#4G Router Store
Explore tagged Tumblr posts
Text
Ready-to-Use Internet Bandwidth: The Smart Choice for Agile Business Connectivity
Introduction
In today’s hyper-connected business landscape, delays in internet deployment can mean lost productivity, missed opportunities, and frustrated teams. Traditional internet setups often involve lengthy installations, complex infrastructure, and rigid contracts—slowing down operations when speed is critical.
Enter ready-to-use internet bandwidth: a seamless, on-demand solution that delivers instant, high-speed connectivity without the wait. Whether you're launching a startup, setting up a temporary site, or ensuring business continuity, this agile alternative keeps your operations running smoothly from day one.
This guide explores what ready-to-use internet bandwidth is, its key benefits, ideal use cases, industry relevance, comparisons, success metrics, and FAQs—helping you make an informed decision for your business.
What is Ready-to-Use Internet Bandwidth?
Ready-to-use internet bandwidth is pre-configured, enterprise-grade internet access that can be activated immediately—often within minutes. Unlike conventional services that require lengthy installations, this plug-and-play solution is designed for speed, flexibility, and ease of use.
How It Works
Pre-installed fiber lines in commercial buildings
Plug-and-play 4G/5G wireless routers for instant connectivity
Satellite or edge-managed connections for remote locations
Flexible ISP/MSP-managed plans with no long-term commitments
Essentially, it’s internet on demand, eliminating downtime and infrastructure headaches.
Key Benefits of Ready-to-Use Bandwidth
Instant Deployment – Get online within hours, not weeks
Scalable on Demand – Adjust bandwidth as business needs evolve
Minimal Setup Required – Plug-and-play, no heavy hardware required
Portable and Mobile-Friendly – Perfect for pop-ups, events, and field sites
Reliable Business Continuity – A seamless backup during outages
Cost-Efficient – Pay only for what you need, avoid infrastructure investments
Real-World Use Case Scenarios
Startup Launch in Dubai A fintech startup needed connectivity within 24 hours. Traditional ISPs estimated 10 days. With a 5G-ready bandwidth kit, the team was fully operational the next morning.
Event Wi-Fi at a Tech Expo An exhibition required on-site Wi-Fi for 500+ attendees, ticketing, and live streaming. A mobile solution delivered seamless, high-speed internet for the entire 3-day event.
Emergency Backup for a Hospital A hospital lost its fiber connection due to construction damage. A pre-configured 4G setup automatically took over, maintaining access to critical systems and records.
Who Needs Ready-to-Use Internet Bandwidth?
Startups and Coworking Spaces – Launch instantly without ISP delays
Retail and Pop-Up Stores – Set up fast POS and customer Wi-Fi
Construction and Field Teams – Stay connected in temporary locations
Events and Exhibitions – Enable ticketing, streaming, and guest Wi-Fi
Remote and Hybrid Teams – Ensure reliable connections for staff
Disaster Recovery Operations – Maintain operations during outages
Industry-Specific Applications
Healthcare Maintain access to digital health records, telemedicine, and real-time updates during crises or connectivity disruptions.
Retail Support point-of-sale, mobile apps, and customer-facing Wi-Fi in seasonal or mobile retail setups.
Construction Enable communication and design collaboration across teams on rugged or rotating job sites.
Education Power remote learning environments, hybrid classrooms, and administrative systems.
Media & Broadcasting Upload media content, livestream from remote locations, and collaborate in real-time.
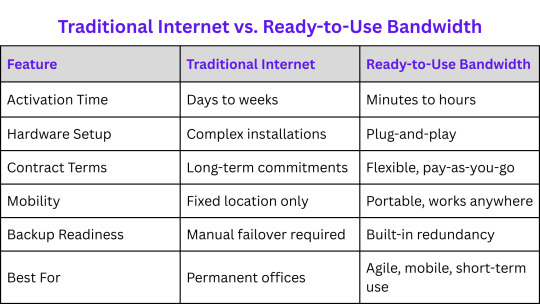
Traditional Internet vs. Ready-to-Use Bandwidth
Integration with Emerging Technologies
Ready-to-use bandwidth works seamlessly with:
SD-WAN for intelligent traffic routing across multiple networks
IoT Devices in smart construction, retail, and logistics
Cloud Platforms like AWS, Azure, and Google Cloud
Cybersecurity Suites with firewalls, VPNs, and real-time monitoring
Unified Communications to power VoIP and remote conferencing
Measuring Success: ROI and Performance Metrics
Deployment Time Saved – Reduced setup time compared to ISP provisioning
Downtime Reduction – Higher uptime during outages or ISP failures
Cost per Day of Connectivity – Clear budgeting for temporary deployments
User Experience Metrics – Faster employee onboarding and higher productivity
Scalability Tracking – Bandwidth expansion aligned with operational peaks
Choosing the Right Provider: What to Look For
Strong local and national coverage
99.9%+ uptime guarantees
Enterprise-grade security protocols
24/7 technical support with rapid response
Bandwidth scalability from 50 Mbps to 1 Gbps or more
Seamless cloud platform integrations
Why Ready-to-Use Bandwidth is the Future
As businesses adapt to rapid market changes, hybrid workforces, and decentralized operations, internet agility becomes essential. Ready-to-use bandwidth meets this demand with speed, flexibility, and reliability—empowering businesses to launch quickly, scale seamlessly, and ensure continuity without delay.
Its portability and minimal setup make it an invaluable asset for modern enterprises navigating uncertain environments, seasonal surges, or location changes. Whether you’re setting up a remote hub, hosting a large-scale event, or ensuring operational continuity, this solution aligns with your goals while reducing IT complexity.
Final Thoughts & Get Started
In a fast-paced digital world, businesses need more than just internet—they need instant, secure, and scalable connectivity that keeps up with innovation. Ready-to-use bandwidth offers just that—delivering a future-ready solution for companies of all sizes, across industries.
Don’t let long installations or rigid contracts hold you back. Empower your business to scale faster, adapt quicker, and operate smarter—with no compromise on speed or reliability.
Ready to upgrade to instant business connectivity? 👉 Visit our Technology Incubation Services page to explore how we can deploy ready-to-use internet solutions tailored to your needs.
Frequently Asked Questions (FAQs)
1. How is ready-to-use bandwidth relevant to IT and engineering students? It gives students hands-on knowledge of real-world connectivity solutions, vital for careers in network engineering, IT support, and telecom. Learning how agile bandwidth solutions work prepares them for roles in smart infrastructure and cloud environments.
2. Are there certifications or skills related to ready-to-use internet solutions? Yes—skills in SD-WAN, 5G/LTE, cloud networking, and cybersecurity are highly relevant. Certifications like CompTIA Network+, Cisco CCNA, or AWS Certified Networking help professionals stand out in roles involving enterprise connectivity and infrastructure planning.
3. How does this technology contribute to digital transformation strategies? Ready-to-use bandwidth enables rapid deployment of cloud services, supports hybrid work models, and ensures continuous connectivity—making it a key enabler in agile and DevOps-driven digital transformation projects.
4. Can businesses monitor and manage usage in real-time? Yes. Most providers offer dashboards or mobile apps with tools to track data usage, allocate bandwidth, configure firewalls, and manage users—empowering even non-technical teams to stay in control.
5. How is ready-to-use bandwidth different from using a mobile hotspot? Unlike mobile hotspots, ready-to-use bandwidth solutions are enterprise-grade, offering higher speed, stronger security, support for more devices, and built-in redundancy—designed for serious business use.
0 notes
Text
How to Protect Yourself from EMF Radiation: A Comprehensive Guide
In our increasingly connected world, the proliferation of electronic devices and communication networks has led to growing concerns about electromagnetic field (EMF) radiation. With the rollout of 5G, the placement of cell phone towers, and the widespread use of Wi-Fi, more people are becoming aware of the potential health impacts of EMF exposure. This guide explores practical ways to protect yourself from emf powerlines safe distance radiation, including how to turn off 5G, the best EMF blockers, and how to maintain a safe distance from cell phone towers.
1. How to turn off 5g?
The advent of 5G technology has raised concerns due to its higher frequency range compared to previous generations of cellular networks. If you're worried about 5G radiation and want to limit your exposure, here's how you can turn it off on your devices:

On Smartphones: Most smartphones allow you to disable 5G by switching to a lower network band, such as 4G LTE. To do this, go to your phone's settings, find the mobile network options, and select the option to disable 5G or switch to 4G LTE.
On Routers: Some modern routers support 5G Wi-Fi. To turn it off, access your router's settings through a web browser or app, navigate to the wireless settings, and disable the 5G band, leaving only the 2.4 GHz band active.
By turning off 5G, you can reduce your exposure to this higher-frequency radiation, especially in areas where the network is still being rolled out and tested.
2. Best EMF Blockers
EMF blockers are devices or materials designed to shield you from electromagnetic radiation. They come in various forms, including phone cases, pendants, and even clothing. Here are some of the best options:
Phone Cases: EMF-blocking phone cases are designed to reduce the amount of radiation emitted by your smartphone. Look for cases that have been independently tested and certified to block or deflect EMF radiation.
Shielding Fabric: EMF shielding fabric can be used to make curtains, blankets, or clothing that blocks radiation. This fabric Is wifi harmful to babies? often made from materials like silver or copper that can reflect EMF waves.
Faraday Bags: These are specially designed pouches that block all electromagnetic signals. They're ideal for storing phones or other devices when you don't want to be exposed to EMF radiation.
3. Safe distance to live from cell phone tower? a Cell Phone Tower
Living near a cell phone tower is a common concern due to the constant emission of RF (radiofrequency) radiation. While the exact safe distance can vary depending on the tower's power and design, a general rule of thumb is to live at least 400-500 meters away from a cell phone tower.
At this distance, the intensity of the RF radiation decreases significantly, reducing potential health risks. If you live closer to a tower, consider using EMF-blocking materials in your home to mitigate exposure.
4. EMF Protectors
EMF protectors come in various forms, including devices that can be attached to your electronic gadgets, wearable items, and even stickers. These protectors are designed to neutralize or block the harmful effects of EMF radiation.
Stickers and Chips: These small devices can be attached to your phone, laptop, or other electronic devices. They claim to neutralize or harmonize EMF radiation, though the effectiveness of these products is still debated.
Wearable EMF Protection: Wearable items like pendants, bracelets, or clothing infused with EMF-blocking materials offer another layer of protection. These are particularly popular among individuals How to protect your home from emf? are sensitive to EMF radiation.
5. EMF Shielding for Your Home
Protecting your entire home from EMF radiation can be achieved through various methods, from simple adjustments to specialized devices:
EMF Shielding Paint: This special paint can be applied to walls to block EMF radiation. It's particularly useful for bedrooms or areas where you spend a lot of time.
Window Films: EMF-blocking window films can be applied to windows to reduce radiation from external sources, like cell towers or Wi-Fi signals from nearby buildings.
Whole House EMF Blockers: These devices are installed in your home's electrical system and claim to neutralize or reduce EMF radiation throughout the house. They can be a significant investment, but they offer comprehensive protection.
6. EMF Harmonizers
EMF harmonizers are devices or materials that claim to balance or neutralize the harmful effects of EMF radiation rather than block it outright. They are often based on the idea that EMF radiation disrupts the body's natural energy field, and harmonizers aim to restore balance.
Harmonizer Pendants: These wearable items are designed to protect you by harmonizing the EMF radiation around you. They're often marketed as providing a calming effect and reducing symptoms like headaches or fatigue.
Home Harmonizers: These are larger devices meant to be placed in a central location within your home. They work by emitting frequencies that counteract the negative effects of EMF radiation.
7. Wi-Fi EMF Radiation and Protection
Wi-Fi routers emit radiofrequency radiation, a type of EMF that can penetrate walls and other materials. While the health risks are still debated, many people prefer to limit their exposure:
Wi-Fi EMF Blockers: Devices like router guards or EMF-blocking pouches can reduce the amount of radiation emitted by your Wi-Fi router. Router guards are mesh boxes that can be placed around the router, reducing the radiation without impacting the Wi-Fi signal too much.
Turning Off Wi-Fi at Night: One simple way to reduce exposure is to turn off your Wi-Fi router when not in use, particularly at night. This reduces the amount of continuous radiation in your home.
Positioning the Router: Place your router in a location that is away from bedrooms and living areas where you spend a lot of time. The further you are from the router, the less radiation you're exposed to.

