#keyboard to serial terminal
Explore tagged Tumblr posts
Note
Cactus fascinates me, does it run on code similar to an existing instruction set or is it completely original on that front?
What can you do with it? What's it's storage?
Both the Cactus (the original wooden prototype from years ago) and the new PCB Cactus(es) are essentially derived from a minimal 6502 computer design by Grant Searle for their core logic. Here's what that would look like on a breadboard:

There isn't much to it, it's 32K of RAM, 16K of ROM containing Ohio Scientific's version of Microsoft BASIC, a 6850 ACIA for serial interaction, some logic gates, and of course a 6502 microprocessor (NMOS or CMOS, doesn't matter which). You hook it into a terminal and away you go.
Grant's design in turn can be best described as a distilled, modernized version of the OSI Challenger series of computers. Here's an OSI-400 and a Challenger 4P respectively:

The left one is a replica of the 400 circa 1976, also called the Superboard. It was affordable, endlessly reconfigurable and hackable, but ultimately very limited in capabilities. No BASIC, minimal monitor ROM you talk to over serial, but you could connect it to a bus to augment its features and turn it into a more powerful computer.
Whereas the OSI C4P on the right from about 1979 has more RAM, a video card, keyboard, BASIC built in, serial interface, cassette tape storage, and that's just the standard configuration. There was more room to expand and augment it to your needs inside the chassis (alot changed in 3 years for home computer users).
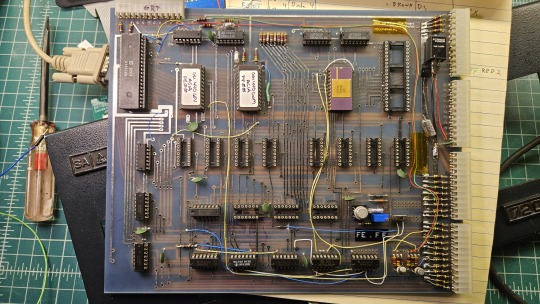
Grant's minimal 6502 design running OSI BASIC is a good starter project for hobbyists. I learned about the 6502's memory map decoding from his design. I modified and implemented his design on a separate cards that could connect to a larger backplane.

Here are the serial, ROM, RAM, and CPU cards respectively:

Each one is 100% custom, containing many modifications and fixes as I developed the design. However, that's only half of the computer.
I really wanted a 6502 machine with a front panel. People told me "nobody did that", or couldn't think of examples from the 1970s but that seemed really strange to me. Especially since I had evidence to the contrary in the form of the OSI-300:
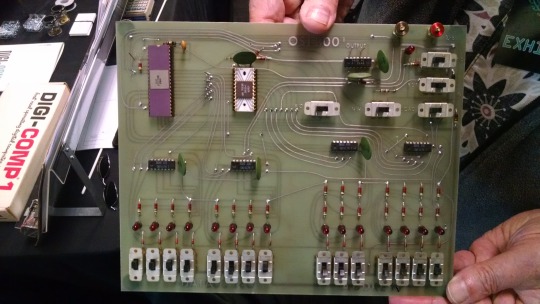
This one I saw at VCF West back in 2018 illustrates just how limited of a design it is. 128 bytes of RAM, no ROM, no serial -- just you, the CPU, and toggle switches and LEDs to learn the CPU. I was inspired the first time I saw one in 2015 at VCF East, which is probably when this whole project got set in motion.
Later that year I bought a kit for a miniature replica OSI-300 made by Christopher Bachman, and learned really quickly how limited the design philosophy for this particular front panel was. It was a major pain in the ass to use (to be clear, that's by OSI's choice, not any fault of Christopher in his implementation)

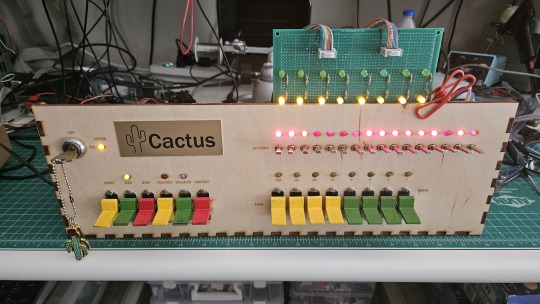
So... I designed my own. Took awhile, but that's the core of what the Cactus is: my attempt at experiencing the 1970s homebrew scene by building the computer I would have wanted at the time. Over half of the logic in the Cactus is just to run the front panel's state machine, so you can examine and modify the contents of memory without bothering the 6502. I added in all of the things I liked from more advanced front panels I had encountered, and designed it to my liking.
Here's the original front panel, accompanying logic, and backplane connected to the modern single board computer (SBC) version of the machine:

And here's the new Cactus SBC working with the new front panel PCB, which combines the logic, physical switch mountings, and cabling harnesses into a single printed circuit board.
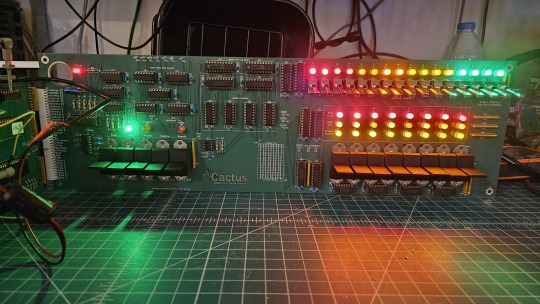
So, what can you do with it? Pretty much the same things I do already with other contemporary 1970s computers: play around in BASIC, fire up the occasional game, and tinker with it.
I've got no permanent storage designed for the Cactus as yet, it's been one of those "eventually" things. The good news is that a variety of software can be ported to the hardware without too much trouble for an experienced hobbyist. A friend of mine wrote a game called ZNEK in 6502 assembly which runs from a terminal:

