#BitLocker removable media problems
Explore tagged Tumblr posts
Text
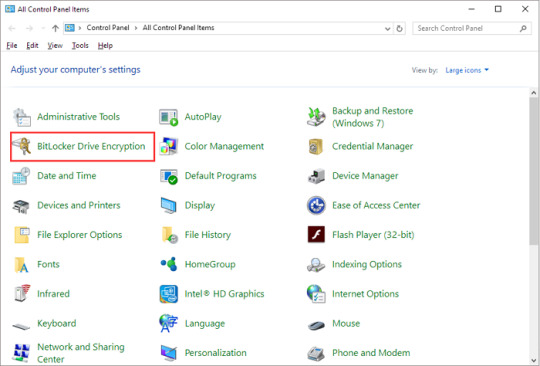
Why is BitLocker unable to encrypt Removable Drives via MBAM?
Fixed Data Drives refer to non-removable storage drives installed in a PC such as internal hard drives (HDDs) or solid-state drives (SSDs). Unlike removable drives (like USB flash drives). Fixed drives are used to store data, applications, and the operating system. In this article, we shall discuss how to resolve ‘Why is BitLocker unable to encrypt Removable Drives via MBAM?”. Please see Why does…
#BitLocker drive encryption troubleshooting#BitLocker encryption issues#BitLocker management with MBAM#BitLocker not encrypting USB drives#BitLocker removable drives#BitLocker removable media problems#BitLocker settings MBAM#encryption errors removable drives#MBAM and BitLocker#MBAM configuration issues#removable drive encryption problems#resolve BitLocker encryption failure#troubleshoot BitLocker MBAM#why BitLocker fails to encrypt#Windows#Windows 10#Windows 11
0 notes
Text
A series of unfortunate events:
- Power supply on my PC blew due to bring underpowered. I have a replacement but I can't do it myself because the company that built my PC hard-wired a fan to the power supply. It's under warranty but I'll get it back with the same problem of lacking power.
- Attempt to reset laptop to clear old stuff off and update to win11. Updates to win11, then gets locked down by bitlocker. Can't bypass.
- Pull out old laptop from a box somewhere. It somehow works. I leave it overnight to do regular updates. I wake up the next morning and it won't boot and makes very loud beeping noises at me. (Read: so fucked it's resorted to Morse code to tell me)
- Spend several days trying to get my hands on windows installation media. No one I know seems entirely willing to actually help in this. I walk to the local library to try to download it and discover that I cannot do so. Wind up having my landlord do it.
- Discover via installation media that my laptop is just not thoroughly recognizing my ssd. Decide to try to swap it out. Screw strips on the ssd cover plate. Spend 2 hours trying to get it off. Wind up ripping the plate off, discovering in the process that it was soldered on. Discover that my laptop, against what I had been told while researching this, is not compatible with the m.2 ssd I had anyway.
Side note: I also gouged the hell out of my thumb on my laptop chassis. The blood was not enough to sate whatever higher power I have pissed off.
- Discover that I damaged my laptop while removing the ssd plate and it's junked now anyway.
Stay tuned for more, as this is almost certain to continue
2 notes
·
View notes
Text
Disable bitlocker

manage-bde –unlock drive-letter: -rp 48-digit-numerical-recovery-keyĮ.g.
Once you find the drive letter of the encrypted drive, give the following command to unlock the encrypted drive by using the recovery key. In command prompt, give the following command to view the BitLocker status of all drives:ĥ. Then go to Troubleshoot -> Advanced options -> Command promptĤ.
In the screen you asked for the recovery key, click Skip this drive.ģ. At the first screen click Next and then Repair you computer.Ģ. Boot your system from a Windows 10 Installation Media (USB or DVD).Ģ. After unlocking the drive, follow the instructions at case-1 to turn off the bitlocker encryption. Attach the encrypted drive on another Windows 10 PC and then double click on the drive and type the recovery key to unlock it. If the Bitlocker recovery key, is not accepted at system startup, then you have the following options: Type the bitlocker recovery key (48-digit number) at system startup. Unlock the drive by Entering the Recovery key. If you find the recovery key, proceed to step-2 below, otherwise proceed to step-3. if you use an MSA account to logon to Windows 10, or to download Apps from the Microsoft Store, or to get your emails, or to activate Microsoft Office), then from another device with Internet access, sign in with that Microsoft Account at Microsoft's Bitlocker Recover Key webpage to get the Recovery key for your device. Note for DELL devices: If you own a Dell PC or laptop and you have added a Microsoft account (MSA) on you device, for any reason (e.g.
On your Azure Account if you sign in with an Azure Active Directory account.
