#subdomain-enumeration
Explore tagged Tumblr posts
Text
Subdomain Enumeration: A Complete Guide
Hey everyone, Welcome to pentestguy, In this article, we are going to focus on the subdomain enumeration in detail, but it will be in an automatic way where we are combining different tools and trying to gather subdomains as much as possible. Why is Subdomain Enumeration required? The answer to this question is simple, an organization may have different products/services for internal or…
0 notes
Text
A Comprehensive Guide to Bug Hunting
This guide provides a structured, step-by-step approach to bug hunting, focusing on reconnaissance, subdomain enumeration, live domain filtering, vulnerability scanning, and JavaScript analysis.
It incorporates essential tools like SecretFinder, Katana, GetJS, Nuclei, Mantra, Subjs, Grep, and Anew to enhance efficiency and coverage.
1. Initial Reconnaissance
Gather information about the target to identify IP blocks, ASNs, DNS records, and associated domains.
Tools and Techniques:
ARIN WHOIS: Lookup IP blocks and ownership details.
BGP.HE: Retrieve IP blocks, ASNs, and routing information.
ViewDNS.info: Check DNS history and reverse IP lookups.
MXToolbox: Analyze MX records and DNS configurations.
Whoxy: Perform WHOIS lookups for domain ownership.
Who.is: Retrieve domain registration details.
Whois.domaintools: Advanced WHOIS and historical data.
IPAddressGuide: Convert CIDR to IP ranges.
NSLookup: Identify nameservers.
BuiltWith: Discover technologies used on the target website.
Amass: Perform comprehensive information gathering (subdomains, IPs, etc.).
Shodan: Search for exposed devices and services.
Censys.io: Identify hosts and certificates.
Hunter.how: Find email addresses and domain-related data.
ZoomEye: Search for open ports and services.
Steps:
Identify the target domain and associated IP ranges.
Collect WHOIS data for ownership and registration details.
Map out nameservers and DNS records.
Use Amass to enumerate initial subdomains and IPs.
Leverage Shodan, Censys, and ZoomEye to find exposed services.
2. Subdomain Enumeration
Subdomains often expose vulnerabilities. The goal is to discover as many subdomains as possible, including sub-subdomains, and filter live ones.
Tools and Techniques:
Subfinder: Fast subdomain enumeration.
Amass: Advanced subdomain discovery.
Crt.sh: Extract subdomains from certificate transparency logs.
Sublist3r: Enumerate subdomains using multiple sources.
FFUF: Brute-force subdomains.
Chaos: Discover subdomains via ProjectDiscovery’s dataset.
OneForAll: Comprehensive subdomain enumeration.
ShuffleDNS: High-speed subdomain brute-forcing (VPS recommended).
Katana: Crawl websites to extract subdomains and endpoints.
VirusTotal: Find subdomains via passive DNS.
Netcraft: Search DNS records for subdomains.
Anew: Remove duplicate entries from subdomain lists.
Httpx: Filter live subdomains.
EyeWitness: Take screenshots of live subdomains for visual analysis.
Steps:
Run Subfinder, Amass, Sublist3r, and OneForAll to collect subdomains.
Query Crt.sh and Chaos for additional subdomains.
Use FFUF and ShuffleDNS for brute-forcing (on a VPS for speed).
Crawl the target with Katana to extract subdomains from dynamic content.
Combine results into a single file and use Anew to remove duplicates: cat subdomains.txt | anew > unique_subdomains.txt
Filter live subdomains with Httpx: cat unique_subdomains.txt | httpx -silent > live_subdomains.txt
Use EyeWitness to capture screenshots of live subdomains for manual review.
3. Subdomain Takeover Checks
Identify subdomains pointing to unclaimed services (e.g., AWS S3, Azure) that can be taken over.
Tools:
Subzy: Check for subdomain takeover vulnerabilities.
Subjack: Detect takeover opportunities (may be preinstalled in Kali).
Steps:
Run Subzy on the list of subdomains: subzy run --targets live_subdomains.txt
Use Subjack for additional checks: subjack -w live_subdomains.txt -a
Manually verify any flagged subdomains to confirm vulnerabilities.
4. Directory and File Bruteforcing
Search for sensitive files and directories that may expose vulnerabilities.
Tools:
FFUF: High-speed directory brute-forcing.
Dirsearch: Discover hidden directories and files.
Katana: Crawl for endpoints and files.
Steps:
Use FFUF to brute-force directories on live subdomains: ffuf -w wordlist.txt -u https://subdomain.target.com/FUZZ
Run Dirsearch for deeper enumeration: dirsearch -u https://subdomain.target.com -e *
Crawl with Katana to identify additional endpoints: katana -u https://subdomain.target.com -o endpoints.txt
5. JavaScript Analysis
Analyze JavaScript files for sensitive information like API keys, credentials, or hidden endpoints.
