#Secure data management
Explore tagged Tumblr posts
Text
Streamline Your Workflow with Microsoft 365 Suite Deployment Services in 2025
In today’s fast-paced business environment, achieving efficiency and seamless collaboration is critical to staying ahead. The Microsoft 365 Suite offers a comprehensive range of tools designed to streamline workflows, enhance productivity, and foster better communication. However, to unlock its full potential, businesses need tailored deployment services that align with their specific goals and operational requirements.

Why Microsoft 365 Suite is Essential in 2025
Unified Communication and Collaboration Microsoft Teams, SharePoint, and Outlook provide integrated platforms that support real-time communication, file sharing, and collaboration across teams—whether they’re in the same office or dispersed globally.
Enhanced Productivity with AI and Automation Tools like Microsoft Viva and Power Automate bring AI-driven insights and automation capabilities, enabling businesses to reduce manual tasks and focus on strategic initiatives.
Scalable and Secure Solutions With advanced security features and compliance tools, Microsoft 365 ensures businesses can scale their operations confidently while safeguarding sensitive data.
Flexibility for Hybrid Work Models The suite’s cloud-based architecture empowers employees to work from anywhere, ensuring a seamless transition between remote and on-site operations.
The Importance of Professional Deployment Services
While Microsoft 365 offers robust features, implementing it effectively can be challenging without expert guidance. Professional deployment services are crucial for:
Customised Solutions: Tailoring the suite’s features to your business’s unique needs ensures maximum ROI.
Efficient Migration: Migrating data from legacy systems with minimal disruption requires technical expertise.
Training and Support: Ensuring your teams are equipped to leverage the suite effectively enhances adoption rates.
Ongoing Optimisation: Regular assessments and updates keep your systems aligned with evolving business objectives.
Addressing Modern Business Challenges
Reducing Silos By integrating tools like Teams, OneDrive, and Planner, organisations can eliminate data silos and promote cross-departmental collaboration.
Improving Decision-Making Power BI within Microsoft 365 provides actionable insights through real-time analytics, enabling leaders to make informed decisions swiftly.
Boosting Employee Engagement Features like Viva Insights prioritise employee well-being and productivity, helping organisations retain top talent.
Key Considerations for Microsoft 365 Deployment
Assess Your Business Needs: Understand your current challenges and how Microsoft 365 can address them.
Plan for Change Management: Foster a culture of adaptability to ensure smooth adoption.
Focus on Security: Leverage tools like Microsoft Defender to mitigate cybersecurity risks.
Partner with Experts: Collaborate with experienced providers to ensure a seamless deployment process.
Conclusion
Microsoft 365 Suite is not just a productivity tool; it’s a strategic asset for driving innovation and efficiency in 2025. By partnering with a trusted deployment service provider, businesses can ensure a smooth transition, empowering their teams to achieve more while staying agile in a competitive landscape.
Ready to revolutionise your workflow? Explore how Microsoft 365 Suite deployment can transform your business today.
#Microsoft 365 Suite deployment#Microsoft 365 migration services#Cloud-based collaboration tools#Hybrid work solutions#Microsoft Teams integration#Secure data management#AI-driven business tools#Customised Microsoft 365 implementation#Enhanced business collaboration#Power BI analytics for businesses#Microsoft 365 professional deployment#Data security in Microsoft 365#Employee engagement with Microsoft Viva
0 notes
Text
I am so unbelievably pissed off. FUCK HOAs
Oh, my trash/recycling bin can't be visible except on pickup day? Ok whatever fine I hate you but I can deal with this
Weekly inspections?????? FU FU FU FU FU
SECOND NOTICE ALSO WE'RE CHARGING YOU MONEY TO SEND YOU CERTIFIED MAIL OF THIS TOTALLY LEGIT TOTALLY SECOND NOTICE OF WHAT IS ACTUALLY A VIOLATION cue me: checks notes. Hmm. My recycling bin was. on the curb. on recycling pickup day. You know. The day it has to be out. The day it is motherfucking ALLOWED TO BE FUCKING OUT AND VISIBLE.
