#it infrastructure monitoring software
Explore tagged Tumblr posts
Text
Top 5 IT Infrastructure Monitoring Tools to Boost Your Business Performance
IT infrastructure monitoring provides insight into the overall health of your project. By collecting and analyzing data from IT infrastructure, systems, and processes, you may prevent issues, analyze performance, better optimize and scale, or identify the underlying cause of everything that occurs within your system. The world is getting increasingly digital every day. This puts pressure on…

View On WordPress
#business#Business Intelligence#Information Technology#infrastructure#IT infrastructure monitoring#it infrastructure monitoring software#IT infrastructure monitoring tools#IT infrastructure security#it monitoring systems#it network monitoring#ITIM#ITIM tools#monitoring system it#technology
0 notes
Text
MeshTek’s Smart IoT Framework: Building the Future of Connected Systems

MeshTek’s advanced IoT development service in action — where powerful software meets real-time automation. From smart connectivity to integrated mesh-based communication, the setup represents how businesses can monitor, manage, and optimize connected devices through a seamless, intelligent platform. The background workspace and digital overlays highlight MeshTek’s vision for scalable, secure, and low-latency IoT ecosystems designed for the modern world.
#MeshTek#IoT development service#Bluetooth mesh IoT#connected devices#smart automation#real-time IoT monitoring#low-latency communication#industrial IoT platform#smart infrastructure#scalable IoT systems#IoT software development#next-gen connectivity#AI-powered IoT#secure IoT network#edge computing solutions#smart business automation#intelligent IoT services#future-ready technology#MeshTek solutions#IoT mesh technology
0 notes
Text
#Network Performance Monitoring Market#Network Monitoring Solutions#Market Research Report#IT Infrastructure Monitoring#Network Performance Management#Cloud Network Monitoring#Network Optimization Tools#Market Size and Forecast#Network Security and Performance#Real-Time Network Monitoring#Competitive Landscape#Network Analytics and Insights#Emerging Trends in Network Monitoring#Software-Defined Networking (SDN) Monitoring#Network Troubleshooting Tools#Global Network Monitoring Market#AI in Network Performance Monitoring#Network Performance for Enterprises#5G Network Monitoring#Network Health and Diagnostics
0 notes
Text
GIS-Based Solutions for Efficient Telecom Network Management
The telecom industry is undergoing rapid transformation, driven by the increasing demand for seamless connectivity, efficient network management, and improved customer experience. As networks become more complex, the need for innovative solutions to manage these networks has never been greater. Geographic Information System (GIS)-based solutions have emerged as a game-changer in the telecom sector, offering a robust platform for managing, analyzing, and visualizing network data. This blog explores how GIS-based solutions can revolutionize telecom network management, ensuring efficiency and reliability.
Learn more at https://www.cyberswift.com/blog/telecom-utility-solution-a-brief-overview/

#gis for 5g network planning#telecom network monitoring with gis#gis for telecom service coverage analysis#gis enabled telecom site selection#gis mapping for telecom connectivity#gis solutions for managing telecom utilities#role of gis in telecom infrastructure planning#telecom utility gis software for asset management#gis technology for fiber optic network design#geospatial analytics for telecom network optimization#telecom asset management system#gis telecom utility software#fiber optic network mapping#gis based telecom service optimization#telecom network visualization tools#utility network analysis in telecom#geospatial solutions for telecom utilities
0 notes
Text

Gold Standard Service Founded on the Golden Rule
Auxiom is your trusted partner on your technology journey, guided by the Golden Rule.
We provide IT and Cybersecurity Services and Support for businesses, organizations, and State and Local Government and educational institutions (SLED).
What do we mean by "Outsmart Chaos"? We know that for every one problem that gets solved in the world of IT, there always seems to be several more threats. We work to stay ahead of them all with a smarter, more proactive approach.
Managed IT Managing every aspect of IT is incredibly complex, so hiring the right IT partner is critical to the success of your business.
Cybersecurity Protecting your assets, from servers all the way to individual files, is a multi-layered and potentially complicated task.
IT Projects & Consulting Make every IT investment count. Auxiom works with you to plan, design, and implement IT projects to meet your needs.
Auxiom is an E-Rate Certified service provider.
#software#servers#securityconsulting#MANAGEDSERVICES#ITServices#ITSecurity#ITHardware#IT Department monitoring#infrastructure#cybersecurity#Consulting#BusinessContinuityServices
0 notes
Text
IT Infrastructure Monitoring & Network Security Software
At Techsa Services Pvt. Ltd., their mission is to diligently monitor, expertly manage, meticulously analyze, and unwaveringly secure the customer's IT infrastructure. Through their dedicated efforts and innovative solutions, they ensure comprehensive protection, performance, and strategic insights related to the hybrid IT infrastructure. Contact them to learn more about their services!
