#idempotent
Explore tagged Tumblr posts
Text
In trying to get round a limitation of a text expander I now have a “text expansion” that uses the shell functionality of the expander to modify the config file that the expansion is defined in. This feels like it should be against some sort of law, it's just not right, it's a crime against computers.
#it isn't even idempotent#no safety measures whatsoever#certainly not the worst thing ever done in bash but it just feels bad
2 notes
·
View notes
Note
*multiplies you by 1*
hmph. idempotent.
7 notes
·
View notes
Text
What are HTTP requests?
HTTP (Hypertext Transfer Protocol) requests is one of the most common ways information is communicated between clients and servers on the internet. A client will go to the server to get resources or perform an action via a HTTP request.
HTTP requests follow a standard structure:
Request line - the request line specifies what HTTP method is being used (more on that below), the endpoint (a URL/URI, a server location on the web) that the request is being sent to. And what version of HTTP is being used.
Headers - Additional information that needs passing between client and server (cookies, authentication, OS version, etc)
Message body - data to be passed as part of the request.
HTTP has set methods which can be used for requests, they're used for different purposes.
HTTP methods
GET - used to retrieve data from a server
HEAD - is similar to get but has no body, it's usually used to assess if an API is currently available.
POST - used to send information to the server to create or update a resource using information stored in the body of the HTTP request.
PUT - Updates or creates a resource. PUT requests are idempotent, the results of them stay the same no matter how many times it's called.
DELETE - used to delete a resource from a server.
PATCH - used to update information on the server with a partial modification. E.g. updating only the title of an article.
TRACE - used as a loop back test, usually used for debugging and diagnostics of APIs
CONNECT - creates a tunnel connection to a server specified by the URL provider.
5 notes
·
View notes
Text
battlesong wip
Xivu Arath, She of Idempotent Victory, is forging a weapon. It is a weapon of totality, of all-that-is-her, and so it must encompass every form of violence.
---
The song drags at her and she is laughing, laughing. Her life is not such a small thing to redefine, but the shrilling chorus tugs it up from her chest, fluttering in her mouth until she clamps her jaws shut on it. She listens fiercely as the deathsong scrabbles for a hold.
It says: there is nothing that has lived that will not die.
It says: here is your beating heart, here is your laboured breath, here is your will. Your heart is stopped, your breath is dust, your will is broken.
It says, triumphant: o dead thing, this cessation of existence is all that you are and all that will ever be –
But by striving to kill her it becomes an attack, a method of waging war and enacting violence, and what is she if not defined by violence alone?
THIS IS MINE, she declares. THESE VOICES. THIS DEATH. THIS SONG. This is true, because she has said it. The melody falters as the words carve themselves in, an urgent undercurrent biting deep into air and sound and throat and bone. The deathsingers sing back with renewed fervor, clawing with every scrap of will to free themselves from her proclamation. It is too late. If they are hers, then they cannot hope to kill her. This is a violence described and embraced, and she folds it into another layer of her will and power.
Xivu closes her hand and the song snuffs out. The choir’s skulls, still overfull with killing resonance, crack and splinter in her grasp.
A good effort, still.
#destiny#xivu arath#my words#felt like tossing this up since I'm in a celebratory mood#osmium sorrows
44 notes
·
View notes
Text
Idempotent Linear Maps
%view at https://trivial-observations.tumblr.com/post/734896076331646976/idempotent-linear-maps to render the math
Just some nice facts about linear maps when they are idempotent. These are from the last two exercises from chapter 9 of Napkin.
Lemma 1. Let \(P \colon V \longrightarrow V\) be a linear map, where \(V\) is a (not necessarily finite-dimensional) vector space. Suppose that \(P\) is idempotent, i.e. \(P(P(v)) = P(v)\), or equivalently that \(P\) is the identity on its image. Then,
\[V = \text{ker } P \oplus \text{im } P.\]
Thus, we can think of \(P\) as projection onto the subspace \(\text{im } P\).