so. 1) not a violation
I have sent them the trash AND recycling pickup schedules, which are DIFFERENT, btw
I have disputed the fact of the violation
I have disputed the linking of this "violation" to a previous violation MONTHS AGO--their "first notice" in this case was a "Courtesy Notice" LITERALLY 5 MONTHS AGO and they've done so many inspections since then and my bin CLEARLY WASN'T OUT IN THOSE INTERVENING MONTHS so WTMFH
So I am posting like a crazy person here instead of sending the absolutely deranged email I almost sent (I did send a slightly less deranged version with the disputes, and requesting a hearing)
OMG. It has been. Less than one hour since I learned this fun fun news. My bin was out YESTERDAY, y'all. YESTERDAY. I am going to blow a gasket
#it's a relatively privileged problem to have (omg i have a home truly i am grateful) but it's still a goddamned problem and i'm allowed#to fucking complain about it#in case it needs to be said#*rolling my eyes*#i advocate for free/actually affordable housing for everyone who needs it because we ALL deserve a safe secure stable home#whatever type of home that may be#it is absolutely goddamned ridiculous that megacorps can buy all the housing#rent it out at extortionate rates and evict people willy nilly#and we're talking about a “housing crisis” and not a “STOP LETTING CORPORATIONS AND BILLIONAIRES HOARD ALL THE HOUSING” crisis#goddamn.#ha elect me president (ahaha don't do this i am not a good public speaker) and I'll push congress to pass some really neat legislation#hey be more direct: elect me to congress (ahaha don't do this) and i'll WRITE some goddamn nifty legislation and yell about it as long and#as loud as i can until people start to just fucking say yes to make me shut the fuck up#(i know that's not how it works. again. don't actually elect me to a government position)#exemplia gratis:#No individual person shall own more than 6 homes UNLESS they pay a Housing Market Shrinkage Fee for removing viable housing from the market#why 6 and not 2? 2 is a lot! it's excessive! but having A vacation home shouldn't be a crime. Having 5 vacation homes is ridiculous and#awful and whatever but it's not likely to be the source of all our greatest “housing shortage” problems. no. I'm aiming for the absolutely#monstrously greedy and egregious motherfuckers who---ok#hang on. how many homes does the average min and max homeowner own? I would like to see data on that. but anyway#the next part of the legislation:#Homes owned >6 shall be charged X% Housing Market Shrinkage Fee UNLESS they are rented for affordable (15% or less than renter net income)#housing and are actively occupied by said renters. Rented out and charging more than 15% of renter's net? still gotta pay up.#EMPTY housing >6 shall be subject to an additional Y% Housing Market Shrinkage Fee (tax? should I call it a tax?) which increases with ever#month that the housing goes unoccupied. no one living in it? sell it rent it or pay the fuck up. and still pay the fuck up if you rent it#for way too goddamn much money#but like. less. we only REALLY hate you if you sit on empty houses that you don't even let anyone use#ok that's individuals. now onto BUSINESSES#ok so immediately it gets a little complicated cuz like presumably there's rental management businesses that don't own the rental propertie#that they manage BUT there are also companies that just outright own a shitfuckton of housing and THIS is the truly egregious monstrous sid
24 notes
·
View notes
Text
Abathur

At Abathur, we believe technology should empower, not complicate.
Our mission is to provide seamless, scalable, and secure solutions for businesses of all sizes. With a team of experts specializing in various tech domains, we ensure our clients stay ahead in an ever-evolving digital landscape.
Why Choose Us? Expert-Led Innovation – Our team is built on experience and expertise. Security First Approach – Cybersecurity is embedded in all our solutions. Scalable & Future-Proof – We design solutions that grow with you. Client-Centric Focus – Your success is our priority.
