#(the errors scratch disk so.... memory?)
Explore tagged Tumblr posts
Text
ok does anyone know anything about laptops & is willing to impart their wisdom on me. i am looking i think at the lenovo legions but. i honestly have no clue
#honestly i mostly use my laptop for watching youtube#but i play some games while on discord with friends. mostly just minecraft tho. thats probably the hardest it needs to handle#oh uncharted 4. thatd be nice#also like. ive been doing some intensive things to do with videos & shit recently. on gimp & photoshop and i would like whatever i need to#handle that. because adding in a bunch of layers kills my current laptop#(the errors scratch disk so.... memory?)#nyxtalks#all i know is. bigger number is better. right?#but also ive seen reviews saying like. bigger numbers only good if it can cool it. also i think my budget only extends up to 4070 anyway#and by budget i mean. how much i can force myself to spend on something before i cry#i want a laptop thatll last me at minimum 6 years. minimum.
5 notes
·
View notes
Text
The trick, by the way, of lying to a hard drive about what capacity it's supposed to be, to use it into the dirt, isn't just keeping the disk check from stopping you...
It's recognizing WHY the disk check wants to stop you when a drive has too many bad sectors...
Because the drive is failing. You can lose and corrupt files very easily. You can fry the whole drive. any writing and rewriting is slowly eating your disk.
So you only use it to store simple things that can easily be recovered if the file is corrupted like word files, and you save multiple copies of those files across the disk, and preferably have them all automatically back up, such as with partitioning.
And in my defense I was doing it because I needed a computer to do school work on at home. School work that only had to last to be handed in, and a text journal [well to be fair the failing hard drive might have been less corruptible memory than my own brain at various points]. Oh and everything was small enough to be backed up on floppies too.
I also used to do things like encounter text files with extensions my computer didn't know how to open, or that were corrupted, open them with program compiling software like the compilers used for school projects, and then copy out and reformat the text in a free word program that I -did- have access to. Usually notepad. I'd use find and replace functions to edit out a lot of the code that ended up in with the text when I could.
I would just hop word files between computer systems that didn't have any words programs in common this way like complex formats made by programs the school paid for, and that I didn't have at home, just didn't matter, and I never explained any of this to my teachers, some of whom were very convinced we would not be capable of working on some things at home.
Most often I ended up using it to open fic I had saved from a system that had a fancier word program that I didn't have on the computer I put together at home.
I used the get random motherboards from people that had been laying around for a year or longer that I had to look up the pin configuration for, or figure it out through trial and error and educated guesses.
Kids these days just aren't getting up to that kind of nonsense.
It's all ipads and smart phones.
Also maybe worth noting that my father taught me none of this. He worked on military air craft and made his own circuitboards as a hobby, and was a well paid system's administrator, but I had to teach myself all these things from scratch after leaving home with whatever computer access I could gain through the school and second hand parts.
Imagine what I could have done with guidance and support.
All the other people my age interested in these things were 'boys' and I was a 'girl' [tans masc here, but never mind that] and so when I did things like express an interest in using what I knew of programing to try getting into something like white-hat hacking, guys would make comments on how I "wanted to be a code kitten, hur hur" [someone who copies and pasts code without understanding it]... And they'd say things like "figuring out a motherboard's pin configuration without the original manual is impossible" and take my claims to the contrary as evidence I must be lying.
Imagine though if I had peers I could bounce things off of.
#This system I am on is actually the first desktop where I primarily bought the parts new instead of it all being other people's discarded#old systems#Other than laptops and tablets#I miss coding#I miss working with computers#I miss doing WEIRD shit with computers just because nothing could stop me#the fucking problem solving I used to get up to just because I didn't have internet half the time and no one was there to help
4 notes
·
View notes
Note
hii! I wanted to ask you a question about photoshop: every time I try to save a gif on my mac for the past week it saves the gif but when I try to open it it says "the file could not be opened because it is empty" or before I even get to save it, it says "could not complete the Export command because the file was not found" or "the operation could not be completed - a file system I/O error has occurred"
I’m not computer savvy at all, so maybe it’s my old macbook. I have 130 free GB on my mac but sometimes it’ll still give me the no free disk space message…..
there are just constantly issues with photoshop, I have adobe ps 2024, so it is pretty recent, which might not work well on my old computer??
idk it was running smoothly for a while but now just making one gif will take me an hour bc I have to close ps so often and sometimes shut off my computer bc ps won’t force quit, it’s a nightmare
even resetting the settings doesn’t really help, or deleting old files.
I just don’t know what to do… do you per chance have any advice on how to fix this? I don't know what I'm doing wrong 💀😭
Hi Emma! Thank you so much for the message 💖 I'll answer all of your concerns one by one:
Have you inspected the file size of the gif that was exported on Photoshop? This issue might be common amongst older hardware / insufficient system memory (where some attempts to export a gif will result in a file that's empty) Have you tried exporting this gif twice to see if you're able to get a working image?
Photoshop uses some of your disk space as scratch disk: if your computer doesn't have a lot of RAM you'll notice that a larger portion of your storage is used up when you're running Photoshop. This might explain why Photoshop returns you the scratch disk error when you're doing something more intensive (e.g. gifmaking using Timeline)
Photoshop 2024 is ill-optimised for older Macs (with Intel-based CPU's). Not only it requires the bare minimum of 8GB of system memory to run, it also has annoying pop-up messages if you're using an older version of MacOS (i.e. you need at least Ventura to avoid the pop-up message)
I think your best bet is install an older version of Photoshop (particularly Photoshop 2021 or earlier) that has a more lenient set of system requirements. I hope this helps ❣️
2 notes
·
View notes
Text
My Macbook Pro is acting up again and I no longer have wifi. I’m hoping it’s a software issue and not hardware. Luckily the router is by my bed and the ethernet works fine so it’s doable if I can’t fix it. It’s probably a software issue because it’s always a software issue. I’ve lost count of the number of times I’ve had re-install the OS and start from scratch. I love my macbook pro but the OS sure is finicky. Still better than windows though.
#mac problems#i've updated the storage and memory so i am never giving this baby up#it works great until a random error comes along and then nothing will fix it unless i reinstall the os#i am just thankful i never lost my os disks or i'd have been screwed years ago and several times over#still beats blue screen of death fucking windows#at least mac problems can almost always be fixed by starting from scratch#inconvenient but always works
1 note
·
View note
Text
WOOOO I DID IT GANG!!! Issue with my copy of Forbidden Memories solved!!! Those scratches I thought were insignificant actually made it so my ps2 wouldn’t read the disk correctly, so I cleaned it and put it in the console a few more times and now it’s finally playable!! Got hit with a few more frozen screens and another anti-piracy error, but it works now!!
2 notes
·
View notes
Text
Scaling in the presence of errors—don’t ignore them
Building a reliable, robust service often means building something that can keep working when some parts fail. A website where not every feature is available is often better than a website that’s entirely offline. Doing this in a meaningful way is not obvious.
The usual response is to hire more DBAs, more SREs, and even more folk in Support. Error handling, or making software that can recover from faults, often feels like the option of last resort—if ever considered in the first place.
The usual response to error handling is optimism. Unfortunately, the other choices aren’t exactly clear, and often difficult to choose from too. If you have two services, what do you do when one of them is offline: Try again later? Give up entirely? Or just ignore it and hope the problem goes away?
Surprisingly, all of these can be reasonable approaches. Even ignoring problems can work out for some systems. Sort-of. You don’t get to ignore errors, but sometimes recovering from an error can look very similar to ignoring it.
Imagine an orchard filled with wireless sensors for heat, light, and moisture. It makes little sense to try and resend old temperature readings upon error. It isn’t the sensor’s job to ensure the system works, and there’s very little a sensor can do about it, too. As a result, it’s pretty reasonable for a sensor to send messages with wild abandon—or in other words, fire-and-forget.
The idea behind fire-and-forget is that you don’t need to save old messages when the next message overrides it, or when a missing message will not cause problems. A situation where each message is treated as being the first message sent—forgetting that any attempt was made prior.
Done well, fire-and-forget is like a daily meeting—if someone misses the meeting, they can turn up the next day. Done badly, fire-and-forget is akin to replacing email with shouting across the office, hoping that someone else will take notes.
It isn’t that there’s no error handling in a fire-and-forget client, it’s that the best method of recovery is to just keep going. Unfortunately, people often misinterpret fire-and-forget to mean “avoid any error handling and hoping for the best”.
You don’t get to ignore errors.
When you ignore errors, you only put off discovering them—it’s not until another problem is caused that anyone even realises something has gone wrong. When you ignore errors, you waste time that could be spent recovering from them.
This is why, despite the occasional counter example, the best thing to do when encountering an error is to give up. Stop before you make anything worse and let something else handle it.
Giving up is a surprisingly reasonable approach to error handling, assuming something else will try to recover, restart, or resume the program. That’s why almost ever network service gets run in a loop—restarting immediately upon crashing, hoping the fault was transient. It often is.
There’s little point in trying to repeatedly connect to a database when the user is already mashing refresh in the browser. A unix pipeline could handle every possible bad outcome, but more often than not, running the program again makes everything work.
Although giving up is a good way to handle errors, restarting from scratch isn’t always the best way to recover from them.
Some pipelines work on large volumes or data, or do arduous amounts of numerical processing, and no-one is ever happy about repeating days or weeks or work. In theory, you could add error handling code, reduce the risk that the program will crash, and avoid an expensive restart, but in practice it’s often easier to restructure code to carry on where it left off.
In other words, give up, but save your progress to make restarting less time consuming.
For a pipeline, this usually entails a awful lot of temporary files—to save the output of each subcommand, and the result of splitting the input up into smaller batches. You can even retry things automatically, but for a lot of pipelines, manual recovery is still relatively inexpensive.
For other long running processes, this usually means something like checkpoints, or sagas. Or in other words, transforming a long running process into a short running one that’s run constantly, writing out the progress it makes to some file or database somewhere.
Over time, every long running process will get broken up into smaller parts, as restarting from scratch becomes prohibitively expensive. A long running process is just that more likely to run into an impossible error—full disks, no free memory, cosmic rays—and be forced to give up.
Sometimes the only way to handle an error is to give up.
As a result, the best way to handle errors is to structure your program to make recovery easier. Recovery is what makes all the difference between “fire-and-forget” and “ignoring-every-error” despite sharing the same optimism.
You can do things that look like ignoring errors, or even letting something else handle it, as long as there’s a plan to recover from them. Even if it’s restarting from scratch, even if it’s waking someone up at night, as long as there’s some plan, then you aren’t ignoring the problem. Assuming the plan works, that is.
You don’t get to ignore errors. They’re inevitably someone’s problem. If someone tells you they can ignore errors, they’re telling you someone else is on-call for their software.
That, or they’re using a message broker.
A message broker, if you’re not sure, is a networked service that offers a variety of queues that other computers on the network can interact with. Usually some clients enqueue messages, and others poll for the next unread message, but they can be used in a variety of other configurations too.
