#Best TCP Assignment Help
Explore tagged Tumblr posts
Text
can vpn port be blocked
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can vpn port be blocked
VPN port blocking
VPN port blocking occurs when internet service providers or network administrators restrict or limit the flow of data through specific ports commonly used by VPN services. This practice aims to control or prevent users from accessing VPNs to maintain network security or enforce restrictions. Understanding how VPN port blocking works is crucial for users seeking to bypass these restrictions and secure their online activities.
When a VPN connection is established, it typically uses specific communication ports to transmit encrypted data between the user's device and the VPN server. Some ISPs or network administrators employ deep packet inspection techniques to identify and block VPN traffic by targeting these ports. By blocking these ports, they hinder the VPN's ability to function correctly, leading to connection failures or slow speeds.
To overcome VPN port blocking, users can employ various strategies. One common approach is to switch to a different VPN protocol or port that is not commonly targeted for blocking. For example, using TCP port 443, which is commonly used for secure HTTPS connections, can help disguise VPN traffic as regular web traffic and bypass restrictions.
Users can also try using obfuscation techniques provided by certain VPN services to mask VPN traffic and make it harder to detect and block. Additionally, utilizing obfuscated servers or servers that support stealth VPN protocols can help evade port blocking measures effectively.
In conclusion, VPN port blocking poses a challenge for users seeking to maintain online privacy and security. By understanding how it works and implementing the appropriate countermeasures, individuals can overcome these restrictions and continue to enjoy the benefits of using VPN services without interference.
Network traffic restriction
Network traffic restriction refers to the practice of controlling and managing the flow of data across a network to ensure optimal performance, security, and efficiency. By imposing limitations on the amount and types of data that can pass through a network, organizations can prevent issues such as network congestion, data breaches, and unauthorized access.
One common method of network traffic restriction is the use of firewalls, which act as gatekeepers by filtering incoming and outgoing traffic based on predefined security rules. Firewalls can block potentially harmful traffic, such as malware or suspicious connections, while allowing legitimate data to pass through unimpeded.
Another approach to network traffic restriction is the implementation of Quality of Service (QoS) policies, which prioritize certain types of traffic over others. For example, real-time services like video conferencing or VoIP calls may be given higher priority to ensure a smooth and uninterrupted user experience, while less time-sensitive traffic like file downloads can be assigned lower priority.
Network traffic restriction is essential in modern networks where the volume of data being transferred is constantly increasing. By effectively managing and controlling network traffic, organizations can improve the overall performance of their networks, enhance security posture, and ensure that critical applications and services receive the bandwidth they require to function optimally.
In conclusion, network traffic restriction plays a crucial role in maintaining a secure, efficient, and reliable network environment. By leveraging tools such as firewalls and QoS policies, organizations can effectively manage the flow of data across their networks and mitigate potential issues that could impact performance and security.
Firewall configurations for VPN ports
Title: Best Practices for Firewall Configurations for VPN Ports
In today's digital landscape, where remote work is increasingly prevalent, securing virtual private networks (VPNs) has become paramount. A crucial aspect of VPN security is the configuration of firewall settings to safeguard against unauthorized access and potential threats. Understanding the best practices for firewall configurations for VPN ports is essential for maintaining a robust defense against cyber attacks.
Firstly, it's important to limit access to VPN ports by configuring the firewall to only allow traffic from authorized sources. This can be achieved by implementing strict access control lists (ACLs) that specify which IP addresses or ranges are permitted to connect to the VPN server. By restricting access in this manner, organizations can minimize the risk of unauthorized individuals gaining entry to the network.
Additionally, configuring the firewall to enforce strong encryption protocols such as Transport Layer Security (TLS) or Internet Protocol Security (IPsec) is vital for ensuring the confidentiality and integrity of data transmitted over the VPN. These encryption protocols establish secure communication channels between endpoints, thereby safeguarding sensitive information from interception or tampering by malicious actors.
Furthermore, regularly updating firewall rules and security policies is essential for adapting to evolving threats and vulnerabilities. As new exploits and attack vectors emerge, organizations must remain vigilant in maintaining a proactive stance against potential security breaches. Conducting periodic security audits and assessments can help identify any weaknesses in firewall configurations and address them promptly.
In conclusion, implementing robust firewall configurations for VPN ports is imperative for protecting organizational networks from cyber threats. By adhering to best practices such as restricting access, enforcing encryption protocols, and staying updated on security measures, businesses can fortify their VPN infrastructure and mitigate the risk of data breaches and unauthorized access.
Bypassing port restrictions with VPN
Virtual Private Networks (VPNs) are powerful tools that enable internet users to bypass port restrictions for a variety of reasons. Many countries, organizations, or internet service providers impose restrictions on certain ports to control access to specific content or services.
In situations where specific ports are blocked, using a VPN can provide a solution by encrypting internet traffic and routing it through a server located in a different region. By doing so, VPNs mask the user's true IP address and assign a new one based on the server location. This allows users to access the internet as if they were located in a different country, effectively bypassing any port restrictions that may be in place.
One common scenario where bypassing port restrictions with a VPN is useful is in accessing online gaming platforms. Some online games require specific ports to be open for gameplay, and if these ports are restricted by an internet service provider, players may experience connectivity issues. By using a VPN to reroute their internet traffic through a different port or server, gamers can ensure a smoother gaming experience without being hindered by port restrictions.
It is important to note that while using a VPN can help bypass port restrictions, users should also be aware of any potential legal implications or terms of service violations associated with circumventing such restrictions. Additionally, not all VPN services may be effective in bypassing port restrictions, so users should choose a reputable VPN provider known for its ability to provide reliable access to restricted ports. By understanding how VPNs work and their potential benefits, users can navigate port restrictions more effectively and enjoy a more open internet experience.
VPN tunneling protocols
VPN tunneling protocols are the foundation of secure and private internet connections. These protocols establish the rules and encryption methods that govern how data packets are transmitted between a user's device and a VPN server. There are several popular VPN tunneling protocols used today, each with its own strengths and weaknesses.
One of the most widely used VPN tunneling protocols is OpenVPN. Known for its open-source nature and strong security features, OpenVPN is highly versatile and compatible with a wide range of devices and operating systems. It uses SSL/TLS protocols for encryption and offers excellent privacy and security.
Another commonly used protocol is IPsec (Internet Protocol Security). IPsec operates at the network layer of the OSI model and provides strong encryption and authentication mechanisms. It is often used in combination with other protocols to enhance security and ensure data integrity.
PPTP (Point-to-Point Tunneling Protocol) is another older but still widely supported VPN protocol. While PPTP is known for its ease of use and fast connection speeds, it is considered less secure than newer protocols like OpenVPN and IPsec.
L2TP/IPsec (Layer 2 Tunneling Protocol over IPsec) combines the best of both L2TP and IPsec protocols to provide a secure and stable VPN connection. L2TP/IPsec is often used on mobile devices due to its strong security features and compatibility with a wide range of platforms.
In conclusion, choosing the right VPN tunneling protocol depends on your specific needs and priorities. Whether you prioritize speed, security, or compatibility, there is a protocol that can meet your requirements and ensure a safe and private internet browsing experience.
0 notes
Text
Computer Network Assignment Help

Computer Network Assignment Help
In Computer Network Assignment Help we provide assistance and guidance to students individuals who are tasked with assignments or projects related to computer networking. This assistance can come in various forms, including:
Clarification of Concepts: Assignment help may involve explaining fundamental concepts and theories related to computer networks. This can help students understand the underlying principles and theories that are necessary for their assignments.
Problem Solving: Many computer network assignments involve solving specific problems or scenarios. Assignment help can guide individuals in tackling these problems step by step and coming up with the correct solutions.
Research Guidance: For more in-depth assignments, research may be required. Assignment help can assist in finding relevant resources, such as books, articles, or online sources, and guide students on how to use these materials effectively.
Network Design: Some assignments may require designing computer networks. Assignment help can provide insights on how to plan, design, and implement network solutions based on specific requirements.
Protocol Explanation: Networking assignments often involve understanding and explaining network protocols. Assignment help can simplify complex protocol
explanations and make it easier to comprehend.
Troubleshooting: If the assignment involves diagnosing and resolving network issues, assignment help can assist in identifying the problems and providing troubleshooting steps.
Documentation and Reports: Assignment help can guide students on how to structure their reports and document their work properly, ensuring that it is well-organized and well-presented.
Programming: In computer network assignments that require coding or scripting for network-related tasks, assistance may be provided in writing code, debugging, or explaining the logic behind the code.
Security and Analysis: For assignments related to network security or performance analysis, assignment help can offer insights into the best practices and tools to use.
Review and Feedback: Assignment help can involve reviewing the work completed by the student and providing feedback for improvement.
About Computer Network :
A computer network is a collection of interconnected devices and systems that communicate and share resources with each other. These networks are essential components of modern computing and play a crucial role in enabling data exchange, resource sharing, and communication among various devices, such as computers, servers, smartphones, and other hardware.
Here are some key elements and concepts related to computer networks:
Nodes: Nodes are individual devices or computers connected to the network. These can include personal computers, servers, routers, switches, smartphones, tablets, and more.
Links: Links represent the physical or logical connections that allow data to flow between nodes. These connections can be wired, such as Ethernet cables, or wireless, such as Wi-Fi or cellular connections.
Topology: The network’s topology defines the physical or logical layout of nodes and links. Common network topologies include bus, star, ring, mesh, and hybrid configurations.
Protocols: Network protocols are a set of rules and conventions that govern data transmission and communication on a network. Examples include TCP/IP, HTTP, FTP, and many others.
LAN (Local Area Network): LANs are typically confined to a limited geographic area, such as a home, office, or campus. They are used for connecting devices within close proximity and are usually owned and managed by a single entity.
WAN (Wide Area Network): WANs cover larger geographical areas, often spanning cities, countries, or even continents. The internet is a global example of a WAN, connecting networks and devices worldwide.
Internet: The internet is a vast, interconnected network of networks that enables global communication and information exchange. It operates on a variety of protocols, primarily the TCP/IP suite.
Intranet: An intranet is a private network built using internet technologies but restricted to an organization or specific group of users. It is used for internal communication and collaboration.
Extranet: An extranet extends the capabilities of an intranet to include authorized external users, such as business partners or customers, providing controlled access to specific resources.
Firewall: A firewall is a network security device or software that monitors and controls incoming and outgoing network traffic to protect against unauthorized access and potential threats.
Router: Routers are devices that forward data between networks, typically connecting a local network to the internet. They use routing tables to determine the best path for data packets.
Switch: Switches are network devices that operate at the data link layer and are used to create and manage LANs. They forward data to the appropriate destination based on MAC (Media Access Control) addresses.
Server: Servers are specialized computers designed to provide services or resources to network clients. These services can include file storage, email, web hosting, and more.