#Software Development#Web Development#Mobile App Development#API Integration#Artificial Intelligence#Machine Learning#Predictive Analytics#AI Automation#NLP#Data Analytics#Business Intelligence#Big Data#Cybersecurity#Risk Management#Penetration Testing#Cloud Security#Network Security#Compliance#Networking#IT Support#Cloud Management#AWS#Azure#DevOps#Server Management#Digital Marketing#SEO#Social Media Marketing#Paid Ads#Content Marketing
2 notes
·
View notes
Text
'if youre looking to be secure, MFA is best' shut up + dont speak to me again + rot in hell + fuck you + fuck you again + let me turn it off or i crush you and your family with my psychic powers.
#i dont care if MFA made you guaranteed safe from any and all malware and security breaches#Im Not Doing That!!!!!#if u think im chaining myself to one phone youre out of your mind. this things gonna give up the ghost any day now!!!#and her battery is shit so shes dead a lot of the time anyway! plus sometimes its just in the other room!!! Fuck You!!!!#worst security measure by far. hate it.#hate it when banks try to pull it when paying for stuff. fuck it! take my bank details i dont care#ive carefully curated an ascetic life for myself where i keep as little money in my actual account as possible#both to curb against impulsive online purchases (bcos i need to go into town to put money into my account b4 buying anything)#and because i fancy myself cool and roguish and anti-establishment when likely what i am is a fucking fool but whatever. not punished so fa#EDIT WAIT TAG RANT NOT FINISHED I REMEMBER WHY I WAS ON IT!!!#FUCKING BITWARDEN WANTS ME TO SWITCH TO 2FA AND GOT PISSY AT ME IN SETTINGS WHEN I SWITCHED IT BACK???#bro youre my fucking password manager. do you know why youre here?#for a couple months i lived off demo sessions of debian where all my data vanished every time i turned off my laptop#and i got thru it BECAUSE! OF! BITWARDEN! because i could just log into my vault and continue business as usual!#without having to piss around with my phone!! fuck!!!!!!!!!!!!!!!!!!!!!#like bro cmon. ideal world is one where i can just decide to go use a library computer with no tech on me and have it fuckinggg work#Because I Have All My Passwords In My Vault And I Have A USB Stick For Retaining Files#aughh. augh!!!!!!!!!!!!!!!!!!!!!! i just want to be anonymous#well. in a technical sense. in a broader sense the previous post is me talking extensively abt my irl presentation#but whatever. i dont get into discourse these days i trust u tumblrinas < bad thing to say but what the fuck ever#my famous catchphrase Last Time I Got Doxxed Nothing Came Of It So If It Happens Again I'll Probably Be Fine
3 notes
·
View notes
Text
Why Security and Compliance Are Vital for Today’s Data Centers
Modern data centers must prioritize security and regulatory compliance to safeguard data, ensure uptime, and meet evolving standards like GDPR, ISO 27001, HIPAA, and NIS2 in an increasingly complex threat landscape.
#technology#security#data center#cybersecurity#data#center#regulatory#compliance#GDPR#ISO27001#HIPAA#NIS2#directive#threat#landscape#protection#secure#infrastructure#risk#management#access#control#frameworks#IT#modern#centers#operational#resilience#governance#network
1 note
·
View note
Text
Secure Configurations on your Technology

Ensuring secure configurations on your technology is crucial to protect against cyber threats and vulnerabilities. Here are some tips to make sure your configurations are secure:
-Change Default Settings: Always change default usernames and passwords on your devices.
-Enable Firewalls: Use firewalls to block unauthorized access to your network.
-Regular Updates: Keep your software and firmware up to date to patch any security holes.
-Strong Passwords: Use complex and unique passwords for all your accounts and devices.
-Disable Unnecessary Services: Turn off services and features you don't use to reduce potential entry points for attackers.
