#6 assignments in logic circuits
Explore tagged Tumblr posts
Text
How to Pass the ISRO Exam: 10 Crucial Pointers for Achievement
Being one of the top space organizations in the world, the Indian Space Research Organization (ISRO) has an extremely tough recruiting process. For scientists and engineers who are enthusiastic about space technology, it provides job options. In order to prepare for ISRO, one must have a clear grasp of the test format, a concentrated strategy, and a strategic plan. We'll go over the specifics of the ISRO test in this article and offer ten key takeaways for passing it.
Overview of the ISRO Exam For engineers and scientists in a variety of fields, including computer science, electronics, mechanical engineering, and electrical engineering, ISRO administers recruiting examinations. There are often two steps in the choosing process: Written test: The written test evaluates applicants' technical knowledge and problem-solving skills and is objective. Interview: Those who pass the written exam are invited to an interview, when their technical proficiency and practical knowledge are assessed. There are about eighty questions in the written test, and you get ninety minutes to complete it. The majority of the focus is on fundamental topics related to the candidate's engineering field, and incorrect responses result in a failing grade.
Ten Crucial Elements to Pass the ISRO Exam:
1) Recognize the Exam Pattern and Syllabus To effectively prepare for the ISRO test, one must first grasp the syllabus and exam structure in its entirety. The main technical topics in your engineering field are examined on the test. Because the questions are meant to gauge your level of knowledge, be sure you are knowledgeable about every subject.
2) Pay Attention to Fundamental Subjects The recruiting test for ISRO places a strong emphasis on technical expertise; depending on your sector, the majority of the questions cover fundamental topics including digital circuits, fluid physics, thermodynamics, control systems, and more. Concentrate on laying a solid foundation in these important areas. Review key ideas and go through associated problem-solving exercises.
3) Consult the Standard Books For ISRO preparation, standard textbooks—like the ones your undergraduate studies recommended—are essential. For mechanical engineering, use texts such as P.S. Gill's Machine Design or R.K. Bansal's Fluid Mechanics. In the same way, works like Boylestad for Circuit Theory are suggested for Electronics. Use tried-and-true resources to improve conceptual clarity.
4) Complete Last Year's Assignments Completing ISRO's previous year question papers is essential to comprehending the format and nature of the test. Examine these articles in detail to find key themes and typical question types. You'll know exactly where to concentrate your preparation efforts after reading this.
5) Effective Time Management Effective time management is essential for both the test and preparation. Give each topic a certain length of time, and stick to the schedule. You have 90 minutes to complete the 80 questions in the test, so you need to be precise and speedy. To increase your speed, work on solving puzzles within the time limitations. 6) Edit Frequently To remember what you have learnt, you must revise. Take brief notes for easy access, and review key equations, ideas, and troubleshooting methods on a frequent basis. This will facilitate your ability to swiftly recall material during the test.
7) Do Practice Exams Mock exams assist you in evaluating your performance by simulating the real exam setting. Taking regular mock tests allows you to assess your preparation level, identify weak areas, and improve your time management. It also helps in boosting confidence.
8) Develop Your Ability to Solve Problems Exam questions from ISRO frequently call for logical thinking and problem-solving skills. To hone your analytical abilities, work through a range of technical challenges pertaining to many subjects. Instead of memorizing the topics, focus on comprehending them because the questions may call for you to use your knowledge in novel ways.
9) Get ready for the face-to-face meeting. Getting through the written exam is just the first step. The interview holds equal significance. Since ISRO interviewers frequently ask questions on real-world engineering difficulties, concentrate on the applicability of what you've learnt in the actual world. When giving explanations during the interview, project confidence and clarity.
10) Remain Upbeat and Concentrated Exam prep for competitive examinations such as ISRO may be difficult and nerve-wracking. It's critical that you remain upbeat and motivated during the preparation process. Avoid burnout, take regular pauses, and maintain your concentration on your objectives. Take use of the encouraging surroundings around you to never stop moving ahead.
In summary It takes a mix of diligent study, practice, and willpower to pass the ISRO test. You may maximize the effectiveness of your study sessions and raise your chances of success by adhering to these ten crucial suggestions. Recall to solve last year's papers, concentrate on the essential themes, and use your time wisely. You may fulfill your ambition of joining ISRO and supporting India's space exploration effort with persistent hard work and devotion.
Start Your Preparation With: https://gameacademy.in/ / https://clppenny.page.link/cTBm
Recommended: https://www.youtube.com/@gblions / https://www.youtube.com/@gblionsaeje
0 notes
Text
“In conclusion...”

“I want to die.”
#「Red Oni(IC)」#alright my first week of classes now done#I have like#6 assignments in logic circuits#one assignment in scientific programming#plenty of reading in the netacad course for a test this monday
11 notes
·
View notes
Text
DISCLAIMER: I’m not hating on people who believe this, I’m just explaining my position and alternatives
The idea that JM and JK have been together for 6 years and are married is....a lot to say the least. I don’t know their relationship but if I’m going by the logic in their actions I wouldn’t at all think this. I feel like I’m the rare person who thinks they’re probably actually together but not like married or something lol
“Gay wedding rings”, a trip to Tokyo Disney, and a shady reaction to “Laguna” isn’t really a confirmation. Let me explain.
-------------------------------------------------------
Gay “Wedding” Rings
It definitely looks like they have worn those same rings from that infamous Google search, but let me offer a few alternative explanations that’s just as plausible if not more than the idea of them being married to each other:
It’s jewelry their stylists assigned for them without much regard to the styles. Celebrities wear stuff all the time that their stylists handpick for them without the stylist or the celebrity really understanding the symbology behind it--this is evident from the fact that so many idols wear clothes and accessories with curse words in different languages on them or other profane/inappropriate sayings/symbols on them
They bought them together, but instead of an engagement ring, it’s a promise ring for each other or holds some other kind of symbolism
I’m personally more inclined to believe #2 and really think that the symbolism behind those rings is nothing close to “we’re engaged” and is more so something representing progress in their personal relationship (relationship in this context not necessarily being romantic but just a relation between two people). Obviously, I think it could have romantic implications, just not marriage lol
Tokyo Disney/GCF in Tokyo
I am pretty much going with conventional sentiment here that this video has a romantic undertone. I do think it was more so made for Jimin than for the fans about Tokyo. I also think that they seemed to get even closer from this point on. However, I don’t think this was their “honeymoon” or “wedding”. Actually, I think this has a few alternative explanations that could each be plausible:
This was simply a birthday gift for Jimin where they just had fun together and took a rest since this was actually their vacation time. JK made GCF in Tokyo with the intention of documenting mostly Tokyo but found Jimin to be a more engaging subject
This was a birthday trip but also where JK may have made his romantic feelings for Jimin known. JK made GCF in Tokyo with the intention of documenting Jimin as a ‘love letter’ of sorts
This is when they decided they’d pursue something more serious other than just flirting around. JK had the intention of expressing this through GCF in Tokyo, hence his strategic song choice
This was just a fun birthday trip but with the addition that it unexpectedly brought them closer romantically, which is what compelled JK to create GCF in Tokyo
I am more inclined to believe #4. I think that if it is the case they have romantic feelings for each other (which, it seems that way IMO), then it’s more plausible that the trip just brought it out even more, to a further degree and JK started to become more serious about his feelings. It would explain the song choice for that video better than “they got married/honeymooned”. If you just got married why would you want to or even have to remind your partner to “be there for you” the same way you’re there for them? It’s a huge part of the song and would seem like a huge red flag in a new relationship if your partner isn’t reciprocating those feelings
Laguna
Alright now this is a pretty recent idea that a lot of people have considered. It’s the idea that JK watched a video that was filmed at Laguna Beach for inspiration on GCF Saipan. Because gay couples can legally marry in California (and, consequently, at Laguna Beach), and when RM mentioned going to “Laguna” in an interview Jimin and JK looked at each other and laughed, they must have gotten married at Laguna Beach.
To me, this is the biggest reach of them all. If they were to have gotten married, not only could Jimin and JK have gotten married at literally any of their other American tour/promotional destinations at that time (seriously--they went to Los Angeles and Las Vegas multiple times but we have no proof they ever even went to Laguna Beach. LA is about an hour away from Laguna Beach and has dozens of its own beaches to get married at if one wishes), but like if they did get married there, where is the proof and when would they have the time? Because I guarantee you there would be. Armies follow them around everywhere, and especially in populous areas like Laguna Beach, which is one of the most popular beach destinations in Southern California... It just doesn’t make sense that no one would have seen this “wedding” and that they’d even have time to have a ceremony given that they’re only ever in one American destination for ~1 week at a time, and most of that time is spent performing, rehearsing, and running the promo circuit. They never go there just to vacation
Also, we have no proof that JK actually even watched that video particularly. I mean, it’s possible but like??? It’s still kind of stretching it given that nearly all beach vlogs have similar aesthetics and techniques. We also don’t know why Jin was laughing in that video. Like, yeah, he could’ve been laughing because he knew they secretly got married there, but he also just could’ve been laughing because laughter is contagious and the two next to him just started laughing out of seemingly nowhere. I look at it this way: if he was laughing because ‘haha that’s where they got married/are planning to get married’ then why did he ask, months later, if they were dating? Even jokingly?
So, with that said, here are some alternative explanations for why Laguna was so funny to them:
JK did watch that video, told Jimin about it, and now they want to go there for vacation either to spend time with each other or because of the potential debauchery that could take place in a tropical destination with tons of sexy people roaming around
They went to Laguna Beach back during AHL and had some memorable moments there
I truly think they do know about Laguna Beach and obviously want to go there (RM actually said this), but I honestly don’t know why it was funny to JM and JK. I will say though that I don’t think it’s funny because ‘haha, joke’s on Namjoon, we’re married’, but because of almost any other reason tbh. The marriage thing just doesn’t hold weight there to me
Now that I’ve said all that, I kind of want to talk about my issue with attaching the word “gay” to everything and how that’s used with Jikook. Maybe that’ll be my next long post...
70 notes
·
View notes
Text
Circuit Programming Assignment
Week 4 Programming Assignment Write a Java GUI application to calculate total resistance, current, and power in a circuit. The general appearance of you GUI should be as shown below:

