Don't wanna be here? Send us removal request.
Text
Mass Hunting for CVE-2025-24813 – Apache Tomcat PUT RCE
Introduction: Apache Tomcat servers running vulnerable versions are currently exposed to a critical unauthenticated remote code execution (RCE) vulnerability – CVE-2025-24813. This flaw is caused by the PUT method being enabled by default, which allows an attacker to upload arbitrary files to the server. If exploited properly, this can lead to remote code execution.Here’s a quick look at the…
0 notes
Text
Pickle Rick Tryhackme Walkthrough
Introduction: This Pickle Rick TryHackMe walkthrough will guide you through a fun, Rick and Morty-themed challenge that requires you to exploit a web server and find three ingredients to help Rick make his potion and transform himself back into a human from a pickle. Available for free on Tryhackme, this room is beginner-friendly—just join, start the machine, and follow this walkthrough to…
0 notes
Text
How I Added Money Without OTP Verification
Introduction: When a Bug Finds You I wasn’t trying to be a hacker that day. I wasn’t running Burp Suite, intercepting requests, or testing for vulnerabilities. I was just a regular user, casually adding money to my wallet, when I noticed something strange: there was no OTP verification in online payments. You know that mandatory OTP verification every time you make an online transaction? That…
0 notes
Text
WordPress Bug Bounty Guide
IntroductionWordPress is the most popular CMS, powering over 40% of websites. This widespread use makes it a prime target for hackers—and an excellent opportunity for ethical hackers and bug bounty hunters. Companies and website owners rely on security researchers to find and report vulnerabilities before malicious attackers exploit them. If you’re new to bug hunting and want to explore…
0 notes
Text
A quick guide to smb enumeration
Introduction SMB (Server Message Block) is a widely used file-sharing protocol in Windows and Linux environments. While it enables seamless file and printer sharing, misconfigured SMB services can expose sensitive data, leading to serious security risks. That’s why SMB enumeration is a critical step in penetration testing, allowing ethical hackers to gather valuable system, user, and…
0 notes
Text
A detailed guide to rustscan
0 notes
Text
Subdomain Enumeration: A Complete Guide
Hey everyone, Welcome to pentestguy, In this article, we are going to focus on the subdomain enumeration in detail, but it will be in an automatic way where we are combining different tools and trying to gather subdomains as much as possible. Why is Subdomain Enumeration required? The answer to this question is simple, an organization may have different products/services for internal or…
0 notes
Text
A quick guide to CeWL
Hi everyone, Welcome to Pentestguy. This article will focus on a quick guide to cewl, one of the most powerful tools used for custom wordlist generation. There are other tools available for generating a custom wordlist, like crunch, but cewl is serving a different purpose. Every pentester should add the custom wordlist approach in their methodology, this will help to give better results, and…
0 notes
Text
Jangow: 1.0.1 Vulnhub CTF Walkthrough
Hello everyone, Welcome to Pentestguy. In this post we are going to see the walkthrough of the Jangow: 1.0.1 Capture the Flag (CTF) challenge available on Vulnhub. In this Jangow: 1.0.1 vulnhub walkthrough we will cover the initial port scanning, enumeration, command injection, finding the credentials, and privilege escalation to the root user (this ctf contains two flags). Let’s dive into the…
0 notes
Text
Exploiting Race Conditions in API
Hi everyone, welcome to Pentestguy! In this post, we’re diving into exploiting race conditions in API. We’ll set up our own vulnerable API to demonstrate how race conditions occur and explore methods for exploiting them effectively. What is Race Condition? A race condition happens when two or more processes or actions try to access or change the same data at the same time, and the final outcome…
0 notes
Text
Install Metasploit on android (rootless)
Hi everyone, welcome to Pentestguy. This article will show how to install metasploit on an Android (rootless) device. Here we will use termux to install metasploit on an android device (rootless) which is the best way to do it successfully. Metasploit is one of the most widely used frameworks for vulnerability assessment and penetration testing, commonly utilized by both ethical hackers and…
0 notes
Text
Detailed Walkthrough on Evil-WinRM
Hi everyone, welcome to Pentestguy! In this post, we will provide a detailed walkthrough on Evil-WinRM. This detailed walkthrough on Evil-WinRM will cover everything you need to know about using this powerful tool for remote access and command execution in penetration testing scenarios. Whether you’re new to Evil-WinRM or looking to enhance your skills, this detailed walkthrough on Evil-WinRM…
0 notes
Text
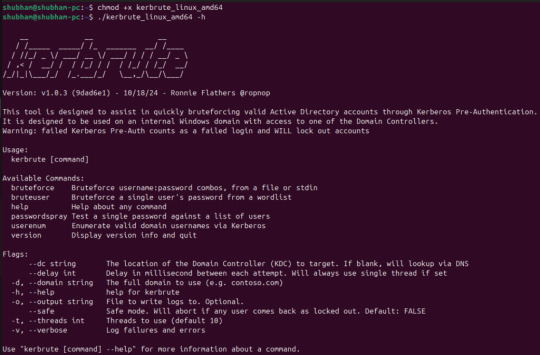
A Detail Duide to Kerbrute
Hi everyone, welcome to pentestguy. In this post, we are going to focus on kerbrute, what is kerbrute and how to use the different options available in kerbrute. What is Kerbrute? Kerbrute is a tool written in go language which help enumerate and bruteforce valid Active Directory accounts through Kerberos Pre-Authentication. Kerbrute has four main commands which are given below – bruteuser –…
View On WordPress
1 note
·
View note
Text
ZAP Automation Framework in CI/CD
Hi everyone, welcome to pentestguy. In this post, we are going to discuss the ZAP Automation Framework in CI/CD, specifically how to implement the ZAP Automation Framework in your CI/CD pipeline to enhance security testing and streamline the integration process. ZAP Automation Framework? ZAP Automation Framework is an extension of the ZAP tool. It enhances ZAP’s capabilities by providing…
0 notes
Text
MobSF Automation in CI/CD Pipeline
Hi everyone, Welcome to pentestguy. In this post, we are going to focus on how to set up and run mobsf automation in the ci/cd pipeline. We are using the Azure platform to run the mobsf automation and there creating a simple pipeline. What is MobSF-Automation? In the development process of any mobile application, there is a continuous process, where every time new code gets deployed and…
0 notes
Text
Dependency-Check in Azure DevOps
Hi everyone, In this post we are going to setup OWASP dependency-check in azure devops. As this process is the part of Software Composistion Analysis(SCA) which is really important phase in secure software development lifecycle. OWASP Dependency-Check is one of the popular SCA tool and implementing it in azure devops pipeline. What is Software Composition Analysis? Software Composition Analysis…

View On WordPress
#dependency-check#known vulnerabilities#nvd#nvdapikey#owasp-dependency-check#pentestguy#software-composition-analysis
0 notes
Text
Browser Extensions for Bug Hunters
Hello everyone! Welcome to Pentestguy. In this article, we will see the browser extensions for bug hunters. Which makes tasks easy in a more efficient way. There are many browser extensions available for bug bounty hunters or pentesters but here we are discussing the top browser extensions which help bug hunters. DotGit: DotGit is a powerful extension that allows you to check if a website has…

View On WordPress
1 note
·
View note