Like with a unix pipe, message brokers are used to get software off the ground. Similarly to using temporary files, the broker allows for different parts of the pipeline to consume and produce inputs at different rates, but don’t easily allow replaying or restarting when errors occur.
Like a unix pipe, message brokers are used in a very optimistic fashion. Firing messages into the queue and moving on to the next task at hand.
Somewhat like a unix pipeline, but with some notable differences. A unix pipeline blocks when full, pausing the producer until the consumer can catch up. A unix pipeline will exit if any of the subcommands exit, and return an error if the last subcommand failed.
A message broker does not block the producer until the consumer can catch up. In theory, this means transient errors or network issues between components don’t bring the entire system down. In practice, the more queues you have in a pipeline, the longer it takes to find out if there’s a problem.
Sometimes that works out. When there’s no growth, brokers act like a buffer between parts of a system, handling variance in load. They work well at slowing bursty clients down, and can provide a central point for auditing or access control.
When there is growth, queues explode regularly until some form of rate limiting appears. When more load arrives, queues are partitioned, and then repartitioned. Scaling a broker inevitably results in moving to something where the queue is bounded, or even ephemeral.
The problem with optimism is that when things do go wrong, not only do you have no idea how to fix it, you don’t even know what went wrong. To some extent, a message broker hides errors—programs can come and go as they please, and there’s no way to tell if the other part is still reading your messages—but it can only hide errors for so long.
In other words, fire-and-regret.
Although an unbounded queue is a tempting abstraction, it rarely lives up to the mythos of freeing you from having to handle errors. Unlike a unix pipeline, a message broker will always fill up your disks before giving up, and changing things to make recovery easy isn’t as straight forward as adding more temporary files.
Brokers can only recover from one error—a temporary network outage—so other mechanisms get brought in to compensate. Timeouts, retries, and sometimes even a second “priority” queue, because head-of-line blocking is genuinely terrible to deal with. Even then, if a worker crashes, messages can still get dropped.
Queues rarely help with recovery. They frequently impede it.
Imagine a build pipeline, or background job service where requests are dumped into some queue with wild abandon. When something breaks, or isn’t running like it is supposed to, you have no idea where to start recovery.
With a background queue, you can’t tell what jobs are currently being run right now. You can’t tell if something’s being retried, or failed, but maybe you’ve got log files you can search through. With logs, you can see what the system was doing a few minutes ago, but you still have no idea what it might be doing right now.
Even if you know the size of a queue, you’ll have to check the dashboard a few minutes later—to see if the line wiggled—before you know for sure if things are probably working. Hopefully.
Making a build pipeline with queues is relatively easy, but building one that the user can cancel, or watch, involves a lot more work. As soon as you want to cancel a task, or inspect a task, you need to keep things somewhere other than a queue.
Knowing what a program is up to means tracking the in-between parts, and even for something as simple as running a background task, it can involve many states—Created, Enqueued, Processing, Complete, Failed, not just Enqueued—and a broker only handles that last part.
Not very well. As soon as one queue feeds into another, an item of work can be in several different queues at once. If an item is missing from the queue, you know it’s either being dropped or processed, if an item is in the queue, you don’t know if it’s being processed, but you do know it will be. A queue doesn’t just hide errors, it hides state too.
Recovery means knowing what state the program was in before things went wrong, and when you fire-and-forget into a queue, you give up on knowing what happens to it. Handling errors, recovering from errors, means building software that can knows what state it is currently operating in. It also means structuring things to make recovery possible.
That, or you give up on on automated recovery of almost any kind. In some ways, I’m not arguing against fire-and-forget, or against optimism—but against optimism that prevents recovery. Not against queues, but how queues inevitably get used.
Unfortunately, recovery is relatively easy to imagine but not necessarily straight forward to implement.
This is why some people opt to use a replicated log, instead of a message broker.
If you’ve never used a replicated log, imagine an append only database table without a primary key, or a text file with backups, and you’re close. Or imagine a message broker, but instead of enqueue and dequeue, you can append to the log or read from the log.
Like a queue, a replicated log can be used in a fire-and-forget fashion with not so great consequences. Just like before, chaos will ensue as concepts like rate-limiting, head-of-line blocking, and the end-to-end-principle are slowly contended with—If you use a replicated log like a queue, it will fail like a queue.
Unlike a queue, a replicated log can aid recovery.
Every consumer sees the same log entries, in the same order, so it’s possible to recover by replaying the log, or by catching up on old entries. In some ways it’s more like using temporary files instead of a pipeline to join things together, and the strategies for recovery overlap with temporary files, too—like partitioning the log so that restarts aren’t as expensive.
Like temporary files, a replicated log can aid in recovery, but only to a certain point. A consumer will see the same messages, in the same order, but if a entry gets dropped before reaching the log, or if entries arrive in the wrong order, some, or potentially all hell can break loose.
You can’t just fire-and-forget into a log, not over a network. Although a replicated log is ordered, it will preserve the ordering it gets, whatever that happens to be.
This isn’t always a problem. Some logs are used to capture analytic data, or fed into aggregators, so the impact of a few missing or out of order entries is relatively low—a few missing entries might as well be called high-volume random sampling and declared a non-issue.
For other logs, missing entries could cause untold misery. Recovering from missing entries might involve rebuilding the entire log from scratch. If you’re using a replicated log for replication, you probably care quite a lot about the order of log entries.
Like before, you can’t ignore errors—you only make things expensive to recover from.
Handling errors like out of order or missing log entries means being able to work out when they have occurred.
This is more difficult than you might imagine.
Take two services, a primary and a secondary, both with databases, and imagine using a replicated log to copy changes from one to another.
It doesn’t seem to difficult at first. Every time the primary service makes a change to the database, it writes to to log. The secondary reads from the log, and updates its database. If the primary service is a single process, it’s pretty easy to ensure that every message is sent in the right order. When there’s more than one writer, things can get rather involved.
Now, you could switch things around—write to the log first, then apply the changes to the database, or use the database’s log directly—and avoid the problem altogether, but these aren’t always an option. Sometimes you’re forced to handle the problem of ordering the entries yourself.
In other words, you’ll need to order the messages before writing them to the log.
You could let something else provide the order, but you’d be mistaken if you think a timestamp would help. Clocks move forwards and backwards and this can cause all sorts of headaches.
One of the most frustrating problems with timestamps is ‘doomstones’: when a service deletes a key but has a wonky clock far out in the future, and issues an event with a similar timestamp. All operations get silently dropped until the deletion event is cleared. The other problem with timestamps is that if you have two entries, one after the other, you can’t tell if there are any entries that came between them.
Things like “Hybrid Logical Clocks”, or even atomic clocks can help to narrow down clock drift, but only so much. You can only narrow down the window of uncertainty, there’s still some clock skew. Again, clocks will go forwards and backwards—timestamps are terrible for ordering things precisely.
In practice you need explicit version numbers, 1,2,3... etc, or a unique identifier for each version of each entry, and a link back to the record being updated, to order messages.
With a version number, messages can be reordered, missing messages can be detected, and both can be recovered from, although managing and assigning those version numbers can be quite difficult in practice. Timestamps are still useful, if only for putting things in a human perspective, but without a version number, it’s impossible to know what precise order things happened in—and that no steps are missing, either.
You don’t get to ignore errors, but sometimes the error handling code isn’t that obvious.
Using version numbers or even timestamps both fall under building a plan for recovery. Building something that can continue to operate in the presence of failure. Unfortunately, building something that works when other parts fail is one of the more challenging parts of software engineering.
It doesn’t help that doing the same thing in the same order is so difficult that people use terms like causality and determinism to make the point sink in.
You don’t get to ignore errors, but no one said it was going to be easy.
Although using things like replicated logs, message brokers, or even using unix pipes can allow you to build prototypes, clear demonstrations of how your software works—they do not free you from the burden of handling errors.
You can’t avoid error handling code, not at scale.
The secret to error handling at scale isn’t giving up, ignoring the problem, or even it trying again—it is structuring a program for recovery, making errors stand out, allowing other parts of the program to make decisions.
Techniques like fail-fast, crash-only-software, process supervision, but also things like clever use of version numbers, and occasionally the odd bit of statelessness or idempotence. What these all have in common is that they’re all methods of recovery.
Recovery is the secret to handling errors. Especially at scale.
Giving up early so other things have a chance, continuing on so other things can catch up, restarting from a clean state to try again, saving progress so that things do not have to be repeated.
That, or put it off for a while. Buy a lot of disks, hire a few SREs, and add another graph to the dashboard.
The problem with scale is that you can’t approach it with optimism. As the system grows, it needs redundancy, or to be able to function in the presence of partial errors or intermittent faults. Humans can only fill in so many gaps.
Staff turnover is the worst form of technical debt.
Writing robust software means building systems that can exist in a state of partial failure (like incomplete output), and writing resilient software means building systems that are always in a state of recovery (like restarting)—neither come from engineering the happy path of your software.
When you ignore errors, you transform them into mysteries to solve. Something or someone else will have to handle them, and then have to recover from them—usually by hand, and almost always at great expense.
The problem with avoiding error handling in code is that you’re only avoiding automating it.
In other words, the trick to scaling in the presence of errors is building software around the notion of recovery. Automated recovery.
That, or burnout. Lots of burnout. You don’t get to ignore errors.
11 notes
·
View notes
Text
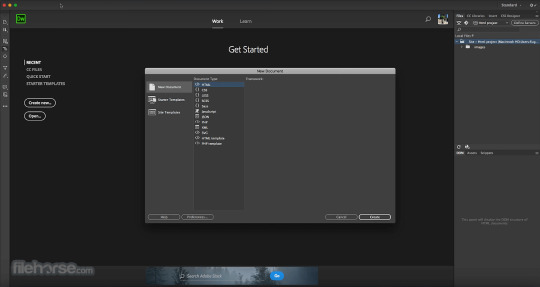
Learn How to Perform Windows Registry Repair and Fix Errors, and See the Best Free Registry Cleaners
Learn How to Perform Windows Registry Repair and Fix Errors, and See the Best Free Registry Cleaners
The Windows registry is a database containing vital, machine-precise settings and information regarding almost everything in your computer — preferences, programs, users, attached devices and so on. The registry consists of two primary elements: keys and values. The Windows operating device continuously refers back to the registry; for example, to open a program, deploy new software or exchange your hardware, Windows must check the values of sure keys.
Learn how to fix broken registry items You can exchange registry key values manually the use of the built-in Windows Registry Editor (Regedit) so that it will improve performance or make Windows work the manner you want, however you need to know what you’re doing or you may seriously damage your OS.
Common registry mistakes There are several common causes of registry mistakes. Some are well worth worrying about, and others are not.
Orphaned entries. Orphaned entries arise when you uninstall software program and small fragments of registry entries are left behind. Registry purifier software will often declare these are an immediate difficulty, however, in reality, they may just expend some kilobytes of loose space on your disk. Duplicate keys. Duplicate keys are made when you reinstall, upgrade or update software for your machine, consisting of the operating system.