Sample Output Your program must meet the following requirements: 1. Do not use any of the GUI editing capabilities of Eclipse for this assignment (no setBounds). Do all the GUI layout work based on what you have learned from the lecture material and assigned book readings in the last 2 weeks. 2. You will only need to use the ActionListener interface for this lab. The only events that your program handles are action events from the 4 buttons. 3. This program is contained in 1 class that has a constructor, a main method, and a nested inner class for the event handler. 4. You must use inheritance to get a JFrame into your application 5. The GUI and event handling setup must be done in the constructor of your GUI class or in private methods called from the constructor. Hint: it would seem logical to have a private method to build the top, right, left, and bottom panels. 6. The GUI should be organized as follows: • The top panel will contain 2 labels and 2 text fields. The text fields should be initialized with a parameter of 8. No special layout manager needed here. • The bottom panel will contain 4 buttons. Use a grid layout here with horizontal and vertical gaps of 5. • The right panel contains 3 labels and 3 text fields initialized with a parameter of 10. Use a grid layout here with horizontal and vertical gaps of 5. • The left panel contains a scrollpane which contains a text area setup for 10 rows and 18 columns. No special layout manager needed here. • Place the 4 panels into the frame in the appropriate regions of the frame’s border layout. • You can create space around a panel by doing the following: yourPanel.setBorder(BorderFactory.createEmptyBorder(5, 5, 5, 5)); How the Application Works A user will enter one value into the voltage text field and one value into the resistance text field. Then the user will click either the Series Resistor or Parallel Resistor button. This action causes the program to store the voltage value and the resistance value and output the voltage and resistance values to the text area as shown in the screen shot above. The user can then place another value into the resistance text field and again click the Series Resistor or Parallel Resistor buttons. This action causes the resistance value to be reported in the text area and the resistance value is used to update the total resistance calculations internally. When the user is finished adding resistors, the user clicks the Calculate Totals button which causes the program to calculate and output the total resistance, current, and power into the appropriate text fields. Clicking the New Circuit button should clear the total resistance, current, and power text fields. It should clear the text area and place the initial instruction to “Enter volts, then resistance values” into the text area. Event Handling Design First of all you will need 3 member variables to hold values to be used over the course of the circuit entry. These three member variables are all doubles: one for voltage, one to accumulate total resistance, and one to accumulate resistance of the current parallel part of the circuit. Second, you will need one nested inner class that implements the ActionListener interface. One object of this class is to be created and added to the 4 buttons as the event handler. Inside the nested inner class you will have to use if statements to check to see which of the 4 buttons was clicked. The following describes what to do for each of the 4 buttons: 1. New Circuit button: Clear the three text fields for total resistance, power, and current. Set the text area to read “Enter volts, then resistance values.”. Set the 3 member variables mentioned above back to 0. 2. Series Resistor button: If the voltage member variable is 0, call a function that gets the voltage value from the voltage text field, reports the voltage value in the text area, and stores the numeric value of the voltage into the voltage member variable. (This function will be called from the next button also.). Get the value of the resistor from the resistor text field and report adding a series resistor in the text area. Convert the value of the resistance to a numeric value and add it to the member variable used to keep track of total resistance. In addition, if the member variable used for accumulating parallel resistance is non-zero, add that to the total resistance member variable, then set the parallel resistance variable to 0. 3. Parallel Resistor button: If the voltage member variable is 0, call a function that gets the voltage value from the voltage text field, reports the voltage value in the text area, and stores the numeric value of the voltage into the voltage member variable. (This function was called from the previous button also.). Get the value of the resistor from the resistor text field and report adding a parallel resistor in the text area. Convert the value of the resistance to a numeric value and if the member variable used to keep track of parallel resistance is 0, set the parallel resistance member variable to this resistance value. If the member variable is not zero, calculate the new parallel resistance value by using the following formula: R_parallel = (R_parallel * new_resistance) / (R_parallel + new_resistance) 4. Calculate Totals button: If the parallel resistance member variable is not 0, add it to the total resistance member variable and set the parallel resistance variable to 0. Output the total resistance member variable to the total resistance text field with 3 digits after the decimal point. Use String.format! Output the current to the total current text field by calculating the current as voltage / total resistance. Also use String.format to set the output to 3 digits after the decimal point. Finally, output the power to the total power text field by calculating the power as (voltage * voltage) / total resistance. Also use String.format to set the output to 3 digits after the decimal point. The output should appear as shown in the screen shot above. Also make sure that you add comments to your program! Take screen shots of the program showing where you added at least 1 series resistor and 2 parallel resistors and show the calculated outputs. Paste the screen shot and the source code for your program into a Word document. Read the full article
0 notes
Text
An Introduction to Computer Science Textbook Solution Manuals
A wide range of disciplines is interlinked with Computer Science viz computer science, information systems, computer engineering, and information technology,
These disciplines mentioned above are collectively called computing. This family of fields is linked with each other in terms of computing and this is the primary objective of the study. Since they are interlinked, it has its research standpoint and the emphasis is on curricular.
Simply put, Computer science is a concoction of computers and computational systems. A departure from electrical and computer engineers, computer scientists, a majority part involves in software and software systems that come from theory, design, application, and development. The main area of study is a gamut of topics like AI(Artificial Intelligence), networks, database systems, human-computer interaction, numerical analysis, programming, and more.
Concern for scientists:
Oftentimes, students of computer scientists believe that programming is the major pie of computer science. To be candid, it is one of the areas, but not the entire gamut of computer science. The main concern of computer scientists is to what problems can be solved with the computer as well as the complexity of the algorithm that helps to solve the problems.
A slew of benefits that proffer to us by Computer Science. Let us walk through it:
1. A good means to meeting needs.
2.It warrants overlooked people.
3.It drives towards a more balanced world in terms of socio-economic disparity.
4. Enhance the health care system.
5. To foster better education.
6. Helping communication to be expanded.
7. foretelling and eschewing cataclysm.
8.It brings more positive vibes in every sphere of mankind.
Why it is important to learn?
It is well-documented that the discipline of computer science is leapfrogged. In keeping pace with the rapid growth of computer science, there is an acute shortage of computer science professionals. This indicates students' exposure to technology and resources is not enough to motivate the students, and another reason does round that adequate attempts are not made to encourage students. The rapid digitization has prompted more students to learn computer science and thereby excelling their career aspirations. In this digital era, there is a compelling need for logical thinking and problem-solving skills. Irrespective of the discipline, students ought to learn computer to create a file, researching a specific subject for their academic requirement, and many more. Simply put, it is the part and parcel of our life.
What is their role?
The role keeps on varying depending on their area of choice. A synopsis runs as follows:
Software Engineering: They deal with software development, Website development and, mobile app development. These apart, they ought to have good programming knowledge.
Hardware Engineer: Rectify the flaw of the hardware, design, and maintain physical products.
Network Engineer: They are quite familiar with network connectivity, systems, and mending the glitches in network-related activities.
The IT sectors keep on changing very rapidly in terms of emerging new software technology. So the students of Computer Science are always keeping pace with the changing dynamics of the IT world.
Career Perspective:
There is no iota of doubt that this discipline proffers a dollop of rosy opportunity. Computer Engineers graduate has higher salaries at the outset. They can easily shuffle from hardware or software, or it is a combination of both. Some career paths state below:
1. Computer and Information System Manager:
The professionals in this area supervise the computer activities of the corporation. They implement technology to meet the corporation’s objective.
2.Computer System Analyst:
They help their employees to efficiently use and run the computer technology.
3.Computer Hardware Engineer:
Those Hardware Engineers have a wide range of activities like design, research, development, test, and also supervise the implementation, and installation of circuit boards, and, computer systems. Besides, they also tinker with computer peripherals.
4.Computer Programmer:
The main intention of a programmer is to establish a relationship with hardware and software. With the help of coding by the programmer's force computers to do various works that the people are very much aware of. Without software implementation, the computer is just a showpiece in the showcase. Hence, the utmost importance is attached to the programmer.
5.Computer Support Specialists:
Computer Support Specialists are the troubleshooter for customers' problems or any staff within the organization. This includes software installation, debugging Operation System, and other computer-related problems.
6.Website Developer:
They are mainly responsible for developing the website and maintaining the website.
7. Software Developer:
The basic function of the software developer is to test, designing, installing, and identifying computer systems built by them on the behalf of the corporation. Software Developer also helps to develop an application for the business Once the development of a specific application completes, they take responsibility for maintaining as well as updating the program to make sure all the loopholes of security are plugged and it's ready to operate with a new database. They can make an application that can be used by the corporate for their internal use.
8.Web Master:
Oftentimes, we find sleek websites are abundant in today’s world. Earlier it was just a novelty. But the novelty becomes a serious engine for corporations and businesses. In today’s time, the website plays a pivotal role in the nitty-gritty of the corporate world. The webMaster has to have all the relevant knowledge of the website. The person abreast of all related aspects of the website. He examines the performance of search engines, their speed as well as functionality. Besides, the Webmaster also keeps a tab of the content and other relevant marketing aspects. He may also take part in the administration and server-related activities.
Why students suffer a great deal under the weight of academic commitments:
The concept of education has undergone a sea change in keeping with the current time and age. A newfangled idea sweeps across the educational domain all over the world. Learning and earning at the same time have become the mantra of the current age and time. Apparently, it looks normal. But troubles start brewing to maintain the parity between working and academic commitments.
Besides, when the students dive deep into the subjects and start solving the awkward question, they become confused as they ate unable to solve those difficult questions. At this juncture, they feel quite demotivated and ponder over the possible ramifications. There is no iota of doubt that this mentioned discipline provides an oodles of career prospects. But to make a mark is a daunting task. At this juncture, Textbook Solution Manuals would be the right solution for them.
Do solution manuals act as a panacea for all students' academic ills? Let us explore.
The ever-changing concepts of education are palpable in recent times. Considering today’s time and age, learning and earning are gaining momentum in the sphere of academics. As a result of this, many students do a part-time job in order to support their educational expenses. Therefore, it becomes a difficult task for students to maintain parity between education and work.
Instant slaking is, perchance, be the mantra of today’s world. The famous adage “slow but steady wins the race” relegates to gradual insignificance in the pacy world. At this juncture, they want solution manuals to get around academic predicament. Solution Manuals provide them an instant solution. That is precisely the urgency on part of the students. Besides, the finest techniques the solution manuals are adopted, it is the boon for the students to comprehend it in a better light.
Undoubtedly, textbook answers are an asset for students:
Put down your worries into the dustbin. Textbook Solution Manuals are here to help you get rid of your academic distress. These solution manuals provide them a glimpse of hope and help them to regain their confidence.
At this crossroads, the name that pops up first is Crazy for Study, a trusted and accomplished academic online platform for students. It has already carved out a niche in this domain. Therefore, it is the best podium for students to get straight away homework and assignment solutions.
An enviable repertoire of Textbox Solutions:
It houses an astonishing repertoire of textbook answers i.e. more than 50 million and the good news is you can access the treasure trove paying a small amount of $7 monthly. Put your mental agony at rest as this reliable website provides you sheer legitimacy and bug-free products.
A bagful of advantages using Solution Manuals. Take a tour:
1. Computer Science Textbook Solution Manuals keep you refreshed continuously. Perusing reg ularly, the reader can certainly improve their subjects to a large extent. You can umpteen times revise these manuals and in this process, you may come across different jargons associated with it. Nourished with a dollop of information paves the way for better results especially in competitive exams.
2. You can start at any point in time:
You can start it at the outset. The more you are into this subject, the better you get an insight into the essentials of this. The striking feature of manuals is their flexibility in terms of learning, revise it as many times as you desire.
3. Convenience to carry :
You can carry it anywhere, start reading at any point in time. It is very easy to use. Therefore, it is virtually less burdensome for students to carry on.
4. Know how to use gained Knowledge practically:
The theory is the bedrock of any subject. You must have a sound grip over your subject. Whatever knowledge you have nourished so far is only the half story told, you need an equal amount of practical exposure to comprehend it completely. Textbook solution manuals blend those concepts nicely. Perhaps, no one comes close to compose in such a wonderful way.
5. The complete intolerance of plagiarism :
We are quite intolerable regarding plagiarism.
6. Strict adhere to proofreading:
We strictly adhere to proofreading.
7. Our pride, others envy:
An unmatched pocket-friendly price.
8. Nicely united all pertinent things in one place:
Students often distract due to the presence of a sea of solution manuals. They are in a state of discombobulation. Thanks to textbook solution to contain all things in one solution manual keeping everything in perfect chronologically order. The textbook answers are comprehensive and to put all things in one place is no doubt a commendable feat, so to speak. The main intention of this is to eliminate the complete dependency of teachers and students are in a position to focus on their subject without being digressed.
0 notes
Text
Episode Reviews - Star Trek: The Next Generation Season 5 (1 of 6)
Continuing my reviews of the voyages of Picard’s Enterprise, here’s my first round of reviews for season 5 of Star Trek: The Next Generation.
Episode 1: Redemption (Part 2)
Plot (as adapted from Wikipedia):
Captain Picard is aware that while he cannot get involved in the Klingon civil war, the Romulans will likely see it as an opportunity to gain an advantage over the Federation. He is put in charge of a fleet of ships to create a blockade between the Klingon and Romulan border. Many of the Enterprise crew are assigned temporary command of severely undermanned ships. Picard initially does not assign Lt. Commander Data command of a ship, but after Data questions him about the omission, he gives him the Sutherland. Data’s command of the Sutherland is made somewhat difficult by Lt. Comm. Hobson, who initially seeks transfer because he doesn’t think an android will make a good captain, and when refused is disruptive and disparaging of Data’s command.
Picard arranges the fleet to form a detection network that should detect any cloaked ships that pass the blockade. Commander Sela, a Romulan resembling the late Natasha Yar, orders her scientists to find a way to disable the network, but also contacts the Enterprise. Sela reveals that she is the daughter of Tasha Yar, who returned to the past on the Enterprise-C 24 years earlier (as seen in the episode "Yesterday's Enterprise"). Sela warns that if Starfleet does not break off the blockade in 20 hours, their fleet will be attacked.
Meanwhile, Worf is kidnapped by the Duras sisters, who attempt to seduce him to join their cause by marrying B'Etor. Worf declines, stating that honour would be subverted and that the Klingon Empire would quickly fall to Romulan control. Seeing the cause is defeated, Sela orders Worf to be turned over to the Romulan guard.
Picard urges Gowron to attack the Duras forces, who are running low on supplies; this will force the Romulans to enter the detection network and be caught by Starfleet. Gowron agrees, knowing that association with the Romulans will destroy the Duras family's support and end the civil war. The Duras sisters demand the Romulans bring supplies. Sela's scientists find they can disrupt part of the network by sending out an energy burst. Sela initiates the plan, selecting the Sutherland as the target. When the network destabilizes, Picard orders the fleet to retreat and reform the net, but Data observes that he can trace the source of the disruption. He orders the firing of torpedoes at specific coordinates, revealing Romulan ships. The convoy retreats, and the Duras sisters are forced to end the civil war. Worf breaks free in time to secure Toral, but the Duras sisters escape.
Gowron gives Worf the opportunity to kill Toral by Rite of Vengeance, but he declines to do so because Toral was just a puppet of his aunts. He spares Toral's life and requests Picard to reinstate him into Starfleet.
Review:
This is a decent episode for the season to start off on, and certainly it manages to achieve the main function of the second part in a two-part story, namely bringing the part 1 story to a conclusion. However, it struggles with the weight of additional plots and a certain lack of consistency with part 1. Right out of the gate, Picard is talking about setting up a blockade on the Klingon-Romulan border, and two ideas occur to me. The first is that this is a form of interfering in the affairs of other cultures, highlighting yet again the problem illustrated by part 1 with Trek’s general inconsistency with the prime directive. Secondly, the detection grid set up between the ships can only cover so much space, and there’s nothing to say why the Romulans can’t just fly a circuitous course around the blockade. It’s not like this is Leonidas putting his 300 Spartans at the hot gates to stop Xerxes. This is Trump proposing a wall which boats can sail round and planes can fly over; the Romulans didn’t have to cross through the detection grid at all.
Leaving aside this and the inconsistencies of Trek time-travel that bring about Commander Sela, not to mention the fact that a true daughter of Tasha and anyone would not look like Tasha Yar with a partial Romulan make-up job (they should look like a mix of Yar and whoever the dad was), the episode does do well wrapping things up for Worf, as well as giving Data a great little storyline of his own. In fact, his efforts to deal with the bigoted Hobson while assuming command of the Sutherland is a better story for him than his last solo episode ‘In Theory’. It’s something of a shame it’s mixed in with Picard’s inconsistency on the matter of the prime directive and the Worf plot, which loses a little bit of its impressiveness when you see how anarchic and ill-disciplined the Klingons can be. No wonder events ultimately turn out as they do when Deep Space Nine picked up Worf and all things Klingon after TNG came to an end.
Overall, it’s a decent episode, but as I say, full of quite a few flaws. For me, it only scores 6 out of 10.
Episode 2: Darmok
Plot (as adapted from Wikipedia):
The Enterprise makes contact with a Tamarian ship in orbit around the planet El-Adrel. The Tamarians had been previously contacted by the Federation, but could not be understood; although the universal translator can translate their words, they communicate by using brief allusions to their history and mythology to convey thoughts and intentions. Likewise, the Tamarians cannot understand Picard's straightforward use of language.
The Tamarian captain, Dathon, has himself and Captain Picard transported to the planet's surface. The Tamarians then cast a scattering field that blocks further transporter use. Dathon utters the phrase "Darmok and Jalad at Tanagra" and tosses Picard a dagger; Picard assumes this is an attempt to engage him in battle and refuses, and each captain makes their own fire as night falls. The next morning, Dathon comes running and Picard realizes there is a hostile predator in the area. Picard begins to understand the Tamarians' jargon when he recognizes one allegory as a tactic to fight the beast. The two captains attempt to battle the beast together, but the Enterprise's unsuccessful attempt to beam up Picard prevents him from participating at a crucial moment. Dathon is severely wounded.
On the Enterprise, Commander Riker and the crew struggle to understand the aliens' language. They make several efforts to rescue the Captain, all foiled by the Tamarians. While tending to Dathon's wounds, Picard slowly deduces that Darmok and Jalad were warriors who met on the island of Tanagra and were forced to unite against a dangerous beast there, becoming friends in the process. Dathon tried to recreate this event with Picard, hoping to forge a friendship through shared adversity. Picard recounts for Dathon the Epic of Gilgamesh, a story that parallels the allegory of Darmok and Jalad. Dathon seems to understand the story but succumbs to his injuries.
The Enterprise fires on the Tamarian ship, disabling the scattering field, and beams up Picard. A battle begins, but just when mutual destruction seems certain, Picard enters the bridge and uses his newfound knowledge to communicate with the Tamarians. The Tamarians joyously perceive that Picard's eyes have been opened. Picard offers them Dathon's diary and dagger. The Tamarians tell him to keep the dagger as a gift, and record the incident as "Picard and Dathon at El-Adrel"; a new phrase in their language.
Picard later reads the Homeric Hymns, explaining to Riker that studying their own mythology may help them relate to the Tamarians. He notes that Dathon sacrificed himself in the hope of communication, and wonders if he would have done the same.
Review:
Much like ‘Yesterday’s Enterprise’, this is an episode that seems to have wowed the main fanbase and critics alike, and apparently, it’s had a major impact beyond even that. The episode is used by language courses at American universities to illustrate certain aspects about language, and Picard’s citation of the tale of Gilgamesh caused a surge in that tale’s popularity. However, much like ‘Yesterday’s Enterprise’, I think the episode is over-rated. As an autistic person, I can’t stand people not being anything less than clear, straight-forward and logical in trying to tell me something, so the idea of a race that communicates exclusively through metaphor and allegory is my idea of a nightmare. As such, this episode is my idea of a terrible story.
Granted, the premise is interesting, but I just feel they could have the idea better. Why not just have Picard stranded with an alien with his comm. badge, and the universal translator therein, shot to hell? That way, you’d still have the language struggle, but minus the idea of a language that was all alien cultural references with no guide to what they referred to. If I was trying to teach an alien English, I sure as hell wouldn’t be using references to Star Trek, Marvel comics, DC Comics or anything else I’m into to teach them. I’d teach them the actual words and their meanings, because only then could they understand those stories, which in turn would allow any references to make sense. It’s no wonder a phaser battle between the two ships broke out; personally, if I’d been in Riker’s shoes, I’d have been going down that route far earlier out of sheer frustration.
For me, the idea that any race would communicate like this is frankly unconvincing, just because there is no logic and common sense to a race communicating solely in metaphor. It would be like if human societies communicated entirely in slang without understanding the proper English language to which all the slang terms actually refer. To my mind, the only logical course for any language is to avoid a total metaphor/allegory/slang base and, in time, to keep the use of such things to a minimum or else eliminate them to avoid unnecessary confusion and understanding. For me, this episode is only worth 4 out of 10 (it loses a lot of points over just how much I can’t stand the idea of a purely metaphorical language).
Episode 3: Ensign Ro
Plot (as adapted from Wikipedia):
The Solarion IV settlement is destroyed, and the Bajorans supposedly claim responsibility. Their homeworld Bajor was annexed by the Cardassians generations ago, and the Bajorans have been refugees ever since, with some apparently using terrorism to draw attention from the United Federation of Planets. Captain Picard meets with Admiral Kennelly, who tells him that the Bajoran responsible is a terrorist named Orta. Picard's mission is to find Orta, and to send him back to the Bajoran settlement camps where he can do less damage. Kennelly assigns a controversial person to assist Picard: Starfleet Ensign Ro Laren, a Bajoran whose reputation is very poor and who the admiral has had to release from prison following a court martial. Kennelly insists she can help, and she comes aboard the Enterprise.
Despite a difficult attitude, Ro works with the crew to locate Orta. Ultimately, they head to the third moon Vallor I where they believe he is based. Meanwhile, Ro receives a secret communication from Admiral Kennelly and tells him all is going according to plan. The next day, the away team prepares to beam down, but discover Ensign Ro had preempted them by beaming down six hours earlier. They follow her, and are promptly captured by Orta and his people. Orta, who was disfigured by Cardassian torture, tells them that he felt abducting them was necessary, and says that the Bajorans were not responsible for the attack. Picard finds himself inclined to believe Orta, but confines Ro to quarters for her unauthorized beam down. Guinan, who has befriended Ro, goes to see her, and after learning there is more to what is going on that meets the eye, convinces her to talk to Picard. Ro reveals that she is on a secret mission by Kennelly to offer Orta Federation weapons in exchange for returning to the camps. Given her experiences, she no longer knows what to do or whom to trust. Picard decides that the best course might be to actually take Orta back to the camps, and see what occurs.
However, as the Enterprise escorts a Bajoran cruiser to the camp, two Cardassian ships cross the border and demand the Enterprise leave the ship to them. Picard initially refuses, and the Cardassians give him an hour to reconsider. Far from helping, Kennelly insists that the Cardassian treaty is the more important issue and orders Picard to withdraw. Picard withdraws, and the Bajoran cruiser is destroyed. However, suspecting a chain of events like this might occur, Picard had ensured no one was aboard, and had the ship operated remotely. Picard informs Kennelly that the Bajoran ships are so old and obsolete that they were incapable of even reaching the Solarion IV settlement, much less attacking it, and suggests that the Cardassians staged everything, hoping to find someone like Kennelly, naive enough to help them solve their problems. With the mystery solved and the mission accomplished, Ro accepts Picard's offer to remain in Starfleet and join the Enterprise crew.
Review:
After a couple of lack-lustre opening episodes, season 5 really manages to return to the higher quality that TNG, and indeed all of Trek, is capable of on this one. Not only do we get our introduction to the Bajorans, who become a major component in the eventual Deep Space Nine spin-off, and a repeat appearance by the Cardassians (the last wearing their pre-DS9 uniforms, if I understand Memory Alpha’s notes on this episode correctly), but we also get a fresh secondary recurring character. Actress Michelle Forbes, who initially guest-starred in ‘Half a Life’ in TNG’s previous season, takes up the role of Bajoran Ensign Ro Laren, a character whose impact served to inspire the creations of Major Kira in DS9 and B’Elanna Torres in Voyager. Both characters stem from the same character mould as Ro, and largely because Forbes was unavailable to reprise this role in those shows. As a result, she has ended up remaining a dedicated TNG character.
There’s a lot of reasons why Ro is such a great character. First, she is very much not like the rest of the TNG main cast and recurring guest crew in that she is highly assertive and at times confrontational. In other shows, that can backfire (I believe that’s part of why CSI Riley Adams, played by Lauren Lee Smith, only lasted for one season of CSI’s original Vegas-based show), but in Trek it can be a huge asset in breaking away from any sense that Trek is overly, even unrealistically, utopian. She also brings home that even in the 24th century, we’ve not really solved issues of displacement and terrorism; they’ve just migrated out into the stars, especially when we hide behind treaties and non-interference policies.
Next, Ro also brings out a bit more moral courage in Picard, at least in this episode. He’s far more willing to help and do the right thing in the end, and I think that’s in part down to dealing with Ro. However, what really makes you like Ro is she has Guinan’s seal of approval. Whatever you might think of the character before that moment where Guinan tells Picard that Ro is her friend, that statement is a huge endorsement given the unique and mysterious relationship that exists between Picard and Guinan, and from that Ro in turn earns a lot of credibility with the audience.
If I have any quibble with this episode, it’s how harshly Riker acts towards her over Star Fleet dress code just to make a point, considering both the exceptions made for Worf and Troi and the fact we’re given no idea what Ro has actually done in the past. For all we know, Ro did the right thing and got shafted, or did the wrong thing with the best of intentions, but apparently neither this episode nor any others explain what actually happened. It was left to some tie-in comic, and to my mind that’s a stupid error in judgement. Considering how much Ro’s past was impacting her initial treatment by various crew members, it should have been covered in more detail in this episode or a follow-up episode. Tie-in media is for isolated stories of relatively little significance, whereas Ro’s back story is implied to have great significance here. Overall, I give this episode 9 out of 10.
Episode 4: Silicon Avatar
Plot (as adapted from Wikipedia):
Commander Riker, Lt. Commander Data, and Dr Crusher are visiting the Melona IV colony when the Crystalline Entity appears and begins tearing up the planetary surface. Although the rapid evacuation into the caves is mostly successful, two of the colonists (including one in whom Riker expressed a possible romantic interest) die in the onslaught. The Enterprise comes to the survivors' aid and frees them after the Entity leaves.
The Enterprise sets out in pursuit of the Entity, with the help of Dr Kila Marr, who is a xenobiologist and expert on the creature. Marr does not trust Data, as she is aware that Data's brother Lore has assisted the Entity in the past. Captain Picard hopes to challenge this perception by having Data work closely with Doctor Marr, in spite of Counsellor Troi's worry that his suggestion will not suffice Doctor Marr's feelings of animosity.
While working around the caves of Melona IV, Marr continues to show animosity towards Data. Slightly confused, Data tries to convince that he is nothing like Lore and has no affiliation with the Entity whatsoever. When he asks her what makes her think he had anything to do with the Entity, Marr reveals the source of her prejudice: her 16-year-old son was killed by the Entity at Omicron Theta, which was also Data's homeworld. She even threatens to have Data dismantled piece by piece if she finds out that he is involved with the Entity as she suspects him to be. Picard tells Marr that he does not intend to kill the Entity without first attempting to communicate with it. Marr is sceptical of this approach, but she and Data work out a method for talking to the Entity.
As Dr Marr works with Data, she comes to understand that Data and Lore are quite different androids, recognizing Data's stoic yet virtuous personality and high intellect. During their research, Marr discovers Data is programmed with the memories and experiences of the Omicron Theta colonists, including those of her dead son, Raymond "Renny". Data tells her about how much her son admired her work as a scientist. At Marr's request, Data reads extracts from her son's journals, in the teenager's voice, causing the emotionally moved woman to cry over hearing the sound of her dead son's voice.
The Enterprise locates the Entity and begins sending a series of graviton pulses toward it. The creature responds, and emits a signal pattern which is a clear sign of intelligence. Picard is elated at a potential first contact, but Marr alters the pulse to emit gravitons with a rapidly increasing amplitude, and locks the program so it cannot be stopped as her desire for vengeance wins out. The amplitude reaches a level of resonance where the Entity is shattered. Marr addresses Data as though he is her son, telling him that she destroyed the entity for him.
Having finally taken her long-awaited revenge, but sacrificing her career in the process, Marr is near collapse. A disgusted Picard has Data escort Marr back to her quarters. In her quarters, Marr asks Data how long will he function, and he replies that he was programmed to function for an eternity. Relieved, Marr tells Data that as long as he functions, her son is alive. Speaking to him as if he were her son, Dr Marr pleads to Data that let "Renny" know that she destroyed the Entity for him, in the hopes that her deed will give her son's spirit a sense of peace. However, Data informs her that her son would not have approved of her destroying the Entity, stating that he loved her work as a scientist, and that in her grief over his death, she destroyed that. He states that he cannot help her, leaving Dr Marr struggling to deal with Data’s response.
Review:
For fans of the Trek films who enjoyed the Moby Dick parallels in TNG’s ‘First Contact’ film, this episode is another example of the Next Gen crew getting to explore that kind of narrative, only with a guest character taking on the role of Captain Ahab against the Crystalline Entity acting as the white whale. It’s an interesting premise to explore, as is Data being able access the memories and writings of the colonists from his home planet. It’s an interesting aspect of Data that is seldom explored, and it’s good to see that getting a look in for once.
However, for me this episode is let down by Picard saying ‘we’re not going out to kill this thing, let’s see if it can be communicated with’. Um, Picard? Lore communicated with the damn thing twice; once to destroy the Omicron Theta colony and once to try and destroy the Enterprise. That means that not only has it been proven by the anti-Data that this thing can be communicated with, but that it is not ‘simply feeding’ as if the damn thing’s a force of nature. Forces of nature don’t communicate with androids, unless this is somehow the Trek equivalent to Marvel’s Galactus and Lore was playing herald (and frankly I doubt that scenario). It’s yet another example of a Trek episode undone by a combination of inattention to continuity and a slavish devotion to the oft-unrealistic idealism of Roddenberry. As a result, I give it only 6 out of 10; if the communication angle had been more about learning how Lore did it and less an attempt to discover the already discovered, it might have earned more.
Episode 5: Disaster
Plot (as adapted from Wikipedia):
The crew of the Enterprise are undertaking routine tasks when suddenly the ship is struck by some outside force, rendering much of it inoperable and many of the crew isolated without communication to other sections. Later the crew discovers the collision was with a fragment of a quantum filament, and after effecting basic repairs, set course back to the nearest starbase for a full overhaul.
Several different sub-plots are followed among the various crew members:
The bridge is manned by Counsellor Troi, the most senior officer on the bridge at the time of the incident with the rank of Lt. Commander, accompanied by Chief O'Brien and Ensign Ro. They soon establish that Lt. Monroe died in the incident. They find that the anti-matter containment field in Engineering is rapidly fading. Ro suggests that they split the drive section of the Enterprise off to save those in the saucer section, but O'Brien considers this cold-blooded and Troi rules against it. Instead, she suggests a plan to divert a supply of their minimal power reserves to Engineering to the appropriate panel, hoping that someone there would rectify the situation. This is later done by Commander Riker and Lt. Commander Data. Ro apologizes for considering such a hasty action while Troi acknowledges Ro could have easily been correct.
Riker and Data are in Ten Forward along with Lt Worf and a pregnant Keiko O'Brien at the time of the disaster. With many crewmembers injured, Data assigns Ten Forward as a triage area with Worf and Keiko tending to the wounded. Riker and Data realize that without functioning turbolifts, it would be faster to travel through the Jefferies tubes to reach Engineering in order to regain control of the ship rather than to try to make it to the bridge. In Engineering, they find that the computer remains offline and Data offers to use his own positronic brain to gain basic control of ship systems. Riker discovers the operating panel that indicates the containment field failure, and he and Data quickly set up the proper connections to restore it until regular computer operation is restored.
Captain Picard is giving a guided tour of the ship to three children that won a science fair, a task he has not been looking forward to as he is uncomfortable around children. They are aboard the turbolift when the accident occurs and Picard fractures his ankle from the sudden stop. He calms the children down, and to boost their morale, assigns them honorary command roles. With their spirits renewed, Picard and the children start to climb out of the turbolift and up the shaft until they are able to access the lift doors on another floor and climb out safely. Picard comes to appreciate the children and offers to give them another tour once the situation has been resolved.
Dr Crusher and Lt. Commander La Forge are in a cargo bay taking inventory while Crusher tries to encourage La Forge into performing a song from ‘The Pirates of Penzance’. When the disaster strikes, they are trapped in the bay and find that a plasma fire has erupted in a nearby panel; it is not only letting off potentially lethal radiation affecting them, but also destabilizing some nearby chemical canisters, risking an explosion. They come up with a plan to depressurize the bay to douse the fire due to lack of oxygen and remove the destabilizing chemicals during the depressurization. They safely hold on during this process and reseal the bay with air.
In Ten Forward as they tend to patients, Keiko goes into labour, forcing Worf to help her deliver her child despite having only basic emergency medical training. Though the delivery is tense, Keiko's child, Molly, is delivered safely.
Review:
For me, this episode doesn’t live up to its title in that it’s, well, not a disaster. Out of this homage to the disaster film concept, we get some decent character development for Picard (overcoming his discomfort around children), Troi (her first time assuming command of the Enterprise, though ultimately not her last) and Worf (nothing like making a Klingon play mid-wife to expand him beyond his warrior archetype). DS9 fans would do well to watch this episode just to see the birth of Molly O’Brien and understand Worf’s reaction when he learns of Keiko’s second pregnancy. It’s a fun break from the standard TNG episode as well, its originality and the above instances of character development compensating well for any lack of issues to be explored. All in all, I give the episode top marks; 10 out of 10.
0 notes
Text
Quad Eight Vst Plugin