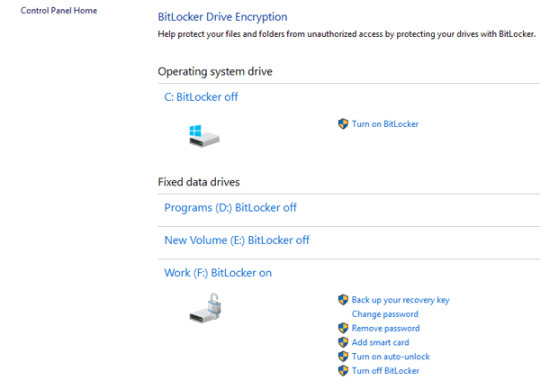
(Plug the USB drive on the locked PC and follow the instructions) (Type the 24-digit number recovery key from the printout) So, If you have enabled the Bitlocker Drive encryption on your system, then look at the following locations to find the bitlocker recovery key: First of all, you should know that there is no way to bypass the Bitlocker encryption, if you don't have the Bitlocker password or the bitlocker recovery key. How to Disable Bitlocker if you Cannot login to Windows. Click Turn off Bitlocker on the encrypted drive.Ĭase 2. At 'Manage Bitlocker' section, click Bitlocker Drive Encryption.ģ. Navigate to Windows Control Panel and open System and Security.Ģ. The normal way to disable the bitlocker encryption in Windows 10 is the following:ġ. How to Disable Bitlocker Encryption If you can login to Windows 10. How to Remove Bitlocker Encryption in Windows 10.Ĭase 1.
Related article: How to Encrypt Drive C: with BitLocker in Windows 10 Pro & Enterprise.
In this tutorial, you 'll find all the available methods to remove the Bitlocker Drive Encryption in Windows 10. In other cases, some users complained that the Bitlocker encryption was enabled automatically, after updating the BIOS on their Dell laptop. Recently, one of my customers, brought his Windows 10 Dell laptop to our service, with the following problem: When the laptop starts, it prompts to enter the BitLocker recovery key, but, as my customer says, it has never enabled the BitLocker encryption on the system.Īfter some research on the Internet, I found that on some Dell devices the bitlocker is starting automatically to encrypt the drive if a Microsoft Account (MSA) is used on the system.

0 notes
Text
Auto installer deluxe download to hdd

#Auto installer deluxe download to hdd driver
#Auto installer deluxe download to hdd full
#Auto installer deluxe download to hdd software
#Auto installer deluxe download to hdd windows 7
On network computers, when data is written to a file, it is written to the cache and not immediately flushed to the redirector. * Disable Network Redirector File Caching for Workstation Service: Remove DLLs from memory after use to free up more resources. This Option lets Windows create more critical threads for when your system load is high in order to improve your systems performance. * Allocate more Critical Threads to Increase Performance: The Boot Optimization function will automatically defragment boot files and rearrange them so that all boot files are in close proximity to one another. Speeds up the access of AVI folders as well as makes the renaming and deletion of AVIs easier. This will tell windows not to cache erroneous DNS data at all. Disabling this option reduces the overhead during the creation of new files or directories.īy default Windows also caches erroneous data and this can take space of valid cache items and thus slow down your Internet access. NTFS Files systems create file names in 8.3 format. * NTFS Disable 8.3 Names and Last Access: However, you may notice that it does have some latency to display the preview after mouse over the icon, Thumb Time-Delay has been improved to avoid this problem. Windows 7 has provided a cool feature with ability to preview taskbar thumbnails whenever the mouse is hovered on the program icon. This program collects information about computer hardware and how people use Windows 7.
#Auto installer deluxe download to hdd windows 7
The Windows Customer Experience Improvement Program in Windows 7 is a completely voluntary program designed to help Microsoft improve its operating systems over time. * Disable CEIP (Customer Experience Improvement Program): (to enable a services type services.msc in the start menu search box and enable it from the services manager or run the xDark™ Services Manager) * Windows Media Player Network Sharing Service * Program Compatibility Assistant Service
#Auto installer deluxe download to hdd software
* Microsoft® Windows® Malicious Software Removal Tool (1) * Time Zone: (UTC-08:00) Pacific Time (US & Canada) * BitLocker To Go requires a USB flash drive * BitLocker requires Trusted Platform Module (TPM) 1.2 * DVD/CD authoring requires a compatible optical drive * HomeGroup requires a network and PCs running Windows 7 * Windows Touch and Tablet PCs require specific hardware * For some Windows Media Center functionality a TV tuner and additional hardware may be required * Depending on resolution, video playback may require additional memory and advanced graphics hardware
#Auto installer deluxe download to hdd driver
* DirectX 9 graphics device with WDDM 1.0 or higher driver * DVD / USB HDD-Stick with more than 5,4 GB Space If you are an experienced user xDark™ 4.0 Series lets you create your own switchless installers or execute applications with parameters / silent switches in live mode using the context menu, you will also find many other options like customizing the icons appearance of the system and applications individually, changing the attributes options of files, renaming or copying the name of multiple files at once, saving the desktop icons position to restore them whenever you want.
#Auto installer deluxe download to hdd full
In the Start Menu you will find many tools to Edit, Tweak, Customize, Fix or Search anything you need in the System, the xDark™ Power Tools compile everything you need to Customize your OS to the limits making it more personal than ever and even faster, giving you the option to edit system files and applications with just a single right click and supporting the full modification or creation of Windows 7 Styles with the Integration of 7 Style Builder. dll files modified to integrate a new and different look into Windows 7. The xDark™ core consists of more than 500. XDark™ has been build using only WAIK without removing any components or disabling any important services at all. Windows 7 xDark™ Deluxe v4.6 圆4 RG - Codename: State Of Independence

0 notes
Text
What are the benefits and disadvantages of Windows 7?