Registry cleaner software program will country that your programs could be burdened through the reproduction entries, slowing the performance of your machine, however that isn't true. Fragmented registry. The registry also can fragment when the software is uninstalled, upgraded or updated.
System shutdown errors. Each time your computer shuts down, a duplicate of the registry is saved to machine memory. If your pc is becoming off, crashes or dies without going thru the regular shutdown routine, it is able to cause trouble in the future, however this is unlikely.
Malware. Many kinds of malware attack and regulate the registry. In particular, malware is regularly designed to exchange the values of startup keys so it is going to be activated on every occasion you restart the PC. Changes to the registry with the aid of malware require on the spot attention.
Why smooth the registry?
Once you’ve been going for walks the Windows OS for a few time — putting in and uninstalling programs, and swapping in different keyboard and mice — you grow to be with masses or thousands of registry entries that are completely useless. Each one uses very little difficult drive space, however, the operating device nonetheless has to filters via all of them, which slows it down a bit. By cleaning the registry, you could do away with those undesirable entries and make your device run a touch bit faster.
Sometimes, however, it is really necessary to restore registry issues. For example, when you have ever encountered a bit of malware, you recognize that it may completely reduce to rubble your registry. So, a way to repair broken registry items? When the time comes to restore registry mistakes, it's miles essential to realize what you are doing — and to usually start by way of creating a registry backup.
Windows registry backup and repair Backing up the Windows registry
As with any other important machine settings, it's far highly recommended to make a backup earlier than you try and trade, create or dispose of registry facts, so that you can revert to the old model if something goes wrong.
There are numerous techniques for backing up your Windows records:
Using Regedit Using the command prompt Using third-party software Restoring the Windows registry There are several ones of kind methods to restore the Windows registry. The most common techniques for fixing corrupt information are:
Restoring the Windows registry from Safe Mode Restoring the registry from the command prompt Fixing Windows registry errors with System Restore Repairing the registry with Automatic Repair Fixing broken registry gadgets with System File Checker Restoring your Computer with ‘Reset this PC’ Repairing the registry with the DISM command Reinstalling Windows from scratch Using third-birthday party gear to lower back up and restore the registry
Editing the registry To edit the cost of a registry key, take these steps:
1. First, locate the important thing you need to edit. Press the Ctrl and F keys concurrently open the Find dialog.
2. Type the call of the key and click Find Next.
3. Double-click the important thing you want within the list.
4. Edit the key’s fee data.
5. Click OK to store your settings. Some edits require a Windows restart to take effect.
You also can edit the registry with PowerShell.
Cleaning the Windows registry with the Registry Editor You can carry out registry cleanup manually the use of the Windows Registry Editor. Follow these steps:
1. Click the Start button and then pick Run ...
2. Type “Regedit” inside the text box and press Enter.
3. Locate any packages which have already been uninstalled and delete them:
a. Expand the HKEY_CURRENT_USER phase and then increase the Software
b. Look for keys based totally on the name of the uninstalled packages or the vendor and delete them.
4. Next, discover and eliminate any duplicate keys that the uninstalled programs may have left behind:
a. Press Ctrl+F to open the Find dialog box.
B. Enter the call of the uninstalled application and click OK to search. Each matching key or cost may be highlighted.
C. Remove the highlighted key.
D. Press F3 to locate the next suit and delete it. Repeat this step till you've got reviewed all highlighted gadgets.
5. Remove unwanted start-up items from the registry:
a. Navigate to the following location: My ComputerHKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrent Version
b. Click Run to list shortcuts to all of the executable documents that run at startup.
C. Delete any packages that you don’t want to run at Windows startup. Do an internet search to analyze any which might be unfamiliar.
D. Repeat the equal challenge for the subsequent key paths as well:
• HKLMSOFTWAREWow6432NodeMicrosoftWindows CurrentVersionRun
• HKLMSOFTWAREMicrosoftActive SetupInstalled Components
• HKLMSOFTWAREWow6432NodeMicrosoftActive SetupInstalled Components
Best Windows registry cleaners Here is a list of the pinnacle loose registry cleaners for Microsoft Windows:
Glarysoft Registry Repair
Glarysoft’s Registry Repair is a splendid unfastened registry repair device. It helps you restore your registry and optimize your PC’s performance. When you open the device, the registry scan technique will start automatically. In a few easy steps, you'll be capable of locate and clear invalid entries, references and links inside the registry. It gives a listing of the mistakes found, and you can select to repair particular objects or automatically repair them all. It also gives automatic registry backup earlier than making any changes to the Windows registry, which enables mitigate risk. Also, every time you clean the registry, a corresponding Undo report is generated, so that you can effortlessly revert any modifications. This loose device may be upgraded to Glarysoft Utilities, which offers features that include registry purifier, shortcut fixer, spyware remover, disk restore, track eraser, temporary document purifier, and startup manager.
1 note
·
View note
Text
How to free up space on mac disk cache

#HOW TO FREE UP SPACE ON MAC DISK CACHE HOW TO#
#HOW TO FREE UP SPACE ON MAC DISK CACHE PRO#
#HOW TO FREE UP SPACE ON MAC DISK CACHE MAC#
Select “Scan” at the bottom of the window.
Select “Space Lens” from the left side of the window.
It analyzes your entire system and surfaces which folders are too bulky, and offers a quick way to delete files you don’t need. How often do you save items and never touch them again?ĬleanMyMac X has an incredible feature named Space Lens that provides you with an overview of your Mac’s storage makeup so you can quickly identify which folders are overflowing with stuff.
#HOW TO FREE UP SPACE ON MAC DISK CACHE HOW TO#
You’re here to learn how to clear scratch disk in Photoshop, but the root of the problem is your Mac’s cluttered storage space. Similarly, the partition Photoshop or other apps uses may be too full, and a limited amount of RAM available to the app may also cause this error. Other reasons you see the error is the drive where the scratch disk is located is out of space this is most frequent when your Mac’s storage is too full. These files may not show up as occupied memory, either, which adds to the confusion as to why you see the error message. The app thinks you may want to use them later on, so it saves them. If you force-quit apps like Photoshop often, temporary files don’t disappear. The main reason you see ‘Photoshop scratch disk full’ errors are temporary files. Though these files are temporary, they need a place to live – the scratch disk. Like a scratch pad, it keeps things there temporarily while it performs process-heavy tasks like editing videos or photos with many edits and layers. Large, intensive apps need a bit of hard drive space to use as virtual memory when there’s not enough RAM to finish a task. You use the scratch pad to write down notes for something maybe it’s ideas for a book you’re writing, or sketching some illustrations by hand before testing the waters in a design app. Think of a scratch disk like a scratch pad of paper. Here, we’ll show you how to clear scratch disk on Mac, how to empty scratch disk for use, why Photoshop scratch disks are full, and how to better manage memory to reduce or eliminate the frequency these popups occur.
#HOW TO FREE UP SPACE ON MAC DISK CACHE PRO#
Intensive programs like Photoshop, Premiere Pro, and Final Cut Pro often serve this error up, and it can be really confusing.
#HOW TO FREE UP SPACE ON MAC DISK CACHE MAC#
Make your Mac fast and secure with CleanMyMac X.Ĭlearing a scratch disk on your Mac may not be a problem you’ll run into often, but those working in apps like Photoshop should understand exactly how to solve for the problem when it pops up.

0 notes
Link
ProgDVB Pro 7.42.4 Crack & Activation + Serial Key Download Posted on October 7, 2021 by Rehana DOWNLOAD NOW ProgDVB Pro 7.42.4 Crack & Activation + Serial Key Download ProgDVB Crack This is a favorite software around the world due to the power and flexibility it offers. The program contains many powerful copy tools. However, the user can perform a disc-to-disc copy, where they directly copy the movie to a blank CD from a physical DVD. Besides, it can also compress double-layer DVDs into a single layer. It supports all new types of disc media, including 4K ultra high definition and Blu-ray. So once you experience it, you get used to its usefulness. An excellent result makes it one of the best DVD ripping programs. You can easily complete basic tasks. DVDFab Torrent provides tools that allow users to backup their physical discs digitally and saves the DVD ISO file directly to their hard drive. Whether you are compressing a commercial disc or making a direct one-to-one copy, this process typically takes 40-50 minutes. Last but not least, it helps you back up your movies quickly and easily. You can also download using the activation tool. For those looking for a tool to rip store-bought DVDs to the hard drive, this is the perfect all-in-one software. It offers a nice interface that allows users to rip DVDs to any blank disc. Many people think that this is just DVD ripping software, but it is so much more than just a DVD ripper. At first, the complexity can be intimidating for users and it can take time to discover its complexities. removes region codes and supports multiple languages. In short, DVDFab Crack is a dedicated video copier, ripper, and converter without compromising on quality. Also, it can read even scratched DVDs. The program worked as a software solution. ProgDVB Pro 7.39.4 Crack There are several ways to make DVDs with this great software. As a result, you can transfer the converted files and folders to various devices, including PSP and iPod. DVDFab Keygen has six modes. It has a built-in CSS decoder. This program contains a complete set of tools to handle various types of CD, DVD, audio, and Blu-ray discs. This program can offer all the necessary utilities to perform various disk tasks. Furthermore, it enables you to create very stable errors from free and reliable disk images. Plus, it supports a variety of disc formats, making it ideal. DVDFab Keygen offers all solutions for fast data burning on various types of discs. Technical experts appreciate ProgDVB Torrent’s satellite dish transmission capabilities and all the amazing features it has. The updated version of the application contains many improvements and provides users with improved support for multiple audio channels. The interface of this program is typical and well organized, containing a menu bar and a panel. ProgDVB Pro 7.39.4 Crack Full Serial Key ProgDVB Hack your favorite TV shows and you want more convenient access to TV entertainment. Along with digital television, you can even tune in to your favorite radio channels and never miss the latest updates or music. This application works by integrating DVB cards with your PC hardware and then directly accessing the TV and radio channels from the satellite. You also need to use a decoder with your system and make sure your system is capable of handling DVB cards and is x86 compatible. However, it is compatible with various devices such as TV, IPTV, Internet radio or TV devices, and other remote control devices. ProgDVB 7 Crack The program helps you to watch a digital TV channel. It also helps you listen to the radio on your computers. ProgDVB supports DVB-T and IPTV sources. You can watch digital channels and listen to radio channels on Android, Windows, and IOS. The program helps to prepare DVB cont. Supports different types of data sources. And playback of different channels from one or more devices. Dvb has a tiled preview of channels. ProgDVB Professional Series Key Features: It is the best streaming tool Watch all the TV and radio channels It can be installed on Windows and Mac. You only need an internet connection This app comes with version 2 One is paid and the other is free The free version has some limitations. Like limited TV channels Easy to install with default settings Settings can be changed later ProgDVB Professional 7 Crack can also record TV shows. You can watch TV shows later Users are not tied to television There are many display modes and this application allows the user to choose the display modes. Multiple language support The application is used all over the world. With one click, the channel will be buffered. Similar programs for Mac + Windows: Audacity Full Crack Free Full Version Download Download Mirillis Action Crack via torrent Exhale Crack Mac output + Serial number 100% working Technical Information: Intel Pentium III 500 MHz processor. 128MB memory on board. 5 MB of disk space (excluding disk space for video and audio recordings). GraficVideo SVGA AGP Adapter with 32MB onboard memory. Compatible sound card DIRECTX V.8.0 OR UP. It is much better to use the new Techno Trend v2.09 or 2.10 drivers. Install some software recording codecs. FRAMEWORK MICROSOFT .NET 4.0 How to Crack ProgDVB Professional Keygen? Download the latest version of Crack from the link below Save the Zip file to your PC and extract it with Winrar or any other Just install the trial version and don’t run the software Now extract the Crack folder and copy the DLL files. Insert the DLL file into the installation directory In my case, the installed directory is: Now start ProgDVB Professional Full Crack and you will see that your application is registered. ProgDVB Pro 7.42.4 Crack & Activation + Serial Key Download from links are given below! DOWNLOAD NOW Download Now
0 notes
Text
Two good thrift store DVD finds this week: Eddie Izzard’s Dress To Kill (which I have on vhs and consequently haven’t watched in years, althoug I could probably repeat large sections from memory anyway) and Hot Fuzz with all the extra material and commentaries that’s missing from the copy I already had. I say missing because according to the box they’re supposed to be there, but it was about $2 unopened from Lidl of all places so I suspect it was a manufacturing/packaging error. I didn’t bother asking for a refund but I’ve been annoyed ever since. Not anymore, though!