Client: A client is a device or computer that requests and uses services or resources from servers or other network devices.
Wireless Networks: These networks use radio waves to transmit data, and they are prevalent in homes, businesses, and public spaces. Common wireless standards include Wi-Fi and cellular networks.
Computer networks have become an integral part of our daily lives, enabling communication, information sharing, online collaboration, and access to a wide range of services and resources. They come in various sizes and complexities, from small home networks to vast global internetworks, and are essential for modern business, education, entertainment, and research.
We provide these services : computer network assignment help in universities , computer network assignment help in colleges , computer network assignment help with discount , computer network assignment help for students.
We provide plagiarism-free and insightful solution. Our processional team build each solution from scratch, assisted with intensive research from high-quality sources. Proofreading is done so that the final answers are orderly, real, and properly formatted. We not only assure you success but also guarantee you that learning with our solutions will be a easy.
We thoroughly study and provide help from various sources, including teachers, professors, textbooks, online resources, and tutoring services. When seeking help, it’s important to ensure that it aligns with your institution’s academic integrity policies, as plagiarism or unethical practices can have serious consequences.
0 notes
Text
Top CCNA Topics You Need to Master in 2025: A Guide to What Really Matters

If you're planning to take the Cisco Certified Network Associate (CCNA) exam, you might be wondering: What are the most important topics I need to focus on? With so much to study, it's easy to feel overwhelmed. The good news is that the CCNA covers a structured set of core topics, and some areas are especially important for both the exam and real-world networking jobs.
In this guide, we'll walk you through the most critical CCNA training topics you should master in 2025. Whether you're preparing for the exam or building your foundational skills, understanding these key subjects will boost your confidence and help you succeed.
Why It’s Important to Know the Key CCNA Topics
The CCNA certification is designed to test your ability to install, configure, and troubleshoot networks. Employers value it because it proves you have hands-on knowledge of networking fundamentals. But not all exam topics carry equal weight, and some are more practical and relevant than others.
Focusing on the right topics not only prepares you for the exam but also ensures you're ready to handle real-world tasks—like setting up IP addresses, configuring routers, or securing a network from threats. Understanding these concepts deeply will also prepare you for advanced Cisco certifications and career growth.
Network Fundamentals: The Building Blocks of Networking
Network fundamentals form the backbone of the CCNA exam. This section includes basic networking concepts, terminology, and models—like the OSI and TCP/IP models—that help you understand how data travels from one device to another. You'll need to grasp what happens at each layer of the OSI model and how different devices (like switches and routers) operate within a network.
You'll also encounter key concepts such as bandwidth, latency, data encapsulation, and the difference between unicast, multicast, and broadcast traffic. These basics might sound simple, but they create the foundation for everything else in the CCNA curriculum.
IP Addressing and Subnetting: Your Passport to Network Configuration
Mastering IP addressing is absolutely essential. Without it, you won’t be able to configure networks properly. The CCNA covers both IPv4 and IPv6, which are used to identify devices on a network. You’ll learn how to calculate and assign IP addresses, as well as how to create efficient subnetting schemes.
Subnetting helps divide a large network into smaller, more manageable segments. For example, a company might use subnetting to isolate departments like HR, Sales, and IT. Supernetting, on the other hand, is used to aggregate multiple subnets. Knowing when and how to use each method is a must-have skill for any networking professional.
If you struggle with subnetting at first, you're not alone—it’s a challenging topic, but with practice, it becomes second nature.
Routing and Switching: Navigating the Heart of the Network
Routing and switching are central to network operation. In this section, you'll learn how routers determine the best path for data to travel and how switches direct traffic within a local network. The CCNA exam tests your ability to configure and troubleshoot both types of devices.
You'll study routing protocols such as RIP, EIGRP, and OSPF, which help routers exchange information with each other. Each protocol has different features and use cases, so understanding when to use them is important. You'll also dive into VLANs (Virtual Local Area Networks) and STP (Spanning Tree Protocol), which are key to managing large networks and avoiding loops.
These are not just exam topics—they’re real-world tools that you’ll use daily in jobs like Network Engineer or IT Administrator.
Additional Key CCNA Topics to Study
Once you’re comfortable with the fundamentals, there are several other important areas you’ll need to understand to be fully prepared for the CCNA certification:
LAN Technologies: You’ll need to know how Ethernet works, including frame formats, MAC addresses, and switch operation.
WAN Technologies: This covers technologies used to connect networks over long distances, such as PPP, HDLC, and Frame Relay. While older, these still appear in legacy systems.
Network Security Concepts: Topics like Access Control Lists (ACLs), Network Address Translation (NAT), and device hardening techniques are crucial for protecting networks.
Wireless Networking: As Wi-Fi becomes more widespread, you’ll learn how to set up and secure wireless networks, understand wireless standards (like 802.11ac), and troubleshoot common issues.
IPv6: With the global adoption of IPv6 increasing, you’ll need to understand how IPv6 works, how it’s different from IPv4, and how to configure devices for it.
Tips to Master CCNA Topics Faster
To help you retain and apply what you’ve learned, here are some effective strategies to keep in mind:
Practice with Packet Tracer or GNS3: Use these tools to simulate real networking environments. They help you gain hands-on experience without expensive hardware.
Break Down Complex Topics: Take challenging areas like subnetting and routing protocols step by step. Use diagrams and cheat sheets to simplify them.
Study a Little Every Day: Daily practice builds long-term memory. Even 30 minutes a day can make a difference over time.
Use CCNA-Specific Study Guides: Trusted resources like Cisco’s official cert guides and video courses can help reinforce your understanding.
Join Online Communities: Participate in forums like Reddit, Cisco Learning Network, or Discord groups to discuss tricky questions and get help from peers.
Conclusion
The CCNA exam covers a wide range of topics, but by concentrating on the ones we’ve outlined here, you can prepare smarter—not harder. From IP addressing to routing protocols and network security, each topic serves a real-world purpose that you’ll encounter in your career.
The key to success is consistency. Study regularly, get hands-on practice, and don’t hesitate to ask for help when needed. Whether you’re new to networking or building on existing skills, mastering these essential CCNA topics in 2025 will put you on the path to a successful IT career.
Ready to start your journey? Open your study guide, fire up Packet Tracer, and begin building your networking future today.
FAQs
How much math is involved in CCNA? Not too much, but you’ll need to be comfortable with binary and decimal conversions, especially when learning subnetting.
Is IPv6 really important to learn now? Yes. Although many networks still use IPv4, IPv6 adoption is growing. Learning it now ensures you're ready for future changes.
Do I need to memorize the OSI model? Yes, but more importantly, you need to understand how it works. Knowing what each layer does helps you troubleshoot network issues more effectively.
0 notes
Text
CCNA Course Overview: What You Will Learn in the Latest Cisco Certification

The Cisco Certified Network Associate (CCNA) certification is one of the most popular and respected IT credentials for professionals entering the field of networking. Designed by Cisco, this certification verifies your knowledge of core networking concepts, security basics, IP services, and even emerging technologies like network automation.
If you're planning to join a CCNA course, it's important to understand what topics the current version of the exam covers.
Let’s take a detailed look at each domain covered in the updated CCNA syllabus.
Network Fundamentals
In this first section of the CCNA course, you’ll learn the basics of how computer networks work. This includes understanding the OSI and TCP/IP models, which explain how data travels from one device to another over a network.
You’ll also get introduced to different network components such as routers, switches, hubs, access points, and firewalls. A major focus will be on IPv4 and IPv6 addressing, subnetting, and the use of IP addresses to connect devices.
Network Access
The second topic in the CCNA course focuses on how devices connect to a Local Area Network (LAN). You’ll study how Ethernet works, and how data is transmitted over cables and switches. This includes learning about switching technologies, MAC addresses, and how switches forward data.
An important topic here is VLANs (Virtual Local Area Networks), which allow network administrators to logically separate traffic within the same physical network. You’ll also explore trunking protocols like 802.1Q that allow multiple VLANs to communicate through a single link. The course also covers port security, which helps protect switches from unauthorized access, and provides an introduction to wireless networking (WLANs) and how Wi-Fi connects devices in a LAN environment.
IP Connectivity
This part of the course focuses on how devices on different networks communicate with each other. You’ll begin with routing concepts — understanding how routers choose the best path for data. You’ll configure static routing, which involves manually setting up routes, and explore dynamic routing protocols like RIP, OSPF, and EIGRP, which automatically adjust to changes in the network.
You’ll also learn to analyze routing tables and understand how routers make decisions. Both IPv4 and IPv6 routing are covered, making sure you’re prepared for current and future networking environments. By mastering IP connectivity, you'll be able to build and troubleshoot complex network topologies confidently.
IP Services
Modern networks rely on various IP services to function efficiently. In this section, you’ll dive into NAT (Network Address Translation) and PAT (Port Address Translation), which allow private networks to access the internet using a single public IP address. You'll also configure DHCP (Dynamic Host Configuration Protocol) to automatically assign IP addresses to devices, and DNS (Domain Name System) to resolve domain names into IP addresses.
Another crucial topic in this domain is Access Control Lists (ACLs), which are used to filter traffic and enhance security. The course also introduces Quality of Service (QoS), which helps prioritize important traffic like voice or video over less critical data. These services ensure better control, performance, and protection within a network.
Security Fundamentals
Security is a major concern in today’s digital world, and the CCNA course includes a solid introduction to network security. You’ll learn about common threats like malware, phishing, spoofing, and Denial of Service (DoS) attacks. This section emphasizes best practices for protecting networks, including the use of strong passwords, secure remote access (SSH), and firewalls.
You’ll also get hands-on experience with ACLs to control which devices or users can access specific parts of the network. Other topics include endpoint security tools such as antivirus software and implementing policies that ensure device-level safety. Although this is not an advanced security course, it prepares you well for both securing small networks and learning more advanced concepts later.
Automation and Programmability
As networks grow in size and complexity, automation has become essential. The final topic in the CCNA course introduces the basics of network automation and programmability. You’ll learn about tools and concepts that allow you to automate repetitive network tasks and manage devices more efficiently.
This includes an introduction to APIs (Application Programming Interfaces) and RESTful APIs, which allow software applications to communicate with network devices. You’ll also learn about Cisco DNA Center, a controller-based solution for managing networks through a centralized dashboard. The course explains JSON (JavaScript Object Notation) and other data formats used in automation tools. Even though you won’t dive deep into coding, you’ll understand how automation is shaping the future of networking and how to prepare for it.
Conclusion The CCNA certification gives you a strong foundation in both the theoretical and practical aspects of networking. With topics ranging from basic IP addressing to advanced services and security, it prepares you for real-world IT roles such as Network Technician, IT Support, Network Engineer, and more.
Whether you’re a student, working professional, or someone switching careers, the updated CCNA course is a smart investment. It also acts as a stepping stone to more specialized Cisco certifications like CCNP or CyberOps Associate.
