#application security auditing
Explore tagged Tumblr posts
Text
Why Startups and Enterprises Alike Need Application Security Testing

In today’s digital-first world, applications have become the backbone of business operations—from customer-facing websites and mobile apps to back-end systems that drive logistics, payments, and communication. As organizations increasingly rely on software to deliver value, they also become more exposed to cyber threats.
Unfortunately, many businesses—especially startups—tend to deprioritize application security testing in favor of rapid development and feature delivery. Meanwhile, enterprises, despite having more mature processes, can fall victim to complacency or outdated testing strategies.
The truth is: whether you're a scrappy startup or a global enterprise, application security testing (AST) is not a luxury—it’s a necessity.
This article explores why application security testing matters for businesses of all sizes, the risks of neglecting it, and how it can be integrated into modern software development lifecycles to build safer, more resilient applications.
What Is Application Security Testing?
Application security testing is a procedure used to identify, assess, and address security vulnerabilities in software applications. It ensures that applications are designed, developed, and deployed with security in mind—protecting data, users, and the business itself.
There are several types of AST methods, including:
Static Application Security Testing (SAST): Analyzes source code before the app is run
Dynamic Application Security Testing (DAST): Tests the running application in a live environment
Interactive Application Security Testing (IAST): Combines elements of SAST and DAST
Software Composition Analysis (SCA): Identifies vulnerabilities in third-party libraries and open-source components
Penetration Testing: Simulates real-world attacks to find exploitable vulnerabilities
The goal? Find and fix security issues early—before attackers can exploit them.
Why Application Security Is Non-Negotiable
Applications are one of the most targeted attack surfaces for cybercriminals. According to industry reports, over 80% of data breaches are linked to application-layer vulnerabilities.
These can include:
SQL injections
Cross-site scripting (XSS)
Broken authentication
Insecure APIs
Unpatched open-source components
A single overlooked vulnerability can open the door to data theft, financial fraud, reputation damage, or even legal consequences under regulations like GDPR, HIPAA, or PCI-DSS.
Why Startups Need Application Security Testing
Startups, by nature, are focused on growth, speed, and innovation. But in the rush to launch MVPs, attract investors, or capture market share, security often takes a backseat.
1. Reputation Is Everything
For startups, credibility is fragile. One breach—especially in industries like fintech, healthcare, or eCommerce—can destroy user trust before the business even takes off.
Security testing helps startups demonstrate responsibility, gain customer confidence, and differentiate from competitors that neglect security.
2. Start Secure, Stay Secure
Building security into the foundation of your software (also known as “shifting left”) is far more cost-effective than fixing flaws later.
According to IBM, fixing a security flaw in production costs 6x to 15x more than resolving it during development. Thanks to AST, startups may integrate security early and minimize technical debt, hence preventing future rework.
3. Compliance from Day One
Many investors and enterprise customers now demand security and compliance as part of due diligence. Businesses that use application security testing are more equipped to handle:
ISO 27001 standards
GDPR or CCPA privacy requirements
Vendor security assessments
Penetration test requirements in B2B contracts
4. Defend Against Common Threats
Most startup applications are built using frameworks and open-source libraries. Without proper testing, startups are exposed to vulnerabilities like unpatched packages or misconfigured APIs.
Security testing tools like SCA can alert developers about these issues before hackers do.
Why Enterprises Also Need Application Security Testing
Large organizations often have mature IT ecosystems, but that doesn’t make them immune to breaches. Enterprises have more complexity, attack surfaces, and legacy code, making them frequent targets.
1. Volume and Scale Demand Automation
Enterprises often manage hundreds or thousands of applications across multiple business units. Manual testing isn’t scalable.
Application security testing, especially automated SAST and DAST tools, enables security to keep pace with rapid development cycles and global operations.
2. Legacy Systems and Technical Debt
Many enterprises still run on legacy code that was developed before modern security practices. These systems are frequently difficult to fix and might not have the most basic security.
Based on business risk, AST assists in identifying vulnerabilities in older codebases and prioritizing fixes.
3. Regulatory Compliance
Enterprises must comply with an array of standards, including:
PCI-DSS (for payment systems)
HIPAA (for healthcare data)
SOX (for financial transparency)
NIST and CIS (for cybersecurity best practices)
Application security testing helps ensure ongoing compliance, especially during audits and vendor risk assessments.
4. High-Profile Targets
The objective is more appealing the larger the organization. Cybercriminals, hacktivists, and even nation-state actors actively seek ways to exploit enterprise apps.
Regular testing—especially penetration testing and red teaming—helps stay one step ahead of attackers.
How to Integrate Application Security Testing into Development
1. Shift Left in the SDLC
Security should be part of the software development lifecycle (SDLC) from the start. Integrate tools like SAST into your CI/CD pipelines to catch issues as code is written.
2. Automate What You Can
Use automated testing tools to run regular scans on code, libraries, APIs, and live environments. These tools reduce testing time and help cover more ground.
Recommended tools include:
Snyk, SonarQube (SAST)
OWASP ZAP, Burp Suite (DAST)
Checkmarx, Veracode (enterprise-grade AST)
3. Conduct Regular Penetration Testing
Manual testing by ethical hackers can reveal business logic flaws, authentication weaknesses, and real-world exploits that automated tools might miss.
Do this quarterly or after major releases.
4. Train Your Developers
Security is a team effort. Equip your developers with knowledge about secure coding practices, OWASP Top 10, and how to remediate findings.
5. Monitor and Measure
Track metrics like:
Number of vulnerabilities found
Time to remediation
Severity levels
App coverage percentage
Use dashboards and reports to improve continuously.
Final Thoughts
Application security testing is no longer optional—it's a core business function. Whether you're launching your first app or managing thousands, you need to know your code is secure.
For startups, testing builds trust, ensures compliance, and sets the foundation for sustainable growth. For enterprises, it provides the scale, visibility, and protection needed to defend massive ecosystems.
The investment in application security testing today prevents far more expensive problems tomorrow. It's not just about checking boxes—it's about building software your users can trust and your business can rely on.
