#php case statement
Explore tagged Tumblr posts
Text
PHP switch Statement
Learn how to use the PHP switch statement with syntax, examples, use cases, and best practices. A complete guide to mastering switch-case control in PHP. PHP switch Statement: A Complete Guide The switch statement in PHP is a control structure that allows you to compare a single expression against multiple possible values. It’s an efficient alternative to using multiple if...elseif...else…
#php case statement#php conditional statements#php control statements#php switch#php switch example#php switch statement#php switch syntax#php switch vs if else#switch case php#switch in php
0 notes
Text
SQLi Potential Mitigation Measures
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
Why Developers and Marketers Love Direct Mail APIs for Campaign Automation
In an age dominated by digital noise, direct mail marketing has made a powerful comeback—this time fueled by technology. Developers and marketers are increasingly turning to Direct Mail APIs to automate personalized, data-driven physical mail campaigns. These APIs bridge the gap between digital interfaces and physical customer engagement, making offline outreach as measurable and scalable as online marketing.

This article explores why marketers are adopting direct mail APIs, their benefits, use cases, and how these tools redefine campaign automation for ROI-focused teams.
What is a Direct Mail API?
A Direct Mail API (Application Programming Interface) is a digital interface that enables developers to programmatically send physical mail—such as letters, postcards, brochures, and catalogs—via third-party mailing services. These APIs integrate with CRM systems, marketing automation platforms, and eCommerce platforms to streamline offline customer communication workflows.
Why Developers Love Direct Mail APIs
1. Easy Integration with Tech Stacks
Developers appreciate APIs that integrate seamlessly with modern SaaS tools like Salesforce, HubSpot, Shopify, and Zapier. Most direct mail APIs offer RESTful architecture with SDKs for languages like Python, PHP, Java, and Node.js.
2. Scalability for High-Volume Campaigns
With direct mail APIs, developers can automate batch sending of thousands of personalized letters or postcards in a single call. This scalability is invaluable for large enterprises managing multi-region campaigns.
3. Workflow Automation
Developers use direct mail APIs to set event-based triggers—such as cart abandonment, renewal reminders, or subscription milestones—to dispatch personalized physical mail without human intervention.
4. Error Handling and Webhooks
Modern APIs support advanced features like webhooks for delivery status, error handling, tracking, and debugging. This allows developers to create resilient workflows with full visibility into the mail lifecycle.
Why Marketers Love Direct Mail APIs
1. Campaign Personalization at Scale
Marketers can personalize content, images, and offers based on CRM data—similar to email marketing but through a tangible medium. APIs allow for variable data printing, making each piece of mail unique.
2. Multichannel Marketing Integration
Direct mail can now be part of a unified omnichannel strategy. APIs make it easy to trigger a postcard after a user opens an email, clicks an ad, or visits a store.
3. Enhanced Tracking and ROI Attribution
APIs allow marketers to track direct mail effectiveness via UTM links, QR codes, PURLs (Personalized URLs), and call tracking. When paired with analytics tools, it provides measurable ROI data.
4. A/B Testing and Optimization
Thanks to APIs, A/B testing of creative elements and offers in direct mail is now possible, just like in digital campaigns. Marketers can analyze engagement metrics and iterate campaigns based on real-world responses.
Use Cases of Direct Mail APIs
E-Commerce: Sending automated thank-you cards, reactivation offers, and abandoned cart reminders.
Financial Services: Dispatching compliance letters, account statements, and loan approval notices.
Healthcare: Mailing HIPAA-compliant appointment reminders, test results, and wellness tips.
SaaS: Re-engaging dormant users with custom postcards and win-back offers.
Education: Sending enrollment letters, alumni newsletters, and fundraising appeals.
Security and Compliance Benefits
Reputable Direct Mail APIs are GDPR, HIPAA, and SOC 2 compliant. For developers handling sensitive data, this ensures legal and ethical handling of personal information.
Top Direct Mail API Providers
Lob
PostGrid
Click2Mail
Postalytics
Sendoso
Each of these providers offers comprehensive documentation, sandbox environments, and real-time tracking capabilities, making them ideal for modern development and marketing teams.
Conclusion
Developers love Direct Mail APIs for their programmability, reliability, and scalability. Marketers love them for personalization, ROI attribution, and omnichannel strategy execution. Together, they create a synergy that elevates traditional direct mail into a dynamic, data-driven marketing tool.
Whether you're building high-volume campaigns or refining customer journeys, direct mail APIs offer a competitive edge in an increasingly crowded digital world.
youtube
SITES WE SUPPORT
Automated Mailing APIs – Wix
1 note
·
View note
Text
Complete PHP Tutorial: Learn PHP from Scratch in 7 Days
Are you looking to learn backend web development and build dynamic websites with real functionality? You’re in the right place. Welcome to the Complete PHP Tutorial: Learn PHP from Scratch in 7 Days — a practical, beginner-friendly guide designed to help you master the fundamentals of PHP in just one week.
PHP, or Hypertext Preprocessor, is one of the most widely used server-side scripting languages on the web. It powers everything from small blogs to large-scale websites like Facebook and WordPress. Learning PHP opens up the door to back-end development, content management systems, and full-stack programming. Whether you're a complete beginner or have some experience with HTML/CSS, this tutorial is structured to help you learn PHP step by step with real-world examples.
Why Learn PHP?
Before diving into the tutorial, let’s understand why PHP is still relevant and worth learning in 2025:
Beginner-friendly: Easy syntax and wide support.
Open-source: Free to use with strong community support.
Cross-platform: Runs on Windows, macOS, Linux, and integrates with most servers.
Database integration: Works seamlessly with MySQL and other databases.
In-demand: Still heavily used in CMS platforms like WordPress, Joomla, and Drupal.
If you want to build contact forms, login systems, e-commerce platforms, or data-driven applications, PHP is a great place to start.
Day-by-Day Breakdown: Learn PHP from Scratch in 7 Days
Day 1: Introduction to PHP & Setup
Start by setting up your environment:
Install XAMPP or MAMP to create a local server.
Create your first .php file.
Learn how to embed PHP inside HTML.
Example:
<?php echo "Hello, PHP!"; ?>
What you’ll learn:
How PHP works on the server
Running PHP in your browser
Basic syntax and echo statement
Day 2: Variables, Data Types & Constants
Dive into PHP variables and data types:
$name = "John"; $age = 25; $is_student = true;
Key concepts:
Variable declaration and naming
Data types: String, Integer, Float, Boolean, Array
Constants and predefined variables ($_SERVER, $_GET, $_POST)
Day 3: Operators, Conditions & Control Flow
Learn how to make decisions in PHP:
if ($age > 18) { echo "You are an adult."; } else { echo "You are underage."; }
Topics covered:
Arithmetic, comparison, and logical operators
If-else, switch-case
Nesting conditions and best practices
Day 4: Loops and Arrays
Understand loops to perform repetitive tasks:
$fruits = ["Apple", "Banana", "Cherry"]; foreach ($fruits as $fruit) { echo $fruit. "<br>"; }
Learn about:
for, while, do...while, and foreach loops
Arrays: indexed, associative, and multidimensional
Array functions (count(), array_push(), etc.)
