#APT37
Explore tagged Tumblr posts
Text
KoSpy es un nuevo software espía para Android atribuido al grupo norcoreano APT37 que se hace pasar por aplicaciones de utilidad y está dirigido a usuarios de habla coreana e inglesa en @GooglePlay.
0 notes
Text
North Korea-linked APT37 exploited IE zero-day in a recent attack
http://i.securitythinkingcap.com/TFWCfr
0 notes
Text
North Korean Hackers Using New VeilShell Backdoor in Stealthy Cyber Attacks
Threat actors with ties to North Korea have been observed delivering a previously undocumented backdoor and remote access trojan (RAT) called VeilShell as part of a campaign targeting Cambodia and likely other Southeast Asian countries. The activity, dubbed SHROUDED#SLEEP by Securonix, is believed to be the handiwork of APT37, which is also known as InkySquid, Reaper, RedEyes, Ricochet Chollima,
0 notes
Text
Nordkoreanische Hacker nutzen neue VeilShell-Hintertür bei getarnten Cyberangriffen
Bedrohungsakteure mit Verbindungen zu Nordkorea wurden dabei beobachtet, wie sie eine zuvor nicht dokumentierte Backdoor und einen Remote-Access-Trojaner (RAT) namens VeilShell im Rahmen einer Kampagne einsetzten, die auf Kambodscha und wahrscheinlich andere südostasiatische Länder abzielte. Die Aktivität mit dem Namen SHROUDED#SLEEP von Securonix wird APT37 zugeschrieben, das auch als InkySquid,…
0 notes
Text
China's HUGE New Year's Eve Windows Hack Attack Targets Millennial Democrats.
China’s HUGE New Year’s Eve Windows Hack Attack Targets Millennial Democrats.
I’d just like to thank you, China. By including me in yesterday’s massive, personally motivated anti-Windows hack attack, as covered yesterday by Forbes Magazine, you gave me the best present anyone ever has, in this whole ten-year period. Furthermore, you used a Russian ransomware virus, but a variant of it created by yourselves, hinting strongly that you and Russia were in on this…
View On WordPress
#AltRight#AmazonOfMalware#AntonKamykin#APT37#BraveNewsBlog#Bromium#Buttigieg#Cerber#Cerber32#China#DailyStormer#DeepPanda#DemocraticParty#Democrats#DonaldTrump#DystopianTechnology#ElliottRodger#FarLeftIsAltRight#FLOKINet#FranciscoDias#FranTech#Hackers#Instagram#ipv4infoRU#JinpingXi#Malevanov#Maltego#MayorPete#Microsoft#MortonTelecom
1 note
·
View note
Text
North Korean hackers target phones, Windows devices with new malware
State-sponsored North Korean hackers are as soon as once more concentrating on victims with a brand new type of malware that would presumably hijack cell and PC units. In keeping with a brand new report from cybersecurity researchers AhnLab, a bunch generally known as APT37 (AKA RedEyes, Erebus, a recognized North Korean group believed to be strongly affiliated with the federal government), was…

View On WordPress
0 notes
Text
North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
The Hacker News : The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics. APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea's Ministry of State Security (MSS) unlike the Lazarus and http://dlvr.it/SjSyN4 Posted by : Mohit Kumar ( Hacker )
0 notes
Text
APT37 utiliza Internet Explorer Zero-Day para propagar malware
APT37 utiliza Internet Explorer Zero-Day para propagar malware
El grupo de amenazas norcoreano APT37 pudo explotar una vulnerabilidad de día cero de Internet Explorer para implementar documentos cargados con malware como parte de su campaña en curso dirigida a usuarios en Corea del Sur, incluidos desertores, periodistas y grupos de derechos humanos. El Grupo de análisis de amenazas (TAG) de Google encontró la falla de día cero en el motor JScript de Internet…
View On WordPress
0 notes
Text
北朝鮮のサイバー犯罪グループ「APT37」がInternet Explorerのゼロデイ脆弱性を突く攻撃を行っていたと判明
北朝鮮のサイバー犯罪グループ「APT37」がInternet Explorerのゼロデイ脆弱性を突く攻撃を行っていたと判明 Source: https://gigazine.net/news/rss_2.0/
View On WordPress
0 notes
Text
North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
http://i.securitythinkingcap.com/SjSfXK
0 notes
Text
State hackers are still using Internet Explorer zero-days
State hackers are still using Internet Explorer zero-days
Google’s Threat Analysis Group (TAG) revealed today that a group of North Korean hackers tracked as APT37 exploited a previously unknown vulnerability in Internet Explorer (known as a zero-day) to infect South Korean targets with malware. Google TAG was made aware of this recent attack on October 31 when multiple VirusTotal contributors from South Korea malicious Microsoft Office document named…

View On WordPress
0 notes
Text
[Media] stegoWiper
stegoWiper A powerful and flexible active attack for disrupting stegomalware Over the last 10 years, many threat groups have employed stegomalware or other steganography-based techniques to attack organizations from all sectors and in all regions of the world. Some examples are: APT15/Vixen Panda, APT23/Tropic Trooper, APT29/Cozy Bear, APT32/OceanLotus, APT34/OilRig, APT37/ScarCruft, APT38/Lazarus Group, Duqu Group, Turla, Vawtrack, Powload, Lokibot, Ursnif, IceID, etc. https://github.com/mindcrypt/stegowiper
0 notes
Text
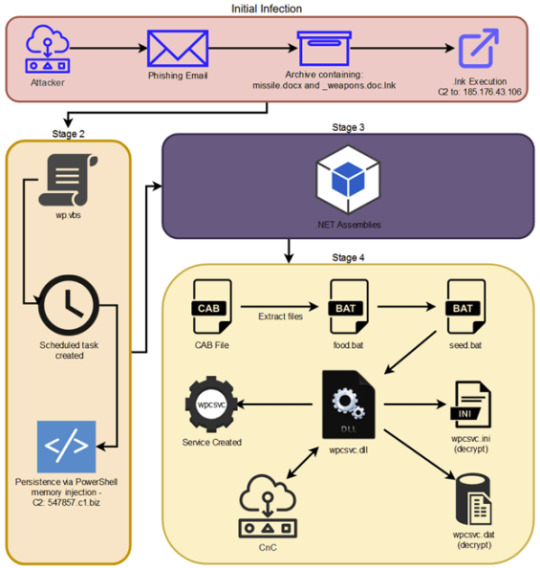
Is APT28 behind the STIFF#BIZON attacks attributed to North Korea-linked APT37?
Is APT28 behind the STIFF#BIZON attacks attributed to North Korea-linked APT37?
View On WordPress
0 notes
Text
【蠢蠢欲動】北韓國家級黑客組織APT37發惡意軟件竊南韓機密 - wepro180 而其他網絡安全公司也將其追蹤,各自將之命名為StarCruft(Kaspersky Lab)、Group123(Cisco Talos)或FreeMilk(Palo Alto Networks)。該組織為朝鮮政權利益 ... https://ift.tt/3D0CGsw
0 notes
Text
Los piratas informáticos del estado-nación atacan a los periodistas con malware Goldbackdoor
Los piratas informáticos del estado-nación atacan a los periodistas con malware Goldbackdoor
Una campaña de APT37 usó un malware sofisticado para robar información sobre las fuentes, que parece ser un sucesor de Bluelight. Fuente
View On WordPress
0 notes