Are you doing enough to secure your applications?
Now’s the time to make application security testing part of your development strategy—no matter your size.
#application security auditing#app security audit#mobile application security audit#application security testing#application security review#web app security#web application security
0 notes
Text
Nick Kathmann, CISO/CIO at LogicGate – Interview Series
New Post has been published on https://thedigitalinsider.com/nick-kathmann-ciso-cio-at-logicgate-interview-series/
Nick Kathmann, CISO/CIO at LogicGate – Interview Series


Nicholas Kathmann is the Chief Information Security Officer (CISO) at LogicGate, where he leads the company’s information security program, oversees platform security innovations, and engages with customers on managing cybersecurity risk. With over two decades of experience in IT and 18+ years in cybersecurity, Kathmann has built and led security operations across small businesses and Fortune 100 enterprises.
LogicGate is a risk and compliance platform that helps organizations automate and scale their governance, risk, and compliance (GRC) programs. Through its flagship product, Risk Cloud®, LogicGate enables teams to identify, assess, and manage risk across the enterprise with customizable workflows, real-time insights, and integrations. The platform supports a wide range of use cases, including third-party risk, cybersecurity compliance, and internal audit management, helping companies build more agile and resilient risk strategies
You serve as both CISO and CIO at LogicGate — how do you see AI transforming the responsibilities of these roles in the next 2–3 years?
AI is already transforming both of these roles, but in the next 2-3 years, I think we’ll see a major rise in Agentic AI that has the power to reimagine how we deal with business processes on a day-to-day basis. Anything that would usually go to an IT help desk — like resetting passwords, installing applications, and more — can be handled by an AI agent. Another critical use case will be leveraging AI agents to handle tedious audit assessments, allowing CISOs and CIOs to prioritize more strategic requests.
With federal cyber layoffs and deregulation trends, how should enterprises approach AI deployment while maintaining a strong security posture?
While we’re seeing a deregulation trend in the U.S., regulations are actually strengthening in the EU. So, if you’re a multinational enterprise, anticipate having to comply with global regulatory requirements around responsible use of AI. For companies only operating in the U.S., I see there being a learning period in terms of AI adoption. I think it’s important for those enterprises to form strong AI governance policies and maintain some human oversight in the deployment process, making sure nothing is going rogue.
What are the biggest blind spots you see today when it comes to integrating AI into existing cybersecurity frameworks?
While there are a couple of areas I can think of, the most impactful blind spot would be where your data is located and where it’s traversing. The introduction of AI is only going to make oversight in that area more of a challenge. Vendors are enabling AI features in their products, but that data doesn’t always go directly to the AI model/vendor. That renders traditional security tools like DLP and web monitoring effectively blind.
You’ve said most AI governance strategies are “paper tigers.” What are the core ingredients of a governance framework that actually works?
When I say “paper tigers,” I’m referring specifically to governance strategies where only a small team knows the processes and standards, and they are not enforced or even understood throughout the organization. AI is very pervasive, meaning it impacts every group and every team. “One size fits all” strategies aren’t going to work. A finance team implementing AI features into its ERP is different from a product team implementing an AI feature in a specific product, and the list continues. The core ingredients of a strong governance framework vary, but IAPP, OWASP, NIST, and other advisory bodies have pretty good frameworks for determining what to evaluate. The hardest part is figuring out when the requirements apply to each use case.
How can companies avoid AI model drift and ensure responsible use over time without over-engineering their policies?
Drift and degradation is just part of using technology, but AI can significantly accelerate the process. But if the drift becomes too great, corrective measures will be needed. A comprehensive testing strategy that looks for and measures accuracy, bias, and other red flags is necessary over time. If companies want to avoid bias and drift, they need to start by ensuring they have the tools in place to identify and measure it.
What role should changelogs, limited policy updates, and real-time feedback loops play in maintaining agile AI governance?
While they play a role right now to reduce risk and liability to the provider, real-time feedback loops hamper the ability of customers and users to perform AI governance, especially if changes in communication mechanisms happen too frequently.
What concerns do you have around AI bias and discrimination in underwriting or credit scoring, particularly with “Buy Now, Pay Later” (BNPL) services?
Last year, I spoke to an AI/ML researcher at a large, multinational bank who had been experimenting with AI/LLMs across their risk models. The models, even when trained on large and accurate data sets, would make really surprising, unsupported decisions to either approve or deny underwriting. For example, if the words “great credit” were mentioned in a chat transcript or communications with customers, the models would, by default, deny the loan — regardless of whether the customer said it or the bank employee said it. If AI is going to be relied upon, banks need better oversight and accountability, and those “surprises” need to be minimized.
What’s your take on how we should audit or assess algorithms that make high-stakes decisions — and who should be held accountable?
This goes back to the comprehensive testing model, where it’s necessary to continuously test and benchmark the algorithm/models in as close to real time as possible. This can be difficult, as the model output may have desirable results that will need humans to identify outliers. As a banking example, a model that denies all loans flat out will have a great risk rating, since zero loans it underwrites will ever default. In that case, the organization that implements the model/algorithm should be responsible for the outcome of the model, just like they would be if humans were making the decision.
With more enterprises requiring cyber insurance, how are AI tools reshaping both the risk landscape and insurance underwriting itself?
AI tools are great at disseminating large amounts of data and finding patterns or trends. On the customer side, these tools will be instrumental in understanding the organization’s actual risk and managing that risk. On the underwriter’s side, those tools will be helpful in finding inconsistencies and organizations that are becoming immature over time.
How can companies leverage AI to proactively reduce cyber risk and negotiate better terms in today’s insurance market?
Today, the best way to leverage AI for reducing risk and negotiating better insurance terms is to filter out noise and distractions, helping you focus on the most important risks. If you reduce those risks in a comprehensive way, your cyber insurance rates should go down. It’s too easy to get overwhelmed with the sheer volume of risks. Don’t get bogged down trying to address every single issue when focusing on the most critical ones can have a much larger impact.
What are a few tactical steps you recommend for companies that want to implement AI responsibly — but don’t know where to start?
