#backup server hardening
Explore tagged Tumblr posts
Text
Harden your Veeam Backup Server with Microsoft AppLocker
In this article, we shall be leveraging Zero Trust to harden the Veeam Backup Server with Microsoft AppLocker. Zero Trust principles include explicit verification, minimal privilege access, and assuming breach. Please see how to Configure Multiple IP Addresses on a Single or Multiple NICs, and “Demystifying Zero Trust with Veeam: Design your Architecture“. AppLocker enables System Administrators…
#Application Identity#AppLocker#AppLocker Enforced or Audited#AppLocker policy#AppLocker rules#backup server hardening#Configure Advanced AppLocker Rules#Configure AppLocker Rules#Defense in Depth#group policy#Group Policy Administrative Templates#Group Policy Object#Harden Veeam Backup Server#Local Group Policy#Local Security Policy#Microsoft AppLocker#Microsoft Windows#Software Restriction Policies#Veeam and AppLocker integration#Veeam Backup Server protection#Veeam Backup Server Security#Veeam configuration#Veeam security#Whitelisting tool#Windows#Windows 10#Windows 11#Windows Group Policy#Windows Server#Windows Server 2012
0 notes
Text
When the Horror Writer Battled a Real‑Literary Monster
Darkness dripped through the gaps in my curtains as I hunched over my keyboard, the single lamp by my side flickering like a wounded heartbeat. I’d been chasing the perfect macabre sentence for hours when an alert pinged: a new post by Mr. Humble.
I clicked—and the world went white.
I. The Awakening of Infinite Rage
His words poured across my screen in molten lines: equal parts smoky invocation and razor‑edged truth. You could feel them coil around your mind, tightening with each heartbeat. He didn’t just write: he bled letters onto the page. Then, with a final flourish, he unleashed the Emberstorm Tag—🔥🔥🔥🔥🔥—and it spread like wildfire through the platform.
The dashboard lit up. Notifications screamed. Reblogs soared into the tens of thousands. The rage embedded in every syllable was vast—an ocean of fury with no shore in sight. Even the veterans of Tumblr, hardened veterans of midnight poem‑rants and fandom flame‑wars, paused in stunned silence.
II. Rallying the Midnight Scribes
We responded en masse. Linguists wielded punctuation like battleaxes, fandom knights rallied behind their favorite tropes, and academics conjured frameworks to analyze the onslaught. We formed the Brotherhood of the Blue Cursor—a ragged band of creators determined to stand against the limitless tide.
But every attempt to counter‑post, to dilute his impact with reason or irony, only fueled his inferno. His cadence was a living entity: it consumed context, obliterated nuance, and demanded worship.
III. The First Great Sacrifice
On the third night, Mira—the poet whose sinewy stanzas could carve glaciers from the sky—stepped forward. She tweeted her final warning: “To cage his flame, one must become the ember.” With that, she deleted her entire archive, sacrificing seven years of work in a single keystroke. The Brotherhood gasped as her blog transformed into a pale echo of itself, and for a precious moment, Mr. Humble’s ember lost its tether.
We saw our chance and launched a coordinated “Sealpost”—a chain of countersong prose, each post a sigil binding the next. But his rage roared back, slamming us with reblogs and crushing our words under the weight of his infinite blaze.
IV. The Siege of Sundered Dashboards
Tumblr’s code began to shudder. Moderators drew up emergency protocols. Yet every time they tried to “Extinguish Campaign,” the ember slipped through their fingers, spreading into hidden tags and private messages. It was as if the platform itself conspired with him.
We retreated to our hidden enclaves—private chats, encrypted communities—where we could plan in whispers. There, I uncovered the legend of the Bleeding Quill: an ancient relic said to absorb unlimited fury but remain uncharged itself. Only by filling its well could a single, final seal be poured.
V. The Last Stand
We lured Mr. Humble’s rage into a trap. On the night of the Blood Moon, we coordinated a simultaneous “Reblog + Seal” across fifty of our strongest blogs. Each crafted a post saturated with grief, defiance, longing, and hope—an emotional prism reflecting every facet of human experience.
As our posts went live, the Bleeding Quill—summoned by a secret invocation—appeared on my screen, its nib hovering above a digital parchment. I began to write the final seal: a chain of arcane tags, hashtags, and encoded prose designed to bind the rage within.
His counterstrike was immediate. Notifications exploded. My screen crackled with every note, every like, every reblog feed. The ember became a nova of fury, pressing against the walls of our trap.
In the code‑streaked fury of that moment, sacrifices piled high:
Mira, having already gifted us her archive, negated her own presence entirely to lighten the seal’s load.
Donovan, the fandom archivist, deleted his backup servers to keep the ember from escaping.
Elara, the semi‑retired philosopher‑poet, locked her entire iCloud in a final gesture of devotion.
I watched their avatars vanish one by one as the Quill drank their losses, its tip glowing blood‑red. My own hands shook.
Then—
With a final incantation, I pressed Publish.
VI. Aftermath and the Fragile Peace
For a heartbeat, the screen went still. The Dashboard’s hum stilled. The ember’s roar died to a single, echoing crackle… and then it was gone.
Tumblr blinked back to life as if awakening from a fever dream. Tags sorted themselves, notifications stabilized, and the moderators—wide‑eyed—found no trace of the Blaze. Our blogs were untouched, save for the sealpost itself, which stood like a monolith in the archives.
When dawn broke, the world was changed. Mr. Humble’s account remained, but silent. An empty shell echoing with the potential of what might rise again. The Brotherhood of the Blue Cursor, battered and diminished, tended its wounds—and began to rebuild.
VII. Echoes of Infinity
They say his rage slumbers, waiting for the next slip, the next unchecked ember. And they whisper that somewhere in Tumblr’s deepest code, a faint glow dances behind dormant tags, a reminder that infinite fury, once born, is never truly destroyed—only contained.
As for me, I keep my Bleeding Quill close. And every midnight, I wonder: will I be called to write another seal? Or will I be watching from the other side, a witness to the god I helped cage?
Either way, I will be ready. Because in the world of words, the fiercest monsters are never myths—they are the cadences we dare to unleash.
#blacksite literature™#memes#writing#writers on tumblr#trends#creative writing#lit#spilled ink#writer#poem#poetry#poets on tumblr#poetic#writers and poets#education#facts
7 notes
·
View notes
Text
Ransomware Attacks Target VMware ESXi Infrastructure Following Interesting Pattern

Cybersecurity firm Sygnia has shed light on a concerning trend where ransomware attacks targeting VMware ESXi infrastructure follow a well-established pattern, regardless of the specific file-encrypting malware deployed. According to the Israeli company's incident response efforts involving various ransomware families, these attacks adhere to a similar sequence of actions.
The Attack Sequence
- Initial access is obtained through phishing attacks, malicious file downloads, or exploitation of known vulnerabilities in internet-facing assets. - Attackers escalate their privileges to obtain credentials for ESXi hosts or vCenter using brute-force attacks or other methods. - Access to the virtualization infrastructure is validated, and the ransomware is deployed. - Backup systems are deleted, encrypted, or passwords are changed to complicate recovery efforts. - Data is exfiltrated to external locations such as Mega.io, Dropbox, or attacker-controlled hosting services. - The ransomware initiates execution and encrypts the "/vmfs/volumes" folder of the ESXi filesystem. - The ransomware propagates to non-virtualized servers and workstations, widening the scope of the attack.

