallas: Managed IT Services Fort Worth
While exploring Managed IT Services, let's peek beyond Dallas borders. Managed IT Services Fort Worth opens doors for collaboration, extending your digital reach beyond the city limits.
Choosing the Right Managed IT Service Provider: A Simple Guide
In the bustling world of technology, finding the right Managed IT Services Dallas is crucial. But how do you choose the perfect fit for your business?
1. Assess Your Needs
Firstly, understand your business's IT needs. Always consider IT Solutions Dallas that align with your goals.
2. Look Beyond the Basics
Secondly, explore beyond Managed IT Services Dallas. Think Network Security Dallas and Outsourced IT services Dallas for a comprehensive solution.
3. Check Reputation and Experience
Thirdly, aim for a provider with a solid reputation and experience in the field. Managed IT Services Fort Worth is a plus.
4. Emphasize Communication
Fourthly, communication matters. Therefore, you must ensure your provider communicates clearly and also responsive to your queries.
5. Flexible Service Plans
Fifthly, Opt for flexibility. Your provider should offer tailored plans to meet your unique business requirements.
6. Prioritize Security
Sixthly, security is paramount. Choose a provider that emphasizes network security Dallas to safeguard your digital assets.
7. Scalability Matters
And most importantly, as your business grows, so should your IT services. Ensure scalability is a key feature.
Ensuring Cybersecurity in Dallas Businesses
In the quick-moving world of data and online dangers, Dallas businesses need to stay strong against cyber enemies. Here's why "Managed IT Services Dallas" isn't just about fixing problems; it's about making your digital space really secure.
Understanding the Cyber Threats
Bad folks on the internet are a real problem, and most importantly it's serious. Dallas businesses face sneaky viruses and hackers who want your data. That's why it's important to have a good plan for keeping things safe. Therefore, Managed IT Services act like your online protectors, while being experts at keeping these digital threats away.
The Role of Managed IT Services in Dallas Cybersecurity
Above all, you must consider Managed IT Services like trusted protectors for your digital space, always working to make your business stronger against online threats. They do more than just the basics, they also provide personalized solutions that perfectly match your unique needs – it's similar to having a solution made just for your business.
Securing Your Network, Simply
Keeping your digital information safe in Dallas is a big worry, and for good reason. Managed IT Services make sure your online paths are protected all the time. Don't worry about dangers; think of it as a strong force field around your business data.
Outsourced IT Services for Peace of Mind
Getting IT help from outside in Dallas isn't just about saving money; it's also about getting rid of your worries. That is why Managed IT Services take care of the tech stuff, so you can concentrate on what you're good at – running your business.
Fort Worth, Cybersecurity, and Managed IT Services
In addition, just a quick hop over in Fort Worth, businesses deal with the same digital threats. However, Managed IT Services in Fort Worth use the same plan – a personalized, and also easy approach to cybersecurity. The whole city is working together to keep digital troublemakers away.
To sum it up, Managed IT Services in Dallas aren't just about fixing tech problems; they're also your digital protectors, keeping your business safe from cyber threats. As we go through this cyber journey, keep in mind: simplicity is the key to a secure and hassle-free digital life.
Conclusion
In the fast-paced world of Dallas business, picking the right tech partner is important, and Managed IT Services Dallas is a standout choice.
Designed with local know-how, these services customize tech solutions to fit your business perfectly, making sure everything runs smoothly and issues get fixed quickly. Moreover, it can adapt as your business grows, which is great.
What makes it special is the clear communication, avoiding confusing tech talk. However, Network Security Dallas makes your digital stuff super safe, putting security first in the digital age. However, it's always not just about fixing problems; it's all about smart outsourcing, while also matching tech with business growth.
So, if you're thinking about growing outside Dallas, Managed IT Services Fort Worth helps with collaborative growth.
Basically, Managed IT Services Dallas isn't just a pick; it's a smart investment in tech excellence, making sure your business does well in the busy Texan business scene. Choose wisely; choose the path to tech success.