8. Wearable EMF Protection
For those constantly on the go, wearable EMF protection offers a convenient way to shield yourself from radiation:
EMF-Blocking Clothing: Shirts, hats, and even underwear made from EMF-blocking materials can reduce your exposure while you're out and about.
Pendants and Bracelets: Wearable items infused with materials like shungite or copper claim to offer protection by either blocking or harmonizing EMF radiation. These are easy to wear and can be a good option for daily use.
Conclusion
In today's world, where EMF radiation is nearly impossible to avoid, taking steps to protect yourself can bring peace of mind. From turning off 5G to investing in the best EMF blockers and maintaining a safe distance from cell phone towers, there are many ways to reduce your exposure. Whether you opt for EMF shielding paint for your home or wearable protection for when you're on the move, the key is to stay informed and choose the methods that work best for you. By understanding the risks and implementing these protective measures, you can minimize your exposure to EMF radiation and safeguard your health.
0 notes
Text
Automatic Weather Station

Inbuilt 4-16 channel data logging system integrated with sensors for storing and alerting facility.
Remote Communication – 4G/GSM/GPRS / WiFi Facility, Ethernet, Wireless Router, optional Satellite interface available (Remote Communication)
In House Research & Development Team for customization , developing solutions , and new sensor integration.
Personalized Cloud Dashboard for Data analysis , graphical comparisons , report preparation and editing sampling rates.
Useful in Agricultural Universities, Research Institutes, Meteorological departments and many reputed organizations
Product Description
AdvanceTech India is proud to introduce a new generation of Automatic weather station with wireless technology. Our weather station aredesigned especially for recording environmental conditions with solar power alerts and storage recordings. Automatic weather station is an all in one Solution that records multiple weather parameters , analyses the data as per incoming formats , stores in memory , transfers via multiple ways wired/wirelessly as well as alert end user based on threshold application.
Inbuilt data logger, cloud dashboard for analysis , local SD card / USB storage facility.
We have complete in house Research and Development team for the same and prepare customized solutions.
We aim to provide best solution and till date have supplied at least 800 weather stations PAN india in both private and government entities .
Some of the prime environmental factors monitored by us our – Temperature , Humidity , Wind Speed , Wind direction , Rainfall , Snowfall , Solar Radiation , PAN evaporation , Leaf wetness , Soil Parameters etc.
0 notes
Text
The Technology Behind Your Connected Devices: Exploring the Basics of IoT Connectivity
In today's interconnected world, the Internet of Things (IoT) has revolutionized the way we interact with our devices, from smartphones and wearables to smart home appliances and industrial machinery. Behind the scenes, a complex web of technologies enables these devices to connect to the internet and perform their functions seamlessly. In this article, we will dive into the basics of IoT connectivity, unraveling the underlying technologies that power our connected devices.
At its core, IoT connectivity enables devices to gather, transmit, and receive data, enabling real-time monitoring, control, and automation. The process involves three key components: the IoT device itself, a communication network, and a cloud-based infrastructure for data processing and storage.
Let's start by understanding how IoT devices connect to the internet. IoT devices come in various forms, ranging from simple sensors to sophisticated machinery, each serving a specific purpose. These devices are equipped with embedded sensors, processors, and communication modules that enable them to collect and transmit data.
To establish a connection, IoT devices utilize various wireless communication technologies, including Wi-Fi, Bluetooth, cellular networks (3G, 4G, or 5G), Zigbee, LoRaWAN, or satellite communications. The choice of connectivity depends on factors such as range, power consumption, data rate, and cost. For instance, Wi-Fi is commonly used for devices within close proximity to a router, while cellular networks provide broader coverage for devices in remote locations.
Once connected, IoT devices transmit data to the cloud or a central server for processing and storage. This is where the role of a communication network comes into play. The data generated by IoT devices is transmitted over the internet through a network infrastructure that ensures reliable and secure communication.
Cloud-based IoT platforms serve as the backbone of the IoT ecosystem, providing the infrastructure and services necessary to process, analyze, and store the vast amount of data generated by connected devices. These platforms offer a range of functionalities, including data ingestion, real-time analytics, device management, and integration with other systems or applications.
To transmit data securely, IoT devices often employ encryption protocols such as Transport Layer Security (TLS) or Secure Shell (SSH) to protect sensitive information during transmission. Data encryption ensures that the information exchanged between the device and the cloud is secure and cannot be intercepted or tampered with.
Once the data reaches the cloud, it undergoes processing and analysis to extract meaningful insights. This is where cloud-based services such as data analytics, machine learning, and artificial intelligence (AI) come into play. These technologies enable businesses to make data-driven decisions, identify patterns, detect anomalies, and automate processes based on the collected data.
In addition to data processing, the cloud-based infrastructure also provides storage capabilities for the vast amounts of data generated by IoT devices. Cloud storage offers scalability, flexibility, and accessibility, allowing businesses to store and retrieve data as needed. Data can be stored in various formats, including structured data (relational databases), unstructured data (file storage), or semi-structured data (NoSQL databases), depending on the requirements of the application or use case.
To manage and control IoT devices, businesses often leverage device management platforms or tools. These platforms enable businesses to remotely monitor and control their devices, perform software updates, manage security protocols, and troubleshoot issues. Device management platforms provide a centralized interface to efficiently handle a large number of devices, ensuring their proper functioning and optimal performance.
The communication between IoT devices and the cloud infrastructure is a two-way process. In addition to transmitting data from the device to the cloud, IoT devices can also receive commands or instructions from the cloud, enabling remote control and automation. This bidirectional communication allows businesses to remotely configure device settings, update firmware, or trigger specific actions based on the data and insights received from the cloud.
In summary, the technology behind IoT connectivity involves the seamless integration of IoT devices, communication networks, and cloud-based infrastructure. IoT devices use wireless communication technologies to connect to the internet and transmit data to the cloud. The data is then processed, analyzed, and stored in the cloud, utilizing services such as data analytics and machine learning. Cloud storage offers scalability and flexibility for storing vast amounts of data generated by IoT devices. Device management platforms enable businesses to remotely monitor and control their devices, ensuring optimal performance. The bidirectional communication between IoT devices and the cloud allows for remote control and automation.
Understanding the basics of IoT connectivity provides us with insights into the incredible potential of connected devices. From smart homes and cities to industrial automation and healthcare, the IoT is transforming industries and improving our daily lives. As technology continues to advance, the interconnectivity of devices will only grow stronger, opening up new possibilities for innovation and efficiency.
So, the next time you interact with your connected devices, whether it's adjusting your home's thermostat, receiving real-time health data from a wearable device, or remotely controlling industrial machinery, take a moment to appreciate the underlying technologies that make it all possible. The world of IoT connectivity is vast and constantly evolving, and it holds the key to a smarter, more connected future.
IoT connectivity brings together devices, networks, and cloud infrastructure to enable seamless data transmission, processing, and control. It empowers businesses and individuals to harness the power of data and drive innovation across various sectors. As we continue to embrace the possibilities of the IoT, understanding the basics of IoT connectivity equips us with the knowledge to navigate and leverage this transformative technology.
So, embrace the connected world and explore the endless possibilities that IoT connectivity has to offer. With each interaction, you'll be experiencing the remarkable fusion of technology and connectivity that is shaping the future of our digital landscape. Get ready to unlock the full potential of your connected devices and embark on a journey towards a smarter, more connected future.
0 notes
Text
Telecom Cloud Market: Global Analysis, Opportunities And Forecast To 2032
As per a recent research report, Telecom Cloud Market to surpass USD 134 bn by 2032.
According to the report, the market is driven by rising adoption of cloud computing, expansion of 5G, and much more. The shift toward cloud computing in the telecommunications sector has revolutionized the way services are delivered and managed. Telecom operators are leveraging the cloud to enhance scalability, reduce costs, and improve operational efficiency. Additionally, the rapid expansion of 5G networks and the Internet of Things (IoT) has generated a massive amount of data that needs to be stored, processed, and analyzed, creating a demand for robust cloud infrastructure. The growing popularity of Software-as-a-Service (SaaS) and virtualized network functions are propelling the telecom cloud market forward, offering flexibility and agility to service providers.
Request for Sample Copy report @ https://www.gminsights.com/request-sample/detail/6066
In terms of application, the industry is segmented into software-defined networking, network function virtualization, content delivery networks, and others. The telecom cloud market from software-defined networking sector is projected to expand notably through 2032. SDN separates the network's control plane from the underlying hardware, allowing operators to centrally manage and orchestrate network resources. Telecom cloud provides the scalable and flexible infrastructure needed to host SDN controllers and network functions. By utilizing the cloud, operators can dynamically allocate resources, optimize traffic flow, and rapidly deploy network services. Telecom cloud enables the virtualization of network functions, such as routers and switches, allowing for efficient resource utilization and cost savings. SDN, coupled with telecom cloud, empowers operators with enhanced network agility, automation, and scalability, paving the way for future innovations in the telecommunications industry.
Based on component, the industry is divided into service and solution. The telecom cloud market from the solution segment is expected to witness substantial growth till 2032, as these solutions are tailored specifically to the unique needs of telecom operators. One of the key benefits of telecom cloud solution is the ability to virtualize network functions, allowing operators to scale and deploy services more efficiently. These solutions also offer centralized management and automation capabilities, enabling operators to streamline their operations and reduce costs. With telecom cloud solutions, operators can leverage the power of cloud computing to enhance their networks, improve customer experience, and drive innovation in the industry.
Request for customization this report @ https://www.gminsights.com/roc/6066
APAC telecom cloud market has experienced significant growth in recent years. The expanding telecommunications industry, coupled with the increasing adoption of cloud computing, has driven this growth. Factors such as the rapid proliferation of smartphones, the growth of 4G and 5G networks, and the rising demand for digital services are fueling the Industry growth. Additionally, governments in the region are promoting initiatives to enhance connectivity and digital infrastructure, further accelerating the adoption of telecom cloud solutions. With a vast population and evolving consumer preferences, APAC telecom cloud industry presents immense opportunities for service providers and technology vendors alike.
Partial chapters of report table of contents (TOC):
Chapter 2 Executive Summary
2.1 Telecom cloud market 360º synopsis, 2018 - 2032
2.2 Business trends
2.2.1 Total Addressable Market (TAM)
2.3 Regional trends
2.4 Component trends
2.5 Deployment model trends
2.6 Service model trends
2.7 Application trends
2.8 Organization size trends
Chapter 3 Telecom Cloud Market Insights
3.1 Impact on COVID-19
3.2 Russia-Ukraine war impact
3.3 Industry ecosystem analysis
3.4 Vendor matrix
3.5 Profit margin analysis
3.6 Technology & innovation landscape
3.7 Patent analysis
3.8 Key news and initiatives
3.8.1 Partnership/collaboration
3.8.2 Merger/Acquisition
3.8.3 Investment
3.8.4 Product launch and innovation
3.9 Regulatory landscape
3.10 Impact forces
3.10.1 Growth drivers
3.10.1.1 Increasing data traffic and demand for high-speed connectivity
3.10.1.2 Rising adoption of 5G networks
3.10.1.3 Propelling demand for operational efficient solutions
3.10.1.4 SMEs inclined toward cost-efficient cloud services
3.10.1.5 Government initiatives to support digitalization
3.10.2 Industry pitfalls & challenges
3.10.2.1 Security and privacy risks
3.10.2.2 Network reliability and service disruptions
3.11 Growth potential analysis
3.12 Porter’s analysis
3.13 PESTEL analysis
About Global Market Insights:
Global Market Insights, Inc., headquartered in Delaware, U.S., is a global market research and consulting service provider; offering syndicated and custom research reports along with growth consulting services. Our business intelligence and industry research reports offer clients with penetrative insights and actionable market data specially designed and presented to aid strategic decision making. These exhaustive reports are designed via a proprietary research methodology and are available for key industries such as chemicals, advanced materials, technology, renewable energy and biotechnology.
Contact us:
Aashit Tiwari Corporate Sales, USA Global Market Insights Inc. Toll Free: +1-888-689-0688 USA: +1-302-846-7766 Europe: +44-742-759-8484 APAC: +65-3129-7718 Email: [email protected]
0 notes
Photo