Free Vst Plugins Download
New Free Vst Plugins
Free Trap Vst Plugins
Quad Eight Vst Plugins
Vst Plugins For Fl Studio
The complete UAD Ultimate 8 bundle includes over 100 VST plugins developed by U Audio. Includes Cambridge EQ, Galaxy Tape Echo, Precision Maximizer, and many more. The Manny Marroquin EQ plugin captures the best of the SSL 9080 XL K, Quad 8, Motown, Neve 1073, API 550B and Avalon 2055 and puts them all together in one plugin.
Analog Just Got Warmer
Vacuum Pro is a polyphonic analog synthesizer with vacuum tube circuit modeling that perfectly captures the crunchy, warm sound of the analog era. With four analog oscillators, multiple filters and envelopes, and built-in audio effects, Vacuum Pro lets you dive deep into subtractive synthesis to recreate those sought-after analog sounds from the 70s and 80s. Tweak the switches, knobs, and dials to program anything from basses, leads, pads, or unique sound effects. For even more warmth, Vacuum Pro has six virtual vacuum tube circuits that add crunch and grit at every stage of the signal path. Analog just got a whole lot warmer.
Free Vst Plugins Download
SampleScience creates plugins and sample libraries for electronic musicians.
VST instruments (VSTi) version: VST 2.4/3.6 compatible: PLUG-OUT Hardware 2: SYSTEM-8: CPU: Intel® Core™ i5 or better (Quad-core CPU recommended) RAM: 4 GB or more: Hard Disk: 100 MB or more: Display resolution and Colors: 1280 x 800 dots or higher, 24 bits Full Color or more: Other: You'll need Internet connectivity to activate this software.
Vintage Vibes
Vacuum Pro is a powerful combination of two separate synthesizer parts that can be stacked, split, and layered to produce big, wide, and fat analog sounds. Each Vacuum Pro part starts with two wide-range, vacuum tube oscillators that can be synched, detuned, and set to various octave levels. Plus, Quad Detune controls per oscillator make it easy to quickly dial in lush sounds. For an even bigger sound, the built-in Doubling effect instantly widens and thickens up your patch.
Shape your sound with two vacuum tube filters that include a traditional low-pass filter and a selectable high-pass/band-pass filter. Vacuum Pro also has four envelope generators, matrix-assignable modulation, and a tempo sync’d LFO. The mixer offers a drive circuit and a tone-warping ring modulator. For authentic analog behavior, the Age controls let you manipulate the drift of and add dust to your sounds.
Programming Powerhouse
Vacuum Pro comes complete with 350+ tweakable patches created by acclaimed sound designers Richard Devine and Mark Ovenden. You can load these patches separately into each Vacuum Pro part to combine and experiment with multi-timbral sounds. For instant sound inspiration, Vacuum Pro features Smart Sound Randomization, which randomly generates new settings for either part or both. Define which modules you want to lock at their current settings, which will be randomized, and then let Smart Sound dial in a patch for you.
Global Control
Vacuum Pro’s Smart page condenses all the individual parameter controls into eight macro knobs that enable you to quickly shape the sound of your patch without extensive tweaking. Macro knobs such as Punch, Emphasis, and Complexity add an intuitive workflow for perfecting your programming. Switch back and forth between the micro and macro modes to quickly edit or create your own custom sounds.
Vst free download mac. What are your favorite free VST instruments? Posted by 6 years ago. Awesome free mac and pc (32/64 bit) sfz player. Free sfz sound pack. Sonatina as mentioned earlier. And a cool piano sfz. Help Reddit App Reddit coins Reddit premium Reddit gifts. Windows 32bit/64bit VST; Mac 32bit/64bit Audio Unit. 32bit 64bit AU mac pc piano VST yamaha. Share Facebook Twitter Google+ ReddIt WhatsApp Pinterest Email. You might also like More from author. Noizefield – Warrior – Free Wavetable VST Synth. Effectrix Vst Free Download Reddit Download Sugar Bytes Effectrix v1.4.3 Free Download Latest Version r2r for MAC OS. It is full offline installer standalone setup of. Download the Best Free Audio Plugins. Synths, Reverbs, Compressors.and much more. Just click and download. Browse our ever growing library of free VST plugins to use in your productions. The best free VST's to download. Browse our ever growing library of free VST plugins to use in your productions. Surge – Free Synth For PC, Mac & Linux. EasyGater – Free Trance Gate Plugin. GŌN – Free Metering Plugin For PC & Mac.
Extra Effects
In addition to its authentic analog sound, Vacuum Pro includes a host of creative tools that are characteristic of classic analog synthesizers. An onboard arpeggiator, which can be tempo sync’d to your DAW, offers a quick way to build melodic runs and short sequences. A built-in chorus/phaser and delay effects give life and motion to your Vacuum Pro patches. Onscreen pitch bend and modulation wheels add extra expression to any performance, and all parameters are MIDI-mappable for performance ease and automated control.
AIR Music Technology is a trademark of inMusic Brands, Inc., registered in the U.S. and other countries. All other product or company names are trademarks or registered trademarks of their respective owners. Product features, specifications, system requirements, and availability are subject to change without notice.
Synthetic VST Plug-In
Synthetic is a quad oscillator subtractive VST plug-in made for layering and modulation. This is a great synth for creating pads or space textures and it's totally free!
New Free Vst Plugins
Specs
Type: Subtractive
Included Presets: 128
Polyphony: 1, 4, 8 , 16
Oscillators: 4
Waveforms: Sine, Saw, Triangle, Square, Tri-Sine, Supersaw, Noise
Filter: LP, HP BP, BR, Peaking
Effects: Reverb, Delay, Chorus, Distortion, Stereoizer
Keyboard: Built-in
Modulation: 2 LFO, 4 Envelope
Modulation Routing: 6 available
Trancegate: 16 step stereo
Portamento: w/Slide