Windows 7 has a lot of exciting and innovative features that aren't available found in the previous versions. It is beautiful and is specifically designed to work with touchscreens It's more efficient than Vista and Windows XP, It is faster than its predecessors both in terms of the installation process and boot-uptime.
Benefits of Windows 7
Windows Defender has been proven to be the best choice for protecting the system. It is fast to begin and shut down and windows 7 update are a feature that is available for all components of software. SoftMany is the most reliable option Windows 7 Ultimate 32 bit Download.
Windows 7 supports Virtual Hard Disks because of the increased performance of multi-core processors. This helps overcome clutter on the desktop and also introduces three new features: Aero Peek, Aero Shake and snap
Windows 7 has been made more user-friendly than predecessors, and it is probably secure from hackers. It also has advanced touch feature and handwriting recognition.
You can download some eye-catching themes and background pictures on its own Microsoft site or RSS feeds, and you can personalize each aspect of the themes and save for your future usage or even send to others windows 7 customers.
Windows Media Player now has several new features as well as drag-and drop options.
Windows 7 helps you to make the most use of graphics cards made by numerous manufacturers. Windows 7 offers a fresh concept of jump lists, which arrange the recently used files as well as websites.
BitLocker provides encryption for Vista's internal drives, but it also extends to external drives within Windows 7. This allows for easier backup and restore.
Word Pad for Windows 7 is now better and can be used in exactly the same way as Microsoft Office Word. Word prediction, which was released earlier in MS-Office 2007 can now be utilized in Word Pad to predict the future. Paint has a realistic brush.
The calculator was upgraded with new features, such as the conversion of units, the calculation of the fuel efficiency and auto lease payments, and default settings of user account were removed to guard from the unauthorized software to be installed.
There are fewer crashes on Windows 7 Because Windows 7 is more stable than Windows Vista, and Windows Media Player comes with numerous new features within Windows 7, and drag and drop alternative has been included that was not there inside the earlier versions.
Disadvantages of Windows 7
Windows 7 requires RAM capacity that is at least 1GB. It cannot be upgraded quickly from Windows XP.
A lot of applications fail to run in Windows 7 and users are seeking help on the internet. A few users aren't content with new features, as they need additional resources, for instance RAM, to make use of these features.
It's more expensive than prior Microsoft operating system. Some users experience problems with their computer after installing Windows 7. Only advanced users are able to use Windows 7. New users typically have difficulty deciding whether to use Windows 7 and switch to Windows XP.
If the user is using an HP multifunction printer and the driver is being upgraded for Windows 7, then the printer isn't responding to print commands. So the user needs to visit the new HP remedy Center to resolve this issue. SoftMany is the best location to go if want to Windows 7 Ultimate 32 bit Download.
A lot of older programs won't be compatible with Windows 7, and it will be difficult to locate compatible Windows 7 versions. The driver support doesn't provide support for older systems or the older version of motherboards. This disables certain features of Windows 7.
Only the high-end computers can install the Microsoft windows7 7 and it can be used only on highly configured systems, many users have faced the issue of BSOD in conjunction with Windows 7 and have reported, It occurs often because of the software and changes to the hardware in the system.
0 notes
Text
Paragon Ntfs For Mac Os X Аналоги

OS X 10.11 El Capitan; OS X 10.10 Yosemite; Other limitations: Supports VDI backup creation is removed from the UI (not implemented in the engine). Disk management and backup operations with NTFS encrypted with the Bitlocker are not supported. A default iCloud Keychain might need to be re-created after a full system recovery.
Microsoft NTFS for Mac by Paragon Software supports ALL the versions of NTFS (from Windows NT 3.1 to Windows 10). Microsoft NTFS for Mac by Paragon Software is able to get access to compressed files and folders, it has no problems with sparse files and enables all the needed operations with files and folders with security permissions.
Paragon ntfs for mac os x free download - Paragon NTFS for Mac Special Edition, Paragon NTFS for Mac, R for Mac OS X, and many more programs.
Paragon Software Ntfs For Mac
Paragon Ntfs For Mac Os X
Paragon Software Ntfs For Mac 15
Paragon Ntfs For Mac ® Os X
Paragon ntfs for os x free download - Paragon NTFS for Mac Special Edition, Paragon NTFS for Mac, Paragon ExtFS, and many more programs. Popular free Alternatives to Paragon NTFS for Mac OS X for Mac, Software as a Service (SaaS), Windows, Linux, Web and more. Explore apps like Paragon NTFS for Mac OS X, all suggested and ranked by the AlternativeTo user community. List updated: 2/8/2015 10:48:00 PM.
