Don't wanna be here? Send us removal request.
Text

GDPR Compliance: What Businesses Need to Know
In pursuit of protecting EU residents’ personal data, GDPR also exhibits extraterritorial reach, extending its scope beyond EU boundaries. Consequently, non-EU nations may fall under its purview. However, not all Indian businesses must comply with GDPR. Obligation arises for those Indian enterprises offering goods or services in the EU, processing EU-origin personal data, or profiling EU residents’ personal data.
Website: https://skill-mine.com/products/complyment-it-compliance-management-software/
0 notes
Text
Unveiling the Power of Digital Transformation: Skillmine's Expertise
In today's rapidly evolving business landscape, staying ahead of the competition requires more than just traditional approaches. The key to achieving sustainable growth and success lies in embracing Digital Transformation. Skillmine, a prominent Digital Transformation services provider based in Bangalore, is here to empower businesses with innovative solutions that pave the way for unparalleled success.
Website: https://www.slideshare.net/SkillMine3/unveiling-the-power-of-digital-transformation-skillmines-expertise
0 notes
Text
Streamlining Operations with SAP Managed Business Services: A Comprehensive Guide
In the rapidly evolving landscape of business operations, companies are constantly seeking ways to enhance efficiency, optimize processes, and ensure seamless management of their systems and applications. This is where Skillmine, a distinguished systems, applications, and products company based in Bangalore, comes into the picture with its cutting-edge SAP Managed Business Services. In this comprehensive guide, we will delve into the world of SAP managed services and explore how Skillmine is revolutionizing the way businesses streamline their operations.
Website: https://www.slideshare.net/SkillMine3/streamlining-operations-with-sap-managed-business-services-a-comprehensive-guide
0 notes
Text
Exploring the Backbone of Connectivity: 5 Types of Network Operation Processes
In today's hyper-connected world, where digital interactions define our daily routines, the role of seamless networking cannot be underestimated. In this intricate web of data and communication, Network Operations Center Services (NOC Services) emerge as the unsung heroes, ensuring that the digital highways remain smooth and uninterrupted. One such company that stands at the forefront of this mission is Skillmine, a Network Operations Center Services company based in Bangalore. In this blog, we delve into the world of NOC Services and explore the five types of network operation processes that form the cornerstone of their operations.
Website: https://www.slideshare.net/SkillMine3/exploring-the-backbone-of-connectivity-5-types-of-network-operation-processes
0 notes
Text
6 stages of software development life cycle

At a foundational level, software development is writing and maintaining source code. A broader scope includes stages from idea generation to final product manifestation. This increases requirements for sophisticated models and tools. While the industry faces its own challenges, several methodologies have been developed over time to achieve effective and efficient software development.
Website: https://skill-mine.com/service/digital-transformation-services/
0 notes
Text
Benefits of RPA

The organization implemented an RPA system that automated key processes, including patient registration, insurance verification, and claim submission. As a result of the RPA implementation, the healthcare organization significantly reduced the time it took to process insurance claims, resulting in faster reimbursements and improved cash flow.
Website: https://skill-mine.com/service/robotic-process-automation-services/
0 notes
Text
Identity Authentication methods used by MFA Tools
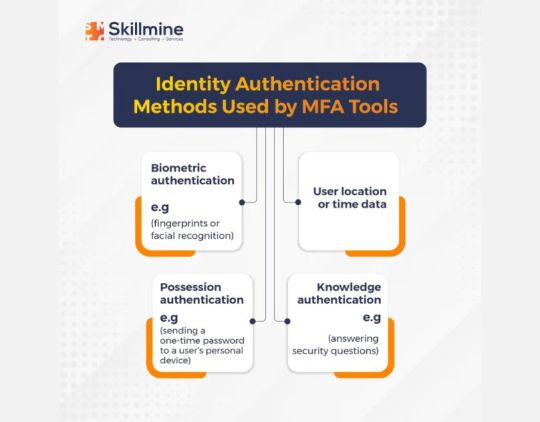
Multi-Factor Authentication (MFA) is a critical component of effective identity and access management practices. Without proper user authentication, an organization’s data may be at risk, and unauthorized users may gain access to sensitive information. MFA tools are designed to simplify and automate the authentication process by requiring two or more forms of validation to confirm a user’s identity. By requiring additional forms of identification, such as a fingerprint scan or a code generated by a mobile app, MFA tools can significantly reduce the risk of unauthorized access to company resources.
Website: https://skill-mine.com/products/best-multifactor-authentication/
0 notes
Text