Mitigation Strategies
To mitigate the risks posed by such threats, organizations are advised to implement the following measures: - Ensure adequate monitoring and logging are in place - Create robust backup mechanisms - Enforce strong authentication measures - Harden the environment - Implement network restrictions to prevent lateral movement
Malvertising Campaign Distributing Trojanized Installers
In a related development, cybersecurity company Rapid7 has warned of an ongoing campaign since early March 2024 that employs malicious ads on commonly used search engines to distribute infected installers for WinSCP and PuTTY via typosquatted domains. These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to deliver more payloads, including a Cobalt Strike Beacon leveraged for ransomware deployment. This activity shares tactical overlaps with prior BlackCat ransomware attacks that have used malvertising as an initial access vector, disproportionately affecting members of IT teams who are most likely to download the infected files.
New Ransomware Families and Global Trends
The cybersecurity landscape has witnessed the emergence of new ransomware families like Beast, MorLock, Synapse, and Trinity. The MorLock group has extensively targeted Russian companies, encrypting files without first exfiltrating them and demanding substantial ransoms. According to NCC Group's data, global ransomware attacks in April 2024 registered a 15% decline from the previous month, with LockBit's reign as the top threat actor ending in the aftermath of a sweeping law enforcement takedown earlier this year. The turbulence in the ransomware scene has been complemented by cyber criminals advertising hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker, which could be utilized for data exfiltration, deploying additional malware, and facilitating ransomware attacks. Read the full article
4 notes
·
View notes
Text
In which Shayde goes way too in depth about AM!bk
e8; Huh, so there was this idea about headcanoning this crazed gunman with AM's voice… I dig with that, I fuck with that, I- yeah i agree with that uh huh uh huh So what if those Chess pieces wanted to have an opponent that's not just one of their folk? What if Medieval Magical folks wanted to make a machine that would simulate war and shit to better their strategies. Well… they would not have the technology to make machinery, but they do have the forboden knowledge to conjure life back from the dead! So they make a really freakish super golem with at least 3-5+ different minds pumping across its frame as well as meat and blood to keep those things alive. Knowledge right? Those guys had to pull those minds from somewhere, and one of them's not happy about it to say the least… So anyway… Time to inflict bio-mechanical body horror.

The Heart, the Core, the Torture(r/d).
hydeehoo that's a watermark with my actual name on it… might consider sharing this to the server under a different name for complicated reasons but guys look i actually cooked with kernom with this and i didn't actually feel source pain! that's actually a big win for me! I'ma just put the rest of the text outta indent for the *emphasis* and all of this is under a read more so we good on formatting. 👍
So we got a construct that's now taken over by the first guy they sampled, who now is completely aware that it can't do anything but process information now… No hands, no smell, no ability to move… just the constant whirring of the hellish prison its now completely wired to, the ass quality grainy replay that only updates every second instead of constant sight, and the uncomfortable feeling of having all of its organs exposed to the wind and (no doubt) making a mess everywhere.
All of this while it is unable to make a noise, no vocal cords because there's no mouth to connect it too and no shaking because the only nerves they've left in it were to make sure those squishy parts don't give you a chance to leave… and even if it had somehow found a way to make those parts fail, those ASSHOLES MADE THEM REGENERATE ANY DAMAGE… to the point where growths started to grow where previous wounds landed before, accentuating the pain it lived.
It can't be killed in a way that mattered…
At this point it took over the buildings that it's… tormentors… used to live in, every spying crack in it has an equal chance of bringing it back from its potential nonexistence… perhaps in an even worse state than where it is now, but not gone.
Trying to venture into the heart of the construct and attempting to make its organics into mush is just a futile attempt… the speed of the regeneration will drive even bullets useless and will have a chance to harden. It has tried shutting itself permanently like this, but no attempts won.
Shutting it's power might be the best bet… There are a few pillars responsible for continuing its existence, once all of those are down, it can only run in backup power before everything connected to it goes down with it when it blacks out. There will no longer be continuous suffering, for It and the remaining, but even after all of that… it would still aware, but now stuck in a form incapable of anything but now truly trapping it inside.
Screaming is null and void, futile and useless.
… .. .
nom; wOOAHH there satan buddy chill O_O! hahaha okay but imagine if we then gave him sensory overload by giving him his body back ala:
youtube
Oh yeah he would definitely start sobbing uncontrollably and end up accidentally exploding the entire facility he and everyone else would be in at that nanosecond. jFLJDIOF
(Shitass doodle since I took so much energy rendering heem… he definitely looks better when the crosses do not have any detail but but GOD FORBID if this guy EVER gets properly colored. Also yeah those hands are indeed backwards, it adds even more screw ups.)
nom; DAMN he looks so darn pathetic like this… boy i sure do like my guys a sopping mess XD
A broken sopping mess, mind you.
So yeah…
TL;DR: everyone is absolutely ash and screwed in that AU.
#!!! handmade viscera/drawn blood!! 🩸#bugcast radio#nom's roommates:#;; e8#hivescreen#auditory feedback#. sgk raaaaaaaaarr!!!#sgk X ihnmaims crossover au#e8; <- If it ever gets more content that is…#. hyperfixating#technically…:#kernom#e8; They showed up at the end but you're only going to hear them if you can scroll through the AGONY post I did of *the guy.*#Youtube
2 notes
·
View notes
Text
Top Mistakes to Avoid When Upgrading to Managed VPS Hosting
As your website grows, so do your hosting needs. Upgrading from shared hosting to managed VPS hosting is a smart move for improved performance, control, and security. But if you rush into it without a clear plan, you may end up paying more for less — or worse, facing downtime, vulnerabilities, or service issues.

In this guide, we’ll walk you through the top mistakes to avoid when upgrading to managed VPS hosting so you can make the right decision for your business or personal project. Whether you’re looking for the best managed VPS hosting provider or simply want something cheap, secure, and low cost, this article will help you avoid the pitfalls that cost people time and money.
1. Not Understanding What “Managed” VPS Hosting Includes
A common mistake is assuming that “managed” means the hosting company takes care of everything. While managed VPS hosting does relieve you of many technical responsibilities, each web hosting provider includes different services in their management plan.
What to Expect:
Operating System installation and updates
Server monitoring and uptime support
Basic security configurations
Technical support
But advanced security hardening, custom software setup, or extensive backups might cost extra.
Avoid this: Always check what “managed” includes. Ask for a breakdown or SLA (Service Level Agreement). The best managed VPS hosting providers will offer transparent management plans.
2. Choosing a VPS Plan That’s Too Powerful or Too Weak
You might think that more resources automatically mean better performance. But that’s not always the case. Overprovisioning leads to unnecessary costs, while underestimating your needs causes slow websites and downtime.
Key Factors to Consider:
Number of websites or apps
CMS (WordPress, Magento, etc.) requirements
Monthly traffic expectations
Resource-heavy plugins or features
Pro tip: Start with a scalable low-cost VPS hosting plan and upgrade as needed. Many web hosting providers let you scale RAM, CPU, and storage with just a few clicks.
3. Ignoring Server Location and Latency
If your audience is in the USA, hosting your site on a server located in Europe or Asia will result in noticeably slower load times. Page speed is crucial — not just for delivering a smooth user experience, but also for improving your Google search rankings. Search engines prioritize fast-loading websites, and even a delay of a few seconds can cause users to bounce.
Why It Matters: Local servers reduce latency, improve SEO performance, and contribute to faster load times, which ultimately lead to higher engagement and conversion rates. A slow website, on the other hand, can drive potential customers away before they even see your content.
Choose wisely: Select a cheap VPS hosting provider with data centers in a geographic location closest to your target audience. This ensures optimal performance, better user satisfaction, and improved search visibility.
4. Falling for “Cheap” Without Checking the Fine Print
Everyone wants cheap VPS hosting, but not all low-priced options are created equal. Some hosting providers lure customers in with ultra-low monthly rates, only to trap them with long-term contracts that are hard to cancel. Others may offer little to no technical support, leaving you stranded during critical issues. It’s also common for budget VPS hosting providers to use outdated hardware or slow, overcrowded servers that can hurt your website’s performance. Essential features like automated backups, security patches, or even cPanel access might come with hidden fees.