Day 5: Functions & Form Handling
Start writing reusable code and learn how to process user input from forms:
function greet($name) { return "Hello, $name!"; }
Skills you gain:
Defining and calling functions
Passing parameters and returning values
Handling HTML form data with $_POST and $_GET
Form validation and basic security tips
Day 6: Working with Files & Sessions
Build applications that remember users and work with files:
session_start(); $_SESSION["username"] = "admin";
Topics included:
File handling (fopen, fwrite, fread, etc.)
Reading and writing text files
Sessions and cookies
Login system basics using session variables
Day 7: PHP & MySQL – Database Connectivity
On the final day, you’ll connect PHP to a database and build a mini CRUD app:
$conn = new mysqli("localhost", "root", "", "mydatabase");
Learn how to:
Connect PHP to a MySQL database
Create and execute SQL queries
Insert, read, update, and delete (CRUD operations)
Display database data in HTML tables
Bonus Tips for Mastering PHP
Practice by building mini-projects (login form, guest book, blog)
Read official documentation at php.net
Use tools like phpMyAdmin to manage databases visually
Try MVC frameworks like Laravel or CodeIgniter once you're confident with core PHP
What You’ll Be Able to Build After This PHP Tutorial
After following this 7-day PHP tutorial, you’ll be able to:
Create dynamic web pages
Handle form submissions
Work with databases
Manage sessions and users
Understand the logic behind content management systems (CMS)
This gives you the foundation to become a full-stack developer, or even specialize in backend development using PHP and MySQL.
Final Thoughts
Learning PHP doesn’t have to be difficult or time-consuming. With the Complete PHP Tutorial: Learn PHP from Scratch in 7 Days, you’re taking a focused, structured path toward web development success. You’ll learn all the core concepts through clear explanations and hands-on examples that prepare you for real-world projects.
Whether you’re a student, freelancer, or aspiring developer, PHP remains a powerful and valuable skill to add to your web development toolkit.
So open up your code editor, start typing your first <?php ... ?> block, and begin your journey to building dynamic, powerful web applications — one day at a time.

0 notes
Text
SafeNet Protocols Package (SPP) project
Still in cardboard boxes...
(Last update : Networks Managers who want to use SPP for security reasons should make sure that every other protocols are only allowed through VM or light sandboxes to do it properly. Attackers may use regular https internet links, in order to fish through e-mail boxes. As every SPP contents are certified, only a regular https website can carry malicious contents. As long as any content provider hasn't been hacked...)
Introduction / initial statement
The goal is not to completely erase https, smtp etc. It is to make a side network where there is no point watching clients.
Brainstorming
Because all contents are legal and certified, and clients can't publish publicly accessible contents on SPP (except if servers can be access by legal authorities). Banish clients tracking from SafeNet and a lot of other details... So, contents providers will have to find other ways to get money using SafeNet protocols. I'm sure they will ... SafeNet anonymous user identities, only known by SafeNet managers. Transitives mail box address ... optional VPN and optional onion-like access features (crypted) ... Integrate firewall with an "allow only SPP" button. We still have to work on softwares updates strategy ... A dedicated OS including virtualisation of other OS and access to regular network only by using a Virtual Machine.
The fact that the goal is to make it useless to track clients doesn't mean it will be immediately the case. The network will probably needs some time to insure that users can't do anything illegal or harmfull before : completely reject legal authorities access to clients or users "useless" data and just shot "everything" down on illegitimate legal requests.
Using only SafeNet on the host reduces risks to get virus as every contents are certified. You still can get a virus by opening a .exe file coming from an e-mail... Or if you still use other protocols on the host machine. A "no .exe or .zip or .vbs or .bat or docm or .dat or files without extensions etc. in e-mails => *allow only ... " policy stays on study. As SPP is not a network made for professional use but for private users. Find a way to allow e-mail boxes safely are a tuff challenge for SPP.
One of the major interest of SPP is that it allow you to watch videos or listen to audio contents with a garanty that you will not be tracked. As it was the case on Hertzien TVs. So, it may save audio/video industry.
SPP network cannot be use for remote access. Legal authorities should be convinced that there is no use of such a thing on a 100% SPP machine and may still use regular networks and protocols.
There also will be a policy about microphones and cameras but I think you get the idear. - Break your phone integrated microphone and use a removable hand-free kit to get a microphone... -
Contents Providers must respect more rules if they want to publish contents using SPP... They also have to financially contribute to SPP management. It's supposed to become a new market. A way to ensure better user experience and rich a new customer base.
The main protocol "shttps" will use same languages as https : html5, css3, JS, PHP, SQL etc. So, porting will be simplified. Developers can simply make a copy of their https website root directory and erase, from files, every stuff that is not allowed on shttps. Or make a completely new website using the same languages.
SPP contracts says that users data collected by contents providers can't be passed to third parts*. Yes, this means contents providers have to do everything by their own and can't sell users data.
*Except for anonymous SPP coordinates and only to deliver the service provided or receive a payment. We still have to work on that too.
SPP policies can evolve to become more permissives, in order to allow needed stuff, or to become more restrictives, in case of any legal flaw observation.
There is also a Public Health dimension to this project. Panem et circences ...
Taking commissions on financial transactions may help to reduce the cost of publication authorization requests.
First SPP e-mail virus
**** Nothing here ! *****
Solution found ! : "E-Mail through SPP" services providers will now have to check every attached contents : check if the extension is allowed as before and at least check if open it doesn't throw any errors, as "file may be corrupt" or stuff like that.
Fantasy statment : Microsoft also add one more safety protocol on .docm files. You now have to complete a puzzle that say "I know that asking peoples to unlock .docm files is a common way to hack a computer !" in order to unlock files.
Pirates strike back
****** Nothing here ! *****
So, we banned .txt files too...
Pirates strike back again
***** Nothing here ! ****
So, E-mail services providers also have to block any message containing scripts command or lines of code, especially batch or VBS. Senders must receive a message indicating that their message has been blocked because "In order to be allowed, your message should not contain .XXXX code lines, even in a simple text field or attached documents". "If you want to send this kind of information to a SPP user, through SPP network (SPPN), you need to become a certified provider and use publicly access documents. Or at least documents made accessible to our bots and Content Watch Offices. Or use an e-mail address certified by the SafeNet Identity Certification Service."