If you're looking to join a CCNA course near you, make sure the training includes hands-on labs, covers all these topics, and offers exam preparation support. A well-structured course can make a huge difference in how confidently you pass the exam and apply your skills in real jobs.
0 notes
Text
ing routine — and stick with it
(TCP)How to start a healthy morning routine — and stick with it — decidedly or adversely — on the remainder of your day. By rehearsing a solid morning schedule, you can build your efficiency, decline pressure, support satisfaction and that’s just the beginning.
Healthy Morning Routine: An excessive number of individuals awaken every day to a torrent of obligations that wind up directing the progression of their mornings. On the off chance that you have children or pets, you need to really focus on them. The vast majority have morning tasks, need to make breakfast, prepare for work, etc. I’m not proposing you evade your obligations. However, actually, you will be more ready to deal with everything on your plate every morning, in the event that you start with a sound self-care schedule.
Beneath, I share my very own portion solid morning propensities, just as tips and deceives for making a standard that sticks — and what to do when you vacillate. A portion of the propensities in my standard will impact you, while others may not. As you read on, remember your own way of life and wellbeing objectives, so you can make a morning schedule that will turn out best for you.
1. Set your alarm to work for you — not against you
To give yourself enough an ideal opportunity for self-care in the first part of the day, set your morning timer a bit before – and head to sleep prior, as well.
The initial step to dismissing your day from right is changing your rest timetable to guarantee you have sufficient time in the first part of the day for you as well as your obligations. In the event that your children get up at 6:30 a.m., this implies getting up before them. Or on the other hand, regardless of whether you don’t have children or pets to really focus on, on the off chance that you as a rule get up at 7 a.m. to scramble out the entryway by 7:30, it’s the ideal opportunity for you to begin your days sooner.
All things considered, rest is significant. At the point when you change your caution to awaken sooner, you likewise need to change your sleep time to turn in prior. There isn’t anything sound about being restless, so intend to get no less than seven hours of rest.
2. Take in the new day
What’s the principal thing you do when you get up in the first part of the day?
Tragically, for some individuals, the appropriate response is “going after my telephone.” If that is you, how long do you go through every early daytime looking over and possibly allowing pressure to work because of what you find on the news, web-based media or actually looking at messages?
Imagine a scenario where you made a standard that — prior to going after you telephone — you took six long, full breaths to concentrate on the force and gift of your own life power.
Since the stomach goes about as both a respiratory and center postural muscle, diaphragmatic breathing not just assists you with decidedly centering your brain, it primes your body to help development and great stance.
3. Drink water before coffee
Rehydrating with a glass of water first thing can support your digestion by up to 30%, research has shown.
Since we lose water through our breath and sweat while we rest, we generally awaken parched. Taking into account that the grown-up human body is included up to 60% water, hydration is fundamental for acceptable wellbeing.
Drinking water first thing won’t just assistance rehydrate you yet can likewise kick off your digestion, boosting it by up to 30%, as indicated by research.
4. Move your body every which way
There is an explanation we instinctually stretch when we first wake up. Our bodies need development in the wake of being inactive. Why not immediate that nature to be just about as useful as could be expected?
Maybe than just doing a fast stretch in bed and afterward approaching your day, preferring your prevailing side, put your body right and set it up for day by day movement by taking it through all planes of movement, equitably utilizing the two sides of our bodies. You can achieve this with a speedy yoga stream or this 10-minute body-weight exercise:
5. Make time to work out
Possibly you can’t fit in a full exercise toward the beginning of the day. That is OK. You can sneak in practice by stacking it onto a portion of your current morning propensities. Throughout recent years, I’ve been doing push-ups before I get into the shower and squats while I clean my teeth.
It’s called propensity stacking, an idea James Clear references in his book, “Nuclear Habits.” By stacking another activity propensity onto a morning propensity that is now imbued, it makes it simpler to maintain.
6. Put your psyche right
Give yourself a fresh start to begin the day with only a couple of moments of care reflection.
There are various applications that proposition free directed reflections under 10 minutes. Or then again you can set a clock on your telephone to whatever length and sit unobtrusively centered around the impressions of your breath or discreetly rehashing a positive confirmation, mantra or expectation you need to set for your day.
7. Cultivate an attitude of gratitude
Exploration shows that rehearsing appreciation can diminish torment, upgrade sympathy and lessen animosity — which is an extraordinary method to begin your day, particularly on the off chance that you have a regularly scheduled drive in rush hour gridlock. You can rehearse appreciation toward the beginning of the day by waking every day to watch the dawn, composing things you are thankful for in a diary, or joining an appreciation center into your contemplation.
By and by, I share an appreciation white board with my better half, and we each compose three things on it daily. It’s in fact an evening propensity, but since of its area in our main restroom, it’s one of the principal things we see each day. We’ve done it for a long time now, I actually love awakening to perceive what he composed and being helped to remember what I was appreciative for from the other day.
8. Make your bed
By making your bed each day, you exhibit to yourself that you assume individual liability for your assignments and focus on keeping your own space agreeable and clean. It starts a trend that builds up the establishment of your capacity to finish.
For additional on this, look at Adm. William H. McRaven’s book “Make Your Bed: Little Things That Can Change Your Life … furthermore, Maybe the World.”
9. Rehash your daily practice
This is the hardest part. Building up a routine is difficult. It’s justifiable, on the off chance that you begin solid in any case, waver. In the event that you rest in one morning or fail to remember some new propensities, don’t be too hard on yourself … yet in addition don’t surrender. Start again the following morning and attempt a portion of the ideas beneath to assist with keeping you on target.
8. Make your bed
By making your bed each day, you exhibit to yourself that you assume individual liability for your assignments and focus on keeping your own space agreeable and clean. It starts a trend that builds up the establishment of your capacity to finish.
9. Rehash your daily practice
This is the hardest part. Building up a routine is difficult. It’s justifiable, on the off chance that you begin solid in any case, waver. In the event that you rest in one morning or fail to remember some new propensities, don’t be too hard on yourself … yet in addition don’t surrender. Start again the following morning and attempt a portion of the ideas beneath to assist with keeping you on target.
10. Set yourself up for success
To make it simpler for you to achieve your sound morning self-care schedule, make strides the prior night to reduce your heap and make the things you need to accomplish more advantageous. For example, set your garments out for the following morning. On the off chance that you have youngsters, put their out garments, as well (or have them do it). Another choice is planning breakfast ahead of time. I make a major pot of cereal that I can simply heat up in the first part of the day. On the off chance that you take lunch to work or have to pack lunch for youngsters, do that ahead also.
Starting off prior can be perhaps the greatest test to survive. Influence innovation to help. Perhaps you need a more progressive alert tone to wake you. Or then again you may require a stronger, seriously surprising sound. Test out the various choices on your telephone. Since I battled with continually hitting nap, I put $30 in a clock with a warm light that progressively lights up the room before the alert goes off — and it worked for me. Sort out what works for you.
It is safe to say that you are prepared to begin another better morning schedule?
Tomorrow first thing is your chance!
Life is rushed for us all, however we can generally set aside a few minutes for things that we consider commendable. Trust me — your general wellbeing and day by day point of view are awesome.
1 note
·
View note
Text
College Theater AU
Hey guys! I’m back with the first chapter of a new fic. It’s small and mostly setup, but I promise it’ll get more involved in later chapters. Hope y’all like!
~~~~~
Chapter 1
“How goes your bio homework?” Jude’s best friend, Liliver, asks as she looks up from her assortment of turn-of-the-twentieth-century magazines.
Jude snorts, turning her computer to expose the fact that she has four different Chegg webpages pulled open. It’s only a week into sophomore year and the general education courses required of her were already kicking her ass.
“Why aren’t you doing your homework? I thought you had calc three this year,” she muses unhappily, going back to Chegg’s description of plant cells and cursing the fact she wasn’t in upper division yet. She wanted to do finance, not biology.
“I’m getting ideas for Katherine’s costumes,” she smiles, running her fingers over the delicate pages of the antique magazines. “I want to be ready when I get given my budget.”
“Don’t you need to know who’s playing Katherine before you start planning her costumes?” Jude raises a brow.
Liliver sends her a you’ve got to be kidding me look. “You’ll be Katherine, you dolt. You’ve been the lead girl in every musical you’ve tried out for.”
Jude tried to hide her self-satisfied smirk, but she knows Liliver isn’t wrong. She’s always been involved in performing arts, ever since she and her twin, Taryn, were adopted by her half-sister’s father.
Her adoptive father, Madoc, had a love of discipline and success drilled into him during his early days as a marine. It’s something he’d worked very hard to pass on to his children. Jude was the only one who really took his insistence to heart.
She’d been in dance class since her adoption. She started pointe in ballet and heels in tap a year before all her peers. She started taking voice lessons when she was eleven and she was the first person to try out for her high school’s production of Little Shop of Horrors, where she’d scored the roll of Audrey.
Now in college, Jude is the head of the the theater club. Her freshman year, she’d met Liliver—who went by the Bomb, due to her insistence on making costumes as complex as explosives—and the two had become fast friends. Bomb loved theater because she loved costuming, and she loved having money to sew stuff outside of her costume design classes.
“Have you found where you’re going to buy the newsboy caps?” Jude asks, steadfastly ignoring her homework for as long as possible.
Insmire College’s College Players had voted last semester and decided, almost universally, to perform Newsies for the fall semester. Jude was super excited, because she absolutely adored the story, but Bomb was kind of upset. She said that the costumes were all far too similar for her to really shine.
“I’ve been trolling Etsy and EBay,” she says as she flips the page of one of her magazines—bought from one of the local antique stores. “I’m more concerned about the jazz and tap shoes we’ll have to buy.”
“Not everyone will need new ones.”
“How many people do you know with tap shoes that look like Edwardian boots?” Liliver fixes her with a tired look and she just raises both hands in surrender.
“Well we’ll just have to see,” Jude shrugs. “I’ve talked to the dance team captain and the instructors for the dance classes at the gym. Maybe they’ll convince some students to try out.”
The issue with doing theater at a small college like Insmire is it’s difficult getting people to actually try out. Especially guys. And, given that the entire show is about newsboys, it’ll be problematic if only girls go out. While everyone involved knows Jude will be the main girl, nobody knows who is going to be playing Jack.
“Maybe we can convince Ghost to go out,” Bomb offers.
Both girls share a look before bursting out into cackling laughter that fills their shared dorm room. Ghost, their stage manager and good friend, is called Ghost because he is famous for hating being seen.
“Roach wants to be Davey,” Bomb says, trying and failing to keep her voice disinterested.
“Are you two a thing yet?” Jude calls her out, grinning as her friend hides her face behind a magazine and groans in embarrassment.