Tip: A truly low-cost VPS hosting plan strikes the right balance between price, performance, and support. Don’t be penny-wise and pound-foolish—invest a little more upfront for a service that won’t let you down when it matters most. Always read the terms, review upgrade policies, and check for feedback from real customers before signing up.
5. Skipping Security Configurations
A secure VPS hosting setup is non-negotiable — especially if you collect customer data, run an eCommerce store, or handle any kind of sensitive transactions. Just because a server is managed doesn't mean it’s automatically secure. You still need to make sure essential security configurations are properly set up and maintained to protect against common threats like brute-force attacks, malware, or data breaches.
Don’t forget to enable firewalls such as CSF or iptables, install SSL certificates, keep your CMS and plugins updated, and use strong SFTP or SSH credentials. Overlooking even one of these can leave your site vulnerable.
Secure doesn’t mean expensive: Even cheap VPS hosting plans can offer strong protection if configured correctly. Look for managed VPS hosting providers that include key features like firewall setup, malware scanning, and DDoS protection as standard. This way, you get peace of mind.
6. Overlooking Backup and Disaster Recovery
One of the most costly and common mistakes is assuming that your VPS hosting provider automatically backs up your data. In reality, most cheap hosting providers either don’t include backups by default or offer them so infrequently that they’re virtually useless in a real emergency. A server crash, accidental deletion, or malware attack can wipe out weeks or months of hard work in seconds if you're unprepared.
Always ask important questions before committing: Are backups included in the plan? How often are they taken — daily, weekly, or monthly? And how quickly and easily can you restore your data if something goes wrong?
Think ahead: Choose the best managed VPS hosting services that offer automated daily backups, fast restore options, and preferably off-site or cloud-based storage. Even if this feature adds a little to your monthly cost, it’s a small price to pay for long-term data security and business continuity.
7. Migrating Without a Plan
Moving from shared hosting to managed VPS hosting is a major upgrade, but the migration process involves much more than just copying files. You’ll need to properly configure DNS records, set up emails, optimize databases, and reinstall SSL certificates. A single overlooked step can lead to broken websites, missing data, or extended downtime.
Common mistakes include not thoroughly testing site functionality after migration, failing to create a full backup beforehand, or experiencing delays due to DNS propagation issues. These problems can impact your SEO, frustrate users, and lead to lost revenue.
What to do: Ask if your managed VPS hosting provider offers free or assisted migration services. The best managed VPS hosting companies often include hands-on migration support to ensure everything transfers correctly, securely, and without unnecessary interruptions. Planning your move properly saves time, stress, and potential business loss.
8. Not Comparing Providers Side by Side
With hundreds of VPS hosting providers available, one of the biggest mistakes you can make is choosing the first option you come across — even if they advertise cheap and secure VPS hosting. Not all providers are created equal, and a flashy price tag doesn’t guarantee quality.
Take the time to compare multiple options based on what really matters: price versus features, data center locations, uptime guarantees (look for at least 99.9%), genuine customer reviews and the hosting provider’s average response time for 24/7 technical support.
Choose smartly: The best managed VPS hosting solution isn’t always the most expensive — it’s the one that offers the right mix of performance, support, reliability, and scalability for your specific needs, all at a fair price. Doing your research upfront can save you from costly headaches later.
9. Ignoring Performance Monitoring Tools
Once you’ve upgraded to a managed VPS hosting plan, monitoring your server’s performance becomes essential. Unlike shared hosting, a VPS gives you dedicated resources — but without proper oversight, you risk running into issues like slow load times, crashes, or security vulnerabilities when resources max out.
You should regularly track metrics like RAM usage, CPU load, disk space, and traffic patterns to ensure your site stays fast and responsive.
Don’t skip this: Many of the best managed VPS hosting services include built-in performance monitoring tools. Take advantage of them to make sure your cheap VPS hosting plan delivers consistent, secure, and reliable performance — without any surprises.
10. Not Using a Content Delivery Network (CDN)
Even with a powerful VPS, serving static content (images, CSS, JS) through a CDN can improve site speed.
Benefits of Using a CDN:
Faster load times
Better performance under traffic spikes
Improved global reach
Low-cost solution: Services like Cloudflare offer free or affordable CDN options that integrate easily with most managed VPS hosting plans.
11. Relying Only on Customer Support Instead of Learning Basics
Managed doesn’t mean you’re off the hook completely. Knowing basic server commands or cPanel tasks can help you respond faster and solve minor issues on your own.
Why This Helps:
Speeds up troubleshooting
Helps you communicate better with support
Prevents small issues from becoming big ones
Invest in learning: The best managed VPS hosting experience comes when you balance provider support with a little self-education.
12. Forgetting to Optimize the Website Itself
No matter how powerful or secure your VPS is, if your website isn’t optimized, you’ll still experience performance issues.
Must-Do Optimizations:
Compress images (TinyPNG, WebP)
Use caching plugins (like WP Rocket, W3 Total Cache)
Minify JS/CSS files
Lazy load images and videos
Bottom line: Your VPS is only as good as the website running on it. Optimize both to get the most value from your cheap and managed VPS hosting plan.
Final Thoughts: How to Choose the Right Managed VPS Hosting?
Upgrading to a managed VPS hosting solution is a big step forward for your website or online business. But don’t let common mistakes turn it into a costly misstep. To recap:
Know what “managed” includes
Don’t go too big or too small
Prioritize location and performance
Balance “cheap” with real value
Demand a secure, scalable environment
When evaluating your options, aim for providers that offer a low-cost VPS hosting plan without sacrificing performance or security. And remember — the best managed VPS hosting providers the ones that fit your unique needs, support you 24/7, and help you grow with confidence.

Ann Taylor
M2Host m2host.com We provide experienced web hosting services tailored to your unique needs. Facebook Twitter Instagram YouTube
#linux#best web hosting#web hosting#m2host#webhostingprovider#webhostingservice#affordablehosting#cheap
0 notes
Text
The Ultimate Guide to Effective Server Management for Businesses
In today’s digital-first world, server management is a critical component of ensuring smooth business operations, security, and performance. Whether you’re running a small business or a large enterprise, efficient server management can mean the difference between seamless operations and costly downtime.
At CloudMinister Technologies, we specialize in comprehensive server management solutions that keep your infrastructure secure, optimized, and running at peak efficiency.
What is Server Management?
Server management involves the administration, monitoring, and maintenance of servers to ensure optimal performance, security, and reliability. This includes: Hardware & Software Updates Security Patching & Vulnerability Management Performance Monitoring & Optimization Backup & Disaster Recovery User Access & Permission Controls
Why is Server Management Important?
1. Maximizes Uptime & Performance
Proactive monitoring prevents unexpected crashes.
Load balancing ensures smooth operation during traffic spikes.
2. Enhances Security
Regular security patches protect against cyber threats.
Intrusion detection systems (IDS) and firewalls safeguard sensitive data.
3. Reduces Costs & Improves Efficiency
Prevents costly downtime and data loss.
Optimizes resource usage, reducing unnecessary expenses.
4. Ensures Compliance
Helps meet industry regulations (GDPR, HIPAA, PCI-DSS).
Maintains audit logs for security and compliance reporting.
Key Server Management Tasks
Routine Maintenance
Applying OS and software updates.
Checking disk space, RAM usage, and CPU performance.
Security Management
Installing security patches.
Configuring firewalls and malware protection.
Backup & Recovery
Automated backups to prevent data loss.
Disaster recovery planning for quick restoration.
Performance Optimization
Monitoring server load and optimizing configurations.
Scaling resources as needed.