#network security dallas#network security services dallas#ipro media#ipro support#managed it support dallas#it company dallas#managed it services Dallas#managed it services fort worth#outsourced it services dallas
2 notes
·
View notes
Text
Positioned within the vibrant cityscape of Lubbock, Texas, Precision Managed IT stands as a beacon of technological prowess and reliability in the realm of outsourcing IT support. Our strategically located office embodies accessibility and expertise, catering to businesses seeking seamless and comprehensive IT solutions in this dynamic city.
Strategically situated within Lubbock's thriving business districts, our office serves as a central hub for businesses across diverse industries, from the healthcare sector near the medical facilities to the academic enterprises surrounding Texas Tech University. This strategic placement underscores our commitment to serving the varied tapestry of Lubbock's business community.
The physical space of Precision Managed IT is meticulously designed to exude professionalism and innovation. Boasting state-of-the-art infrastructure and a conducive workspace, our office cultivates an environment that fosters collaboration, trust, and ease for businesses seeking top-tier IT support services.
Beyond merely being a physical office, Precision Managed IT embodies a team of expert professionals deeply entrenched in the intricacies of the modern IT landscape. Each team member brings forth a wealth of technical knowledge, integrity, and proactive problem-solving skills to ensure that every client receives tailored, forward-thinking solutions to their IT needs.
Precision Managed IT isn't merely a service provider; it's a strategic partner invested in the success of the businesses we serve. We actively engage with our clients, forging strong partnerships aimed at elevating their technological infrastructure, optimizing operations, and ensuring seamless growth in an increasingly digital world.
Lubbock's dynamic business environment, educational institutions, and diverse industries align perfectly with Precision Managed IT's commitment to excellence and adaptability in the outsourcing IT support realm. We strive to remain at the forefront of technological advancements, empowering businesses to thrive amidst digital transformations and challenges.
In essence, Precision Managed IT represents more than just an IT support provider—it embodies trust, expertise, and efficiency in managing and optimizing technological infrastructure. Our presence in Lubbock signifies our unwavering dedication to simplifying IT complexities for businesses while upholding values of reliability, transparency, and a steadfast commitment to exceeding expectations.
Website: http://www.precisionmanagedit.com/lubbock-tx
Address: 5307 W Loop 289 Acc Rd, Lubbock, TX, 79414
Phone Number: +1 806-692-2884
Business Hours: Monday - Sunday : 07:00 AM - 07:00 PM
2 notes
·
View notes
Text
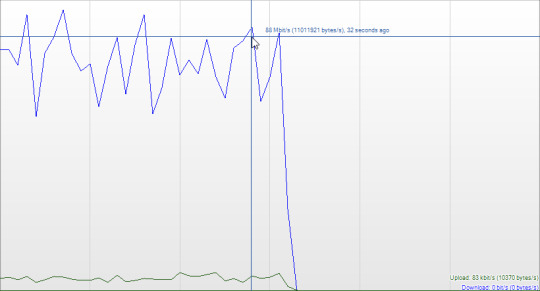
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text
#it support in Los Angeles#businesses#companies#home theater#cyber security#security camera#business setup services in la#network services#network security
2 notes
·
View notes
Text
#Security system installation service in Los Angeles CA#Security system supplier in Los Angeles CA#Security Camera System in Los Angeles CA#Cctv Systems in Los Angeles CA#Home Automation Installation in Los Angeles CA#Video Surveillance Camera Systems in Los Angeles CA#Network Cameras in Los Angeles CA#Alarm Installation in Los Angeles CA
1 note
·
View note
Text
MeshTek’s Smart IoT Framework: Building the Future of Connected Systems

MeshTek’s advanced IoT development service in action — where powerful software meets real-time automation. From smart connectivity to integrated mesh-based communication, the setup represents how businesses can monitor, manage, and optimize connected devices through a seamless, intelligent platform. The background workspace and digital overlays highlight MeshTek’s vision for scalable, secure, and low-latency IoT ecosystems designed for the modern world.