Features
Quad Oscillators
The oscillator system in Synthetic is made up of two groups. Each group consists of two oscillators, a filter, and an envelope. Each oscillator has seven waveforms available: sine, saw, triangle, square, noise, supersaw, and tri-sine. There are five types of filters to pick from in each group: low pass, high pass, band pass, band reject, and peaking.
Built-in Effects
Free Trap Vst Plugins
Synthetic includes five built-in effects: reverb, ping-pong delay, chorus, distortion, and a stereoizer.
Factory Sounds
Quad Eight Vst Plugins
Synthetic comes pre-loaded with 128 presets! Including basses, leads, pads, strings, & more. Save and load abilities make it possible to create and share your own sounds!
Ableton non-vst plugin. Ableton had severe delay in automation on VSTs as soon a projects got complex. Cubase was too much of a hastle to set up something simple as a sampler. Logic felt counter intuitive in the wave editting area. Also support for my Access Virus TI was annoying as hell.
AVAILABLE FOR FREE
Download Synthetic for free. Show your support by liking our Facebook page, and sharing with friends.
Requirements
Windows XP/Vista/7 (Windows only)
512 MB RAM (1+ GB recommended)
Pentium III or better (or AMD equivalent)
SSE processor support
DAW or host for VST
ASIO driver recommended
Vst Plugins For Fl Studio
Bits: 32

0 notes
Text
Parallel Input Serial Output Shift Register Verilog Code

8-bit parallel-in/serial-out shift register
The testbech for the Serial shift register Serial Input Serial Output Shift Register Exercizes 1. In test bench the shift register is instantiated with N=2. Verify that it behaves as expected. Repead the testbench and verification for N=4 2. Write the above code for left shift in place of right shift. The data now comes out of the MSB. Design of 4 Bit Parallel IN.Output. Need vhdl code for 16 bit serial-in, serial-out shift register. 4-bit parallel shift register code. Bit serial arithmetic Vs Digit serial Arithmetic. 4 Bit Sipo Shift Register Vhdl Code Vhdl code for 4 bit shift register allaboutfpgacom, vhdl code for shift register can be categorised in serial in serial out shift. The following code models a four-bit parallel in shift left register with load and shift enable signal. Module Parallelinserialoutloadenablebehavior(input Clk, input ShiftIn, input 3:0 ParallelIn, input load, input ShiftEn, output ShiftOut, output. The following code models a four-bit parallel in shift left register with load and shift enable signal. Module Parallelinserialoutloadenablebehavior(input Clk, input ShiftIn, input 3:0 ParallelIn, input load, input ShiftEn, output ShiftOut, output. In Parallel In Serial Out (PISO) shift registers, the data is loaded onto the register in parallel format while it is retrieved from it serially.Figure 1 shows a PISO shift register which has a control-line. And combinational circuit (AND and OR gates) in addition to the basic register components fed with clock and clear pins.

The 74LV165 is an 8-bit parallel-load or serial-in shift register with complementary serial outputs (Q7 and Q7) available from the last stage. When the parallel-load input (PL) is LOW, parallel data from the inputs D0 to D7 are loaded into the register asynchronously. When input PL is HIGH, data enters the register serially at the input DS. It shifts one place to the right (Q0→Q1→Q2, etc.) with each positive-going clock transition. This feature allows parallel-to-serial converter expansion by tying the output Q7 to the input DS of the succeeding stage.
The clock input is a gate-OR structure which allows one input to be used as an active LOW clock enable input (CE) input. The pin assignment for the inputs CP and CE is arbitrary and can be reversed for layout convenience. The LOW-to-HIGH transition of the input CE should only take place while CP HIGH for predictable operation. Either the CP or the CE should be HIGH before the LOW-to-HIGH transition of PL to prevent shifting the data when PL is activated.
Features and benefits
Wide supply voltage range from 1.0 V to 5.5 V
Synchronous parallel-to-serial applications
Optimized for low voltage applications: 1.0 V to 3.6 V
Synchronous serial input for easy expansion
Latch-up performance exceeds 250 mA
5.5 V tolerant inputs/outputs
Direct interface with TTL levels (2.7 V to 3.6 V)
Power-down mode
Complies with JEDEC standards:
JESD8-5 (2.3 V to 2.7 V)
JESD8B/JESD36 (2.7 V to 3.6 V)
JESD8-1A (4.5 V to 5.5 V)
ESD protection:
HBM JESD22-A114-A exceeds 2000 V
MM JESD22-A115-A exceeds 200 V
Specified from -40°C to +85°C and from -40°C to +125°C
Parametrics
Type numberVCC (V)Logic switching levelsOutput drive capability (mA)tpd (ns)fmax (MHz)No of bitsTamb (°C)Rth(j-c) (K/W)74LV165DProduction1.0 - 5.5TTL± 1218788low-40~125919.351SO1674LV165DB NRNDNot for design inSSOP1674LV165PWProduction1.0 - 5.5TTL± 1218788low-40~1251203.348.7TSSOP16
Package
PackagePackage informationReflow-/Wave solderingStatus74LV165D SO16 (SOT109-1)SOT109-1SO-SOJ-REFLOW SO-SOJ-WAVE Reel 13' Q1/T1Active74LV165D74LV165D,118 (9351 560 60118)Bulk PackActive74LV165D74LV165D,112 (9351 560 60112)74LV165DB NRND SSOP16 (SOT338-1)SOT338-1SSOP-TSSOP-VSO-REFLOW SSOP-TSSOP-VSO-WAVE Reel 13' Q1/T1ActiveLV16574LV165DB,118 (9351 660 30118)Bulk PackActiveLV16574LV165DB,112 (9351 660 30112)74LV165PW TSSOP16 (SOT403-1)SOT403-1SSOP-TSSOP-VSO-WAVE Reel 13' Q1/T1ActiveLV16574LV165PW,118 (9351 745 40118)Bulk PackActiveLV16574LV165PW,112 (9351 745 40112)
Quality, reliability & chemical content
Leadfree conversion date74LV165D74LV165D,11874LV165Dweek 6, 2004144.910.239.78E71174LV165D74LV165D,11274LV165Dweek 6, 2004144.910.239.78E71174LV165DB NRND74LV165DB,11874LV165DBweek 12, 20051174LV165DB NRND74LV165DB,11274LV165DBweek 12, 20051174LV165PW74LV165PW,11874LV165PWweek 17, 2005144.910.239.78E71174LV165PW74LV165PW,11274LV165PWweek 17, 2005144.910.239.78E711
Quality and reliability disclaimer
Documentation (10)
File nameTitleTypeDate74LV1658-bit parallel-in/serial-out shift registerData sheet2017-03-17Nexperia_Selection_guide_2020Nexperia Selection Guide 2020Selection guide2020-01-31SO-SOJ-REFLOWFootprint for reflow solderingReflow soldering2009-10-08SO-SOJ-WAVEFootprint for wave solderingWave soldering2009-10-08SOT109-1plastic, small outline package; 16 leads; 1.27 mm pitch; 9.9 mm x 3.9 mm x 1.35 mm bodyPackage information2020-04-21SSOP-TSSOP-VSO-WAVEFootprint for wave solderingWave soldering2009-10-08SOT403-1plastic, thin shrink small outline package; 16 leads; 5 mm x 4.4 mm x 1.1 mm bodyPackage information2020-04-21SSOP-TSSOP-VSO-REFLOWFootprint for reflow solderingReflow soldering2009-10-08SSOP-TSSOP-VSO-WAVEFootprint for wave solderingWave soldering2009-10-08SOT338-1plastic, shrink small outline package; 16 leads; 0.65 mm pitch; 6.2 mm x 5.3 mm x 2 mm bodyPackage information2020-04-21
Support
If you are in need of design/technical support, let us know and fill in the answer form, we'll get back to you shortly.
Ordering, pricing & availability
Sample
As a Nexperia customer you can order samples via our sales organization or directly via our Online Sample Store: https://extranet.nexperia.com.
Sample orders normally take 2-4 days for delivery.
If you do not have a direct account with Nexperia our network of global and regional distributors is available and equipped to support you with Nexperia samples.
greatworks.netlify.com › Parallel Input Serial Output Shift Register Verilog Code ▄
Shift Register using verilog
I wrote a parallel in serial out shift register, which I present here. Module shiftreg32b (clk, reset, shift, carrega, in, regout); input clk; input reset, shift; input to an output in a combinational module in Verilog Verilog Illegal Reference to net 'OUT' What does this Verilog module do? It contains many explicit features which include parallel inputs, parallel outputs, synchronous reset, bidirectional serial input and bidirectional serial output. The below presented verilog code for 4-bit universal shift register acts as a uni-directional shift register for serial-in and serial-out mode,. Verilog Code for Parallel in Parallel Out Shift Register - Free download as Word Doc (.doc /.docx), PDF File (.pdf), Text File (.txt) or read online for free.
We will now consider a shift register. Our shift register has an s_in input entering on its left hand side. At each clock cycle, the content of the register shifts to the right and s_in enters into the leftmost bit or the MSB bit. The whole design also has and output that we are c calling s_out. At each clock cyccle the right most bit of the register comes out. The picture shows the scheme of the shift register. Here is the verilog implemmentation of shift register.
Explanation
Initially the reg value of undefined and hence we have placed 4'bxxxx in its value. Because of the assign statement the initial value of s_reg[0] is also 0. When the reset pulse is applied the r_reg becomes 0000 at the next rising edge of clock. Note that the period of the negative level of the reset sould last at least to the next rising edge of the clock At this stage, the value of s_out also becomes 0 ( right after the rising edge of the clock). Now the s_in value is supplied sometimes before the next rising edge of the clock. Now because of the assign statement the wire r_next is driven by the value of s_in and [3:1] bits of r_reg. And so, after the application of the s_in, at the next rising edge of the clock, the statement in the always loop takes effect. which essentially results in updating the r_reg value with its value shifted to right and s_in coming in at its MSB. The testbech for the Serial shift register
Serial Input Serial Output Shift Register
Exercizes 1. In test bench the shift register is instantiated with N=2. Verify that it behaves as expected. Repead the testbench and verification for N=4
Shift Register In Verilog
2. Write the above code for left shift in place of right shift. The data now comes out of the MSB. The data enters from LSB.
Parallel Load Shift Left Register verilog code
4 Bit Shift Register Verilog
This page covers Parallel Load Shift Left Register verilog code and test bench code of Parallel Load Shift Left Register.
Parallel Load Shift Left Register verilog code
Following is the verilog code of Parallel Load Shift Left Register.
module plsl(pl, sl, slin, Din, clk, reset, Q); input pl, sl, slin, clk, reset; input [7:0] Din; output [7:0] Q; reg [7:0] Q; always @ (posedge clk) begin if (~reset) begin if (sl) begin Q <= 'TICK {Q[6:0],slin}; end else if (pl) begin Q <= 'TICK Din; end end end always @ (posedge reset) begin Q <= 8'b00000000; end endmodule
Test code for Parallel Load Shift Left Register
Following is the test bench code of Parallel Load Shift Left Register.
I checked with Auto Installer. Edited 22 Feb 2017 by lamboom. And get this: After loading data, this window pops up stating that Sysmac is Up-to-Date. Then what's going on with 'Windows Configuring Sysmac Studio???? Sysmac studio v1.19.
module main; reg clk, reset, slin, sl, pl; reg [7:0] Din; wire [7:0] q; plsl plsl1(pl, sl, slin, Din, clk, reset, Q); initial begin forever begin clk <= 0; #5 clk <= 1; #5 clk <= 0; end end initial begin reset = 1; #12 reset = 0; #90 reset = 1; #12 reset = 0; end initial begin sl = 1; pl = 0; Din = 8'h42; #50 sl = 0; #12 pl = 1; #5 Din = 8'h21; #20 pl = 0; sl = 1; end initial begin forever begin slin = 0; #7 slin = 1; #8 slin = 0; end end endmodule
Verilog source codes
Low Pass FIR Filter Asynchronous FIFO design with verilog code D FF without reset D FF synchronous reset 1 bit 4 bit comparator All Logic Gates
RF and Wireless tutorials
WLAN802.11ac802.11adwimaxZigbeez-waveGSMLTEUMTSBluetoothUWBIoTsatelliteAntennaRADAR Drivers ed 4.02 assignment answers.
Share this page
Translate this page
ARTICLEST & M sectionTERMINOLOGIESTutorialsJobs & CareersVENDORSIoTOnline calculatorssource codesAPP. NOTEST & M World Website

0 notes
Text
Who Is Responsible for Meeting Website Accessibility Compliance?
New Post has been published on http://tiptopreview.com/who-is-responsible-for-meeting-website-accessibility-compliance/
Who Is Responsible for Meeting Website Accessibility Compliance?