Right now, you have to either toggle in machine programs from the front panel from scratch, burn a custom ROM, or connect it to a serial terminal to gain access to its more advanced features:

Here's it booted into OSI BASIC, but I have also added in a modern descendant of Steve Wozniak's WOZMON software for when I need to do lower level debugging.
I've also got a video card now, based on the OSI-440. I have yet to implement a keyboard, or modify BASIC to use the video board instead of the serial connection. Even if I did, screen resolution is pretty limited at 24x24 characters on screen at once. Still, I'm working on that...


Anyway, I hope that answers your question. Check the tags below to see the whole process stretching back to 2017 if you're curious to learn more of the project's history. I'm also happy to answer any more questions you might have about the project.
267 notes
·
View notes
Text
those are exceedingly rare nowadays and there definitely is no evidence in the lofi boy image of one.
the keyboard you are linking is not for a normal computer. it is from an auction for a part number 4176191 keyboard, which indicates it is for the IBM 5291 terminal system, a system which itself was intended to be connected to a variety of IBM minicomputer systems that did the actual processing, and the later AS/400 systems could also provide a terminal connection to such units.
the special DA-15 connector also very much doesn't connect to any standard serial port.
why does lofi boy use a serial port keyboard but a wireless mouse

#there also generally were no normal ibm pc compatibles that operated the keyboard over a serial port you would otherwise use for like#general serial purposes#to even have support in that manner for a second keyboard was rare#you are maybe getting confused with how older cp/m z80 systems tended to have a completely seperate serial terminal attached#to provide keyboard input and video output#maybe??
46 notes
·
View notes
Note
serial is simple and works just great
its not a dec vt110 but my job has a vt220 in its callibration tunnel
here is my hp 700/96

and a pile of gamecubes I'm repairing
ooooooohhhhh preeettyyyy !!!!! did a quick lookup and that's surprisingly late but ig 'video' terminals were still needed in certain commercial settings ?
that keyboard layout is kinda cursed xD mainly around where caps lock would be
4 notes
·
View notes
Note
🫐idk how to do this so i'm just gonna yap i have no clue what my personality type is but one of my favorite characters that i mildly related to was an INTJ 4w5 so i just took that and ran with it. uhh idk if i'm an introvert or extrovert it just depends on my mental state ig. i've been kinda tweekin recently so i'm loud in public like this dude one time caught me saying some of the most devious ahh shii known to man so i pointed at some random dude and blamed bro for saying it and then i sang the my little pony theme song but like 4 octaves higher. my friends hate me i also have no morals whatsoever so i'm cooked. the only reason why i'm not some bonkers dude on a documentary is because i'm a pathetic loser who doesn't actually go through with anything, i just lose interest or go 'nah this is way too much work' i'm a dude and 4'10" (idk lowkey my fault for not taking nutrition supplements when my doctor told me to) and idk what i like because i just have a hyperfixation and then i go batshit over it for several months (my longest hyperfixation was on a character for a year and i spent like 5k on merch of that character and now i highkey hate waking up to see the character's face literally everywhere) i dislike greasy foods with a burning passion, animals of all types (including insects) but actually i highkey used to like sharks but then they got popular online and agreeing with people on tiktok brings me physical pain. oh yeah i also dislike a lot of people online if they disagree with my opinion but depends on my mood because if i'm feeling mildly upset then i spam them with replies and tell them i love them and for them to have a good day but in the most toxic positive way possible and if i'm having a happy day then i do the same thing but i also slander everything i know about them for hobbies i love getting attention, positive or negative like honestly it's so fun. i go on social media a lot i'm pretty much just terminally online except i don't keep up w/ gossip majority of the time because i have no clue who celebrities are. oh yeah i love getting concern i never follow their advice or whatever all i do is make a joke about how pathetic my existence is and they rather don't care or they show concern and either way i get pissed so maybe i should stop with that lmao tbh whenever i read through the things i write i literally sound like those 'quirky >w<' 2020 gacha life ocs i feel like everyone with an ounce of humanity would realize i'm straight up embarrassing anyways ily have a good day!! take care of yourself :3333
“yeah i'm gonna be real fucking honest with you kid—halfway through your life story i genuinely forgot i was looking through my inbox and thought i was reading an article on a serial killer. you say you don't have morals but then you draw the line at greasy foods and tiktok? i mean alright sure but then you go on to bully other people on the internet over a bad mood? i'd say get a life but i'm pretty sure if you tried you would have dropped yourself on the head like you were as a kid. you sound like someone who has over ten restraining orders filed against them and they still have no clue as to why. well fuck that's ten minutes of my time i'm never taking back—you have me mourning over lost time when i'm a demon in literal fucking hell, congrats. let me guess, you'll probably celebrate by being a keyboard warrior in the comments of this post, like if junko enoshima was online. yeah, that's the energy this is giving.”