-Monitor and Audit: Regularly monitor and audit your configurations to ensure they remain secure.
Stay vigilant and keep your technology secure! #CyberSecurity #SecureConfigurations #StaySafe – www.centurygroup.net
#Cybersecurity#managed it services#data backup#Secured Configuration#cloud technology services#phishing
3 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider ���smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
6 notes
·
View notes
Text
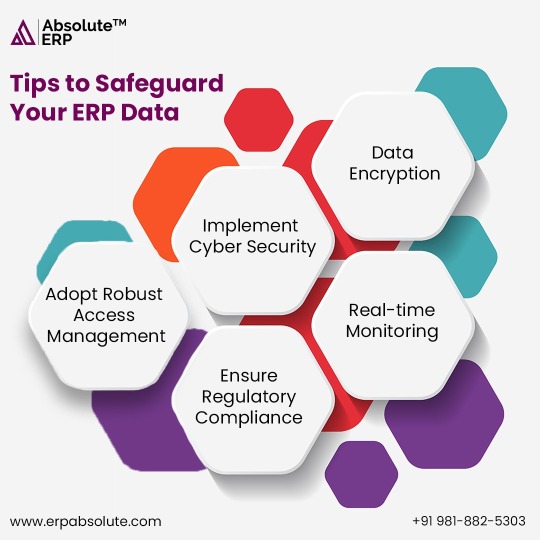
#ERP Data#ERP Safety#ERP Solutions#Enterprise Resource Planning Software#Data Management#Data Security
1 note
·
View note
Text
Securing the Software Supply Chain: Essential Strategies for Protecting Your Business in a Complex Digital Landscape

View On WordPress
#business#Cyber Threats#cybersecurity#data protection#DevSecOps#Digital Security#risk management#secure development#Security#Software Composition Analysis#software integrity#software supply chain security#Supply Chain
1 note
·
View note
Text
Overcoming Employee Data Management Challenges with HRMS
Managing employee data is one of the most critical yet complex tasks for HR departments. From recruitment to payroll, performance evaluations to compliance, HR professionals handle vast amounts of sensitive information. Without the right tools, data management can become overwhelming, leading to errors, inefficiencies, and security risks. This is where a Human Resource Management System (HRMS) comes into play, offering solutions to streamline and secure data management processes. Here’s how HRMS can help overcome the common challenges of employee data management:
1. Centralized Data Storage
One of the most significant challenges in employee data management is handling scattered and siloed data. When data is stored in different systems or even in physical files, it becomes difficult to access and update. HRMS offers a centralized platform where all employee information is stored in one place. Whether it’s personal information, attendance records, or performance data, HR professionals can access the data quickly and easily. This centralization eliminates redundancy and ensures that HR teams have access to up-to-date information at all times.
2. Enhanced Data Accuracy
Manual data entry is prone to errors, which can lead to inaccurate employee records, payroll issues, and compliance risks. HRMS automates many data entry processes, reducing the likelihood of human error. For example, when employees update their personal information through a self-service portal, the data is automatically reflected in the system. Additionally, automation helps ensure that calculations for payroll, benefits, and other HR processes are accurate, minimizing the risk of mistakes that can affect both the organization and its employees.
3. Improved Data Security
Data security is a top concern for HR departments, as they handle sensitive employee information such as social security numbers, bank details, and medical records. Without proper security measures, this data is vulnerable to breaches or unauthorized access. HRMS systems are equipped with robust security features, such as encryption, role-based access, and multi-factor authentication, ensuring that only authorized personnel can access specific data. This level of security helps HR departments protect employee data and comply with data privacy regulations like GDPR or CCPA.
4. Compliance Management
Maintaining compliance with ever-evolving labor laws and regulations is a significant challenge for HR departments. Non-compliance can result in legal penalties, financial losses, and reputational damage. HRMS helps ensure compliance by automatically updating to reflect changes in labor laws, tax regulations, and company policies. It also generates audit trails and compliance reports, helping HR teams stay organized and prepared for audits. Additionally, HRMS systems provide timely reminders for compliance deadlines, such as contract renewals or mandatory training.