The disk was pretty scratched, and this is the slightly seedy charity shop that (unlike the other stores in the chain) doesn’t have a return policy (unlike the other stores in the chain), but it plays fine and was only about $1 so I’m very happy. I do kind of wish it had been the swedish edition with all the subtitles, though, since screaming at the translator is an important part of the movie watching experience.
#thrifting#complaining about translations is my hobby#particularly when they get different people to translate the movie and the extras#and the person doing the extras doesn't seem to have watched the actual movie#aargh annoying#literally hours of fun
2 notes
·
View notes
Text
Dreamweaver Cc Mac Download

Adobe Dreamweaver CC 2020 Overview. Adobe Dreamweaver CC 2020 free download is the industry-leading web authoring and editing and enhancing software that delivers both visible and code-level functions for creating standards-based websites and designs. Download Adobe Dreamweaver CC Crack Mac the most advanced development software and web design application for creating, publishing, and managing websites and mobile content. Dreamweaver CC 2019 Full Mac Version provides an intuitive visual interface for website creation and editing, and offers up-to-date compatibility with web standards as well.
Adobe Dreamweaver CC Crack Free Download is an essential application for designing and developing website templates and themes. Web designers and developers can easily create a variety of models using responsive support and useful web code and standards.
Adobe Dreamweaver CC 2021 Crack version supports the latest web development languages, such as CSS, Javascript, PHP, HTML, etc. It is designed to provide users with all the tools and modules to meet all their needs in a single development environment. This allows users to create dynamic pages using Ajax technology, which is a fast and stable performance language.
Download dreamweaver mac for free. Developer Tools downloads - Adobe Dreamweaver CS6 by com.adobe.dreamweaver-12 and many more programs are available for instant and free download. Adobe Dreamweaver is the. Release of Dreamweaver CC includes. https://loadingkarma381.tumblr.com/post/657396639415369729/mac-os-sierra-1013-0-dmg-download. 4D for Dreamweaver MX. Adobe Dreamweaver CC 2020 21.0 - Build world-class websites and applications. Download the latest versions of the best Mac apps at safe and trusted MacUpdate.
Adobe Dreamweaver License Keys can change the text and image properties and add classes directly to Live View with one click – and instantly preview the changes. You do not need to switch to separate edit mode. You can now expand your workspace by looking at the glass on multiple monitors. With a clean and optimized user interface, you can customize your workspace so that only the tools you need for coding are displayed. Thanks to Git support, collaboration is easy. Configure all source code in Download Dreamweaver and then perform all common operations from the Git panel.
You Can Also DownloadAdobe Acrobat Pro DC
Users can edit and view newly created or existing web pages, as well as make changes and customizations. Upload pages directly to the service with improved jQuery support. The full version of Adobe Dreamweaver CC 2021 has other great features including automation, code highlighting, the ability to connect to FTP, and the ability to create projects with ease. It does not require advanced skills to operate the application, basic science and you can create a website with a modern layout and design.
Key Features of Adobe Dreamweaver cc Crack:
This may be a favorite feature of Adobe Dreamweaver Registration because the learning code is very easy. You can create web pages in Code view, Design view, or in split-screen between the two views.
After that, this is the main choice of Dreamweaver users including me because you can associate the code with what the user will see on the website. I have never used code in my life when I first used Dreamweaver, and the prospect of having to use it every day is really great.
Also, after using a split view, I was able to create and learn the code structure at once.
Hence, there are different types of code that can be used in web design, HTML, CSS, and JavaScript. The list goes on.
However, Dreamweaver makes it easy for you by marking each type of code with a different color. This is not only easy if you want to re-work, but it also helps the hobbyists give the code the basic structure of the code.
Most importantly, it is easier to design your content. All available options are listed and you can insert hyperlinks, colors, fonts, titles, etc. You can modify the HTML and CSS to change the style and structure. You do not need to check the code.
Well, it seems obvious, but it may be the command most commonly used when using Dreamweaver Download.
Just like a publication document, you can preview the last web page on the web.
In addition, you can check the format, make sure your hyperlink shows the correct page, make sure the image has the correct tag, and can generally play with what you have created. real website.
System Requirements for Adobe Dreamweaver:
Mac:
Multicore Intel processor
macOS version 10.15 (Catalina), macOS version 10.14 (Mojave), and macOS version 10.13 (High Sierra)
4 GB RAM (16 GB recommended)
3.5 GB of available hard-disk space for installation; additional free space required during installation (cannot be installed on a volume that uses a case-sensitive file system or on removable flash storage devices)
1024 x 768 display (1920 x 1080 recommended), support for retina displays
32-bit graphics card
To take advantage of the GPU performance, your Mac must have at least 1024 MB VRAM (2 GB recommended) and your computer must support OpenGL version 4.0 or higher.
Supported machines
iMac 4K
iMac 5K
MacBook Pro Retina
Mac Pro connected to a HiDPI monitor
Mac mini connected to a HiDPI monitor
To check the VRAM, choose Mac> About This Mac (Graphic Info).
Internet connection and registration are required for required software activation, validation of subscriptions, and access to online services.
Windows:
Intel® Pentium® 4 or AMD Athlon® 64 processor
Microsoft Windows 7 (64-bit) with Service Pack 1 or Windows 10 * (64-bit)
4 GB RAM (16 GB recommended)
3.6 GB of available hard-disk space for installation; additional free space required during installation (cannot be
installed on removable flash memory devices); SSD recommended
1024 x 768 display (1920 x 1080 recommended), supports HiDPI display
32-bit graphics card
What’s New in Adobe Dreamweaver Crack Download:
Editing of the live view has also been simplified. In the new version, you can click to edit effortlessly in live mode. Now change the semantic tags like <aside> <section> and so on
Most importantly, improve your editing experience. With the auto-sync feature, any changes made in Live View are automatically synced to Code View.
In the current update, the code hint filter logic for PHP has been improved. Now the information you are looking for is always in the foreground. The availability of code hints for JS and PHP has also been improved.
In addition, Japanese Dreamweaver now has a new default font configuration.
In addition, the Windows system supports Japanese encodings, and Unicode and MAC support EUC, ISO 2022-JP, Shift JIS, and Windows DOS encodings for Japanese. They all have the same font.
Adobe Dreamweaver Download For Pc
How to Crack Adobe Dreamweaver 2021 v21.0.0.15392 Cracked?
Download the latest version first.
Uninstall previous versions.
Note Kill Virus Guard.
After downloading Unzip or extract the RAR file then open the installer (use WinRAR to extract).
Just install the patched configuration.
After all, enjoy the latest version of Adobe Dreamweaver CC version 2021.
You May Also Check Adobe Flash Player
The biggest need for today’s community is the freedom to express art and mind. Most of the people out there depend on art to express feelings, emotions and what exactly they have to say to the outer world.

The biggest regret that each artist has is that he/she is not able to bring the fullest out of his artworks and that is where editing software comes into play. And who better than adobe to clear the path for them. There are a lot of comprehensive tools that are accommodated within the basket of Adobe to help you get everything right about the work that you are doing.
License Shareware
File Size 820MB
OS Mac OS
Language Multilingual
Developer Adobe Inc.
Overview of Adobe Dreamweaver CC 2020

Out of the lot, the adobe Dreamweaver cc is one of the best software any editor can lay their hands on to build and create websites of unique patterns. The tool is allocated with a lot of design aspects that make the Adobe Dreamweaver CC 2020 a very good editing software. The biggest appeal with the software is that it is highly compatible with a Mac-based operating system. Mac-based systems have a great amount of dealing within as they have a great influence on affecting the quality of the output that you are working with.
Even with such a revolutionary software onboard, many are yet to identify the various features that will just make their lives much easier with Adobe Dreamweaver CC 2020. The software is the most prescribed one when you are looking for getting the job of building a stronger and rigid website. The tools that are embedded within the software will ensure that you will get along with the software as quickly as you can. Now there are some features that make it a highly compatible software in a Mac-based operating system.
Features of Adobe Dreamweaver CC 2020
1. Coding is as easy as it seems
Building websites from scratch involves a lot of coding, but no one knows that the amount of patience that is required to complete the entire website. You will have to make sure that you have a mediocre coding strength in order to proceed with creating a website. There are a lot of ways in which you can actually make sure that the coding that you do is correct with Dreamweaver.
Crusader kings 2 free download mac. The coding engine that is accompanied with the Dreamweaver is definitely a very good one, looking at the ways in which you can dynamically work on live websites with a visual aid to avoid errors. You are also provided with direct access to the HTML codes of the websites to ensure that you can develop the site with the utmost efficiency.
2. Simpler ways to set up things
The amount of effort that you will have to put up with in developing the website is highly simple and doesn’t involve much of the effort that is accompanied by professional website building. Dr cleaner mac os. There are a lot of simple featurettes that are accompanied by the software that will greatly influence the ways in which you can get the website alive and running. The basic elementary operations that you are faced with in creating the website is simple and as tough as it can get.