Liliver tries to ignore her and go back to her costume research, but more gentle ribbing eventually gets her to admit that they texted a lot over the summer break, but they aren’t official.
“He said we’re both invited to the Pike party after recruitment week.”
“I can’t believe your boyfriend’s in fucking Pike.” Jude can’t hide her disgust. Of all the people to be in Greek life, especially such a seedy fraternity. Although Roach did get his name from his weed dealing connections, so maybe they just use him for drugs.
She can respect the hustle, getting rich off of selling bad weed to entitled trust fund boys.
“He’s not my boyfriend!”
“Yet,” she snorts.
Liliver makes a face, sticking out her tongue.
Jude rolls her eyes and goes back to her biology homework, having officially reached the point where she’s just ready to plagiarize everything and call it a fucking day.
“Do you have a boyfriend?” Bomb asks and Jude has to stop herself from vomiting.
She and Bomb met when they became randomly assigned roommates freshman year. Originally, Jude had planned on rooming with her twin sister, but that all changed at the end of senior year, when Jude found out—on Valentine’s Day—that her boyfriend, Locke, was cheating on her. With Taryn. She swore off guys then and there, saying she’d just focus on her schooling and find a boyfriend later.
“No, and I don’t want one,” she announces with a frown. “Too much work and not worth the payout.”
Bomb purses her lips and fixes Jude with a look that Jude dutifully ignores. She’s not in the mood to get into her dislike of guys right now, not when biology was already putting her in a sour mood.
Her phone buzzes and Jude looks down to find a canvas message from their faculty advisor and director, asking her to confirm the tryout dates and making sure that she’ll be there to help him keep track of all the paperwork.
She responds quickly, saying she’ll make sure that she and Bomb are both there, Ghost might even be able to make it for the Friday tryout date.
They have tabling for the next three days for the Insmire club fair, then they have two more weeks to get the word out about tryouts. Fall semester tryouts are always the worst, because it’s difficult to get freshman to come to club meetings in the first week or so of college, but Jude is hopeful this year.
Tryouts are the first week of September. She’s got so much work to do before then, but she’s excited. She has way too much to focus on, she doesn’t need to worry about her sister or her ex, and she certainly doesn’t need to worry about finding a new guy.
She’ll be just fine.
~~~~~~~~~
Tag list: @cardan-greenbriar-tcp @hizqueen4life @slightlyrebelliouswriter23 @thewickedkings @aelin-queen-of-terrasen @cheekycheekycheeks @queen-of-glass @b00kworm @doingmyrainbow @andromeddea @jurdanhell
#college theater au#tyrannosaurus lex writes#jude duarte#the bomb#cardan greenbriar#soon#like next chapter#dont worry
31 notes
·
View notes
Text
Best Routers for Gaming | Top Gaming Routers of 2021
It is safe to say that you are not happy with your ping in internet games? It's conceivable that your Internet Service Provider (ISP) is easing back you down. Be that as it may, updating your stuff can shockingly affect dormancy in games. Obviously, we are not looking at diminishing the information slack from the screen or mouse. To get to a higher degree of ongoing interaction – you need to get the best WiFi switch for gaming. In any case, is a gaming switch really that significant, or is it's anything but a trick? Stick with us to realize what makes these gadgets diverse for normal switches and find the best gaming switches to get at the present time!
Do You Really Need a Gaming Router?
We should begin with the nuts and bolts. Would it be advisable for you to try and mess with a gaming switch as opposed to purchasing a customary one?
The short answer is "yes." That is to say, in the event that you need to take gaming to a higher level by smoothing out the traffic with explicit highlights like MU-MIMO and Quality of Service (QoS).
Would you like to get familiar with them? Then, at that point, continue to peruse.
What Makes the Best Gaming Router?
Traffic prioritization is the essential motivation behind why such countless individuals select to get WiFi switches for gaming rather than the standard ones. Be that as it may, there are other vital variables to consider when purchasing this sort of item.
What right? We should investigate.
Speed Limits (WiFi and Ethernet)
The most clear thing to guide your consideration toward is a switch's speed.
Be that as it may, you shouldn't take everything composed on the switch's crate at face esteem. The switch's presentation is straightforwardly affected by different variables.
For instance, the producer can brag about the switch supporting up to 3500 Mbps. Yet, without a decent remote norm, it's simply going to frustrate your ISP's latent capacity.
Remote and multi-band principles
The WiFi standard is perhaps the main things to pay special mind to.
Switches for gaming execute the most recent innovation like WiFi 5 and Wifi 6 (802.11ac and 802.11ax, individually) - it will extract the most from your ISP and convey the most ideal speed for countless gadgets.
Furthermore, here's a suggestion. Try not to surrender to allurements of purchasing a spending gaming switch with a WiFi 4 (802.11n). You will save a bit, however you'll get an all around out of date tech that can cause genuine speed choking.
What's more, you should stay away from single-band switches that help just a 2.4 GHz band - a channel fit for office work and web perusing. On the off chance that you are after web based gaming and live streaming – center around double band or tri-band gaming switches.
QoS
QoS adjust the approaching and active data transfer capacity for each gadget associated with a WiFi organization. For example, you can arrange the switch to focus on gaming applications for any remaining associations. With the best WiFi switch for gaming, you can fundamentally improve the speed in-game after some dabbling in with QoS settings.
MU-MIMO
MU-MIMO is an innovation that makes it's anything but a bigger number of gadgets to speak with a switch without upsetting the download speed. Thusly, it makes the association more dependable (particularly if individuals in your family are into versatile gaming or marathon watching TV arrangement from cell phones).
WiFi switch's web interface
Having a gadget with a wide scope of highlights is without a doubt significant. In any case, that doesn't imply that you must be educated to figure out everything.
Best WiFi switches accompany a client instinctive interface that makes it conceivable to explore through tabs and control the entirety of its highlights. The most ideal gadget:
• permits overseeing approaching and active traffic
• makes it conceivable to obstruct or whitelist explicit IPs
• permits port sending (allows you to open TCP and UDP ports to gain admittance to games or online administrations)
• allows you to see the rundown of gadgets associated with the WiFi organize and assign traffic
Handling power
Here's the reality. Gaming switches with amazing CPUs can deal with a bigger number of associations and utilize further developed programming. Therefore, by going for an all the more impressive gadget with more RAM, you will bring down ping in games much further.
Top 6 Best WiFi Routers for Gaming
Things being what they are, you've come here to track down the best switch for gaming? Here is a rundown of the top gadgets you can pick in 2021.
Right away, we should begin!
1 TP-Link Archer C5400X
2 Netgear Nighthawk XR500 Pro Gaming Router
3 Netgear Nighthawk X6 (R8000)
4 Zyxel Armor Z2
5 Asus ROG Rapture GT-AX11000
6 D-Link Exo DIR-882 (AC2600)
Outline
TP-Link Archer C5400X
Extraordinary MU-MIMO
Tri-band
MU-MIMO
VPN speed increase
Broadcast appointment decency
Telephone application
$$
Netgear Nighthawk XR500 Pro Gaming Router
Best for double band
Double band
MU-MIMO
DFS (Dynamic Frequency Selection)
Geo-channel
Telephone ap
$$
Netgear Nighthawk X6 (R8000)
Multi-reason Tri-band
Tri-band
DLNA support
MU-MIMO
Telephone application
$$$
Zyxel Armor Z2
Best mid-range
Double band
MU-MIMO
Qualcomm's StreamBoost
Telephone application
$$
Asus ROG Rapture GT-AX11000
Top All-around
Tri-band
AiMesh
VPN Fusion
Telephone application
$$$
D-Link Exo DIR-882 (AC2600)
Best spending switch
Double band
MU-MIMO
Advance AC SmarthBeam
Fast VPN passthrough
Telephone application
$
Item Details
TP-Link Archer C5400X
TP-Link Archer C5400X
Extraordinary MU-MIMO
Specialized Specifications:
What makes TP-Link Archer C5400X stand apart from the opposition? We believe it's the right blend of cost and productivity, combined with outstanding amongst other MU-MIMO available (we previously addressed the MU-MIMO).
This is a Tri-band switch, which implies it's anything but's an additional 5 GHz channel that you can allot solely for your gaming needs. In addition, you get a horde of LAN (8 ports!), WAN, and USB ports.
What might be said about the WiFi speed? As a matter of fact, it's very acceptable – timing up to 2187 Mbps on the 5 GHz band, which positions it exceptionally among different gadgets in this value range. The 2 GHz channel is likewise very dependable - its speed can get up to 1000 Mbps over a decent reach.
Do you like to play utilizing a VPN administration (or perhaps you need it to get to certain area bolted games or entryways)? Then, at that point, you will profit of the OpenVPN include. A committed innovation can secure up the virtual organization for up to multiple times.
On the drawback, this gaming switch doesn't highlight a high level tech to diminish inertness like its rivals. Be that as it may, TP-Link Archer C5400X ought to be all that could possibly be needed for most multiplayer FPS games.
Best for double band
Specialized Specifications:
Nighthawk XR500 Pro Gaming Router is the main Netgear switch made considering gaming. For what reason is it on our rundown?
To begin with, it can fundamentally decrease dormancy in games by smoothing out the traffic. Likewise, it's entirely dependable. Try not to need your gaming to stop because of a parcel misfortune? Nighthawk XR500 Pro can keep that from truly occurring. Beside how stable it is, this switch has every one of the fundamental highlights like QoS, just as other accommodating augmentations like MU-MIMO and area based association sifting (Geo-channel).
Consider the possibility that you need to precisely check the ping in specific games. Forget about it! Netgear Nighthawk XR500 Pro Gaming Router highlights a standout amongst other web interfaces for a gaming switch we at any point ran over.
If we somehow managed to grumble, it is because of a normal long-range execution of the gadget. In any case, it's outstanding amongst other WiFi switches for gaming in its value range.
Netgear web interface
Multi-reason Tri-band
Specialized Specifications:
Do you believe that the two groups are insufficient for you? Then, at that point, we have uplifting news. Netgear Nighthawk X6 (R8000) switch offers three WiFi groups, one of which can be committed to gaming. In the mean time, it has every one of the highlights you've generally expected from a quality gaming switch (additionally, a phenomenal UI).
This switch shares the majority of the Nighthawk XR500 Pro model's benefits however augments the reasonable download and transfer speed. In other words in the event that you are utilizing a 5 GHz channel.
We should take note of that this gadget has a beautiful dull 2.4 GHz (particularly at long-range). To capitalize on Netgear Nighthawk X6, it's ideal to adhere to the 5 GHz band.
Essentially, this switch is valued somewhat higher than it's archetype. Just barely, as you may already know. However, enough so we can't consider it a modestly evaluated switch. All things considered, Netgear Nighthawk X6 is outstanding amongst other WiFi switches in the event that you are hoping to make a long series of wins in Apex Legends or CoD: Warzone.