0 notes
Text
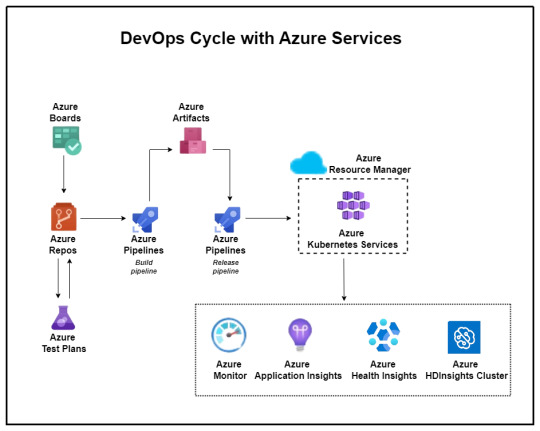
Driving Innovation: A Case Study on DevOps Implementation in BFSI Domain
Banking, Financial Services, and Insurance (BFSI), technology plays a pivotal role in driving innovation, efficiency, and customer satisfaction. However, for one BFSI company, the journey toward digital excellence was fraught with challenges in its software development and maintenance processes. With a diverse portfolio of applications and a significant portion outsourced to external vendors, the company grappled with inefficiencies that threatened its operational agility and competitiveness. Identified within this portfolio were 15 core applications deemed critical to the company’s operations, highlighting the urgency for transformative action.
Aspirations for the Future:
Looking ahead, the company envisioned a future state characterized by the establishment of a matured DevSecOps environment. This encompassed several key objectives:
Near-zero Touch Pipeline: Automating product development processes for infrastructure provisioning, application builds, deployments, and configuration changes.
Matured Source-code Management: Implementing robust source-code management processes, complete with review gates, to uphold quality standards.
Defined and Repeatable Release Process: Instituting a standardized release process fortified with quality and security gates to minimize deployment failures and bug leakage.
Modernization: Embracing the latest technological advancements to drive innovation and efficiency.
Common Processes Among Vendors: Establishing standardized processes to enhance understanding and control over the software development lifecycle (SDLC) across different vendors.
Challenges Along the Way:
The path to realizing this vision was beset with challenges, including:
Lack of Source Code Management
Absence of Documentation
Lack of Common Processes
Missing CI/CD and Automated Testing
No Branching and Merging Strategy
Inconsistent Sprint Execution
These challenges collectively hindered the company’s ability to achieve optimal software development, maintenance, and deployment processes. They underscored the critical need for foundational practices such as source code management, documentation, and standardized processes to be addressed comprehensively.
Proposed Solutions:
To overcome these obstacles and pave the way for transformation, the company proposed a phased implementation approach:
Stage 1: Implement Basic DevOps: Commencing with the implementation of fundamental DevOps practices, including source code management and CI/CD processes, for a select group of applications.
Stage 2: Modernization: Progressing towards a more advanced stage involving microservices architecture, test automation, security enhancements, and comprehensive monitoring.
To Expand Your Awareness: https://devopsenabler.com/contact-us
Injecting Security into the SDLC:
Recognizing the paramount importance of security, dedicated measures were introduced to fortify the software development lifecycle. These encompassed:
Security by Design
Secure Coding Practices
Static and Dynamic Application Security Testing (SAST/DAST)
Software Component Analysis
Security Operations
Realizing the Outcomes:
The proposed solution yielded promising outcomes aligned closely with the company’s future aspirations. Leveraging Microsoft Azure’s DevOps capabilities, the company witnessed:
Establishment of common processes and enhanced visibility across different vendors.
Implementation of Azure DevOps for organized version control, sprint planning, and streamlined workflows.
Automation of builds, deployments, and infrastructure provisioning through Azure Pipelines and Automation.
Improved code quality, security, and release management processes.
Transition to microservices architecture and comprehensive monitoring using Azure services.
The BFSI company embarked on a transformative journey towards establishing a matured DevSecOps environment. This journey, marked by challenges and triumphs, underscores the critical importance of innovation and adaptability in today’s rapidly evolving technological landscape. As the company continues to evolve and innovate, the adoption of DevSecOps principles will serve as a cornerstone in driving efficiency, security, and ultimately, the delivery of superior customer experiences in the dynamic realm of BFSI.
Contact Information:
Phone: 080-28473200 / +91 8880 38 18 58
Email: [email protected]
Address: DevOps Enabler & Co, 2nd Floor, F86 Building, ITI Limited, Doorvaninagar, Bangalore 560016.
#BFSI#DevSecOps#software development#maintenance#technology stack#source code management#CI/CD#automated testing#DevOps#microservices#security#Azure DevOps#infrastructure as code#ARM templates#code quality#release management#Kubernetes#testing automation#monitoring#security incident response#project management#agile methodology#software engineering
0 notes
Text
i know everyone is really excited for the oblivion remake because i was too. oblivion was the first real video game i ever played when i was a kid, and is literally the reason i am a gamer today, but BDS has called for a microsoft boycott, and that includes anything made by bethesda.
this isn't just a "oh they have some obscure business partnerships in isr*el" or "oh they donate to this or that lobby" sort of boycott either, although those are important too. my tone is not meant to be flippant about them, but rather i want to emphasize the gravity of how microsoft directly and deliberately contributes to the palestinian death toll daily, in a way that is uniquely cruel and complicit.