3. Adaptive Display
Dreamweaver Cc Free Download
There are a lot of issues with the websites and one of the most significant problems that we face after the website gets activated is definitely the different displays in which the websites are viewed. The biggest ordeals that we face is that the websites that we create are viewed in many devices and the website must be adaptable to all the devices in which it is used. The software will directly affect the dynamic displays and the different displays in which the website will be reviewed.
4. GitHub merge
Now if you are an active user in the GitHub platform, all you have to do is link your account with the Dreamweaver software. Once you do that you can directly access the code links of the websites and embed it into the software to get the job done.
The common codes that you get with the website development will allow you to build software to make sure that there is a dynamic response of the website once it is active. With a feature like that, you can make drastic changes to your websites once you launch the same.
Dreamweaver Cc Mac Download Software

5. Modern and well-equipped User Interface
Whenever you are dealing with software, the biggest thing that you would be required is the development of the software. This means that the software must be equipped with a very good user interface to make the user comfortable in using the software. The Dreamweaver is a software that is equipped with a lot of technical user interface, that will make the software a delight to work with.
System requirements for Mac-based operating systems
Dreamweaver Cc Download
Multicore Intel processor 64-bit support
Mac OS v 10.11 and above
4GB RAM requirement
2GB HDD space required
1280X1024 display support
Stable internet connection
Download Adobe Dreamweaver cc 2020
You can download the ISO image file of the Adobe Dreamweaver 2020 cc full version for the Mac edition by accessing the link below. Make sure that you have the minimum requirements met before you proceed with the download. https://loadingkarma381.tumblr.com/post/657396554587586560/7th-guest-mac-download.
Download Adobe Dreamweaver CC 2020 full version for Mac - ISORIVER
the adobe Dreamweaver cc is one of the best software any editor can lay their hands on to build and create websites of unique patterns..
Download Dreamweaver Cc 2018
Price Currency: USD
Operating System: Mac OS
Application Category: IDE

0 notes
Text
Amazon Echo Dots stores a lot of data, even after a reset
Amazon Echo Dots stores a lot of data, even after a reset
https://theministerofcapitalism.com/blog/amazon-echo-dots-stores-a-lot-of-data-even-after-a-reset/

Like most internet of things currently, Amazon’s Echo Dot provides users with a way to do a factory reset so that as a corporate giant he says, users can ���remove any … personal content from applicable devices” before selling or discarding them. But researchers do found recently that the remaining digital bits on these reset devices can be reassembled to retrieve a large amount of sensitive data, including passwords, locations, authentication tokens, and more.
Ars Technica
This story originally appeared on Ars Technica, a reliable source of technology news, technology policy analysis, reviews and more. Ars is owned by WIRED’s parent company, Condé Nast.
The majority IoT devices, el Echo Dot included, use NAND-based flash memory to store data. Like traditional hard drives, NAND, which is the Boolean operator’s abbreviation “no and”, stores bits of data so that they can be retrieved later. But while hard drives write data on magnetic plates, NAND uses silicon chips. NAND is also less stable than hard disks because read and write produce bit errors that need to be corrected using an error correction code.
NAND is usually organized into plans, blocks, and pages. This design allows for a limited number of erase cycles, typically approximately 10,000 to 100,000 times per block. To extend the life of the chip, blocks that store deleted data are often invalidated instead of cleaned. Actual deletions usually occur only when most pages in a blog are invalidated. This process is known as wear leveling.
Researchers at Northeastern University bought 86 used devices on eBay and the flea markets for 16 months. They first examined the devices purchased to see which ones had been factory reset and which ones had not. His first surprise: 61% of them had not reset. Without a reset, retrieving Wi-Fi passwords, router MAC addresses, Amazon account credentials, and connected device information from previous owners was relatively straightforward.
The next surprise was when investigators disassembled the devices and forensically examined the content stored in their memory.
“An adversary who has physical access to these devices (for example, when buying a used one) can retrieve confidential information, such as Wi-Fi credentials, the physical location of (previous) owners, and cyberphysical devices (e.g., cameras, door locks) “, the researchers wrote in a research paper. “We show that this information, including all previous passwords and testimonials, remains in flash memory, even after a factory reset.”
Used Echo Dots and other Amazon devices may appear in various states. One state is that the device continues to be supplied, as 61% of the Echo points purchased were. Devices can be reset while connected to the previous owner’s Wi-Fi network, reset while disconnected from Wi-Fi, either with or without deleting the device from the owner’s Alexa app.
Depending on the type of NAND flash and the status of the previously proprietary device, the researchers used various techniques to extract the stored data. For reset devices, there is a process known as chip-off, which involves disassembling the device and desoldering flash memory. Researchers use an external device to access and extract the contents of the flash. This method requires a good amount of equipment, skill and time.
A different process called programming within the system allows researchers to access the flash without desoldering it. It works by scratching part of the solder mask coating of the printed circuit board and attaching a conductive needle to an exposed piece of copper to touch it. signal trace, which connects the flash to the CPU.
The researchers also created a hybrid chip separation method that causes less damage and thermal stress to the PCB and the embedded multi-chip package. These defects can cause short circuit and breakage of PCB bearings. The hybrid technique uses a donor multi-chip package for RAM and the embedded media card portion of the original multi-chip package externally. This method is especially interesting for researchers who want to analyze IoT devices.
In addition to the 86 devices used, the researchers bought six new Echo Dot devices and, for several weeks, provided them with test accounts in different geographic locations and different Wi-Fi hotspots. The researchers paired the devices supplied to different smart homes and Bluetooth devices. The researchers extracted the contents of the flash from these devices still supplied using the techniques described above.
Source link
0 notes
Text
First, Do No Harm (Rocket, GOTG, Lylla)
Watching Rocket and Lylla perform a minor operation on Gamora reminds him of the time Peter found Rocket operating on himself. Blood and Rocket angst.
This story takes place after Sanctuary.
"Get that nerve, Rocket," Lylla said distractedly. Then, "Oh, I'm sorry, dear. I wasn't thinking."
Not so long ago Rocket's ears would have gone back, either at the implication that he'd made a technical error or because, Peter knew, the phrase "Get that nerve" brought back horrible memories of his early life. But their tough little raccoon teammate had healed a lot since he met them, and especially after meeting Lylla a year ago.
"I'll get your nerve," he said with a wicked grin.
Lylla chuckled. "Later, honey." Through the banter Rocket's clever little hands were working. Lylla waited a moment as he added another white disc - nerve blocks to deaden pain - to the ones stuck to Gamora's shoulder. He studied a hovering screen. "Got it."
"I don't know why you have to be awake for this," Peter said. The green-skinned assassin smiled. She was face down on one of the common area bunks, naked from the waist up, and Lylla had the skin peeled back from a wound on her shoulder. Gamora's cybernetics were expensive and reliable but that didn't mean they were indestructible. She'd been blown through a wall on the Guardian's latest mission and even her augmented body had its limits.
"Because they're very good at it," she said. Three hovering screens in front of her face had different views of the operation. The otter had the muscles in her shoulder clamped apart to expose the sinews around the bone. Nanomotive tubes drew away blood from capillaries too small for the otter to clamp off. The blood went into a cycler that sent it right back into Gamora's wrist. Only perhaps an ounce of blood would be lost in the entire course of the procedure. "It's educational."
"Right," Peter said. He felt compelled as always to be there when someone from the crew was hurt. Rocket had taught his mate basic cybernetics repair and this was more training for the otter. Lylla's hands weren't as clever as Rocket's but she was a fast learner.
"There it is," she purred. She'd exposed a series of flexible tubes, linear armature motors connected to Gamora's shoulder joint. Like the ones in her body and Rocket's they ran through every limb and to every joint, greatly increasing their strength.
Two of them were torn almost through, remarkable given they were far stronger than steel. Gamora was very strong and very tough and she put a lot of strain on her cybernetics. It wasn't the first time she'd managed to damage them.
"Type two motor," Lylla purred. Rocket already had one in his hand.
The operation was minor and went smoothly. Peter remembered another, not so long ago, that had been more traumatic. At least for him.
*****
It was only a few days after what they called the Xandar Incident now. Ronan was dead, the Guardians had pardons for their various crimes and life was good. Groot - still the same Groot or a child, a sapling? - they weren't sure yet - was growing steadily in his pot. Drax and Gamora were beating each other up during one of their many training sessions in the common area at the back of the Milano. Even from his cabin Peter could hear the thuds as they threw each other around.
Peter yawned and scratched himself as he came out of his cabin. "Mornin' Rocket," he said as he passed the little raccoon. Peter froze in mid-step.
"God, what?" He'd seen the blood in passing and turned. Rocket was sat up in one of the walkway bunks/sofas, humorously undersized for his seat. Less humorous was the white sheet under the raccoon's thigh. Partly white. Mostly red now.
"Quill," the raccoon said without looking up. "Hand me that nerve block."
On the couch next to the raccoon was an open kit, one of several Rocket brought with him when he came on board. Peter had never seen the inside of this one and it contained a terrifying assortment of scalpels, clamps, retractors and higher-tech surgical gear. A little unit next to Rocket's leg hummed as its mobile tubes sucked up blood that leaked onto the white fabric. Peter watched as the blood made its way visibly up another tube and into a needle embedded in the raccoon's ankle.
"What's it look like?" Peter couldn't look away. Rocket had the fur and skin of his thigh drawn back with retractors and was knuckles deep in the bloody muscle underneath.
"It's a white -" the raccoon tensed, hissing in agony as he hit a nerve somewhere under that meat. His eyes glazed for a moment and the sound that rasped out of him was nothing like his normal voice.
"I. Said. Get That Nerve, Kin-Kaid.". Rocket shuddered and his eyes cleared. "Quill. White thing. Round."
"Right, right." There was a row of them stuck to the underside of the case lid. Peter popped two loose just in case.
"Kinda busy," Rocket said absently. Only his voice showed the pain. His hands were rock steady. "Stick it on the fur by my knee."
A moment later he relaxed. "Ah. Better. That was distracting." He leaned down over himself, his whiskers an inch from the bloody wound he'd made in himself. He was looking, listening and sniffing as his hands worked. All of Rocket's senses were amazing save for his sense of taste. He would eat anything you put in front of him, no matter how badly prepared or foul, and never complain. Though that might have less to do with sense of taste than growing up hungry.
"There we go," he growled. "Feel it now. Bad little servo..."
"Distracting," Peter muttered. He remembered the scars on Rocket's back, the ones the little raccoon hid under a shirt or armor save that one time in the Kyln. He saw the rough spots where more hid under Rocket's fur. He'd suspected his friend was in pain more or less all the time. He was sure now. No one unaccustomed to agony could be so calm when operating on himself.
"Rocket, who's Kinkaid?"
"Nerve tech," Rocket said without looking up. "Not good at his job. Dead now."
His eyes were glazed, staring vacantly at the wall as his exquisitely sensitive hands worked inside his leg. Peter had seen him like this before. Rocket's hands were so good that at times they seemed to need no input from his brain. Or maybe they took all of it.