Best mid-range
Specialized Specifications:
Searching for the best switch for different gadgets and gaming? Zyxel Armor Z2 is absolutely an extraordinary competitor that is more than fit for 4K streaming, fast perusing, and playing web based games – regardless of whether you do the entirety of that simultaneously!
The primary thing you are likely going to see is the switch's plan. However, what grabs our eye is the exhibition. Obviously, you are getting the standard gaming-focused highlights. Nonetheless, it likewise supports Qualcomm's StreamBoost – a sound and effective option in contrast to QoS.
What might be said about the speed? Zyxel Armor Z2 can get up to 2500 Mbps on 5 GHz in the right climate. The reach, nonetheless, is marginally uninspiring. In the interim, the 2.4 GHz band functions admirably as far as both speed and compelling reach.
The best part about this gaming switch is its capacity to focus on WiFi flags and focus on traffic to explicit applications. Seeing as it's a tri-band switch, you can expect a devoted gaming 5 GHz channel to be available to you. Also – this switch is very simple to set up and arrange because of a clear UI.
How to Set Up QoS to Achieve Better Speed?
We previously referenced how QoS could speed up Internet speed for specific applications. Presently, we should perceive how you can do it on the switches talked about above. Try not to stress - it will not take long (and you don't should be a tech-master to do it).
We trust this article will help you track down the best WiFi switch for gaming. In any case, imagine a scenario where you are as yet vacillating on the off chance that you should purchase
1 note
·
View note
Text
All important info about the Dynamic Host Configuration Protocol
You may have heard of the Dynamic Host Configuration Protocol, better known as DHCP. In computer networks it belongs to one of the basic protocols. It is responsible for the automatic IP address management from a server to one or more clients.

What is DHCP?
To understand the working principle of DHCP, you should first ask yourself some basic questions. How is a computer recognized in a network like the Internet? How do you identify where data is sent to and what belongs to the Internet and what belongs to your home network?
Responsible for this are, among others, the IP address, subnet mask, DNS server and other addresses that are automatically assigned by DHCP. Manual setups are then no longer necessary.
What exactly does DHCP manage?
DHCP assigns the following addresses and address information:
IP address, the address of a device on the network Subnet mask, addressing of the network and host part of an IP address Default gateway, the bridge from one network to another Primary and secondary DNS server, the server that holds a list of IP addresses and their human-rememberable names and resolves them accordingly Time and NTP servers, which are responsible for synchronizing the time of day In addition, there are many other things like WINS servers and proxy configurations that can be managed by DHCP.
What is a DHCP server and what is a DHCP client?
In a network, one device must always be the DHCP server that assigns addresses to all (DHCP) clients. While there are often separate DHCP servers in companies and in large communication networks, in your home network a router is used in practically all cases, which assigns the IP addresses and also serves as a gateway and DNS server. It is therefore the central administrator for all data transport between your home network and the Internet, as well as between the devices in your home network.
What exactly is DHCP needed for?
Without IP addresses nothing works in the home network. If a device makes a request to another device without an IP address, the device does not know where to send the response. The result would be an enormous load that would cause a network to collapse. DNS is used, for example, to convert an address that is memorable to you, such as google.com, into an IP address that can be used by computer networks.
In the past, a hosts file was used for this, which still exists in Windows today. For example, if you didn't have a current IP address for google.de in the file and tried to access it without a DNS server, you would only get an error message.
The first DNS server is your router. It knows up to two DNS servers of your Internet provider to which requests are redirected. These two DNS servers are also assigned to your router via DHCP. Without the automatic assignment you would not know which are the current DNS servers. And even if you knew, the setup is extremely complex. The same goes for the other IP addresses and the subnet mask.
How to enable or disable DHCP?
If your DHCP is not working, it can basically be due to two different reasons. Either the DHCP server or the DHCP client is not working. The exclusion principle is the best way to find out the reason. If only one device in your home network doesn't get IP addresses, the client on the PC is usually to blame, while if all devices don't work, it's usually the server.
You can restart or start the DHCP client in the Windows services. To do this, proceed as follows:
Press the Windows key together with "R".
Type "services.msc" and confirm your input with the "OK" key.
Click with the right mouse button on the "DHCP client" and select "Start" or "Restart".
The process will take a few seconds and a new DHCP request will take place. You can disable DHCP in the same way. However, you would then have to assign the IP addresses on your device yourself in order to access the home network and the Internet.
To enable or disable the DHCP server on a Fritz!Box, proceed as follows:
open your Fritz!Box user interface by typing fritz.box or 192.168.178.1 into the address bar of your internet browser
if a password was assigned, you have to enter it now
click on "Home Network" and then on "Home Network Overview
select the tab "Network Settings
click on "IPv4 addresses
here you can now enable or disable the DHCP server
The setting is only available in the advanced view. You can activate it by clicking on the three dots in the upper right corner of Fritz!OS version 6.50 or higher and moving the slider to the right. For older firmware versions, you will find the settings at the bottom center. Here it is sufficient to simply click on the term "Standard".
On older models, the names in the menu may be slightly different.
Error message "No valid IP configuration" - what to do now?
If you don't have access to the Internet anymore, you might quickly get to this error message. It means that an error occurred during the DHCP address assignment, for example because no IP addresses could be assigned. This is often recognizable with Windows operating systems by the IP address 169.254.x.x, which was assigned by Windows itself because a valid configuration is missing. A few steps are often sufficient to eliminate the error.
Starting with Windows 7, the operating system can make some corrections on its own, such as restarting the network adapter, which can solve the problem. To do this, proceed as follows:
Press the Windows key together with "R".
Type "ncpa.cpl" and confirm with "OK".
Right-click on the network connection and select "Repair" or "Diagnose
Follow the instructions on the screen
If this does not help, it may be necessary to assign IP addresses manually. This is how to do it:
Right-click on the network connection
Select "Properties
Check "Internet Protocol Version 4 (TCP/IPv4)" (the IPv6 protocol is not yet fully usable)
Mark the post and select "Properties
Go to "Use the following IP address
The IP addresses for a Fritz!Box with a standard setup are as follows:
IP address: 192.168.178.x, where x must be outside the DHCP range and between 2 and 255
Subnet mask: 255.255.255.0
Subnet mask, primary DNS server: 192.168.178.1
The Google DNS server (8.8.8.8) can be used as the secondary DNS server. The entry can remain free.
3 notes
·
View notes
Text
Top 7 Fastest VPNs of 2020
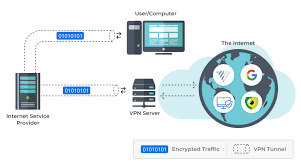
What a VPN is... And what it isn’t
First of all, you still need to preserve your everyday ISP. Using a VPN will no longer update your ISP’s dollars-per-month invoice, but an amazing VPN will act as a cloaking device. All your ISP will see is you having access to anything your VPN makes a decision to show while you connect with your preferred Internet vacation spot.
Second, maximum reputable VPNs will price a subscription price for a motive. You use their offerings, frequently called a tunnel to the Internet. They now personal your information, so you’re paying them to shield your privacy.
Next, your VPN basically turns into your encrypted proxy. Wherever your VPN is, that is additionally where the Internet considers you to be. All roads monitoring your Internet activity will lead returned on your VPN. Do check: ipvanish black friday
Finally, due to the fact a VPN uses encryption, you can file-share and down load securely to coronary heart’s content—even from public WiFi hotspots—as long as your VPN helps peer-to-peer (P2P) record-sharing.
The alternate-off to all of this, of course, is that every one that encryption and additional layers of security can slow Internet get admission to. That’s why it pays to realize precisely which VPNs are maximum probably to maintain you now not best safe and relaxed however additionally up to speed. Here are our top picks, some want-to-recognise specifications and some nods to what makes them special.
Choosing a VPN Political, societal and technological shifts handiest increase the significance of security, anonymity, statistics usage, P2P report-sharing and torrenting competencies, and bandwidth and velocity. Subscription charges vary from the loose—and regularly slow, insecure and volatile—to the high-priced. However, nice VPN providers have a tendency to vary with the aid of just a few greenbacks. When looking for your plan, make certain to recall the following:
Security—as a minimum 256-bit encryption. Compatibility with hardware and software. Server and IP cope with availability and place. Country of registration and information retention laws. Bandwidth or information restrictions, consisting of throttling. Servers unique for P2P report-sharing, torrenting or different designations. Firewalls. Proxies like SOCKS5. Kill switches. Split tunneling and talents for manual configurations. Customer service and help. Considering speed with VPNs When it comes to hurry, understand that a VPN in reality puts a unique license plate in your carload of records inside the flow of visitors. The pleasant VPNs won’t sluggish you down by using a good deal. However, you could occasionally have to weigh protection against speed, and any VPN still relies at the underlying download and upload speeds that your ISP permits.
1. ExpressVPN ExpressVPN is a first rate first pick in a test of VPN speed because we can begin with its VPN Speed Test. This handy menu device types the servers and assigns every a pace index based totally on essential factors:
Latency — the milliseconds’ information travels among your device and a VPN server Download speed — how many kilobits in line with second or Kbps. Based inside the British Virgin Islands, Express substances extra than 1,000 servers in a hundred forty five VPN server places in ninety four nations. Just run your speed check and megastar your favorites.
This VPN is known for its stability of HD streaming abilties, P2P record-sharing, and security features. It supports all gadgets, from mobiles and computers to routers, and any connection— stressed out Wi-Fi or cellular. It allows three simultaneous connections, making it the most limited of our pinnacle selections (however, one of those may be a router). As for its other features, you could anticipate:
Compatibility with Windows, Mac, iOS, Android, Linux, and routers. Protocols OpenVPN TCP/UDP, SSTP, L2TP/IPsec and PPTP. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth, velocity, and server switches. DNS Leak Test device and Express help to remove any leaks. Network Lock, ExpressVPN’s kill transfer for Windows and Mac. Shared IP addresses.
Split tunneling and inverse split tunneling to shield precise connections. Supports VoIP. P2P and torrent-friendly.
Zero logging, with site visitors blending. Terms of provider kingdom that they do music connection dates, server and amount of information strictly for analytics. A full menu of payment alternatives such as credit card, Bitcoin, PayPal and more. Intuitive internet site with lots of informative screenshots and help. Round-the-clock customer service through live chat or e mail.
2. NordVPN Like the alternative six on our list, Nord uses AES-256-bit encryption for all traffic, both incoming and outgoing. However, this VPN adds a second layer to act as a double VPN, encrypting data flowing between your device and your first DNS server and alternatively at a second server before the visitors meets the Internet. Incoming definitely reverses the manner.