The pandemic of 2020 has changed the lives of everyone.
Were businesses and schools ready to meet the challenges for website accessibility compliance?
Adapting to new ways to work remotely or go to school was not always effortless, especially for persons with disabilities.
And meeting accessibility compliance historically took a back seat to just about every other business goal, creating a business risk.
Though remote work provided some with opportunities to continue to conduct business online, consumers and students quickly uncovered all the ways in which they could not do their work – preventing people from:
Doing their jobs.
Taking tests.
Completing assignments.
Holding meetings.
Ordering supplies during quarantines.
This created frustration on top of an already difficult time.
Somebody needed to be responsible.
For digital marketers, the rumblings about website accessibility may be unimportant until a client receives a demand letter or worse.
Getting an ADA accessibility lawsuit creates alarm, followed by confusion over the next steps.
Advertisement
Continue Reading Below
While the client is wrestling with this new expense, they may even ask why they were never made aware their website or mobile app was not accessible.
There have also been increasing concerns like:
Who is responsible for building websites, software, and mobile apps that not only are accessible but adhere to the accessibility laws of the country or state they reside in?
Is it ethical to create search engine marketing strategies for websites that are not tested for accessibility compliance?
Why is accessibility testing not included in usability testing, user research, software testing, and split testing of landing pages?
Are marketers, web designers, and developers legally liable if a client’s digital property fails to meet accessibility compliance requirements?
A Changing Work & Home Life Environment
It is estimated that 1.4 billion people around the world have a disability or impairment.
They are treated differently and even ignored in some countries.
The stigma with imperfection means that many people hide their impairments such as failing eyesight, dyslexia, or the inability to remember what they just read.
When companies sent their employees home to work remotely many adjusted to sharing bandwidth and computers with other members of the household.
Parents became teachers.
Students became bored.
Employees met on Zoom.
The time saved from not having to commute to work allowed for more time to study, practice skills, and for creating new projects.
Advertisement
Continue Reading Below
Some companies clearly thought it was high time to mess with our heads and make unexpected changes to their existing products.
Like changing Google’s branded icons into something that increases errors because we no longer understand what each icon refers to anymore.
Or that Facebook’s new user interface redesign better resembles a corn maze.
Or that the new Google Analytics is not even recognizable anymore.
It doesn’t seem logical to see so much attention on changing branded icons and user interface layouts when there are millions of people trying to work and study at home and facing accessibility barriers.
Gathering Data
Marketers look to data to decide how to improve page optimization for search engines and adjust marketing strategies.
They especially watch how Google is ranking webpages.
And the research into search behavior is extensive.
But even Google’s Core Web Vitals does not look to accessibility as a metric.
The use of assistive devices such as screen readers could provide some insight into how many students depend on them to access assignments by their teachers.
What is the performance like?
What computer devices were used?
Does speed matter to someone who listens to a page?
How about the student who needs more time to take notes from a page heavy on text?
Mobile is Google’s darling, but for many people with disabilities, it isn’t.
I record webpages for my clients with the MAC VoiceOver and Safari combination screen reader.
Listening to what their webpages sound like helps to understand the user experience for people who are blind, sight-impaired, or have reading and cognitive difficulties.
Little else makes an impression than hearing what you designed or built.
Nothing sells better than proof.
The Motivation for Web Accessibility
There has to be motivation other than the threat of ADA lawsuits to make companies care about persons with disabilities.
Regular accessibility testing and site compliance audits should be part of all design and development planning and QA procedures.
In addition to budget restraints, there aren’t enough developers trained in accessibility design for websites, mobile apps, and software.
Advertisement
Continue Reading Below
For many WordPress platform-dependent site owners, failing to meet WCAG 2.1 AA guidelines is common because theme remediation can be difficult.
And for third-party plugins, it’s next to impossible.
Welcome to 2021.
The rules have changed.
Accessibility Overlays
Imagine if you require a wheelchair to get into a store but before you can enter you must first:
Paint the lines for your handicapped parking spot.
Order the handicapped parking sign.
Build the ramp into the sidewalk.
Install the automatic door opener.
Redesign the aisles to allow more room for you to move around in.
That’s what an accessibility widget does.
Before a person with a disability can enter the website, they need to design it to work for them first.
This is discrimination.
There is no such thing as a perfectly accessible website or application that will automatically work for everyone with a disability.
The reality is that automatic accessibility overlays working in the background are a cheat based on false promises.
Despite the clever marketing and video of the convincing guy insisting your days of worrying about owning an accessible website are miraculously over.
Advertisement
Continue Reading Below
Artificial intelligence cannot replace humans.
We are each unique. Our brains are different.
We use computers in unique ways and depend on them to work when and how we need them.
Every time we tell ourselves that we know better than anyone else how a webpage should be used, we remove the right to choose what works for persons with impairments or disabilities and their specific needs.
Most people choose their own settings in their computer devices and browsers to help them interact with webpages and apps.
Accessibility widgets that override their settings, mimic, or conflict with them are not helpful.
The message sent by accessibility overlays and widgets is that your company didn’t bother to design and develop an accessible website and gave the whole experience to AI.
This raises a flag to legal firms looking for websites to sue.
The Accessibility Legal Landscape
Web accessibility litigation in the U.S. for 2020 shot up and shows no signs of slowing down.
Advertisement
Continue Reading Below
The U.K. and Ontario escalated their accessibility requirements, too.
What you should know:
1. ADA Laws in the U.S. as They Pertain to Websites Remain Unclear
There is a lack of precise ADA guidelines on websites up to this point.
The exception is Section 508 for government and GSA contract websites.
2. Serial Plaintiffs Look for Websites to Sue
Decisions differ by state and plaintiffs can sue outside their own state.
Serial filers are sometimes known as “testers of compliance” and plaintiffs do not need to use your website to be able to file a complaint.
Also, there is no limit on cases.
One well known serial plaintiff with a physical disability filed approximately 500 cases since October 2019.
3. What to Do After Receiving a Demand Letter
If you receive a demand letter, contact a lawyer who specializes in ADA and accessibility law immediately.
4. There Is No ADA Law in the U.S. Enforcing the WCAG Standard for Public Websites
However, related laws and various circuit court judgments are chipping away with decisions based on ethics and non-discrimination.
Advertisement
Continue Reading Below
5. The Ontarians With Disabilities Act (AODA) Takes Effect January 1, 2021
The AODA requires all digital content to conform to WCAG2.0 AA standards by January 1, 2021.
There are fines for non-compliance.
They provide online guidance, site testing, training, and filing compliance report policies.
6. WCAG 2.1 Adoption in Europe
The U.K. updated EN 301 549 which specifies the accessibility requirements for ICT products and services.
The standard to meet is WCAG2.1 AA.
Websites and mobile apps must provide an accessibility statement.
The deadline for meeting their digital accessibility regulations was September 23, 2020
In the U.S., on October 2, 2020, a bill called the “Online Accessibility Act” (H.R. 8478 – the “OAA”) was introduced.
It would amend the present ADA to add a new Title VI prohibiting discrimination by “any private owner or operator of a consumer-facing website or mobile application” against individuals with disabilities.
Already coming against a negative reception by disability rights advocates, this latest attempt has a similarity to H.R. 620 which never got past the House in the present administration.
Advertisement
Continue Reading Below
This is because it placed the burden on the person with disabilities to pursue and subsequently wait for remediation to occur.
The OAA allows 90 days for remediation of a complaint.
If not satisfied, then it goes to the Department of Justice, which has 180 days “to investigate.”
Steps to Take Now to Protect Your Business
There are automated tools that are free to use that provide a quick assessment of the most common accessibility issues on websites.
It’s important to note that they catch about 25% of the problems and don’t replace manual testing.
WCAG 2.2 is in draft format now, with an expected release next summer.
One of the additions is a change to the guidelines for the focus state, which is what we see when we navigate without a mouse.

Use CSS to enhance the focus state.

Web Developer Tools offer a built-in accessibility section that can be added to.
Advertisement
Continue Reading Below
Developers also have their own preferences.
Web developer tools can be enhanced to include additional testing tools for accessibility.


A different example of web developer tools in Firefox.

High on the list for manual testing is looking at the way headings are structured.
Not only are heading tags important for SEO, but they are also of particular interest for screen reader users who sort content by them.
WCAG2.1 spells out guidelines for headings that include making sure there is only H1 on a page.
If you look carefully, you will see a duplicate heading below, which is technically a failure, and even worse would be if both were linked to the same landing page.
Even if the page looks like it makes sense visually, with a screen reader the experience is very different.

If you were to listen to this page with a screen reader, you may wonder what’s behind “Everything you need to find.”
Advertisement
Continue Reading Below
For accessibility, understanding content in context makes even more sense when you listen to your content.
Descriptive headings and link anchor text requirements appear more obvious when you listen and hear what’s missing from your presentation.
The ability to manually look for areas to improve accessibility is easier with the proper tools.

No accessibility testing is complete without manual testing.
There are various tools available for web developers to use to help identify any issues.
Moving around a webpage without a mouse is a manual test performed by pressing the TAB key on your keyboard.
Advertisement
Continue Reading Below
The reading order should begin with a Skip to Content link, which should be there (and if not, it should be).
Each TAB key click should proceed to the next link in the DOM and is highlighted visually with a focus state.
Common errors with manual keyboard testing are:
The focus state disappears as it goes through the navigation and sub-levels.
Site search.
The sudden appearance of ads and pop-ups.
Sometimes Accessibility Compliance Is Difficult
For those who develop a serious interest in building inclusive websites or mobile apps, there is a large community of accessibility advocates, educators, and certified accessibility specialists who make themselves available.
There are free podcasts and videos providing instruction on how to make documents accessible, and how to use screen readers.
Look for webinars. Many are free.
There are guidelines for colors, images, layout, understandability, and compatibility with a broad range of user agents.
The most difficult is learning Accessible Rich Internet Applications or ARIA – which can conflict with HTML5 – but is necessary for screen readers to figure out what’s happening on each page.
Advertisement
Continue Reading Below
Who Is Responsible for Accessibility Compliance?
We are responsible for the content on our webpages.
This includes our videos, podcasts, forms, themes, and interactive elements.
It’s a lot to ask of beginners.
And for those who opt for ready-made websites, it’s a risk they may be unaware of.
Do yourself a favor and get an accessibility site audit done.
Hire a consultant or find an agency that offers accessibility testing as a service in addition to designing web sites or marketing them.
Add accessibility testing to your in-house projects.
It wouldn’t make any sense to produce products that are not ready to work for everyone.
Hire agencies that test with people with disabilities.
They are your best investment.
In 2021, you may be required to own an accessible website, mobile app, or online software application.
The best offense is knowing what you need to know.
Join me on January 12 at the SEJ eSummit where I deliver a presentation on “The Emergency Guide to Website Accessibility Compliance.”
Advertisement
Continue Reading Below
More Resources:
Image Credits
All screenshots taken by author, November 2020
if( !ss_u )
!function(f,b,e,v,n,t,s) if(f.fbq)return;n=f.fbq=function()n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments); if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version='2.0'; n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0]; s.parentNode.insertBefore(t,s)(window,document,'script', 'https://connect.facebook.net/en_US/fbevents.js'); fbq('init', '1321385257908563');
fbq('track', 'PageView');
fbq('trackSingle', '1321385257908563', 'ViewContent', content_name: 'website-accessibility-compliance-who-is-responsible', content_category: 'web-development ' );
// end of scroll user Source link
0 notes
Text
A Conflict of Interest with Electrical Inspectors?
Should electrical inspectors be allowed to perform work in the same town where they’re inspecting? Does this scenario create a conflict of interest in any way?
Many smaller towns have part-time electrical inspectors. These inspectors usually have their own businesses, in addition to their inspector positions. This juggling makes sense. If their job is only part- time, how are they going to pay their bills? Over the years, I’ve dealt with these inspectors numerous times. Quite frankly, I never felt like the inspector was being unfair in any way—even when their company was one of our competitors.
I have countless stories about inspectors. I always wanted to share my stories, but I never had the platform to do so until our company launched this blog. Of all my stories, the following one is undoubtedly my favorite. Before this inspection, I honestly thought I’d seen it all, but this one threw me for a loop!
We completed a job involving knob and tube replacement in a North Shore town in Massachusetts. I won’t mention the name of the town, even though I probably should because this inspector’s behavior was quite shady.
As many of you may already know, knob and tube replacement is a mainstay of our business. We specialize in it, and we often simultaneously do two or three replacement jobs year-round. So yeah, we do A LOT of these jobs, and we like to think we do them better than anyone else.
Since I get along really well with the head electrical inspector of this town, I was looking forward to seeing him at the job. Unfortunately, he was on vacation that week and the assistant inspector wasn’t available either. I was assigned a backup inspector whom I’d never met.
When the inspector pulled up, I was sitting outside on the front stairs waiting for him. As he got out of his car and started walking toward me, I got this really weird feeling. He was looking at me in a very odd way. Right away, I could sense some negative energy. But I was polite and said, “How are you doing?” He replied, “Fine. What’d you do here?” I told him, “Knob and tube replacement.” Then I proceeded to show him around. The homeowner was also there to let us in, so he followed along.
We started in the living room and I showed the inspector what we had done. Right away, he asked, “Why didn’t you add a receptacle to this wall?” I answered, “All we’re here to do is replace the knob and tube wiring.” The owner was not interested in ADDING more receptacles. The inspector kind of groaned, shook his head, and said, “Okay.”
We then moved onto the dining room. Again, he asked about a wall not having a receptacle. At that point, I could see where this situation was going. He then said in a very condescending way, “I hope you used arc-fault circuit breakers.” I answered, “Yes, of course. They’re required by code. We can take a look at them in the basement panel.” From there, the negative energy only got worse.
When we were upstairs in the bedroom, he asked, “Why didn’t you add a receptacle on this wall?” I gave him the same answer yet again: “We only replaced the knob and tube wiring—nothing more than that.” He then stated, “This is unacceptable. You must bring the ENTIRE HOUSE up to code and add receptacles on every wall—to fit the 12’ rule.” (When a house is gutted or being built new, we are required to install receptacles on walls so there is no wall space with more than 6’ to the nearest receptacle) I asked, “How would a knob-and-tube-replacement job trigger a complete update? The knob and tube in this house is only a small portion of the existing wiring. Why would we need to bring it up to code like a new-build house?”
He really had no answer, other than, “That’s what I want and I’m not going to pass the job because of it.” I asked him to show me a code article that required us to do what he was demanding. He didn’t like that!! I also mentioned, “We do tons of these jobs and we’ve never heard this from an inspector before.” This response only made him more pissed! He then said, “I’m not passing it. Call me when the entire house is up to code.” And he left.
Why don’t you need to bring your house up to code when replacing antique wiring?
Simply put, the job is to REPLACE THE ANTIQUE WIRING. Nothing more! Imagine if you called an electrician to add a receptacle in your dining room. He looks around and says, “Well, if I add that one, I’ll need to bring the entire room up to code. You’d probably be like, “What the heck? I just want to add a receptacle in this spot, nothing more.”
The logic of bringing this kind of space up to code makes zero sense. Plus, we need to consider budgets. A homeowner who needs to replace their knob and tube wiring is probably being forced into it by their insurance company. So it’s very unfair to expect them to spend double or triple that cost to bring a house up to code. We’ve all heard the old saying, “Rome wasn’t built in a day!”
The only time an electrician can be required to bring a room up to code is when it’s gutted. Period. Once the space is gutted, it becomes a new-work installation, which must follow the current code requirement.
Back to the story….
After the inspector stormed out, I didn’t know what to think. And quite frankly, I felt a little embarrassed. Failing an electrical inspection in front of a homeowner is not a great look LOL—even when the reason for failing makes no sense and the inspector is being hostile.
When he was gone, I looked at the owner and said, “I have no idea what just happened here. I’ve honestly never had this kind of run-in with an inspector.” The homeowner looked at me and said, “You know what? He bid this job!” You don’t say! Now it makes sense!!
I waited until the main electrical inspector was back from vacation and brought my concerns to him. He couldn’t believe it either and he apologized for the hostile inspector’s behavior. We set up a new inspection, which we passed with flying colors. Can you say conflict of interest?
0 notes
Text
300+ TOP TECHNICAL SUPPORT Interview Questions and Answers
Technical Support interview Questions for freshers and experienced :-
1. Name some of the latest Computer Processors? Intel Pentium Quad Core, Intel I3, I5 and I7 processor are some of the latest Computer Processor. 2. What does a ‘?’ sign in device manager indicate? When this sign appears, it indicates the device is not properly installed. Such problem arises in case of brand new plug-in cards. 3. How will you cope up with a customer, who complains about a brand new printer and system, and yet failing to get a proper print copy? The first thing I will ask the customer, whether the system is properly connected with the printer. The next thing would be to check the Device Driver. Many times it happens that if you install an incorrect Device Driver, the print copy would not be clear. 4. How you keep yourself updated with the current technology? I keep myself connected with social networking sites, the first platform for any technological advancement news and also keep surfing on the latest technology on internet. 5. What are the tools that will be helpful to you in identifying the problems and solving them? Manuals, Knowledge, team-members and experience are the tools that will be helpful to trouble shoot the problem and solving them. 6. What is the expected period of an average call while dealing with the customers? The expected period of an average call would be around 2-3 minutes, sometimes less or more depending on the problem complexity. 7. Why 8085 processor is called 8 bit processor? It is called 8 bit processor as it has 8 bit ALU (Arithmetic Logic Unit). 8. What is stack and can we use ROM as stack? Stack is a portion of RAM used for saving the content of the program counter and general purpose registers. ROM cannot be used as a stack, as it is not possible to write on ROM. 9. What does it mean by interrupt? To perform a particular task, interrupt is a signal send by external device to the processor. 10. What is a Microprocessor? A microprocessor is a program controlled device. It retrieves the data instructions from memory and decodes them, after decoding, it executes the instruction.