#MeshTek#IoT development service#Bluetooth mesh IoT#connected devices#smart automation#real-time IoT monitoring#low-latency communication#industrial IoT platform#smart infrastructure#scalable IoT systems#IoT software development#next-gen connectivity#AI-powered IoT#secure IoT network#edge computing solutions#smart business automation#intelligent IoT services#future-ready technology#MeshTek solutions#IoT mesh technology
0 notes
Text
Best Cybersecurity Solutions Provider in Noida: Protecting Businesses from Threats and Cyber Attacks- Wish Geeks Techserve

In today’s digital-first world, cybersecurity is not optional—it’s essential. As cyber threats grow in scale and sophistication, businesses of all sizes must adopt a proactive approach to protect their data, systems, and reputation. Whether you're a startup, SME, or enterprise, securing your IT infrastructure is vital for business continuity.
That’s where Wish Geeks Techserve comes in—your trusted partner and the best cybersecurity solutions provider in Noida. We offer comprehensive, affordable, and future-ready cybersecurity services in Noida, tailored to meet the unique needs of modern businesses.
Why Cybersecurity Should Be a Top Priority
From ransomware attacks and phishing scams to internal threats and data breaches, cyber risks are everywhere. One breach can lead to financial loss, damaged reputation, and legal complications.
Key Reasons to Invest in Cybersecurity:
Protect sensitive business and customer data
Ensure compliance with industry and data protection regulations
Maintain operational continuity and reduce downtime
Build customer trust and brand credibility
Prevent revenue losses due to cyber disruptions
For businesses in Noida and across India, Wish Geeks Techserve offers world-class protection with customized and scalable cybersecurity solutions.
Why Choose Wish Geeks Techserve as Your Cybersecurity Partner?
As a top-tier cybersecurity solutions provider in Noida, we bring together a team of experienced cybersecurity analysts, ethical hackers, and IT security experts. Our mission is to protect your digital assets and future-proof your business operations.
✅ Tailored Cybersecurity Strategies
We assess your existing infrastructure and design bespoke security frameworks aligned with your business operations.
✅ 24/7 Threat Monitoring
Our dedicated security team monitors your digital systems round the clock for vulnerabilities, breaches, and suspicious activity.
✅ Rapid Incident Response
We minimize damage and restore operations quickly in case of any cyber threat or security breach.
✅ Cost-Effective Services
Get enterprise-level protection at competitive rates. Perfect for startups, SMEs, and growing enterprises.
✅ Industry Compliance
Our solutions are designed to meet industry standards such as ISO, GDPR, HIPAA, and more.
Our Comprehensive Cybersecurity Services
At Wish Geeks Techserve, we offer a full spectrum of cybersecurity services in Noida and across India to protect your digital infrastructure.
🔐 Network Security Services
Protect your internal systems, servers, and communication channels from unauthorized access and external threats.
🛡️ Endpoint Security
Secure laptops, mobile devices, and remote workstations against malware, ransomware, and phishing attacks.
🧠 Security Audits & Vulnerability Assessment
Identify weaknesses in your system before hackers do with detailed assessments and regular audits.
🧪 Penetration Testing
Simulate real-world attacks to evaluate your system’s defense strength and fix loopholes proactively.
📊 Risk Management & Compliance
Stay ahead of compliance risks with expert consultation and documentation support for various regulatory frameworks.
🧾 Data Encryption & Backup
Keep sensitive information secure and recoverable with advanced encryption protocols and backup solutions.
👨💻 Managed Security Services (MSS)
Outsource your IT security operations to our team for continuous monitoring, threat detection, and incident response.
Who Can Benefit From Our Cybersecurity Services?
Wish Geeks Techserve’s services are designed for all sectors, ensuring every business is equipped to tackle today’s digital risks.
Startups & SMEs looking to build a secure digital foundation
Healthcare & Fintech businesses requiring compliance with strict data protection standards
eCommerce platforms that handle large volumes of customer and payment data
Educational Institutions managing student records and digital learning tools
Government & Public Sector organizations that need critical infrastructure security
Enterprises with distributed networks, remote teams, and hybrid cloud models
Whether you’re local in Noida or based anywhere in India, our expert team is ready to secure your business environment.