Tools:
GetJS: Extract JavaScript file URLs from a target.
Subjs: Identify JavaScript files across subdomains.
Katana: Crawl for JavaScript files and endpoints.
SecretFinder: Search JavaScript files for secrets (API keys, tokens, etc.).
Mantra: Analyze JavaScript for vulnerabilities and misconfigurations.
Grep: Filter specific patterns in JavaScript files.
Steps:
Use Subjs and GetJS to collect JavaScript file URLs: cat live_subdomains.txt | subjs > js_files.txt getjs --url https://subdomain.target.com >> js_files.txt
Crawl with Katana to find additional JavaScript files: katana -u https://subdomain.target.com -o js_endpoints.txt
Download JavaScript files for analysis: wget -i js_files.txt -P js_files/
Run SecretFinder to identify sensitive data: secretfinder -i js_files/ -o secrets.txt
Use Mantra to detect vulnerabilities in JavaScript code: mantra -f js_files/ -o mantra_report.txt
Search for specific patterns (e.g., API keys) with Grep: grep -r "api_key\|token" js_files/
6. Vulnerability Scanning
Perform automated scans to identify common vulnerabilities.
Tools:
Nuclei: Fast vulnerability scanner with customizable templates.
Mantra: Detect misconfigurations and vulnerabilities in web assets.
Steps:
Run Nuclei with a comprehensive template set: nuclei -l live_subdomains.txt -t cves/ -t exposures/ -o nuclei_results.txt
Use Mantra to scan for misconfigurations: mantra -u https://subdomain.target.com -o mantra_scan.txt
7. GitHub Reconnaissance
Search for leaked sensitive information in public repositories.
Tools:
GitHub Search: Manually search for target-related repositories.
Grep: Filter repository content for sensitive data.
Steps:
Search GitHub for the target domain or subdomains (e.g., from:target.com).
Clone relevant repositories and use Grep to find secrets: grep -r "api_key\|password\|secret" repo_folder/
Analyze code for hardcoded credentials or misconfigurations.
8. Next Steps and Analysis
Review EyeWitness screenshots for login pages, outdated software, or misconfigurations.
Analyze Nuclei and Mantra reports for actionable vulnerabilities.
Perform manual testing on promising subdomains (e.g., XSS, SQLi, SSRF).
Document findings and prioritize vulnerabilities based on severity.
Additional Notes
Learning Resources: Complete TryHackMe’s pre-security learning path for foundational knowledge.
Tool Installation:
Install Anew: go install github.com/tomnomnom/anew@latest
Install Subzy: go install github.com/PentestPad/subzy@latest
Install Nuclei: go install github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Install Katana: go install github.com/projectdiscovery/katana/cmd/katana@latest
Optimization: Use a VPS for resource-intensive tools like ShuffleDNS and FFUF.
File Management: Organize outputs into separate files (e.g., subdomains.txt, js_files.txt) for clarity.
1 note
·
View note
Text
SQLMutant: Advanced Tool for SQL Injection | #Pentesting #RedTeam #SQLInjection #SQLi #SQLMutant #Hacking
1 note
·
View note
Text
فحص واستغلال سب دومين AzSubEnum
AzSubEnum السلام عليكم متابعين قناة ومدونة Shadow Hacker في هذا المقال سوف نستعرض أداة راعه جداً مخصصه في استخراج subdomain واستغلال الثغرات الموجودة فيها تم تصميم أداة AzSubEnum بهدف فحص النطاقات الفرعية بدقة عاليه جداً وفحص جميع النطاقات الفرعية من خلال مجموعة من التقنيات المتواجدة في الأداة فاذا كنت من المهتمين في مجال اكتشاف الثغرات وأختبار الأخلاقي فهذة الأداة ستكون ذو فائدة كبيرة للك.AzSubEnum
فحص واستغلال سب دومين AzSubEnum
AzSubEnum واحدة من اقوى الأدوات في مجال اصتياد الثغرات الأمنيه في المواق�� والسيرفرات وتوفر لك مميزات عديدة مثل فحص العميق الذي يخول لك فحص واستخراج جميع الثغرات المتواجدة في النطاق الفرعي , كما انها تستخرج جميع النطاقات الفرعية بشكل دقيق جداً في الدومين , تعمل أداة AzSubEnum من خلال تحليل DNS بشكل مبتكر وتحليل النطاتقات الفرعية بشكل دقيق عبر قواعد البيانات مثل (including MSSQL, Cosmos DB, and Redis).
