Northwest Arkansas's hacker, INFOSEC, and cybersecurity community.
Don't wanna be here? Send us removal request.
Text
Hey y'all, there's been a zero-day vulnerability found in WinRAR, so you gotta update it if you're on an older version (anything below 6.24/6.23). It doesn't auto update so you need to do it manually. It's been around for a few months and has been fixed, but if you don't update your shit then your computer will still be vulnerable.
please reblog this so that people learn about it or whatever (10/19/23)
10K notes
·
View notes
Link
Tonight we’re talking about Juice Shop. It’s an example web application built for hackers to practice on. If you’re familiar with the older Damn Vulnerable Web App (DVWA), it’s a similar tool.
Tonight’s ArkanSec will be livestreamed on Discord from our meeting at Grub’s. Hope to see you there!
0 notes
Text
OSINT with NCPTF
Last night we talked with a representative of the National Child Protection Task Force. This non-profit group uses Open Source Intelligence (OSINT) to help identify missing & exploited children as well as the traffickers & predators that target them.
Some of the tools that were discussed were:
OSINT COLLECTION
Image metadata Viewer - Online tool for viewing image metadata, which may include information on the camera/device that took the picture, geotagging, and other relevant details
The Ultimate OSINT Collection - A collection of tools by hatless1der in a single page.
WhatsMyName.app - Provides a place to search a single username across multiple websites & social media platforms.
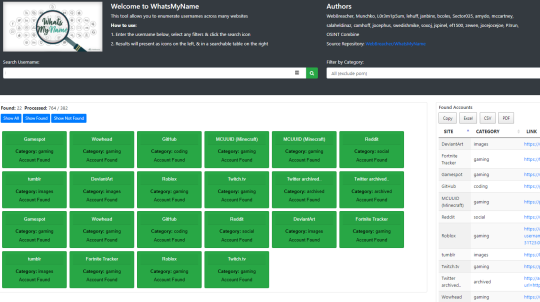
UserSearch.org - Search by username or email on Social Networks, Dating Sites, Forums, Crypto Forums, Chat Sites and Blogs.
Namechk.com - Search across 90 social media account platforms
knowem.com - Search across 500 social networks and other sites, including USPTO.

instantusername.com & CheckUsernames - check multiple social media networks to see if a username is available
host.io - domain name data, including backlinks
epieos.com - Search for an email address to tell whether that address is associated with a Google ID, and what information that Google ID has made public. Includes additional site searches, such as eventbrite, linkedin, adobe, and reverse-image extension.
Google Dorking - Information on how to do targeted searches inside documents, pages, and other google-indexed items with usernames, phone numbers, and other relevant data.
NOTE TAKING & VISUALIZATION
CherryTree - Alternative to OneNote

Hunchly - Note-taking & aggregation tool, records viewing history, tabs, and other artefacts while you view them.

BLOGS & TWITTER FEEDS
Blogs & Reading list for those interested in learning more about OSINT:
https://osintcurio.us/
https://webbreacher.com/
https://inteltechniques.com/
https://www.social-engineer.com/
Helpful Twitter Follows
hatless1der
webbreacher
inteltechniques
humanhacker
Justin Seitz
11 notes
·
View notes
Text
SANS CTI Day 2
For folks interested in more Cyber Threat Intelligence information, or just interested in how to get started in CTI, Here’s a list specifically for new folks, again by Katie Nickels.
If you’re just interested in speakers from the event, there’s a Twitter List going around that contains speakers from the event, plus other security analysts worth following.