Demonstration : ***** NOTHING HERE ! ******
SafeNet E-mail services
Apps of "E-mail through SPP" service providers must now separate e-mail coming from Certified SafeNet Users from e-mail coming from a regular Internet user. Users are informed that the sender of message coming from uncertified senders may be impossible to identify. So, they should never follow instructions coming from a sender that they are not able to certify.
E-mail clients (apps) can't use nicknames instead of the real sender e-mail address except for the real name of Certified SPP Users.
E-mail services should never make it possible to join a real identity to a SPP anonymous identity. Therefore, SPP users must manage two mailbox address... To avoid errors the same application can't manage both real identities and anonymous identities. Providers can develop two applications that are mostly identical except for a very limited quantity of code lines. In order to make it easier to maintain both apps. Apps logo of both these apps must make it easy to know when you are using your "anonymous" mail box and your official mail box.
As a reminder, SPP Anonymous Identities are still attached to a real person, but only SafeNet Identity Certification Services (SICS) can make links between Real and Anonymous identities.
Anonymous Identities can only receive e-mails from SPP contents providers and cannot send mails. This may evolve if it happen to become essential for providers to get users direct returns. Which means a return whose not using their websites forms.
0 notes
Text

FAMILY CODE OF THE PHILIPPINES
TITLE 4. PROPERTY RELATIONS BETWEEN HUSBAND AND WIFE
Article 92. The following shall be excluded from the community property: (1) Property acquired during the marriage by gratuitous title by either spouse, and the fruits as well as the income thereof, if any, unless it is expressly provided by the donor, testator or grantor that they shall form part of the community property; (2) Property for personal and exclusive use of either spouse. However, jewelry shall form part of the community property; (3) Property acquired before the marriage by either spouse who has legitimate descendants by a former marriage, and the fruits as well as the income, if any, of such property. (201a)
Illustration: Inherited Property
Couple: Maria and Juan are married.
Inheritance: Maria's grandmother passes away and leaves her a valuable painting worth PHP 1,000,000.
Exclusion: The painting is considered exclusive property of Maria, as it was acquired by gratuitous title (inheritance) during the marriage. The income generated from renting out the painting or selling it later is also considered her exclusive property.
*case found on poage 617
Nicolas v. CA G.R. No. 122857
Facts:
Roy Nicolas (petitioner) and Blesilo Buan (respondent) entered into a Portfolio Management Agreement.
Nicolas was to manage Buan's stock transactions for a fee of 20% of realized profits.
The agreement was terminated, and Nicolas demanded P68,263.67 in management fees.
Buan claimed mismanagement and refused to pay.
The trial court ruled in favor of Nicolas, but the Court of Appeals reversed.
Issue:
Whether or not the Court of Appeals err in reversing the trial court's decision and dismissing Nicolas' complaint for lack of merit?
Ruling:
The Supreme Court affirmed the Court of Appeals' decision, dismissing Nicolas' complaint.
The Court deemed these statements self-serving and insufficient to establish the existence of profits. This lack of proof directly relates to Article 92 of the Family Code because the management fees were based on the "realized profits" from Buan's stock transactions. Nicolas' claim was essentially based on the "fruits" of Buan's property, which, according to Article 92, would be considered part of the community property only if the donor (Buan) explicitly stated so in the agreement. Since no such explicit statement existed, the burden of proof lay with Nicolas to demonstrate the existence of these "fruits" (profits) to claim his share.
0 notes
Text
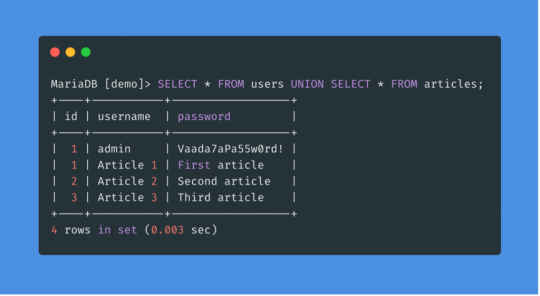
Secure Your WordPress Site: Prevent SQL Injection (SQLi) Attacks
SQL Injection (SQLi) in WordPress: Protect Your Website
SQL Injection (SQLi) attacks are a common security threat for websites using databases, and WordPress sites are no exception. A successful SQLi attack can expose your database, allowing attackers to manipulate data or even take full control of your site. This post explores how SQLi affects WordPress, demonstrates a preventive coding example, and shows how you can use our free website security checker to scan for vulnerabilities.

What Is SQL Injection (SQLi)?
SQL Injection (SQLi) is a security vulnerability that allows attackers to insert or “inject” malicious SQL code into a query. If not protected, SQLi can lead to unauthorized access to your database, exposing sensitive data like user information, login credentials, and other private records. WordPress sites, especially those with outdated plugins or themes, are at risk if proper security practices are not implemented.
How SQL Injection Affects WordPress Sites
SQL injection attacks usually target input fields that accept user data. In a WordPress environment, login forms, search boxes, or comment sections can be potential entry points. Without proper sanitization and validation, these fields might allow attackers to execute harmful SQL commands.
To protect your WordPress site, it’s essential to:
Sanitize user inputs: This prevents harmful characters or commands from being submitted.
Use prepared statements: Using prepared statements binds user inputs as safe data types, preventing malicious SQL code from being executed.
Regularly update plugins and themes: Many SQLi vulnerabilities come from outdated software.
Coding Example to Prevent SQL Injection (SQLi) in WordPress
Here's a simple PHP example to show how you can prevent SQL injection by using prepared statements in WordPress:
php
global $wpdb; $user_id = $_GET['user_id']; // Input parameter // Using prepared statements to prevent SQL injection $query = $wpdb->prepare("SELECT * FROM wp_users WHERE ID = %d", $user_id); $user = $wpdb->get_results($query); if ($user) { echo "User found: " . esc_html($user[0]->user_login); } else { echo "User not found."; }
In this example:
$wpdb->prepare() ensures the user ID input is treated as an integer (%d), protecting against SQLi.
esc_html() sanitizes the output, preventing malicious data from appearing in the HTML.
Detecting SQLi Vulnerabilities with Our Free Tool
Using our free Website Security Checker, you can scan your WordPress site for SQL injection risks. The tool is easy to use and provides a detailed vulnerability assessment, allowing you to address potential security issues before attackers can exploit them.

The free tool generates a vulnerability report that outlines any risks discovered, helping you take proactive measures to protect your site. Here’s an example of what the report might look like:

Best Practices for Securing Your WordPress Site
In addition to using prepared statements and scanning for vulnerabilities, here are some best practices for securing your WordPress site:
Limit user permissions: Ensure that only trusted accounts have administrative access.