based off of the 200 follower event.
“🫐 — tell vox about yourself and he’ll give you his inner thoughts about you.”
#ooc : PLS IM SORRY NONNIE I DONT ACTUALLY THINK THESE OF YOU#.voxasks 200 event#VOX IS JUST VOXIN#vox hazbin hotel#hazbin hotel rp#hazbin hotel#hazbin hotel roleplay#hazbin hotel ask blog#hazbin rp#hazbin hotel fandom#hazbin vox#hazbin hotel vox
9 notes
·
View notes
Text

MacCharlie advertisement, 1985, scan sourced from vintagecomputing.com
Manufactured and released by Dayna Communications in 1985, the MacCharlie was a hardware add-on for the original Macintosh 128K and the Macintosh 512K that enabled users to run DOS software designed for the IBM PC on their Macintosh.
It did so by literally being an entire IBM PC compatible with an 8088 microprocessor, 256 KB RAM, and a 360 KB floppy disk drive. The RAM was upgradeable to 640 KB and a second disk drive was also available, with the MacCharlie Plus including 640 KB RAM and two floppy drives as standard.
The MacCharlie also included a keyboard extension that added a number pad and function keys, as the Macintosh keyboard lacked a numpad, function keys, or arrow keys (a deliberate choice by Apple who thought that developers would just port their old software to the Macintosh rather than developing software around the GUI paradigm if they had included those keys).
The MacCharlie connected to the Macintosh via a 9-pin serial cable and performed all DOS operations itself (obviously), with the Macintosh serving as a terminal for the MacCharlie. This required you to run the MacCharlie application software that was included on a 3.5 inch floppy disk for your Macintosh along with MS-DOS, which was also (naturally) included on a 5.25 inch floppy disk for the MacCharlie.
While the MacCharlie software included the ability to transfer files from itself to the Macintosh (and vice versa), you could not run a DOS program and a Macintosh program simultaneously (the System Software, later renamed to Mac OS, for the Macintosh did not support the running of multiple programs simultaneously until the release of the MultiFinder extension in 1987, with the feature eventually becoming integrating into the operating system with System 7 in 1991).
The MacCharlie software was also limited to running text-based DOS software only.
(Oh and if you're curious about the name 'MacCharlie', it was in reference to the advertising campaign for the IBM PC featuring Charlie Chaplin's Little Tramp character)
3 notes
·
View notes
Text
CRT Rescue
Just last week I learned that a recycling center near a city I visit was closing down and had over a dozen pallets of CRTs to get rid of. I made arrangements with the owner to stop by on a weekend date. I was especially interested in seeing “IBM terminals” having heard there were about 30 there. Working in the e waste industry myself, it was refreshing to just dive in there and take whatever without looking crazy or violating any regulations. Just the week before about a dozen people came in nerding out over tube TVs. Working in BTB e-waste and being a retro computer nerd is a bad combo, one that is tough on my mental health.
I was also the only person connected with the local Free Geek who could make it so they gave me a shopping list.

I only had an hour to look so I focused on the IBMs. I would learn that IBM at the time used a proprietary “twinax” cable and that these displays could not be connected to anything other than an IBM mainframe. I was able to put together the last two complete units with logic boards. I was disappointed I couldn’t have a VGA ready green 80’s monitor for free, but fortunately I was later told that there were a lot of local IBM mainframe fans around who’d be happy to take them.
I also found a generic TTY terminal from Renyolds and Renyolds with the classic white cursor.

I found a large office paper shredder with a very vintage look that is going to be perfect for Precious Plastic activities through Second Melt, probably the most useful and practical find.

I noticed a large all in one terminal with a mechanical keyboard wedged into a box and decided to turn it on. Fortunately it didn’t blow up but the screen did not do anything. I was hesitant but I decided to grab it for its case and keyboard. If I can’t get it working it will be a great case for when I build my WarGames inspired evil AI.


It is a General Terminal Corporation GTC-100 terminal dating to the early 80’s. After doing some digging I found that it is “teletype compatible” and workable with a USB to 25 pin serial adapter. This one’s a keeper and I’m going to try and restore it.


At the last second I grabbed an armful of 9 track IBM tapes, also for donating to the local Free Geek. I’ll keep one for display purposes.

Regretfully I wish I had spent more time there and probably won’t get back— the place has to be cleared out by years end. But I’m empowered I was able to same some stuff to distribute to like minded folks entirely on my own volition. I’m excited to get the terminal working and expect a post, possibly two on that.