1 note
·
View note
Text
Cyber Threat Intelligence Reading Lists
Today is the first day of SANS Cyber Threat Intelligence Summit. During one of the talks, there was a helpful conversation on “recommended readings” for CTI professionals. Scott Roberts (author of Intelligence-Driven Incident Response & Manager of CTI at Splunk) and Katie Nichols (Director of Intelligence at Red Canary & contributing author to the MITRE ATT&CK framework) have written up some really good recommendations. A few books appeared on both of their lists:
Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains by Hutchins, Cloppert & Amin —
The Diamond Model of Intrusion Analysis by Sergio Caltagirone, Andrew Pendergast, and Chris Betz
Psychology of Intelligence Analysis by Richards Heuer
From Scott Roberts:
The Cuckoo’s Egg
Secrets and Lies
Incident Response & Computer Forensics, Third Edition
Practical Malware Analysis
Thwarting Enemies at Home and Abroad
Structured Analytic Techniques For Intelligence Analysis
Dark Territory
Threat Intelligence: Collecting, Analysing, Evaluating
Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains by Hutchins, Cloppert & Amin —
The Diamond Model of Intrusion Analysis by Caltagirone, Pendergast, & Betz —
Psychology of Intelligence Analysis by Heuer
From Katie Nickels
Industrial Control Threat Intelligence by Sergio Caltagirone
Psychology of Intelligence Analysis by Richards Heuer
Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains by Eric Hutchins, Michael Cloppert, and Rohan Amin
The Diamond Model of Intrusion Analysis by Sergio Caltagirone, Andrew Pendergast, and Chris Betz
MITRE ATT&CK™: Design and Philosophy by Blake Strom, et al
A Brief History of Attribution Mistakes by Sarah Jones
CTI SquadGoals — Setting Requirements by Scott J. Roberts
Threat Intelligence Naming Conventions: Threat Actors, & Other Ways of Tracking Threats by Robert M. Lee
Does a BEAR Leak in the Woods? by Toni Gidwani
Cyber Intelligence Tradecraft Report — The State of Cyber Intelligence Practices in the United States by Jared Ettinger
0 notes
Text
Log4Shell Resources
For those coming to our January meeting, here are some resources you can use to familiarize yourself with Log4Shell / CVE-2021-44228:
Sample Log4Shell Vulnerable App by christophetd
Log4J2 Security Vulnerabilities page
Log4J2 Release History
JNDI Injection Exploit by welk1n
Initial Log4Shell POC by tangxiaofeng7
LunaSec write-up on Log4Shell
JNDIExploit by feihong-cs
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228 youTube video by LiveOverflow
0 notes
Text
Security Headlines for September 2019
At this month’s meeting we will be going over the following headlines from the past few weeks:
Google expands Bug Bounty program
Cops purge RETADUP botnet
Imperva admits massive breach
iPhones hacked via web visits
MalwareTech gets no jail team
Twitter CEO gets hacked
Former Amazon engineer dumps data from Capital One & other unsecured AWS systems
Malware found in CamScanner app for Android
TSA implements facial recognition in Las Vegas
8chan removed from clearnet
State Farm reports credential stuffing incident as Data Breach
Pentagon tests surveillance balloons over midwest
Judge allows cryptocurrency suit against AT&T
Commando VM focuses on pentesting with Windows
Ukrainian power plant used to mine cryptocurrency
Valve denies NIST advisory
VMWare buys Carbon Black
Russian voting blockchain cracked a month before elections,
XKCD forums hacked
0 notes
Text
May Download Speaker #1
CTF Design & Implementation
Our first speaker is Ashley B. White, who had the opportunity to host a CTF for the Bentonville schools intern program. He used Facebook’s open source CTF platform for scoring, DVWA for the application CTF, and hosted those components along with some vulnerable networks services (FTP/SMB) for the network CTF in Microsoft’s Azure platform. The presentation will cover methods & lessons learned, and will be especially interesting to those looking to build future CTFs.
0 notes
Photo
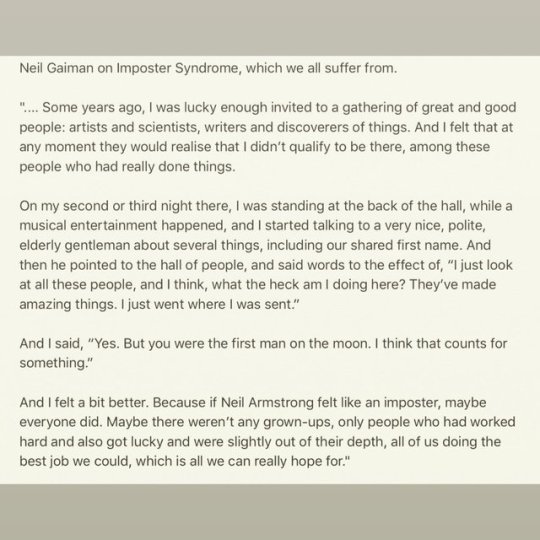
Neil Gaiman on impostor syndrome.