Implement firewall protection: Firewalls can block malicious IPs and provide extra security layers.
Regularly back up your database: In case of an attack, a backup helps restore your data quickly.
Use a strong password policy: Encourage users to create complex passwords and update them periodically.
Conclusion
Securing your WordPress site from SQL Injection is crucial for safeguarding your data and users. By implementing prepared statements, validating inputs, and using security tools like our free Website Security Checker, you can reduce the risk of SQLi vulnerabilities. Take a proactive approach to your site’s security to ensure it remains safe from attacks.
Explore our free website security tool today to check your WordPress site for potential vulnerabilities, and start building a more secure web presence.
#cyber security#cybersecurity#data security#pentesting#security#sql#sqlserver#the security breach show#wordpress
0 notes
Text
PHP Nested if Statement
Learn everything about PHP nested if statements with easy examples, syntax, best practices, and real-world use cases. Perfect for beginners and intermediate learners. Mastering PHP Nested if Statements: A Complete Guide Conditional statements are the backbone of decision-making in programming. In PHP, the if statement allows us to execute code based on whether a condition is true. But what if…
#php conditional statements#php decision making#php if inside if#php multiple conditions#php nested conditions#php nested if statement
0 notes
Text
Article 1353 - ObliCon
Art. 1353. The statement of a false cause in contracts shall render them void, if it should not be proved that they were founded upon another cause which is true and lawful.
This article is similar to the rule on Relative Simulation
Rolando De La Paz vs. L & J Development Company
G.R. No. 183360
September 8, 2014
FACTS: Out of trust and confidence, Rolando dela Paz lent a sum of money worth Php 350,000 to L & J Development Corporation, a property developer represented by Atty. Esteban Salonga as its president and general manager.
The loan was executed without any security and no maturity date. It was however agreed between the parties that the loan will have a 6% monthly interest (amounting to Php 21,000). So far, L&J paid a total of Php 576,000 already – including interest charges from December 2000 to August 2003.
L&J later failed to make payments due to financial difficulties in the business. Rolando then filed a collection case with the MTC and alleged as of January 2005, L&J still owes him Php 772,000 inclusive of monthly interests.
L&J (represented by Atty. Salonga) did not deny that they did incurred a debt from Rolando, and admitted that they failed to pay due to a fortuitous event (financial difficulties). They also contended that the 6% monthly interest is unconscionable and that their total payment of Php 576,000 should be applied to the principal loan which only amounts to Php 350,000.
Rolando also contends that Atty. Salonga tricked him to execute the said loan plus interest without reducing the agreement in writing. He also said that the 6% interest rate was at the suggestion and insistence of L&J.
The MTC rendered judgment in favor of Rolando and upheld the 6% interest rate as valid since L&J complied to it as evidenced by the payment they made from December 2000 to August 2003. L&J is now estopped to impugn said interest rate.
The MTC also reduced the legal interest rate to 12% per annum on the remaining loan for reasons of equity. They did not grant the prayer of moral damages to Rolando since there was no bad faith on the part of L&J.
L&J appealed the decision to the RTC – contending once again that the 6% interest rate is unconscionable, and that their previous payment which totaled Php 576,000 should be used to set off the principal loan of Php 350,000. RTC however affirmed the decision of the MTC. L&J appealed to the CA.
CA ruled in favor of L&J, noting that the agreed 6% interest rate was not reduced in a written agreement and hence, it should not be considered due. CA ruled that the loan was already paid, and that Rolando should return the excess Php 226,000 with interest of 12% per annum. The case has now reached the Supreme Court.
about:blank
ISSUE: Whether or not the unwritten 6% interest agreement should be honored.
HELD: No. The Supreme Court held that, as provided under the Civil Code, an agreement regarding loan interests should be stipulated in writing. Even if the 6% monthly rate was done in writing, it will still be void for being unconscionable and contrary to morals and public policy – for at this time, an interest rate of 3% and higher is considered excessive and exorbitant.
Furthermore, the lack of maturity date puts the total interest to a whooping 72% per annum which the Supreme Court considered to be “definitely outrageous and inordinate.” The Supreme Court affirmed CA’s ruling, but as to Rolando’s obligation to pay the excess Php 226,000, the interest rate was reduced from 12% to 6% per annum.
0 notes
Text
Round 6 : Article 1293
ARTICLE 1293 STATES THAT :
NOVATION WHICH CONSISTS IN SUBSTITUTING A NEW DEBTOR IN THE PLACE OF THE ORIGINAL ONE MAY BE MADE EVEN WITHOUT THE KNOWLEDGE OR AGAINST THE WILL OF THE LATTER, BUT NOT WITHOUT THE CONSENT OF THE CREDITOR. PAYMENT BY THE NEW DEBTOR GIVES HIM THE RIGHTS MENTIONED IN ARTICLES 1236 AND 1237.
What is Substitution?
It is a replacement of the original debtor with a new one.
May there be novation through substitution with the consent of the debtor?
Yes, it may be without the debtor’s consent.
May there be novation through substitution without the consent of the creditor?
No, in all cases, it must be with the consent of the creditor.
What are the kinds of substitution?
Expromision
In expromision, the initiative for the change does not come from the debtor. This requires the consent of the third person and the creditor.
Example:
Ronna owes Larry Php 1,000.00.00. Jimboy told Ronna that he will be the one to pay Ronna’s debt. Ronna agrees.
Delegacion
In delegacion, the debtor offers the substitution. It requires the consent of the debtor, the creditor and the third person.
Example:
Ronna owes Larry Php 1,000.00.00. Ronna told Larry that Jimboy will be the one to pay the debt. Larry agrees.
What are the rights mentioned in Articles 1236 and 1237?
Article 1236. The creditor is not bound to accept payment or performance by a third person who has no interest in the fulfillment of obligation, unless there is stipulation to the contrary.
Whoever pays for another may demand from the debtor what he has paid, except that if he paid without the knowledge or against the will of the debtor, he can recover only in so far as the payment has been beneficial to the debtor.
Article 1237. Whoever pays on behalf of the debtor without the knowledge or against the will of the latter, cannot compel the creditor to subrogate him in his rights, such as those arising from a mortgage, guaranty, or penalty.
Bognot vs RRI Lending
G.R. No. 180144, September 24, 2014
Ponente: Associate Justice Arturo Brion
FACTS:
In September 1996, Leonardo Bognot and his younger brother, Rolando Bognot applied for and obtained a loan of P500,000.00 from RRI Lending, payable on November 30, 1996. The loan was evidenced by a promissory note and was secured by a post dated check dated November 30, 1996. Evidence on record shows that Leonardo renewed the loan several times on a monthly basis. He paid a renewal fee of P54,600.00 for each renewal, issued a new post-dated check as security, and executed and/or renewed the promissory note previously issued. RRI Lending on the other hand, cancelled and returned to Leonardo the post-dated checks issued prior to their renewal. Leonardo paid the renewal fees and issued a post-dated check dated June 30, 1997 as security. As had been done in the past, RRI Lending superimposed the date "June 30, 1997" on the promissory note to make it appear that it would mature on the said date.