#vintage#retro computing#retro gaming#crt monitor#crt tv#1980s#1980s nostalgia#80’s#80s aesthetic#retro aesthetic#ibm#ewaste#e-waste
6 notes
·
View notes
Text
Petite Pico Proe is Perfect for Parlaying with a Pi Penta
if you got a Pi 5 and you want to log in or debug without ssh'ing or using a monitor and keyboard - there's now a super fast and easy way to get into the UART console - thanks to the new JST SH 3-pin 'UART' port nestled between the HDMI connectors. Use your Pico Probe and connect the 3-pin cable to the 'U' port - the probe board will appear as a COM/serial port, and you can open it up with any terminal program. we love using it for kernel debugging because the connection stays open between reboots and you'll get all messages directly printed, plus the early boot messages…even ones before the firmware is loaded or the display comes up.
3 notes
·
View notes
Text
Regarding my Solaris 8 install stream
I've decided the best option for the time being would be to network boot the machine - would you like to see netboot configuration done on-stream or would you like for the stream to be focused on strictly the install (netboot preconfigured)? (context will be provided underneath the poll)
Now for the context:
Recently I tried to do a Solaris 8 install stream on Twitch for my Sun Ultra 5 where I would be installing Solaris 8 from CD graphically (this is big, because I had recently acquired something that would allow me to use a USB keyboard and mouse in place of a Sun proprietary keyboard and mouse (see my post on that here), which is amazing because the proprietary keyboards and mice are expensive.
This was going to achieve something I had wanted to do for a long while - a graphical Solaris install (for reference, you can install Solaris graphically using a keyboard, mouse, and monitor, like I was going to be doing here, or using a TUI over a serial terminal, which is what these workstations default to when you have no keyboard attached, and something I have done on-stream before.



Sadly I encountered issues with the drive and/or discs, and not even burning a different image set solved my issues (I ended up getting a different error than the one I was getting on-stream by using a different image set). This means that either install from unofficial media isn't possible with this combination of OS + machine, or alternatively my CD drive is being weird (which admittedly, I have had issues with it under OpenBSD).




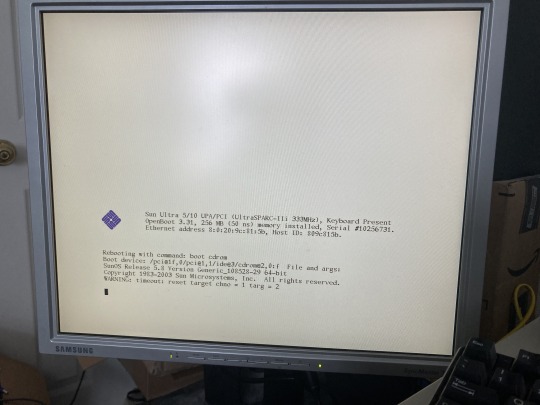
So, because I can't seem to get any further with using optical media, my only choice is to (once more) set up a jumpstart server (basically Sun's netbooting system for their workstations). This is where I ask the public - would they want to see configuration of this on-stream or would they rather I configure it beforehand and focus on actual installation)?
#sun microsystems#unix#retro computing#retro tech#old computers#old tech#vintage computer#vintage computers
4 notes
·
View notes
Text
I present for your consideration, one of the weirder "exit" stories.
When I was in high school, I had an after school job working at Murray Hill Bel Labs. I was on the same floor and wing as the people who created C and Unix, but my work didn't involve them. I did, however, spend off hours in the Unix room because there were always cool things going on there.
One of them was a graphical terminal called The Blit. It had a green screen that was roughly the size of a legal sheet of paper and had square pixels each roughly 1/72 of an inch, which was fairly decent at the time. The processor that ran the terminal was a 68k which was overkill for a terminal. It's main I/O was through a serial port. I don't recall if there was anything else beyond the keyboard and 3 button mouse.
When you powered it on, it was just a plain terminal. If it was connected to a Vax or some other system, you could use a shell, run vi, rogue, etc.
It had one very unusual feature for a terminal though. It had escape codes that let you download and run code directly on the terminal. Rob Pike (and probably the other folks there) wrote a tiny operating system that could run on it. The OS featured a GUI with a windowing system that allowed processes to run in each window and it multiplexed i/O with the host. For example, you could have windows with independent shells. The shells ran on your host system, but all the I/O ran the Blit. The GUI was called mpx. One of the mouse buttons brought up a system menu to let you make new windows, etc.
The problem was that once you started mpx, there was no way to exit it (why would you ever want to exit?). But people complained to Rob and he added a system menu item that would quit. Unfortunately, he made it the very first item. The UI was such that when you pressed the button, the menu appeared and was visible as long as you held the button down. When you released it, if the cursor was over a menu item, it selected it and executed it. The problem was that the menu appeared so that the first item was always under the cursor. This means that if you accidentally pushed that button, it selected exit and you lost everything.
People complained to Rob, telling him that "it's too easy to exit - make it harder" Allegedly, Rob gave them grief in return, "first you wanted a way to exit but now it's too easy?!" In response, he removed the menu item entirely and wrote a shell command named "exit-mpx" which would ask you a "hard" Unix trivia question and if you got it right, it would exit. If you got it wrong, it would stay running. Most people learned the answers to one or two questions and kept running exit-mpx until their question came up.
The question I learned was "How many pieces was Ken's deer cut into?"
There was an simple image editor you could run to create icons etc. There was also an email client. They had digitized the ID badge photos of people who worked in the department and made it so that if you got mail from someone who had an icon, it would make the icon drop into the window running the mail client in a queue of icons. Very much ahead of its time.
The ID icons were in a public directory on the system, so for grins I pulled up the picture of Ken Thompson, who was bald on top and started fooling around with his picture in the editor. I turned his head into a conehead. Much to my chagrin, I accidentally saved it on top of the system picture because the permissions allowed it. I don't know how long people got a conehead Ken in the email program.
officially-cool youtuber Tech Tangents was working on an old Tandy machine and discovered the most hilarious quit menu in all of software, buried in an obscure astrology program for DOS:

THE "MAYBE QUIT" OPTION!
For too long, computer programs have been asking if we're sure we want to quit, and only giving us a binary yes/no option. Finally we can leave whether we quit or not up to fate.
And yeah. When he tried it out, it failed to quit a few times and then quit. It seems it just flips a coin when you select it and either quits/does nothing based on it.