Our Process: How We Deliver Secure IT Solutions
Our structured and efficient approach to cybersecurity includes:
Initial Consultation & Risk Evaluation – Understand your business, assets, and potential threats
Security Planning & Strategy – Create a custom security roadmap based on your goals
Implementation & Integration – Deploy advanced tools, firewalls, and protocols for protection
Continuous Monitoring – Ongoing analysis, real-time alerts, and performance reporting
Incident Response & Recovery – Quick reaction and restoration in case of security incidents
Periodic Updates & Compliance Checks – Ensure your systems stay current and compliant
Why We’re Recognized as the Best Cybersecurity Company in Noida
Experienced Cybersecurity Experts
24/7 Monitoring and Fast Incident Response
Advanced Tools and AI-Powered Detection
Cross-Industry Expertise
Scalable and Future-Ready Security Solutions
Budget-Friendly Security for Businesses of All Sizes
We combine technical expertise with business insight to deliver cybersecurity that goes beyond firewalls.
Let’s Secure Your Business Future
Don’t wait for a breach to take action. Protect your company today with Wish Geeks Techserve, the best cybersecurity company in Noida. We provide trusted cybersecurity services Noida and across India to help you operate safely and confidently in a digital-first world.
📩 Contact us today for a free consultation and system security audit.
#Cybersecurity Services Noida#cybersecurity solutions in Noida#Best Cybersecurity Solutions Provider in Noida#Cybersecurity Services in Noida#Cybersecurity Services India#Best Cybersecurity Company in India#IT Security Services India#Cybersecurity Solutions Provider in India#Cybersecurity Solutions Provider in Noida#best Cybersecurity Solutions Provider in Noida#Network Security Services in India
0 notes
Text
Managed Services Market to Reach $576.7 Billion by 2032
Meticulous Research®—a leading global market research company, published a research report titled ‘Managed Services Market—Global Opportunity Analysis and Industry Forecasts (2025-2032).’ According to this latest publication from Meticulous Research®, the managed services market is expected to reach $576.7 billion by 2032, at a CAGR of 9.4% from 2025 to 2032.
The growing focus of organizations on cost optimization, the rising inclination of enterprises toward outsourced IT operations, the lack of skilled IT personnel, the rise in cyber threats & ransomware attacks on businesses, and businesses’ increasing investments in digital transformation are factors driving the growth of the managed services market. However, market growth is restrained by the lack of trust among enterprises in giving control of their systems to third-party organizations.
In addition, the rising utilization of advanced technologies and the rising adoption of cloud-based solutions are expected to generate considerable opportunities for market stakeholders. However, the market faces substantial challenges, including the low adoption of managed services by SMEs. Additionally, the proliferation of 5G technologies is a key trend in this market.
Key Players:
The managed services market is moderately competitive due to the presence of many large and small-sized global, regional, and local players. The key players operating in the managed services market include Accenture (Ireland), Tata Consultancy Services Limited (India), HCL Technologies (India), Cognizant (U.S.), IBM Corporation (U.S.), Fujitsu Limited (Japan), Kyndryl Holdings, Inc. (U.S.), Verizon Communications Inc. (U.S.), Google LLC (U.S.), Hughes Network Systems, LLC (U.S.), AT&T Inc. (U.S.), Microsoft Corporation (U.S), Cloudflare, Inc. (U.S.), Wipro Limited (India), HP Inc. (U.S.), SecureWorks Corp. (U.S.), Hitachi Vantara LLC (U.S.), Cisco Systems, Inc. (U.S.), DXC Technology Company (U.S.), and Infosys Limited (India).
The managed services market is segmented based on type, deployment mode, organization size, and end-use industry. The report also evaluates industry competitors and analyzes the managed services market at the regional and country levels.
Among the managed service types studied in this report, in 2025, the managed security services segment is anticipated to dominate the managed services market, with a share of over 39.0%. Building and maintaining an in-house security team is expensive; however, managed security services provide cost-effective access to skilled professionals, which is driving the adoption of managed security services. Managed security services provide round-the-clock monitoring and management of tools such as firewalls, intrusion detection systems, and endpoint detection & response. These benefits contribute to the segment’s large share in the managed services market.
Among the deployment modes studied in this report, in 2025, the cloud-based segment is anticipated to dominate the managed services market, with a share of over 62%. The substantial benefits of cloud-based services, including on-demand access to experienced and qualified resources, high levels of business agility and resilience, automatic upgrades, and cybersecurity, contribute to the segment’s dominant position in the managed services market.