Several days before the loan’s maturity, Rolando’s wife, Julieta, went to the respondent’s office and applied for another renewal of the loan. She issued in favor of RRI Lending a promissory note and a check dated July 30, 1997, in the amount of P54,600.00 as renewal fee. On the excuse that she needs to bring home the loan documents for the Bognot siblings’ signatures and replacement, Julieta asked the RRI Lending clerk to release to her the promissory note, the disclosure statement, and the check dated July 30, 1997.
Julieta,however, never returned these documents nor issued a new post-dated check. Consequently, RRI Lending sent Leonardo follow-up letters demanding payment of the loan, plus interest and penalty charges. These demands went unheeded. In his Answer, Leonardo, claimed, among other things, that the complaint states no cause of action because RRI Lending’s claim had been paid, waived, abandoned or otherwise extinguished, and that the one(1) month loan contracted by Rolando and his wife in November 1996 which was lastly renewed in March 1997 had already been fully paid and extinguished in April1997.
ISSUE:
Whether the parties’ obligation was extinguished by payment
HELD:
No, Leonardo failed to satisfactorily prove that his obligation had already been extinguished by payment. As the CA correctly noted, the petitioner failed to present any evidence that RRI Lending had in fact encashed his check and applied the proceeds to the payment of the loan. Neither did he present official receipts evidencing payment, nor any proof that the check had been dishonored. Leonardo merely relied on the respondent’s cancellation and return to him of the check dated April 1,1997. The evidence shows that this check was issued to secure the indebtedness. The acts imputed on the respondent, standing alone, do not constitute sufficient evidence of payment.
Article 1249, paragraph 2 of the Civil Code provides “The delivery of promissory notes payable to order, or bills of exchange or other mercantile documents shall produce the effect of payment only when they have been cashed, or when through the fault of the creditor they have been impaired” .
Although Article 1271 of the Civil Code provides for a legal presumption of renunciation of action (in cases where a private document evidencing a credit was voluntarily returned by the creditor to the debtor), this presumption is merely prima facie and is not conclusive; the presumption loses efficacy when faced with evidence to the contrary. Moreover, the cited provision merely raises a presumption, not of payment, but of the renunciation of the credit where more convincing evidence would be required than what normally would be called for to prove payment. Thus, reliance by the petitioner on the legal presumption to prove payment is misplaced. To reiterate, no cash payment was proven by the petitioner. The cancellation and return of the check dated April 1, 1997, simply established his renewal of the loan- not the fact of payment. Furthermore, it has been established during trial, through repeated acts, that the respondent cancelled and surrendered the post-dated check previously issued whenever the loan is renewed
0 notes
Text

🔰APSS 1st BASIC SPINE WEBINAR SERIES (2024)
🔅 THEME –Thoracolumbar Spinal Trauma
🗓️ Date & Time : Sunday , 26 May , 2024 3:30PM (GMT +8.00) 1:00PM IST (GMT +5.30)
👨💻 Streaming live on OrthoTV: https://tinyurl.com/OrthoTV-APSS-11
🔘Speakers
👨⚕️Dr Harvinder Singh Chhabra (India) 🇮🇳
👨⚕️Dr Rohan Gala (India) 🇮🇳
👨⚕️Dr Masato Tanaka (Japan) 🇯🇵
👨⚕️Dr Chung Weng Hong (Malaysia) 🇲🇾
👨⚕️Dr Mohammad Arif Khan (Pakistan) 🇵🇰
♦️Members of APSS Online Education Sub- Committe
👨⚕️ Dr Loya Vijay Kumar - India 🇮🇳
👨⚕️ Dr Chiu Chee Kidd - Malaysia🇲🇾
🔹Welcome Address by President Elect of APSS - Prof Yat Wa Wong
🔸Programme Overview by Chairman, APSS Online Education Sub-Committee - Dr Vishal Kundnani
❇️Scientific Programme
🔸Role of Modern Classification System - Dr Harvinder Singh Chhabra
🔹Case Presentation 1: Thoracolumbar Burst Fracture - Dr Chung Weng Hong
🔸Management Principles of Thoracolumbar Fractures - Dr Mohammad Arif Khan
🔹Case Presentation 2: Chance Fracture - Dr Rohan Gala
🔸Minimal Invasive Surgery in Thoracolumbar Spine Trauma - Dr Masato Tanaka
🗳️ Summary Statement & Vote of Thanks - Dr Vishal Kundnani
🔵 Organised by Asia Pacific Spine Society
🤝 OrthoTV Team: Dr Ashok Shyam, Dr Neeraj Bijlani
📺 Streaming Live on OrthoTV www.orthotvonline.com
®️‼️Free Registration now at‼️ https://www.apssonline.org/apss-1st-basic-spine-webinar-2024.php
📱 Join OrthoTV - https://linktr.ee/OrthoTV
#SpineWebinar #OrthoTV #APSS #SpinalTrauma #MedicalEducation #Orthopedics #FreeWebinar #AsiaPacificSpineSociety #OrthoTVTeam #OnlineEducation #MinimalInvasiveSurgery #CasePresentations #ClassificationSystem #ThoracolumbarFractures #Orthoconference
0 notes
Text
Mastering PHP: The Ultimate Guide for Aspiring Expert PHP Developers

Introduction
Welcome to CompleteGurus, your go-to resource for all things tech! Today, we’re diving into the world of PHP development. Whether you’re a novice just starting out or an experienced coder looking to level up, becoming an expert PHP developer requires dedication, continuous learning, and practical experience. Let’s explore the roadmap to mastering PHP and the essential skills every expert PHP developer should have. #expertPHPdeveloper
Understanding the Basics
What is PHP?
PHP (Hypertext Preprocessor) is a widely-used, open-source scripting language designed for web development. It’s embedded in HTML and is known for its efficiency in handling dynamic content, databases, and session tracking.
Why PHP?
Ease of Use: PHP’s syntax is easy to understand and learn, making it a favorite among beginners.
Community Support: A large, active community provides extensive resources, frameworks, and libraries.
Compatibility: PHP is compatible with various servers and databases, including Apache, Nginx, MySQL, and PostgreSQL.
Performance: PHP is fast and efficient, especially when it comes to handling server-side scripting.