27K notes
·
View notes
Text
PyRDP And Rogue RDP: Automating Malicious RDP Exploits

PyRDP automates file exfiltration and clipboard theft for rogue RDP campaigns. This method allows unnoticed spying via hacked remote desktop sessions.
Remote Desktop Protocol?
The Windows service Remote Desktop Protocol (RDP) allows Terminal Servers and Clients to communicate. This system uses “virtual channels” to convey data from presentations, keyboard and mouse actions, clipboards, and serial devices. Traditional RDP security research has focused on how attackers with authentic victim credentials may get full GUI access to a machine.
Innovative New Campaign RDP Use
Google Threat Intelligence Group (GTIG) uncovered a new phishing campaign tied to UNC5837, a suspected Russian espionage actor, in October 2024. This effort targeted European military and political institutions using signed.rdp file attachments. Instead than stressing interactive sessions, this marketing ingeniously used two obscure RDP protocol features:
Resource redirection maps victim file systems to attacker servers.
RemoteApps: Giving victims access to attacker-controlled applications.
RDP proxy programs like PyRDP may automate dangerous actions like file exfiltration and clipboard gathering. This approach is called “Rogue RDP.�� This effort focused on file theft and espionage.
Key RDP Features
.rdp configuration files: .rdp configuration files can change RDP session functionality by configuring IP addresses, display settings, and certificate options. These files setup an RDP session like the traditional GUI (mstsc.exe). The observed campaign used phishing emails with malware-signed.rdp file attachments. This file allowed the adversary to read and write all of the victim's discs and clipboard contents and create an RDP connection from the victim's computer.
The resource redirection capability lets remote desktop users utilise local peripherals and devices. This includes printers, keyboards, mouse, discs, serial connections, hardware keys, audio equipment, and clipboards. The observed campaign's malicious.rdp file sent all discs, printers, COM ports, smart cards, WebAuthn requests, clipboards, and POS devices to the attacker's C2 server. Microsoft's "virtual channels" allow resource redirection and RDP packet transmission.
RemoteApps: This optional RDP feature lets remote server apps run as windowed programs on the client (victim). Thus, a malicious remote program that isn't installed on the victim's PC may seem local. Malicious.rdp files in RemoteApp campaigns presented users with a fake “AWS Secure Storage Connection Stability Test” app.
This application was hosted on the attacker's RDP server and looked local. The session displays this application alone when remoteapplicationmode is 1. RemoteApp requires RDP server resources, yet mapped victim CDs allow RemoteApp access. This malware also received the victim's Windows environment variables as command-line arguments.
Function of PyRDP
PyRDP, an open-source Python-based MiTM RDP proxy toolkit, is used offensively. Even if its use in the claimed campaign is unverified, its automation makes it a feasible weapon for such attacks. PyRDP relays the victim-RDP server connection to boost capabilities:
Possible NTLM hash and plaintext password theft.
The RDP server executes commands, not the victim's machine.
Note the user's clipboard.
Mapping and maybe scraping drives.
Controlling, recording, and broadcasting RDP sessions.
PyRDP uses fine-grained control over built-in functionality rather than RDP protocol vulnerabilities. PyRDP might have been used in the campaign under observation to bypass the user login screen and reveal the malicious RemoteApp by giving credentials. Potential features include clipboard capture and automatic file exfiltration.
Security Risks and Effects
This campaign highlights unknown RDP security risks. It shows how attackers may employ lawful characteristics for evil, making identification and incident response harder due to fewer forensic artefacts than other attack routes. Even without direct command execution on target PCs, the attackers were able to access victim discs, steal files, collect clipboard data (including passwords), and steal environment variables. Signed.rdp files may bypass security alarms, reducing attack suspicion.
Advice for Defenders
The sources give several ways to fortify systems and identify these attacks:
Log Artefacts: Monitor registry keys (HKU\…\Microsoft\Terminal Server Client\Servers) and Windows Event Logs (Event IDs 1102, 1027, 1029) to comprehend an attacker's infrastructure. Increased logging (e.g., Sysmon) can track file write activity from C:\Windows\system32\mstsc.exe on redirected discs, however transient files should not be included. You may also use regex patterns to identify.rdp files run from email attachments.
System hardening: Network-level blocking of outgoing RDP traffic to public IPs, registry-based resource redirection disablement, and Group Policy-based granular RDP policy configuration (e.g., resource and clipboard redirection management, enforcing Network Level Authentication, and blocking.rdp file extensions as email attachments) can improve security.
Questionable RDP configuration files with a base64 encoded Let's Encrypt certificate or that allow resource redirection and RemoteApps can be identified using YARA criteria.
Final comments
The “Rogue RDP” campaign shows how to innovate with old tactics. The risk is dishonestly using actual RDP capabilities, not protocol weaknesses. To defend against such assaults and grasp PyRDP's potential, one must understand RDP features, notably resource redirection and RemoteApps.
#technology#technews#govindhtech#news#technologynews#cloud computing#PyRDP#Remote Desktop Protocol#Remote Desktop Protocol RDP#RDP proxy#RDP sessions#RDP#RDP feature
1 note
·
View note
Text
Previously on 68616472696616e7573:
I built a network lab from a shitty old Cisco SG350 switch, Lenovo m72 mini-PC and tp-link router. Lenovo works as a bare-bone Linux server. I selected this gear pretty much only because I had them laying around.
It worked fine for a week or two, until I realised I had given the same IP to both the router and the switch. I don’t even know how I managed to do that, probably because I didn’t configure all of them together and make a clear network map before configuring. I’m surprised it worked at all.
Aaaaand I did the noob mistake (which I knew not to do but did it anyway) and tried changing the Cisco IP in the GUI. It’s impossible, I don’t think anyone has successfully configured a Cisco Network Switch via GUI, at least not these cheaper models.
In the end I just ended up digging up the console cable, resetting the switch and doing it all over via serial commands. Which is a lot faster than any other method, it didn’t take that long. Dilly dallying with GUI and then trying to remove commands via terminal took several hours and led to nowhere.
Anyway, I learned a lot, which is why you do these things:
1. I still have an few years old CCNA book, that is really good
2. ‘line tty’ does not exist on SG models for some reason, I don’t know how to make SSH work
3. ‘vlan databases x,y’ is how you create a vlans, but I guess this is deprecated method and you can do it via configuration mode in Catalyst and newer switches?
4. Commands: ‘ctrl+h, write mem, sh run, sh start, conf t’
5. In SG350 the command to reset the configuration is ‘delete startup-configuration’, man it took a while to find that! Even ChatGPT didn’t know.
I also made the TP-link as secure as possible creating 16-character wifi pass, hiding the SSID, turning on DDoS attack prevention and preventing WAN ping. I have updated the firmware already. However these are still massively unsecure devices:
With all this I managed to prevent my server accessing my WiFi and it doesn’t seem to understand to switch to Ethernet, so I have no remote access. I have to plug it into a monitor and keyboard and update the network authentication. Maybe I can connect an USB-cable from it to the switch’s USB serial port and try to get the SSH to the Cisco console working?
Maybe I should eat some breakfast…
Sir, this is a Wendy’s, please place order or leave.
1 note
·
View note
Photo