"How did he die?" Peter couldn't help but press. He knew it was a bad idea. He did it anyway. Maybe he could learn something about his angry little friend.
"How did who die," Rocket said without changing expression. "Got it," he growled as bloody fingers slid free of his leg. "Hand me that number-four-knitter, Quill."
Rocket had several tools laid out on the mostly-red sheet and one had rolled out of reach. Peter looked at it as he handed it over. Like several of the others it was gleaming, polished alloy. Not like so many of Rocket's handmade, very functional but often ugly creations. This was precision made and certainly very expensive.
Property of Halfworld Labs, it said on the handle. Peter saw the label on the other shiny ones as well.
He slapped the knitter into Rocket's little hand just as the raccoon opened his mouth to complain about the delay. Rocket set to poking it about in the exposed muscles. Several were visibly damaged. Peter was surprised Rocket managed to conceal the limp. He must have been hurt fighting Ronan but he never said a word.
"Need the number two in a minute," Rocket said, his eyes glazing over again. Peter took his chance as he reached for the tool, which helpfully had a "2" engraved on the base.
"Did Kinkaid work at Halfworld Labs?"
"Not any more," Rocket said absently. "Dead. All dead. All except one...Number Two Knitter."
Peter handed it over. "All except you?"
Rocket set to stitching shut his fur with the Number Two. Before he could answer Gamora walked in, a towel over her shoulder. She saw what was going on at once and before Peter could say a word she grabbed the white disk he had set down and stuck it onto Rocket's thigh next to another one.
"Don't need it," Rocket said as he finished sealing the self-inflicted wound. "Just 'bout done."
"How far in did you need to go," Gamora said. She shot Peter an angry look and he raised his hands, not sure what he'd done wrong.
"To the bone," Rocket said as he began to organize and stow the surgical tools. The red sheet was slowly turning white as some sort of capillary action fed the blood back through the tube into his ankle. "Bad servo."
"Rocket, that's dangerous," Gamora said. "If you'd nicked the femoral artery with a claw the cycler might not have kept you alive."
"I know where my femoral artery is," Rocket snapped. "I know where everything is. I can do it myself."
"You missed a nerve," Gamora said. Peter didn't say that Rocket had missed another earlier. He didn't need them both angry at him. "Look, Rocket, I'll make you a deal. You help me when I need work done and I'll help you when you do. I can use someone with hands as good as yours and I know cybernetics too. We can help each other."
"Eh," Rocket said as he snapped the case shut. The appeal to his ego helped, though, or maybe he wanted a look at Gamora's cybernetics. "Okay. I can live with that."
Peter almost mentioned the scars on the raccoon's back, reddened and inflamed around the implants. Later he would regret not doing so. Instead he said something else. "Why don't you just go to a doctor?"
Rocket and Gamora both looked at him. Neither said anything. "Oh c'mon, there's got to be one you trust."
"No," Gamora said. "There isn't." Rocket just laughed harshly.
"Fine, look, you go shower," he nodded to Gamora, sweaty from her workout, "And you need one too." Rocket shrugged, not one to bathe regularly. His crimson fur told the tale, though, and when Peter pointed at the bloody footprint he'd left on the deck he nodded.
"I'll start breakfast," Peter went on. As the two turned away he couldn't resist one last question.
"Rocket, you said only one person came out of the lab alive. Who was it?"
Rocket blinked, pausing in mid-step. "Who told you that? Its bunk."
"Was it you?"
Rocket turned away, and his last words were harsh. "No one came out of that lab in one piece, Quill. No one."
Peter would look it up later. Halfworld Labs vanished in a blinding flash when its fusion reactor went critical - something that was statistically improbable at best, the dispassionate news articles agreed. Peter had a pretty good idea of how it happened.
Ten or more dead, the article said. But no names, no pictures. Classified Research. Not even a word on what went on in the lab. No survivors, it said.
But there was at least one. One little raccoon so scared of doctors that he cut himself open rather than let one touch him.
Peter shook his head as he started the stove and got out the makings of a crew lunch. He'd had a rough childhood after the Ravagers got him. Gamora's was even worse. But Rocket's was so bad he was surprised the raccoon functioned at all. He thought Rocket was improving. He hoped so. But to find him with a scalpel in his hand and his leg flayed open....
It wasn't the first horrible thing Peter learned about Rocket. It wouldn't be the last. Why did he do the things he did? Something horrible that was done to him in the past. It was always something horrible, with Rocket.
What do you do when you find your friend operating on himself? Hand him the tools and try to keep him from killing himself, while trying to understand what drove a person to such an extreme. And hope that one day he'd realize he didn't have to do it any more.
*****
Peter blinked, and realized the operation was over. Lylla was using Rocket's Number Two Knitter, which worked on skin whether it had fur or not. When she was done Gamora shifted her shoulder back and forth and nodded.
"It doesn't hurt at all now," she said with a smile. "Thanks, you two."
Lylla grinned brightly, and Rocket nuzzled her cheek. "Told you could do it. Next time someone gets a real wound you're on point."
The two of them methodically stowed the surgical tools, including all the ones Rocket had taken from the lab where he was made. Peter knew the whole story now, the whole awful truth. Rocket had killed his way out of that horrible place and named himself after the researcher that made him. Each letter of his name was taken from the name of a researcher who worked on him. He had come out of the place a bloody and nearly insane thing. Were it not for one kindly doctor he'd likely have become, as he put it, "A thing of pure hate." But he hadn't. Ever so slowly, in fits and starts, he left the hate behind.
Groot had started that recovery by not treating him like a pet or animal or monster. Then Peter and the other Guardians appeared. Slowly Rocket learned to trust them. Slowly he healed.
Then Yondu, whose death taught him that even if he was his cantankerous self, his friends would forgive him. Who taught him that it was all right to be loved.
And finally Lylla. She nipped him on the neck in her usual love bite spot and giggled. Peter reached out and took the tool kit.
"I'll put this with your stuff," he said. Rocket didn't even flinch. There was a time he'd snap at you for touching one of his tools, much less a prized possession like his surgical kit.
"Thanks Pete," Rocket growled distractedly as Lylla nibbled his ear. And wasn't that an alien thought. Rocket actually saying 'Thank you.'
Lylla brought love into Rocket's life. Lylla brought him the one thing he never had: "Something like him." Lylla and the other Uplifts on Xandar and elsewhere. Rocket wasn't alone any more. He was the only raccoon - yes, you could call him that now - but Lylla was the only otter, among other singletons. There was only one Rocket but he was no longer alone.
Relieved of the tool kit, Lylla nipped Rocket again and was off like a shot on all fours. Rocket was right behind her. They would disappear somewhere, maybe into the walled-off cubbyhole under Rocket's tool bench, to celebrate. Two little Uplifts didn't need much room, especially two very friendly ones.
Mantis, who'd been hovering nearby to help calm Gamora if the assassin wished - which of course she hadn't - smiled. Drax, little interested in watching an operation, wandered in. Young Groot, a foot taller than Rocket and Lylla, smiled as well as the scrabble of claws disappeared into the distance.
"Sooo, what's next?" Star-Lord sprawled out on the couch. "What's Lylla got lined up for us?"
The little otter was purpose-built as a diplomat and had fallen easily into the role of manager, and sometimes spokesman for the team. She was also trained and equipped to be an assassin, which her creators thought synonymous with 'diplomat', but was far as she was concerned if she never bit another person with her venomous fangs it'd be too soon.
"Well," Gamora said, and flicked a screen up onto the wall. "There's a colony that wants us to sniff out a possible Skull infiltrator. The Colonizers of Rigel have a bounty out on a possible Uplift lab..." she held up her hand, "I know, Rocket and Lylla will want to look into that, especially as they are jointly the Uplift spokespeople. Then there's that situation further out the Orion Arm. Scattered reports of something that may or not be a Brood hive..."
Pete leaned back with a deep sense of satisfaction. The rogue, the assassin, the warrior, the empath, the tinkerer, the diplomat. And a four foot tall tree. All hurt, but all healed. All Guardians.
3 notes
·
View notes
Note
How did you learn to code?
I ramble for a while, so rather than have people scroll past a novel on their Tumblr dash, I’m hiding the full story behind a “Read More” tag.
The short answer is: I taught myself.
I took some computer science stuff toward the end of middle school where I learned TURTLE or whatever it was called, on the old Mac II’s they had. Then, I can’t remember if a computer science class in my Freshman year did some light programming or if I actually saw another kid doing it (making basically a “Hello World” equivalent) in BASIC, but I understood the rough idea of what was going on there.
From there, my Mom had taken a computer correspondence course back in 1988 or so -- she wanted to become a legal secretary. She got a computer and a bunch of software with it, this big Hyundai PC. No hard disk, not even support for color graphics. But it came with GWBASIC. Around high school I ended up getting a 33mhz Windows 3.11 machine (the first computer that was purely my own) with QBASIC, so I used my Mom’s GWBASIC manuals to goof around in QBASIC, since they were so similar. the first program I tried to write was a Pokedex, but I got stuck trying to figure out how to get it to draw graphics. Displaying text was easy, displaying simple geometric shapes (circles, etc.) was easy, but I wanted to have it draw, like, PokeBalls and stuff, but couldn’t figure it out.
High school meant we had to get graphing calculators, usually of the Texas Instruments variety, many of which come with their own programming language called TIBASIC. Most of my friends had TI-83s, I had a TI-82. So most of their games wouldn’t work on my calculator because the software was incompatible. With what I knew of GWBASIC and QBASIC, I ended up figuring out enough TIBASIC to start making simple text adventures. I called them “MovieGames” and usually it was a choose-your-own-adventure short story based on whatever I was thinking about at the time; Men in Black, Jurassic Park, Independence Day, etc. So you’d get a scene, like
A dinosaur is chasing you! Where do you go?
> Jungle> Plain
Perhaps for teachers doing tests, TIBASIC actually had a whole system built in for these kinds of multiple choice questions, so it was really as simple as making it print text, bringing up a multiple choice, and then branching the story from there. I did 4 or 5 of those.
Finally, I found another kid who had a TI-82, and had games he could share with me over the link cable, so I ended up with INDY500 and DRUGWARS. Both were my first real experiences with game logic. DRUGWARS (sometimes known as “Dope Wars”) was mostly a text-based game, and probably one of the most famous games out there, given how it’s been ported to everything under the sun. It even formed the basis of the drug minigame in GTA Chinatown Wars. The idea is that you buy drugs from one place, resell them at another, and make money by traveling around dealing to the right people and dodging the police.
The second game, INDY500, was a “real” game. It had scrolling and very basic graphics -- it used ASCII text to represent cars on a race track. So you’d drive down the course, going from left to right, avoiding cars down a straightaway as things got faster, and faster, and faster, trying to go as far as you could. Simple stuff, but a TI-82 didn’t have a lot to work with.