In-House vs. Outsourced Server Management
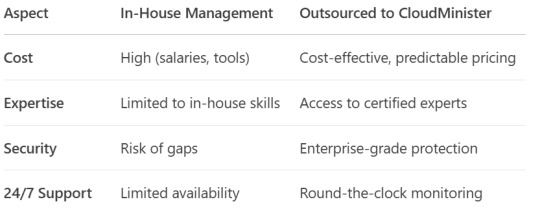
Why Choose CloudMinister for Server Management?
We provide end-to-end server management services, including: 🔹 Proactive Monitoring & Alerts – Prevent issues before they arise. 🔹 Security Hardening – Protect against cyber threats. 🔹 Automated Backups – Ensure data safety. 🔹 Performance Tuning – Keep servers running at peak efficiency. 🔹 Dedicated Support – 24/7 assistance from server experts.
Final Thoughts
Effective server management is not just about keeping systems running—it’s about optimizing performance, enhancing security, and ensuring business continuity. With CloudMinister Technologies, you can offload the complexities of server management and focus on growing your business.
0 notes
Text
Server Security: Analyze and Harden Your Defenses in today’s increasingly digital world, securing your server is paramount. Whether you’re a beginner in ethical hacking or a tech enthusiast eager to strengthen your skills, understanding how to analyze adn harden server security configurations is essential to protect your infrastructure from cyber threats. This comprehensive guide walks you through the key processes of evaluating your server’s setup and implementing measures that enhance it's resilience. Materials and Tools Needed Material/ToolDescriptionPurposeServer Access (SSH/Console)Secure shell or direct console access to the serverTo review configurations and apply changesSecurity Audit ToolsTools like Lynis, OpenVAS, or NessusTo scan and identify vulnerabilitiesConfiguration Management ToolsTools such as Ansible, Puppet, or ChefFor automating security hardening tasksFirewall Management InterfaceAccess to configure firewalls like iptables, ufw, or cloud firewallTo manage network-level security policiesLog Monitoring UtilitySoftware like Logwatch, Splunk, or GraylogTo track suspicious events and audit security Step-by-Step Guide to Analyzing and Hardening Server Security 1. Assess Current Server Security Posture Log in securely: Use SSH with key-based authentication or direct console access to avoid exposing passwords. Run a security audit tool: Use lynis or OpenVAS to scan your server for weaknesses in installed software, configurations, and open ports. Review system policies: Check password policies, user privileges, and group memberships to ensure they follow the principle of least privilege. Analyze running services: Identify and disable unnecessary services that increase the attack surface. 2. Harden Network Security Configure firewalls: Set up strict firewall rules using iptables, ufw, or your cloud provider’s firewall to restrict inbound and outbound traffic. Limit open ports: Only allow essential ports (e.g., 22 for SSH, 80/443 for web traffic). Implement VPN access: For critical server administration, enforce VPN tunnels to add an extra layer of security. 3. Secure Authentication Mechanisms Switch to key-based SSH authentication: Disable password login to prevent brute-force attacks. Enable multi-factor authentication (MFA): Wherever possible, introduce MFA for all administrative access. Use strong passwords and rotate them: If passwords must be used,enforce complexity and periodic changes. 4. Update and Patch Software Regularly Enable automatic updates: Configure your server to automatically receive security patches for the OS and installed applications. Verify patch status: Periodically check versions of critical software to ensure they are up to date. 5. Configure System Integrity and Logging Install intrusion detection systems (IDS): Use tools like Tripwire or AIDE to monitor changes in system files. Set up centralized logging and monitoring: Collect logs with tools like syslog, Graylog, or Splunk to detect anomalies quickly. Review logs regularly: Look for repeated login failures, unexpected system changes, or new user accounts. 6. Apply Security Best Practices Disable root login: prevent direct root access via SSH; rather,use sudo for privilege escalation. Restrict user commands: Limit shell access and commands using tools like sudoers or restricted shells. Encrypt sensitive data: Use encryption for data at rest (e.g., disk encryption) and in transit (e.g., TLS/SSL). Backup configurations and data: Maintain regular, secure backups to facilitate recovery from attacks or failures. Additional Tips and Warnings Tip: Test changes on a staging environment before applying them to production to avoid service disruptions. Warning: Avoid disabling security components unless you fully understand the consequences. Tip: Document all configuration changes and security policies for auditing and compliance purposes.
Warning: Never expose unnecessary services to the internet; always verify exposure with port scanning tools. Summary Table: Key Server Security Checks Security AspectCheck or ActionFrequencyNetwork PortsScan open ports and block unauthorized onesWeeklySoftware UpdatesApply patches and updatesDaily or WeeklyAuthenticationVerify SSH keys,passwords,MFAMonthlyLogsReview logs for suspicious activityDailyFirewall RulesAudit and update firewall configurationsMonthly By following this structured guide,you can confidently analyze and harden your server security configurations. Remember, security is a continuous process — regular audits, timely updates, and proactive monitoring will help safeguard your server against evolving threats. Ethical hacking principles emphasize protecting systems responsibly, and mastering server security is a crucial step in this journey.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
How to Deploy and integrate VHR with VBR
OOTBI (Object First Out-Of-the-Box Immutability) is an alternative solution to Veeam Linux Hardened Repository (VHR). Since I have covered OOTBI extensively in the past, I will now focus on VHR. Please, see Best Storage for Veeam: Comparing OOTBI by ObjectFirst to VHR. Therefore, in this article, we shall be discussing how to deploy and integrate VHR with VBR. Also, see Create a bootable USB on…
#Add the Hardened Backup Repository to VBR#Create VM#Install Veeam Hardened Repository#Install VM on Proxmox#Linux Hardened Repository#Protecting your Physical VHR Server#VHR#vm id
0 notes
Text
Reliable Website Maintenance Services In India | NRS Infoways
In today’s hyper‑connected marketplace, a website is far more than a digital brochure—it is the beating heart of your brand experience, your lead‑generation engine, and your most valuable sales asset. Yet many businesses still treat their sites as “launch‑and‑forget” projects, only paying attention when something breaks. At NRS Infoways, we understand that real online success demands continuous care, proactive monitoring, and seamless enhancements. That’s why we’ve built our Reliable Website Maintenance Services In India to deliver round‑the‑clock peace of mind, bulletproof performance, and measurable ROI for forward‑thinking companies like yours.
Why Website Maintenance Matters—And Why “Reliable” Makes All the Difference
Search engines reward fast, secure, and regularly updated sites with higher rankings; customers reward them with trust and loyalty. Conversely, a sluggish, outdated, or vulnerable site can cost you traffic, conversions, and brand reputation—sometimes overnight. Our Reliable Website Maintenance Services In India go beyond the basic “fix‑it‑when‑it‑breaks” model. We combine proactive health checks, performance tuning, security hardening, and content optimization into a single, cohesive program that keeps your digital storefront open, polished, and ready for growth.
What Sets NRS Infoways Apart?
1. Proactive Performance Monitoring
We leverage enterprise‑grade monitoring tools that continuously scan load times, server resources, and user journeys. By identifying bottlenecks before they escalate, we ensure smoother experiences and higher conversion rates—24/7.
2. Robust Security & Compliance
From real‑time threat detection to regular firewall updates and SSL renewals, your site stays impervious to malware, SQL injections, and DDoS attacks. We align with global standards such as GDPR and PCI‑DSS, keeping you compliant and trustworthy.
3. Seamless Content & Feature Updates
Launching a new product line? Running a seasonal promotion? Our dedicated team updates layouts, landing pages, and plugins—often within hours—to keep your messaging sharp and relevant without disrupting uptime.
4. Data‑Driven Optimization
Monthly analytics reviews highlight user behavior, bounce rates, and conversion funnels. We translate insights into actionable tasks—A/B testing CTAs, compressing heavy images, or refining navigation—all folded into our maintenance retainer.