Benefits of Incident Response plan
The final step in incident response is to learn from the incident. You should conduct a post-incident review to identify what worked well and what needs improvement. You should also update your incident response plan based on the lessons learned from the incident.
Website: https://skill-mine.com/service/cyber-security-services/
0 notes
Text
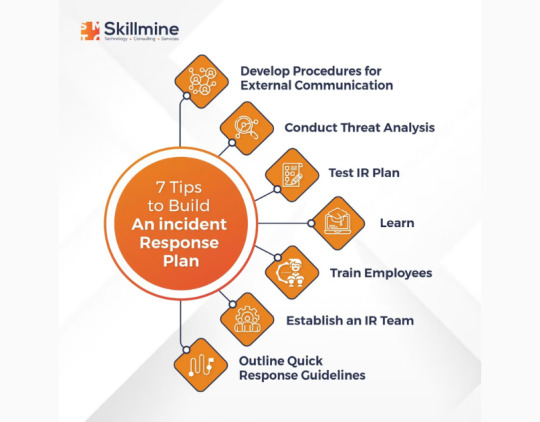
7 tips to build an incident response plan
A cybersecurity incident response plan is a comprehensive and documented set of procedures and guidelines that an organization follows in the event of a security breach or cyber attack. The primary objective of a cybersecurity incident response plan is to minimize the damage caused by a cyber attack and restore normal operations as quickly as possible.
Website: https://skill-mine.com/service/cyber-security-services/
0 notes
Text

Benefits of Single Sign-on
SSO simplifies the user experience by eliminating the need for users to remember multiple sets of credentials. With a single login, users gain access to all authorized applications and systems, enhancing productivity and saving valuable time. Skillmine’s indigenously developed solution Authenticator provides a seamless experience offering Single-Sign-On (SSO) and Multi-Factor-Authentication (MFA). It also offers an additional layer of security coupled with customer identity secrecy at the highest level compatible across different platforms supporting multiple protocols.
Website: https://skill-mine.com/products/best-multifactor-authentication/
0 notes
Text

Mastering Networks: Unraveling the Secrets of NOC Services
AI-powered cybersecurity companies like Skillmine use Machine Learning algorithms to detect and respond to cyber threats. Their technology uses unsupervised Machine Learning to learn what is normal behaviour for a particular network and can quickly detect anomalies that may indicate a cyber-attack. Their AI algorithms detect and respond to previously unknown and advanced cyber-attacks. Security Information and Event Management (SIEM) tools are used to collect, analyze, and respond to security events. AI-powered SIEM tools use Machine Learning algorithms to analyze large amounts of data and identify patterns that may indicate a cyber-attack. These tools can detect and respond to cyber-attacks in real time, improving the organization’s security posture.
Website: https://skill-mine.com/service/security-operations-center-services/
0 notes
Text