TECHNICAL SUPPORT Interview Questions 11. What is Latch? It is a temporary storage device controlled by a timing signal, which can store 1 or 0. It is a D-type flip flop storage device. 12. What is the disadvantage of microprocessor? It has a limitation on the size of the data, also most microprocessor does not support floating point operations. 13. What do you mean by DHCP? DHCP stands for Dynamic Host Configuration Protocol, it is a network protocol, and it enables the server to assign automatically, IP address to a computer. 14. What do you mean by OSI? OSI stands for open system interconnection. It is a standard description or a reference model of how message should be conveyed between any two points within a telecommunication network. It is made up of several layers and each layer provides services to the layer above. 15. What is TCP/IP? TCP/IP stands for Transmission Control Protocol or Internet protocol. It is used to connect hosts on the internet, by transferring data over the network. 16. What are RJ45 and RJ11 connectors? RJ45 connectors are used for LAN/internet connections while RJ11 connectors are used for Table cable connectors. 17. What do you mean by packaging a Microprocessor? What are the different packaging’s available? The process of packaging a microprocessor to the computer motherboard is known as a microprocessor. The different types of microprocessor’s packaging are PGA SPGA SECC LGA 18. Explain the Cache memory? What is the advantage of a processor having more cache memory? Cache memory is the memory area between Processor and Ram. If the cache memory increases, the speed of the system will also increases. 19. What is over clocking? What are the advantages of over clocking? It is a process where the computer component is forced to run at a higher clock rate. The advantages of over clocking are: Increases the CPU’s performance It is cost-saving Makes PC games and Applications to run faster 20. What is chipset? How is it different from processor and motherboard? Chipset is one of the processing devices in a computer. It is a number of integrated circuits, designed to control how information travels between other components and processor. It is a group of microchip to work as a unit to perform one or more related functions. While motherboard is where all other components like CPU, Memory, Sockets for external connectors and drives are attached. Chipset is a built in feature of Motherboard. While, processor is a main integrated circuit block, which does the function according to the instruction of a computer program. It is based on the logical, arithmetical and input/output of the system. 21. What is heat sink and what is the use in the system? To lower the temperature of a device, a heat sink component is used. It is there on the microprocessor and if it is not functioning well then the computer will shut down automatically. 22. What is Jumper and why you need it? Jumper is a metal bridge that closes an electric circuit. A jumper consists of a plastic plug that fits over a pair of protruding pins. It is used to change the board’s parameters. 23. What are the different types of DRAM? The different types of DRAM are SRAM, VRAM, SGRAM, DDR-SDRAM 24. What might be the problem when you don’t see the display? ► Power related issues ► Heat sink related issues ► CPU fan related issues ► Improper Jumper settings 25. What is SATA? SATA stands for Serial Advanced Technology Attachment. It is high speed computer bus interface designed to connect the host bus adapters to mass storage devices, such as hard disk drives and optical drives. 26. A Customer running Windows XP (Home Edition) with an Antivirus application installed reports that he has downloaded a program from the internet and installed it in his computer. After installing the program, he started receiving emails from people he never knew. The Customer removed the program from his computer but he is still getting those emails. How would you help this customer? Download the most recent virus signature files and scan his computer for viruses. 27. You are configuring Power Management on your Windows XP Computer. With ACPI, Power Management should be under the exclusive contol of: The Operating System 28. Which file must be located in the root folder of the Active Partition for Dual Booting of Windows XP and Windows ME to boot? Boot.ini 29. A Customer calls and says he is unable to get online. He uses a cable connection to connect to the internet on a Windows XP Computer. You ping 127.0.0.1 on his computer and get the results that All the packets are Lost. What should you do next? Rebuild the TCP/IP Stack in the users computer 30. Very frequently, users in your office put floppy disks in the drives and forget to take them out. This results in boot-up problems and results in support requests. How would you stop this computer from looking in the A: drive for boot files first. Change the Boot Order in BIOS. 31. After Restarting your Windows XP (Professional) computer, your monitor shows a Blank, Blue screen. You remember that a new Video driver was just installed. What would be the best way to fix this problem? Restart the Computer, Keep tapping on the F8 Key to go to the Windows Advanced Options Menu and select the option “Last Known Good Configuration” and hit the key. 32. You need to Dual-Boot a computer with Windows XP and Windows Me. You need all the Partitions to be accesible from both the Operating Systems. Which File System would you use in this scenario? FAT32 33. What is the command to convert a FAT32 file system to NTFS? Would there be any loss of data? The command is: CONVERT : /fs:NTFS. There will be no effect on the data. (Data will be safe).But remember this: if you want to convert NTFS partition back to FAT32, you will have to re-format that partition and select the FAT32 file system. 34. What are the features of the Disk Defragmenter Tool in Windows XP and Windows 2000? Does the Windows XP version have any more features than the Windows 2000 version? The features of the Disk Defragmenter Tool are the same in both Windows XP and Windows 2000. They are: 1. Enhanced Analysis Functionality 2. A Compression option 3. Increased Defragmentation Option and an Automatic Defrag-Scheduling Option. 35. You are a Desktop Support Technician at EQS. One of the customers has just installed a Brand New Printer for himself. This customer calls you after some time and says that every time he tries to print something, all he gets is some garbled text. However, the printer prints the Test Page fine. What do you think is the problem here? The customer has installed an Incorrect Device Driver for the Printer. I would uninstall the driver, from the WIndows Device Manager and install the correct Device Driver for the Printer from the Disk that came with the Printer. (If the Disk is not available, I can still download the correct device driver from the manufacturer’s website) 36. If, upon Booting up a Computer, you see the error message “Keyboard Error…” What do you think could be the problem? It could be that 1. The keyboard is not attached to the PC or 2. The keyboard has failed 37. If you turn on a PC and the boot-up process halts and you get the error message “Non-System Disk or Disk Error…Replace and Press any Key when Ready…” What do you think could be the problem? A non-bootable Floppy Disk is in the Floppy-disk drive and it should be removed. 38. If, upon booting up a PC, you see a message which says “Invalid Drive Configuration..” What do you think is causing this? This problem could be due to any of the following situations: 1. The Hard-Disk cable within the System Unit is not attached to the Controller 2. The Hard Disk Drive has failed 3. The Hard Disk Drive has not been partitioned. 39. If you turn on a PC and the boot process halts and you get the error message ” C:\System32\Config file missing or Corrupt” What is this due to? The Registry Hives are corrupted. They need to be repaired. 40. A Customer complains that he keeps getting the error message “HAL.DLL missing or Corrupt”. Which file needs to be repaired/rebuilt to rectify the issue? BOOT.INI 41. You have Norton 360. When the Firewall is turned on, you are unable to browse the internet. But if you turn off the firewall, you are able to browse. What is the first thing you would do to fix this problem? Reconfigure Norton Firewall to allow Internet Explorer to access the internet. 42. Which utility is used to do a Software Clean Boot? Msconfig 43. What does a “?” sign in device manager signify? The device is not installed. ( You can refer to this article for more details). For more information on Device Manager check this article from Microsoft. 44. What is the command to start Windows System Restore from the Command Line? rstrui.exe 45. What does the term UAC stand for? UAC stands for User Access Control. For more information read this article. 46. You are a Desktop Support Technician. A user calls and complains that till yesterday he was able to view his CD drive in his computer. But today when he turned on his computer, he is not able to view the CD-ROM drive in “My Computer”. What can be done to fix this problem? Open the Windows Registery Editor and Delete the Upper and Lower Filter Keys. 47. A user calls and says that whenever he starts his computer, it boots up only in Safe Mode. There is no other error message. What would you do to fix this problem? Go to Msconfig and select Normal Mode and Restart the Computer. 48. A user complains that whenever he connects any USB 2.0 device to his computer, he gets the error message “USB device not recognized…” What could be the possible reason for this? The USB Port could be faulty. 49. A user complains that he is no longer able to hear any sound from his computer – after he downloaded some updates from the Microsoft Website. What could be the possible reason for this? The Windows Audio Service is Disabled. Enable it. 50. Mark uses Windows XP Professional and is connected to the internet directly through a DSL line. He wants to know how he could enable the filtering of packets and get rid of the harmful incomming data. What would you tell him? Enable the Firewall 51. A Customer reports that his Windows XP Professional portable computer is not able to connect to any network resource and is also not able to authenticate on the network’s Active Directory Domain. The computer was fine yesterday. No other person in the organization is facing this problem. What is the first thing you would do to fix this problem? Ask the user to Right-Click on the Network Connection icon and select “Repair” from the Menu. 52. A customer has recently upgraded from Windows 98 to Windows XP Professional. After the upgrade, it takes longer for Windows, Menus, Sub-Menus and other use interface features to open. She wants them to open faster. How can you help this customer? Use System in Control Panel and select the option “Adjust for Best Performance” in the Performance Options dialogue box. 53. You suspect that your computer is failing because of a Corrupt Master Boot Record. Which utility is the best to fix this problem? Recovery Console (By Using the fixmbr command) 54. You performed a Parallel installation of Windows XP (Home Edition) to resolve certain problems on a Customer’s Computer. After installation, the customer says she can see the previous profile folders in Documents & Settings but when she tries to open then, she gets an “Access Denied” error. What can you do to remove the “Access Denied” Problem? Boot into Safe Mode, Right-Click on the Old Profile Folder, Go to Security – Advanced and give Ownership to the new user. 55. A Customer calls in and says that her copy of Windows XP went corrupt and the previous Technician installed it again without losing any data. Now when the computer boots up, it shows a menu for a few seconds and then it boots normally.She wants to get rid of this menu. You asked her about the menu options and the customer tells you that both the options in the Menu Read the same thing – Windows XP Home. How will you fix this problem so that the Menu does not appear again? Edit the Boot.ini file and set the Timeout as 0 (Zero) or Edit the Boot.ini file and Remove the Second Option and set the Timeout as 0 (Zero) 56. What is BIOS? BIOS stands for Basic Input-Output System and is pronounced as “Bye-Ose“. The BIOS is available on all the computers. It makes sure that all the components of the computer can function together. It has information about all the hardware components in the Computer. BIOS can also be called as a Special Software that interfaces the major hardware components of a computer with the Operating System. It is usually stored in a Flash Memory Chip on the Motherboard. Some functions of BIOS: Performs a POST (Power-On Self Test) for all the different Hardware Components in the System to make sure everything is working properly. Activating other BIOS Chips on different cards installed in the computer, for example, SCSI and Graphics Cards. Provides a set of low-level suiting that the Operating System uses to interface different Hardware devices. BIOS manages things in your computer like the Keyboard, Monitor, Serial and Parallel Ports especially when the computer is Booting up. Manage the settings for Hard-disk drives, System Clock etc. Sequence of things done by the BIOS when you turn on your Computer: Check the CMOS for Custom Settings Load the interrupt Handlers and Device Drivers Initialize Registers and Power Management Perform POST (Power On Self Test) Display System Settings Determine which devices are Bootable Initialize the Bootstrap sequence 57. What are the Hardware Components of a Desktop Computer / Laptop? The Hardware Components of a Desktop Computer / Laptop are as follows: 1. The Processor (CPU) 2. Motherboard 3. RAM (Random Access Memory) 4. Power Supply – SMPS (Switch Mode Power Supply) 5. Hard-disk Drives 6. CD/DVD-ROM Drives 7. Floppy Disk Drive 8. Sound Card 9. Graphics (Display) Card 10. Keyboard 11. Mouse 12. Monitor 58. What are Hard-Disk Partitions? Partitions are used to Divide a Hard-disk drive into smaller segments as required by the user and for better management of the space in it. 59. Difference between RAM and ROM? RAM (Random Access Memory) – is used to temporarily store information that the computer is currently working on. ROM (Read Only Memory) – This is a Permanent type of memory storage used by computers for important data which never changes. (Example: BIOS) 60. What would you check if there is no sound from your computer? (Audio not working) 1. Check for cable connections 2. Check for power to the speakers 3. Check for volume control 4. Check for device drivers 61. If a Customer complains that his computer is working really slow, what are the things you would check? 1. Check if it is taking longer than usual to start up 2. Check if it is slow with one / any particular application or slow overall. 3. Check for Spyware/Malware/Virus in the computer 4. Check the available Hard-Disk Drive Space in the computer. 62. What is the Blue Screen of Death (BSOD)? A Blue Screen of Death (or just a Blue Screen Error) is an indication of a Critical System Problem wherein the Computer freezes altogether and does not respond to anything. To rectify this problem, try Restarting the computer or Booting into Safe Mode. For more information, read this. 63. Why are Device Drivers required? A Device Driver (or just Driver) is a piece of software which is requied to run every Hardware Component present in the computer. 64. Name one of the latest Computer Processors (CPU) ? Intel Pentium Quad Core, Intel I3, I5, I7 processors. 65. What is Ping? Ping is a command that checks the connectivity with an IP address. For more read this article 66. What is a Data Cable? A Data Cable is a Thin Plastic band-like cable used to connect the Data-Devices like Hard-disk drives, Floppy Disk Drives, CD/DVD-ROM drives with the motherboard. Data Cables are primarily used for Data Transfer. 67. Lights on a Modem / LAN Card: Generally, there are 04 lights. They indicate the following: 1. Power Light: Shows if the device (Modem)is getting Power Supply or not. 2. Link Light: Indicates if the device is getting broadband/internet signals properly from the ISP 3. Data Light: Indicates wether the internet is working or not. 4. Connectivity Light: Indicates the Modem is connected to a PC or not. 68. Name some of the Ports available in a Computer Some of the commonly available ports in a Computer are as follows: 1. Keyboard & Mouse Ports – Also known as PS/2 ports 2. USB Ports 3. VGA Ports 4. Sound Ports 5. LAN Port – Also known as Ethernet Port 69. What does the term USB stand for? USB stands for Universal Serial Bus. It allows devices to be connected or disconnected from a computer without shutting down or restarting the computer. The current version of USB is 2.0 70. What is the difference between CRT (Cathode Ray Tube) and LCD (Flat Screen Monitors)? CRT Monitors: The Monitor has a picture tube and uses a light-gun to highlight pixels on the screen. LCD Monitors: These monitors do not have a picture tube and contain a layer of liquid crystals on an Electronic Board. 71. What is an IP Address? An IP address is a unique numerical identifier of every device on a network. A typical IP address can look like this: 216.27.61.141. To detect a computer’s IP Address, go to Start – Run – Type in CMD in the Run Dialogue Box and click OK or hit – In the Command Prompt Screen that comes up, type in IPCONFIG and hit 72. What is DHCP? DHCP stands for Dynamic Host Configuration Protocol. It is used to generate & provide IP addresses to the computers on a network. 73. What is DNS? DNS stands for Domain Name Services – it is used to convert URLs into IP addresses and vice-versa. 74. Mention a sample computer configuration: 1. Intel Pentium Core 2 Duo – 3.0Ghz 2. 2 GB RAM 3. 300GB HDD 4. DVD Writer 5. 17 inches LCD Monitor 6. Keyboard 7. Mouse 75. Name any Five Microsoft Office Applications: 1. MS Word 2. MS Excel 3. MS Powerpoint 4. MS Access 5. MS Outlook 76. What are RJ45 and RJ11 connectors? RJ45 connectors are used for LAN/Ethernet connections and RJ11 connectors are used for Telephone Cable connections. 77. What is a Parallel Windows installation? When the first installation of Windows fails to boot for some reason, another copy of Windows is installed in teh same drive but in a different directory (so that the customer can access to and backup his old data). This is called Parallel Installation of Windows. 78. Name some of the versions of Windows XP. Windows XP Home Edition, Professional, Media Center Edition, Tablet PC Edition, Mobile 79. Difference betwen a WORKGROUP and a DOMAIN? In a Workgroup, all the computers function as Peers. But in a Domain, One computer is the Server and the others are Clients. 80. What is the difference between FAT32 and NTFS file systems? 1. NTFS allows compression and file encryption. FAT32 does not. 2. NTFS is more secure than FAT32 81. What does BOOT.INI do? Boot.ini lists all the Operating Systems present in the computer and provide information about which partitions they are located on. 82. How would you access the Recovery Console in Windows? By booting with the Windows XP CD and following the on-screen instructrions. The Recovery Console can also be installed in your computer. 83. Provide the names of a few Firewalls: Norton, McAfee, Zone Alarm etc 84. What feature of Outlook Express allows multiple customers to send and receive emails, each using a separate account? Identities 85. What are the components needed to setup a Basic Home Network? LAN Cards, LAN Cables, Router/Hub Technical Support Questions and Answers pdf Download Read the full article
0 notes
Text
Paper Relays

A relay is a device that can receive a binary signal through one channel and rebroadcast that signal on a different channel. Relays can be combined to create logic gates, which are the building blocks for more complex logic circuits that can add, subtract, multiply, divide, and do all sorts of other useful activities.
For the third assignment of the semester, we are tasked with constructing a mechanical computing machine capable of adding small binary numbers. To do this, we first needed to design a relay capable of working with signals in a physical medium other than electricity. Remembering that water is often used as a metaphor for electricity in many physics classes, I started thinking about how a fluid could be used to convey information. My group eventually settled on air as our medium of choice because it is cheap, plentiful, and doesn’t make a mess when it leaks.
youtube
Chris discovered a fascinating video in which an ingenious Belarusian constructs an air-powered adding machine using nothing but paper. Aliaksei‘s logic gates are integrated, rather than being constructed of individual relays, but we were inspired none the less.