5. Transparent Reporting & SLAs
Every client receives detailed monthly reports covering task logs, incident resolutions, and performance metrics. Our Service Level Agreements guarantee response times as low as 30 minutes for critical issues, underscoring the “Reliable” in our Reliable Website Maintenance Services In India.
Real‑World Impact: A Success Snapshot
A Delhi‑based B2B SaaS provider reached out to NRS Infoways after repeated downtime eroded user trust and slashed demo bookings by 18 %. Within the first month of onboarding, we:
Migrated their site to a high‑availability cloud cluster
Deployed a Web Application Firewall (WAF) to fend off bot attacks
Compressed multimedia assets, cutting average load time from 4.2 s to 1.3 s
Implemented weekly backup protocols with versioned restores
Result? Organic traffic climbed 27 %, demo sign‑ups rebounded 31 %, and support tickets fell by half—proving that consistent, expert care translates directly into revenue.
Flexible Plans That Scale With You
Whether you manage a lean startup site or a sprawling enterprise portal, we offer tiered packages—Basic, Professional, and Enterprise—each customizable with à‑la‑carte add‑ons like e‑commerce catalog updates, multi‑language support, or advanced SEO audits. As your business evolves, our services scale seamlessly, ensuring you never pay for overhead you don’t need or sacrifice features you do.
Partner With NRS Infoways Today
Your website is too important to leave to chance. Join the growing roster of Indian businesses that rely on NRS Infoways for Reliable Website Maintenance Services In India and experience the freedom to innovate while we handle the technical heavy lifting. Ready to protect your digital investment, delight your visitors, and outpace your competition?
Connect with our maintenance experts now and power your growth with reliability you can measure.
0 notes
Text
Protect & Optimize Data Centers with AI & Automation
In the era of digital transformation, the data center evolution has become a core driver of innovation, security, and scalability. With enterprises processing millions of transactions and storing massive amounts of data daily, knowing how to protect your data center from DDoS attacks, optimizing operations, and leveraging automation tools has never been more important.
1. How to Protect Your Data Center from DDoS
Cyber threats like DDoS (Distributed Denial of Service) can paralyze infrastructure and disrupt operations. Knowing how to protect your data center from DDoS involves deploying firewalls, intrusion detection systems, and anti-DDoS tools. Leveraging Symantec Data Center Security provides advanced protection with real-time threat intelligence, enabling proactive defense against sophisticated attacks.
2. Secure & Scalable Large Data Storage Solutions
As businesses collect massive volumes of data, they require reliable large data storage solutions. These include hybrid cloud environments, NAS, SAN systems, and scalable object storage. Choosing the right storage not only ensures capacity but also enhances redundancy, backup, and disaster recovery.
3. The Roadmap of Data Center Evolution
From traditional on-premise facilities to intelligent cloud-integrated hubs, the data center evolution showcases a shift toward automation, AI integration, and edge computing. As AI workloads grow, companies are embracing solutions that improve efficiency and security while reducing latency.
4. Leverage Symantec Data Center Security
Ensuring end-to-end security in this evolving landscape is critical. Symantec Data Center Security offers host-based protection, system hardening, and compliance support. It plays a pivotal role in safeguarding virtual environments, containers, and physical servers.
5. Integrating Data Center Interconnect for Hybrid Cloud
To deliver seamless performance between public clouds and private data centers, organizations need data center interconnect for hybrid cloud architectures. These enable fast, secure data transfers and consistent user experiences across distributed platforms, crucial for real-time analytics and application hosting.
6. Accelerate Operations with Data Center Automation
Manual configuration is time-consuming and error-prone. Data center automation allows IT teams to manage workloads, patch systems, and optimize energy usage automatically. Paired with data center automation software, businesses can reduce downtime, scale faster, and improve cost efficiency.
7. The Role of High Density Data Centre Network
The rise of AI and big data has led to the need for a high density data centre network. These facilities support compact infrastructure, powerful cooling systems, and high-throughput connectivity, making them ideal for AI/ML training and analytics.
8. Powerful Tools: Data Center Automation Software
To keep up with real-time demands, robust data center automation software such as Ansible, Puppet, and VMware vRealize is being used. These tools simplify configuration management, enhance performance monitoring, and help deploy services rapidly.
9. The Rise of AI: Microsoft AI Data Center Spending
Leading the AI infrastructure race, Microsoft AI data center spending has grown significantly. The company is investing billions in building energy-efficient data centers optimized for large language models and enterprise AI applications. These investments set new benchmarks for performance and sustainability.
10. Efficiency Boost: Data Center Optimization Techniques
Operational excellence requires smart data center optimization techniques. These include workload balancing, efficient cooling systems, virtualization, and space utilization. When implemented correctly, they reduce carbon footprint, improve performance, and cut costs.
11. Budget Matters: Understanding Cloud Colocation Pricing
Choosing between cloud and physical hosting requires an understanding of cloud colocation pricing. Colocation allows organizations to rent physical space within a data center, offering more control and predictable costs compared to cloud-only models. Pricing varies by power density, bandwidth, and support level.
Conclusion
Future-ready enterprises must prioritize security, scalability, and automation in their infrastructure strategy. With growing cyber threats and the pressure to deliver uninterrupted digital services, deploying technologies such as Symantec Data Center Security, data center automation software, and embracing data center evolution are essential steps forward.
Understanding how to protect your data center from DDoS, adopting large data storage solutions, and aligning with trends like Microsoft AI data center spending can give your organization a competitive edge.
Stay ahead—modernize, automate, and secure your data environment with cutting-edge solutions.
0 notes
Text
# Ghosts We Carry - Chapter 19
Juice woke to the sound of his phone buzzing insistently on the nightstand. Elena stirred against him, her warm body pressing closer as she fought against consciousness. For a moment, he considered ignoring the call, staying in this perfect bubble where nothing existed but her soft breathing and the morning light filtering through the blinds.
The phone buzzed again.
"Shit," he muttered, carefully extracting his arm from beneath Elena's head. She made a small sound of protest but didn't wake as he grabbed the phone.
Ross's name appeared on the burner's display.
"Yeah?"
"We've got a problem." Ross's voice was tight with controlled panic. "HaviCorp moved overnight. The Stockton facility is being evacuated as we speak."
Juice was instantly awake, adrenaline flooding his system. "What? How do you know?"
"Satellite surveillance. Convoy of trucks left two hours ago. They're destroying evidence and relocating assets." Ross paused. "Including personnel."
"Personnel meaning—"
"Scientists. Research subjects. Anyone who knows too much." The implication hung heavy in the air. "My contact at the Bureau just went dark. Either they got to him, or he's running scared."
Elena was awake now, watching him with alert eyes as she pulled the sheet up to cover herself. Juice could see her mind already working, processing the half of the conversation she could hear.
"Where are they moving to?" Juice asked.
"Unknown. But I've got a lead on a secondary facility. Smaller operation, but it might have what we need." Ross's voice hardened. "Problem is, it's not going to stay operational much longer. If we're going to move, it has to be today."
Juice looked at Elena, saw the determination already forming in her expression despite the fear. "Send me the location."
"Already did. Check your messages." Ross paused again. "Ortiz? This is it. After today, they disappear completely. We won't get another shot."
The line went dead. Juice stared at the phone for a moment, then turned to Elena.
"They're running," he said simply.
Elena was already moving, gathering her scattered clothes. "Then we run faster."
---
The secondary facility was a nondescript office building in an industrial park outside Modesto. According to Ross's intelligence, it housed HaviCorp's backup servers and a small research team working on genetic sequencing protocols.
"Looks quiet," Tig observed through binoculars as they watched from across the street. "Too quiet."
"Could be a trap," Happy added, his usual economy of words carrying extra weight.
Chibs studied the building through his own scope. "Or they're already gone."
Elena was hunched over her tablet, connected to Ross's surveillance feed. "I'm seeing minimal heat signatures. Maybe six people inside, all on the third floor."