microsoft has had a $35 million dollar contract with the isr*eli military since 2002. they provide cloud storage for surveillance data of gazan civillians, and an artificial intelligence program called a "mass assassination factory" to assist in planning and targeting their attacks, many of which are on civilians or involve mass civilian casualties.
microsoft's service agreements with the isr*eli military also includes the CPU responsible for the military's tech infrastructure, military intelligence units that develop spy technology used against palestinians and lebanese, the maintenance of the palestinian population registry that tracks and (illegally) limits the movement of palestinains in the west bank and gaza, their air force targeting database, and much more. they work closely with isr*eli military intelligence agencies on surveillance systems used to monitor palestians, provide specialized consulting, technical and engineering support, hosts training software for the IOF, provide financial support to organizations based in the illegally occupied west bank, and have repeatedly invested in isr*eli start ups specializing in war technology.
in 2020, internal and external pressure forced microsoft to pull out of its 74 million dollar investment in an isr*eli company that violated international law due to its use of facial recognition technology for military surveillance.
in 2021, microsoft signed a new, 3-year contract with the isr*eli ministry of defense worth $133 million dollars. the isr*eli military is microsoft's second largest military customer. the first? the united states.
you can read more (w/ sources) about microsoft's complicity here.
BDS asks us to boycott microsoft products whenever possible.

microsoft is directly complicit in countless isr*eli war crimes, and the money you provide them will further proliferate this violence. i know the oblivion remake was exciting, but please, consider the lives of palestinians above your own nostalgia. no one is free until everyone is free.
766 notes
·
View notes
Text
thoughts about the Cardassian writing system
I've thinking about the Cardassian script as shown on screen and in beta canon and such and like. Is it just me or would it be very difficult to write by hand?? Like.

I traced some of this image for a recent drawing I did and like. The varying line thicknesses?? The little rectangular holes?? It's not at all intuitive to write by hand. Even if you imagine, like, a different writing implement—I suppose a chisel-tip pen would work better—it still seems like it wasn't meant to be handwritten. Which has a few possible explanations.
Like, maybe it's just a fancy font for computers, and handwritten text looks a little different. Times New Roman isn't very easily written by hand either, right? Maybe the line thickness differences are just decorative, and it's totally possible to convey the same orthographic information with the two line thicknesses of a chisel-tip pen, or with no variation in line thickness at all.
A more interesting explanation, though, and the one I thought of first, is that this writing system was never designed to be handwritten. This is a writing system developed in Cardassia's digital age. Maybe the original Cardassian script didn’t digitize well, so they invented a new one specifically for digital use? Like, when they invented coding, they realized that their writing system didn’t work very well for that purpose. I know next to nothing about coding, but I cannot imagine doing it using Chinese characters. So maybe they came up with a new writing system that worked well for that purpose, and when computer use became widespread, they stuck with it.
Or maybe the script was invented for political reasons! Maybe Cardassia was already fairly technologically advanced when the Cardassian Union was formed, and, to reinforce a cohesive national identity, they developed a new standardized national writing system. Like, y'know, the First Emperor of Qin standardizing hanzi when he unified China, or that Korean king inventing hangul. Except that at this point in Cardassian history, all official records were digital and typing was a lot more common than handwriting, so the new script was designed to be typed and not written. Of course, this reform would be slower to reach the more rural parts of Cardassia, and even in a technologically advanced society, there are people who don't have access to that technology. But I imagine the government would be big on infrastructure and education, and would make sure all good Cardassian citizens become literate. And old regional scripts would stop being taught in schools and be phased out of digital use and all the kids would grow up learning the digital script.
Which is good for the totalitarian government! Imagine you can only write digitally. On computers. That the government can monitor. If you, like, write a physical letter and send it to someone, then it's possible for the contents to stay totally private. But if you send an email, it can be very easily intercepted. Especially if the government is controlling which computers can be manufactured and sold, and what software is in widespread use, etc.
AND. Historical documents are now only readable for scholars. Remember that Korean king that invented hangul? Before him, Korea used to use Chinese characters too. And don't get me wrong, hangul is a genius writing system! It fits the Korean language so much better than Chinese characters did! It increased literacy at incredible rates! But by switching writing systems, they broke that historical link. The average literate Chinese person can read texts that are thousands of years old. The average literate Korean person can't. They'd have to specifically study that field, learn a whole new writing system. So with the new generation of Cardassian youths unable to read historical texts, it's much easier for the government to revise history. The primary source documents are in a script that most people can't read. You just trust the translation they teach you in school. In ASIT it's literally a crucial plot point that the Cardassian government revised history! Wouldn't it make it soooo much easier for them if only very few people can actually read the historical accounts of what happened.