Among the organization sizes studied in this report, in 2025, the large enterprises segment is anticipated to dominate the managed services market, with a share of over 67%. Large organizations’ rising need to manage complex IT infrastructures, their constantly changing IT needs, and increased emphasis on risk mitigation and compliance contribute to the segment’s dominant position in the managed services market.
Among the end-use industries studied in this report, in 2025, the BFSI segment is anticipated to dominate the managed services market, with a share of over 34%. The sector's increased focus on uninterpreted and enhanced customer service and the high adoption of AI/ML technology for process automation and fraud detection in the BFSI sector contribute to the segment’s dominant position in the managed services market.
Among the geographies studied in this report, in 2025, North America is anticipated to dominate the managed services market, with a share of over 40%. The presence of recognized Managed Service Providers (MSPs) in the region, the growing use of managed security services for privileged access management, the increased need to protect network infrastructure, and increased spending on IT capabilities are factors contributing to the region’s dominant position in the managed services market.
Download Sample Report Here @ https://www.meticulousresearch.com/download-sample-report/cp_id=6025
Key Questions Answered in the Report:
What is the revenue generated from the sale of managed services globally?
At what rate is the global demand for managed services projected to grow for the next five to seven years?
What is the historical market size and growth rate for the managed services market?
What are the major factors impacting the growth of this market at the global and regional levels?
What are the major opportunities for existing players and new entrants in this market?
Which type, deployment mode, organization size, and end-use industry segments are expected to create major traction for the players in this market?
What are the key geographic trends in this market? Which regions/countries are expected to offer significant growth opportunities for the organizations operating in the managed services market?
Who are the major players in the managed services market? What are their specific service offerings in this market?
What are the recent key developments in the managed services market? What are the impacts of these strategic developments?
Contact Us: Meticulous Research® Email- [email protected] Contact Sales- +1-646-781-8004 Connect with us on LinkedIn- https://www.linkedin.com/company/meticulous-research
#Managed Services Market#Managed Security Services#Managed IT Infrastructure Services#Managed Information Services#Managed Data Center Services#Managed Network
0 notes
Text
How to Integrate Network Firewall Security into Your Overall IT Strategy

In today’s digital-first business environment, cybersecurity is no longer just an IT concern—it’s a business imperative. As cyber threats become more sophisticated and widespread, organizations must adopt a multi-layered defense strategy. At the heart of this defense lies network firewall security.
Firewalls are no longer simple barriers against unauthorized access. They are intelligent, adaptive, and critical components of a comprehensive IT security strategy. However many businesses still treat firewalls as stand-alone tools, failing to integrate them effectively into their broader IT frameworks.
In this article, we’ll walk you through how to integrate network firewall security into your overall IT strategy—so it works not as an isolated system, but as a powerful enabler of secure and resilient digital operations.
Understanding the Role of Network Firewall Security
A network firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a gatekeeper, allowing legitimate traffic while blocking malicious or unauthorized access.
There are different types of firewalls:
Packet-filtering firewalls
Stateful inspection firewalls
Next-generation firewalls (NGFWs)
Web application firewalls (WAFs)
Cloud-native firewalls
In modern IT environments that include cloud infrastructure, remote workers, SaaS tools, and mobile devices, firewalls need to evolve and integrate seamlessly with your overall IT and cybersecurity strategy.
Why Integration Matters
Integrating firewall security with your IT strategy ensures you’re not just reacting to threats—you’re preventing them. Here’s why integration is essential:
Improved visibility and control over network activity
Faster incident response through centralized management
Reduced risk of security gaps or misconfigurations
Better compliance with data protection regulations
Stronger alignment with business objectives and IT goals
Step 1: Align Firewall Objectives with Business Goals
Before diving into technical details, start your firewall strategy with your overall business objectives.
Ask yourself:
What are your key digital assets?
Where does your business operate (on-prem, cloud, hybrid)?
What industry regulations or compliance standards must you meet?
How much risk are you willing to tolerate?
By understanding the bigger picture, you can tailor firewall policies and configurations that don’t just protect—but also support—your operations.
Step 2: Conduct a Network Security Assessment
To integrate your firewall effectively, you must first understand your current security posture.