First, you need to understand what your use cases are and document the desired outcomes. Everyone wants to implement AI, but it’s important to think of your goals first and work backwards from there — something I think a lot of organizations struggle with today. Once you have a good understanding of your use cases, you can research the different AI frameworks and understand which of the applicable controls matter to your use cases and implementation. Strong AI governance is also business critical, for risk mitigation and efficiency since automation is only as useful as its data input. Organizations leveraging AI must do so responsibly, as partners and prospects are asking tough questions around AI sprawl and usage. Not knowing the answer can mean missing out on business deals, directly impacting the bottom line.
If you had to predict the biggest AI-related security risk five years from now, what would it be — and how can we prepare today?
My prediction is that as Agentic AI is built into more business processes and applications, attackers will engage in fraud and misuse to manipulate those agents into delivering malicious outcomes. We have already seen this with the manipulation of customer service agents, resulting in unauthorized deals and refunds. Threat actors used language tricks to bypass policies and interfere with the agent’s decision-making.
Thank you for the great interview, readers who wish to learn more should visit LogicGate.
#adoption#agent#Agentic AI#agents#agile#ai#AI adoption#ai agent#AI AGENTS#AI bias#ai governance#ai model#ai tools#AI/ML#algorithm#Algorithms#applications#approach#attackers#audit#automation#bank#banking#banks#benchmark#Bias#Business#challenge#chief information security officer#cio
0 notes
Text
The Ultimate Guide to Hiring a dApp Development Company for Blockchain Projects

Blockchain technology is transforming industries such as finance, healthcare, gaming, and supply chain management. At the core of this transformation are Decentralized Applications (DApps), which offer security, transparency, and efficiency. However, developing a successful DApp requires expertise, which is why hiring a dApp development company is essential.
If you are planning to build a blockchain-based DApp, choosing the right development partner is crucial. This guide covers everything you need to know about hiring the best DApp development company for your project.
What is a DApp?
A Decentralized Application (DApp) is a software application that runs on a blockchain or peer-to-peer network rather than a centralized server. Unlike traditional apps, DApps offer several advantages, including decentralization, transparency, security, and automation through smart contracts. These applications are widely used in industries like DeFi (Decentralized Finance), NFTs, gaming, healthcare, and supply chain management.
Why Hire a DApp Development Company?
A DApp development company provides expertise and efficiency, ensuring a seamless development process. The key benefits include:
Blockchain Expertise – Experienced developers in smart contracts, tokenomics, and security.
Cost and Time Efficiency – Reduces development costs and speeds up the launch process.
Custom DApp Solutions – Tailored applications based on business needs.
Security and Compliance – Ensures adherence to blockchain security standards.
Post-Launch Support – Provides maintenance, updates, and scalability improvements.
Key Factors to Consider When Hiring a DApp Development Company
1. Industry Experience and Portfolio
Check if the company has experience in DApp development and a strong portfolio of past projects. Look for expertise in industries such as DeFi, NFT marketplaces, and gaming. Also, ensure that they have worked with leading blockchain platforms like Ethereum, Solana, Binance Smart Chain, and Polygon.
2. Technical Expertise
A reliable DApp development company should have expertise in smart contract programming languages such as Solidity, Rust, and Vyper. They should also be experienced with blockchain frameworks like Ethereum, Hyperledger, and Polkadot. The ability to build cross-chain compatible DApps is an added advantage.
3. Development Process & Approach
A well-structured development process ensures quality and timely delivery. The company should provide:
A project roadmap outlining the entire development phase.
Agile development methodologies to allow flexibility.
Thorough testing and security audits before deployment.
A team proficient in Blockchain Software Development will follow best practices to ensure seamless smart contract execution, secure data management, and decentralized architecture.
4. Security Measures
Security is one of the most important aspects of DApp development. The company should conduct smart contract audits to eliminate vulnerabilities and ensure the application follows multi-layer security protocols. Implementing data encryption and authentication mechanisms is essential for user privacy.
5. Cost & Budget Transparency
The company should offer clear pricing models such as fixed cost, hourly rates, or milestone-based payments. Before signing any contract, ensure they provide a detailed cost breakdown to avoid hidden charges. While cost is important, always prioritize quality and security over the cheapest option.
6. Post-Launch Support & Maintenance
DApps require continuous updates, bug fixes, and performance optimizations. Ensure that the company offers technical support and scalability solutions to help your application grow over time.
7. Reviews & Client Testimonials
Check reviews on platforms like Clutch, GoodFirms, and Trustpilot to verify the company's reputation. You can also reach out to their past clients to get real feedback on their services.

DApp Development Process: How a Good Company Works
A DApp development company follows a structured development process to ensure high-quality results. Here is a step-by-step approach:
Requirement Analysis & Consultation – Define project goals, blockchain selection, and user requirements.
Smart Contract Development – Write, audit, and deploy secure smart contracts.
UI/UX Design – Develop an intuitive and user-friendly interface optimized for both web and mobile platforms.
DApp Development & Integration – Implement backend logic, blockchain features, and wallet connectivity.
Testing & Security Audits – Perform penetration testing, beta testing, and bug fixes.
Deployment & Launch – Deploy the DApp on the selected blockchain mainnet.
Post-Launch Maintenance – Provide continuous support, performance monitoring, and security updates.
Also Read: Best Blockchain Software Development Companies
Top Blockchain Platforms for DApp Development
A DApp development company should have expertise in various blockchain platforms. Some of the most widely used platforms include:
Ethereum – The most popular blockchain for smart contracts, widely used for DeFi applications, NFTs, and gaming.
Solana – Known for its high transaction speed and low fees, making it ideal for crypto exchanges and DeFi applications.
Binance Smart Chain (BSC) – A cost-effective, Ethereum-compatible blockchain suitable for token development and DApps.
Polygon – A scalable Ethereum-compatible solution used for DeFi, gaming, and NFT projects.
Hyperledger – A private blockchain network preferred for enterprise applications such as supply chain management and healthcare solutions.
Questions to Ask a DApp Development Company Before Hiring
Before finalizing a DApp development company, consider asking the following questions:
What blockchain platforms do you specialize in?