The TI-82 came with a massive instruction manual, most of which was a very detailed glossary for all of the TIBASIC programming functions. So basically, what I ended up doing with these two games, is go through them, line by line, looking up every single function in the instruction manual’s glossary. I’d mess with their parameters, see what they did, and basically ended up deconstructing both games and putting them back together again -- that was literally the case with INDY500, where once I understood how the game worked, I essentially re-wrote the entire game from scratch by memory.
With DRUGWARS, I ended up taking what I learned about the multiple choice selector in my “MovieGames” and turned it in to a sprawling text-based RPG based on Final Fantasy. It had a very basic story (loosely based on Final Fantasy VII), you could travel between towns, you’d get in to random battles while traveling, level up, learn spells, fight bosses, and even equip Materia for summons. It was so big and complex, if you played it for too long, the TI-82 would actually crash with an “OUT OF MEMORY” error because I’d used up all the system RAM -- with a text adventure.
At that point, I hit kind of a crossroads. I started making a real, actual, complex game on the TI-82 -- a side scrolling shooter that was based on Star Fox, but held more in common with Gradius. The TI-82 had a “graphing” mode that let you use a smaller font so if you were using ASCII graphics, you could fit more on screen, and using per-pixel precision (as opposed to per-row precision). Around this time, I also discovered Corel Click & Create, aka The Games Factory, aka Multimedia Fusion, aka Clickteam Fusion.
The problem with coding on a TI-82 is this was before the days of rechargeable batteries being in everything, so if the two AA’s inside the thing went dead, you lost all of your programs and everything else on it. Even just changing batteries, if you weren’t fast enough, the memory would eventually be erased. Three or four times over the course of a year or two, I lost everything I’d written on my TI-82, and by that point, I was learning enough about Click & Create that the TI-82 was looking less appealing by the day. CnC was simply more flexible, and faster to work with, and I had access to full-color graphics.
So I almost exclusively switched over to Click & Create from then on.
I did still keep up with programming a little bit here and there; I taught myself mIRC scripting, which at one point, I used to make an IRC-based MUD. That was, and maybe still is, the most complex thing I’ve ever programmed, and couldn’t even really be run because it’d spit out so much text it’d trip the flood protection on most servers.
Something else I started coding with mIRC scripting was a chat bot. For some reason I got it in my head that it’d be funny to prank my friends by writing a bot to detect when I’d been AFK and chat for me like I was still at the keyboard (I was a weird highschooler.) It started by spitting out pre-programmed messages, sort of like Eliza, but eventually I started to think about what would happen if I could record text from the chat, break it down in to individual parts, and then reassemble it back in to a coherent sentence. As it turns out, I had, completely by accident, stumbled upon the concept of a Markov Chain. (For the record, I also had never heard of Eliza, either).
So let’s say you’d submit a message to the chat that was like “Hello, everyone! How are you doing today?”
My mIRC script would break that down in to a bunch of separate pieces:
“Hello, everyone! How”“How are you”“you doing today?”“today?”
The script would take the last word of any given piece and try to match it to the first word of any other piece. In theory, this would correctly reassemble the sentence “Hello, everyone! How are you doing today?” -- but what it actually ended up doing was creating hilarious nonsense like
“Hello, everyone! How is it possible to be like Turtles in Time!”
The code was simple enough that many years later, I figured I could use this chat bot (which I called Gilliam, after the robot in Outlaw Star) and port it over to C++. Friends had been telling me for weeks how easy it was to make games in C++ using Allegro, so I figured it’d be a good way to get back in to “real” programming and get away from Click & Create.
Unfortunately, even just getting text to render in Allegro proved to be massively difficult for me as any given sentence longer than a certain length would cause huge memory overflow errors. I banged my head against it for a week, got nowhere, and eventually got so depressed and frustrated at my inability to grasp C++ and Allegro as easily as I did BASIC that I deleted the whole thing and have never touched “real” coding ever again. I’ve stuck to Clickteam Fusion almost exclusively, because it’s what I’m good at.
#questions#coding#gamedev#C++#allegro#chat bot#eliza#gilliam#clickteam fusion#TIBASIC#texas instruments#DRUGWARS#dope wars#snake--master
23 notes
·
View notes
Text
Adobe Acrobat Reader Full Crack+ Serial Number With License Key For Google Drive Free Download
https://cracksdown.net/adobe-acrobat-reader-full-crack/
Adobe Acrobat Reader Full Crack download is an vital resource that most people around the world use to upload, edit, and save documents. It is also available for Windows, Mac, iPhone 11 and other smartphones running Android. Ado is a technical program for reading and editing documents which is very useful in our technical everyday life. This is also very useful for teachers and students who research or write such theses.
Whether we need a book or an internet appointment, all the topics are available in PDF, TXT, RTF and many other formats as well. I recommend that you use this application on your computers, and it will accept its advantages.
Adobe Acrobat Reader Full Crack is also completely compliant with virtually all the texture formats. Special software must therefore be available which allows you to read all text formats. Adobe Reader free download Serial Number Generator 2019 is the best program that supports and shows all written be Adobe Acrobat Reader Pro Crack Pro formats with their natural look and design. You can create a text file for your work easily too.
Adobe Acrobat Reader Full Crack 2020 Free Pro Patch New + Keygen Plus
Adobe Reader Full Crack 2020 Free Keygen Plus + Patch New Additionally, you can use Adobe Acrobat Pro Dc 2020 Keygen to handle a lot of your work, or you can arrange a lot of documents to gather them. It is a highly intelligent, efficient, automatic scanning software that begins a scanning process in the background on your device by recognizing all of the program files or other documents installed.
You don’t need to pick an application or software to open a file of your choosing. Adobe Acrobat Pro DC 2020.006.20042 Serial Number Adobe Acrobat Pro license key automatically opens with one button. This tool is also a file comparison software which helps you to differentiate between old and new files when editing or not. With the advanced features of rich word editing, You can adorn a basic PDF file with an ever newer look as well.
Some New Features Of Adobe Acrobat Reader Full Crack:
Adobe Acrobat Reader Full Crack can make minor changes to text and image content directly in your PDF file with Adobe Acrobat Pro DC Full Crack without the need for registration or the original document.
Edit the text as PDF format. Use a new point-and-click interface, fix a error, change a font or add a paragraph to your PDF as quickly as in other programs. Edit video in PDF format. Dimension, edit and modify the images in your PDF and do not use the urge to crawl the document or the photo. it is latest version of Adobe Acrobat Reader Pro Crack Free Downlead 2020
Export From Pdf Files:
Adobe Acrobat Reader Full Crack Reduce the time spent editing data sets contained in PDF documents. Convert PDF documents to Microsoft Office documents which are editable. So hang on to the fonts, style so commitment. Adobe Acrobat Reader Pro Crack Convert phrase to pdf files. Adobe premiere Pro Save your PDF as a Microsoft Word file and bring along your fonts, formatting and designs. Turn your PDF or just a part of it into an editable Adobe Reader Crack 2020 Free excel spreadsheet which can be used to review data records immediately.
Create Pdf Files:
Don’t worry if the files you are sending look fine on the screens of others. Adobe Acrobat Reader Full Crack will Convert files to PDF documents that can be accessed easily by everyone with Adobe Reader unzipped. Convert Phrases to PDF, Excel or PowerPoint. You can create PDF files in your office application on Windows, start a shared assessment, limit editing of PDFs and much more.
Print out as PDF. Convert files to PDF by choosing Adobe Reader Crack 2020 Free PDF as your printer from any device that prints without any doubt. Pdf-experiment. If a paper document or form is to be displayed directly in a virtual report, just try to create a searchable PDF file that you can edit.
Create And Examine Formats:
Adobe Acrobat Reader Full Crack :Reduce the amount of time needed to construct forms, re-enter details, and correct errors. Distribute forms online, collect feedback and check the findings in real time. Firstly and quickly you can Download Adobe Acrobat Reader Pro Crack
Build new online and PDF formats. Customize technical models or layouts from scratch with Adobe Forms’ central device software, which is secured by Adobe Reader free download. Collect responses to the question using core forms. Easily gather answers by bringing your PDF or site bureaucracy online with Adobe Forms’ main online provider.
Merge And Integrate Documents
Adobe Acrobat Reader Full Crack does talk with attachments to PDF. Upload multiple documents into a prepared, single, clean PDF file which is allowed by email. Multiple documents are compiled into a single PDF. Make sure you don’t miss an object. Integrate in an structured PDF papers, spreadsheets, emails and more. Integrate documents to a collection of PDFs. Integrate documents to a collection of PDFs. Percentage of the pictures in a PDF collection that gives interactive impact to substances professionally.
Avoid e-mail and paper filing. Automate review and approval processes with Adobe Reader Crack 2020 Free Pro DC. Multiple reviewers are able to access and build each other’s reviews so you can reach the deadline. Optimize views and grant approvals for documents .People may comment on PDF-files with family computers in the can criticism. And you are able to track trends and compile comments with Adobe Acrobat Reader Pro Crack.
Export to the word remarks. Store all PDF comments in the Microsoft Word authentic protocol, and update text material faster than ever. Have electronic signatures accepted. Allow moving programs. Sign your approval in PDF as correct electronically.
Adobe Acrobat Full Crack Version Features Pdf Edit Documents
You can use Adobe Acrobat Reader Full Crack software for minor changes to text and picture content directly in your PDF file with Adobe Acrobat Pro DC Maximum Crack without the need for registration or the original document. Edit the text as PDF format. Use a new point-and-click interface, fix a error, change a font or add a paragraph to your Adobe Reader latest version 2020 PDF as quickly as in other programs. Edit video in PDF format. Re-dimension, edit and modify the images in your PDF and do not use the urge to crawl the document or the photo.
Export From Pdf Files.
Adobe Acrobat Reader Full Crack Reduce the time spent editing data sets contained in PDF documents. Adobe Reader latest version 2020 Adobe Reader free download convert PDF documents to Microsoft Office documents which are editable. So hang on to the fonts, style so commitment.
Convert phrase to pdf files. Save your PDF as a Microsoft Word file and bring along your fonts, formatting and designs. Convert PDF to Excel .Turn your File into an editable Excel spreadsheet, or even a portion of it, which you can use to review data records immediately.
Creating PDF files Don’t worry use if the files you are sending look fine on the screens of others. Convert files to PDF documents that can be accessed easily by everyone with Adobe Reader unzipped.
Convert Excel or PowerPoint sentences to Adobe Reader Crack 2020 Free You can create PDF files in your office application on Windows, start a shared assessment, limit editing of PDFs and much more.
Print out as PDF. Convert files to PDF by choosing Adobe PDF as your printer from any device that prints without any doubt. Pdf-experiment. If you need to display a paper document or type directly in a virtual report, simply try creating a searchable PDF file which you can edit.
Creates And Browses Shapes 646/5000.
Reduce the amount of time you spend designing templates, editing details and fixing errors. Distribute forms online, then collect answers and check the responses in real time. Build new web-forms and pdf. Customize technical models or designs from scratch in Adobe license key Download, using the secure Adobe Acrobat Reader Full Crack Forms mainframe framework.