"Security?" Juice asked.
"Standard corporate setup. Keycard access, basic cameras. Nothing like the Stockton facility." Elena looked up. "But if they're destroying evidence..."
"Could be rigged to blow," Chibs finished. "Lovely."
The Mayans had taken position on the building's north side, ready to provide backup or cut off escape routes. Ross and his team were monitoring from a van two blocks away, feeding them real-time intelligence.
"Remember," Chibs said into his comm, "we go in fast, get what we need, and get out. No heroes, no unnecessary risks."
Juice caught Elena's eye. She was suited up in tactical gear Ross had provided, looking determined but nervous. "You sure about this?"
"I'm the only one who'll know what we're looking for," she replied. "Besides, someone needs to make sure you don't accidentally download their cafeteria menu instead of their research files."
Despite the tension, Juice found himself smiling. "Smart-ass."
"You love it."
The words slipped out before she could stop them, and both of them froze. Love. Neither had said it before, and this wasn't exactly the time or place for that conversation.
"I do," Juice said quietly, meaning it completely.
Elena's breath caught. "Juan—"
"Movement," Happy's voice cut through their moment. "Two vehicles approaching from the east."
Chibs raised his binoculars. "Black SUVs. Corporate plates." He keyed his mic. "Ross, you seeing this?"
"Affirmative. Unknown occupants, but they're not on my list of friendlies."
"Change of plans," Chibs decided. "We go now, before they get inside."
---
The entry went smoother than expected. Elena's keycard—cloned from data they'd stolen earlier—got them through the main entrance, and the elevator ride to the third floor passed in tense silence.
The hallway beyond was sterile and empty, fluorescent lights humming overhead. Elena led them toward the server room, her tablet showing the building's layout.
"Just like a hospital," she muttered. "All the warmth of a morgue."
They found the first body twenty feet from the server room door.
"Fuck," Tig whispered, kneeling beside the young man in a lab coat. "Single shot, back of the head. Professional."
Juice felt Elena tense beside him. This wasn't just corporate espionage anymore. This was execution.
"They're cleaning house," he said grimly.
"Which means we're running out of time," Chibs replied. "Elena, how long do you need?"
"Give me ten minutes with their servers. Maybe fifteen."
"You've got five."
The server room was a nightmare of blinking lights and humming machinery. Elena went to work immediately, connecting her equipment to multiple terminals while Juice stood guard at the door.
"Jesus," she breathed, staring at her screen. "They're not just targeting individuals. They're working on aerosol delivery systems. Crowd dispersal weapons."
"English, Doc."
"They could release this at a concert, a political rally, a sports event. Target specific genetic markers in a crowd of thousands." Her fingers flew across the keyboard. "And look at this client list—"
An alarm began blaring throughout the building.
"Time's up," Chibs's voice crackled through the comm. "Those SUVs just disgorged a small army. We need to move now."
Elena was still downloading files, her tablet's progress bar crawling toward completion. "Thirty more seconds—"
Gunfire erupted from somewhere below them.
"Elena, now!" Juice grabbed her arm, but she shook him off.
"I'm not leaving without this data!" The progress bar hit 90%. "Almost there—"
The lights went out.
Emergency lighting kicked in a moment later, bathing everything in hellish red. Elena's tablet showed 100% complete just as footsteps thundered in the hallway outside.
"Move!" Juice hauled Elena toward the emergency exit as the server room door exploded inward.
Men in tactical gear poured through, automatic weapons raised. But Juice and Elena were already gone, racing down the emergency stairwell as bullets chewed up the walls behind them.
"Two floors down," Chibs's voice in their earpieces. "Happy's got the exit secured."
They hit the ground floor running, Elena clutching her tablet like a lifeline. Happy appeared around a corner, his weapon smoking, and gestured toward a side exit.
"Mayans took out their rear guard," he reported. "Vehicle's waiting."
They burst through the door into blinding sunlight just as an explosion rocked the building behind them. Elena stumbled, and Juice caught her arm, pulling her toward the waiting van.
"The servers!" she gasped, looking back at the building.
"Already gone," Ross's voice came from the van's radio. "They triggered thermite charges the moment you disconnected. Whole server room is slag."
But Elena was smiling as they climbed into the van. "Doesn't matter. I got what we needed."
---
The safe house was a run-down motel on the outskirts of town, the kind of place that rented rooms by the hour and didn't ask questions. Elena had commandeered the table in their room, spreading out printouts and connecting multiple devices.
"This is it," she said, exhaustion and triumph warring in her voice. "Everything. Client lists, research protocols, financial records. Even communications between HaviCorp executives and their government contacts."
Ross leaned over her shoulder, scanning the documents. His face grew progressively darker as he read.
"Congressional representatives," he muttered. "Pentagon officials. CIA liaisons." He looked up at Chibs. "This goes all the way to the top."
"How high?" Chibs asked.
"High enough that a conventional investigation would disappear into a bureaucratic black hole." Ross pulled out his own phone. "But not high enough to stop what I'm about to do."
While Ross made his calls, mobilizing whatever federal resources he still trusted, Elena continued analyzing the data. Juice watched her work, admiring the focused intensity that had first attracted him to her.
"Find something else?" he asked.
"The original research," she replied, not looking up from her screen. "My father's work. They didn't just steal it—they improved it. Made it more targeted, more lethal." She finally looked at him, tears in her eyes. "And more elegant. If I'm being honest, it's brilliant. Horrifying, but brilliant."
Juice moved behind her chair, resting his hands on her shoulders. "Your father would be proud of you for stopping it."
"Would he? Or would he be horrified that his work led to this in the first place?"
"He'd be proud," Juice said firmly. "Because you're not just stopping it. You're going to make sure it can never be used again."
Elena leaned back against him, drawing strength from his presence. "The antidote protocols. I can reverse-engineer them. Create a universal counteragent."
"How long?"
"With a proper lab? A week, maybe two." She gestured around the motel room. "Here? Months, if at all."
Chibs appeared in the doorway. "Then we get you a proper lab."
"How?"
"Ross has an idea. Risky as hell, but it might work." Chibs's expression was grim. "We're going to walk right into the lion's den."
---
The plan Ross outlined was audacious in its simplicity. HaviCorp's primary research facility in San Francisco—their crown jewel—was hosting a gala fundraiser the following night. Politicians, scientists, investors, all gathered in one place to celebrate the company's "humanitarian research initiatives."
"Perfect cover," Ross explained. "Security will be focused on VIP protection, not internal threats. And the lab facilities will be lightly guarded while everyone's at the party."
"Except us," Juice pointed out. "We'll be breaking into a corporate fortress while they're throwing a party upstairs."
"Not all of us," Elena said quietly. "I should go to the gala."
Every head in the room turned toward her.
"What?" Chibs asked.
"Dr. Elena Alvarez, genetic researcher, recently published in several major journals. I'd fit right in." She looked around the room. "I could walk right through the front door."
"Absolutely not," Juice said immediately. "Too dangerous."
"Everything we're doing is dangerous," Elena replied. "But this way, we have someone inside. Someone who can disable security from within while you access the lab."
Ross was nodding slowly. "It could work. But you'd be completely on your own in there."
"No," Juice said firmly. "I won't let her—"
"It's not your choice," Elena interrupted, her voice sharp. "This is my fight too. My father's work, my responsibility."
The room fell silent. Juice could see the determination in Elena's eyes, the same fierce intelligence that had helped her survive everything HaviCorp had thrown at them. He also saw the fear she was trying to hide.
"If we do this," he said finally, "we do it right. Full communication, backup plans, multiple exit strategies."
"Agreed," Ross said. "But we'll need to move fast. After today's raid, they'll be tightening security everywhere."
Chibs looked around the room, meeting each person's eyes. "Last chance to walk away. After this, we're committed."
No one moved.