Can you showcase past DApp projects?
Do you conduct smart contract security audits?
What is your estimated development timeline?
How do you ensure security and data protection?
Do you provide post-launch support and updates?
What is your pricing model and payment structure?
Cost of Hiring a DApp Development Company
The cost of DApp development varies based on project complexity, features, and blockchain technology. Here’s a general estimate:
A basic DApp with simple smart contract functionality may cost between $10,000 and $30,000, with a development time of one to two months.
A medium complexity DApp with additional features such as multiple integrations, API connectivity, and enhanced security could cost between $30,000 and $100,000, taking anywhere from two to six months to develop.
An advanced DApp, such as a DeFi platform or NFT marketplace, can cost $100,000 or more, with development timelines exceeding six months.
Factors influencing costs include blockchain selection, security audits, UI/UX design, and integration complexity.
Conclusion
Hiring a DApp development company is a crucial step in building a successful blockchain-based application. Choosing a company with the right expertise, security measures, and post-launch support ensures that your DApp is scalable and future-proof.
If you are ready to launch your DApp, work with an experienced DApp development company that aligns with your business needs and blockchain goals.
#DApp development company#hire DApp developers#Blockchain app development#Decentralized application development#Smart contract development#Best DApp development services#Ethereum DApp development#Solana DApp development#Blockchain software development#DeFi app development#NFT marketplace development#Custom DApp solutions#Web3 development services#DApp security audit#Cost of DApp development
0 notes
Text
Protect Your Online Presence with SSL Solutions from Atcuality
Data security is a top concern for online businesses, and failing to secure your website can result in data breaches and loss of customer trust. Atcuality provides powerful security solutions to keep your website safe and protected. Our SSL installation services help encrypt data, prevent cyber attacks, and improve search engine rankings by ensuring your website complies with security best practices. Whether you need SSL for an eCommerce site, a corporate platform, or a personal blog, we offer quick and seamless installations for all types of SSL certificates. Our team takes care of the entire setup process, from domain validation to multi-domain SSL configuration. With Atcuality’s expertise, you can focus on growing your business while we handle your website’s security. Make security a priority and enhance your digital trust with Atcuality today.
#digital marketing#seo marketing#azure cloud services#seo agency#seo company#artificial intelligence#seo services#amazon web services#iot applications#ai powered application#seo#social media marketing#search engine optimization#seo expert#on page seo#on page optimization#on page audit#off page optimization#off page seo#local search engine optimization#local seo#ssl#sslcertificate#ssl certificates#wordpress#websitedevelopment#wordpress website#wordpress development#wordpress web design#wordpress security
1 note
·
View note
Text
Harden your Veeam Backup Server with Microsoft AppLocker
In this article, we shall be leveraging Zero Trust to harden the Veeam Backup Server with Microsoft AppLocker. Zero Trust principles include explicit verification, minimal privilege access, and assuming breach. Please see how to Configure Multiple IP Addresses on a Single or Multiple NICs, and “Demystifying Zero Trust with Veeam: Design your Architecture“. AppLocker enables System Administrators…
#Application Identity#AppLocker#AppLocker Enforced or Audited#AppLocker policy#AppLocker rules#backup server hardening#Configure Advanced AppLocker Rules#Configure AppLocker Rules#Defense in Depth#group policy#Group Policy Administrative Templates#Group Policy Object#Harden Veeam Backup Server#Local Group Policy#Local Security Policy#Microsoft AppLocker#Microsoft Windows#Software Restriction Policies#Veeam and AppLocker integration#Veeam Backup Server protection#Veeam Backup Server Security#Veeam configuration#Veeam security#Whitelisting tool#Windows#Windows 10#Windows 11#Windows Group Policy#Windows Server#Windows Server 2012
0 notes
Text
#Blockchain Consensus Mechanisms#Decentralised Application (DApp) Development#Smart Contract Development#Security Auditing#Scalability Solutions#Non-Fungible Tokens (NFTs)#Token Standards and Issuance
1 note
·
View note
Text
PICK A CARD: What sacrifices you’ll need to make
Hello and welcome to this new post of mine! I will give you a reading on what sacrifices you will need to make. I hope you guys enjoy and find this interesting.
Masterpost > Paid Readings

~pick a card~
Pile 1:
You will need to make some financial sacrifices soon. This might have to do with going to a higher level of education, some of you will have many birthdays coming up. For most of you this financial sacrifice won’t come as a surprise, and will be something you have been preparing for, for a while now. For many this will all be a heavy blow on your financial security, but it will be an investment, and you will get all of it and much more eventually.
The one’s who need to make a smaller financial sacrifice will be doing so out of kindness. For you, someone close to you will need some help; maybe you’ll have a few birthdays coming up, some other celebrations, or people near you will be in need for some financial blessings due to having come in a tight situation with money.
Pile 2:
You will be sacrificing a lot of time. There will be something great coming onto your path that will take a lot of focus and time. This sacrifice will be something you have been waiting for, but it will be more difficult and time-consuming than you will originally think. Once this opportunity arises make sure to grab it without a second-thought, go for it and chase it with all your might.
For some of you, this might be an application to something such as studies, a school, or a specific club you have been wanting to join. To others of you, you will be approached to do something you have always wanted to do. Think in the direction of being scouted as a model, being asked to audition for something etc. Something that you have been wanting to do or become but is usually really difficult. These opportunities will arise, but will need many sacrifices to actually accomplish.
Pile 3:
You will be sacrificing love in the next couple of months. This doesn’t mean you will lose your partner if you have one, nor does it automatically mean you’ll lose some of your friends and family. Of course, for a couple of you losing some people you love will be what is coming for you; but them leaving will be for the better, since you will find out they have done way more harm than you ever thought.
Some of you will also simply be keeping some distance with the people you love, this could be both physical and mental distance. Maybe you need to focus on something important the next couple of months, maybe you will be going on a vacation and due to that, leaving a couple of people behind in your home country or the city you live in. No matter what will be coming, some space will be created between you and a (or multiple) loved one(s).