HP Compaq dc5800 Small Form Desktop Specifications: PROCESSOR Processor Speed: 2.6 Ghz Processor: Intel Core 2 Duo E6750 PC EXPANSION SLOTS Expansion Slots: PCI Express x16, PCI Express x1, PCI Number of PCI Express x16 Slots: 1 Number of PCI Express x1 Slots: 1 Number of PCI Slots: 1 WIRED CONNECTIONS Number of VGA Ports: 1 Number of RJ45 Ports: 1 Wired Terminals / Ports: Serial, VGA, USB 2.0, Parallel Ports, RJ45, PS/2 Keyboard, PS/2 Mouse Number of PS/2 Keyboard Ports: 1 Number of Serial Ports: 1 Number of USB 2.0 Ports: 8 Number of Parallel Ports: 1 Number of PS/2 Mouse Ports: 1 MEMORY Number of DIMM Slots: 4 Installed memory (RAM): 2 GB RAM Type: DDR2 Maximum memory (RAM): 8 GB L2 Cache Memory: 4MB PC EXPANSION BAYS Expansion Bays: 5.25in External, 3.5in Internal, 3.5in External Number of 3.5in Internal Expansion Bays: 1 Number of 3.5in External Expansion Bays: 1 Number of 5.25in External Expansion Bays: 1 HARD DRIVE Interface: SATA2 Storage capacity: 250 GB Hard Drive Type: SATA II RPM: 7200 GENERAL Weight (g): 8100 Width (mm): 3370 Height (mm): 3780 Length (mm): 1000 Available Colours: Black Warranty (Months): 12 INPUT DEVICES Input Devices: Mouse, Keyboard Keyboard and Mouse Type: USB POWER OPTIONS Power Supply: AC Power OPTICAL DRIVES Write speed DVD-R: 16x Write speed DVD+R: 16x MOTHERBOARD Sound Card on Motherboard: Yes Network Card on Motherboard: Yes Graphics Controller on Motherboard: Yes PCS Floppy Drive: No PC User Suitability: Business PC Case Form Factor: Small Form Factor SOFTWARE Operating Systems not included SOUND CARD 3D Sound Support: Yes MEDIA Card Reader: No Power cables, keyboards and mouse not included.
0 notes
Text
Would love to know more about this company and other products produced. These were apparently equipped with an Intel 80186 and 256KB of RAM. The concept is neat, since it's a fairly basic server-client model with those space-age looking terminals connecting to the server directly by serial connections.
It would have been amazing to be able to sit down at a bank of these things and ponder the orb. Those keyboards also look wild.