Download Paragon NTFS full crack free – This software let you access any NTFS volumes under OS X El Capitan, Sierra, High Sierra and Mojave. This software provides full read and write access to Windows-formatted NTFS partitions on OS X for free. It breaks down the barriers between Windows and OS X beautifully. Even with the newest update of the MacOS in October 2018.
The biggest problem of a new Mac user is that the inability to write into their external drive. The latest OS X El Capitan has been updated with the new System Integrity Protection (SIP) feature. This new security policy restricts any modifications to certain system files, folders, and processes. This new security measure is also protecting file and data on disk and at run-time, only allowing system binaries to be modified by the system installer and software updates. Very restrictive right? But you don’t to worry. Do you want to bypass this problem? Check out Paragon NTFS for Mac free. download full Version down below.
Paragon NTFS 15 Features Full Crack
Access to any version of NTFS on Mac X
The best support for the HFS + and NTFS file system features
Easy to use for any NTFS partition without the need for specific commands
New User Interface
A very powerful engine for partitioning tasks
Construct, format, delete, undelete, hide and reveal hard drives
Separate the operating system and information
Redistribute empty space
Convert normal MBR disks to GPT disks
Backing up the sectors or files with incremental or differential updates
Backup in called or not called partitions
Backup and play back to / from FTP / SFTP servers
Support for non-Roman characters and languages
Copy a complete hard disk or separate partitions
Supports various virtual machines like VMware Fusion and Parallels Desktop
Unprecedented stability even under heavy workload
Paragon NTFS 15 High Sierra and Older support
Paragon NTFS for Mac free. download full Version
Support MacOS Mojave and Catalina
How to Install Paragon NTFS for Mac Full Version
Download Paragon NTFS for Mac Full Crack
El Capitan, Sierra, High Sierra, and Mojave, disable SIP and Allow Apps
Unzip with zipper to any folder
Run the DMG files to start installation
Apply the patch, crack or Trial Reset
Restart Mac and Enjoy!
Also Download :Tuxera NTFS 2018 Final High Sierra
Download Paragon NTFS 15 Full Crack Mojave
Paragon NTFS Catalina v15.5 | ZippyShare | FileUpload
Paragon NTFS Mojave v15.4 | ZippyShare | MediaFire
High Sierra v15.2 | ZippyShare | MegaNZ
Older Version v14.3 | MediaFire | FileUpload
Password : www.yasir252.com
NTFS for Mac is macOS Big Sur compatible and already available for Apple Silicon
Full read-write access granted!
Microsoft NTFS is one of the primary file systems of Windows. If you work on a Mac computer and need to read or write files from HDD, SSD or a flash drive formatted under Windows, you need Microsoft NTFS for Mac by Paragon Software.
Write, edit, copy, move and delete files on Microsoft NTFS volumes from your Mac! Fast, seamless, easy to use. Mount, unmount, verify, format or set any of your Microsoft NTFS volumes as a startup drive.
New! Ready for macOS 11.0 Big Sur
Write files to Microsoft NTFS drives on your Mac
Can’t write, copy, edit or delete files on Microsoft NTFS-formatted drives from your Mac? It’s because macOS has limited support for Windows volumes — that is, you can only read data, but can’t write or delete anything. Microsoft NTFS for Mac by Paragon Software provides blazing fast, unlimited read/write access to Microsoft NTFS hard drives, SSDs or thumb drives formatted for Windows computers!
A no-brainer upgrade for those installing macOS 10.14 Mojave, Paragon NTFS for Mac remains the best cross-platform utility money can buy, especially now that it plays nice with Apple’s new dark mode.
MacWorld US, Editors’ Choice 2018 www.macworld.com
Whether you’re a hardcore Boot Camp user or just need to occasionally write to Windows-formatted media, this update keeps things working at peak performance…
MacWorld US, Editors’ Choice 2018 www.macworld.com
Running a Mac and having NTFS formatted external disks, you definitely need NTFS for Mac. It is well priced <…> and enables read and write access to your NTFs drives no matter what size.. The speed at which you can read and write the data on these drives is the best of any competitor if there really is one. Anyone who needs to use Mac and Windows computers, needs this app for easy data transfer. The interface is best of any application found, and the application itself offers additional drive tools for taking full control. The latest version also supports Mojave and APFS format to complete a perfect application. It is without real competition and deserves a full 5 star award. This utility makes your external storage usable on any computer system Windows or Mac. So your data remains interchangeable and is fully adapted for macOS MOJAVE.
MacSoftReview www.macsoftreview.com September 2018
Microsoft NTFS for Mac by Paragon Software is a great upgrade to an exceptional cross-platform utility that’s easily worth the money, especially if you own the previous version 14, in which case this one’s free. The user interface is tastefully designed, with buttons for mounting, unmounting, verifying, or erasing the selected volume. Dual-boot users also have the option to reboot into a compatible mounted Mac or Windows startup volume. There’s even a lovely color-coded space indicator like the one introduced with Mac OS X El Capitan, displaying content by Audio, Video, Apps, Images, and Other categories.