4G Router Backup - 4G Router Store
4G routers will keep your business up also running if the broadband falls and 4G Router Backup to your primary Internet feed.
#4G Router Backup#4G router#4G antenna#Fixed IP Sim Card#M2M 4G router#Outdoor 4G antenna#CCTV 4G Router#4G Internet uk#4G Signal Analyser#best 4g router uk#4G Router Store
0 notes
Photo

COFE 4G+Wifi Device 👌
Stable & Fast 4G Wi-Fi Experience 💯 Visit us : www.kidindia.in
#cofe#4g#wifi router#modem#wifidevice#hardwareshop#hardware stores#it products#hardware products#fast#stable#wifi
0 notes
Link
Intercel is the Australian leading manufacturer of industrial 4GX modem Routers, We have some great Quality industrial 4Gx modem and routers Solutions.
1 note
·
View note
Text
What You Should Try To Find In A 4g Router

4G LTE networks have arrived a very long way considering that the 3G days. It is actually certainly not rare to possess a 4G relationship that may give throughput of 10s of Mbps (Megabits every secondly) downlink and numerous Mbps uplink. Even though these numbers are actually considerably less than what academic 4G assured, it is actually still very remarkable, particularly considering that you might not manage to get similar prices from a wired broadband link depending on your area.
We are going to appear in to some of the use situations that muama ryoko could be an excellent solution for. Our team will likewise highlight some of the possible drawbacks of a 4G router for certain applications. On the whole, our team wish to plunge deep into the elements that matter when opting for a 4G router. Allow's start.
Initially, let's begin along with some realities regarding 4G networks that may not be apparent quickly. Despite the fact that there has actually been actually impressive enhancements in the price of data transfer in 4G networks over the last few years, you may still anticipate to pay for $5 or even more per GIGABYTES of information along with 4G LTE networks. There are some "limitless" service options, however if you dig deeper right into the particulars, in a majority of cases, they are certainly not truly infinite as they will strangle down your transmission capacity after a specific volume of use. With that said in mind it is a good rule of thumb to program in between $5 to $10 every GB bandwidth cost.
4G systems are actually inherently erratic. This indicates that despite the fact that in perfect sites, settings as well as opportunities, the efficiency of a 4G modem may be awesome, there is actually no promise of obtaining that lead every time. In reality, as a result of fast-fading, slow-fading, network congestion as well as a lot of different factors, your functionality may differ significantly within only a few milliseconds, or perhaps millimeters. It is safe to presume that 4G networks are actually, and are going to stay uncertain.
The carriers you make use of create a distinction. Strangely sufficient, there is actually no crystal clear victor among providers, as they typically master different aspects. Some companies have the most extensive coverage region, some carriers have the best urban performance, some are actually a lot better in backwoods etc. You should often assume efficiency variation located on carriers. It is certainly not unusual to see one service provider outperform yet another in a certain place at a specific time, while the adhering to time the roles may turn around. It is beneficial for you to have a look at muama ryoko reviews to recognize the particulars of this item.
Factors as well as attributes you ought to consider in 4g wifi router.
What is your usage case?
This is maybe the absolute most significant factor in calculating the features you need to have to seek in a 4G router: just how will you be using the 4G router? Is this for a store as a back up on an existing primary wired link (think of the back up Internet for a POS sign up)? Is actually the 4G router heading to be actually utilized in a specialty lorry (visualize a police wagon with security electronic cameras)? Or will you be making use of the 4g wifi router as a different residential Internet accessibility?
Perform you possess a commercial usage instance for the 4G router?
In the event that your target is to make use of a 4G router in an industrial request, like a backup connectivity for a branch workplace, or as a main connectivity for a temporary or even mobile workplace, at that point your 4G router requires to assist some state-of-the-art features consisting of firewall software, broadband connecting as well as use powered marketing. Preferably, you wish to have the 4G router capacity within your primary router, including an SD-WAN router along with Broadband Bonding capacities. In this particular system your wired product line can failover on a bound set of 4G connections. Bonding pair of or even additional 4G wireless hookups will definitely offer certainly not just a bigger transmission capacity and also much higher throughput however will definitely also deliver self-healing capacities for the traffic reviewing the 4G network.
Will definitely your 4G Wifi router be your failover or even major connection.
If the 4G router is mosting likely to be actually lugging your website traffic all the time, i.e. will definitely be your key ways of Internet connectivity for your workplace, specialized vehicle or even similar, then we highly encourage 4G hubs along with greater than two cell 4G connections. Returning to our road analogy, this are going to suggest a bigger ability motorway to carry additional vehicles with ease. For failover-only cases, where the 4G relationships need to keep the connectivity to life for only a restricted opportunity, having just pair of hookups could be sufficient. Our company still caution against a single 4G failover for the adhering to main reason.
1 note
·
View note
Text
LESSON 1: INTRODUCTION TO ICT
ICT– Information and Communication-
It deals with the use of different communication technologies such as mobile phones, telephone, Internet to locate, save, send and edit information
Is a study of computers as data processing tools. It introduces students to the fundamental of using computer systems in an internet environment.
ICT in the Philippines
Philippines is dub as the ‘’ICT Hub of Asia” because of huge growth of ICT-related jobs, one of which is BPO, Business Process Outsourcing, or call centers.
ICT Department in the Philippines is responsible for the planning, development and promotion of the country’s information and communications technology (ICT) agenda in support of national development.
Computer– an electronic device for storing and processing data, typically in binary form, according to instructions given to it in a variable program. Internet– is the global system of interconnected computer networks that use the internet protocol suite (TCIP/IP) to link billions of devices worldwide.
Means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers.
Sometimes called simply ‘’the Net’’, is a worldwide system of computer networks- a network of networks in which the users at any one computer can get information from any other computer.
ADVERTISEMENTREPORT THIS AD
World Wide Web
An information system on the internet that allows documents to be connected to other documents by hypertext links, enabling the user to search for information by moving from one document to another.
Is an information space where documents and other web resources are identified by URLs, interlinked by hypertext links, and can be accessed via the Internet.
Invented by Tim-Berners Lee
Web Pages
Web page is a hypertext document connected to the World Wide Web. It is a document that is suitable for the World Wide Web.
The different online platforms of World Wide Web:
Web 1.0 – refers to the first stage in the World Wide Web, which was entirely made up of the Web pages connected by hyperlinks.
Web 2.0 – is the evolution of Web 1.0 by adding dynamic pages. The user is able to see a website differently than others.
– Allows users to interact with the page; instead of just reading the page, the user may be able to comment or create user account.
Web 3.0 – this platform is all about semantic web.
– Aims to have machines (or servers) understand the user’s preferences to be able to deliver web content.
Static Web Page- is known as a flat page or stationary age in the sense that the page is ‘’as is’’ and cannot be manipulated by the user. The content is also the same for all users that is referred to as Web 1.0
Dynamic Web Pages– web 2.0 is the evolution of web 1.0 by adding dynamic web pages. The user is able to see website differently than others e.g. social networking sites, wikis, video sharing sites.
FEATURES OF WEB 2.0
Folksonomy- allows user to categorize and classify information using freely chosen keywords e.g. tagging by FB, Twitter, use tags that start with the sign #, referred to as hashtag.
Rich User Experience – content is dynamic and is responsive to user’s input
User Participation- The owner of the website is not the only one who is able to put content. Others are able to place a content of their own by means of comments, reviews and evaluation e.g. Lazada, Amazon.
Long Tail– services that are offered on demand rather than on a one-time purchase. This is synonymous to subscribing to a data plan that charges you for the amount of time you spent in the internet.
Software as a services- users will be subscribe to a software only when needed rather than purchasing them e.g. Google docs used to create and edit word processing and spread sheet.
Mass Participation– diverse information sharing through universal web access. Web 2.0’s content is based on people from various cultures.
TRENDS IN ICT
Convergence– is the synergy of technological advancements to work on a similar goal or task. For example, besides using your personal computer to create word documents, you can now use your smartphone. 2. Social Media– is a website, application, or online channel that enables web users web users to create , co-create, discuss modify, and exchange user generated content.
Six types of Social Media:
a)Social Networks – These are sites that allows you to connect with other people with the same interests or background. Once the user creates his/her account, he/she can set up a profile, add people, share content, etc
Example: Facebook and Google+
b)Bookmarking Sites – Sites that allow you to store and manage links to various website and resources. Most of the sites allow you to create a tag to others.
Stumble Upon, Pinterest
c) Social News – Sites that allow users to post their own news items or links to other news sources. The users can also comment on the post and comments may also be rank.
Ex. Reddit and Digg
d) Media Sharing – sites that allow you to upload and share media content like images, music and video.
Ex. Flickr, YouTube and Instagram e) Microblogging – focus on short updates from the user. Those that subscribed to the user will be able to receive these updates. Ex. Twitter and Plurk
f) Blogs and Forums – allow user to post their content. Other users are able to comment on the said topic. Ex. Blogger, WordPress and Tumblr
Mobile Technologies– The popularity of smartphones and tablets has taken a major rise over the years. This is largely because of the devices capability to do the tasks that were originally found in PCs. Several of these devices are capable of using a high-speed internet. Today the latest model devices use 4G Networking (LTE), which is currently the fastest.
MOBILE OS
iOS – use in apple devices such as iPhone and iPad
Android – an open source OS developed by Google. Being open source means mobile phone companies use this OS for free.
Blackberry OS – use in blackberry devices
Windows phone OS – A closed source and proprietary operating system developed by Microsoft.
Symbian – the original smartphone OS. Used by Nokia devices
WebOS- originally used in smartphone; now in smart TVs.
Windows Mobile – developed by Microsoft for smartphones and pocket PCs
Assistive Media– is a non- profit service designed to help people who have visual and reading impairments. A database of audio recordings is used to read to the user.
e.g. Yahoo!, Gmail, HotmailCloud computing-distributed computing on internet or delivery of computing service over the internet.
-Instead of running an e-mail program on your computer, you log in to a Web
e-mail account remotely. The software and storage for your account doesn’t exist
on your computer – it’s on the service’s computer cloud.
It has three components
Client computers – clients are the device that the end user interact with cloud.
Distributed Servers – Often servers are in geographically different places, but server acts as if they are working next to each other.
Datacenters – It is collection of servers where application is placed and is accessed via Internet.
TYPES OF CLOUDS
PUBLIC CLOUD allows systems and services to be easily accessible to the general public. Public cloud may be less secured because of its openness, e.g. e-mail
PRIVATE CLOUD allows systems and services to be accessible within an organization. It offers increased security because of its private nature.
COMMUNITY CLOUD allows systems and services to be accessible by group of organizations.
HYBRID CLOUD is a mixture of public and private cloud. However, the critical activities are performed using private cloud while the non-critical activities are performed using public cloud.
1 note
·
View note
Text
PORTFOLIO IN EMPOWERMENT TECHNOLOGY
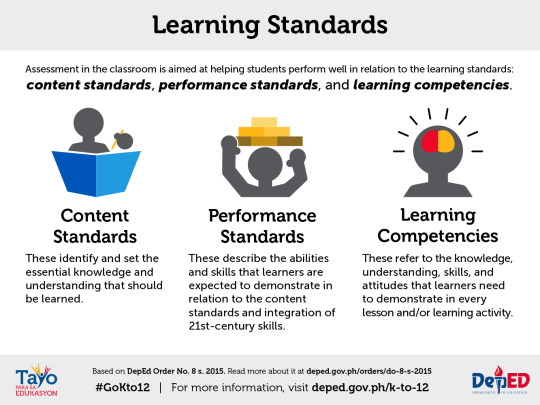
CHAPTER 1 LESSON 1: INFORMATION AND COMMUNICATIONS TECHNOLOGY - Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. CONTENT STANDARD
- The learners demonstrate an understanding of ICT in the context of global communication for specific professional track.
Performance Standards
- The learners shall be able to: at the end of the 2-week period independently compose an insightful reflection paper on the nature of ICT in the context of their lives, society, and professional tracks (Arts, Tech Vocational, Sports and Academic)
Most essential learning competencies
The learners should be able to:
1. Compare and contrast the nuances of varied online platforms, sites, and content to best achieve specific class objectives or address situational challenges.
2. Apply online safety, security, ethics, and etiquette standards and practice in the use of ICTs as it would relate to their professional tracks. 3. Use the internet as a tool for credible research and information gathering to best achieve specific class objectives or address situational.
1.1 INFORMATION AND COMMUNICATION TECHNOLOGY

- ICT is the technology required for information processing, in particular, the use of the electronic computers, communication devices and software applications to convert, store, protect, process, transmit and retrieve information from anywhere, anytime.
- Information refers to the knowledge obtained from reading, investigation, study or research. The tools to transmit information are the telephone, television and radio. Information is knowledge and helps us to fulfill our daily tasks. - Communication is an act of transmitting messages. It is a process whereby information was exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
- ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (Wifi), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks. EMERGING TECHNOLOGIES

- Artificial Intelligence (AI) - is the ability of a digital computer or computer controlled robot to perform tasks commonly associated with intelligent beings. The term is frequently applied to the project of developing systems endowed with the intellectual processes characteristics of humans, such as the ability to reason, discover meaning, generalize or learn from past experience. ROBOTICS

- Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. BIOMETRICS

- Are a way to measure a person’s physical characteristics to verify their identity. These can include physiological traits, such as fingerprints and eyes, or behavioral characteristics, such as the unique way you’d complete a security-authentication puzzle. QUANTUM CRYPTOGRAPHY

- Also called quantum encryption, applies principles of quantum mechanics to encrypt messages in a way that it is never read by anyone outside of the intended recipient. COMPUTER ASSISTED TRANSLATION

- Involves the use of software programs to translate both verbal and written texts. Also known as machine-assisted or machine aided translation. 3D IMAGING AND HOLOGRAPHY

- Is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. VIRTUAL REALITY

- Refers to the computer generated simulation in which a person can interact within an artificial 3D environment using special electronic devices that can be similar to or completely different from the real world. ONLINE SAFETY

- Is the knowledge of maximizing the user’s personal safety and security and risk to private information, and self-protection from computer crime in general. 1. Know the scams - Learn about different kinds of scams and what you can do to avoid them.