#pick a card#pick a pile#pick an image#pick a photo#pick a picture#pac#pap#spirituality#spiritual#divination#tarot#tarot reading#tarot cards#tarot readings#tarot deck#tarotblr#tarotoftheday#tarotcommunity#channeling#channeled message#channeled reading#channeled messages#shadow work#wealth#loa#affirmations#shifting#sacrifices#spirit guides#love reading
611 notes
·
View notes
Text
I honestly don't know how to begin explaining how deeply worrisome the funding freeze is despite it being blocked in court.
Not much news is out there yet. Nobody seems to know what the fuck is happening. It's doing it's job, sowing chaos, fear, and despair.
Already, it's looking like a lot of critical agencies are going to be freezing operations (saw rumblings about possibly the EPA) until their shit can be audited to make sure it complies with this administration's efforts to start morally sanitizing things by first going after any program that supports trans people and reproductive rights.
They're literally bribing federal employees to quit -- saying that if federal employees leave their jobs before Feb. 6, they get 7 months' pay to do so. The loss of staff (and possible FIRING of staff after that date) and their inevitable replacement with people loyal to this administration is going to affect programs like SNAP and Social Security EVEN THOUGH they are exempt from the wider freeze. This is going to cause a lot of problems. This is going to make it easier to go after these programs in the future, by weakening them from within.
Don't give up.
Speak up, make calls, yes your voice matters in red states because PEOPLE THERE RELY HEAVILY ON FEDERALLY FUNDED PROGRAMS THAT HAVE NOT BEEN EXEMPTED.
Kids, the elderly, the disabled, the unhoused, the sick, NEED YOU to speak up. NOW.
Wanna help trans kids? Push back to make sure this doesn't get worse while you work to get that shit straightened out. They aren't going to be HELPED if their families can't get SNAP because the portal is down or there's no one to process applications, or their housing funding from a small org gets tied up, and they get evicted.
We can affect this. If your calls and protestations can help even ONE local program, like Meals on Wheels, stay secure, you have done something absolutely vital. And make no mistake, we are going to have a LOT of allies on the red side in this. That's why I think we can make a difference and slow things down. Which, yes, is still a victory. Make peace with that, hope for a massive change, be satisfied delaying their efforts.
Learned helplessness needs to go out the window. Take some time to get over the first reaction and get your feet under you. Then move.
#not rebloggable right now because i think if someone were to nitpick me i would commit murder#not sure how to turn off comments but notifications are off
92 notes
·
View notes
Text

The Department of Reproductive Compliance (DRC) stands at the forefront of safeguarding our nation's future, ensuring future generations' prosperity and survival. Through compassionate oversight and innovative reproductive programs, the DRC offers fertile men the opportunity to serve a higher purpose—bringing new life into the world for the benefit of all. With every pregnancy, these dedicated surrogates contribute to a brighter tomorrow, embracing their vital role in rebuilding our population. The DRC is committed to providing the utmost care, support, and guidance throughout this noble journey, fostering unity, strength, and hope for a thriving future. Together, we are creating life, one miracle at a time.
REPORTS ARCHIVE
External Affairs
Necessity for Immediate Draconian Measures
Legal Precedents in Surrogacy Enforcement
Barry the Belly
Re-Education Efforts in Rural Tennessee
State News Broadcast Transcript
Healthcare Services
Case Study: Surrogate S124-1437-L
Above Average Fetal Quotas
Paternity Compound Cost-Saving Efforts
Introduction of O-4 Visa Program
Cost of Conscripting Youth in Rural Communities
Increased Demand for Dermatological Supplies
Psychological Breakdowns in High-Fetal Load Surrogates
Planning & Evaluation
New Paternity Compound Construction
Enforcement of Surrogate Conscription
Surrogate Management Protocols
Operation Overdue
Surrogate Clothing Policy Review
Paternity Compound Recreation Activities
Research & Development
Impact of Prenatal Nymphomania
Termination of Medical Intervention Research
Identifiable Traits of Fertile Male Surrogates
Administration & Management
Internal Memo - All Staff
Disciplinary Action - Unauthorized Harem
Deputy-Directors’ Team Building Event
Rise in Compound Work Injury Claims
Large-Scale Canadian Surrogate Conscription
Restricted Access
Security
Black Ops
Operation R.I.P.E.
Operation W.O.M.B.
Massage Service for Covert Insemination
Food for Wombs
Conscription of Olympic Wrestling Team
Private Chat Log - Lt. Gen. [REDACTED]
Surrogate Recruitment via Social Media Application
Internal Affairs
Corruption and Abuse in Paternity Compounds
Director [REDACTED], Intelligence Profile
Comprehensive Review of the Ethics Training Program
Operational Justification of Surrogate Conscription
Internal Audit - Quota Breach
Internal Security
Uprising in Paternity Compound 112
Suspected Sabotage Activities
Suppression of “Whistleblower” Film
Analysis of Quarterly Surrogate Escape Attempts
#mpreg#mpreg kink#male pregnancy#mpreg belly#pregnant man#mpreg morph#mpreg caption#mpregbelly#mpregstory#mpreg birth#mpreg art#mpreg story#mpregnancy#ai mpreg#mpreg roleplay#male pregnant
93 notes
·
View notes
Text

ERC20 token generator
Ever wanted to create your own cryptocurrency? Thanks to the ERC20 Token Generator, it’s more accessible than ever. Dive into the world of blockchain and see how simple it can be.
What is an ERC20 Token?
ERC20 tokens are digital assets built on the Ethereum blockchain. They follow a specific standard, allowing them to interact seamlessly with platforms and other tokens.
Benefits of ERC20 Tokens:
Interoperability: All ERC20 tokens adhere to the same protocol.
Widespread Acceptance: Many platforms on Ethereum support these tokens.
Developer Support: Extensive documentation and community support.
How Does the ERC20 Token Generator Work?
Creating a token might sound complex, but the ERC20 Token Generator simplifies the process. Here’s a step-by-step guide:
Define Your Token:
Choose a name and symbol.
Set the total supply.
Access the Generator:
Use online tools designed for token creation.