MacWorld, USA, August 2017, macworld.com
Microsoft NTFS for Mac by Paragon Software, the excellent third-party file system driver that enables writing to Windows-formatted volumes at native speeds.
MacWorld, USA, June 2017, macworld.com
Microsoft NTFS for Mac by Paragon Software is the best such software solution: reliable, fast, and now affordable as well… Fast, seamless, and easy to use, Microsoft NTFS for Mac by Paragon Software is required for those who need to write to Windows volumes. And now it’s more affordable than ever.
MacWorld, USA 2016, macworld.com
A very specialized product that does its job in a very unobtrusive way. You just install it and it works. When you plug an NTFS disk into your Mac, it just mounts on the desktop like any other disk, and when you copy a file to it, it just works, no muss, no fuss. This utility is also invaluable if you find yourself in a situation where you need to format a disk as NTFS, and it performs this task with an equal lack of drama
Apple Press, DVMUG
Microsoft NTFS for Mac by Paragon Software is an essential installation for anyone working with Macs and PCs, as it helps to break down the barriers that exist between the two operating systems
Mac World UK, macworld.com
It’ll install cleanly and easily on macOS 10.12 Sierra and “just work”, so it’s a good option
How-to-Geek
Microsoft NTFS for Mac by Paragon Software does exactly what we expect from it, by offering a seamless NTFS disk management. It’s good performances even allow working directly on the Windows partition, including for heavy applications such as video or photo processing.
mac4ever.com
WOW….Ive been struggling with the whole MAC/Windows NTFS issue for some time and have a number of external drives that I need to swap between Mac/PC all the time. I’ve always had a headache with NTFS drivers etc. I bought and downloaded your Microsoft NTFS for Mac by Paragon Software today and WOW. Amazing. Everything just works. Brilliant product. Worth every penny. Thank you.
Robinson Philip
It is pretty fast with NTFS transfers (slightly slower than OSX extended partitions obviously) and I’ve never had any problems mid-transfer or anything. For me, it’s always done what it said on the box, and now with V14 it’s got El Capitan compatibility, so no complaints here. If you’re looking for a way to have plug-and-play NTFS drives on your mac, there really isn’t a better alternative to Microsoft NTFS for Mac by Paragon Software. Highly recommended for all Mac users!
M. Doyle
If you have a Mac and you need to access volumes that are formatted NTFS, this is the best solution out there. Why Apple hasn’t just baked in support for NTFS after all these years still remains a mystery. I’ve been using Microsoft NTFS for Mac by Paragon Software for several years now and have never had any problems with it.
H. Jaynes
Blazing Fast
Microsoft NTFS for Mac by Paragon Software is up to six times faster than any of its closest commercial competitors!
Fully Compatible
Supports macOS Big Sur and older macOS See Specifications
Powerful Features
Safe data transfer, hassle-free work, easy to use, seamless user experience
How it Works
Simple as 1-2-3
Install
Download and install Microsoft NTFS for Mac by Paragon Software onto your Mac.
Done!
Microsoft NTFS volumes connected to your Mac are available in the Finder.
All operations just a click away!
If you need more than just a blazing fast and reliable Microsoft NTFS driver, our lightweight menubar and full-featured Microsoft NTFS for Mac by Paragon Software apps are always at your service.
Access all of your Microsoft NTFS drives and perform the most common volume operations like mount, unmount and verify.
Quickly restart your Mac in Windows from the menubar (assuming it’s installed on your mounted Microsoft NTFS drive).

Seamless User Experience
If you’ve ever used Apple’s Disk Utility, you already know how to use Microsoft NTFS for Mac by Paragon Software. If you haven’t, it will only take a few moments to get acquainted.
Microsoft NTFS for Mac by Paragon Software takes the best of Apple’s Disk Utility and moves it to the next level, augmenting Microsoft NTFS volume operations and advanced mount options.
Mounting is entirely under your control with advanced options
Mount in Read-Only: select this option if you need to access sensitive data without modifying any files.
Do not mount automatically: select this option if you want to manually control access to a volume.
Outstanding performance at blazing fast speed
Microsoft NTFS for Mac by Paragon Software is the fastest file system driver on the market:
6x times faster*
than competing solutions
Paragon Software Ntfs For Mac
*Tested on 2016 MacBook Pro with SSD drive, view benchmarks here.

Fresh review: check out the video review by European Motion Picture Association.
Paragon Ntfs For Mac Os X
Latest award: 5-star review of the Mojave-ready edition.
Features
Features
Benefits
Supported Operating Systems
macOS Big Sur
macOS Catalina
macOS Mojave
macOS High Sierra
macOS Sierra
Supported File Systems
All Microsoft NTFS versions are supported (from Windows NT 3.1 to Windows 10).
Write Access
When a volume is mounted in write mode, you can do everything with the files and folders it contains: read, edit, delete, rename, create new.
Automount
Microsoft NTFS for Mac by Paragon Software mounts supported volumes automatically at startup, so you don’t need to worry each time you restart the operating system or power your computer on. However, this feature can be disabled at any time in the program interface.