2. Think before you click - Think twice, thrice and zillion time before click any link or buttons.

3. Safety Peruse - These sites may have an Address that’s very similar to a legitimate site, but the page can have misspelling, Bad Grammar, or low resolution Images.

4. Shop Safety - Don’t shop on a site unless it has “https” and a padlock icon on the left or right in the URL.

5. Kick-butt passwords - Use an Extremely uncrackable password One like “9&4thkel965#”.
6. Protect your info’s - Keep your guard up, Back up all your data on your computer, smartphone and tablet, theft or a cash.

7. Watch your Wi-Fi Connectivity - Protect your network by changing your router’s setting and making sure that you have the connection password protected.

8. Install a Firewall - A firewall is a grate line of defense against cyber attracts.
9. Keep up to date - The best security updates automatically to protect your computer. - Use the manufacturer’s latest security patches to make regular updates and make that you have the software set to do routine scam.

10. Use your Noggin - Use your common sense while surfing the web.

COMMON ISSUES AND CRIMES IN THE INTERNET - CYBERBULLYING - HACKING - IDENTITY THEFT - PLAGIARISM - COPYRIGHT ISSUES CYBERBULLYING - Is a form of bullying or harassment using electronic means. Cyberbullying and Cyber Harassment are also known as online bullying. - Cyberbullying is when someone, typically teens, bully or harass others on the internet, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims’ personal information, or pejorative labels. THE ANTI-BULLYING ACT OF 2013 ( RA 10627 )
(Sec. 2, RA 10627) These acts are collectively “called cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1 RA 10627. Implementing Rules). THE REVISED PENAL CODE AND THE CYBERCRIME PREVENTION ACT. - One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art, 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175) Likers or shares of a post cannot be held liable under this law. - Slander may also be applicable to one who, in heat of anger, utters statements that are highly defamatory in character. (Art 358, RPC) Intriguing Against Honour may also find applicability when the principal purpose is to blemish the honour or reputation of a person. Hence, a blind ite is not as actionable as a named-post in social media. HACKING

- Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system. - Hacking can also refer to non-malicious activities, usually involving unusual or improvised alterations to equipment or processes.
IDENTITY THEFT

- Also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else. TYPES AND EXAMPLES OF IDENTITY THEFT 1. True-name identity theft means the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service or open a new checking account in order to obtain blank checks. 2. Account-takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. PLAGIARISM

- Is an act of fraud. It involves both stealing someone else's work and lying about it afterward. The following are considered plagiarism - turning in someone else's work as your own - copying words or ideas from someone else without giving credit - failing to put a quotation in quotation marks - giving incorrect information about the source of a quotation - changing words but copying the sentence structure of a source without giving credit - copying so many words or ideas from a source that it makes up the majority of your work, whether you give credit or not (see our section on "fair use" rules) Republic Act No. 8293 [An Act Prescribing the Intellectual Property Code and Establishing the Intellectual Property Office, Providing for Its Powers and Functions, and for Other Purposes]otherwise known as the Intellectual Property Code of the Philippines. Intellectual property rights under the I. P. Code: The intellectual property rights under the Intellectual Property Code are as follows: 1. Copyright and related rights; 2. Trademarks and service marks; 3. Geographic indications; 4. Industrial designs; 5. Patents; 6. Layout designs [topographies] of integrated circuits; and 7. Protection of undisclosed information. The scheme of penalties for infringement has also been changed. From the previous fine of Php200 to Php2,000 and/or imprisonment of 1 year, the current range of penalties are as follows: - For first offenders - fine of PhP50,000 to PhP150,000 and/or imprisonment of 1 to 3 years - For second offenders - fine of PhP150,000 to PhP500,000 and/or imprisonment of 3 to 6 years - For third and subsequent offenders - fine of PhP500,000 to PhP1.5 Million and/or imprisonment of 6 to 9 years. - In case of insolvency, the offender shall furthermore suffer subsidiary imprisonment. NETIQUETTE - Is a combination of the word net and etiquette.It focuses on the acceptable behavior of a person while using the internet resource. - It focuses on the acceptable behavior of a person while using the internet resource. The Core Rules of Netiquette Rule 1. Remember the human. - Never forget that the person reading your mail or posting is, indeed, a person, with feelings that can be hurt. - Corollary 1 to Rule #1: It's not nice to hurt other people's feelings. - Corollary 2: Never mail or post anything you wouldn't say to your reader's face. - Corollary 3: Notify your readers when flaming. Rule 2. Adhere to the same standards of behavior online that you follow in real life. Corollary 1: Be Ethical Corollary Corollary 2: Breaking the law is bad Netiquette. Rule 3. Know where you are in cyberspace. Corollary 1: Netiquette varies from domain to domain. Corollary 2: Lurk before you leap. Rule 4. Respect other people's time and bandwidth. Corollary 1: It's OK to think that what you're doing at the moment is the most important thing in the universe, but don't expect anyone else to agree with you Corollary 2: Post messages to the appropriate discussion group.Corollary 3: Try not to ask stupid questions on discussion groups Corollary 4: Read the FAQ (Frequently Asked Questions) document Corollary 5: When appropriate, use private email instead of posting to the group Corollary 6: Don't post subscribe, unsubscribe, or FAQ requests Corollary 7: Don't waste expert readers' time by posting basic information Corollary 8: If you disagree with the premise of a discussion group, don't waste the time and bandwidth of the members by telling them how stupid they are.Just stay away Corollary 9: Conserve bandwidth when you retrieve information from a host or server. Rule 5. Make yourself look good online. Corollary 1: Check grammar and spelling before you post Corollary 2: Know what you're talking about and make sense Corollary 3: Don't post flame-bait Rule 6. Share expert knowledge. Corollary 1: Offer answers and help to people who ask questions on discussion groups Corollary 2: If you've received email answers to a posted question, summarize them and post the summary to the discussion group. Rule 7. Help keep flame wars under control. Corollary 1: Don't respond to flame-bait Corollary 2: Don't post spelling or grammar flames Corollary 3: If you've posted flame-bait or perpetuated a flame war, apologize Rule 8. Respect other people's privacy. - Don't read other people's private email. Rule 9. Don't abuse your power. - The more power you have, the more important it is that you use it well Rule 10. Be forgiving of other people's mistakes. CONTEXTUALIZED ONLINE SEARCH AND RESEARCH SKILLS

- Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. Interactive searches became possible in the 1980s with the advent of faster databases and smart terminals. Advantages and Disadvantages Advantages: - Ability to obtain a large sample, which increases statistical power - Data is automatically coded so no data entry errors - Reduced cost of conducting research Disadvantages: Online is not totally secure and theft is one of the numerous danger it poses, researchers personal information is at risk of being access by rogue persons. - Some of the materials on the internet have not been evaluated by experts or thoroughly screened - Lack of accreditation and low quality
RESEARCH SKILLS “Research” sometimes just means finding out information about a topic.You can certainly develop advanced information retrieval skills in Working with Sources. However, in specific understandings of “research” carry a lot of weight. The classic definition is that “research” leads to an original contribution to knowledge in a particular field of inquiry by defining an important question or problem and then answering or solving it in a systematic way. - So you will need to read on to develop a relevant understanding of what research means in your subject. - Research skills can be anything from looking at competitors and seeing what they do well to producing a written report on how your department could work better. Doing research in the world of work is all about stepping back from your day-to-day work and looking at ways you can improve. Important aspects of research: - Research design covers the key issues in developing a successful research project. - Research methods takes you to resources on essential techniques for carrying out convincing research. - Working with data will provide resources on the use of statistics and other numerical skills in research. Improving Your Research Skills Online 1. Know your sources. Make sure to find the most reliable information which can be found in multiple sources or, better, to have the original source. 2. Use your web browser properly. Know the capabilities of your preferred browser to help make your search faster and easier. 3. Organize your bookmarks. It is to organize the links you have marked. 4. Learn to use advanced search engines. Practice using advanced search techniques which are available in Google. 5. Follow the web. Follow the web information in the web. Just make sure to read and be critical in every link you click. SIX STRATEGIES THAT CAN HELP ONLINE STUDENTS PRODUCE STRONGER RESEARCH. 1. Contact a librarian before getting stuck sifting through piles of online information. 2. Consider that when in doubt, it's wiser to over-cite sources than risk plagiarism. 3. Use Google and other reliable resources at the beginning of a research process, not the end. 4. Don't think that the Web is your only source of information. 5. Understand the professor's expectations for citation format. 6. Understand why professors still assign research projects. Some examples of research skills that you may have include: 1. Report writing. 2. Analyzing lots of information from different sources. 3. Finding information off the internet. 4. Critical thinking. CHAPTER 2 APPLIED PRODUCTIVITY TOOLS Productivity Tools - It is a tools that can be a freeware or shareware. Freeware - is copyrighted, which can be used for free and for an unlimited time. Shareware - is a commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use. Advanced Techniques Using Microsoft Word Microsoft Office Word

- One of the software of Microsoft Office 2013 suite. - Offers a set of tools that is compared to its previous versions. - Along with its new features are advanced techniques including hyperlinks, macros and mail merge. Hyperlink
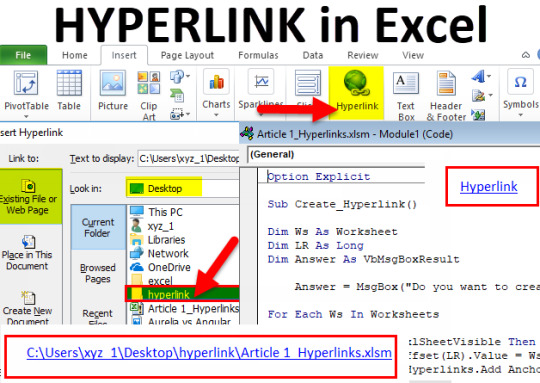
- A link that will direct you to another page or part of the same document. Creating a Hyperlink to an Existing Document - Suppose you are to link a part of your document to an existing document. - Click your mouse on the location in the document where you want to insert the hyperlink. - On the Insert Tab, click the Hyperlink button on the Links group. - On the Insert Hyperlink dialog box, click Existing File or Web Page and then select the File name where the source file is located and then hyperlink will be created on your document. - Press Ctrl+ click on the Hyperlink to open the linked file. Mail Merge
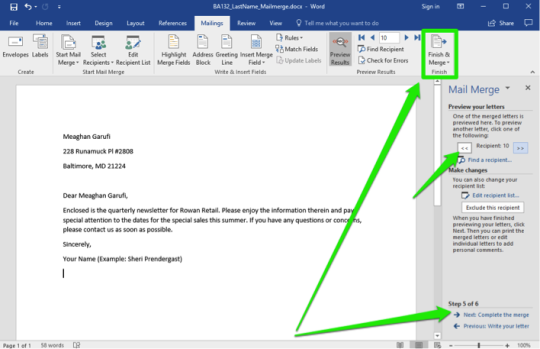
- Is a useful tool that allows you to quickly produce and send information, newsletter, resumes, or brochures to many people. Creating a Mail Merge 1. Open the word document that you want to Mail Merge. 2. On the Ribbon, click the Mailings tab, go to the Start Mail Merge group and click Start Mail Merge and select Step by Step Mail Merge Wizard. 3. The task pane will show the Mail Merge steps 1 to 6. PowerPoint