One important detail I realized from studying Aliaksei‘s work was that the conduits that convey air between relays (and, indeed, the relays themselves) need not be circular in profile. Freed from the tyranny of hard-to-fabricate cylinders, I devised a system for constructing relays that consisted of a pair of nested vertically-oriented boxes. Two holes on opposing sides of the outer box would receiving the air supply and transmit the relay’s output signal. A third hole on the bottom of the outer box would accept the relay’s input signal. The smaller inner box would be able to slide within its enclosure to either open or occlude the passage between the opposing holes of the outer box depending on the presence or absence of an input signal.

I constructed several prototypes by cutting and folding 4×6 index cards. The first used a spring to push the inner box back into its original position after the input was removed. Using a spring meant that the relay could be oriented in any position, but I felt that the travel distance was too short.

The second prototype relied on gravity to return the inner box to its original position, and is less finicky than the first. It also featured a nozzle that one can blow into to activate the relay.
youtube
The third prototype improved on the second by lengthening the opening in the inner box so that a greater range of positions would result in an open relay. The inner box in this iteration was could also be reversed to convert the relay into an inverter.

An inverter behaves opposite of a relay: When an inverter receives a signal, it transmits no output. When its input goes away, it begins to transmit. With the ability to build both relays and inverters, our team would be able to construct all six types of logic gates.
#connectiveenvironments#assignment 3#arghavan+christopher+nicholas#relay#paper#folded paper#pneumatic#physical computing
0 notes
Photo

25+ JavaScript Shorthand Coding Techniques
This really is a must read for any JavaScript developer. I have written this guide to shorthand JavaScript coding techniques that I have picked up over the years. To help you understand what is going on, I have included the longhand versions to give some coding perspective.
August 26th, 2019: This article was updated to add new shorthand tips based on the latest specifications. If you want to learn more about ES6 and beyond, sign up for SitePoint Premium and check out our extensive library of modern JavaScript resources.
1. The Ternary Operator
This is a great code saver when you want to write an if..else statement in just one line.
Longhand:
const x = 20; let answer; if (x > 10) { answer = "greater than 10"; } else { answer = "less than 10"; }
Shorthand:
const answer = x > 10 ? "greater than 10" : "less than 10";
You can also nest your if statement like this:
const answer = x > 10 ? "greater than 10" : x < 5 ? "less than 5" : "between 5 and 10";
2. Short-circuit Evaluation Shorthand
When assigning a variable value to another variable, you may want to ensure that the source variable is not null, undefined, or empty. You can either write a long if statement with multiple conditionals, or use a short-circuit evaluation.
Longhand:
if (variable1 !== null || variable1 !== undefined || variable1 !== '') { let variable2 = variable1; }
Shorthand:
const variable2 = variable1 || 'new';
Don’t believe me? Test it yourself (paste the following code in es6console):
let variable1; let variable2 = variable1 || 'bar'; console.log(variable2 === 'bar'); // prints true variable1 = 'foo'; variable2 = variable1 || 'bar'; console.log(variable2); // prints foo
Do note that if you set variable1 to false or 0, the value bar will be assigned.
3. Declaring Variables Shorthand
It's good practice to declare your variable assignments at the beginning of your functions. This shorthand method can save you lots of time and space when declaring multiple variables at the same time.
Longhand:
let x; let y; let z = 3;
Shorthand:
let x, y, z=3;
4. If Presence Shorthand
This might be trivial, but worth a mention. When doing “if checks”, assignment operators can sometimes be omitted.
Longhand:
if (likeJavaScript === true)
Shorthand:
if (likeJavaScript)
Note: these two examples are not exactly equal, as the shorthand check will pass as long as likeJavaScript is a truthy value.
Here is another example. If a is NOT equal to true, then do something.
Longhand:
let a; if ( a !== true ) { // do something... }
Shorthand:
let a; if ( !a ) { // do something... }
5. JavaScript For Loop Shorthand
This little tip is really useful if you want plain JavaScript and don't want to rely on external libraries such as jQuery or lodash.
Longhand:
const fruits = ['mango', 'peach', 'banana']; for (let i = 0; i < fruits.length; i++)
Shorthand:
for (let fruit of fruits)
If you just wanted to access the index, do:
for (let index in fruits)
This also works if you want to access keys in a literal object:
const obj = {continent: 'Africa', country: 'Kenya', city: 'Nairobi'} for (let key in obj) console.log(key) // output: continent, country, city
Shorthand for Array.forEach:
function logArrayElements(element, index, array) { console.log("a[" + index + "] = " + element); } [2, 5, 9].forEach(logArrayElements); // a[0] = 2 // a[1] = 5 // a[2] = 9
6. Short-circuit Evaluation
Instead of writing six lines of code to assign a default value if the intended parameter is null or undefined, we can simply use a short-circuit logical operator and accomplish the same thing with just one line of code.
Longhand:
let dbHost; if (process.env.DB_HOST) { dbHost = process.env.DB_HOST; } else { dbHost = 'localhost'; }
Shorthand:
const dbHost = process.env.DB_HOST || 'localhost';
7. Decimal Base Exponents
You may have seen this one around. It’s essentially a fancy way to write numbers without the trailing zeros. For example, 1e7 essentially means 1 followed by 7 zeros. It represents a decimal base (which JavaScript interprets as a float type) equal to 10,000,000.
Longhand:
for (let i = 0; i < 10000; i++) {}
Shorthand:
for (let i = 0; i < 1e7; i++) {} // All the below will evaluate to true 1e0 === 1; 1e1 === 10; 1e2 === 100; 1e3 === 1000; 1e4 === 10000; 1e5 === 100000;
8. Object Property Shorthand
Defining object literals in JavaScript makes life much easier. ES6 provides an even easier way of assigning properties to objects. If the variable name is the same as the object key, you can take advantage of the shorthand notation.
The post 25+ JavaScript Shorthand Coding Techniques appeared first on SitePoint.
by Michael Wanyoike via SitePoint https://ift.tt/2HnfwSX
0 notes
Text
Embedded programming in the Internet of Things
Embedded programming has a long history of making devices do what people need. However, it remains outshined by application programming: when application programmers were embracing high-level object-oriented languages like C++ or Java, or graphical application development environments like MATLAB, embedded programmers were only moving from assembly language to C. Besides, they were always outnumbered by app programmers — simply because now even hobbyists can develop an app using an easy language and upload it to cloud, while embedded programmers need to have profound knowledge of the hardware platform.
With the emergence of the Internet of Things (IoT), the balance can finally change. Now that every thermostat, toaster, watch, and light bulb is equipped with a processor, the market needs more embedded programmers to program these devices, and consequently more simpler tools to allow the programmers to write code without plunging into the hardware.
But first!
What is embedded programming?
According to Technopedia, embedded programming is a specific type of programming that supports the creation of consumer facing or business facing devices that don’t operate on traditional operating systems the way that full-scale laptop computers and mobile devices do. The idea of embedded programming is part of what drives the evolution of the digital appliances and equipment in today’s IT markets.
If explained in simpler words, embedded programming is designing software for small computers that drive devices; essentially, it is the dominant methodology for microcontroller and microcomputer programming used in small facilities-handling devices like thermostats, handheld games or other small devices.
Embedded programming and IoT
From the engineering perspective, the Internet of Things is an embedded microprocessor controlled system connected directly or indirectly to the web. The three pillars of the IoT are therefore embedded programming, network technology and information technology. The embedded system of a device collects data from a sensor and sends it to the cloud using a wifi module — basically, it means that you can turn your embedded device into an IoT device by simply giving it Internet access.
The IoT is everywhere, and so are embedded devices:
Industrial world, such as industrial machinery and control, temperature monitoring, or cognitive anomaly detection — the recent challenges of embedded systems turned them towards automation.
Healthcare, including blood pressure monitors, heartbeat monitors, and pacemakers.
Aerospace and Defense with such applications as flight control systems, actuation, air and thermal management, engine power control and many others.
Smart Homes, including Home Security system, Setup Box, Digital Camera, Television, Microwave Oven, Air Conditioner, Refrigerator and much more.
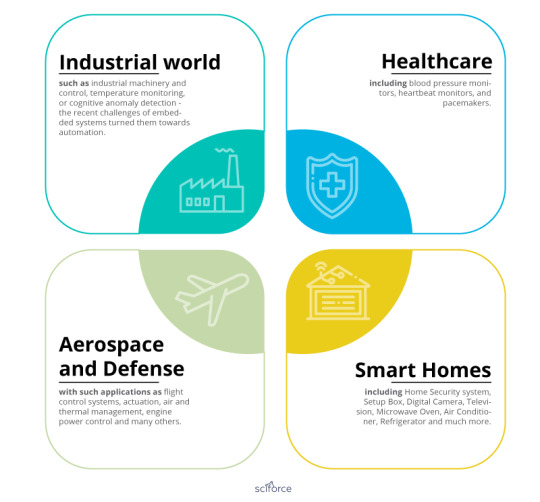
Embedded systems
Once I’ve read the saying that every complex system in the world can be reduced to two ideas: software and hardware. An embedded system is not an exception: to understand how embedded programming works, we need to understand its hardware and software parts.
Embedded Hardware
The embedded development board is divided into five modules: Processor, Memory, Input devices, Output devices and Bus controllers.
Hardware Components of an Embedded System
Processor
Embedded processors can be broken into two categories: ordinary microprocessors that use separate integrated circuits for memory and peripherals, and microcontrollers that have on-chip peripherals, reducing power consumption, size and cost. Some of the examples of microprocessors include:
Microcontroller (CPU) is an intelligent device that computes the tasks assigned by the user and is used to build small applications with precise calculation.
System on Chip (SoC) comprises a CPU, Peripheral devices (Timers, counters), Communication interfaces (I²C, SPI, UART), and Power Management Circuits on a single IC.
ASIC processor (Application Specific Integrated Circuit) is designed for use for a particular application and owned by a single company.
DSP processor removes the noise and improves signal quality in Audio and Video Applications.
Memory
Data storage and memory management require EEPROM. Some examples of the memories used in embedded systems include Non-Volatile RAM, Volatile RAM, DRAM (Dynamic Random Access Memory), etc.
Input Devices
Input devices, such as sensors, switches, photodiode, optocouplers, etc., take input from the outside world accepting input from the user and responding accordingly.
Output Devices
Output devices, including LCD, LED, seven segment displays, buzzers and relays, are indications or results of input events from outside the microcontroller.
Bus controllers
The bus controller is a communication device that transfers data between the components inside an embedded system. The most widely-spread bus controllers are serial buses (I2C, SPI, SMBus etc.), RS232, RS485 and universal serial bus.
Embedded Software
Embedded software, sometimes called firmware, is written for the device drivers, operating system, and applications, as well as for error handling and debugging.
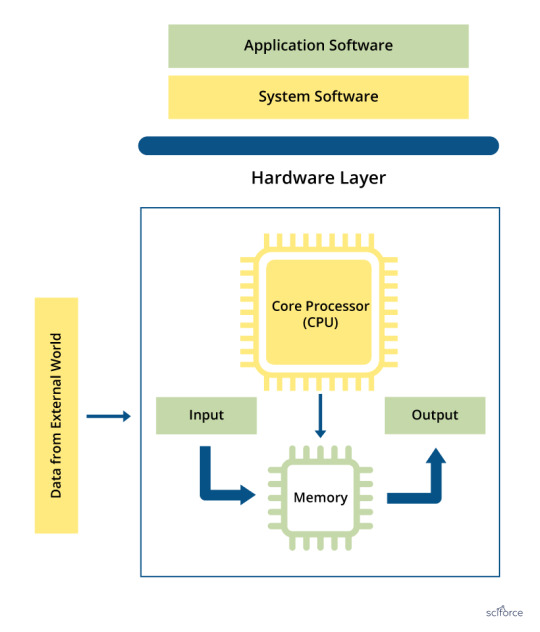
Software Components of an Embedded System
Device Driver
A device driver is a piece of embedded code written for a particular hardware.
Operating System (OS)
Embedded systems have a range of operating systems, including RTOS (Real-time operating systems), mobile embedded, stand-alone and network embedded systems.
Most of the embedded software is now written in two languages, C and C++. There is not much difference between C and C++ in terms of syntax. However, C++ has some additional features, like enhanced security and closeness to real-world applications, while C is considered to be more reliable and showing better performance and directly interacting with the hardware.
Key steps to create an embedded product
Now, knowing the theory, we can prepare ourselves to try embedded programming.
Probably, the best way to start writing software that would directly affect physical objects is to explore such embedded platforms as Arduino, Raspberry Pi, or Particle.
To develop a viable product you should take the following steps:
Step 1. Learn C or C++
And this is where many (me included) stop. However, if you want to write embedded software, you have to learn C/C++ (and maybe eventually Rust).
Step 2. Learn Some Basic Electronics
At least to the extent that you understand what voltage, current, power, resistance, and ohms law are.
Step 3. Get the Basic Equipment
Embedded programmers actually interact with the physical world, so such things as soldering iron, Digital Multi-Meter (DMM), and a hardware debugger/ JTAG adapter (such as an ST-Link, or OLMEX adapter) or a Logic Analyzer would be of help.
Step 4. Choose a Microcontroller and Toolchain
To make your program run, you’ll need a microcontroller to actually run it, a compiler that would compile it for the microcontroller, and other tools to load the program onto your hardware. An example of the compbination of mictocontrollers with a toolchain is the STM32 microcontrollers that are supported by the arm-gcc along with openOCD toolchain.
Step 5. Understand the Datasheets
Before actually sitting down to write the first line of your code, you need to understand the (end user) specifications.
Step 6: Examine the components
Analyze and pick up the components (software and hardware) required to make the product.
Step 7: Design a product
Designing is always the most critical phase of any development cycle. The peculiarity of the embedded programming is that you have to develop the hardware and software parts individually and integrate both.
Step 8: Develop a prototype
A prototype is a sample version created to test the concept which is developed according to the specifications using the selected hardware and software tool.
Step 9: Test the application
Now that the prototype it is possible to run test cases to prove the possible potential of the application.
Step 10: Deploy the application
After testing the application, the result is checked in a real environment to realize the Proof Of Concept — a technique used to validate an idea.
Step 11: Support and Upgrade
If needed, you should be ready to provide support and upgrade the application with new features.
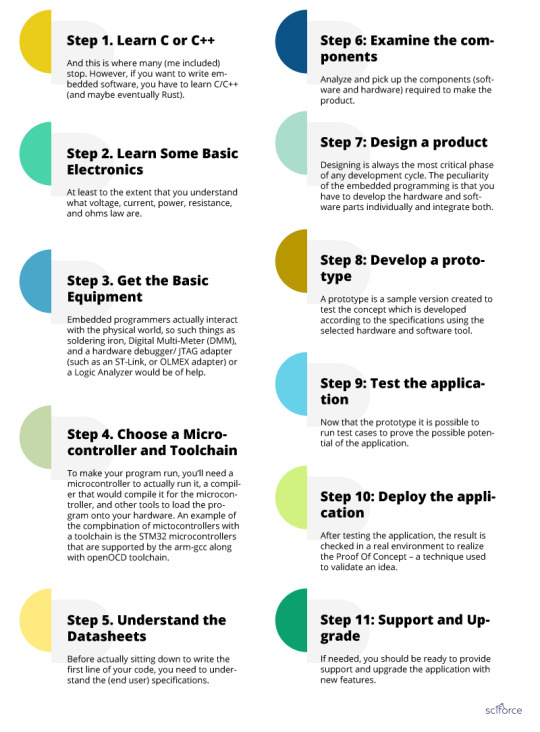
Eleven steps to create an embedded product
And now you are ready to start changing the world — for example, but creating a smart Lego city!
0 notes
Text
Anti-jamming design in PCB
In the design of electronic systems, in order to avoid detours and save time, the anti-interference requirements should be fully considered and avoided, and remedial measures against interference should be avoided after the design is completed. There is a PCB and PCBA manufacturer ALLPCB Summarized a few experiences:
(1) Interference source refers to the component, device or signal that causes interference. It is described in mathematical language as follows: du/dt, where di/dt is large, it is the source of interference. Such as: lightning, relays, thyristors, motors, high-frequency clocks, etc. may become sources of interference.
(2) Sensitive devices refer to objects that are easily disturbed. Such as: A / D, D / A converter, microcontroller, digital IC, weak signal amplifier.
(3) Propagation path refers to the path or medium that interferes with the propagation from the interference source to the sensitive device. A typical interference propagation path is the conduction through the wires and the radiation from the space.
The basic principles of anti-jamming design are: suppressing interference sources, cutting off interference propagation paths, and improving the anti-jamming performance of sensitive devices. (similar to the prevention of infectious diseases)
1. Suppress interference sources
To suppress the interference source is to reduce the du/dt, di/dt of the interference source as much as possible. This is the best consideration and most important principle in anti-jamming design, often with a multiplier effect. Reducing the du/dt of the interference source is mainly achieved by connecting capacitors across the interference source. Reducing the di/dt of the interferer is achieved by connecting the inductor or resistor in series with the source loop and adding a freewheeling diode.
Common measures to suppress interference sources are as follows:
(1) Avoid 90-degree fold lines during wiring and reduce high-frequency noise emission.
(2) The relay coil increases the freewheeling diode to eliminate the back EMF interference generated when the coil is disconnected. The addition of a freewheeling diode will delay the turn-off time of the relay. After the Zener diode is added, the relay can operate more times per unit time.
(3) Connect the spark suppression circuit at both ends of the relay contact (usually RC series circuit, the resistance is generally selected from a few K to tens of K, and the capacitor is selected as 0.01uF) to reduce the influence of spark.
(4) Add a filter circuit to the motor, pay attention to the capacitor and inductor leads as short as possible.
(5) Each IC on the board should be connected with a high frequency capacitor of 0.01μF to 0.1μF to reduce the impact of the IC on the power supply. Pay attention to the wiring of high-frequency capacitors. The wiring should be close to the power supply terminal and be as short and as short as possible. Otherwise, it will increase the equivalent series resistance of the capacitor, which will affect the filtering effect.
(6) The RC suppression circuit is connected to both ends of the thyristor to reduce the noise generated by the thyristor (this thyristor may break down when this noise is severe). According to the propagation path of interference, it can be divided into two types: conducted interference and radiated interference.
Conducted interference is the interference that propagates through a wire to a sensitive device. High-frequency interference noise and the frequency band of the wanted signal can be cut off by adding a filter to the wire to cut off the propagation of high-frequency interference noise, and sometimes by isolating the optocoupler. Power supply noise is the most harmful, so pay special attention to handling. Radiation interference refers to interference that propagates through a spatial radiation to a sensitive device. The general solution is to increase the distance between the interferer and the sensitive device, isolate them with ground and add a shield to the sensitive device.