Proof. Let \(u \in V\). Suppose \(w \in \text{ker } P\) such that \(u = v + w\). This forces \(P(u) = P(v)\), and since \(P\) is idempotent \(v \in \text{im} V\). \( \blacksquare\)
This is fun because linear endomorphisms of finite-dimensional vector spaces are idempotent when raised to a power.
Lemma 2. Let \(V\) be a finite-dimensional vector space, and let \( T \colon V \longrightarrow V \) be a linear map. Let \(T^n\) denote \(T\) composed with itself \(n\) times. Then there is some \(N\) for which \(T^N\) is idempotent.
Proof. Notice that for each \(k\in \textbf{N}\), \(\text{im } T^{k+1} \subseteq \text{im }T^k\). Hence, \(\text{dim } \text{im } T^{k+1} \leq \text{dim } \text{im } T^k\). Since \(V\) is finite-dimensional, there is some \(m\) such that \(\text{dim } \text{im } T^m\) is minimal.
Now, the restriction of \(T^{m^j}\) on \(\text{im } T^m\), where \(j \in \mathbf{N}\), is an isomorphism. Thus, for any basis of \(\text{im } T^m\), it gets permuted by \(T^{m^j}\), implying the existence of some \(j\) for which \(T^{m^j}\) is the identity on \(\text{im } T^m\), and \(N = m^j\) works. \( \blacksquare \)
Combining this result with the previous one, we get
Theorem 3. Let \(V\) be a vector space and \(T \colon V \longrightarrow V\) a linear map. Then there is an \(N \in \textbf{N}\) such that
\[V = \text{im } T^N \oplus \text{ker } T^N.\]
8 notes
·
View notes
Text
using the word “idempotent” on a work call while slightly buzzed i might be the goat
5 notes
·
View notes
Text
Idempotent in Computing: A Comprehensive Guide

In the realms of computer science and software engineering, certain concepts and principles play crucial roles in ensuring systems' robustness, reliability, and predictability. One such concept is idempotency, a term that, while seemingly esoteric, has profound implications in various areas, including web services, databases, and functional programming. This article delves into the definition, importance, and practical applications of idempotency, aiming to provide a comprehensive understanding of its role in modern computing.
What is Idempotency?
Idempotency is a property of certain operations that denotes their ability to be applied multiple times without changing the result beyond the initial application. Formally, an operation fff is idempotent if, for all inputs xxx, applying fff to xxx multiple times yields the same result as applying fff once. Mathematically, this is represented as:
f(f(x))=f(x)f(f(x)) = f(x)f(f(x))=f(x)
This definition implies that no matter how many times the operation is executed, the outcome remains constant after the first application.
The Importance of Idempotency
The significance of idempotency in computing can be appreciated across various dimensions:
Reliability: Idempotent operations ensure that systems can handle retries gracefully. In distributed systems, where network failures and partial system failures are common, retrying operations without fearing unintended consequences is crucial.
Safety: In web services, making HTTP requests idempotent means that if a client sends the same request multiple times, the server's state remains unchanged after the first request. This is particularly important for operations like payment processing or resource creation.
Consistency: Idempotency helps maintain data consistency. For instance, in database operations, an idempotent transaction can be retried multiple times in the event of a failure, ensuring that the database remains in a consistent state.
Simplicity: Idempotent operations simplify error handling logic. Since the result of applying an operation multiple times does not change, developers can avoid complex checks and conditions in their code.
Idempotency in Web Services
Idempotency is a critical concept in the design of RESTful web services. The HTTP specification defines certain methods as idempotent:
GET: This method is inherently idempotent, as it is used to retrieve resources without modifying them.
PUT: Used to update or create resources, PUT requests are idempotent because applying the same update multiple times does not change the resource state beyond the initial application.
DELETE: While logically idempotent (deleting a resource that is already deleted does not change the state), it can have side effects such as triggering notifications.
HEAD and OPTIONS: These methods are also idempotent as they are used for metadata retrieval and preflight requests, respectively.
Implementing Idempotency
The implementation of idempotency depends on the context and specific requirements of the operation. Here are some common strategies:
Idempotency Keys: For operations like resource creation or transaction processing, clients can generate unique idempotency keys. The server stores these keys and the results of the operations. Subsequent requests with the same key return the stored result without re-executing the operation.