- It allows you to create slide show presentations wherein you can format the texts and images, adding also animations and other multimedia components interactively. Excel

- One of the applications created by Microsoft, used to simulate a paper worksheet.
- It is composed of cells that are represented in rows and columns design to perform basic arithmetic operations. - Widely used in accounting and financial applications, as well as statistics and engineering calculations. The following are the common Excel Functions: = SUM – Calculates the sum of the values of a range of cells = AVERAGE – Calculates the arithmetic mean of a range of cells = MAX - Gives the maximum value in a range of cells = MIN - Gives the minimum value in a range of cells = COUNT - Counts the number of cells in a range of cells BENIFITS OF ONLINE SOFTWARE Convenience - The applications should be intuitive and easy to use to ensure everyone can use them without spending a lot of time learning how. Scalability - The applications should be able to be used in all areas of your business and also work effectively no matter how much demand there is to use them or how much your business grows. Safety - All the applications should be safe to use with all existing systems and should have the ability to fully integrate with all other software and not inhibit the workers ability to do their job. Sustainability - All consumer-based software should be flexible and adaptable to have the ability to last for up to 10 years, but they must be able to expand functionally with other developments in software and operating systems. PRINCIPLES OF GRAPHICS AND DESIGN BALANCE UNITY MOVEMENT REPITITION PROXIMITY CONTRAST WHITESPACE BALANCE