Volume Management
Microsoft NTFS for Mac by Paragon Software easily formats, checks integrity and repairs corrupted volumes.
Internationalization
Microsoft NTFS for Mac by Paragon Software supports all alphabets supported by your operating systems, including those that use non-Roman and non-Latin characters, so you will never face the problem of not getting access to file names on volumes mounted in non-native OS.
Compatible with Apple Boot Camp
Microsoft NTFS for Mac by Paragon Software is fully compatible with Apple Boot Camp software and provides direct read and write access to Mac partitions from Windows installed on Boot Camp.
Compatible with 3rd party software
Microsoft NTFS for Mac by Paragon Software is compatible with popular virtualization and encryption applications including VMware Fusion and Workstation, Parallels Desktop, TrueCrypt and its forks.
Paragon Software Ntfs For Mac 15
Paragon Technology Center
Want to learn more about the technology behind Microsoft NTFS for Mac by Paragon Software? Check out the Paragon Technology Portal!
Frequently Asked Questions
Could I try your product for free before buying?
Sure, you can try Microsoft NTFS for Mac by Paragon Software for ten days completely for free. After that it will be locked until you activate a purchased license.
I’m a user of a Seagate or Western Digital device with pre-installed NTFS for Mac. How can I get my update?
You are eligible for a special update for you current version of Microsoft NTFS for Mac by Paragon Software. Please contact our Support Service at [email protected] to reclaim your update.
Does it work with macOS 11.0 Big Sur?
Yes, Microsoft NTFS for Mac by Paragon Software works with the latest available macOS versions (incl. macOS Big Sur Public Beta).
How can I get the update if I have bought the previous version of Microsoft NTFS for Mac by Paragon Software?
Please, visit your MyParagon account. If an update is released, you will be able to download it there.
What operations do you mean saying “Full read/write access”?
You can perform create/read/modify/copy/delete operations as usual.
What data transfer rate I will get using Microsoft NTFS for Mac by Paragon Software?
The data transfer rate is fully the same as with the native macOS file system. There you can see the statistics.
What versions and features of the Microsoft NTFS file system are supported?
Microsoft NTFS for Mac by Paragon Software supports ALL the versions of NTFS (from Windows NT 3.1 to Windows 10). Microsoft NTFS for Mac by Paragon Software is able to get access to compressed files and folders, it has no problems with sparse files and enables all the needed operations with files and folders with security permissions.
Is BootCamp supported?
Yes, we completely support all BootCamp configurations.
What should I do if I have OS X 10.9 but Microsoft NTFS for Mac by Paragon Software doesn’t support OS older than 10.10?
Please follow steps below.
Uninstall Microsoft NTFS for Mac 15 by Paragon Software.
Restart Mac.
Download Microsoft NTFS for Mac 14 by Paragon Software from your MyParagon Account.
Install it.
Restart Mac.
Can I re-activate my license on another Mac?
Sure. Please re-activate the product following the steps below.
Log in to MyParagon portal.
Find your product in the list of My Products, then click “Show details”, press “Release license”.
License status will be marked as “Not in use”: article in Paragon Knowledge Base.
Then activate your product again.
How many times can I re-activate my license?
You can re-activate it 4 times. If you need to re-activate your license more than 4 times, please contact our Support or file a support ticket and we will help you to release the counter of licenses.
It doesn’t work! My Microsoft NTFS drive is not recognized by macOS, even after installing Microsoft NTFS for Mac by Paragon Software.
First of all, please check that Activate/Buy buttons are shown, and (if you have started the trial period) that you see “X days left” message. Then check NTFS for Mac Preferences and make sure that the driver is enabled. If it did not work, please check the troubleshooting guide.
I frequently work with NTFS, HFS+, APFS-formatted partitions on my Mac and Windows PC. Can I get a discount, if I buy all drivers at once?
Yes, you can purchase our new Paragon Mac ToolBox for just $39.95. The Suite contains 4 tools to guarantee seamless cross-platform data exchange and disk space management:
Microsoft NTFS for Maс by Paragon Software
APFS for Windows by Paragon Software
HFS+ for Windows by Paragon Software
Paragon CampTune
Ensure multi-platform access - activate required file system drivers based on your IT park, regardless of OS, in any proportion.
Resources
Current Version
Download Microsoft NTFS for Mac by Paragon Software
Product Documentation
Download Microsoft NTFS for Mac by Paragon Software One Pager
Need help?
Contact Support or file a support ticket
Latest review
European Motion Picture Association (EURMPA) reviews Microsoft NTFS for Mac by Paragon Software. Watch the videos!
NTFS for Mac build for Apple Silicon
Apple has announced a two-year transition to ARM-based processors known as “Apple Silicon.” Since the new Apple Silicon-based Mac computers are just around the corner, we proactively took on this project. We are delighted to offer Mac users our new NTFS for Mac build for Apple Silicon, which is available for download below.
This offer may be of particular interest for Developer Transition Kit users. If you currently participate in the Universal App Quick Start Program or are just planning to enroll, right now you can download and begin using the new NTFS for Mac build for Apple Silicon on your DTKs.