Resource Versioning: In update operations, using versioning can ensure idempotency. Clients include the resource version in their requests, and the server only applies changes if the version matches the current state.
Conditional Requests: HTTP provides mechanisms like If-Match and If-None-Match headers to make requests conditional. This can help ensure that operations are applied only when certain conditions are met, thus maintaining idempotency.
State Checks: Before performing an operation, the system can check the current state to determine if the operation has already been applied. This is common in systems where the state can be queried efficiently.
Idempotency in Functional Programming
In functional programming, idempotency is often associated with pure functions. A pure function, by definition, does not produce side effects and always returns the same result given the same input. While not all pure functions are idempotent, idempotency is a valuable property in the context of functional programming because it ensures predictability and reliability.
For example, consider a function that sanitizes input strings by removing whitespace:
haskell
Copy code
sanitize :: String -> String
sanitize = trim . replaceMultipleSpaces
-- Assuming 'trim' and 'replaceMultipleSpaces' are both idempotent functions
If both trim and replaceMultipleSpaces are idempotent, then sanitize is also idempotent. Applying sanitize multiple times to the same input string yields the same result as applying it once.
Challenges and Considerations
While idempotency offers numerous benefits, implementing it can be challenging. Some operations are inherently non-idempotent, such as generating unique identifiers or processing user input that changes with each request. In such cases, ensuring idempotency requires careful design and often involves trade-offs.
Moreover, idempotency can have performance implications. For example, maintaining idempotency keys or resource versions might require additional storage and processing overhead. Balancing these costs with the benefits of idempotency is a critical consideration in system design.
Conclusion
Idempotency is a fundamental concept that enhances the reliability, safety, and simplicity of computing systems. By ensuring that operations can be repeated without unintended consequences, idempotency plays a crucial role in the robustness of web services, the consistency of databases, and the predictability of functional programming. Understanding and implementing idempotency effectively can significantly improve system design and operation, making it an indispensable tool in the arsenal of software engineers and computer scientists.
0 notes
Note
Is your transition idempotent?
Hmm, this is a fascinating question!
I think I gotta say no. I consider myself rather fluid, if I did this again I think I would be unlikely to turn out exactly the same – heck I haven't even chosen a single name yet! I can very easily see myself “transitioning” again into a different version of me, whether or not my gender changes with that.
On a deeper level though, what does it mean for a process that is still ongoing and has no clearly defined result or ending to be idempotent? In a sense my transition will never end, it's idempotence is unknowable because it's not a well defined operation.
It is probably converging I guess, as my transition continues I'll find myself trending towards the best version of me until it essentially becomes idempotent.
2 notes
·
View notes
Text
Migrating Virtual Machines to Red Hat OpenShift Virtualization with Ansible Automation Platform
In today’s hybrid cloud environments, organizations are increasingly looking to modernize their infrastructure by moving traditional VMs into Kubernetes-native platforms. Red Hat OpenShift Virtualization (OSV) bridges the gap between legacy virtualization and modern containerized workloads. When paired with Red Hat Ansible Automation Platform, this migration becomes not only scalable but also repeatable and reliable.
In this blog, we’ll explore how to migrate Virtual Machines (VMs) to Red Hat OpenShift Virtualization using Ansible Automation Platform, and why this combination is the key to infrastructure modernization.
🧩 Why Migrate to OpenShift Virtualization?
OpenShift Virtualization allows you to run and manage VMs alongside containers, enabling consistent operations and a unified control plane. Key benefits include:
Unified Kubernetes-native management for VMs and containers.
Reduced licensing costs from traditional hypervisors.
Faster modernization and DevOps integration for legacy apps.
Policy-based automation and enhanced observability.
🛠️ What is Red Hat Ansible Automation Platform’s Role?
Migrating VMs is not a one-click job—it involves:
VM discovery and inventory.
Pre-migration checks and network mappings.
VM image conversion and storage migration.
Deployment and post-migration validation.
Ansible Automation Platform provides:
Idempotent playbooks to handle each stage reliably.