I guess I am thinking of this like Chinese characters. Like, all the different Chinese "dialects" being written with hanzi, even though otherwise they could barely be considered the same language. And even non-Sinitic languages that historically adopted hanzi, like Japanese and Korean and Vietnamese. Which worked because hanzi is a logography—it encodes meaning, not sound, so the same word in different languages can be written the same. It didn’t work well! Nowadays, Japanese has made significant modifications and Korean has invented a new writing system entirely and Vietnamese has adapted a different foreign writing system, because while hanzi could write their languages, it didn’t do a very good job at it. But the Cardassian government probably cares more about assimilation and national unity than making things easier for speakers of minority languages. So, Cardassia used to have different cultures with different languages, like the Hebitians, and maybe instead of the Union forcing everyone to start speaking the same language, they just made everyone use the same writing system. Though that does seem less likely than them enforcing a standard language like the Federation does. Maybe they enforce a standard language, and invent the new writing system to increase literacy for people who are newly learning it.
And I can imagine it being a kind of purely digital language for some people? Like if you’re living on a colonized planet lightyears away from Cardassia Prime and you never have to speak Cardassian, but your computer’s interface is in Cardassian and if you go online then everyone there uses Cardassian. Like people irl who participate in the anglophone internet but don’t really use English in person because they don’t live in an anglophone country. Except if English were a logographic writing system that you could use to write your own language. And you can’t handwrite it, if for whatever reason you wanted to. Almost a similar idea to a liturgical language? Like, it’s only used in specific contexts and not really in daily life. In daily life you’d still speak your own language, and maybe even handwrite it when needed. I think old writing systems would survive even closer to the imperial core (does it make sense to call it that?), though the government would discourage it. I imagine there’d be a revival movement after the Fire, not only because of the cultural shift away from the old totalitarian Cardassia, but because people realize the importance of having a written communication system that doesn’t rely on everyone having a padd and electricity and wifi.
#if I read over this again I will inevitably want to change and add things so I'm refraining from doing that. enjoy whatever this is#forgive my very crude recounting of chinese and korean history! I am neither a historian nor a linguist#but I will NOT apologize for talking abt china so much. that's my culture and I'm weird abt it bc of my family history#and it's my GOD GIVEN RIGHT to project what little I know abt it onto all my worldbuilding#also I've never actually read abt any of the various cardassian conlangs but I'm curious if this contradicts or coincides with any of them#I still want to make my own someday. starting college as a linguistics major (in 2 weeks!!) so presumably I will learn how to do that#narcissus's echoes#ds9#asit#star trek#cardassians#cardassian meta#a stitch in time#hebitians#lingposting
769 notes
·
View notes
Text
Vittoria Elliott at Wired:
Elon Musk’s takeover of federal government infrastructure is ongoing, and at the center of things is a coterie of engineers who are barely out of—and in at least one case, purportedly still in—college. Most have connections to Musk and at least two have connections to Musk’s longtime associate Peter Thiel, a cofounder and chairman of the analytics firm and government contractor Palantir who has long expressed opposition to democracy. WIRED has identified six young men—all apparently between the ages of 19 and 24, according to public databases, their online presences, and other records—who have little to no government experience and are now playing critical roles in Musk’s so-called Department of Government Efficiency (DOGE) project, tasked by executive order with “modernizing Federal technology and software to maximize governmental efficiency and productivity.” The engineers all hold nebulous job titles within DOGE, and at least one appears to be working as a volunteer. The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian, Gavin Kliger, and Ethan Shaotran. None have responded to requests for comment from WIRED. Representatives from OPM, GSA, and DOGE did not respond to requests for comment. Already, Musk’s lackeys have taken control of the Office of Personnel Management��(OPM) and General Services Administration (GSA), and have gained access to the Treasury Department’s payment system, potentially allowing him access to a vast range of sensitive information about tens of millions of citizens, businesses, and more. On Sunday, CNN reported that DOGE personnel attempted to improperly access classified information and security systems at the US Agency for International Development (USAID), and that top USAID security officials who thwarted the attempt were subsequently put on leave. The AP reported that DOGE personnel had indeed accessed classified material. “What we're seeing is unprecedented in that you have these actors who are not really public officials gaining access to the most sensitive data in government,” says Don Moynihan, a professor of public policy at the University of Michigan. “We really have very little eyes on what's going on. Congress has no ability to really intervene and monitor what's happening because these aren't really accountable public officials. So this feels like a hostile takeover of the machinery of governments by the richest man in the world.”
[...] “To the extent these individuals are exercising what would otherwise be relatively significant managerial control over two very large agencies that deal with very complex topics,” says Nick Bednar, a professor at University of Minnesota’s school of law, “it is very unlikely they have the expertise to understand either the law or the administrative needs that surround these agencies.” Sources tell WIRED that Bobba, Coristine, Farritor, and Shaotran all currently have working GSA emails and A-suite level clearance at the GSA, which means that they work out of the agency’s top floor and have access to all physical spaces and IT systems, according a source with knowledge of the GSA’s clearance protocols. The source, who spoke to WIRED on the condition of anonymity because they fear retaliation, says they worry that the new teams could bypass the regular security clearance protocols to access the agency’s sensitive compartmented information facility (SCIF), as the Trump administration has already granted temporary security clearances to unvetted people. This is in addition to Coristine and Bobba being listed as “experts” working at OPM. Bednar says that while staff can be loaned out between agencies for special projects or to work on issues that might cross agency lines, it’s not exactly common practice.