Just 5 years antique and based totally in Panama, NordVPN has approximately 1,000 servers in fifty nine nations. It is one of the maximum generous of our selections, allowing an impressive six simultaneous connections. However, each must use a extraordinary protocol. You have 4 options—OpenVPN TCP/UDP, L2TP and PPTP—so essentially, in case you want to apply all six devices straight away, you’ll ought to break up between two or greater servers. Nord does guide routers—which count as one—as well as all other mobile and desktop gadgets. As for the capabilities rundown, NordVPN gives:
Compatibility with Windows, Mac, Android and iOS, with custom software program available. Protocols OpenVPN TCP/UDP, L2TP and PPTP; confined IKEv2/IPsec. IPv6 support expected for 2017. AES-256-bit double-layer encryption ingoing and outgoing. Unlimited bandwidth and velocity. Automatic kill switch for Windows, Mac and iOS. Identified double VPN, Onion over VPN, anti-DDoS, devoted IP, general VPN and P2P servers. Ultra Fast TV and P2P-optimized servers; permits torrenting. Supports VoIP. Supports SOCKS5 and HTTPS proxy servers. Smart Play relaxed proxies to circumvent geoblocking and permit content streaming.
Option for upload-on committed IP server and static IP deal with in U.S., U.K., Germany or Netherlands. Zero logging. Full menu of price options consisting of credit cards, Bitcoin, PayPal and extra on Paymentwall. Well-maintained internet site with useful FAQs page and dietary supplements. 24/7 customer support thru stay chat, email, Nord’s price ticket gadget, Facebook or Twitter.
Three. IPVanish IPVanish is based in Florida’s Orange County. IPVanish is thought for its speed and being torrenting- and P2P-friendly—making it a fave for game enthusiasts. The organization boasts greater than 750 servers in at the least 60 countries, with more than forty,000 IPs general and as a minimum 10 specific—often more—shareable IP addresses per server.
IPVanish permits five simultaneous connections on a couple of gadgets—such as routers—at the four protocols—OpenVPN TCP/UDP, L2TP and PPTP—in addition to IPSec and IKEv2 for iOS. IPVanish consists of SOCKS5 in all its plans, which means that which you have the option of passing traffic—downloading torrents, for instance—thru an nameless high-pace, offshore proxy. In addition, the carrier consists of:
Compatibility with Windows, Mac, iOS, Android, Linux Ubuntu and Chromebook. Protocols OpenVPN TCP/UDP, L2TP and PPTP; IPSec and IKEv2 for iOS and IPv4. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth and server switching. SOCKS5 proxy. IP address biking. Support of VoIP. Unlimited P2P supporting BitTorrent. NAT firewall. Kill transfer for Mac OS X and Windows. No traffic logs.
Extensive charge options including credit score card, Bitcoin, PayPal and plenty of others. Extensive website. Technical records, but, can be hard to discover. Support to be had thru electronic mail. When we checked, there was a wait of about 36 hours.
Four. PureVPN
Celebrating “10 years of safety,” PureVPN claims greater than 1,000,000 users and guarantees them “entire freedom” and “global-class” safety on both a personal and enterprise scale. The company is primarily based in Hong Kong, which has no mandatory facts retention laws—why many individuals pick a VPN inside the first area.
Meanwhile, PureVPN is a connectivity maven. Its community covers 141 nations with 180 places and more than 750 servers. It allows five simultaneous connections for greater than 20 exclusive devices. Its virtual router feature allows you to show any Windows pc or computer into a digital router for up to ten gadgets. On pinnacle of that, PureVPN writes its personal code for all of the primary structures and uses no third events for real statistics transfer. PureVPN covers all of the fundamental desirables like:
Compatibility with Windows, Mac, iOS, Android and Linux. Selection of protocols—OpenVPN TCP/UDP, PPTP, L2TP, IKEv2/IPsec and Stealth. IPv6 leak safety for Windows and Mac. AES-256-bit encryption ingoing and outgoing. Unlimited bandwidth, facts transfer and server switching. Split tunneling for Windows and Android. File-sharing restricted to specified servers. Kill switch for Windows and Mac.
Optional add-on dedicated IP and static IP address. Zero logs. Extensive fee alternatives—credit score playing cards, PayPal, Alipay, assorted Bitcoin organizations, Paymentwall and Cashu. Very consumer-friendly, intuitive website with seek option. 24/7 stay chat pop-up for assist.
Five. VPNArea Based in Bulgaria, VPNArea opened store in 2012, with its headquarters servers and electronic mail hosted in Switzerland. The organization is committed to keeping a speedy consumer-to-server ratio, citing a server for every 250 clients. It’s now up to more than two hundred servers in 68 international locations and greater than 10,000 IP addresses.
Another generous VPN issuer, VPNArea permits you six simultaneous connections to your favourite devices, together with routers, through OpenVPN TCP/UDP, PPTP or L2TP. It also gives its very own Chameleon app for Windows. Like a number of different vendors—however no longer all—VPNArea’s service consists of a kill switch machine; in case your VPN service drops for a few cause, your IP deal with will stay covered. VPNArea’s carrier also affords:
Compatibility with Windows, Mac, Android, iOS and Linux. Protocols OpenVPN TCP/UDP, PPTP or L2TP. IPv6 and WebRTC leak protection. Chameleon OpenVPN software program for Windows. AES-256-bit encryption ingoing and outgoing.
Unlimited bandwidth and server switching. Shared IPs, with adjustable car random IP changer. Speed check with ping and download in addition to users on-line server load screen. Kill switch device.
P2P permitted on distinct servers. Account sharing. Custom business accounts available. Optional add-on personal VPN server with dedicated IP cope with $15 a year. No logs. Payment options restricted to Visa, MasterCard, PayPal, Payza and Bitcoin. 24/7 help to be had through stay chat, electronic mail and Skype.
6. Buffered Buffered VPN is the youngster in our seven. Registered in Budapest, Hungary, in 2013, it has servers in 37 international locations and guarantees that in case you don’t see the only which you need, they just might be capable of get one for you. This VPN is enthusiastic about preserving freedom of speech and access to data irrespective of in which you're. Buffered no longer most effective says that it’s torrent-pleasant however is also cited for being so.
Buffered allows customers five simultaneous connections and houses in on the want for comfortable velocity with out the constraints of throttling. It gives some of the offerings you would anticipate with a few obstacles:
Compatibility with Windows, Mac, Linux, iOS, Android in addition to DD-WRT and Tomato routers. Exclusively OpenVPN TCP/UDP protocols. Supports IPv4. 256-bit Blowfish encryption. Friendly to P2P record-sharing, torrenting, gaming and streaming. Unlimited bandwidth, speed and server switching Optional add-on dedicated server with static IP cope with. Supports VoIP and Skype. NAT Firewall.
Dynamic IP addresses. Will set up servers upon request. Does no longer allow split tunneling. No kill switch. No logs policy. Salesy website. All the technical records—everything you really want to realize—is within the internet site’s FAQs phase and tutorials. Payment menu includes the primary credit playing cards, Maestro, JCB and PayPal. 24/7 guide via stay chat with Knowledge Center.
7. VyprVPN VyprVPN is sincerely a Golden Frog introduction included in Switzerland, which—because the Golden Frog site explains—has set up safe harbors with the EU, the U.S. And other countries. These folks take their security critically. Their very own inhouse engineers write their code. They very own and manage all their own hardware and software and keep their operation inhouse, and not using a 1/3 parties. They’ve were given more than 700 servers and 2 hundred,000 IP addresses spanning the globe, supplying cease-to-stop privateness.
If you need a seasoned bono download of a GB to strive out the VPN, you may sign on for VyperVPN Free. Just choose your app at the website—it really works for desktops in addition to iOS and Android. You could have two simultaneous connections and get right of entry to to the Cypher encrypted messaging app. It’s a one-time deal, but you could without problems improve to a subscription.
A lot of misunderstanding exists over the feature of split tunneling, and Vypr isn't any exception. At its only, the exercise lets in customers to consist of or exclude certain devices or applications, putting a few below VPN protection while permitting others to interface or stream at once out of your ISP. Not all VPNs even provide it. The configuration that VyprVPN uses allows split tunneling with the aid of app. In addition, a subscription comes with:
Compatibility with Windows, Mac, iOS, Android, Linux, TVs, OpenELEC clever gadgets, routers and extra. Protocols OpenVPN TCP/UDP, L2TP/IPsec, PPTP and Chameleon. 256-bit encryption. Unlimited bandwidth, pace and server switching. Golden Frog-optimized code for cutting-edge broadband connections. NAT Firewall. SOCKS5 proxy supported.
Dynamic server switching. Kill switch in Windows and Mac. Split tunneling for apps however now not servers or gadgets. Desktop and mobile apps, consisting of Blackphone and Anonabox. Chameleon proprietary metadata scrambler for Windows, Mac, Android and routers.
Conclusion: Zero-know-how VyperDNS provider preserves privateness and geolocational get right of entry to, defeats censorship and geoblocking. User-pleasant, exceptionally informative website with the entirety inside the right place—just in which you’d placed it. No logs. End-to-end code, possession and management.
1 note
·
View note
Text
the “sincerely, me” scene is completely about jared and evan’s relationship and @ me about it
they’re actually alone and in the same place for once and we see evan acting more at ease and unfiltered than at any other point, unflinchingly showing the kind of behavior he later denies when trying to act like his own notion of his Ideal Self (“i don’t even think things that aren’t nice”), speaking up without hesitation / arguing with jared rather than trying to avoid all conflict as he otherwise does so often, slowly gradually getting into the flow of things as jared writes
similarly, jared actually enjoys engaging with evan while evan’s being this way, and he’s actually having fun and becoming genuinely engaging in the email writing as they go on
they’re getting the inspiration from the material from Somewhere, and since evan didn’t actually ever have this kind of close friendship or really know connor at all, his ideas for what the content should be are based on his ideal concept of himself and his ideal concept of what a friendship should be like, which, the relevance of that to him and jared is Right There
nobody ever acknowledges it but jared has also gotta be projecting his own desires onto this story they’re creating. evan’s probably dictating his half of the emails but imo the strong implication is that connor’s emails are all jared’s creations. he’s aware of how little either of them really know about connor and is never trying to fill in these blanks / make assumptions about who connor was, and yet it’s a bit unlikely he’s just constructing this “evan’s best friend who was totally close to him and it was all great” material on the go from like, thin air. he’s playing off of evan’s material and responding to it with dialogue to suggest caring about evan and enjoying their relationship and their interactions. if you stop and consider that jared has real thoughts and feelings beyond the front he puts up and filter he uses, it’s Right There that jared is using those real thoughts and feelings as inspiration to create an adequately convincing Exchange Between Evan And His Close Friend.