Integration with Red Hat tools (e.g., RHV, vSphere, OpenShift).
Event-driven workflows and role-based execution.
Automation analytics for reporting and auditing.
🔁 End-to-End Migration Workflow
1️⃣ Inventory & Discovery
Start by creating an inventory of VMs from your source virtualization platform (like VMware vSphere or RHV). Ansible modules for VMware (community.vmware) or RHV (ovirt.ovirt) help gather data:
yaml
- name: Gather VMs from VMware community.vmware.vmware_vm_info: hostname: "{{ vcenter_host }}" username: "{{ vcenter_user }}" password: "{{ vcenter_pass }}"
2️⃣ Pre-Migration Assessment
Use Ansible to check:
VM specs and OS compatibility
Network and storage mapping
Existing dependencies or hardcoded IPs
3️⃣ VM Image Conversion
Convert VMDK or QCOW2 images using virt-v2v or qemu-img. Ansible can automate this process with shell modules and custom roles.
yaml
- name: Convert VM disk to QCOW2 ansible.builtin.shell: | qemu-img convert -f vmdk -O qcow2 /source/disk.vmdk /target/disk.qcow2
4️⃣ Create VM in OpenShift Virtualization
Using the kubevirt Ansible collection or OpenShift’s REST API, define the VM as a Kubernetes Custom Resource (VirtualMachine):
yaml
- name: Deploy VM to OpenShift Virtualization kubernetes.core.k8s: state: present definition: "{{ lookup('template', 'vm_template.yml') }}"
Your YAML should define the VM’s CPU, memory, disk, and network.
5️⃣ Post-Migration Validation
Automate the validation steps:
VM boot success
Service health check
DNS and network connectivity
With Ansible’s uri module or command, verify services inside the migrated VM:
yaml
- name: Check HTTP service on VM uri: url: http://{{ vm_ip }}:80 return_content: yes status_code: 200
🧠 Tips for Production-Grade Migrations
Use Ansible Tower or AAP Controller for visual workflows and RBAC.
Enable event-driven automation to react to migration success/failures.
Monitor VM performance post-migration using OpenShift Monitoring stack.
Include rollback strategies in playbooks in case of issues.
🎯 Conclusion
Migrating VMs to OpenShift Virtualization is a strategic move toward unified, cloud-native infrastructure. But without automation, it can be error-prone and time-consuming.
By leveraging Ansible Automation Platform, organizations can transform VM migrations into standardized, repeatable processes—reducing risk, increasing speed, and simplifying operations.
For more details www.hawkstack.com
0 notes
Text