WIRED’s report on the 6 college-aged men between 19 and 24 that are shaping up DOGE in aiding and abetting in co-”President” Elon Musk’s technofascist takeover.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration II#General Services Administration#Office of Personnel Management#Scott Bessent#USAID#Akash Bobba#Edward Coristine#Luke Farritor#Gautier Cole Killian#Gavin Kliger#Ethan Shaotran#Treasury Department#Musk Coup
65 notes
·
View notes
Text
Elon Musk’s minions—from trusted sidekicks to random college students and former Musk company interns—have taken over the General Services Administration, a critical government agency that manages federal offices and technology. Already, the team is attempting to use White House security credentials to gain unusual access to GSA tech, deploying a suite of new AI software, and recreating the office in X’s image, according to leaked documents obtained by WIRED.
Some of the same people who helped Musk take over Twitter more than two years ago are now registered as official GSA employees. Nicole Hollander, who slept in Twitter HQ as an unofficial member of Musk’s transition team, has high-level agency access and an official government email address, according to documents viewed by WIRED. Hollander’s husband, Steve Davis, also slept in the office. He has now taken on a leading role in Musk’s Department of Government Efficiency (DOGE). Thomas Shedd, the recently installed director of the Technology Transformation Services within GSA, worked as a software engineer at Tesla for eight years. Edward Coristine, who previously interned at Neuralink, has been onboarded along with Ethan Shaotran, a Harvard senior who is developing his own OpenAI-backed scheduling assistant and participated in an xAI hackathon.
“I believe these people do not want to help the federal government provide services to the American people,” says a current GSA employee who asked not to be named, citing fears of retaliation. “They are acting like this is a takeover of a tech company.”
The team appears to be carrying out Musk’s agenda: slashing the federal government as quickly as possible. They’re currently targeting a 50 percent reduction in spending for every office managed by the GSA, according to documents obtained by WIRED.
There also appears to be an effort to use IT credentials from the Executive Office of the President to access GSA laptops and internal GSA infrastructure. Typically, access to agency systems requires workers to be employed at such agencies, sources say. While Musk's team could be trying to obtain better laptops and equipment from GSA, sources fear that the mandate laid out in the DOGE executive order would grant the body broad access to GSA systems and data. That includes sensitive procurement data, data internal to all the systems and services GSA offers, and internal monitoring software to surveil GSA employees as part of normal auditing and security processes.
The access could give Musk’s proxies the ability to remote into laptops, listen in on meetings, read emails, among many other things, a former Biden official told WIRED on Friday.
“Granting DOGE staff, many of whom aren't government employees, unfettered access to internal government systems and sensitive data poses a huge security risk to the federal government and to the American public,” the Biden official said. “Not only will DOGE be able to review procurement-sensitive information about major government contracts, it'll also be able to actively surveil government employees.”
The new GSA leadership team has prioritized downsizing the GSA’s real estate portfolio, canceling convenience contracts, and rolling out AI tools for use by the federal government, according to internal documents and interviews with sources familiar with the situation. At a GSA office in Washington, DC, earlier this week, there were three items written on a white board sitting in a large, vacant room. “Spending Cuts $585 m, Regulations Removed, 15, Square feet sold/terminated 203,000 sf,” it read, according to a photo viewed by WIRED. There’s no note of who wrote the message, but it appears to be a tracker of cuts made or proposed by the team.
“We notified the commercial real estate market that two GSA properties would soon be listed for sale, and we terminated three leases,” Stephen Ehikian, the newly appointed GSA acting administrator, said in an email to GSA staff on Tuesday, confirming the agency’s focus on lowering real estate costs. “This is our first step in right-sizing the real estate portfolio.”
The proposed changes extend even inside the physical spaces at the GSA offices. Hollander has requested multiple “resting rooms,” for use by the A-suite, a team of employees affiliated with the GSA administrator’s office.
On January 29, a working group of high-ranking GSA employees, including the deputy general counsel and the chief administrative services officer, met to discuss building a resting room prototype. The team mapped out how to get the necessary funding and waivers to build resting rooms in the office, according to an agenda viewed by WIRED.
After Musk bought Twitter, Hollander and Davis moved into the office with their newborn baby. Hollander helped oversee real estate and office design—including the installation of hotel rooms at Twitter HQ, according to a lawsuit later filed by Twitter executives. During the installation process, one of the executives emailed to say that the plans for the rooms were likely not code compliant. Hollander “visited him in person and emphatically instructed him to never put anything about the project in writing again,” the lawsuit alleged. Employees were allegedly instructed to call the hotel rooms “sleeping rooms” and to say they were just for taking naps.
Hollander has also requested access to Public Buildings Service applications; PBS owns and leases office space to government agencies. The timing of the access request lines up with Ehikian’s announcement about shrinking GSA’s real estate cost.
Musk’s lieutenants are also working to authorize the use of AI tools, including Google Gemini and Cursor (an AI coding assistant), for federal workers. On January 30, the group met with Google to discuss Telemetry, a software used to monitor the health and performance of applications, according to a document obtained by WIRED.
A-suite engineers, including Coristine and Shaotran, have requested access to a variety of GSA records, including nearly 10 years of accounting data, as well as detailed records on vendor payments, purchase orders, and revenue.