Building a Strong Foundation
Learning the Language
To become an expert, you must have a thorough understanding of PHP’s syntax, functions, and features. Here are some key areas to focus on:
Variables and Data Types: Understand how to declare and use different data types.
Control Structures: Master if-else statements, switch cases, loops (for, while, foreach).
Functions: Learn to create and use functions, including variable scope and anonymous functions.
Arrays and Strings: Work extensively with arrays (indexed, associative, multidimensional) and string manipulation functions.
Object-Oriented Programming (OOP)
OOP is a critical aspect of advanced PHP development. Ensure you understand the following concepts:
Classes and Objects: Learn how to define and instantiate classes.
Inheritance: Understand how child classes inherit properties and methods from parent classes.
Encapsulation: Learn to protect the state of an object using access modifiers.
Polymorphism: Understand how objects can take on many forms through interfaces and abstract classes.
Advanced PHP Development
Frameworks
To streamline development and maintain code quality, familiarize yourself with popular PHP frameworks:
Laravel: Known for its elegant syntax and powerful features, Laravel is a favorite among developers.
Symfony: Offers a robust set of reusable PHP components and a modular architecture.
CodeIgniter: Lightweight and straightforward, ideal for small to medium projects.
Working with Databases
An expert PHP developer must be proficient in database management:
SQL: Master SQL queries to interact with databases.
PDO and MySQLi: Learn to use PHP Data Objects (PDO) and MySQLi for secure and efficient database operations.
ORM: Understand Object-Relational Mapping (ORM) with tools like Eloquent in Laravel.
Security Practices
Security is paramount in web development. Ensure you follow best practices:
Data Sanitization and Validation: Always sanitize and validate user inputs.
Prepared Statements: Use prepared statements to prevent SQL injection.
Password Hashing: Securely store passwords using hashing algorithms like bcrypt.
HTTPS: Ensure secure data transmission by implementing HTTPS.
Testing and Debugging
Quality assurance is essential. Learn to:
Unit Testing: Write unit tests to ensure code reliability using PHPUnit.
Debugging: Use debugging tools and techniques to identify and fix issues.
Version Control: Use Git for version control and collaboration.
Continuous Learning and Community Engagement
Stay Updated
The tech world evolves rapidly. Stay ahead by:
Reading Blogs: Follow blogs and forums like CompleteGurus, PHP.net, and Stack Overflow.
Attending Conferences: Participate in PHP conferences and meetups.
Taking Courses: Enroll in advanced PHP courses on platforms like Udemy, Coursera, and LinkedIn Learning.
Contribute to the Community
Open Source Projects: Contribute to open-source projects to gain real-world experience.
Writing and Speaking: Share your knowledge through blogging, speaking at events, or creating tutorials.
Networking: Connect with other developers, join PHP groups, and participate in discussions.
Conclusion
Becoming an expert PHP developer is a journey that involves mastering the language, understanding advanced concepts, and continuously learning. By following this roadmap and engaging with the community, you'll hone your skills and stay at the forefront of PHP development. Ready to take the next step? Dive into the resources available here at CompleteGurus and embark on your path to becoming an #expertPHPdeveloper!
0 notes
Text
Create your own Blockchain - Build a Blockchain From Scratch

What is Blockchain Development?
Blockchain is a decentralized and distributed digital ledger technology that allows multiple parties to maintain a shared record of transactions or information securely and transparently. It is the underlying technology behind cryptocurrencies like Bitcoin, but its applications go beyond just financial transactions. Blockchain is secure and transparent. It uses cryptography to secure the data. Each information is encrypted and linked to the previous information in a chain, making it very difficult to alter or delete data without being detected. Anyone can view the transactions on a blockchain, which provides high transparency and accountability.
Blockchain development encompasses building applications and systems that leverage the power of blockchain technology. It involves designing and building decentralized applications (DApps), smart contracts, and the underlying infrastructure required to support blockchain networks.
To build a blockchain one requires proficiency in programming languages such as Java, PHP, SQL, Rust, Ruby, etc. Additionally, developers should have a strong understanding of cryptography, distributed systems, and the specific features and limitations of the chosen blockchain platform.
How to create a Blockchain?
Step 1 - Identify a Problem to solve
While blockchain boasts impressive advantages, it's crucial to avoid a "one-size-fits-all" mentality. Before diving in, thoroughly scrutinize your desired outcome. Align your specific business goals with the blockchain use cases outlined above.
Formulating a clear problem statement is crucial. This statement should meticulously detail the challenges you seek to address. Subsequently, verify if blockchain is genuinely equipped to tackle these issues. Finally, determine whether migrating your existing solution or building a new application from scratch aligns better with your project.
Step 2 - Draft your business requirements
Following an in-depth analysis, meticulously craft your business requirements document to ensure a comprehensive and successful implementation. This document should identify both on-chain and off-chain technologies necessary for building a fully functional ecosystem. Leverage these details to establish a concrete product roadmap, aiding in maintaining adherence to deadlines and facilitating resource allocation.
3 things the blockchain can do well
Data Authentication & Verification
Smart Asset Management
Smart Contracts
Step 3 - Identify the Consensus Mechanism
After defining your business requirements, the crucial step involves selecting a consensus mechanism. This mechanism serves as the foundation for trust, security, and agreement within the decentralized network. While various options exist, some widely adopted mechanisms include:
Proof of Work (PoW)
Proof of Stake (PoS)
Byzantine Fault Tolerance (BFT)
Deposit-based consensus
Proof of Elapsed Time (PoET)
Therefore, conducting thorough research and selecting the best fit is paramount for a successful implementation.
Step 4 - Identify the suitable blockchain platform
Selecting the appropriate platform for your blockchain application directly impacts the required skillset of your development team. Choosing wisely is crucial, as proper development requires thorough research and investment of time. To ensure the best fit for your business needs, consider the following factors during your evaluation:
Targeted problems
Cost considerations
Development expertise
Project Timeline
By carefully evaluating these factors, you can make an informed decision that sets your project up for success.
Step 5 - Design your Blockchain Nodes
Before commencing development, several key decisions must be made, to determine whether your project requires a permissioned blockchain or a permissionless one. Choose suitable programming languages and assess their impact on development. Decide between a private, public, or hybrid model for your blockchain solution. Will the nodes be cloud-based, on-premises, or a combination? Select the compatible operating system that best supports your application.
Meticulous evaluation of these factors weighed against your project's objectives, available resources, and budget, will ensure a well-designed and strategically developed blockchain solution.
Step 6 - Identify your Blockchain Configuration
Most blockchain platforms require careful planning for various configuration elements, such as:
Permissions
Asset Issuance and Re-issuance
Atomic Exchange
Key Management and Multi-Signatures
Parameters
Native Assets, Address Formats, and Key Formats
Block Signatures and Handshaking
While some elements allow for dynamic adjustments during operation, thorough planning beforehand is crucial for streamlined development and successful implementation.