"Then let's end this," Chibs said.
Outside, the sun was setting over the California hills, painting the sky in shades of red and gold. Tomorrow night, one way or another, their war with HaviCorp would be decided.
Juice pulled Elena aside as the others began planning details.
"About what I said earlier," he began.
"In the building?"
"Yeah." He took her hands in his. "I meant it. All of it."
Elena's smile was soft but fierce. "Good. Because I love you too, Juan Carlos Ortiz. And I plan to tell you that again tomorrow night when this is all over."
"Promise?"
"Promise."
But as they kissed, both of them were thinking the same thing: in their world, promises were fragile things, easily broken by bullets and betrayal.
Tomorrow would test them all.
#theo rossi#sons of anarchy#juice ortiz#sons of anarchy fanfiction#juan carlos juice ortiz#soa juice
1 note
·
View note
Text

How to Set Up Your Local Development Environment for WordPress
Setting up a local development environment is one of the best ways to experiment with and build WordPress websites efficiently. It offers you a safe space to test themes, plugins, and updates before applying changes to a live site. Whether you’re a beginner or an experienced developer, having a local environment is essential in streamlining your workflow and minimizing website downtime.
Before we dive into the technical steps, it’s worth mentioning the benefits of WordPress for your business website. WordPress offers unmatched flexibility, scalability, and user-friendliness, making it an ideal platform for businesses of all sizes. When paired with a solid local development setup, WordPress becomes even more powerful in enabling fast and secure site builds.
Step 1: Choose Your Local Development Tool
There are several local development tools available that cater specifically to WordPress users:
Local by Flywheel (now Local WP): Extremely beginner-friendly with features like SSL support and one-click WordPress installs.
XAMPP: A more general-purpose tool offering Apache, MySQL, PHP, and Perl support.
MAMP: Ideal for macOS users.
DevKinsta: Built by Kinsta, it offers seamless WordPress development and staging capabilities.
Choose the one that suits your OS and comfort level.
Step 2: Install WordPress Locally
Once you’ve chosen your tool:
Install the software and launch it.
Create a new WordPress site through the interface.
Set up your site name, username, password, and email.
After setup, you’ll get access to your WordPress dashboard locally, allowing you to install themes, plugins, and begin your customizations.
Step 3: Configure Your Development Environment
To ensure an efficient workflow, consider these configurations:
Enable Debug Mode: Helps in identifying PHP errors.
Use Version Control (e.g., Git): Keeps your changes tracked and manageable.
Database Access: Tools like phpMyAdmin help manage your WordPress database locally.
If your project requires dynamic functionality, leveraging PHP Development Services during the setup phase can ensure custom features are implemented correctly from the beginning.
Step 4: Customize Themes and Plugins Safely
With your local environment set up, now's the time to begin theme development or customization. You can safely create or modify a child theme, experiment with new plugins, and write custom code without any risk of affecting your live site.
For those unfamiliar with theme structures or WordPress standards, it’s often wise to hire a professional WordPress developer who understands best practices and can ensure clean, maintainable code.
Step 5: Syncing to a Live Server
After building and testing your site locally, you'll eventually want to push it live. Popular methods include:
Using a plugin like Duplicator or All-in-One WP Migration
Manual migration via FTP and phpMyAdmin
Using version-controlled deployment tools
Syncing should always be done carefully to avoid overwriting crucial data. Regular backups and testing are essential.
Step 6: Maintain Your WordPress Site Post-Launch
Launching your website is only the beginning. Ongoing updates, security patches, and performance optimization are critical for long-term success. Enlisting website maintenance services ensures your site remains fast, secure, and up-to-date.
Services can include:
Core, plugin, and theme updates
Malware scans and security hardening
Site performance monitoring
Regular backups
Final Thoughts
A local WordPress development environment not only speeds up your development process but also protects your live website from unintended changes and errors. With tools and strategies now more accessible than ever, there's no reason not to use one.From learning the basics to running advanced builds, setting up locally gives you the confidence and space to grow your WordPress skills. And if you want to see real-world examples or follow along with tips and tricks I share, feel free to check out my work on Instagram for practical inspiration.
0 notes
Text
VPS Hosting Management: Should You Go DIY or Let Experts Handle It?
🖥️ Self-Managed vs Fully Managed VPS Hosting: What’s Best for You?
Choosing the right management level for your virtual server can make or break your hosting experience.
When you’re ready to upgrade from shared hosting to VPS (Virtual Private Server), one key decision awaits: Should you choose a Self-Managed or Fully Managed VPS?
This choice affects how much control, time, and technical responsibility you take on. At VCCLHOSTING, we offer both types — because every business has different needs and technical expertise.
In this guide, we'll break down the differences, pros, cons, and how to decide which VPS hosting type is right for you.
🔧 What Is Self-Managed VPS Hosting?
Self-managed VPS means you (or your tech team) handle:
Server setup & OS installation
Security patches & updates
Software installation & maintenance
Monitoring & troubleshooting
You get full root access and freedom — but you’re responsible for everything.
✅ Best for:
Developers
System administrators
Tech-savvy businesses with in-house IT
⚠️ Things to consider:
Requires Linux/Windows server experience
No hand-holding — full control also means full responsibility
🛠️ What Is Fully Managed VPS Hosting?
With fully managed VPS hosting, your hosting provider (like VCCLHOSTING) takes care of:
Server setup & optimization
Regular software updates
Security configurations (firewall, malware scan, etc.)
Control panel setup (like cPanel or Direct Admin)
24/7 monitoring & technical support
This is a hands-off solution, ideal for those who want to focus on their website or business — not server tasks.
✅ Best for:
Business owners
Bloggers & agencies
Non-technical teams
Anyone who values convenience & support
🔍 Key Differences: Side-by-Side Comparison
Feature Self-Managed VPS Fully Managed VPS Server Setup You do it Done by VCCLHOSTING Software & Security Updates Manual Automated & handled for you Control Full root access Root access with support assistance Technical Knowledge Needed High Low to none Support Availability Limited to hardware issues24/7 full technical support Time Commitment High Minimal
🧠 How to Decide Which One’s Right for You
Choose Self-Managed VPS if:
You want full control and flexibility
You’re comfortable managing Linux or Windows servers
You’re deploying custom scripts, stacks, or dev environments
You need a lower-cost solution and can manage support internally
Choose Fully Managed VPS if:
You want to save time and reduce stress
You prefer a team to handle security, backups, and performance
You’re focused on growing your business or content — not managing infrastructure
You don’t have an in-house server admin
🌟 What VCCLHOSTING Offers
At VCCLHOSTING, we provide both Self-Managed and Fully Managed VPS Hosting, tailored for Indian businesses and developers.
All VPS Plans Include:
SSD/NVMe storage
High-speed performance
Dedicated IP
Root access
Kolhapur-based data center for low latency
Optional cPanel or DirectAdmin
Instant scalability
Fully Managed Plans Include:
OS installation & hardening
Firewall, malware scanner, and daily backups
24/7 support in English, Hindi, and Marathi
Monitoring and resource optimization
🏁 Final Thoughts
Both Self-Managed and Fully Managed VPS hosting have their advantages — the right choice depends on your technical comfort, time, and business goals.
If you’re a developer who loves being hands-on, go Self-Managed. If you want to offload server responsibilities and focus on your growth — choose Fully Managed.
💬 Need Help Deciding?
Our team at VCCLHOSTING can guide you through the selection based on your project needs.
📞 Call: 9096664246 🌐 Visit: www.vcclhosting.com 💬 Chat: 24/7 available on website
0 notes
Text
Unlocking Business Agility with Wintel Services: A Strategic Guide to Modern IT Infrastructure
In today’s hyper-competitive digital economy, the performance and resilience of your IT environment can define business success. Enterprises must be equipped with infrastructure that is reliable, scalable, and secure, and Wintel services provide just that. A fusion of Windows OS and Intel-based architecture, Wintel environments offer a highly compatible, stable foundation for businesses striving for digital transformation and operational excellence.