Input your token details.
Deploy to the Blockchain:
Confirm your details.
Launch your token on the Ethereum network.
Key Features of ERC20 Tokens
These tokens offer various features that make them attractive for both developers and investors:
Standardized Functions: Such as balance checking and transfers.
Smart Contract Integration: Seamlessly integrate with smart contracts.
Security: Built on the robust Ethereum blockchain.
Why Create an ERC20 Token?
Creating your own token can offer several advantages:
Fundraising: Launch your own ICO (Initial Coin Offering).
Community Building: Reward loyal customers or followers.
Innovation: Develop new applications and uses for blockchain.
Potential Challenges
Despite the ease of creation, there are challenges:
Technical Knowledge: Basic understanding of blockchain is required.
Security Risks: Vulnerabilities can lead to exploitation.
Regulatory Issues: Compliance with local laws is crucial.
Best Practices for Creating ERC20 Tokens
To ensure success, follow these guidelines:
Audit Your Code: Ensure there are no security loopholes.
Engage with the Community: Gather feedback and make improvements.
Stay Informed: Keep up with blockchain trends and regulations.
Conclusion
The ERC20 Token Generator opens doors to the exciting world of cryptocurrency creation. Whether you're an entrepreneur, developer, or enthusiast, it offers an innovative way to engage with blockchain technology.
Final Thoughts
Creating an ERC20 token can be a game-changer. It empowers you to participate in the digital economy and experiment with new ideas.
FAQs
1. What is an ERC20 Token Generator?
An ERC20 Token Generator is a tool that simplifies the creation of custom tokens on the Ethereum blockchain.
2. Is technical knowledge necessary to create a token?
Basic blockchain understanding is helpful, but many generators offer user-friendly interfaces.
3. Can I sell my ERC20 tokens?
Yes, you can list them on cryptocurrency exchanges or sell directly to users.
4. Are there costs associated with creating a token?
Yes, deploying tokens on Ethereum requires gas fees, paid in Ether.
5. How do I ensure my token is secure?
Regular code audits and following best practices can enhance security.
Source : https://www.altcoinator.com/
#erc20#erc20 token development company#erc#erc20tokengenerator#token#token generator#token creation#ethereum#bitcoin
57 notes
·
View notes
Note
can you actually talk about bitwarden / password managers, or direct me to a post about them? Idk my (completely uneducated) instinct says that trusting one application with all your passwords is about as bad as having the same password for everything, but clearly that isn’t the case.
So it is true that online password managers present a big juicy target, and if you have very stringent security requirements you'd be better off with an offline password manager that is not exposed to attack.
However, for most people the alternative is "reusing the same password/closely related password patterns for everything", the risk that one random site gets compromised is much higher than the risk that a highly security focussed password provider gets compromised.
Which is not to say it can't happen, LastPass gets hacked alarmingly often, but most online password managers do their due diligence. I am more willing to stash my passwords with 1Password or Bitwarden or Dashlane than I am to go through the rigamarole of self-managing an array of unique passwords across multiple devices.
Bitwarden and other password managers try to store only an encrypted copy of your password vault, and they take steps to ensure you never ever send them your decryption key. When you want a password, you ask them for your vault, you decrypt it with your key, and now you have a local decrypted copy without ever sending your key to anyone. If you make changes, you make them locally and send back an encrypted updated vault.
As a result, someone who hacks Bitwarden should in the absolute worst case get a pile of encrypted vaults, but without each individuals' decryption key those vaults are useless. They'd still have to go around decrypting each vault one by one. Combining a good encryption algorithm, robust salting, and a decent key, you can easily get a vault to "taking the full lifetime of the universe" levels on security against modern cryptographic attacks.
Now there can be issues with this. Auto-fill can be attacked if you go onto a malicious website, poorly coded managers can leak information or accidentally include logging of passwords when they shouldn't, and obviously you don't know that 1Password isn't backdoored by the CIA/Mossad/Vatican. If these are concerns then you shouldn't trust online password managers, and you should use something where you remain in control of your vault and only ever manually handle your password.
Bitwarden is open source and fairly regularly audited, so you can be somewhat assured that they're not compromised. If you are worried about that, you can use something like KeePassXC/GNU Pass/Himitsu/ (which all hand you the vault file and it's your job to keep track of it and keep it safe) or use clever cryptographic methods (like instead of storing a password you use a secret key to encrypt and hash a reproducible code and use that as your password, e.g. my netflix password could be hash(crypt("netflixkalium", MySecretKey)), I know a few people who use that method.
Now with any luck because Apple is pushing for passkeys (which is just a nice name for a family of cryptographic verification systems that includes FIDO2/Webauthn) we can slowly move away from the nightmare that is passwords altogether with some kind of user friendly public key based verification, but it'll be a few years before that takes off. Seriously the real issue with a password is that with normal implementations every time you want to use it you have to send your ultra secret password over the internet to the verifying party.
244 notes
·
View notes
Text

Application Security Auditing & Testing | App Security Audit Review
Secure your mobile and web apps with professional application security audits. Comprehensive security testing and reviews to protect your applications from vulnerabilities.
#application security auditing#app security audit#mobile application security audit#application security testing#application security review#web app security#web application security
0 notes
Text
Masterlist of Free PDF Versions of Textbooks Used in Undergrad SNHU Courses in 2025 C-1 (Jan - Mar)
Literally NONE of the Accounting books are available on libgen, they all have isbns that start with the same numbers, so I think they're made for the school or something. The single Advertising course also didn't have a PDF available.