Paragon Ntfs For Mac ® Os X
Microsoft NTFS for Mac by Paragon Software speaks fluently many languages: English Deutsch Русский Español Français Italiano Čeština 简体中文 繁體中文 한국어 Svenska Suomi Magyar Polski

0 notes
Text
Configuration Manager Technical Preview 2005

Configuration Manager Technical Preview 2005. You can now initiate an application install in real time for a tenant attached device from the Microsoft Endpoint Management admin center. Helpdesk users can initiate real-time queries and run PowerShell scripts from the cloud against an individual Configuration Manager managed device and return the results to the admin center. Additionally, you can now see a timeline of events that shows past activity on the device that can help you troubleshoot problems for each device. Tenant attach: Device timeline in the admin center When Configuration Manager synchronizes a device to Microsoft Endpoint Manager through tenant attach, you can now see a timeline of events. This timeline shows past activity on the device that can help you troubleshoot problems. Tenant attach: Install an application from the admin center You can now initiate an application install in real time for a tenant attached device from the Microsoft Endpoint Management admin center. Tenant attach: CMPivot from the admin center Bring the power of CMPivot to the Microsoft Endpoint Manager admin center. Allow additional personas, like Helpdesk, to be able to initiate real-time queries from the cloud against an individual ConfigMgr managed device and return the results back to the admin center. This gives all the traditional benefits of CMPivot, which allows IT Admins and other designated personas the ability to quickly assess the state of devices in their environment and take action. Tenant attach: Run Scripts from the admin center Bring the power of the Configuration Manager on-premises Run Scripts feature to the Microsoft Endpoint Manager admin center. Allow additional personas, like Helpdesk, to run PowerShell scripts from the cloud against an individual Configuration Manager managed device. This gives all the traditional benefits of PowerShell scripts that have already been defined and approved by the Configuration Manager admin to this new environment. VPN boundary type To simplify managing remote clients, you can now create a new boundary type for VPNs. Previously, you had to create boundaries for VPN clients based on the IP address or subnet. This configuration could be challenging or not possible because of the subnet configuration or the VPN design. Now when a client sends a location request, it includes additional information about its network configuration. Based upon this information, the server determines whether the client is on a VPN. All clients that connect through a VPN automatically belong to the boundary group associated with this new boundary type. Azure AD authentication in Software Center This release fixes an issue with Software Center and Azure Active Directory (Azure AD) authentication. For a client detected as on the intranet but communicating via the cloud management gateway (CMG), previously Software Center would use Windows authentication. When it tried to get the list of user available apps, it would fail. It now uses Azure Active Directory (Azure AD) identity for devices joined to Azure AD. These devices can be cloud-joined or hybrid-joined. Install and upgrade the client on a metered connection Previously, if the device was connected to a metered network, new clients wouldn't install. Existing clients only upgraded if you allowed all client communication. For devices that are frequently roaming on a metered network, they would be unmanaged or on an older client version. Starting in this release, client install and upgrade both work when you set the client setting Client communication on metered internet connections to Allow. To define the behavior for a new client installation, there's a new ccmsetup parameter /AllowMetered. When you allow client communication on a metered network for ccmsetup, it downloads the content, registers with the site, and downloads the initial policy. Any further client communication follows the configuration of the client setting from that policy. Task sequence media support for cloud-based content Even though there are more remote devices to manage these days, you may still have business processes to recover devices using task sequence media. For example, you send a USB key to a remote user to reimage their device. Or a remote office that has a local PXE server, but devices mainly connect to your main network over the internet. Instead of further taxing the VPN to download large OS deployment content, boot media and PXE deployments can now get content from cloud-based sources. For example, a cloud management gateway (CMG) that you enable to share content. Improvements to cloud management gateway cmdlets With more customers managing remote devices now, this release includes several new and improved Windows PowerShell cmdlets for the cloud management gateway (CMG). You can use these cmdlets to automate the creation, configuration, and management of the CMG service and Azure Active Directory (Azure AD) requirements. For example, an Azure administrator first creates the two required apps in Azure Active Directory (Azure AD). Then you write a script that uses the following cmdlets to deploy a CMG: Import-CMAADServerApplication: Create the Azure AD server app definition in Configuration Manager.Import-CMAADClientApplication: Create the Azure AD client app definition in Configuration Manager.Use Get-CMAADApplication to get the app objects, and then pass to New-CMCloudManagementAzureService to create the Azure service connection in Configuration Manager.New-CMCloudManagementGateway: Create the CMG service in Azure.Add-CMCloudManagementGatewayConnectionPoint: Create the CMG connection point site system. Community hub and GitHub The IT Admin community has developed a wealth of knowledge over the years. Rather than reinventing items like Scripts and Reports from scratch, we've built a Configuration Manager Community hub where IT Admins can share with each other. By