5. Seamless Employee Onboarding and Offboarding
Onboarding new employees and offboarding departing staff involves managing a lot of paperwork, from contracts and tax forms to benefits enrollment. If these processes are handled manually, it can lead to delays, lost documents, and missed deadlines. HRMS streamlines both onboarding and offboarding processes by automating document generation, digital signatures, and task tracking. New employees can complete all required paperwork online, and HR can track their progress in real time. Similarly, when an employee leaves, HRMS ensures that all necessary steps, such as exit interviews and final pay settlements, are completed efficiently.
6. Employee Self-Service Options
Without HRMS, HR teams often spend a significant amount of time handling routine inquiries and data updates, such as leave requests or address changes. This administrative burden can detract from more strategic HR tasks. HRMS empowers employees with self-service capabilities, allowing them to manage their own profiles, update personal information, request leaves, and view payslips without HR intervention. This not only saves time for HR professionals but also improves employee satisfaction by giving them more control over their own data.
7. Scalability and Flexibility
As organizations grow, the volume of employee data increases exponentially. Managing this growth with traditional data management methods can become overwhelming. HRMS offers scalability, allowing HR teams to handle an increasing amount of data without sacrificing efficiency. Whether the company is adding new employees, expanding to new locations, or implementing new policies, HRMS can easily accommodate these changes. Moreover, HRMS systems are flexible, allowing customization to meet the specific needs of an organization.
8. Data-Driven Decision Making
Without effective data management, it’s difficult for HR teams to make informed decisions. HRMS not only organizes and stores employee data but also provides analytical tools that enable data-driven decision-making. For example, HR professionals can generate reports on employee performance, attendance, and turnover rates, helping them identify trends and make strategic improvements. With access to real-time data, HR leaders can make better decisions regarding hiring, promotions, and workforce planning.
9. Reduced Administrative Burden
The manual management of employee data is time-consuming and labor-intensive. HRMS reduces the administrative burden on HR teams by automating repetitive tasks such as data entry, report generation, and payroll processing. This automation allows HR professionals to focus on more strategic initiatives, such as employee engagement, talent development, and organizational culture, rather than getting bogged down by administrative duties.
10. Simplified Reporting and Analytics
Tracking key HR metrics, such as employee turnover, engagement levels, and performance trends, is crucial for organizational success. Without a proper system in place, generating accurate reports can be time-consuming and prone to errors. HRMS simplifies reporting by providing real-time analytics and customizable reports. These insights allow HR professionals to identify patterns, address issues, and make data-driven decisions that contribute to the overall success of the organization.
Conclusion
In conclusion, employee data management is a challenging but essential aspect of HR. HRMS software offers a comprehensive solution to streamline data management, enhance security, and improve efficiency. By adopting HRMS, organizations can not only overcome data management challenges but also create a more organized, secure, and efficient HR function, ultimately contributing to the success and satisfaction of employees.
1 note
·
View note
Text

Wastewater Treatment Company in Trivandrum
Water Purification Services in Trivandrum
#purification#startup#waste management#wastewatertreatment#water purifier#watercolor#kerala#waterpurifier#watertreatment#effluent treatment plant#service#sewage water treatment#water security#sewage treatment plant manufacturer#efficiency#effluentdisposalreport#wastewater data#zero waste#wasteland#water plants#disposable vape
2 notes
·
View notes
Text
Unlock Fort Knox for Your Laptop: The Definitive Guide to Bulletproof Security

What steps can I take to enhance my laptop's security?
Dive into my latest Blog post and discover the ultimate secrets to fortifying your laptop's defenses! Transform your device into a digital fortress and safeguard your data like never before.