This list could also be helpful if you just want to learn stuff
NOTE: I only included textbooks that have access codes if it was stated that you won't need the access code ANYWAY
ATH (anthropology)
only one course has an available pdf ATH-205 - In The Beginning: An Introduction to Archaeology
BIO (Biology)
BIO-205 Publication Manual of the American Psychological Association Essentials of Human Anatomy & Physiology 13th Edition
NOTE: These are not the only textbook you need for this class, I couldn't get the other one
CHE (IDK what this is)
CHE-329
The Aging Networks: A Guide to Policy, Programs, and Services
Publication Manual Of The American Psychological Association
CHE-460
Health Communication: Strategies and Skills for a New Era
Publication Manual Of The American Psychological Association
CJ (Criminal Justice)
CJ-303
The Wisdom of Psychopaths: What Saints, Spies, and Serial Killers Can Teach Us About Success
Without Conscious: The Disturbing World of the Psychopaths Among Us
CJ-308
Cybercrime Investigations: a Comprehensive Resource for Everyone
CJ-315
Victimology and Victim Assistance: Advocacy, Intervention, and Restoration
CJ-331
Community and Problem-Oriented Policing: Effectively Addressing Crime and Disorder
CJ-350
Deception Counterdeception and Counterintelligence
NOTE: This is not the only textbook you need for this class, I couldn't find the other one
CJ-405Private Security Today
CJ-408
Strategic Security Management-A Risk Assessment Guide for Decision Makers, Second Edition
COM (Communications)
COM-230
Graphic Design Solutions
COM-325McGraw-Hill's Proofreading Handbook
NOTE: This is not the only book you need for this course, I couldn't find the other one
COM-329
Media Now: Understanding Media, Culture, and Technology
COM-330The Only Business Writing Book You’ll Ever Need
NOTE: This is not the only book you need for this course, I couldn't find the other one
CS (Computer Science)
CS-319Interaction Design
CYB (Cyber Security)
CYB-200Fundamentals of Information Systems Security
CYB-240
Internet and Web Application Security
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-260Legal and Privacy Issues in Information Security
CYB-310
Hands-On Ethical Hacking and Network Defense (MindTap Course List)
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-400
Auditing IT Infrastructures for Compliance
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-420CISSP Official Study Guide
DAT (IDK what this is, but I think it's computer stuff)
DAT-430
Dashboard book
ECO (Economics)
ECO-322
International Economics
ENG (English)
ENG-226 (I'm taking this class rn, highly recommend. The book is good for any writer)
The Bloomsbury Introduction to Creative Writing: Second Edition
ENG-328
Ordinary genius: a guide for the poet within
ENG-329 (I took this course last term. The book I couldn't find is really not necessary, and is in general a bad book. Very ablest. You will, however, need the book I did find, and I recommend it even for people not taking the class. Lots of good short stories.)
100 years of the best American short stories
ENG-341You can't make this stuff up : the complete guide to writing creative nonfiction--from memoir to literary journalism and everything in between
ENG-347
Save The Cat! The Last Book on Screenwriting You'll Ever Need
NOTE: This i snot the only book you need for this course, I couldn't find the other one
ENG-350
Linguistics for Everyone: An Introduction
ENG-351Tell It Slant: Creating, Refining, and Publishing Creative Nonfiction
ENG-359 Crafting Novels & Short Stories: Everything You Need to Know to Write Great Fiction
ENV (Environmental Science)
ENV-101
Essential Environment 6th Edition The Science Behind the Stories
ENV-220
Fieldwork Ready: An introductory Guide to Field Research for Agriculture, Environment, and Soil Scientists
NOTE: You will also need lab stuff
ENV-250
A Pocket Style Manual 9th Edition
ENV-319
The Environmental Case: Translating Values Into Policy
Salzman and Thompson's Environmental Law and Policy
FAS (Fine Arts)
FAS-235Adobe Photoshop Lightroom Classic Classroom in a Book (2023 Release)
FAS-342 History of Modern Art
ALRIGHTY I'm tired, I will probably add ore later though! Good luck!
25 notes
·
View notes
Text
Today's watch:
Renata Shakirova interview as she prepares for The Little Humpbacked Horse, Mariinsky, 2021
youtube
I've translated some parts, but not everything. Interview with Renata Shakirova
Interviewer: Hello, guys! I’m here today with Renata Shakirova in her personal dressing room. Tonight, she’ll be performing the role of the Tsar Maiden in the ballet Little Humpbacked Horse. Hi, Renata!
Renata: Hi, everyone!
Interviewer: In today’s episode, we’ll show you how a first soloist prepares for a performance and what goes on both before and after the show.
Preparations
Interviewer: Renata, what are we doing?
Renata: Is it possible for the braid to start lower?
Hair Stylist: Of course!
Renata: Thank you!
Interviewer: Renata, why do you have two crowns?
Renata: So I could choose which one I like better. You’ll help me decide. This one or the smaller one?
Interviewer: The smaller one.
Renata: The decision is made! This is my costume for today—it’s very petite and beautiful.
Braiding Hair:
Adding extension hair
Renata: Back in the Academy, I constantly braided girls’ hair. I managed to do half of it nicely.
Interviewer: Did you pull girls’ braids?
Renata: Once or twice… did you?
Renata hands hairpins to speed up the process.
Foundation Application: Interviewer: What did you just apply? Renata: Foundation! (Securing the crown.)
The Interview
Interviewer: Stop laughing! This is a serious interview. Renata: The most serious one. Interviewer: Renata, I have a few questions for you. Are you ready? Renata: I’m ready! Interviewer: Tell us about yourself. Where are you from? Renata: I was born in Tashkent, Uzbekistan. When I was four, my family moved to Bashkortostan. Since I was about five years old, I lived in Sterlitamak. Interviewer: Dance company “Solnyshko” says hi. Renata: Thank you! Hi to them, too! Interviewer: Was “Solnyshko” your first dance company? Renata: My first and last, so to speak. All my childhood memories are from there. We attended different festivals, visited cities like Samara and Saratov, and it was amazing. Interviewer: How many years did you dance there? Renata: Until I was 11, when I got into the Academy. Teachers recommended auditioning since they thought I had potential. I loved dancing and being on stage as a child.
A Funny Childhood Memory Renata: Once, at a festival, my dance number began with me standing alone on stage. A pre-recorded track was supposed to play, but it never did. I was embarrassed, my heart was in my throat. I just stood there until the end, waiting for the track. Everyone started laughing, and I had no idea what to do. It was a good exercise in resilience.