بستخدام أداة AzSubEnum يمكن تحليل شامل لـ Subdomain في مفيدة جداً للمهتمين في مجال BUG BUNTY او المهتمين في اكتشاف الثغرات المنية بشتى انواعها.
طريقة أستخدام أداة AzSubEnum
➜ AzSubEnum git:(main) ✗ python3 azsubenum.py --help usage: azsubenum.py [-h] -b BASE [-v] [-t THREADS] [-p PERMUTATIONS] Azure Subdomain Enumeration options: -h, --help show this help message and exit -b BASE, --base BASE Base name to use -v, --verbose Show verbose output -t THREADS, --threads THREADS Number of threads for concurrent execution -p PERMUTATIONS, --permutations PERMUTATIONS File containing permutations
Basic enumeration:
1 note
·
View note
Text
WebCopilot: Open-source automation tool enumerates subdomains, detects bugs
http://securitytc.com/T4NW9l
0 notes
Text
Productivity Log 11/02/23 +
11/03/23
I forgot to log yesterday and I'm feeling a little lazy so another 2 day post it is!
Personal Things 🌱
Still watching these good doggos!
Got my hair cut! I've been going shorter every time and I love it.
I've been listening to more music as I do things around the house and it makes life just so much more enjoyable
I.T. Computer Girly Things 🤖
Applied to three more jobs. One of them I'm really excited about -It's a reach, but it's in the field I want to end up in and I would have regretted not applying.
Completed lessons and labs on content discovery, subdomain enumeration, authentication bypass and IDOE vulnerabilities on TryHackMe.
Other Things 👾
I stopped by a cd store and a thrift store for some CDs. Got a good haul and listened to Shinedown's album The Sound of Madness on the way home. I forgot how much I loved that album as a tween!
I got a bottle of Snoop Dog's wine. I want to use it as a candle holder once it's empty lol. It's pretty good too and cheap.
Suga from BTS was in my dream last night. He's the only member that has been in them which I find really funny.
Gave Golden a listen to as well!
0 notes
Text
What is footprinting?

In the realm of cybersecurity, knowledge is power, and the first step in defending against potential threats is understanding them. Footprinting, often regarded as the initial phase of a cyberattack, is the process of gathering information about a target, be it an organization, an individual, or a network. In this blog, we will delve into the concept of footprinting, exploring its significance, methodologies, and ethical considerations.
What is Footprinting?
Footprinting, in the context of cybersecurity, refers to the systematic process of gathering information about a target entity, primarily through open-source intelligence (OSINT) techniques. The goal is to create a digital map that encompasses various aspects of the target, such as its infrastructure, employees, technologies, and online presence. This information is invaluable for both defensive and offensive cybersecurity purposes.
Methodologies of Footprinting
Passive Footprinting:
Website Analysis: Analyzing a target's website for publicly available information like contact details, organizational structure, and technology stack.
Social Media Profiling: Scouring social media platforms for clues about the target's employees, their interests, and connections.
WHOIS Lookup: Querying the WHOIS database to find domain registration information, including domain owners and contact details.
Active Footprinting:
Port Scanning: Actively probing the target's network to discover open ports, services, and potential vulnerabilities.
DNS Enumeration: Gathering information about DNS records to unveil subdomains and network topology.
Network Scanning: Using tools like Nmap to identify network devices, their configurations, and vulnerabilities.
Physical Footprinting:
On-Site Reconnaissance: Physical visits to target locations to gather information about security measures, access points, and potential weaknesses.
Also Read: What is the Scope of Ethical Hacking?
Ethical Considerations
It's imperative to approach footprinting ethically, respecting privacy and legal boundaries. Ethical hackers and cybersecurity professionals use these techniques for defensive purposes, helping organizations strengthen their security posture. Unethical or malicious use of footprinting techniques can lead to privacy violations, data breaches, and legal consequences.
Significance of Footprinting
Security Assessment: Footprinting provides organizations with insights into how much information is readily available to potential attackers. This information helps them assess their security measures and make necessary improvements.
Vulnerability Identification: Footprinting reveals potential vulnerabilities, allowing organizations to address weaknesses before they are exploited.
Incident Response: In the event of a security incident, having a pre-existing digital footprint of the organization can aid in identifying the scope and nature of the breach.
Competitive Intelligence: In the business world, footprinting can be used to gather information about competitors, their products, and strategies.
Conclusion
In the ever-evolving domain of cybersecurity, understanding and mitigating potential threats begin with comprehensive knowledge, and footprinting is a fundamental part of this process. Footprinting, when conducted responsibly and ethically, unveils the digital trail that can be vital for security professionals and organizations.