Components of Digital Transformation
Customer experience (CX) is the perception that customers have of a business based on their interactions with the company across all touchpoints, including online and offline channels. CX encompasses every aspect of the customer journey, from the initial awareness of a product or service to the post-purchase follow-up. A positive CX can lead to customer loyalty, repeat business, and positive word-of-mouth recommendations, while a negative CX can result in lost revenue, a damaged reputation, and a decrease in customer retention. A leading airline company sought more seamless and personalized experiences in their digital transformation journey after recognizing that its customers’ expectations were evolving. To address these changing demands, the company embarked on a digital transformation journey with a strong focus on enhancing the customer experience.
Website: https://skill-mine.com/how-can-you-leverage-data-to-fuel-your-digital-transformation-journey/
0 notes
Text
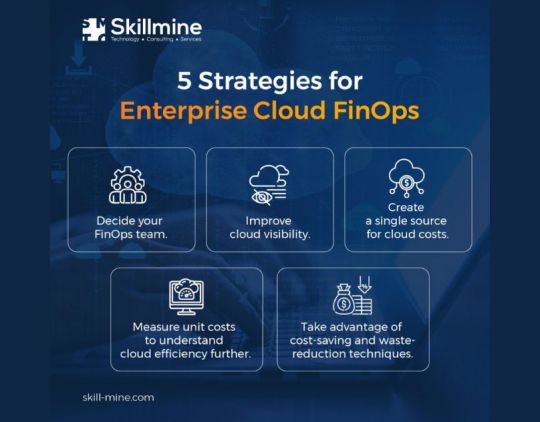
5 Strategies for Enterprise Cloud Finops
Accelerate your business with our cloud transformation services. Scalability and granular pricing is the foundation on which our cloud transformation services rest. Every organization is trying to leverage the cloud to enhance the user experience without causing any disruption to the business. With our cloud transformation capability, you can be successful in your cloud transition journey. Cloud offers a phenomenal set of features like scalability, agility, granular pricing. Our services range from microservices, mobile device management, analytics, streaming services to Hadoop and SAP HANA offerings. Take a look at how one can plan a cloud transformation.
Website: https://skill-mine.com/service/cloud-transformation-services/
0 notes
Text

Benefits of digital transformation
The firm built a robust digital banking platform. They introduced an app, which offered a wide range of banking services, including account management, payments, investments, and loans. The organization also leveraged data analytics and AI technologies to gain valuable insights into customer behaviour. They established cross-functional teams, empowered them to make decisions quickly, and encouraged a fail-fast, learn-fast mentality. This agile approach enabled them to iterate and refine their digital solutions rapidly. They also invested heavily in upskilling programs to equip employees with digital skills and knowledge.
Website: https://skill-mine.com/how-can-you-leverage-data-to-fuel-your-digital-transformation-journey/
0 notes
Text

SOAR Platform Pros and Cons
SOAR platforms benefit organizations by offering them the ability to automate and streamline their cybersecurity processes and tasks, particularly those that were traditionally inefficient, reactive, or manual. By implementing SOAR, organizations can enhance their operational efficiency and enable their skilled security teams to focus on critical tasks that require human expertise. This leads to better resource allocation and improved overall cybersecurity posture. Furthermore, SOAR platforms enable organizations to harness the full potential of their internal threat intelligence.
Website: https://skill-mine.com/service/cyber-security-services/
0 notes
Text

Benefits of IT Compliance Audit
Internally scrutinize the organization’s IT processes and systems to pinpoint potential areas for enhancement. Identify the pivotal focal points that compliance auditors generally concentrate on. For instance, if the organization is engaged in cybersecurity, auditors might assess the IT systems for compliance with industry standards. Grasping the auditors’ priorities enables you to concentrate on crucial business aspects during the review.
Website: https://skill-mine.com/products/complyment-it-compliance-management-software/
0 notes
Text
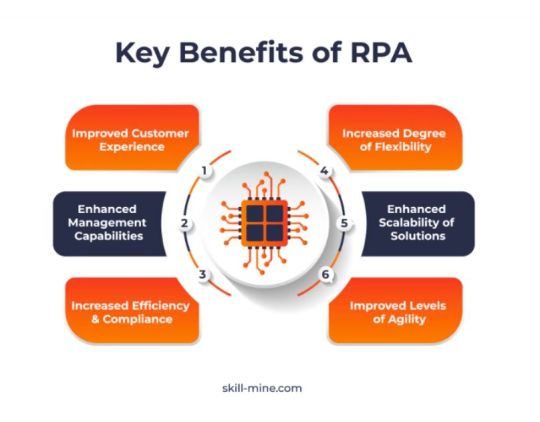
Key benefits of RPA
According to a Forrester survey, 80% of decision-makers believe that RPA increases the productivity of employees, allowing them to be more agile in responding to customer demands. Agility is the ability of an organization to respond swiftly and effectively to market changes, customer needs, and emerging opportunities. By automating repetitive tasks, RPA reduces the time and effort required to complete them. This, in turn, accelerates processes, leading to faster response times and improved operational efficiency.
Website: https://skill-mine.com/service/robotic-process-automation-services/
0 notes