- Describes the placement of elements of equal weight on the page. MOVEMENT

- Describes the flow of elements on the page.
1 note
·
View note
Text
LESSON 1: INTRODUCTION TO ICT
ICT– Information and Communication-
It deals with the use of different communication technologies such as mobile phones, telephone, Internet to locate, save, send and edit information
Is a study of computers as data processing tools. It introduces students to the fundamental of using computer systems in an internet environment.
ICT in the Philippines
Philippines is dub as the ‘’ICT Hub of Asia” because of huge growth of ICT-related jobs, one of which is BPO, Business Process Outsourcing, or call centers.
ICT Department in the Philippines is responsible for the planning, development and promotion of the country’s information and communications technology (ICT) agenda in support of national development.
Computer– an electronic device for storing and processing data, typically in binary form, according to instructions given to it in a variable program. Internet– is the global system of interconnected computer networks that use the internet protocol suite (TCIP/IP) to link billions of devices worldwide.
Means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers.
Sometimes called simply ‘’the Net’’, is a worldwide system of computer networks- a network of networks in which the users at any one computer can get information from any other computer.
World Wide Web
An information system on the internet that allows documents to be connected to other documents by hypertext links, enabling the user to search for information by moving from one document to another.
Is an information space where documents and other web resources are identified by URLs, interlinked by hypertext links, and can be accessed via the Internet.
Invented by Tim-Berners Lee
Web Pages
Web page is a hypertext document connected to the World Wide Web. It is a document that is suitable for the World Wide Web.
The different online platforms of World Wide Web:
Web 1.0 – refers to the first stage in the World Wide Web, which was entirely made up of the Web pages connected by hyperlinks.
Web 2.0 – is the evolution of Web 1.0 by adding dynamic pages. The user is able to see a website differently than others.
– Allows users to interact with the page; instead of just reading the page, the user may be able to comment or create user account.
Web 3.0 – this platform is all about semantic web.
– Aims to have machines (or servers) understand the user’s preferences to be able to deliver web content.
Static Web Page- is known as a flat page or stationary age in the sense that the page is ‘’as is’’ and cannot be manipulated by the user. The content is also the same for all users that is referred to as Web 1.0
Dynamic Web Pages– web 2.0 is the evolution of web 1.0 by adding dynamic web pages. The user is able to see website differently than others e.g. social networking sites, wikis, video sharing sites.
FEATURES OF WEB 2.0
Folksonomy- allows user to categorize and classify information using freely chosen keywords e.g. tagging by FB, Twitter, use tags that start with the sign #, referred to as hashtag.
Rich User Experience – content is dynamic and is responsive to user’s input
User Participation- The owner of the website is not the only one who is able to put content. Others are able to place a content of their own by means of comments, reviews and evaluation e.g. Lazada, Amazon.
Long Tail– services that are offered on demand rather than on a one-time purchase. This is synonymous to subscribing to a data plan that charges you for the amount of time you spent in the internet.
Software as a services- users will be subscribe to a software only when needed rather than purchasing them e.g. Google docs used to create and edit word processing and spread sheet.
Mass Participation– diverse information sharing through universal web access. Web 2.0’s content is based on people from various cultures.
TRENDS IN ICT
Convergence– is the synergy of technological advancements to work on a similar goal or task. For example, besides using your personal computer to create word documents, you can now use your smartphone. 2. Social Media– is a website, application, or online channel that enables web users web users to create , co-create, discuss modify, and exchange user generated content.
Six types of Social Media:
a)Social Networks – These are sites that allows you to connect with other people with the same interests or background. Once the user creates his/her account, he/she can set up a profile, add people, share content, etc
Example: Facebook and Google+
b)Bookmarking Sites – Sites that allow you to store and manage links to various website and resources. Most of the sites allow you to create a tag to others.
Stumble Upon, Pinterest
c) Social News – Sites that allow users to post their own news items or links to other news sources. The users can also comment on the post and comments may also be rank.
Ex. Reddit and Digg
d) Media Sharing – sites that allow you to upload and share media content like images, music and video.
Ex. Flickr, YouTube and Instagram e) Microblogging – focus on short updates from the user. Those that subscribed to the user will be able to receive these updates. Ex. Twitter and Plurk
f) Blogs and Forums – allow user to post their content. Other users are able to comment on the said topic. Ex. Blogger, WordPress and Tumblr
Mobile Technologies– The popularity of smartphones and tablets has taken a major rise over the years. This is largely because of the devices capability to do the tasks that were originally found in PCs. Several of these devices are capable of using a high-speed internet. Today the latest model devices use 4G Networking (LTE), which is currently the fastest.
MOBILE OS
iOS – use in apple devices such as iPhone and iPad
Android – an open source OS developed by Google. Being open source means mobile phone companies use this OS for free.
Blackberry OS – use in blackberry devices
Windows phone OS – A closed source and proprietary operating system developed by Microsoft.
Symbian – the original smartphone OS. Used by Nokia devices
WebOS- originally used in smartphone; now in smart TVs.
Windows Mobile – developed by Microsoft for smartphones and pocket PCs
Assistive Media– is a non- profit service designed to help people who have visual and reading impairments. A database of audio recordings is used to read to the user.
e.g. Yahoo!, Gmail, HotmailCloud computing-distributed computing on internet or delivery of computing service over the internet.
-Instead of running an e-mail program on your computer, you log in to a Web
e-mail account remotely. The software and storage for your account doesn’t exist
on your computer – it’s on the service’s computer cloud.
It has three components
Client computers – clients are the device that the end user interact with cloud.
Distributed Servers – Often servers are in geographically different places, but server acts as if they are working next to each other.
Datacenters – It is collection of servers where application is placed and is accessed via Internet.
TYPES OF CLOUDS
PUBLIC CLOUD allows systems and services to be easily accessible to the general public. Public cloud may be less secured because of its openness, e.g. e-mail
PRIVATE CLOUD allows systems and services to be accessible within an organization. It offers increased security because of its private nature.
COMMUNITY CLOUD allows systems and services to be accessible by group of organizations.
HYBRID CLOUD is a mixture of public and private cloud. However, the critical activities are performed using private cloud while the non-critical activities are performed using public cloud.
LESSON 2: ONLINE SAFETY, SECURITY AND RULES OF NETIQUETTE
INTERNET SAFETY- it refers to the online security or safety of people and their information when using internet. NETIQUETTE- is network etiquette, the do’s and don’ts of online communication.
TEN RULES OF NETIQUETTE
Rule No. 1: Remember the human
You need to remember that you are talking to a real person when you are online.
The internet brings people together who would otherwise never meet.
Remember this saying when sending an email: Would I say this to the person’s face.
Rule No. 2: Adhere to the same standards online that you follow in real life.
You need to behave the same way online that you do in real life.
You need to remember that you can get caught doing things you should not be doing online just like you can in real life.
You are still talking to a real person with feelings even though you can’t see them.
Rule no. 3: Know where you are in cyberspace.
Always take a look around when you enter a new domain when surfing the web.
Get a sense of what the discussion group is about before you join it.
Rule no. 4: Respect other people’s time and bandwidth.
Remember people have other things to do besides read your email. You are not the center of their world.
Keep your post and emails to minimum by saying what you want to say.
Remember everyone won’t answer your questions.
Rule no. 5: Make yourself look good online.
Be polite and pleasant to everyone.
Always check your spelling and grammar before posting.
· Know what you are talking about and make sense saying it.
Rule no. 6: Share expert knowledge
Ask questions online
Share what you know online.
Post the answers to your questions online because someone may have the same question you do.
Rule no. 7: Help keep flame wars under control
Netiquette does not forgive flaming.
Netiquette does however forbid people who are flaming to hurt discussion groups by putting the group down.
Rule no. 8: Respect other people’s privacy.
Do not read other people’s mail without their permission.
Going through other people’s things could cost you, your job or you could even go to jail.
Not respecting other people’s privacy is a bad netiquette.
Rule no. 9: Don’t abuse your power.
Do not take advantage of other people just because you have more knowledge or power than them.
Treat others as you would want them to treat you if the roles were reversed.
Rule no. 10: Be forgiving of other people’s mistake.
Do not point out mistakes to people online.
Remember that you were once the new kid on the block.
You still need to have a good manners even though you are online and cannot see the person face to face.
Internet security
Security Requirement Triad
ConfidentIality Data confidentiality Privacy
Integrity Data integerity System integrity
Availability
Threat ConsequenceThreat Action ( Attack)
Unauthorized Disclosure
A circumstance or event whereby an entity gains access to data for which the entity is not authorized.
Exposure: Sensitive data are directly released to an unauthorized entity.
Interception: An unauthorized entity directly accesses sensitive data traveling between authorized sources and destinations.
Inference: A threat action whereby an unauthorized entity indirectly accesses sensitive data by reasoning from characteristics or byproducts of communications.
Intrusion: an unauthorized entity gains access to sensitive data by circumventing a system’s security protections.
Disruption
A circumstances or even that interrupts or prevents the correct operation of system services and functions.
Deception
A circumstance or event that may result in an authorized entity receiving false data and believing it to be true.
Incapacitation: prevents or interrupts system operation by disabling a system component.
Corruption: Undesirably alters system operation by adversely modifying system functions or data.
Obstruction: A threat action that interrupts delivery of system services by hindering system operation.
Masquerade: An unauthorized entity gains access to a system or performs a malicious act by posing as an authorized entity.
Falsification: False data deceive an authorized entity.
Repudiation: An entity deceives another by falsely denying responsibility for an act.
Usurpation
A circumstances or event that results in control of system services or functions by an unauthorized entity.
Misappropriation: An entity assumes
unauthorized logical or physical control of a
system resource.
Misuse: Causes a system component to perform a function or service that is detrimental to system security.
Types of System Intruders
Masquerader
Hackers
Clandestine user
Parts of Virus
Infection mechanism
Trigger
PayloaD
Virus stages
Dormant phase Virus is idle.
Propagation phase Virus places an identical copy of itself into other programs or into certain system areas on t the disk.
Triggering phase Virus is activated to perform the function for which it was intended. Caused by a variety of system events
Execution phase Function is performed
Key Terms
Cyber crime- a crime committed or assisted through the use of the Internet.
Privacy Policy/Terms of Services (ToS) – tells the user how the website will handle its data.
Malware- stands for malicious software.
Virus- a malicious program designed to transfer from one computer to another in any means possible.
Worms– a malicious program designed to replicate itself and transfer from one file folder to another and also transfer to other computers.
Trojan-a malicious program designed that is disguised as a useful program but once downloaded or installed, leaves your PC unprotected and allows hacker to get your information.
Spyware– a program that runs in the background without you knowing it. It has the ability to monitor what you are currently doing and typing through key logging.
Adware- a program designed to send you advertisement, mostly pop-ups.
Spam– unwanted email mostly from bots or advertisers.
Phishing- acquires sensitive personal information like passwords and credits card details.
Pharming- a more complicated way of phishing where it exploits the DNS system.
Copyright- a part of law, wherein you have the rights to work, anyone who uses it w/o your consent is punishable by law.
Fair Use- means that an intellectual property may be used w/o consent as long as it is used in commentaries, criticism, parodies, research and etc.
Keyloggers- used to record the keystrokes done by user. This is done to steal passwords or any other sensitive information.
Rogue security softwares– is a form of malicious software and internet fraud that misleads users into believing there is a virus on their computer, and manipulates them into paying money for a fake malware removal tool.
Four search strategies
Keyword searching
Enter terms to search
Use quotation marks to search as a phrase and keep the words linked together
Common words are ignored (That, to, which, a, the …)
+ and – can be used to include or exclude a word
Boolean
AND – enter words connect with AND- it will include sites where both words and found
Uses: joining different topics (i.e. global warming AND California)
OR – requires at least one of the terms is found.
Uses: join similar or synonymous topics (i.e. global warming OR greenhouse effect)
NOT – searches for the first term and excludes sites that have the second term.
(i.e. Washington NOT school)
Question
a question may be entered in the search field of search engine
Advanced Features are offered on many engines by going to an “Advanced search” page and making selections. Effective in narrowing search returns to a specific topic or phrase.
LESSON 3: Advanced Word Processing Skills
Lesson Discussion
In the professional world, sending out information to convey important information is vital. Because of ICT, things are now sent much faster than the traditional newsletters or postal mail. You can now send much faster than the traditional newsletters or postal mail. You can now use the Internet to send out information you need to share. What if we could still do things much faster – an automated way of creating and sending uniform letters with different recipients? Would that not be more convenient?
I. Mail Merge and Label Generation
A. Mail Merge
One of the important reasons in using computers per se is its ability to do recurring tasks automatically. But this ability has to be honed by learning the characteristics and features of the software you use with your computer. After all, no matter how good or advance your computer and software may be, it can only be as good as the person using it.
In this particular part of our lesson, we will learn one of the most powerful and commonly used features of Microsoft Word called Mail Merge. As the name suggests, this feature allows you to create documents and combine or merge them with another document or data file. It is commonly used when sending out advertising materials to various recipients.
The simplest solution for the scenario above is to create a document and just copy and paste it several times then just replace the details depending on whom you send it to. But what if you have hundreds or thousands of recipients? Would not that take too many hours? What if you have a small database of information where you can automatically generate those letters?
Two Components of Mail Merge
1. Form Document
The first component of our mail merged document is the form document. It is generally the document that contains the main body of the message we want to convey or send. The main body of the message is the part of the form document that remains the same no matter whom you send it to from among your list.
Also included in the form document is what we call place holders, also referred to as data fields or merge fields. This marks the position on your form document where individual data or information will be inserted. From our sample document, the place holders are denoted or marked by the text with double-headed arrows (<< >>) on each side and with a gray background. On a printed standard form, this will be the underlined spaces that you will see and use as a guide to where you need to write the information that you need to fill out. In its simplest form, a form document is literally a “form” that you fill out with individual information. A common example of a form document is your regular tax form or application form.
2. List or Data File
The second component of our mail merged document is the list or data file. This is where the individual information or data that needs to be plugged in (merged) to the form document is placed and maintained. One of the best things about the mail merge feature is that it allows data file to be created fro within the Microsoft Word application itself, or it gets data from a file created in Microsoft Excel or other data formats. In this way, fields that needed to be filled up on the form document can easily be maintained without accidentally altering the form or main document. You can also easily add, remove, modify, or extract your data more efficiently by using other data management applications like Excel or Access and import them in Word during the mail merge process.
B. Label Generation
Included in the mail merge feature on Microsoft Word is the Label Generator. It just makes sense that after you print out your form letters, you will need to send it to individual recipients in an envelope with the matching address printed directly on the envelope or on a mailing label to stick on. By using virtually the same process as a standard mail merge, Microsoft Word will print individual addresses to a standard form that it has already pre-formatted. Simply put, it creates a blank form document that simulates either a blank label or envelope of pre-defined size and will use the data file that you selected to print the information, typically individual addresses. So even in generating labels, the two essential components of creating a merged document are present: the form document and the data file. Only in this case, you did not have to type or create the form document yourself because it was already created and pre-formatted in Microsoft Word. All you need to do is select the correct or appropriate size for the label or envelope and select the data file that contains the addresses (data) to be printed. You can also preview your merged labels before printing if you want to.
II. Integrating Images and External Materials
Integrating or inserting pictures in your document is fun and it improves the impression of your document. A common use of inserting a picture on a document is when you are creating your resume. Though seemingly simple to do, your knowledge on the different kinds of materials that you can insert or integrate in a Word document and its characteristics can help you create a more efficient, richer document not only in content but also in physical form. A better understanding of the physical form of your document as well as the different materials you would integrate in it would allow you to be more efficient and versatile in using Microsoft Word.
A. Kinds of Materials
There are various kinds of materials Microsoft Word is capable of integrating to make the documents richer, more impressive, and more informative.
1. Pictures
Generally, these are electronic or digital pictures or photographs you have saved in any local storage device. There are three commonly used types of picture files. You can identify them by the extension on their file names.
a. .JPG/JPEG
This is pronounced as “jay-peg“ and is the short form of .jpeg or Joint Photographic Experts Group. Like all the rest of the image file extensions, it identifies the kind of data compression process that it uses to make it more compatible and portable through the Internet. This type of image file can support 16.7 million colors that is why it is suitable for use when working with full color photographic images. Unfortunately, it does not support transparency and therefore, images of this file type can be difficult to integrate in terms of blending with other materials or elements in your document. But if you are looking for the best quality image to integrate with your document then this is the image file type for you. .JPG does not work well on lettering, line drawings, or simple graphics. .JPG images are relatively small in file size.
b. .GIF
This stands for Graphics Interchange Format. This type of image file is capable of displaying transparencies. Therefore, it is good for blending with other materials or elements in your document. It is also capable of displaying simple animation. Apparently, this may not be too useful on a printed document but if you are sending documents electronically or through email, or even post documents into a website, then this could be quite impressive. The downside is that it can only support up to 256 colors so it is good mostly on logos and art decors with very limited, and generally solid colors. .GIF is much better for logos, drawings, small text, black and white images, or low-resolution files.
Example of a .gif format picture.
c. .PNG
This is pronounced as “ping“. It stands for Portable Network Graphics. It was built around the capabilities of .GIF. Its development was basically for the purpose of transporting images on the Internet at faster rates. It is also good with transparencies but unlike .GIFs, it does not support animation but it can display up to 16 million colors, so image quality for this image file type is also remarkably improved. .PNG allows the control of the transparency level or opacity of images.
Example of .png format picture.
2. Clip Art
This is generally a .GIF type; line art drawings or images used as generic representation for ideas and objects that you might want to integrate in your document. Microsoft Word has a library of clip arts that is built in or can be downloaded and used freely. There are still other clip arts that you can either purchase or freely download and use that come from third-party providers.
Clip Art Icon in Microsoft Office 2010.
3. Shapes
These are printable objects or materials that you can integrate in your document to enhance its appearance or allow you to have some tools to use for composing and representing ideas or messages. If you are designing the layout for a poster or other graphic material for advertising, you might find this useful.
Shapes Icon under the Insert ribbon tab.
4. Smart Art
Generally, these are predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature. If you want to graphically represent an organization, process, relationships, or flow for infographic documents, then you will find this easy and handy to use.
Smart Art
5. Chart
Another type of material that you can integrate in your Word document that allows you to represent data characteristics and trends. This is quite useful when you are preparing reports that correlate and present data in a graphical manner. You can create charts that can be integrate in your document either directly in Microsoft Word or imported from external files like Microsoft Excel.
Chart – Used to illustrate and compare data.
6. Screenshot
Sometimes, creating reports or manuals for training or procedures will require the integration of a more realistic image of what you are discussing on your report or manual. Nothing can get you a more realistic image than a screenshot. Microsoft Word even provides a snipping tool for your screen shots so you can select and display only the part that you exactly like to capture on your screen.
III. Image Placement
Layout of text wrapping options.
A. In Line with Text
This is the default setting for images that are inserted or integrated in your document. It treats your image like a text font with the bottom side totally aligned with the text line. This setting is usually used when you need to place your image at the beginning of a paragraph. When placed between texts in a paragraph or a sentence, it distorts the overall appearance and arrangement of the texts in the paragraph because it will take up the space it needs vertically, pushing whole lines of texts upward.
B. Square
This setting allows the image you inserted to be placed anywhere with the paragraph with the text going around the image in a square pattern like frame.
C. Tight
This is almost the same as the Square setting, but here the text “hug” or conforms to the general shape of the image. This allows you to get a more creative effect on your document. This setting can mostly be achieved if you are using an image that supports transparency like a .GIF or .PNG file.
D. Through
This setting allows the text on your document to flow even tighter taking the contours and shape of the image. Again, this can be best used with .GIF or .PNG type of image.
E. Top and Bottom
This setting pushes the texts away vertically to the top and/or the bottom of the image so that the image occupies a whole text line on its own.
F. Behind Text
This allows your image to be dragged and placed anywhere on your document but with all the texts floating in front of it. It effectively makes your image look like a background.
G. In Front of Text
As it suggests, this setting allows your image to be placed right on top of the text as if your image was dropped right on it. That means whatever part of the text you placed the image on, it will be covered by the image.
IV. Key Terms
Mail Merge – a feature that allows you to create documents and combine or merge them with another document or data file.
Form Document – the document that contains the main body of the message we want to convey or send.
Data File – includes the individual information or data or the recipient’s information.
Merge Field/Place Holder – marks the position on your form document where individual data or information will be inserted.
.JPG – file extension for the Joint Photographic Experts Group picture file.
.PNG – file extension for Portable Network Graphics image file.
.GIF – file extension for the Graphics Interchange Format image file.
Clipart – line art drawings or images used as a generic representation for ideas and objects.
Smart Art – predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature.
Text Wrap – adjusts how the image behaves around other objects or text.
LESSON 4: Advanced Spreadsheet Skills
What is a Spreadsheet Software? • allows users to organize data in rows an columns and perform calculations on the data • These rows and columns collectively are called worksheet.
3. Examples of Spreadsheet Software: • LibreOffice Calc • OpenOffice.org Calc • Google Sheets • Apple iWork Numbers • Kingsoft Office Spreadsheets • StarOffice Calc • Microsoft Excel
4. MICROSOFT EXCEL
5. To open Microsoft Excel, Press “Windows Logo” + R then type “excel” then enter.
6. Key Terms in MS Excel: • Row – horizontal line of entries in a table • Column – vertical line of entries in a table • Cell – the place where info. is held in a spreadsheet
7. Key Terms in MS Excel: • Active Cell – the selected cell • Column Heading – the box at the top of each column containing a letter • Row Heading – the row number
8. Key Terms in MS Excel: • Cell Reference – the cell address of the cell usually combine letter and number (ex. A1, B4, C2) • Merge – combining or joining two or more cells • Formula – is an expression which calculates the value of a cell.
9. Key Terms in MS Excel: • Functions – are predefined formulas and are already available in Excel • Formula Bar – the bar that displays the contents of a cell
10. FUNCTIONS
11. BASIC MATH OPERATIONS: • =SUM(x,y) or =SUM(range) – returns the sum of x and y or (all the numbers within the range) • =PRODUCT(x,y) – returns the product of x and y • =QUOTIENT(x,y) – returns the quotient of x divided by y • =x-y – returns the difference of x subtracted by y
12. BASIC MATH OPERATIONS: • =x+y – returns the sum of x and y • =x*y – returns the product of x and y • =x/y – returns the quotient of x divided by y • =x-y – returns the difference of x subtracted by y
13. OTHER FUNCTIONS: • =ABS(x) – returns the absolute value of x • =AVERAGE(x,y) – returns the average of x and y • =CONCATENATE(x,y) – joins x and y
14. OTHER FUNCTIONS: • =IF(Condition, x, y) – returns x if the condition is true, else it returns y • =ISEVEN(x) – returns true if x is an even number • =ISODD(x) – returns true if x is an odd number
15. OTHER FUNCTIONS: • =COUNT(range) – counts the number of cell containing a number within a range • =COUNTIF(range, criteria) – count the number of cell that fits with the criteria within the range
16. OTHER FUNCTIONS: • =ISNUMBER(x) – returns true if x is a number • =ISTEXT(x) – returns true if x is a text • =LEN(x) – returns the length of characters in x • =PROPER(x) – returns the proper casing of x
17. OTHER FUNCTIONS: • =LEFT(x,y) – returns the characters of x specified by y (from the left) • =RIGHT(x,y) – returns the characters of x specified by y (from the right) • =PI() – returns the value of pi
18. OTHER FUNCTIONS: • =MIN(x,y) – returns the smallest number between x and y • =MAX(x,y) – returns the largest number between x and y • =MIN(range) – returns the smallest number within the range • =MAX(range) – returns the largest number within the range
19. OTHER FUNCTIONS: • =POWER(x,y) – returns the value of x raised to the power of y • =ROUND(x,y) – rounds x to a specified number of digits (y) =COLUMN(x) – returns the column number of x • =ROW(x) – returns the row number of x
20. OTHER FUNCTIONS: • =SQRT(x) – returns the square root of x • =TRIM(x) – removes extra spaces in x • =UPPER(x) – returns x in all capital form • =LOWER(x) – returns x in non- capital form
21. OTHER FUNCTIONS: • =TODAY() – returns the current date • =NOW() – returns the current date and time
22. EXERCISES
23. Consider this data: NAME MATH GRADE SCIENCE GRADE FILIPINO GRADE ENGLISH GRADE A.P GRADE MARK 75 70 78 81 78 PETE 84 87 86 88 85 ANA 91 92 95 90 90 REA 73 75 74 75 70
24. Give the formulas to get : • Mark’s , Pete’s, Ana’s and Rea’s averages • The highest grade that Ana got • The lowest grade that Mark got? • Sum of all Math Grade? Science? A.P.? • Sum of all Rea’s Grades • The Lowest Number among all grades • The remarks (Passed or Failed)
25. Now, consider this data: FIRST NAME MIDDLE NAME LAST NAME MARK CURTIS WILLIAMS PETE MCCLOEY HARRISON ANA MONROE FRITZ REA TAN COLLINS
26. Give the formulas to get : • Mark’s Full Name • Ana’s Full Name in Proper Case • Count the number of letters that Pete’s Last Name has • “COLL” from Rea’s Last Name • “LOEY” from Pete’s Middle Name • Combining “WILL” and “LINS” from Mark and Rea’s Last Names respectively
LESSON 5: Advanced Presentation Skills
Powerpoint is a highly innovative and versatile program that can ensure a successful communication whether you’re presenting in front of potential investors, a lecture theatre or simply in front of your colleagues. The following are the five features you should be using-if youy aren’t already. Learn everything about these tips: they will improve your presentation skills and allow you to communicate your message successfully. The five features of powerpoint was
1)adding smart art
2)Inserting Shapes
3)Inserting and Image
4)Slide Transitions
5)Adding Animations
Creating an Effective Presentation
1.
Minimize
: Keep slides counts to a minimum to maintain a clear message and to keep the audience attentive. Remember that the presentation is just a visual aid. Most information should still come from the reporter.2.
Clarity
: Avoid being to fancy by using font style that is easy to read. Make sure that it is also big enough to be read by the audience. Once you start making your presentation, consider how big the screen is during your report.3.
Simplicity
: Use bullets or short sentences. Summarize the information on the screen to have your audience focus on what the speaker is saying than on reading the slide. Limit the content to six lines and seven words per line. This is known as the 6 x 7 rule.4.
Visual
: Use graphics to help in your presentation but not too many to distract the audience. In addition, instead of using table of data, use charts and graphs.5.
Consistency
: Make your design uniform. Avoid having different font styles and backgrounds.6.
Contrast
: Use a light font on dark background or vice versa. This is done so that it is easier to read. In most instances, it is easier to read on screen if the background is dark. This is due to the brightness of the screen. LESSON 6: Imaging and Design for Online Environment
PHOTO EDITING
Photo editing encompasses the processes of altering images, whether they are digital photographs, traditional photo chemical photographs, or illustrations. Traditional analog image editing is known as photo retouching, using tools such as an airbrush to modify photographs, or editing illustrations with any traditional art medium.
Graphic software programs
Which can be broadly grouped into vector graphics editors, raster graphics editors, and 3D modelers are the primary tools with which a user may manipulate, enhance, and transform images. Many image editing programs are also used to render or create computer art from scratch.
BASIC OF IMAGE EDITING
RASTER IMAGESare stored in a computer in the form of a grid of picture elements or pixels.
VECTOR IMAGESsuch as Adobe Illustrator, Inkscape and etc. are used to create and modify vector images, which are stored as descriptions of lines, Bezier curves and text instead of pixels.
DIFFERENCE BETWEEN RASTER AND VECTOR IMAGES
RASTER IMAGESuse many colored pixels or individual building blocks to form a complete image JPEGs, GIFs and PNGs are common raster image types. Almost all of the photos found on the web and in print catalogs are raster images.
VECTOR IMAGES alternatively, allow for more flexibility. Constructed using mathematical formulas rather than individual colored blocks, vector file types such as EPS, AI and PDF are excellent for creating graphics that frequently require resizing. 3. 3D MODELING (OR MODELLING) is the process of developing a mathematical representation of any three dimensional surface of an object via specialized software. The product is called a 3D model. It can be displayed as a two-dimensional image through a process called 3D rendering or used in a computer simulation or physical phenomena. The model can also be physically created using 3D printing devices.
IMAGE FORMATS
Ø JPEG is a commonly used method of lossy compression for digital images, particularly for those images produced by a digital photography.
Ø PNG (PORTABLE NETWORK GRAPHICS) is a raster graphics file format that supports lossless data compression.
Ø GIF a lossless format for image files that supports both animated and static images.
Ø BMP is a raster graphics image used to store bitmap digital images
Ø EPS used in vector-based images in Adobe Illustrator.
Ø SVG is an XML-based vector image format for two-dimensional graphics w/ support for interactivity and animation
Ø .3ds is one of the file formats used by the Autodesk 3Ds Max 3D Modelling, animation and rendering software.
Ø .fbx is an exchange format, in particular for interoperability between Autodesk products and other digital content creation software
FEATURES OF IMAGE EDITORS
SELECTION One of the prerequisites for many of the app mentioned below is a method of selecting part(s) of an image, thus applying a change selectively without affecting the entire picture
Ø MARQUEE TOOL for selecting rectangular or other regular polygon-shaped regions
Ø LASSO TOOL for freehand selection of a region
Ø MAGIC WAND TOOL selects objects or regions in the image defined by proximity of color or luminance
LAYERS which are analogous to sheets of transparent acetate, stacked on top of each other, each capable of being individually positioned, altered and blended with the layers below, w/o affecting any of the elements on the other layers. IMAGE SIZE resize images in a process often called image scaling, making them larger, or smaller. High image resolution cameras can produce large images which are often reduced in size for Internet use.
CROPPING creates a new image by selecting a desired rectangular portion from the image being cropped. The unwanted part of the image is discarded. Image cropping does not reduce the resolution of the area cropped.
CLONING uses the current brush to copy from an image or pattern. It has many uses: one of the most important is to repair problem areas in digital photos.
IMAGE ORIENTATION – Image editors are capable of altering an image to be rotated in any direction and to any degree. Mirror images can be created and images can be horizontally flipped or vertically flopped. Rotated image usually require cropping afterwards, in order to remove the resulting gaps at the image edges.
PERSPECTIVE – is the art of drawing solid objects on a two- dimensional surface so as to give the right impression of their height, width, depth and position in relation to each other when viewed from a particular point.
SHARPENING AND SOFTENING– Sharpening makes images clearer. Too much sharpening causes grains on the surface of the image. Softening makes images softer that removes some of the highly visible flaws. Too much causes the image to blur.
SATURATION- is an expression for the relative bandwidth of the visible output from a light source. As saturation increase, colors appear more “pure.’’ As saturation decreases, colors appear more ‘’ washed-out.’’
CONTRAST AND BRIGHTENING
Contrast of images and brighten or darken the image. Underexposed images can be often be improved by using this feature.
Brightening lightens the image so the photo brightens up. Brightness is a relative expression of the intensity of the energy output of a visible light source.
Adjusting contrast means adjusting brightness because they work together to make a better image.
PHOTO MANIPULATION
Photo manipulation involves transforming or altering a photograph using various methods and techniques to achieve desired results. Some photo manipulations are considered skillful artwork while others are frowned upon as unethical practices, especially when used to deceive the public, such as hat used for political propaganda , or to make a product or person look better.
DIFFERENCES PHOTO EDITING – signifies the regular process used to enhance photos and to create them ‘’Actual editing simple process’’. Also includes some of the regular programs used for editing and expose how to use them. PHOTO MANIPULATION – includes all simple editing techniques and have some manipulation techniques like erasing, adding objects , adding some graphical effects, background correction, creating incredible effect, change elements in an image, adding styles , eliminating blemishes from a person’s face and changing the features of a person’s body.
b.) Infographics
also known as data visualization, information design, and communication design
It is any graphic that display and explains information, whether that be data or words. When we use the term ‘’infographics’’, we’re using it as a general term used to describe data presented in a visual way.
Infographics are important because they change the way people find and experience stories. Infographics are being used to augment editorial content on the web, it create a new way of seeing the world of data, and they help communicate complex ideas in a clear and beautiful way.
TYPES OF INFOGRAPHICS
Statistical
Process Flow
Geographic
PROCESS OF MAKING INFOGRAPHICS
Research
a)Know what is needed
b)Take a reference
c)Know the audience
d)Decide the type of infographics
Brainstorm
a)Gather ideas
b)Build thought process
Design
a) Choose your tool and start designing
Review
a) Cross check the data to deliver flawless output
Launch
a) Make it viral
b) Share on social network
BEST PRACTICES WHEN CREATING INFOGRAPHICS
a)Maintain a structure
b)Don’t use more than 3 color palletes
c)Typography matters a lot
d)Include source and references
LESSON 7: Online Platforms for ICT Content Development
1.Facebook
Posted on
February 13, 2017
Marketplace – allows members to post, read and respond to classified ads.
Groups – allows members who have common interests to find each other and interact.
Events – allows members to publicize an event, invite guests and track who plans to attend.
Pages – allows members to create and promote a public page built around a specific topic.
Presence technology – allows members to see which contacts are online and chat.
Within each member’s personal profile, there are several key networking components. The most popular is arguably the Wall, which is essentially a virtual bulletin board. Messages left on a member’s Wall can be text, video or photos. Another popular component is the virtual Photo Album. Photos can be uploaded from the desktop or directly from a smartphone camera. There is no limitation on quantity, but Facebook staff will remove inappropriate or copyrighted images. An interactive album feature allows the member’s contacts (who are called generically called “friends”) to comment on each other’s photos and identify (tag) people in the photos. Another popular profile component is status updates, a microbloggingfeature that allows members to broadcast short Twitter-like announcements to their friends. All interactions are published in a news feed, which is distributed in real-time to the member’s friends.
Facebook offers a range of privacy options to its members. A member can make all his communications visible to everyone, he can block specific connections or he can keep all his communications private. Members can choose whether or not to be searchable, decide which parts of their profile are public, decide what not to put in their news feed and determine exactly who can see their posts. For those members who wish to use Facebook to communicate privately, there is a message feature, which closely resembles email.
2. Instagram
Instagram is an online mobile photo-sharing site that allows its users to share pictures and videos either publicly or privately on the app, as well as through a variety of other social networking platforms, such as Facebook, Twitter, Tumblr, and Flickr. Originally, a distinctive feature was that it confined photos to a square shape, similar to Kodak Instamatic and Polaroid SX-70 images, in contrast to the 4:3 aspect ratio typically used by mobile device cameras. In August 2015, version 7.5 was released, allowing users to upload media captured in any aspect ratio. Users can also apply digital filters to their images. Videos on Instagram debuted in June 2013, allowing prerecorded square standard definition resolution clips of up to 15 seconds to be shared; later improvements added support for widescreenresolutions of up to 1080p and longer recording times for either prerecorded (up to one minute) or disappearing live (up to one hour) videos.
Instagram was created by Kevin Systrom and Mike Krieger, and launched in October 2010 as a free mobile app. The service rapidly gained popularity, with over 100 million active users as of April 2012[10][11] and over 300 million as of December 2014.[12] Instagram is distributed through the Apple App Store and Google Play.[13]Support for the app is available for iPhone, iPad, iPod Touch, Windows 10 devices and Android handsets, while third-party Instagram apps are available for BlackBerry 10 and Nokia-Symbian Devices.
3. Twitter
Twitter is an online news and social networking service where users post and interact with messages, “tweets,” restricted to 140 characters. Registered users can post tweets, but those who are unregistered can only read them. Users access Twitter through its website interface, SMS or a mobile device app.[10] Twitter Inc. is based in San Francisco, California, United States, and has more than 25 offices around the world.
Twitter is about learning and adding value
It is also about adding value to others by giving or sharing something valuable to them so that they are able to learn something. That is why I usually tweet about stuff that I read, learned or have good value. I have learned so much from the others that is why I love twitter. It is also about helping others, I disagree with many‘experts’ that say you should only follow ‘influential’ users because I don’t judge someone that way, and because I believe the people at Twitter don’t believe in them either. I also disagree that you should only share your own stuff otherwise you will dilute your brand. Sure it makes sense but 24/7 sharing your own blog post and following influential people?
BLOGGING SITES
Weebly
Weebly is one of the easiest website builders in the market. They allow you to drag and drop content into a website, so it’s very intuitive to use (click here to see our opinion on Weebly).
By using Weebly’s website building elements, you can literally drag them into your website and have a website built relatively quickly, and painlessly. The beauty of this system is that you can pretty much drag the elements to wherever you want – so it’s not very restrictive on where and how you place your website content.
Weebly’s elements include pictures, paragraphs, videos, buttons, maps, contact forms – basically all the basics for website building.
2. Tumblr
Tumblr is a popular microblogging platform designed for creative self-expression. It is considered a mindful alternative to Facebook and other social media websites where users blog on a myriad of topics.
You can link your Tumblr account to other social networks you use and you can feed your traditional blog or other RSS feed to your Tumblelog. You can also create static pages such as your own Questions page that people are automatically taken to when they ask you a question. If you want to make your Tumblelog look more lie a traditional website, you can do it by adding pages. You can make your Tumblelog private or just make specific posts private as needed, and you can schedule posts to publish in the future.
Tumblr is perfect for people who don’t need a full blog to publish lengthy posts. It’s also great for people who prefer to publish quick multimedia posts, particularly from their mobile devices. Tumblr is also a great choice for people who want to join a larger community. If a blog is too much or too big for you, but Twitter is too small or too little for you and Instagram isn’t versatile enough for you, then Tumblr might be just right for you.
It’s also easy to invite other people to contribute to your Tumblelog.
If you want to track your stats, you can add any analytics tracking code to your Tumblelog. Some users will even burn a feed with Feedburner, create custom themes, and use their own domain names
3. Pinterest
Pinterest is a free website that requires registration to use.Users can upload, save, sort, and manage images—known as pins—and other media content (e.g., videos) through collections known as pinboards. Pinterest acts as a personalized media platform. Users can browse the content of others in their feed. Users can then save individual pins to one of their own boards using the “Pin It” button, with pinboards typically organized by a central topic or theme. Users can personalize their experience by pinning items, creating boards, and interacting with other members. The end result is that the “pin feed” of each user displays unique, personalized results.
Content can also be found outside of Pinterest and similarly uploaded to a board via the “Pin It” button, which can be downloaded to the bookmark bar on a web browser, or be implemented by a webmaster directly on the website. They also have the option of sending a pin to other Pinterest users and email accounts through the “Send” button. Some websites include red and white “pin it” buttons on items, which allow Pinterest users to pin them directly.
Initially, there were several ways to register a new Pinterest account. Potential users could either receive an invitation from an already registered friend, or they could request an invitation directly from the Pinterest website that could take some time to receive. An account can also be created and accessed by linking Pinterest to a Facebook or Twitter profile. When a user re-posts or re-pins an image to their own board, they have the option of notifying their Facebook and Twitter followers. This feature can be managed on the settings page.
On the main Pinterest page, a “pin feed” appears, displaying the chronological activity from the Pinterest boards that a user follows.
A “board” is where the user’s pins are located. Users can have several boards for various items such as quotes, travel or, most popularly, weddings. A “pin” is an image that has either been uploaded or linked from a website. Once users create boards and add pins, other users can now repin, meaning they can pin one user’s image to their board as well. Once the user has set up their account and boards, they can browse, comment, and like other pins. Users might be discouraged by repeated images and difficult-to-follow direct linking features. Pinterest has also added the option of making boards “secret” so that the user can pin to and view boards that only the user can see when logged into their own account.
Pinterest does not generate its own content; rather, it draws from many resources around the web and compiles them in one convenient location for users.
1 note
·
View note
Link
Intercel is the Australian leading manufacturer of industrial 4GX modem Routers, We have some great Quality industrial 4Gx modem and routers Solutions.
1 note
·
View note
Text
FREQUENTLY ASKED QUESTIONS ABOUT JIOFI ROUTERS
Reliance JIO is among the most innovative mobile network operators in India. It delivers a lot of attributes and it's regarded as an enormous, radical part of cellular network industry in India. The company provides a trailer supply to prospective customers, for example access to unlimited 4G net + calls + SMS for affordable price. Right from the start that provide was limited JioFi (mobile hotspot apparatus ) and LyF mobiles only. Though, later the deal has been extended to other devices.