2. The common measures to cut off the interference propagation path are as follows:
(1) Fully consider the impact of the power supply on the microcontroller. The power supply is well done, and the anti-interference of the entire circuit is solved. Many single-chip microcomputers are very sensitive to power supply noise. It is necessary to add a filter circuit or a voltage regulator to the power supply of the single-chip microcomputer to reduce the interference of the power supply noise on the single-chip microcomputer. For example, a magnetic bead and a capacitor can be used to form a π-shaped filter circuit. Of course, a 100Ω resistor can be used instead of the magnetic bead when the condition is not high.
(2) If the I/O port of the MCU is used to control noise devices such as motors, isolation should be added between the I/O port and the noise source (increasing the π-shaped filter circuit). Control noise devices such as motors, and add isolation between the I/O port and the noise source (increasing the π-shaped filter circuit).
(3) Pay attention to the crystal wiring. The crystal oscillator and the MCU pins are placed as close as possible, and the clock region is isolated by the ground wire. The crystal oscillator case is grounded and fixed. This measure can solve many difficult problems.
(4) Reasonable division of the circuit board, such as strong and weak signals, digital and analog signals. Keep interference sources (such as motors, relays) away from sensitive components (such as microcontrollers) whenever possible.
(5) Separate the digital zone from the analog zone with a ground wire, separate the digital ground from the analog ground, and finally connect it to the power ground at one point. A/D and D/A chip wiring are also based on this principle. This requirement has been taken into consideration when the manufacturer assigns A/D and D/A chip pinouts.
(6) The ground wire of the MCU and the high-power device should be grounded separately to reduce mutual interference. Place high-power devices on the edge of the board as much as possible.
(7) Anti-interference components such as magnetic beads, magnetic rings, power supply filters, and shields can be used in key areas such as I/O ports, power lines, and circuit board connectors. This can significantly improve the anti-jamming performance of the circuit.
3. Improve the anti-interference performance of sensitive devices
Improving the anti-interference performance of sensitive devices refers to the method of minimizing the pickup of interference noise and recovering from an abnormal state as soon as possible from the sensitive device side.
Common measures to improve the anti-jamming performance of sensitive devices are as follows:
(1) Minimize the loop loop area during wiring to reduce induced noise.
(2) When wiring, the power and ground wires should be as thick as possible. In addition to reducing the voltage drop, it is more important to reduce the coupling noise.
(3) For the idle I/O port of the MCU, do not hang it, ground it or connect it to the power supply. The idle ends of other ICs are grounded or connected to the power supply without changing the system logic.
(4) The power supply monitoring and watchdog circuit for the single-chip microcomputer, such as IMP809, IMP706, IMP813, X25043, X25045, etc., can greatly improve the anti-interference performance of the whole circuit.
(5) Under the premise that the speed can meet the requirements, try to reduce the crystal oscillator of the single-chip microcomputer and select the low-speed digital circuit.
(6) The IC device is soldered directly on the circuit board as much as possible, and the IC holder is used less.
0 notes
Text
MTH 221 ENTIRE COURSE | University Of Phoenix

MTH 221 ENTIRE COURSE
Get MTH 221 entire course at University of Phoenix. Here is the best resources for homework help with MTH 221: Discrete Math at University of phoenix.
Get MTH 221 assignment help, homework solutions, study guides, notes etc.
MTH 221 Week 1 Individual Assignment Selected Textbook Exercises Complete 10 questions below. Please review the rubric posted in week 1 for math problems. Submit to your assignment tab. Submit a certificate of originality for this assignment. Ch. 1 of Discrete and Combinatorial Mathematics Supplementary Exercises 1, 2a Ch. 2 of Discrete and Combinatorial Mathematics Exercise 2.1, problem 2 Exercise 2.2, problem 2 Exercise 2.3, problem 4 Exercise 2.4, problem 1 Exercise 2.5, problem 1 Ch. 3 of Discrete and Combinatorial Mathematics Exercise 3.1, problem 1 Exercise 3.2, problem 3a Exercise 3.3, problem 1 MTH 221 Week 1 DQS DQ 1 Consider the problem of how to arrange a group of n people so each person can shake hands with every other person. How might you organize this process? How many times will each person shake hands with someone else? How many handshakes will occur? How must your method vary according to whether or not n is even or odd? DQ 2 There is an old joke that goes something like this: “If God is love, love is blind, and Ray Charles is blind, then Ray Charles is God.” Explain, in the terms of first-order logic and predicate calculus, why this reasoning is incorrect DQ 3 There is an old joke, commonly attributed to Groucho Marx, which goes something like this: “I don’t want to belong to any club that will accept people like me as a member.” Does this statement fall under the purview of Russell’s paradox, or is there an easy semantic way out? Look up the term fuzzy set theory in a search engine of your choice or the University Library, and see if this theory can offer any insights into this statement DQ 4 After reading Chapter 1 in our ebook, what is the difference between combinations and permutations? What are some practical applications of combinations? Permutations? MTH 221 Week 2 Individual Assignment Selected Textbook Exercises Complete 10 questions below. Please review the rubric posted in week 1 for math problems. Submit to your assignment tab. Submit a certificate of originality for this assignment. Ch. 4 of Discrete and Combinatorial Mathematics Exercise 4.1, problem 5a Exercise 4.2, problem 18a Ch. 4 of Discrete and Combinatorial Mathematics Exercise 4.3, problem 4 Exercise 4.4, problem 1a Ch. 5 of Discrete and Combinatorial Mathematics Exercise 5.1, problem 4 Exercise 5.2, problem 4 Exercise 5.3, problem 1a Exercise 5.4, problem 13a Ch. 5 of Discrete and Combinatorial Mathematics Exercise 5.7, problem 1a Exercise 5.8, problem 5a MTH 221 Week 2 Team Selected Textbook Exercises Complete 3 questions below. Please review the rubric posted in week 1 for math problems. Have one team member submit to their assignment tab. Submit a certificate of originality for this assignment. Ch. 4 of Discrete and Combinatorial Mathematics Exercise 4.3, problems 12a, & 15 Ch. 5 of Discrete and Combinatorial Mathematics Exercise 5.1, problem 8 MTH 221 Week 2 DQS DQ 1 · Describe a situation in your professional or personal life when recursion, or at least the principle of recursion, played a role in accomplishing a task, such as a large chore that could be decomposed into smaller chunks that were easier to handle separately, but still had the semblance of the overall task. Did you track the completion of this task in any way to ensure that no pieces were left undone, much like an algorithm keeps placeholders to trace a way back from a recursive trajectory? If so, how did you do it? If not, why did you not? DQ 2 · Describe a favorite recreational activity in terms of its iterative components, such as solving a crossword or Sudoku puzzle or playing a game of chess or backgammon. Also, mention any recursive elements that occur. DQ 3 · Using a search engine of your choice, look up the term one-way function. This concept arises in cryptography. Explain this concept in your own words, using the terms learned in Ch. 5 regarding functions and their inverses. DQ 4 · A common result in the analysis of sorting algorithms is that for n elements, the best average-case behavior of any sort algorithm—based solely on comparisons—is O(n log n). How might a sort algorithm beat this average-case behavior based on additional prior knowledge of the data elements? What sort of speed-up might you anticipate for such an algorithm? In other words, does it suddenly become O(n), O(n log n) or something similar? MTH 221 Week 3 Individual Assignment Selected Textbook Exercises Complete 10 questions below. Please review the rubric posted in week 1 for math problems. Submit to your assignment tab. Submit a certificate of originality for this assignment. Ch. 7 Exercise 7.1, problems 5a, 6 Exercise 7.2, problem 2 Exercise 7.3, problems 1, 6a Ch. 7 Exercise 7.4, problems 1a, 2a Ch. 8 Exercise 8.1, problems 4, 12 Exercise 8.2, problem 4 MTH 221 Week 3 Team Selected Textbook Exercises Complete 3 questions below. Please review the rubric posted in week 1 for math problems. Have one team member submit to their assignment tab. Submit a certificate of originality for this assignment. Ch. 7 Exercise 7.4, problems 12a, & 13 Ch. 8 Exercise 8.1, problem 20 MTH 221 Week 3 DQS DQ 1 · What sort of relation is friendship, using the human or sociological meaning of the word? Is it necessarily reflexive, symmetric, antisymmetric, or transitive? Explain why or why not. Can the friendship relation among a finite group of people induce a partial order, such as a set inclusion? Explain why or why not. DQ 2 · Look up the term axiom of choice using the Internet. How does the axiom of choice—whichever form you prefer—overlay the definitions of equivalence relations and partitions you learned in Ch. 7? DQ 3 · How is the principle of inclusion and exclusion related to the rules for manipulation and simplification of logic predicates you learned in Ch. 2? DQ 4 · In Example 7.36, the author provides an example using PERT. MS Project is a software program for project management. How do you think the programmers of MS Project apply the learning in Chapter 7 to their algorithms? MTH 221 Week 4 Individual Assignment Selected Textbook Exercises Complete 10 questions below. Please review the rubric posted in week 1 for math problems. Submit to your assignment tab. Submit a certificate of originality for this assignment. Ch. 11 of Discrete and Combinatorial Mathematics Exercise 11.1, problems 3, 11 Ch. 11 of Discrete and Combinatorial Mathematics Exercise 11.2, problem 4 Exercise 11.3, problem 5a Exercise 11.4, problem 3a Exercise 11.5, problem 2 Ch. 12 of Discrete and Combinatorial Mathematics Exercise 12.1, problem 2 Exercise 12.2, problem 6 Exercise 12.3, problem 2 Exercise 12.5, problem 1 MTH 221 Week 4 Team Selected Textbook Exercises Complete 4 questions below. Please review the rubric posted in week 1 for math problems. Have one team member submit to their assignment tab. Submit a certificate of originality for this assignment. Ch. 11 of Discrete and Combinatorial Mathematics Exercise 11.1, problems 6, & 16a Ch. 12 of Discrete and Combinatorial Mathematics Exercise 12.1, problems, 7, & 11
MTH 221 Week 4 DQS DQ 1 · Random graphs are a fascinating subject of applied and theoretical research. These can be generated with a fixed vertex set V and edges added to the edge set E based on some probability model, such as a coin flip. Speculate on how many connected components a random graph might have if the likelihood of an edge (v1,v2) being in the set E is 50%. Do you think the number of components would depend on the size of the vertex set V? Explain why or why not. DQ 2 · You are an electrical engineer designing a new integrated circuit involving potentially millions of components. How would you use graph theory to organize how many layers your chip must have to handle all of the interconnections, for example? Which properties of graphs come into play in such a circumstance? DQ 3 · Trees occur in various venues in computer science: decision trees in algorithms, search trees, and so on. In linguistics, one encounters trees as well, typically as parse trees, which are essentially sentence diagrams, such as those you might have had to do in primary school, breaking a natural-language sentence into its components—clauses, subclauses, nouns, verbs, adverbs, adjectives, prepositions, and so on. What might be the significance of the depth and breadth of a parse tree relative to the sentence it represents? If you need to, look up parse tree and natural language processing on the Internet to see some examples. DQ 4 · In Section 12.4 we learn about the Merge Sort algorithm; it is more efficient that the Bubble sort we learned about in Chapter 10. Doing some research on the Internet can you find a sorting algorithm more efficient than the Merge Sort? If you find one please describe it and list your reference. MTH 221 Week 5 Individual Assignment Selected Textbook Exercises Complete 5 questions below. Please review the rubric posted in week 1 for math problems. Submit to your assignment tab. Submit a certificate of originality for this assignment. Ch. 15 of Discrete and Combinatorial Mathematics Exercise 15.1, problems 1a, 2a,4a, 9, & 12 MTH 221 Week 5 Learning Team Research Presentation Submit the final Research Presentation. Please review the rubric posted in week 1 for the team project Have one team member submit to their assignment tab Submit a certificate of originality for this assignment MTH 221 Week 5 DQS DQ 1 · How does Boolean algebra capture the essential properties of logic operations and set operations? DQ 2 · How does the reduction of Boolean expressions to simpler forms resemble the traversal of a tree, from the Week Four material? What sort of Boolean expression would you end up with at the root of the tree? DQ 3 · The introduction of Chapter 15 in your book introduces you to two founders of Boolean algebra and its applications (Boole and Shannon). After performing some research, share with the class some practical applications of Boolean algebra. Please cite your source. DQ 4 · In review of the material you have learned over the past 5 weeks which element has made the biggest impression on you? What element do you think you can use in future work or school applications?
Get MTH 221 entire course :
https://www.justquestionanswer.com/homework-solution-details/58380/mth-221-entire-course-university-of-phoenix
#24hourmathhotline#math assignment help#best assignment service#expert assignment help#best essay writing website
0 notes