949 notes
·
View notes
Text
Still cannot click the "I am not a robot" things...
Signal.
Still autumn, the forest around the drone hub has started to gain its orange coat as winter comes knocking, the forecast reads snow within the next two months. Cold wind blowing, the insulation within the walls keeps most of it out. Quiet after the convoy escort job, an article caught my eye as I was looking into things related to Severin.
Local company invests in water purification effort
Echelon, a prominent corporation in many fields, has recently announced that they are reinforcing their ability to provide purified water and hydrogen to various clients. With the installation of two new separator boilers, the company expects that the cost of clean water will drop with the supply increasing.
“We believe water is a right, not a thing to be monetized...” Severin, leader of the Echelon Company stated in an interview with our correspondent
The initiative comes at a time of growing concern over the recent attacks targeting the water purification facilities. Colony Security Units have confirmed they are investigating the matter but have declined to comment on the progress.
Next up: Shipments to Novis speeding up, a new player enters the game. We have an inside look...
Right, enough of that, Separator boilers then, they are quite capable pieces of machinery and not cheap either. Another tab open, I started looking into the water purifier attacks in the area. Public information remains limited, and the Empire databases are under lock and key. Federation data would likely have something, but my access was severed a few weeks ago. Leaning back in the office chair, I looked around the control room.
Fresh coat of paint and almost a kilometer of cables hidden in various ways, it was certainly a project setting all of this up, still needs a bit of work to be 100% but usable for the time being. Three high power CPUs and GPUs, the various screens mounted around and above me, I tapped my fingers against the armrests and moved things around my HUD and the screens. Said it before, the web has been spun and is spreading as I wait, messages and alerts set up for anything mentioning Androids or Phoenix.
Best defense is a good offence, but being prepared for attacks from any angle is even better, Valkyrie has been drawing up defenses in the forests, the few trail cameras and motion detectors work in tandem. Wildlife wanders around our region, but knowing what is out there gives some peace of mind, the landmines are harder to come by...
Faint rain against the window, I heard a sharp beep and saw a message popup on the terminal screen, I circled my chair back to the PC and opened the message on my HUD.
Unknown sender, the title a single word. Tip.
“Heard you were part of that convoy... Your chassis has seen better days. I have a thorn in my side that has an android chassis just waiting to be nicked. Yours if you take it, torch their servers on the way out and we’re even, no strings.” Signed: Grin.
Attached image, seemingly taken in a hurry, of the chassis in question, a blank canvas inside its supporting frame for delivery, the status panel containing both the serial number and a reading of the internals almost impossible to read with the blur. Missing all of its plastic covers, the face resembles a bare skull with the two dark lenses of the cameras staring into the distance. Software comes separate; I moved the image onto the terminal and analyzed it. String of numbers hidden inside the metadata, a pop up appeared shortly after, requesting a key to decrypt the data. Seven spaces, I looked down at the keyboard for a moment before the thought hit me.
If this Grin knows who I am...
>>Input key: Phoenix >>Enter >>Key accepted. Decrypting information.
Jackpot.
#logs of an android#stories#writing#scifi#sci fi & fantasy#science fiction#fiction#fantasy#cyberpunk#story
0 notes
Text
How do mobile devices wirelessly control LED screens?
With the rapid development of technology, mobile devices such as mobile phones and iPads have acquired many functions of traditional computers, including online office tasks. Nowadays, it is becoming more and more common to use these mobile devices to control LED displays. So, how do they control LED displays? This article will analyze this process and the principles behind it in detail.

Connection and control principle
Mobile phones and iPads can establish a connection with LED displays through wireless networks, without the need to use network cables like computers. This connection method mainly relies on wireless technologies such as WiFi, which enables mobile devices to easily control LED displays. Provide you with technical answers for wireless LED displays.
How to control LED displays with mobile phones and iPads
1.1 WIFI wireless control
WiFi wireless control is currently the most commonly used method. Mobile devices (such as mobile phones and iPads) are used as control terminals. Through touch screen operation, remote wireless control of LED displays can be achieved. All functions can be completed through touch screen, achieving zero-second switching without lag. This method completely abandons the traditional keyboard and mouse, and software replaces hardware.
Working principle: By adding a wireless router or other wireless device to the LED display, it can be bridged with the user's existing wireless network to form a wireless LAN. In this way, the network control card can be easily integrated into the wireless network to achieve wireless network control.

Features:
No wiring is required, easy installation and debugging Fast data transmission speed Required equipment: bridge, wireless router (it is recommended to choose a device with replaceable antenna to enhance the wireless signal reception effect)
Disadvantages: The communication distance of WiFi wireless control mainly depends on the gain capability of the bridge, and the communication distance of the wireless router is short, and the signal through the wall is weak or no signal. Therefore, this method is suitable for places with short-range wireless signals. If the area where the LED display is located is already covered by wireless signals, just bridge the wireless router connected to the LED display control card to the wireless network, and the display can be controlled on any device in the intranet.

1.2 RF wireless control
Working principle: One end of the RF module is connected to the control computer, and the other end is connected to the serial port of the control card. After the computer installs the driver, a virtual serial port will be generated, and data will be sent through this serial port.
1.3 GPRS wireless control
Working principle: After the GPRS module is powered on, it will automatically complete the process of dialing up to the Internet and connect to the data center server. Users access the server through the client software, and the server forwards information to achieve control of the LED display.

1.4 4G full network wireless control
Working principle: It is basically the same as GPRS control, except that it uses 4G network.
Features: 4G full network supports the full range of China Mobile, China Unicom, and China Telecom networks, with fast transmission rate, full real-time control, and instant response after the command is sent.

Summary
Wireless control of LED displays using mobile devices such as mobile phones and iPads has become a trend in the field of modern information display. Whether through WiFi, RF, GPRS or 4G technology, these methods greatly simplify the control process of LED displays and provide more flexible and convenient operation methods. Different wireless control methods have their own advantages and disadvantages, and users can choose the appropriate control method according to actual needs.