The GSA takeover mimics Musk’s strategy at other federal agencies like the Office of Personnel Management (OPM). Earlier this month, Amanda Scales, who worked in talent at Musk’s xAI, was appointed as OPM chief of staff. Riccardo Biasini, former Tesla engineer and director of operations at the Boring company, is now a senior adviser to the director. Earlier this week, Musk cohorts at the US Office of Personnel Management emailed more than 2 million federal workers offering “deferred resignations,” allegedly promising employees their regular pay and benefits through September 30.
The email closely mirrored the “extremely hardcore” note Musk sent to Twitter staff in November 2022, shortly after buying the company.
Many federal workers thought the email was fake—as with Twitter, it seemed designed to force people to leave, slashing headcount costs without the headache of an official layoff.
Ehikian followed up with a note to staff stressing that the email was legitimate. “Yes, the OPM email is real and should be taken very seriously,” he said in an email obtained by WIRED. He added that employees should expect a “further consolidation of offices and centralization of functions.”
On Thursday night, GSA workers received a third email related to the resignation request called “Fork in the Road FAQs.” The email explained that employees who resign from their positions would not be required to work and could get a second job. “We encourage you to find a job in the private sector as soon as you would like to do so,” it read. “The way to greater American prosperity is encouraging people to move from lower productivity jobs in the public sector to higher productivity jobs in the private sector.”
The third question posed in the FAQ asked, “Will I really get my full pay and benefits during the entire period through September 30, even if I get a second job?”
“Yes,” the answer read. “You will also accrue further personal leave days, vacation days, etc. and be paid out for unused leave at your final resignation date.”
However, multiple GSA employees have told WIRED that they are refusing to resign, especially after the American Federation of Government Employees (AFGE) told its members on Tuesday that the offer could be void.
“There is not yet any evidence the administration can or will uphold its end of the bargain, that Congress will go along with this unilateral massive restructuring, or that appropriated funds can be used this way, among other issues that have been raised,” the union said in a notice.
There is also concern that, under Musk’s influence, the federal government might not pay for the duration of the deferred resignation period. Thousands of Twitter employees have sued Musk alleging that he failed to pay their agreed upon severance. Last year, one class action suit was dismissed in Musk’s favor.
In an internal video viewed by WIRED, Ehikian reiterated that GSA employees had the “opportunity to participate in a deferred resignation program,” per the email sent by OPM on January 28. Pressing his hands into the namaste gesture, Ehikian added, “If you choose to participate, I offer you my heartfelt gratitude for your service to this nation. If you choose to stay at the GSA, we’ll work together to implement the four pillars from the OPM memo.” He ended the video by saying thank you and pressing his hands into namaste again.
52 notes
·
View notes
Text
New Contractor Announcement ✨
Friends, please welcome our new contractor and first-official-sysadmin, Kat 🎉
Kat is not only a long-term member of Fandom Coders, but a prolific self-hoster of fandom software, and we're SO excited to have her aid in our quest!
Over the next few months Kat will work on getting our servers in order: from backing up our data, to setting up monitoring of our resources (no more accidental 20GB log file), to much needed "service down!" alerts. She'll also help us set up infrastructure for future services!
This is Kat's first professional experience as a sysadmin, and a huge step in our mission to create opportunities for members of the fandom community!
If you'd like to join us, we're looking for writers, technical and not! Drop your contact in our form 👇⬇️👇
And if you'd like to give *your* aid to our mission of creating professional opportunities for software hobbyists (and beyond) in our community, ESPECIALLY now that being a junior in tech is so incredibly hard, support us on Patreon!
Help us help them help the web!!
(Last thing, to get ahead of potential questions about Kat's TOS banning certain content from her sites: we talked extensively about her stance on issues dear to fandom, and we're comfortable with where she stands. Likewise, we stand by her right to choose what she's personally comfortable hosting.)
19 notes
·
View notes
Text
Revolutionising Road Construction with Technology: Enhancing Project Management for a Smarter Future
The road construction industry plays a vital role in shaping modern infrastructure, driving economic growth, and ensuring efficient transportation networks. However, it faces persistent challenges, including project delays, safety risks, cost overruns, and inefficient resource management. As construction projects grow in complexity, the need for innovative solutions to boost productivity and efficiency has never been more critical.
Learn more https://www.cyberswift.com/blog/revolutionising-road-construction-with-technology-enhancing-project-management-for-a-smarter-future/

#road construction monitoring software#road project tracking system#csrmonitoringsoftware#road construction progress tracking#gis based road monitoring system#road construction management software#real time road project monitoring#road construction tracking application#construction project tracking system#road project progress monitoring#road asset management software#road construction analytics tools#road infrastructure monitoring system#construction monitoring software for roads#road project planning software#digital road project monitoring system#smart road monitoring solutions#road construction quality monitoring#road project performance tracking#road mapping and monitoring software
0 notes
Text
The Trump administration is working on a plan to save TikTok that involves tapping software company Oracle and a group of outside investors to effectively take control of the app's global operations, according to two people with direct knowledge of the talks. Under the deal now being negotiated by the White House, TikTok's China-based owner ByteDance would retain a minority stake in the company, but the app's algorithm, data collection and software updates will be overseen by Oracle, which already provides the foundation of TikTok's web infrastructure. Thatwould effectively mean American investors would own a majority stake in TikTok, butthe terms of the deal could change and are still being hammered out. "The goal is for Oracle to effectively monitor and provide oversight with what is going on with TikTok," said the person directly involved in the talks, who was not authorized to speak publicly about the deliberations. "ByteDance wouldn't completely go away, but it would minimize Chinese ownership."