while evan and jared and RPing this close friendship with each other via Fake Evan and Fake Connor, they both get more in sync with each other. i mean for example you have the writing come to a halt while they argue back and forth about whether it can be gay, whereas towards the end evan throws in another No Homo and connor, aka jared, just seamlessly rolls with it at that point
speaking of, jared is out here saying he thinks the idea of The Love That One Man Feels For Another is beautiful. yeah he says “some would say there’s something quite beautiful” but since when is jared ever Not assigning his own feelings to a theoretical third person. everything he says is totally “i’m a closeted high schooler” and he’s really out there pushing to write an RP with evan as his secret lover. everything that seems gay about Sincerely, Me is thanks to jared, because he is in love with evan.
the fact that jared gets so enthused as the fake exchange they’re writing—which is supposed to be an exchange between Evan’s Best Self and Evan’s Best Friend but is actually an indirect exchange between evan and jared—really gets into a flow, that by the end he’s enjoying writing the emails when just before he was all Are We Done Yet
this is such a high point for them that jared spends the rest of the play wanting to recreate more of this sort of interaction with evan, if you don’t believe me believe will roland, and also the content that’s right there in canon as jared keeps chasing evan’s attention however he can for the rest of the play, e.g. getting on board with tcp, engaging with him in ywbf like he does, offering to be more involved when evan says they don’t need him, inviting him to hang out, throwing out the Truth of how evan’s benefitting from the situation b/c he knows it’ll make evan pay attention to him and it does, tfw you’re just casually willing to do anything for the chance of getting to have a good time interacting with your boy again, nbd
i’ll say it again and say it anytime, re: his own contributions to the emails evan is just further constructing this fantasy of Not having to feel alone, and jared is getting to play the part of “a friend who is close to evan,” and everything that seems gay is due to jared being in love with evan; this song is kleinsen because canon is kleinsen, thanks
“sincerely, me” as a title is obvs a Good One cuz it’s all full of lies but also b/c both jared and evan are so rarely truly Sincere. including here, since in terms of “these are real emails and things were really like this” they’re being dishonest, but as an exchange between evan and jared in which they use their own thoughts / ideas to write the material, they’re getting to channel their own desires in a way that’s more honest than usual, since the idea that they’re Only Pretending actually gives them both the opportunity to feel safer actually being more open with their feelings about how Being Close With (A Friend)/(Evan) should ideally go
if “sincerely, me” isn’t about jared and evan’s relationship then explain why the reprise juxtaposes with the earlier scene to show how their relationship is now very obviously fragmenting further. that’s all the scene is about. jared is wanting evan’s attention, now outright putting himself in the emails just to be that much more Obvious, then trying to make evan jealous about nonexistent other friends, then offering to help with tcp in other ways, then reminding evan that his dating zoe is weird b/c it’s thanks to evan pretending to be connor’s friend, then reminding evan that maybe he’s doing other messed-up self-benefitting things re: connor’s death, and that maybe he shouldn’t be brushing jared off over and over. and even after all that jared’s risking it all and outright inviting evan over just to share an empty house and drink. and then being driven away by seeing zoe kiss evan. it’s all very heterosexual.
sincerely, me is about jared and evan’s relationship okay
it gives jared stronger motivation to want to have more time and attention from evan
is evan ever more Genuinely Himself than when he’s alone with jared?? showing these parts of himself which he later hides to pretend to be a “better” version of himself, talking about how nobody would like him if they knew What He Was Really Like, meanwhile jared sees this more honest and genuine and less “”nice”” version of evan and likes it so much that everything he subsequently does is about trying to continue that experience and be closer to evan? Hmm? what’s that??
jared continuing to do the emails for evan and the only thing that makes him refuse is feeling personally rejected by evan? the last thing that happens before their fight in gfy, the breaking point for jared if you will, is seeing zoe kiss evan? Hmm????? and then when evan next interacts with jared, jared is upset enough to actually stand his ground and directly push back, almost directly state his feelings???? what’s that?
jared is in love with evan actually and sincerely, me is as much about this as it is about informing us “so yeah they wrote the emails btw”
@ will roland: divulge the lore!! we need your help
kleinsen is THAT real
516 notes
·
View notes
Text
Wireless Router & Security - A Stage-By-Stage Manual
The addresses are 10.../8, 172.16../12, and 192.168../16. If the link is operating, go via every router and apply the wi-fi security options (i.e. The default username is admin and d-link password is blank. This article covers the best procedure to update your ILOM's firmware. I found SUN's documentation really scattered about this important topic. I read through their PDF's and decided to use the ILOM to do this as opposed to command line where it was a bit more documented.
Be sure both the modem and router are plugged into the electrical outlet. See if any lights light up on the front of them. If both the modem and router have lights on the front follow the instructions bellow. If not, you know which one doesn't work.
On the bottom right of the laptop there is the internet connection icon next to the speakers icon. When I moved the mouse over the icon it showed an old internet connection name. It was therefore necessary to log in to the router to change the settings. This was achieved by typing 192.168.1.1 in the browser window.
A broadband router that uses this IP address can function normally as it combines several elements together. Installing many switches and DHCP (Dynamic Host Configuration Protocol) server is not necessary if the router is able to process all data in a single unit. Although it is called a default address, it can be modified for mending connection problems. It is suitable for a single device and adding more devices may cause malfunctioning of a network.
The 192.168.0.1 address doesn't just facilitate data travel. It also helps in streamlining network installation and set up procedures. It eliminates the need to put in DHCP switches. Using this IP address, setup is quicker.
With an IP address everything on the internet is organized. A DNS server can deliver the right information for as long as the IP address is included in the request made to them. Where there is no IP address, then there is no address to return the information requested. DNS server are categorized into two which are the public and the Private. However, using these public servers might result in problems such as cache poisoning, pharming and DNS amplification attacks.
You'll then configure your network. Log onto your router/modem through your PC. Read the owner's manual for the router for specific directions. You'll want to direct it to automatically assign IP addresses to any PC attached to it. It's recommended that you stick to basic network configurations and use the 192.168.01 as the first IP address and the 0.9 as the ending address, which gives you the potential for eight additional devices to be installed, if you like.
Once you have connected the modem, it is time to install and configure the settings of your router. Connect your main computer to the router. Install the disc included in the package. Follow the procedures mentioned there.
On your second PC (the client) open Control Panel -> double click Network Connections -> right click your network connection (the one connecting the two PCs) and select Properties -> select Internet Protocol (TCP/IP) and click the "Properties" button. Click Use the following IP address and enter IP address: 192.168.0.2 Subnet mask: 255.255.255.0, default getaway 192.168.0.1 select Use the following DNS server addresses and enter 192.168.0.1 for the first one and leave the second one blank.
1 note
·
View note
Text
Where Can You Get The Best TCP Assignment Help?

Transmission Control Protocol (TCP) is a connection-oriented protocol it establishes a virtual connection between two devices via a series of request and replies messages sent across the physical network. It is also generally used with Internet protocol and together can establish and maintain a network conversation via which application programs can exchange data defining how computers send packets of data to each other.
The two are commonly used together as TCP/IP but are in fact two distinct computer network protocols. Hence, you cannot learn one without understanding the other. Together they set the basic rules defining the internet. You know, that place online that we all love to go for every little bit of information we can get about everything around us. There are four layers of TCP/IP functionality with different protocols. The Data link layer, the networking layer (internet), transport layer and the application layer. TCP is considered a protocol in the transport layer responsible for communication between hosts and reliability, multiplexing and flow control.
It is really such a vast amount of information to take in and once you learn and understand the enormous internet applications it has then you will see why it is a very powerful knowledge to have. Students taking computer network courses have to contend with complicated and complex TCP assignment.
That is why we at computernetworkassignmenthelp.com are known to provide the best TCP assignment help. Below are some of the reasons why students come to us:
1. Experienced Experts and Tutors
We have the best tutors and experts with vast years of experience and nightly qualified in computer network and computer network-related topics like TCP. They are handpicked by us from esteemed institutions all over the world. If there is anyone who can help you score those top grades by providing you with exemplary TCP assignment help, it is these guys.
2. 100% Plagiarism Free Content
The content we provide is all done from scratch. Our expert TCP assignment writers ensure that the work is always original and unique. The final draft is revised by a fresh pair of eyes so as to minimize the effects of mind saturation. Thus your TCP assignment will always be plagiarism free.
3. On-Time Delivery
We offer delivery of all TCP assignments on time. Our ability to guarantee this service has kept us in good terms with our clients and helped boost their confidence in us. Never missing a deadline helps to relieve the student of any stress they may bare when submission dates are fast approaching
4. Top Quality Solutions
We strive to offer nothing but the best top quality solution. Our experts are very proficient in TCP protocols and will ensure the quality of work that is nothing short of amazing. Guaranteed to impress your professor and definitely earn you top grades.
5. Economical Prices and Amazing Discounts
Our prices are the best. We offer fair and economical prices for the best professional services that are unrivaled anywhere in this field. Our prices are very considerate of the student’s budget, hence a student can never miss out on the opportunity of getting their TCP assignment done by us.
Contact us today at computer network assignment help for the best TCP assignment help.
0 notes
Text
IP 101: The Fundamentals of IP Addresses

The "speech" part identifies a exceptional number which gets connected to all online action that you do. . .somewhat just like a return address on a letter you would send out. (All this occurs in milliseconds.)
TCP IP
That is the conclusion of the lesson. It ought to be.
And confusing. Information technology (IT) is mad stuff and it is best left to people who need to manage networks and computers.
TCP IP
However, we are all about the Internet nowadays, and it appears we are
And with so much vague information (and misinformation) out about the IP address, it is helpful to be aware of the fundamentals.
You have got connections.
Your personal computer is hooked up to the world wide web, 1 way or another. When you get on the internet for email, to chat or shop, your petition needs to be routed out to the ideal destination, and also the answers and data you need need to return directly to you.
An IP address plays a main part in that.
You along with your computer really connect to the Web indirectly: You initially connect to a community which is 1) linked to the Web itself and 2) permits or provides you access to the net.
Or a business network on the job or even a wireless network in a hotel or coffee shop when you are on the street. However, with countless computers on the web, how do your computer leap in and get you your job or private emails and much more without any issues?
To Be Sure You can do everything on the World Wide Web, your computer's Media applications is hardwired to obey a listing of built-in media standards and guidelines (yes, protocols) to link to Internet, and also to swap data and information back and forth.
One of these networking protocols on your own computer, the Net Protocol, is in charge of fixing, routing and delivering your online orders exactly. It evolves an"electronic return address" to all of your online requests and action for you. The speech it utilizes is the IP address for the link.
Provided that, IP address. It was fine while it lasted. As they're the ones providing you access to the world wide web, it is their function to assign an IP address to your PC.
But do not get connected to it. Arm, since it is not yours. At home it may change if you do something as straightforward as turn your router or modem off and on.
You can not take it with you.
Additionally, If you go on holiday and take along your notebook, your house IP Address does not go with you. It can not, because on holiday you are going to use a different system to connect with the web.