Step 7 - Build your APIs
Depending on the platform you choose, pre-made application programming interfaces (APIs) might be available. However, in some cases, you may need to develop custom APIs to address specific needs, such as:
Key and Address Management
Auditing and Data Verification
Data Access
Smart Asset Management
Smart Contract Interaction
By carefully considering your project's requirements, you can determine the need for custom API development and ensure a comprehensive and functional blockchain solution.
Step 8 - Design Admin and User Interface
Upon finalizing the overall application plan, you can move on to designing the user interface (UI) for each individual software component. The previously designed APIs will serve as the foundation for integrating the UI elements with the back-end functionalities. Remember, the visual design choices will influence the application's overall aesthetics, while the technical design decisions will impact its architectural structure and functionality.
Step 9 - Optimize your Blockchain Application
Evaluating the success of a deployed blockchain application is crucial. For compute-intensive applications, hardware acceleration can significantly enhance performance, flexibility, and power efficiency.
These accelerators act as performance boosters for key blockchain functionalities like transaction validation, governance, and data storage. By distributing transaction processing across multiple components, they can improve both transaction speed and overall system output, while also optimizing resource utilization and reducing storage needs.
Step 10 - Adding Future Tech
Blockchain technology presents exciting possibilities when combined with other innovative solutions like AI, biometrics, and the Internet of Things (IoT). This integration can significantly enhance the capabilities of blockchain systems.
While the initial hype surrounding blockchain may have overstated its universal applicability, its potential to revolutionize various industries remains undeniable. By embracing these technological advancements in conjunction, we can unlock a future where blockchain empowers us to tackle complex challenges in a secure, efficient, and innovative manner.
Blockchain Development Challenges
There are three main challenges for those who wants to create your own blockchain such as decentralization, security, and scalability.
Decentralization
The main reason to use blockchain is decentralization.
In the realm of finance, blockchain empowers individuals to manage their own cryptocurrency, bypassing the need for centralized control by banks. This system leverages a distributed consensus mechanism, where verification relies on approval from a network of participants instead of a single authority. This unique system ensures the immutability of transactions, meaning they cannot be altered once confirmed.
However, the decentralization offered by blockchain comes with a trade-off: achieving consensus through multiple confirmations can lead to slower transaction processing times. Accelerating this process remains a significant challenge for developers in the blockchain space.
Scalability
The global adoption of blockchain technology depends on its ability to handle a growing volume of transactions while maintaining expected performance and robust defense against cyberattacks. However, achieving high transaction scalability can present challenges, especially as block sizes increase.
In the case of Bitcoin, the original block size limit of 1 megabyte was set to mitigate the risk of cyber threats. However, each Bitcoin transaction contributes to the size of the block, potentially leading to blocks surpassing the imposed size limitations. This can negatively impact processing speed.
Although the block-size debate was initially sparked by Bitcoin, the decisions made by developers regarding block size increase will have implications for all blockchain applications. It becomes a critical consideration to strike a balance between block size expansion and maintaining transaction speed across various blockchain implementations.
Security
Another main challenge faced in creating your own blockchain by the developers is security, even though it is also one of the benefits of blockchain development. Blockchain is a secure technology, and also a target for cybercriminals. Anything that endangers blockchain security will cause a ridge between decentralization and scalability. Ans no centralized party can intervene without regulatory oversight in the moment of security breach. In blockchain security breaches are rare, so developers need to create blockchain networks that not only add business value but also add complete security
It is important to remember that blockchain technology is in the early stages, and these challenges are involved in the development of blockchain solutions.
Why choose Osiz as your Blockchain Development Company?
The development of blockchain is a complex and tedious task you might need an expert to build your blockchain solution. Osiz is an expert in developing blockchain, as a leading blockchain development company, we specialize in cryptography, distributed systems, and smart contract development. Our experienced team of developers builds blockchain software that benefits your business to deliver a reliable, future-rich solution that aligns with your business objectives.
Our other extensive services,
Cryptocurrency Exchange Clone Script
Crypto Trading Bot Development Company
DApp Development Company
Custom Blockchain solutions
ERC20 Token development company
Real Estate Tokenization Development
Contact our blockchain consulting services team, and get free consultation on how to create your blockchain solution.
Source - https://www.osiztechnologies.com/blog/create-your-own-blockchain
#blockchain development#blockchain development company#blockchain services#blockchain solutions#blockchain development services#custom blockchain solution#enterprise blockchain services#cryptocurrency exchange clones#cryptocurrency exchange clone script
0 notes
Text
How can I connect an HTML page to multiple tables from a database?
To connect an HTML page to multiple tables from a database, you typically use a server-side scripting language like PHP or Node.js along with a database management system like MySQL or PostgreSQL. Here's a general outline of the process:
Set up your database: Create the necessary tables in your database to store the data you want to display on your HTML page. Ensure that the tables are properly structured and contain the relevant data.
Write server-side code: Use a server-side scripting language such as PHP or Node.js to query the database and retrieve the data from the multiple tables. You'll need to write SQL queries to fetch the data you need from each table.
Format the data: Once you've retrieved the data from the database, format it in a way that can be easily displayed on your HTML page. This might involve organizing the data into arrays or objects, depending on your programming language.
Generate HTML content: Use the formatted data to dynamically generate HTML content that will be rendered in the user's browser. This could involve using loops or conditional statements to iterate over the data and create HTML elements such as tables, lists, or cards.
Display the HTML page: Serve the HTML page to the user's browser using your server-side code. The user will then be able to view the data from the multiple tables in their web browser.
Remember to handle any errors or edge cases that may arise during the database query process, and ensure that your server-side code is secure against SQL injection attacks. Additionally, consider implementing pagination or filtering options if you're dealing with large datasets to improve performance and user experience.
0 notes
Text
Difference Between SQL and MySQL | Key Factors in Database Decision-Making

In the vast landscape of data management, SQL and MySQL stand out as two prominent players. These technologies are often mentioned interchangeably, leading to confusion regarding their distinctions and best-use scenarios. In this blog, we'll dissect the difference between SQL and MySQL, explore their applications, and provide insights into making informed decisions when choosing a database solution.
What is SQL and MySQL?
To begin, let's clarify the basics. A standardized computer language called SQL, or Structured Query Language, is used to manage and work with relational databases. It serves as the foundation for various database management systems (DBMS), allowing users to interact with databases through queries, updates, and modifications.
On the other hand, MySQL is an open-source relational database management system (RDBMS) that utilizes SQL as its querying language. MySQL, created by Oracle Corporation, is well known for its dependability, scalability, and user-friendliness. It powers countless applications and websites worldwide, making it one of the most popular database systems in the industry.