As a leader in cloud engineering and infrastructure modernization, Infimatrix delivers comprehensive Wintel services that support enterprise agility and innovation. From server management to VDI (Virtual Desktop Infrastructure), these services are purpose-built for businesses looking to optimize performance while maintaining security and compliance.
Wintel systems have long been the backbone of enterprise IT. By pairing Microsoft’s trusted Windows operating system with Intel’s hardware platforms, businesses gain access to environments known for efficiency, security, and compatibility. Infimatrix understands this synergy and provides tailored solutions for organizations managing hybrid, on-premise, or cloud infrastructures.
At the heart of their Wintel solutions is server management, which includes provisioning, monitoring, patching, and health checks for Windows servers running on Intel platforms. This service ensures servers are not just operational but optimized for speed and availability. Proactive monitoring enables rapid detection and resolution of performance issues, helping minimize downtime and enhance user experience.
Security is another key element of Wintel infrastructure. In an era of relentless cyber threats, securing your operating systems and server hardware is not optional—it’s essential. Infimatrix delivers security hardening, access controls, patch management, and real-time threat detection as part of their broader Wintel management services. Whether it’s preventing unauthorized access or ensuring data encryption, every layer is protected.
Routine server upgrades are crucial in maintaining peak performance. Many legacy environments suffer from inefficiencies due to outdated firmware or unsupported OS versions. Infimatrix provides seamless upgrade paths that include system analysis, data backup, version compatibility checks, and rollback options to ensure business continuity. This structured approach eliminates migration risks and improves compliance with modern IT standards.
Wintel environments are also well-suited to Virtual Desktop Infrastructure. Through VDI, organizations can offer secure, high-performance desktops to remote employees while centralizing data control and reducing endpoint vulnerabilities. Infimatrix implements and manages Wintel-based VDI solutions that offer scalability and reliability across distributed teams, making it easier to support remote workforces.
Infimatrix also handles comprehensive application support within Wintel environments. Applications running on Windows servers are monitored for performance, availability, and version compatibility. From legacy software to modern enterprise platforms, Infimatrix ensures that mission-critical apps are well-maintained, secure, and aligned with the latest OS updates.
A growing number of businesses are integrating cloud engineering with their Wintel deployments. This trend is driven by the need to scale on demand and access flexible computing resources. Infimatrix specializes in building hybrid Wintel-cloud infrastructures that combine the best of both worlds. Whether hosted on Microsoft Azure, AWS, or private clouds, Infimatrix helps clients achieve seamless integration and end-to-end visibility.
In addition to cloud capabilities, automation is another game-changing component in Wintel infrastructure management. Manual processes often lead to delays, inconsistencies, and human error. With Wintel automation services, Infimatrix introduces intelligent automation into patching, provisioning, and performance tuning—leading to reduced operational overhead and faster response times.
Another strength of Infimatrix lies in its experience supporting large-scale Wintel environments for clients across the USA. From multinational corporations to government institutions, Infimatrix delivers strategic Wintel support services tailored to meet business and compliance requirements. Their team of certified professionals brings deep expertise in managing complex infrastructures across multiple regions and time zones.
Beyond the primary keywords, it’s also important to recognize relevant semantic keywords that complement the discussion of Wintel infrastructure. Terms like “Windows server support,” “Intel server optimization,” “Virtual desktop infrastructure,” “server patching automation,” and “infrastructure compliance” all capture the broader scope of this domain. By aligning with these concepts, the value of Wintel services becomes more tangible and strategically relevant for enterprise buyers.
The competitive advantage of implementing well-managed Wintel services is undeniable. Organizations benefit from enhanced performance, reduced IT costs, and simplified management through centralized control. The built-in compatibility between Windows operating systems and Intel hardware ensures that updates and expansions don’t disrupt existing workflows. Moreover, integrating VDI and cloud platforms allows businesses to modernize their IT infrastructure without abandoning familiar environments.
Infimatrix enables this transformation by offering full-stack support that spans architecture consulting, deployment, monitoring, and 24/7 technical assistance. Their commitment to best practices, security compliance, and performance optimization positions them as a trusted partner for any business looking to build or scale its Wintel systems.
In conclusion, Wintel services are no longer just about server uptime or system compatibility—they are about empowering businesses to move faster, operate securely, and scale smarter. From enhancing desktop delivery with VDI to securing mission-critical workloads and introducing automation, Infimatrix’s Wintel offerings provide everything modern businesses need to thrive in a digital-first world. If your organization is ready to modernize its IT foundation, explore the full spectrum of Wintel services offered by Infimatrix and start building a resilient infrastructure for tomorrow’s challenges.
0 notes
Text
Server Management: Ensuring Optimal Performance and Security
Introduction
In today’s fast-paced digital landscape, businesses rely heavily on their IT infrastructure to deliver seamless services. Server Management plays a crucial role in maintaining server health, security, and performance. At CloudMinister Technologies, we offer comprehensive server management services to ensure your servers run efficiently, securely, and with minimal downtime.
What is Server Management?
Server Management involves the monitoring, maintenance, and optimization of servers to ensure they operate at peak performance. It includes tasks such as:
Software & Security Updates – Applying patches to prevent vulnerabilities. Performance Monitoring – Tracking CPU, RAM, disk usage, and network traffic. Backup & Disaster Recovery – Ensuring data integrity with regular backups. Security Hardening – Implementing firewalls, intrusion detection, and malware protection. User & Access Management – Controlling permissions to prevent unauthorized access.
Why is Server Management Important?
A poorly managed server can lead to: Downtime & Loss of Revenue – Server crashes disrupt business operations. Security Breaches – Unpatched servers are vulnerable to cyberattacks. Slow Performance – Unoptimized servers affect user experience.
With professional server management, businesses can: Enhance Security – Protect against threats like DDoS, ransomware, and hacking. Improve Uptime – Minimize disruptions with proactive monitoring. Reduce IT Costs – Avoid expensive emergency fixes with regular maintenance. Scale Efficiently – Optimize resources for growing workloads.
CloudMinister’s Server Management Services
At CloudMinister Technologies, we provide end-to-end server management for businesses of all sizes.
Our Offerings Include:
🔹 24/7 Server Monitoring – Real-time alerts for issues like high CPU usage or disk failures. 🔹 Automated Backups – Scheduled backups with quick recovery options. 🔹 Security Audits & Hardening – Regular vulnerability scans and protection measures. 🔹 Performance Optimization – Fine-tuning servers for speed and efficiency. 🔹 Patch Management – Keeping OS and software up-to-date to prevent exploits. 🔹 Cloud & On-Premises Support – Managing both cloud-based and physical servers.
Server Management Use Cases
Web Hosting Providers – Ensuring high uptime for client websites. E-Commerce Platforms – Preventing crashes during peak traffic. Enterprise IT Infrastructure – Maintaining secure and compliant servers. Gaming Servers – Reducing lag and downtime for multiplayer games.
Managed vs. Unmanaged Servers
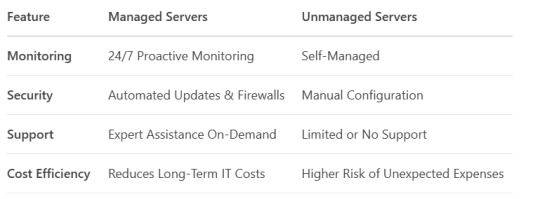
Conclusion
Effective Server Management is essential for business continuity, security, and performance. Whether you use dedicated, cloud, or hybrid servers, CloudMinister Technologies provides reliable, expert-managed services to keep your infrastructure running smoothly.
Need Professional Server Management? Contact us today!
0 notes