Jalaska Jawaii Jashington Joregon Jalifornia Jevada Jarizona Jidaho Jyoming Jontana Jolarado Jew Mexico ...Jexico? oh i forgot Jutah Jorth Dakota/Jouth Dakota/Jakota Jiowa Jebraska Jansas Joklahoma Jexas Jouisiana Jarkansas Jissouri Jillinois Jisconsin Jinnesota (and tonic!) Jichigan Jindiana Johio Jentucky Jennessee Jississippi Jalabama Jorida Jeorgia (that's basically the same) Jarolina (Jorth and Jouth) Jirginia Jest Virginia Jaryland Jelaware Jennsylvania Jersey (yeah we're dropping the "new" after this point b/c it was only funny once. so. IDEMPOTENCE UNLOCKED) Jork Jermont Jampshire Jonnecticut Jhode Island Jassachusetts (already called out) Jaine

HAD TO ITERATE THROUGH EVERY STATE BUT I FINALLY FIGURED OUT WHO THIS IS VAGUING ABOUT
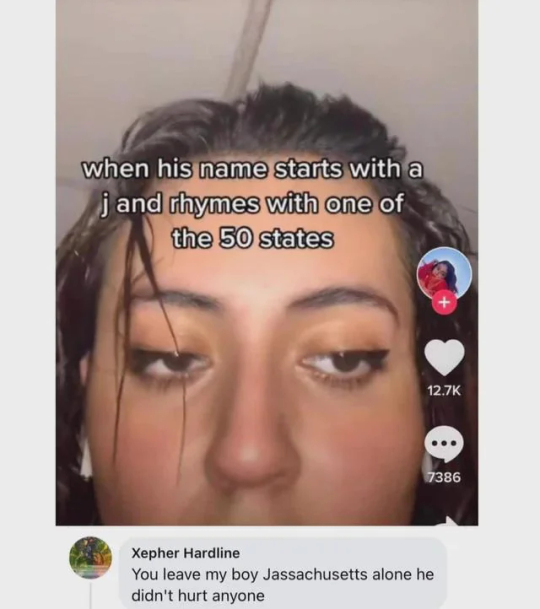
#shitpost#as people have said in the notes it's probably 'Jordan' and tiktok OP is using a slangy pronunciation of 'Oregon'#us states#long post#names#firefly#runners up: Jistrict of Jolumbia. Juerto Rico. Jamerican Jamoa. Juam. uhh probably more
18K notes
·
View notes
Text
RESTFUL API DESIGN
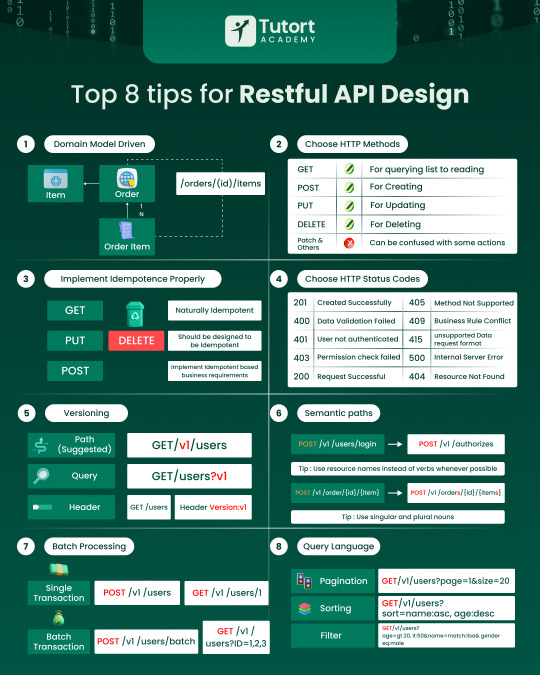
🚀 Designing robust APIs is more than just choosing the right method—it's about clarity, scalability, and consistency.
Here are Top 8 tips for RESTful API Design by Tutort Academy that every developer should bookmark! From proper versioning and semantic paths to smart use of status codes and idempotent operations, these practices ensure your API remains clean, predictable, and easy to maintain🌐💡 ✅ Domain-Driven Design ✅ Proper HTTP Methods ✅ Idempotence ✅ Meaningful Status Codes ✅ Versioning Best Practices ✅ Semantic & Clean URLs ✅ Batch Operations ✅ Smart Querying
Whether you're building your first API or scaling your architecture, following these best practices can make all the difference🧑💻
0 notes
Text
10 Life-Saving Yocto Tips, Tricks & Commands Every Developer Should Know
As embedded engineers, we know that Yocto is unmatched for building custom Linux distributions. But it’s also notoriously complex—small oversights can derail your entire build. Whether you're debugging u-boot, optimizing build time, or managing dependencies, these 10 advanced (non-generic) tips can be a game-changer in your daily Yocto workflow. They're pulled straight from the trenches—tested, impactful, and engineered to save your sanity.
1. 🔍 Use Devshell to Troubleshoot Complex Recipes
Command: bitbake u-boot -c devshell Launch an environment with all patches applied. Great for running commands like make menuconfig or tweaking u-boot/kernel directly. 👉 Speeds up debugging drastically. ⚠️ Be in the right build directory, and close the terminal after use.
2. ♻️ Invalidate sstate Cache for a True Rebuild
Sometimes the sstate cache doesn’t detect upstream changes. A quick comment tweak can trigger a rebuild:- # Package task + # Package task (force rebuild)
👉 Ensures your changes reflect in production builds. ⚠️ Use sparingly to avoid long rebuilds.