Thus, Once You're in a coffee shop in a different state or city (or simply Down the street ) and you are using their WiFi to receive your email, you are utilizing another (and temporary) IP address, you assigned to a notebook on the fly from the ISP for this java shop's Internet supplier.
Same thing occurs when you travel. As you travel from the airport to your resort to the neighborhood coffee house, your own IP address will change every moment.
However, You don't need to Consider it whatsoever, or open the hood of your own Computer and reverse switches. Everything occurs thanks to the smart Design supporting the world wide web, wireless networks and those world wide web Protocols your computer applications.
1 note
·
View note
Text
Morto Worm Attacks RDP / waredot
Morto - A new and virulent worm, dubbed Morto, raised reached online users. It’s spreading quickly, through the Microsoft Windows RDP (Remote Desktop Protocol (RDP). Though the days of worms such as Blaster and Code Red were long gone?
This worm is developing a large amount of outbound RDP traffic – is capable of compromising both servers and workstations-infecting machines that are completely patched.
Morto is an old-fashioned internet worm, which targets Windows workstations and servers by exploiting poorly-chosen weak passwords to spread via Remote Desktop Protocol (RDP) connections (port 3389). It’s possible if you had a large number of infected computers within your local network, that the amount of traffic generated by the Morto worm might be so significant that it would effectively clog your system.
In this time, the Morto worm has also received a lot of press attention we need to keep the threat in proportion. However, Sophos Labs has received a very low number of exports of this worm being seen in the wild. Possible reasons for the low number of Morot reports may be that Sophos customers have chosen better passwords on their shares, or because Sophos products had detection relatively early on for this compared to some competitors.
What is RDP?
RDP refers to Microsoft Desktop Protocol (RDP) provides remote display and input capabilities over network connections for Windows-based applications running on a server. Additionally, RDP allows users to control their remote Windows machines as if they were working on it locally (well, almost).
Morto Worm Spread via Remote Desktop Protocol
As we have read above, Morto is a computer worm and it spreads via Windows Remote Desktop Protocol (RDP) and infects Microsoft Windows workstations and servers. It was first appeared in August 2011, when network administrators started noticing heavy spikes in traffic on Port 3389/TCP.
Once Morto infects one computer on a network, the worm scans for other devices that have Remote Desktop Protocol enabled and copies itself to these computer’s local drives as a DLL file, which then created additional files on the computers. This worm can also be controlled remotely. There are currently two currently variants known by security experts.
How to Mitigate Morto Worm
Morto Worm is danger threat but still, it can be mitigated by following some basic security best practices.
First of all, make sure that you’re enforcing strong password choices on your user accounts. Not that the unique “Administrator” accounts password AWS automatically assigns to your instance upon launch complies with this recommendation and should be sufficiently strong to make brute force password guessing infeasible. In case, you’re using the EC2 Windows Configuration Service to override this automatically assigned password, please ensure that your selection is cryptographically strong.
In addition, you can also run an antivirus scan that prevents Morto and other types of malware as well. We recommend you to choose Waredot Ultimate that comes with the package of other advanced security protection. You can take the 30-day free trial and if you find it useful, you can purchase it.
Summary
Hey guys! This was the guide about “Morto worm attacks RDP.” This guide is a short description of Morto Worm and its troubleshooting. Hope you find this article helpful and informative. If you’ve any queries regarding this article, please let us know in the comment section. We would be glad to answer you!
0 notes
Text
2022 Update CCNP Security 300-710 SNCF Dumps
The latest CCNP Security 300-710 SNCF Dumps are new updated for your Securing Networks with Cisco Firepower exam. PassQuestion provides you the latest 300-710 questions and answers to help you attempt a real exam so you can achieve the best results. With our CCNP Security 300-710 SNCF Dumps, you can be rest assured that you will Pass your Cisco 300-710 Exam on Your First Try. It will also save your valuable time. We recommend you to go through the CCNP Security 300-710 SNCF Dumps several times so you can pass the Cisco 300-710 exam on the first attempt. It is the right way to attempt a real exam so you can achieve the best results.
300-710 SNCF Exam Description - Securing Networks with Cisco Firepower
The Securing Networks with Cisco Firepower v1.0 (SNCF 300-710) exam is a 90-minute exam associated with the CCNP Security, and Cisco Certified Specialist - Network Security Firepower certifications. This exam tests a candidate's knowledge of Cisco Firepower® Threat Defense and Firepower®, including policy configurations, integrations, deployments, management and troubleshooting.
Cisco 300-710 Exam Overview:
Exam Name: Securing Networks with Cisco Firepower Exam Number: 300-710 SNCF Exam Price: $300 USD Duration: 90 minutes Number of Questions: 55-65 Passing Score: Variable (750-850/1000 Approx.)
300-710 SNCF Exam Topics Included :Deployment (30%)
1.1 Implement NGFW modes 1.1.a Routed mode 1.1.b Transparent mode 1.2 Implement NGIPS modes 1.2.a Passive 1.2.b Inline 1.3 Implement high availability options 1.3.a Link redundancy 1.3.b Active/standby failover 1.3.c Multi-instance 1.4 Describe IRB configurations
Configuration (30%)
2.1 Configure system settings in Cisco Firepower Management Center 2.2 Configure these policies in Cisco Firepower Management Center 2.2.a Access control 2.2.b Intrusion 2.2.c Malware and file 2.2.d DNS 2.2.e Identity 2.2.f SSL 2.2.g Prefilter 2.3 Configure these features using Cisco Firepower Management Center 2.3.a Network discovery 2.3.b Application detectors (Open AppID) 2.3.c Correlation 2.3.d Actions 2.4 Configure objects using Firepower Management Center 2.4.a Object Management 2.4.b Intrusion Rules 2.5 Configure devices using Firepower Management Center 2.5.a Device Management 2.5.b NAT 2.5.c VPN 2.5.d QoS 2.5.e Platform Settings 2.5.f Certificates
Management and Troubleshooting (25%)
3.1 Troubleshoot with FMC CLI and GUI 3.2 Configure dashboards and reporting in FMC 3.3 Troubleshoot using packet capture procedures 3.4 Analyze risk and standard reports
Integration (15%)
4.1 Configure Cisco AMP for Networks in Firepower Management Center 4.2 Configure Cisco AMP for Endpoints in Firepower Management Center 4.3 Implement Threat Intelligence Director for third-party security intelligence feeds 4.4 Describe using Cisco Threat Response for security investigations 4.5 Describe Cisco FMC PxGrid Integration with Cisco Identify Services Engine (ISE) 4.6 Describe Rapid Threat Containment (RTC) functionality within Firepower Management Center
View Online Securing Networks with Cisco Firepower 300-710 Questions and Answers
1.Which interface type allows packets to be dropped? A. passive B. inline C. ERSPAN D. TAP Answer: B
2.An engineer is building a new access control policy using Cisco FMC. The policy must inspect a unique IPS policy as well as log rule matching. Which action must be taken to meet these requirements? A. Configure an IPS policy and enable per-rule logging. B. Disable the default IPS policy and enable global logging. C. Configure an IPS policy and enable global logging. D. Disable the default IPS policy and enable per-rule logging. Answer: C
3.On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface? A. transparent inline mode B. TAP mode C. strict TCP enforcement D. propagate link state Answer: D
4.A Cisco FTD has two physical interfaces assigned to a BVI. Each interface is connected to a different VLAN on the same switch. Which firewall mode is the Cisco FTD set up to support? A. active/active failover B. transparent C. routed D. high availability clustering Answer: C
5.An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices? A. Add a native instance to distribute traffic to each Cisco FTD context. B. Add the Cisco FTD device to the Cisco ASA port channels. C. Configure a container instance in the Cisco FTD for each context in the Cisco ASA. D. Configure the Cisco FTD to use port channels spanning multiple networks. Answer: C
6.An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements? A. Inline tap B. passive C. transparent D. routed Answer: A
7.Which two dynamic routing protocols are supported in Firepower Threat Defense without using FlexConfig? (Choose two.) A. EIGRP B. OSPF C. static routing D. IS-IS E. BGP Answer: B,E
8.An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment? A. in active/active mode B. in a cluster span EtherChannel C. in active/passive mode D. in cluster interface mode Answer: C
0 notes
Text
Pick A Suitable One Among Reactjs And Node.Js App Development
Node.js and ReactJS are the two most prominent JavaScript technologies. ReactJS and Node.js app development have given new heights to the technical environment. They keep the customers engaged on their devices with edge-cutting technology.
Being a Node.js and ReactJS Development Company, Mitiz Technology is creating high-performing business applications. Both, somehow, belong to the same technology but altogether different things. React is used for UI development and Node.js is a back-end framework.
Mitiz Technologies is a Node.js web Development Company that provides fast and scalable development of server-side and network applications. Nowadays, several businesses are using Node.js for their audience, and Netflix, Uber, and many big names are on this list.
Node.js app development is gaining popularity with incredible features –
• Open source: Node.js is an open-source framework and it is free-of-cost.
• Server development: Node.js has in-built APIs and it allows making various servers like an HTTP server, DNS server, and TCP server, etc.
• Performance: Since the developers can perform non-blocking operations with Node.js, the overall performance of web applications is elevated effectively.
• Scalability: The web applications made with Node.js are scalable in both horizontal and vertical ways that further help to elevate the overall performance of the apps.
• Unit testing: Jasmine is a unit testing of Node.js that allows the testing ready code quickly.
Know ReactJS
Mitiz Technologies offers ReactJS development services to various businesses. React is an open-source JavaScript library that allows a simpler programming model for better performance of web applications. ReactJS is used as a base in single-page for interactive web projects. The multiple components are involved in one react application, where each is responsible for specific action.
ReactJS development services include different features –
• Code stability: ReactJS offers great code stability for incredible app performance. It uses only downward data flow.
• Performance: ReactJS uses a virtual document object model (abbreviated DOM) to improve the overall app performance.
• Easy to maintain: ReactJS has a library where the system components are re-used and the issues are resolved effectively.
• Toolset: ReactJS includes and provides the developer toolset to ensure the high performance of the application with all the design and debugging tools.
• JSX: React library has JavaScript XML, which is also known as JSX. It is basically an HTML-like syntax to be processed into JavaScript calls.
Both are Incredible
If you are looking to assign your requirements to a ReactJS and Node.js web Development Company, Mitiz Technology is the only name. We serve in both the development streams, where each has its pros and cons; you need to evaluate and act accordingly –
• Both are open-source frameworks. But Node.js is used to write code for dynamic web page contents whereas ReactJS is a client-side library to deliver high-performing dynamic apps.
• Node.js is used for web development whereas ReactJS is used for both Android and iOS apps.
Being a responsible Node.js and ReactJS Development Company, Mitiz Technology believes in delivering the best solution. We will elicit the most useful framework for your requirements!
To know more visit at 5 Mistakes to be Avoided with ReactJS Development
0 notes