15 notes
·
View notes
Text
NEW DELHI (Reuters) -Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require manufacturers of CCTV cameras to submit hardware, software and source code for assessment in government labs, official documents and company emails show.
The security-testing policy has sparked industry warnings of supply disruptions and added to a string of disputes between Prime Minister Narendra Modi's administration and foreign companies over regulatory issues and what some perceive as protectionism.
New Delhi's approach is driven in part by its alarm about China's sophisticated surveillance capabilities, according to a top Indian official involved in the policymaking. In 2021, Modi's then-junior IT minister told parliament that 1 million cameras in government institutions were from Chinese companies and there were vulnerabilities with video data transferred to servers abroad.
Under the new requirements applicable from April, manufacturers such as China's Hikvision, Xiaomi and Dahua, South Korea's Hanwha, and Motorola Solutions of the U.S. must submit cameras for testing by Indian government labs before they can sell them in the world's most populous nation. The policy applies to all internet-connected CCTV models made or imported since April 9.
"There's always an espionage risk," Gulshan Rai, India's cybersecurity chief from 2015 to 2019, told Reuters. "Anyone can operate and control internet-connected CCTV cameras sitting in an adverse location. They need to be robust and secure."
Indian officials met on April 3 with executives of 17 foreign and domestic makers of surveillance gear, including Hanwha, Motorola, Bosch, Honeywell and Xiaomi, where many of the manufacturers said they weren't ready to meet the certification rules and lobbied unsuccessfully for a delay, according to the official minutes.
In rejecting the request, the government said India's policy "addresses a genuine security issue" and must be enforced, the minutes show.
India said in December the CCTV rules, which do not single out any country by name, aimed to "enhance the quality and cybersecurity of surveillance systems in the country."
This report is based on a Reuters review of dozens of documents, including records of meetings and emails between manufacturers and Indian IT ministry officials, and interviews with six people familiar with India's drive to scrutinize the technology. The interactions haven't been previously reported.
Insufficient testing capacity, drawn-out factory inspections and government scrutiny of sensitive source code were among key issues camera makers said had delayed approvals and risked disrupting unspecified infrastructure and commercial projects.
"Millions of dollars will be lost from the industry, sending tremors through the market," Ajay Dubey, Hanwha's director for South Asia, told India's IT ministry in an email on April 9.
The IT ministry and most of the companies identified by Reuters didn't respond to requests for comment about the discussions and the impact of the testing policy. The ministry told the executives on April 3 that it may consider accrediting more testing labs.
Millions of CCTV cameras have been installed across Indian cities, offices and residential complexes in recent years to enhance security monitoring. New Delhi has more than 250,000 cameras, according to official data, mostly mounted on poles in key locations.
The rapid take-up is set to bolster India's surveillance camera market to $7 billion by 2030, from $3.5 billion last year, Counterpoint Research analyst Varun Gupta told Reuters.
China's Hikvision and Dahua account for 30% of the market, while India's CP Plus has a 48% share, Gupta said, adding that some 80% of all CCTV components are from China.
Hanwha, Motorola Solutions and Britain's Norden Communication told officials by email in April that just a fraction of the industry's 6,000 camera models had approvals under the new rules.
CHINA CONCERN
The U.S. in 2022 banned sales of Hikvision and Dahua equipment, citing national security risks. Britain and Australia have also restricted China-made devices.
Likewise, with CCTV cameras, India "has to ensure there are checks on what is used in these devices, what chips are going in," the senior Indian official told Reuters. "China is part of the concern."
China's state security laws require organizations to cooperate with intelligence work.
Reuters reported this month that unexplained communications equipment had been found in some Chinese solar power inverters by U.S. experts who examined the products.
Since 2020, when Indian and Chinese forces clashed at their border, India has banned dozens of Chinese-owned apps, including TikTok, on national security grounds. India also tightened foreign investment rules for countries with which it shares a land border.
The remote detonation of pagers in Lebanon last year, which Reuters reported was executed by Israeli operatives targeting Hezbollah, further galvanized Indian concerns about the potential abuse of tech devices and the need to quickly enforce testing of CCTV equipment, the senior Indian official said.
The camera-testing rules don't contain a clause about land borders.
But last month, China's Xiaomi said that when it applied for testing of CCTV devices, Indian officials told the company the assessment couldn't proceed because "internal guidelines" required Xiaomi to supply more registration details of two of its China-based contract manufacturers.
"The testing lab indicated that this requirement applies to applications originating from countries that share a land border with India," the company wrote in an April 24 email to the Indian agency that oversees lab testing.