37K notes
·
View notes
Text
ArkanSec will not be meeting this weekend and there is no January Download. We will have an administrative meeting later this month and continue our regularly scheduled events in February.
Happy New Year!
0 notes
Text
Recap: December Download
We had a good time last night at Foghorn’s. Thanks to everyone that came out. If you missed it, here’s a brief recap:
Introductions
Some of our friends from the 2600 club in Fort Smith drove up and talked about the upcoming Shell on the Border CTF on January 26-28. If you’re interested in participating or joining a team, give us a shout and we’ll connect you with other folks starting a team. People concerned about the price tag should still reach out, as there may be options for students or other individuals intimidated by the registration fee.
Survey
We introduced our first “RTFM” survey, asking the attendants what topics they would like to hear more about. From our current list of topics, these were the 5 most popular:
burpsuite
honeypots
nmap
penetration testing
SDNS (Software Defined Networks)
If you are interested in presenting on these or any other security-related topics, please send an email to [email protected] or shoot us a DM on twitter @ArkansecNWA.
Headlines
We briefly discussed some of the major news items of the past month, such as:
MacOS Root vuln
Uber admits to paying off hackers
Satori botnet builds up steam
SWIFT sends out vague warning
Google sued over privacy violations (UK)
INSCOM data left on AWS machines
FAFSA criticized for risking student data
Supreme Court & 3rd party warrants
RTFM: Maltego
We took a look at Maltego and introdued the OSIN collection & intellgience analyst tool. Our guest speaker was a threat intelligence professional who was interested in solving various puzzles using the free Community Edition included with Kali.
Announcements
There will be no January Download. Instead, ArkanSec will meet to establish a Board of Directors and make some plans for 2018. This is an open meeting that anyone is welcome to attend. Details to follow.
0 notes
Text
Get Connected to ArkanSec
Hey folks -
It’s been a while since we updated the blog, but hopefully you’ve been following us on Facebook to see what we have going on. If you’re looking for how to connect with hcakers & INFOSEC folks in Northwest Arkansas, we’d love to see you! We’re currently working on a website overhaul, but until that happens, here’s where you can track us down online:
Mailing List - Don’t want to have to hunt down information about us from across the Internet? Then don’t! Sign up for our monthly newsletter and we’ll let you know what’s going on. (No spam, we promise.)
Slack - If collaborative communities are your thing, then come join our slack channel and see what interesting projects folks are working on or what we’re trying to plan for our next events. To get an invite to Slack, send a message with your email address to our facebook page and we’ll get one sent your way.
EventBrite - All of our events will be posted on EventBrite, including our Monthly Download. Come hang out on the first Wednesday of the month for a recap of all the great and terrible security news updates from the past 30 days.
Facebook - For those of you in security that haven’t already sworn off of Facebook, we have a Page there to help promote events & engage folks online.
Twitter - Follow our Twitter feed for information about local events, CTFs, and trending security topics.
LinkedIn - If you’re interested in networking and making some professional connections, we’ve got a group on LinkedIn.
1 note
·
View note
Photo

T-shirts are in! For $20 you can celebrate the launching of Northwest Arkansas's own Capture the Flag tournament with an ArkanSec t-shirt that has our logo on the front. Members of the winning team will each receive the "HACKER 16" shirt pictured here, as well as free admission to next year's events.
0 notes
Text
DoSing other competitors during a CTF
by @liamosaur
19 notes
·
View notes
Text
When I finally learn the answer to that ctf challenge
by piffd0s
5 notes
·
View notes
Text
When they announce the top 3 winners of the CTF, and I'm not one of them
by @joshdustin
2 notes
·
View notes
Text
Got flag in CTF, cannot submit flag because site is down.
by @RlIxOTA4
12 notes
·
View notes