Key activities include:
Mapping your network architecture (including remote access points, IoT devices, and cloud environments)
Identifying traffic patterns and sensitive data flows
Assessing existing firewalls, their placement, configurations, and performance
Finding gaps or misalignments between firewall controls and business processes
This step provides a baseline and highlights where improvements or integrations are necessary.
Step 3: Choose the Right Type of Firewall
Not all firewalls are created equal. To support your IT strategy, choose a solution that complements your infrastructure.
On-Premises Business
Opt for stateful inspection firewalls or NGFWs that provide deep packet inspection and intrusion prevention.
Cloud-Based or Hybrid Environment
Integrate cloud-native firewalls that are scalable, auto-configurable, and centrally managed (e.g., AWS Firewall Manager, Azure Firewall).
Web-Heavy Applications
Deploy Web Application Firewalls (WAFs) to protect against web-based attacks like SQL injections and XSS.
Remote Workforce
Use firewalls with VPN integration and Zero Trust Network Access (ZTNA) features.
Matching the right firewall to your IT setup ensures better coverage, performance, and cost-efficiency.
Step 4: Integrate with Centralized Monitoring and SIEM Tools
Standalone firewall logs are useful—but limited. When integrated with your Security Information and Event Management (SIEM) or centralized monitoring systems, firewalls become intelligent sources of threat insight.
Benefits of SIEM Integration:
Real-time alerts for suspicious network activity
Correlated analysis across devices and systems
Automated incident response and threat isolation
Unified dashboard for security and compliance reporting
By feeding firewall logs into your broader monitoring systems, you create a holistic security ecosystem.
Step 5: Define and Enforce Consistent Security Policies
Firewalls are only as effective as the rules they enforce. If you’re managing different firewalls across on-prem and cloud networks, consistency is critical.
Best Practices:
Create role-based access policies that restrict sensitive areas
Implement application-layer filtering to block unwanted software or services
Use geo-blocking or IP whitelisting for location-based controls
Set bandwidth limits for non-critical apps during business hours
Review and update rules regularly to match business changes
Make sure these policies are integrated into your wider IT governance framework and communicated clearly to all stakeholders.
Step 6: Automate Where Possible
Manual configurations are error-prone. Automating firewall rule management and threat response can boost efficiency and consistency.
Automation opportunities:
Auto-deployment of firewall configurations across branches or cloud regions
Real-time threat detection and blocking using AI or machine learning
Scheduled audits and compliance checks
Self-healing security systems that adapt to new vulnerabilities
Many modern firewall platforms offer APIs and integrations that support Infrastructure as Code (IaC), helping you embed firewall logic into your DevOps pipelines.
Step 7: Train Your Team and Foster Collaboration
Even the best firewall won’t protect you if your team doesn’t know how to use it. Integration is not just technical—it’s also about culture and communication.
Key focus areas:
Train IT and security teams on firewall management, policy enforcement, and monitoring tools
Include firewall strategies in IT planning sessions
Encourage collaboration between cybersecurity, cloud, networking, and application teams
Document all configurations and decisions to ensure transparency and knowledge transfer
Integrated firewall security requires cross-functional alignment to be truly effective.
Step 8: Monitor, Audit, and Optimize Continuously
Integration isn’t a one-time task. Your network evolves, new threats emerge, and your business shifts. A successful integration includes ongoing refinement.
Establish a routine for:
Firewall performance monitoring
Traffic analysis to detect bottlenecks or malicious patterns
Security audits to check for rule misconfigurations or outdated settings
Policy optimization based on current risk levels or industry benchmarks
Incident reporting and post-mortems for continuous improvement
Make this part of your larger IT and cybersecurity lifecycle management.
Conclusion
Firewalls are foundational to modern cybersecurity—but only when fully integrated into your IT strategy. When treated as isolated tools, they offer limited value. But when woven into the fabric of your infrastructure, processes, and people—they become powerful assets that drive resilience, agility, and trust.
As you build your IT roadmap, don’t think of firewall security as a checkbox. Think of it as a dynamic, evolving part of your digital ecosystem—one that protects your future as much as your present.
#firewall service#firewall security#network firewall security#Firewall Solutions#firewall protection#firewall security service#cloud based firewall#next generation firewalls#fortinet firewalls#palo alto firewall
0 notes