Xiaomi didn't respond to Reuters queries, and the IT ministry didn't address questions about the company's account.
China's foreign ministry told Reuters it opposes the "generalization of the concept of national security to smear and suppress Chinese companies," and hoped India would provide a non-discriminatory environment for Chinese firms.
LAB TESTING, FACTORY VISITS
While CCTV equipment supplied to India's government has had to undergo testing since June 2024, the widening of the rules to all devices has raised the stakes.
The public sector accounts for 27% of CCTV demand in India, and enterprise clients, industry, hospitality firms and homes the remaining 73%, according to Counterpoint.
The rules require CCTV cameras to have tamper-proof enclosures, strong malware detection and encryption.
Companies need to run software tools to test source code and provide reports to government labs, two camera industry executives said.
The rules allow labs to ask for source code if companies are using proprietary communication protocols in devices, rather than standard ones like Wi-Fi. They also enable Indian officials to visit device makers abroad and inspect facilities for cyber vulnerabilities.
The Indian unit of China's Infinova told IT ministry officials last month the requirements were creating challenges.
"Expectations such as source code sharing, retesting post firmware upgrades, and multiple factory audits significantly impact internal timelines," Infinova sales executive Sumeet Chanana said in an email on April 10. Infinova didn't respond to Reuters questions.
The same day, Sanjeev Gulati, India director for Taiwan-based Vivotek, warned Indian officials that "All ongoing projects will go on halt." He told Reuters this month that Vivotek had submitted product applications and hoped "to get clearance soon."
The body that examines surveillance gear is India's Standardization Testing and Quality Certification Directorate, which comes under the IT ministry. The agency has 15 labs that can review 28 applications concurrently, according to data on its website that was removed after Reuters sent questions. Each application can include up to 10 models.
As of May 28, 342 applications for hundreds of models from various manufacturers were pending, official data showed. Of those, 237 were classified as new, with 142 lodged since the April 9 deadline.
Testing had been completed on 35 of those applications, including just one from a foreign company.
India's CP Plus told Reuters it had received clearance for its flagship cameras but several more models were awaiting certification.
Bosch said it too had submitted devices for testing, but asked that Indian authorities "allow business continuity" for those products until the process is completed.
When Reuters visited New Delhi's bustling Nehru Place electronics market last week, shelves were stacked with popular CCTV cameras from Hikvision, Dahua and CP Plus.
But Sagar Sharma said revenue at his CCTV retail shop had plunged about 50% this month from April because of the slow pace of government approvals for security cameras.
"It is not possible right now to cater to big orders," he said. "We have to survive with the stock we have."
7 notes
·
View notes
Text
Man Down!
Over the weekend, it seems that our beloved game hosting site, Itch.io, has been attacked by brand Funko Pop and their usage of the AI tool called "Brand Shield". Sunday night, the site spent hours completely offline.
"[Brand Shield] created some bogus phishing report to our registrar, iwantmyname, who ignored our response and just disabled the domain," (— itch.io (@itchio) December 9, 2024) said Itch on social media, but not before taking a moment to brand the software as "trash." The software allegedly used by Funko that took the itch.io site down is made by a company called BrandShield. BrandShield describes itself as an “AI-powered online anti-counterfeiting solution” that monitors for “trademark infringements, phishing attempts, brand abuse, and counterfeit activity.”
Itch.io claims to have taken down the “disputed page” that triggered the phishing report immediately on receiving a takedown notice, but said no-one at iwantmyname appeared to have read the email confirming the page’s removal.
An iwantmyname representative said, “The domain name was already reinstated earlier today after the registrant finally responded to our notice and took appropriate action to resolve the issue.” At the time iwantmyname’s reply was sent, itch.io appeared to have been back online for less than 40 minutes. The ability to reinstate a domain name in such a short time frame is currently unconfirmed.
Luckily, the website at large appears to be up-and-running again, as of our reporting this, and the company behind Itch.io has noted that their servers haven't shown any signs of impact from the incident.
Itch decided to hold tight before taking any drastic measures, such as putting up a new domain, but did offer a workaround for indie developers to use: "There are implications with third party services that make [switching domains] not a trivial swap. In the meantime, if you know how to tweak your hosts file use: 45.33.107.166."
"If you do edit your hosts file, please remember to remove all the lines after domain is restored. Although we typically hold an IP for a while, it can change if we update our back-end infrastructure. If the downtime exceeds 8 hours then we'll likely prioritize deploying a new domain. Hopefully things are able to get sorted out before then." Itch came back online between 5 and 6 a.m. EST on Monday morning, after at least three hours during which it was completely offline for most users, including both players and developers who use the open platform. Games and other products already bought from itch.io can be used without issue, but the storefront outage will likely be a significant problem for creators who use it for distribution.
We here at YanSim News urge creators to double-check their games to ensure nothing has been lost or corrupted.
Other's reports referenced: - https://www.gamedeveloper.com/business/itch-io-taken-down-by-collectible-maker-funko-and-ai-tool-brand-shield - https://www.polygon.com/gaming/492791/itch-io-funko-takedown
14 notes
·
View notes