What is SQL used for?
SQL is incredibly versatile, catering to a wide range of data-related tasks. Its primary functions include:
Data Querying: SQL enables users to retrieve specific information from databases using SELECT statements. These queries can filter, sort, and aggregate data based on user-defined criteria, facilitating efficient data retrieval.
Data Manipulation: With SQL, users can insert, update, and delete records within a database. This functionality is essential for maintaining data integrity and keeping information up-to-date.
Schema Modification: SQL allows for the creation, alteration, and deletion of database schema objects such as tables, views, and indexes. This flexibility enables database administrators to adapt to evolving business requirements seamlessly.
Access Control: SQL includes robust security features for managing user access and permissions within a database. Administrators can grant or revoke privileges to ensure data confidentiality and integrity.
What is MySQL used for?
As an RDBMS built on SQL, MySQL inherits many of the same capabilities while offering additional features tailored to specific use cases. Some common applications of MySQL include:
Web Development: MySQL is widely used in web development for storing and retrieving dynamic content. It integrates seamlessly with popular web development frameworks like PHP, Python, and Ruby on Rails, making it an ideal choice for building dynamic websites and web applications.
Enterprise Solutions: Many enterprises leverage MySQL for mission-critical applications such as e-commerce platforms, content management systems, and customer relationship management (CRM) software. Its scalability and high availability make it well-suited for handling large volumes of transactions and concurrent users.
Data Warehousing: MySQL can also serve as a backend database for data warehousing solutions. By aggregating and analyzing vast amounts of data, organizations can gain valuable insights into their business operations and make data-driven decisions.
MySQL vs SQL
It's important to note that MySQL is not an alternative to SQL but rather an implementation of it. When comparing MySQL to SQL, we're essentially comparing a specific RDBMS to the broader SQL language. However, there are key distinctions worth highlighting:
Features and Functionality: MySQL offers additional features beyond the standard SQL language, such as support for transactions, replication, and stored procedures. These features enhance MySQL's capabilities but may not be present in all SQL-compliant databases.
Performance and Scalability: MySQL is renowned for its performance and scalability, particularly in web-based applications with high concurrency. Its optimized query execution and efficient storage engine contribute to faster response times and improved throughput compared to some other SQL-based databases.
Licensing and Support: While SQL is a standardized language with multiple implementations, MySQL is governed by Oracle Corporation, which provides commercial support and services for enterprise users. However, there are also open-source distributions of MySQL available for users who prefer community-driven development and support.
Best Place to Learn SQL and MySQL
For those interested in mastering SQL and MySQL, there are numerous resources available online.These are some of the places where you can learn both SQL as well as MySQL are mentioned down below:
Online Courses: Platforms like Coursera, Udemy, and Codecademy offer comprehensive courses on SQL and MySQL, catering to learners of all skill levels. These courses typically include video lectures, hands-on exercises, and quizzes to reinforce learning.
Institute and Training Center: There are many institutes which offer SQL and MySQL courses which are actually included in the Data Science course. If you want best career guidance as well as training from experts then do check Milestone Institute of Technology for better learning and placement. They also provide internships as well as personal training if required.
Conclusion
In conclusion, while SQL and MySQL are closely related, they serve distinct purposes within the realm of data management. Understanding their differences and applications is crucial for making informed decisions when selecting a database solution. By leveraging the right technology for the job and investing in continuous learning, individuals and organizations can harness the power of SQL and MySQL to drive innovation and success.
0 notes
Text
4 Udemy Paid Courses for Free with Certification (Limited Time for Enrollment)

1. 07 Days of Code | Python Programming BootCamp
Python Programming Language with Full Practical, Exercises, Assignments, Problems and their Solutions.
What you'll learn
You will learn Python within few days with practical examples, exercises, assignments, and problems with solutions.
You will learn Fundamental of Python as data types, Input / Output Operations, List, Tuples, Dictionary, SET, Decision Making, Loops, Functions etc
You will learn Python Programming with solving Real World Problems with their solution.
You will learn how to create a Python based website.
You will get Python based Quiz at the end of the Course
By the end of this 7-day course, students will have the confidence and skills to learn more advanced Python topics, such as machine learning, data science, and
By the end of this course, students will have a solid understanding of Python programming fundamentals and be able to write basic Python programs.
Take This Course
👇👇👇👇👇👇👇
4 Udemy Paid Courses for Free with Certification (Limited Time for Enrollment)
2. Java And PHP Complete Course
Learn Java Programming And PHP Programming In One Complete Course
What you'll learn
You will learn how to write a complete Java program that takes user input, processes and outputs the results
You will learn java concepts such as console output, Java Variables and Data Types, Java Operators And more
You will learn PHP concepts such as basic syntax, input and output techniques, and console IO
You will learn PHP arithmetic, assignment, conditional, comparison operators
You will learn PHP loops and conditional statements,POST and GET and more.
Take This Course
👇👇👇👇👇👇👇
4 Udemy Paid Courses for Free with Certification (Limited Time for Enrollment)
3. Learn Coding with Java from Scratch: Essential Training
Mastering Java 17 with the modern features, know how it works. Become A Professional Java Developer in no time!
What you'll learn
Introduction to coding with Java
Java Tools and Setup
Variables, Data Types, Casting, Operators, and doing Mathematics
Strings and Working with text using Java Techniques
Flow control and Making Different Decisions: if - else if - else, and switch - case
Loops, Repetitions, and Iterations: while, do while, for, and Controlling blocks
Working with Arrays in depth
Methods and functional programming in Java
Object-Oriented Programming: Classes, Objects, Attributes, Modifiers, and More
Advanced Object-Oriented Programming: Inheritance, Interfaces, Enumerations and More
Take This Course
👇👇👇👇👇👇👇
4 Udemy Paid Courses for Free with Certification (Limited Time for Enrollment)
4. Object-Oriented Programming (OOP) - Learn to Code Faster
Learn and Practice Object-Oriented Programming(OOP) with Python, Know how it works, and Learn how to code faster 2024
What you'll learn
Understand the benefit of using Object-Oriented Programming
Learn how to build programs faster in Python
Use and apply the classes and instances components and tools with many examples
How to use different types of inheritance in different scales
Learn Encapsulation for wrapping code and data together into a single unit
Learn all about Access Modifiers and Getters and Setters
How to use and apply Polymorphism in an object oriented style with many examples
Learn how to abstract a problem in OOP in action
Practice Object oriented programming, basics to advanced level, using Modern Python
Get the instructor QA support
Take This Course
👇👇👇👇👇👇👇
4 Udemy Paid Courses for Free with Certification (Limited Time for Enrollment)
0 notes