3. 🔗 Visualize Dependencies with Graphviz
Command:bitbake -g core-image-minimal dot -Tpng recipe-depends.dot -o dependencies.png
Explore recipe-depends.dot to analyze dependency chains. 👉 Crucial for resolving weird build issues. ⚠️ Keep focus—graphs can get heavy!
4. ⚡ Use Local Sources for Fast Dev Cycles
Add to conf/local.conf:INHERIT += "externalsrc" EXTERNALSRC_pn-yourpkg = "/local/path"
Edit code directly without constant patching. 👉 Game-changer for rapid driver or app iteration. ⚠️ Not ideal for final production images.
5. 🛠️ Automate with Post-Install Scripts
In your .bb recipe:pkg_postinst_${PN}() { cp /foo/bar.conf /etc/bar.conf systemctl enable my-service }
👉 Saves time by automating config and service setup. ⚠️ Ensure it's idempotent to avoid bricking the rootfs.
6. 🔍 Discover Layers Instead of Reinventing
Browse: https://layers.openembedded.org Find community-maintained layers like meta-qt5, meta-raspberrypi, etc. 👉 Cuts weeks off dev time. ⚠️ Double-check layer compatibility with your Yocto release.
7. 📁 Access Recipe Files Using FILESEXTRAPATHS
FILESEXTRAPATHS_prepend := "${THISDIR}/files:" SRC_URI += "file://your.conf"
👉 Keeps your recipes neat while bundling needed configs/patches. ⚠️ Ensure all referenced files exist—build will fail otherwise.
8. 🧰 Add Dev Packages to Your SDK
IMAGE_INSTALL_append = " cppzmq-dev" TOOLCHAIN_TARGET_TASK_append = " cppzmq-dev"
Also, modify SDK meta files if needed. 👉 Makes cross-compilation seamless. ⚠️ Check licenses before shipping SDKs externally.
9. 🚀 Speed Up Builds with Parallelization
In conf/local.conf:BB_NUMBER_THREADS = "8" PARALLEL_MAKE = "-j 8"
👉 Dramatically reduces build time on multi-core machines. ⚠️ Don’t max out your system—monitor memory and CPU usage.
10. 🐞 Troubleshoot Like a Pro with Verbose Logs
bitbake -v -D core-image-minimal bitbake -v -D log.domains=bb.fetch core-image-minimal
👉 Cuts down root-cause hunt time. ⚠️ Logs can get huge—redirect output to a file when needed.
🔁 Bonus: Debug Shared State with .siginfo Files
bitbake --dump-signatures core-image-minimal bitbake-diffsigs file1.siginfo file2.siginfo
Understand why sstate reuse fails by comparing task signatures. 👉 Fixes mysterious rebuild issues. ⚠️ Requires understanding of Python pickled data.
🚨 These Tips Save Time, Effort & Frustration
✅ Faster debugging (devshell, verbose logs, siginfo)
✅ Shorter dev cycles (externalsrc, parallel builds)
✅ Fewer bugs (dependency graphs, cache invalidation)
✅ Cleaner customization (postinst scripts, recipe file handling)
🔧 Working with Yocto?
Let Silicon Signals help you with custom BSPs, embedded Linux builds, and Yocto-based product development. Whether it's board bring-up, device driver integration, or image optimization—we’ve got you covered.
👉 DM us or drop a message to explore how we can support your Yocto needs! or Mail us on [email protected]
www.siliconsignals.io
#YoctoProject#EmbeddedLinux#BSPDevelopment#OpenEmbedded#BitBake#EmbeddedSystems#SiliconSignals#LinuxForDevices#FirmwareEngineering#TechTips
0 notes
Text
idempotency
when youre married its always same sex. because when youre haveing sex. youre both havving the same sex. 👍🏻
2K notes
·
View notes
Text
How to implement idempotent APIs in ASP.NET Core
When designing your APIs, you should make them idempotent to ensure that they are robust, reliable, and fault-tolerant. An operation is idempotent when repeating it will always result in the same outcome. For example, an elevator button is idempotent. No matter how many times you press the same elevator button, the elevator will make one trip to the designated floor. Your APIs should work the…
0 notes