From foolproof password strategies to state-of-the-art encryption techniques, explore a treasure trove of tips and tricks to keep hackers at bay. Say goodbye to cyber worries and hello to peace of mind!
Ready to take control of your laptop's security? Arm yourself with knowledge now!
Read the full post and become the guardian of your digital domain. #LaptopFortress #SecureYourData #ReadMore
#LaptopSecurity#DataProtection#CybersecurityTips#Laptop security#Data protection#Cybersecurity tips#Digital privacy#Encryption#Password management#Cyber threats#Data security measures#Online safety#Tech security#Information security#Secure computing#IT security#Protecting sensitive data#Internet safety
2 notes
·
View notes
Text
Cybersecurity Made Easy: Sigzen Technologie’s Approach to Effective Vulnerability Management
In today’s digital age, cybersecurity is paramount to safeguarding sensitive data and maintaining business continuity. As cyber threats continue to evolve, organizations must adopt comprehensive strategies to mitigate risks effectively. Sigzen Technologies offers cutting-edge solutions in Vulnerability Management, making cybersecurity easy and effective for businesses of all sizes. Vulnerability…

View On WordPress
#Cybersecurity Solutions#Data Privacy#Information Security#Network Vulnerabilities#Security Solutions#Vulnerability Management
3 notes
·
View notes
Text
THE IMPORTANCE OF DATA MANAGEMENT AND DATA SECURITY IN HEALTHCARE
Data is the lifeblood of the healthcare industry. It encompasses patient records, treatment plans, medical histories, and an array of vital information that healthcare providers rely on to deliver the best possible care. As the healthcare landscape becomes increasingly digital, the importance of data management and data security has never been more critical. In this Blog, we’ll delve into the significance of safeguarding patient data and how E_care, a leader in healthcare management software, prioritizes data security to protect sensitive patient information.
Preserving Patient Confidentiality:
Compliance with Data Protection Regulations:
The Importance of Data Management & Data Security in Healthcare
Data Encryption:
Access Control:
Data Backups and Recovery:
Security Audits and Monitoring:
Education and Training:
Data Security as a Competitive Advantage:
E Care Hospital Management Software
Our Social medias:
LinkedIn: E CARE - Hospital Management Software
Facebook: E-care
Instagram: e_care_hms
X: E-Care Hospital Management Software
#e care#hms#hospital management software#hospital management system#health#data management#data security
3 notes
·
View notes
Text

Ditch the disorganized chaos of traditional document management. Embrace seamless, AI-powered file sharing and storage with eShare.ai. Our smart platform helps businesses and professionals stay organized, secure, and efficient. Clutter Off. Clarity On.
📂 Instantly declutter 🔐 Keep data secure 🚀 Improve team collaboration 📲 Scan the QR code to get started today!
Work smart with eShare.ai — beyond storage & sharing.
#eShare.ai#document management#AI storage#cloud storage#file sharing#productivity#digital workspace#work smart#clarity#declutter#digital organization#SaaS#smart storage#remote work tools#secure file sharing#AI document platform#tech startup#clutter-free work#digital solutions#QR code#data management
0 notes
Text
Manager, Sales
Job title: Manager, Sales Company: CyberArk Job description: , CyberArk provides the most comprehensive security offering for any identity – human or machine – across business applications…, distributed workforces, hybrid cloud workloads and throughout the DevOps lifecycle. The world’s leading organizations trust… Expected salary: Location: London Job date: Fri, 18 Jul 2025 04:28:43 GMT Apply for…
#5G#Android#Azure#Backend#Blockchain#cleantech#Cloud Security Specialist#cloud-computing#computer-vision#Crypto#data-engineering#DevOps#digital-twin#Ecommerce#embedded-systems#Frontend#gcp#generative AI#hybrid-work#Java#mobile-development#product-management#prompt-engineering#rpa#Salesforce#SEO#site-reliability#technical-writing#telecoms
1 note
·
View note