Don't wanna be here? Send us removal request.
Text
If you’re looking to create a reverse SOCKS proxy, the TL;DR solution to do so is to run the following commands on the machine you want to proxy from:
ssh -D 6666 local-user@localhost
ssh -R 6666:localhost:6666 remote-user@remotehost
And then you just point your browser to 127.0.0.1:6666.
If you’d like context, or you’re curious as to why something like this might be helpful, let me explain.
Background
I was recently working on a penetration test of a wireless network. Since I’m writing this in 2020, when COVID-19 is still... around, it’s probably not going to be surprising that I didn’t do this penetration test in person, so the setup was going to be weird for a wireless test to begin with.
My laptop needed to connect to a VM with a reverse SSH tunnel (over 4G) to a wireless enabled jump box that was in range of the target network in order to access the router.
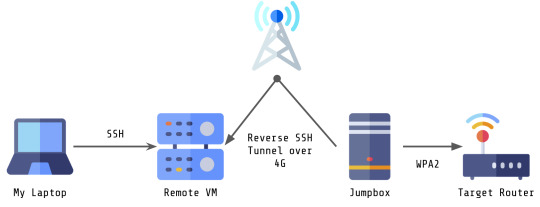
This connection was SUPER slow. Furthermore, there was only really one interesting target on the network at the time of the test, and that was the router which only had HTTPservices running. One fairly traditional way of opening a browser in a VM or host you’re SSH-ing to is to use X11 forwarding, but due to the connection speed, this would have taken about an hour to render one webpage.
Approach
I chose to circumvent the remote VM and the 4G connection by establishing a reverse SOCKS5 proxy over SSH from my jumpbox to my laptop. I accomplished this with a few simple steps.
1. The first thing I had to do was make sure my laptop had SSH accessible via some address. In this example, we’ll say my laptop was addressable as remotehost. So if I were to say, connect via SSH using the following command:
ssh kali@remotehost
That would give me a session on my laptop as the user kali, who already exists on my laptop.
2. Next, I ran two commands on my jumpbox.
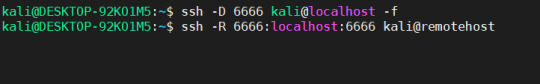
The first command, ssh -D 6666 kali@localhost opens port 6666 as a SOCKS proxy server which is now running locally. I do this as the kali user that is on the jumpbox. The -f command just puts this in the background.
The second command, ssh -R 6666:localhost:6666 kali@remotehost forwards a connection over SSH to the remote server. It uses the format port:host:hostport. The remote server will use the first port for connecting to the SOCKS proxy running on localhost:6666. If I wanted to I could forward any other port, such as 1337, using ssh -R 1337:localhost:6666 kali@remotehost.
Keep in mind: In both of these commands, the user is kali, since both machines are running Kali Linux. In the first command, this is the user on the jumpbox. In the second command this is the user on the remote host. This is because forwarding this connection actually requires us to connect to the remote host over port 22 (or whatever port SSH is running on).
3. Finally, I can connect to the SOCKS proxy on my laptop. Because the proxy is already being forwarded, all I have to do is configure my browser to use this proxy.
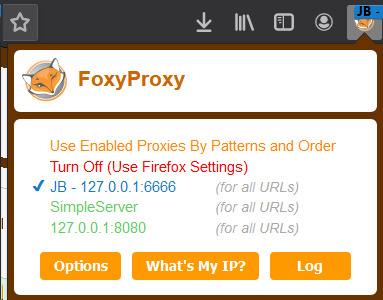
I personally chose to do this with FoxyProxy, but you can do this with any proxy tool by pointing your proxy at 127.0.0.1:6666.
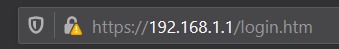
And with that, I can now connect directly to the router page by pointing my browser at 192.168.0.1!
In the end, the way my setup looks is as follows:
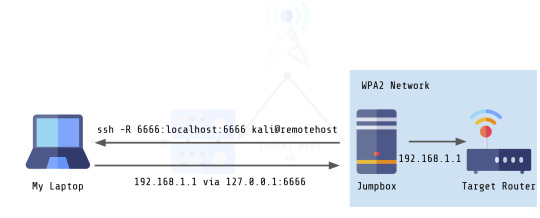
Much less complicated, much faster! Anyway, I hope this helps somebody with a project that they might be working on! :)
3 notes
·
View notes