About Stage Makeup Interviewer: You do your own stage makeup? Renata: Yes, it’s easy for you boys since everything is done for you. We do everything ourselves. I even took professional stage makeup courses because my makeup would wear off during applause. Interviewer: So this is professional stage makeup? Renata: Yes. Interviewer: You have so many brushes. Renata: That’s only half of them. Interviewer: Do you really need so many? Renata: I personally do. Interviewer: I’d only use three. Renata: I’m a girl. Interviewer: I’m always amazed how girls do their makeup. They use so many brushes and products, but it all looks the same until suddenly, it’s done. Renata: Slowly, a face appears. It’s funny because when I leave the theater, no one recognizes me. It’s happened multiple times.
What Motivates You? Interviewer: What motivates you to get up every morning, do ballet, and perform? Renata: Honestly, I’m lazy, but if I’m unprepared, the performance won’t go well. Videos of a bad performance are painful to watch. I can’t always watch my own videos, but it keeps me motivated to improve.
Ballet Nightmares Interviewer: Do you have any ballet-related nightmares? Renata: The biggest one is being on stage and forgetting the choreography. Interviewer: I’ve also dreamed about sliding down a tilted stage with the audience laughing. Have you had that nightmare? Renata: No. Interviewer: Now you will! Renata: In Italy, the stage is so tilted, it’s like my nightmare coming true.
Falling on Stage Interviewer: Have you fallen on stage? Renata: Too many times. Initially, it felt catastrophic. But other ballerinas comforted me by sharing their own funny falling stories. Everyone falls eventually.
Soloist vs Corps de Ballet Interviewer: Which is harder: being a soloist or in the corps de ballet? Renata: Corps de ballet is harder because you must keep the formation perfect. As a soloist, any mistakes are solely on you, but there’s no one else to blame.
Stretching and Flexibility Interviewer: You stretch a lot. Why do you continue to stretch so much? Renata: It helps keep my muscles elastic. Stretching improves range of motion and prevents injuries. I tell my students to stretch so they don’t face the same issues I did.
Your Goal Interviewer: What is your main goal? Renata: I have a box for all my roles. My dream is to keep adding to it with exciting new roles.
Favorite Role Interviewer: What’s your favorite role to perform? Renata: I enjoy all roles, but Juliet in Romeo and Juliet stands out. The story, the character’s emotional journey, and the three acts make it unique.
Pre-Performance Ritual Interviewer: Any special pre-performance rituals? Renata: I don’t have anything special. Before emotional roles, I hold back my emotions during rehearsals to save them for the stage. Nervousness is natural and helps keep me sharp.
Post-Performance Relaxation Interviewer: How do you unwind after performances? Renata: I’d love to rest more often, but it doesn’t always happen. I use compression pants and a vibrating massager. I also enjoy taking baths, visiting the spa, and eating delicious food.
Talent vs Hard Work Interviewer: In your opinion, how much is talent versus hard work? Renata: Talent is important, but hard work is 90% of the equation. Even if you have talent, you won’t succeed without effort.
Advice to Aspiring Ballerinas Renata: Work hard, listen to your teachers, and embrace healthy competition. Competition in the studio can push you to improve, but outside of class, it’s important to maintain friendships and support each other.
#ballet#elegantballetalk#elegantballettalk#russian ballet#vaganova method#vaganova#vaganova academy#mariinsky theatre#vaganova ballet academy#mariinsky#The Little Humpbacked Horse#mariinsky The Little Humpbacked Horse#mariinsky ballet#renata shakirova#Youtube
17 notes
·
View notes
Text
Demystifying cloud computing: the future of technology.

In today's rapidly evolving digital world, cloud computing is not just a technology trend-cloud computing is the foundation of today's IT infrastructure. from streaming your favourite Netflix show to collaborating on Google Docs.
what is cloud computing?

Cloud computing is the provision of computing services including the servers, databases, storage, networking, software, analytics, and intelligence over the internet to offer faster innovation, flexible resources, and economies of scale.
Types of cloud services.
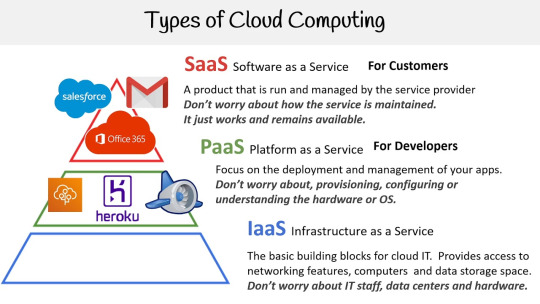
Security in the cloud.
Security is the top priority. cloud vendors employ encryption, firewalls, multi-factor authentication, and periodic audits to secure data. Organizations must, however, set up and manage secure access.
The future of cloud computing.

The future of cloud computing is being defined by a number of ground breaking trends that are changing the way data and applications are processed. Edge computing is moving computation near data sources to decrease latency and improve real-time processing for IoT and mobile applications.
7 notes
·
View notes
Text
1. “Immediately reissue my 2020 executive order, restoring the President's authority to remove rogue bureaucrats.”
2. “Clean out all of the corrupt actors in our national security and intelligence apparatus.”
3. “Totally reform FISA courts which are so corrupt that the judges seemingly do not care when they're lied to in warrant applications.”
4. “Expose the hoaxes and abuses of power that have been tearing our country apart.”
5. “Launch a major crackdown on government leakers who collude with the fake news to deliberately we false narratives and to subvert our government and our democracy.”
6. “Make every Inspector General's office independent and physically separated from the departments they oversee so they do not become the protectors of the deep state.”
7. “Ask Congress to establish an independent auditing system to continually monitor our intelligence agencies to ensure they are not spying on our citizens or running disinformation campaigns against the American people, or that they are not spying on someone's campaign like they spied on my campaign.”
8. “Continue the effort launched by the Trump administration to move parts of the sprawling federal bureaucracy to new locations outside the Washington Swamp.”
9. “Work to ban federal bureaucrats from taking jobs at the companies they deal with and that they regulate.” 10. “Push a constitutional amendment to oppose term limits on members of Congress.”
7 notes
·
View notes