To truly harness the power of footprinting and use it for ethical and defensive purposes, individuals and organizations should consider enrolling in an online ethical hacking course. These courses provide structured learning environments, imparting knowledge about not only footprinting but also a broader array of cybersecurity practices. Importantly, they emphasize the ethical responsibility that accompanies this knowledge.
In conclusion, footprinting, when employed ethically and in tandem with an ethical hacking course, becomes a potent tool for safeguarding digital assets. It equips individuals with the skills and mindset needed to proactively defend against cyber threats, ultimately enhancing the security and resilience of our increasingly interconnected digital world.
0 notes
Text
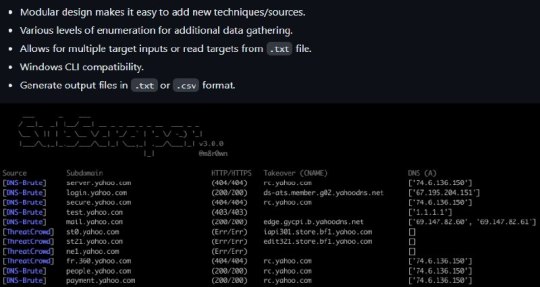
[Media] SubScraper
SubScraper Perform subdomain enumeration through various techniques and retrieve detailed output to aid in further testing. https://github.com/m8sec/subscraper #infosec #pentesting #bugbounty
0 notes
Text
Sunday Round Up - 27 January 2019
amzn_assoc_ad_type = "banner"; amzn_assoc_marketplace = "amazon"; amzn_assoc_region = "US"; amzn_assoc_placement = "assoc_banner_placement_default"; amzn_assoc_campaigns = "amzn_vicc_cloudcam_1017"; amzn_assoc_banner_type = "category"; amzn_assoc_isresponsive = "true"; amzn_assoc_banner_id = "1J0CHGJT75D586M66602"; amzn_assoc_tracking_id = "kraljevicn1-20"; amzn_assoc_linkid = "c122cc4768b349b4aab7d3099b74ea1c";
Sunday Round up for this week!
Articles:
The Top Cybersecurity Breaches of 2018
Why Internet Security Is So Bad
Kubernetes: unauth kublet API 10250 token theft & kubectl
Domained – Multi Tool Subdomain Enumeration
If You Use Freelancers, Do You Need to Educate Them About Security Awareness?
If you found some other interesting stuff this week feel free to leave a link to it in the comments section. Otherwise feel free to check out the last roundup here.
These round ups are brought to you by PassVult.
#PassVult#Cybersecurity#breaches#20128#Why is security so bad#Kubernetes#token theft#kubectl#Domained#Multi tool#Subdomain#enumeration#Freelancers#Education#Security Awareness
1 note
·
View note
Link
0 notes
Text
Omnisci3nt: Unveiling the Hidden Layers of the Web | #Omnisci3nt #Reconnaissance #Web
0 notes
Text
ReconDog v2.0 - Reconnaissance Swiss Army Knife
ReconDog v2.0 - Reconnaissance Swiss Army Knife #Reconnaissance #Hacking #InfoGathering #Hacking
Reconnaissance Swiss Army Knife
Main Features
Wizard + CLA interface
Can extracts targets from STDIN (piped input) and act upon them
All the information is extracted with APIs, no direct contact is made to the target
Utilities
Censys: Uses censys.io to gather massive amount of information about an IP address.
NS Lookup: Does name server lookup
Port Scan: Scan most common TCP ports
Detect CMS: Can…
View On WordPress
#cms detector#command line#Configuration#enumerate subdomains#Honeypot Detector#Information#information Gathering#Management#python#recon#ReconDog#Reverse#scan#Subdomain Enumeration#subdomains
1 note
·
View note
Photo

Aquatone By far the best subdomain enumerator I have ever used, I love this tool-set both Aquatone Discover and Aquatone Scan. I would definitely recommend using this tool if you are a bug bounty hunter! Please note that I used the Nmap Scanme site as to avoid doing anything illegal and as you can see it already pulled the nameservers and does some cool stuff like pulling the subdomains and all their IPs and information! I quite often use this in combination with a very powerful program called Photon but for some reason haven’t been able to install Docker on Parrot because of some weird error. Will update as soon as I am able to fix this.
#Aquatone#subdomain#url#websites#webdevelopment#vulnerability scanner#dns#hacking tools#nmap#github#hacking#ethical hacking#ip address#enumeration
0 notes
Text
[Media] subnerium
subnerium A fast passive subdomain enumeration tool that uses various sources to gather data. All requests are made through yaml templates, to see more see the documentation:👇 https://github.com/d3f1ne/subnerium #infosec #pentesting #bugbounty

2 notes
·
View notes