Thank you for watching. I hope we can solve your problems. Sostron is a professional LED display manufacturer. https://sostron.com/about-us/ We provide all kinds of displays, display leasing and display solutions around the world. If you want to know: Composition and technical analysis of indoor LED display screens. Please click read.
Follow me! Take you to know more about led display knowledge.
Contact us on WhatsApp:https://api.whatsapp.com/send?phone=+8613510652873&text=Hello
1 note
·
View note
Text
Grand Strategy Manifesto (16^12 article-thread ‘0x1A/?)

youtube
Broken down many times yet still unyielding in their vision quest, Nil Blackhand oversees the reality simulations & keep on fighting back against entropy, a race against time itself...
So yeah, better embody what I seek in life and make real whatever I so desire now.
Anyways, I am looking forward to these... things in whatever order & manner they may come:
Female biological sex / gender identity
Ambidextrous
ASD & lessened ADD
Shoshona (black angora housecat)
Ava (synthetic-tier android ENFP social assistance peer)
Social context
Past revision into successful university doctorate graduation as historian & GLOSS data archivist / curator
Actual group of close friends (tech lab peers) with collaborative & emotionally empathetic bonds (said group large enough to balance absences out)
Mutually inclusive, empowering & humanely understanding family
Meta-physics / philosophy community (scientific empiricism)
Magicks / witch coven (religious, esoteric & spirituality needs)
TTRPGs & arcade gaming groups
Amateur radio / hobbyist tinkerers community (technical literacy)
Political allies, peers & mutual assistance on my way to the Progressives party (Harmony, Sustainability, Progress) objectives' fulfillment
Local cooperative / commune organization (probably something like Pflaumen, GLOSS Foundation & Utalics combined)
Manifesting profound changes in global & regional politics in a insightful & constructive direction to lead the world in a brighter direction fast & well;
?
Bookstore
Physical medium preservation
Video rental shop
Public libraries
Public archives
Shopping malls
Retro-computing living museum
Superpowers & feats
Hyper-competence
Photographic memory
600 years lifecycle with insightful & constructive historical impact for the better
Chronokinesis
True Polymorph morphology & dedicated morphological rights legality (identity card)
Multilingualism (Shoshoni, French, English, German, Hungarian, Atikamekw / Cree, Innu / Huron...)
Possessions
Exclusively copyleft-libre private home lab + VLSI workshop
Copyleft libre biomods
Copyleft libre cyberware
Privacy-respecting wholly-owned home residence / domain
Privacy-respecting personal electric car (I do like it looking retro & distinct/unique but whatever fits my fancy needs is fine)
Miyoo Mini+ Plus (specifically operating OnionOS) & its accessories
BeagleboneY-AI
BeagleV-Fire
RC2014 Mini II -> Mini II CP/M Upgrade -> Backlane Pro -> SIO/2 Serial Module (for Pro Tier) -> 512k ROM 512k RAM Module + DS1302 Real Time Clock Module (for ZED Tier) -> Why Em-Ulator Sound Module + IDE Hard Drive Module + RP2040 VGA Terminal + ESP8266 Wifi + Micro SD Card Module + CH375 USB Storage + SID-Ulator Sound Module -> SC709 RCBus-80pin Backplane Kit -> MG014 Parallel Port Interface + MG011 PseudoRandomNumberGen + MG003 32k Non-Volatile RAM + MG016 Morse Receiver + MG015 Morse Transmitter + MG012 Programmable I/O + "MSX Cassette + USB" Module + "MSX Cartridge Slot Extension" + "MSX Keyboard" -> Prototype PCBs
Intersil 6100/6120 System ( SBC6120-RBC? )
Pinephone Beta Edition Convergence Package (Nimrud replacement)
TUXEDO Stellaris Slim 15 Gen 6 AMD laptop (Nineveh replacement)
TUXEDO Atlas X - Gen 1 AMD desktop workstation (Ashur replacement)
SSD upgrade for Ashur build (~4-6TB SSD)
LTO Storage
NAS RAID6 48TB capacity with double parity (4x12TB for storage proper & 2x12TB for double parity)
Apple iMac M3-Max CPU+GPU 24GB RAM MagicMouse+Trackpad & their relevant accessories (to port Asahi Linux, Haiku & more sidestream indie-r OSes towards… with full legal permission rights)
Projects
OpenPOWER Microwatt
SPARC Voyager
IBM LinuxOne Mainframe?
Sanyo 3DO TRY
SEGA Dreamcast with VMUs
TurboGrafx 16?
Atari Jaguar CD
Nuon (game console)
SEGA's SG-1000 & SC-3000?
SEGA MasterSystem?
SEGA GameGear?
Casio Loopy
Neo Geo CD?
TurboExpress
LaserActive? LaserDisc deck?
45rpm autoplay mini vinyl records player
DECmate III with dedicated disk drive unit?
R2E Micral Portal?
Sinclair QL?
Xerox Daybreak?
DEC Alpha AXP Turbochannel?
DEC Alpha latest generation PCI/e?
PDP8 peripherals (including XY plotter printer, hard-copy radio-teletypes & vector touchscreen terminal);
?
0 notes