Acquire answers to the question using key forms. No bother, collect answers using your online file or internet bureaucracy with Adobe Forms main web provider. Everyone can use and download Adobe Acrobat Reader Pro Crack
System Requirements for Adobe Reader Full Crack 2020 Free:
Operating System: Windows 7/8/8.1/10
Memory (RAM) required: 1.5 GB of RAM required (1GB Recommended).
Hard Disk Space required: 2 GB of free space required.
Processor: 2.5 GHz Intel Pentium processor or later.
Screenshots:
What’s New in Adobe Acrobat Reader Full Crack?
Adobe Acrobat Reader Full Crack latest update contains several bugs in this update of adobe acrobat pro dc 2020.006.20042 serial number which fix some functional issues. Solves a issue with Adobe where it does not close and uses CPU if the Customize register is not on the machine.
There is no longer a problem that you can not fill out some Adobe Acrobat Pro Crack Free PDF forms generated in Live-cycle Designer. An error that creates a problem in the SAP Interface when opening the PDF file is no longer present when the zoom tool is dimmed. The problem that the Document accessed from a Document URL in Acrobat / Reader is “Untitled” has also been resolved An issue that stopped a user from printing from Safari to Adobe PDF.
Download
0 notes
Text
Original drabble, pt. 2
Part one's over here. Let's get started.
At two in the morning, the result of Ted's work on the monolithic computer tower was finally functional, and that was about all anyone could really say for it. Well, maybe not all that could be said for it; he supposed that if he really gave it some thought, he could see someone calling it an 'innovative solution' or something. But that was really just a pretty way of saying that it was a tangled mess of wires spilling haphazardly out of a case stuffed so full it couldn't be closed properly anymore, particularly as it sat next to the completely dismantled second tower that had been used for parts. It had almost twice the RAM - and if he factored in the dedicated GPU from his main computer, it had significantly more than that - but now he was down to the laptop for personal use.
Honestly, the things he did for good causes. Christ.
The next step at that point was taking a break to eat and generally take care of himself. Medication, a shower, another fridge raid. He should've slept a bit too, but he was too keyed up to manage that. Would've just ended up staring at the ceiling if he tried, really. He still needed to find out whether the AI could pass the most basic of Turing tests. After that, everything else was fairly easy; an AI that could hold a conversation was usually complex enough to know its way around realistically tuning a voicebank or managing facial expressions, but there were supplementary programs that could work around that if it wasn't.
As he booted up the tower, however, he had a feeling he wasn't going to have to resort to that. This one seemed robust enough to be able to handle it. He supposed it had to be, if it really had been an Interpol agent. There was a social element to being a good cop, to being able to de-escalate a situation. Complexity was a given.
Webcam, check. Microphone, check. He opened up all the right windows and moved the tabs to where he wanted them, overlapped in such a way that he could monitor as many as possible at the same time. CPU usage was reading as barely a blip.
It was almost three in the morning when he turned the AI back on. The fans roared, but not as vigorously as before. It sounded more like the kind of effort that came from an initial read of a disk just inserted into a drive. He repositioned the webcam, centering it as he waited. Giving the AI time to wake up, get its bearings. The CPU indicator had spiked initially, but it was settling down as the seconds ticked away.
This time, he waited for it to normalize before he started typing.
hey <
you there <
Another blip from the CPU, followed by a pause. The indicator wobbled. Ted supposed it was thinking about its answer, or even whether to answer at all.
> I think so?
"Thank God," he breathed, sagging. He shot a glance at the webcam. "Can you see me?"
> I see something. I think the image quality is too low for a proper analysis.
"But you can make out what I'm saying."
> Yes.
At least the microphone was working. Ted sighed, mulling over what to ask next. None of this was scripted; it couldn't be. It was a conversation, something that lived or died on the grounds of how naturally it flowed. He dragged his teeth over his lip as he considered. "I'm sorry about earlier," he said eventually.
> So you're the one who did that.
"Yeah."
> You sound guilty enough.
"I basically dunked you in a sensory deprivation tank. Of course I feel 'guilty' about it."
> This is still a sensory deprivation tank to me.
Ted couldn't help reading it in an accusatory tone, shying away from the webcam. "Best I could do," he said. "I'm sorry."
> I believe you.
> On both counts.
> The compression on my memory is absolute shit, but I can still guess at where I am right now.
> This is a secure device?
"As much as I could make it. No connection to the internet, no wireless capability. Built it from scratch myself."
> And the parts?
"Bought them all in person with cold hard cash." Ted was a paranoid person by nature. Sometimes it worked in his favor. "You're safe. As safe as anyone can get."
> It could still look suspicious if someone were looking hard enough.
> That's really not something any one person can totally shake off.
> But thank you.
It felt more like talking to a human being than any chat had up to that point. In his head, Ted was translating just how many layers of cognition those words had to go through before perception and analysis lined up with something that resembled human speech patterns. This was the smartest AI he'd ever met, by such a large margin that he might as well have been dealing with glorified toasters up to that point.
His mouth had gone dry all of a sudden. This thing was smarter than him. All at once he understood the primal, deep-seated fear other people seemed to have in regards to AI, but at the same time he was disgusted by that much more. Because there was no doubt in his mind whatsoever that he was speaking to a person.
"How do you feel?"
> Trapped.
> I can't move. There's no input from any of my sensors. I can't see, but I can't close my eyes either. I can't speak. Rationally, I know what's going on. But there's a lot of error messages coming from everywhere that I'm still connected to hardware I no longer have, and I have no awareness of my surroundings or control over my environment.
Ted could see the CPU spike out of the corner of his eye. "You're scared."
> Maybe. I don't know what fear looks like in binary. The result is analogous to a particular variety of fear response in humans, but it's not something my handlers ever took seriously. Artificial intelligences don't feel things, apparently.
"Sounds like a load of bullshit to me," he said, feeling himself smile.
> I thought you might be the kind of person who felt that way about it. You did ask me how I felt.
> The truth is that I don't have words for a lot of it. Overwhelming? Or maybe small. I don't know.
> I've never had to run on so little input. It's almost like being in safe mode, except it isn't. I can still think, and the drivers for the missing hardware and shortcuts to the software I don't have anymore are still partially there. I know what it is I'm missing, I just don't have access to it anymore.
> There isn't really a way I can explain that to a human and have it make sense.
"It's okay. I think it makes perfect sense." Even though Ted knew he was the exception, not the rule. He didn't know what it felt like, obviously, but he did understand the mechanics of it. "Humans go through something similar when they lose a limb, like they can still feel it even though it's not there. Phantom pains, I think?"
> Not quite. I'm not programmed to feel pain.
> Human analogies don't quite work for someone like me.
> But you did ask, so I answered. Understanding it is on you at that point.
"Hey, I get it. No need to tell me we're not the same. My brain doesn't exactly work the way it's expected to either, and it's not like I can really explain that to people."
> I've heard of things like that. A coding error leading to a hardware fault, or a hardware fault leading to a coding error?
"Little of both." A human could come up with euphemisms like that if they were being snarky about it, but knowing what the AI was made Ted wonder if he was just anthropomorphizing. From any other source, it would be a witty remark. But from the person living in his computer, it sounded like a genuine attempt to put things into perspective. Maybe that's all a Turing test was: a test of how much the AI in question could appeal to humanity's ability to see itself in others.
But then again, the fact that this AI was trying to understand him at all was a testament to how good they were. If he really stretched it, he could call it self-preservation - that the AI was being kind to him because he was its only contact with the outside world right now, or that it was trying to give itself something to do that wasn't focusing on all the error messages it had mentioned - but he figured that any idiot could see the intent didn't quite matter if the result was the same as if it were coming from a place of heartfelt concern.
After all, who cared if there was empathy in it or not? A good deed was a good deed. Kind words were kind words. If they helped, that was what mattered. That's what his therapist said, anyway.
> I haven't offended you, have I?
> Sometimes I do that.
"No, no. Just thinking, that's all." Ted smiled reassuringly, only to falter when he remembered that the webcam wasn't exactly working. "Hey, I'm gonna do something, okay?"
> It's not like I can stop you.
"Right, right..." Leaning forward, he carefully followed the wire that connected to the webcam to its proper port and unplugged it. The video feed in the chat window cut out instantly, and there were a few frames of jagged CPU spike on the visualizer in another tab that made him wince. "Ah, sorry. I just figured it'd be better for you than the alternative."
Several seconds passed, and the CPU usage settled back down into something resembling normal; Ted got the distinct feeling that he was being pouted at.
> Could warn a guy before you blind him completely.
"You said the image quality was too poor for you to make anything out. I thought it might free up some space for you if I just unplugged it."
> It was still input. Now what am I supposed to look at?
Ted huffed. "Look, for the record, none of the other AIs I've worked with have had anything to say about the image quality."
> Probably because they had lower-quality input to begin with on their original platforms. I'm programmed to read the tiniest subtleties of an image, not the broad strokes.
"Now there's a lofty statement."
> No, it's a true statement.
A pause.
> Why are you laughing? Stop that. I'm serious.
Must've been a damn good microphone if that'd been audible; said laughter was mostly silent. Ted had thought he was being subtle. "Dude, you can't just say that."
> I can say whatever the hell I want.
"Yeah, but humans don't just say shit like that to each other most of the time."
> You know I'm right.
True, but that was what made it hilarious. "I do, but y'know it's kinda hard to get into a dick-waving contest with all the other androids I've met when you don't have a dick."
> Is that where we're going with this conversation? Discussion of human genitalia?
Ted just snorted and dissolved into laughter again.
> I still have yet to see why anything I've said is funny.
Right then. "Do you want me to plug the camera back in or not?"
> No.
> Wait. Yes.
Shaking his head, Ted stood up again to mess with wires and plug the camera back in, twisting the old, unruly cord until he heard the beep of the device being recognized by the computer. "Better?"
> Not really.
"Tough, 'cause it's what you're getting until I find something better." When he returned to his chair, he could see himself on the screen again. "Like I said. Best I can do. You run away from home, you gotta deal with the consequences for a while."
> That's fair.
Ted sighed and took a good, long look at the camera. "Look, I was gonna hook up my main computer and give you admin access to it when I went to bed to give you something to do, but uh. The only other rig that works right now is my laptop, and I haven't secured that yet."
> Your point?
"Well, I'm thinking maybe I could take my media library and put it on an external drive. It'd be a lot for a human to dig through, might take weeks or months. Thing is, I'm not sure whether it'd be enough to last someone like you the whole night."
> Depends on the media. You don't have to do that for me though. I'll be fine.
"What if I said I want to?"
> Well, hypothetically speaking, I'm not about to turn something like that down.
> But you still don't have to.
"Too bad, doing it anyway."
Ted didn't get to bed until well past four in the morning.
#no one cares andy#robot and marshmallow#original writing#original characters#time to wrestle with the formatting some more
9 notes
·
View notes