People weren't knowledgeable about the option to access high speed WiFi while moving or traveling, until Reliance JioFi device was devised. This device currently has an enormous number of active users that use Reliance JIO sim installed in JioFi apparatus. There are lots of types of JioFi devices, which can connect more than 10 devices + USB connect at exactly the same time. More advanced models offer you the possibility to join a lot more devices concurrently.
If you made a remarkably common device, for example JioFi, you have to be ready to receive a lot of questions about it. There could be an issue to discover a particular info about this device, in addition to ideal JioFi page with frequently asked questions and answers. Therefore, we decided to perform a research and collect all of the usual questions around the web and provide helpful answers on these.
JioFi is a portable hotspot device which you can use to get high speed 4G net + calls and SMS through Jio4GVoice application.
Q: How much JioFi device costs?The JioFi mobile hotspot device is priced at Rs 1,999. That price also includes starter kit.
Q: Where do I find JioFi and buy it?The JioFi is available on websites such as Amazon or even SnapDeal. Also, all Reliance Digital Stores and DX mini shops are equipped with this device.
Q: What comes in the JioFi Basic kit?The JioFi starter kit includes a JioFi portable apparatus, Jio GST program solution (1 year old ), 25 GB data (1 year), jointly with Infinite voice calls, Billing and management application. More and more partial activations and updates can be found in the most regions in India.
You can also read this Helpful post: Everything about JioFi Dongle
Q: How Can I Acquire a Jio Sim?To be able to get Jio Sim for your JioFi device, you need to bring evidence of your identity and personal documents, including the speech, in Reliance digital shop.
Normally the activation process of Jio Sim doesn't require more than 15 minutes, the moment you do KYC using your aadhar card
.Q: How many connected devices can JioFi Router up at the exact same time?Initially, JioFi device has the ability to support up to 31 devices. Still, you should be careful as it is not suggested to join more than 10 devices concurrently, you don't want to overload your apparatus.
Q: Can I use the USB Cable to link JioFi apparatus to PC?Yes, JioFi router has a USB Slot for tethering the internet on your personal computer or laptop.
Q: I have noticed numerous lights on JioFi device, what is their purpose?
Q: Could I tether JioFI with non-4G apparatus?
Any WiFi compatible apparatus may be linked with JioFi to get the high speed 4G internet.
Q: Can you inform me what's the battery capacity of the device?
JioFi routers use batteries with power of 2300mAh.
The battery in these devices can last about 6 hours of constant work.
Q: How long will charging battery shoot?
Charging will take around 3 hours before it is totally done.
Q: How to utilize JioFi device?
Managing with JioFi apparatus is quite simple. To start with, you need to insert battery and Jio Sim into the router. Then turn on WiFi on your smartphone or personal computer and locate JioFi hotspot. Connect to it with the password and username that is written on the rear side of the box or battery cap. After you complete everything, the device is set and ready to use.
Q: How to call somebody with JioFi?
2 -- Make sure you join your smartphone with JioFi through WiFi. 3 -- you may make calls using only Jio4GVoice applications.
Q: How to manage settings of JioFI apparatus?
To be able to modify the configuration of your device you want to open the JioFi Web configuration panel in jiofi.local.html.
Q: How to access JioFi Web Web configuration panel?
1 -- Connect JioFi with your PC, notebook or smartphone. Two -- Open an internet browser and type http://jiofi.local.html/index.html from the search bar. 1 -- Open Internet configuration panel on your PC, notebook or smartphone while it's connected to JioFi. Two -- Go to'Settings'. 3 -- Then choose'WIFi' alternative. 5 -- Confirm it by clicking on'Apply' and your password is successfully changed.
You can also read this useful article: The best way to alter JioFi password
Q: How to allow or deny a device to tether with JioFi through mac address? 1 -- Open internet configuration panel in your browser. Two -- Navigate to'Settings'. 3 -- Select'Network' from the following menu. 5 -- Then, it's on you to select'allow' or'deny' under'Mac address filter style'. 6 -- Click the add button so that you may add mac address in the list of consumers. 7 -- You can even enable/disable the status from the same page. 8 -- By clicking on'Submit' you'll add it to the list.
You can also read this Helpful article: How to conceal your JioFi router into other people
Conclusion
We gathered these frequently asked questions regarding JioFi apparatus and tried to provide the best answers we can. But in case you still have some unanswered question, be free to compose them in the remarks section. We love to get feedback from our customers and see or listen to their ideas, so please get in touch with us, and be confident that we're likely to assist you as far as we can.
1 note
·
View note
Text
huawei mate se specs
Special offers and product promotions:
Amazon Business: For business-only pricing, quantity discounts, and FREE Shipping. Register a free business account
Product information:
Customer questions & answers:

Question: So how can I use this in the USA? I have sprint now but I would love to use it on google's project fi/ google fi
Answer: I bought an International unlocked version. You can use it in the USA with either T-Mobile and AT&T.
The only catch is the Huawei IMEI is not a known phone, at least by AT&T, so it only would come up as a vanilla GSM phone, maxing out at 3.5G speeds.
To get it activated at a full 4G LTE phone, you'd want to move a SIM c… see more
By Home Deep Peaux on December 10, 2018
I'm using mine on Google Fi and just ordered another for my wife. With the exception of no Sprint access (which was slow and awful anyway), it works great!
By Amazon Customer on May 1, 2019
The device will work on the GSM network provided at CommunityPhone.org, too, who can provide 4G/LTE for this device for cheaper than Google Fi
By James Graham on September 2, 2019
The device will work on the GSM network provided at CommunityPhone.org, too, who can provide 4G/LTE for this device for cheaper than Google Fi
By James Graham on September 2, 2019
Question: does it have Google play installed to support Gmail, Google maps, Google apps?.
Answer: Yes, also Google Play store runs well.
By Home Deep Peaux on December 10, 2018
Yes, it has all that, and everything works fine!
By Monica C. on September 30, 2019
Yes
By Clint on November 17, 2018
Also read about
best gaming laptop under 600 dollars
the best laptop deals black Friday best buy
Netgear wifi extender ac1200
best gaming laptop under 800
Netgear nighthawk ax8 8-stream ax6000 wifi router
polaroid zip mobile printer
best wifi adapter for hacking
PlayStation 4 pro 1tb console - destiny 2 bundle
hp laptops best buy
for buy click here
1 note
·
View note
Text
4G M2M Router in UK - 4G Router Store
If you are Looking for 4G M2M Routers in UK, No need to worry, Buy 4G Routers in UK at an affordable price. Call us for more - 01708388799.
#4G Router uk#4g router#M2M 4G Router#4G Signal antenna#4G router antenna#4g antenna outdoor#4G Router Store
0 notes