leveraging the work of others, you can save hours of work. The Community hub fosters creativity by building on others' work and having other people build on yours. GitHub already has industry-wide processes and tools built for sharing. Now, the Community hub will leverage those tools directly in the Configuration Manager Console as foundational pieces for driving this new community. For the initial release, the content made available in the Community hub will be uploaded only by Microsoft. Currently, you can't upload your own content to GitHub for use by Community hub. Community hub supports the following objects: PowerShell ScriptsReportsTask sequencesApplicationsConfiguration items Microsoft 365 Apps for enterprise Office 365 ProPlus was renamed to Microsoft 365 Apps for enterprise on April 21, 2020. Starting in this technical preview the following changes have been made: The Configuration Manager console has been updated to use the new name.This change also includes update channel names for Microsoft 365 Apps.A banner notification was added to the console to notify you if one or more automatic deployment rules reference obsolete channel names in the Title criteria for Microsoft 365 Apps updates. If you use Title as criteria for Microsoft 365 Apps updates in your automatic deployment rules, use the next section to help modify them. Update channel information for Microsoft 365 Apps When Office 365 ProPlus was renamed to Microsoft 365 Apps for enterprise, the update channels were also renamed. If you use an automatic deployment rule to deploy updates, you'll need to make changes to your rules if they rely on the Title property. That's because the name of update packages in the Microsoft Update Catalog is changing. Currently, the title of an update package for Office 365 ProPlus begins with "Office 365 Client Update" as seen in the following example: Office 365 Client Update - Semi-annual Channel Version 1908 for x64 based Edition (Build 11929.20648) For update packages released on and after June 9, the title will begin with "Microsoft 365 Apps Update" as seen in the following example: Microsoft 365 Apps Update - Semi-annual Channel Version 1908 for x64 based Edition (Build 11929.50000) New Channel namePrevious Channel nameSemi-Annual Enterprise ChannelSemi-Annual ChannelSemi-Annual Enterprise Channel (Preview)Semi-Annual Channel (Targeted)Monthly Enterprise ChannelNACurrent ChannelMonthly ChannelCurrent Channel (Preview)Monthly Channel (Targeted)Beta ChannelInsider Report setup and upgrade failures to Microsoft If the setup or update process fails to complete successfully, you can now report the error directly to Microsoft. If a failure occurs, the Report update error to Microsoft button is enabled. When you use the button, an interactive wizard opens allowing you to provide more information to us. In technical previews, this button is always enabled even when the setup completes successfully. When running setup from the media rather than the console, you'll also be given the Report update error to Microsoft option if setup fails. Notification for Azure AD app secret key expiration Based on your UserVoice feedback, if you Configure Azure services to cloud-attach your site, the Configuration Manager console now displays notifications for the following circumstances: One or more Azure AD app secret keys will expire soonOne or more Azure AD app secret keys have expired Improvements to BitLocker task sequence steps Based on your UserVoice feedback, you can now specify the Disk encryption mode on the Enable BitLocker and Pre-provision BitLocker task sequence steps. The Enable BitLocker step also now includes the setting to Skip this step for computers that do not have a TPM or when TPM is not enabled. Improvements to the content library cleanup tool If you remove content from a distribution point while the site system is offline, an orphaned record can exist in WMI. Over time, this behavior can eventually lead to a warning status on the distribution point. The content library cleanup tool in delete mode could remove orphaned files from the content library. It can now also remove orphaned content records from the WMI provider on a distribution point. Remove command prompt during Windows 10 in-place upgrade During a task sequence to upgrade a device to Windows 10, during one of the final Windows configuration phases a command prompt window opens. The window is on top of the Windows out-of-box experience (OOBE), and users can interact with it to disrupt the upgrade process. Starting in this release, the SetupCompleteTemplate.cmd and SetupRollbackTemplate.cmd scripts from Configuration Manager include a change to hide the command prompt window. Read the full article
#Mac#MacOS#MECM#MEMCM#MicrosoftAzure#MicrosoftEndpointConfigurationManager#MicrosoftOffice365#MicrosoftOfficeInsider#OfficeProPlus#SystemCenterConfigurationManager#Windows#Windows10
0 notes
Text
Windows Services complete list with ShortName and DisplayName

Here's a comprehensive list of most - if not all - Windows Service available nowadays on the major Windows operating systems - Windows 10, Windows Server 2016 and so on. The list shows the Display Name and the system's ShortName, which is the unique name used by the OS to locate and idenfity the service. The list should contain almost any known built-in service from both Windows and Windows Server: however, if you happen to find a missing one, feel free to write it in the comments section of this post, so that we'll be able to fill the gap! Display Name ShortName ActiveX Installer (AxInstSV) AxInstSV Adaptive Brightness SensrSvc Application Experience AeLookupSvc Application Host Helper Service AppHostSvc Application Identity AppIDSvc Application Information Appinfo Application Layer Gateway Service ALG Application Management AppMgmt ASP.NET State Service aspnet_state Background Intelligent Transfer Service BITS Base Filtering Engine BFE BitLocker Drive Encryption Service BDESVC Block Level Backup Engine Service wbengine Bluetooth Support Service bthserv BranchCache PeerDistSvc Certificate Propagation CertPropSvc Client for NFS NfsClnt CNG Key Isolation KeyIso COM+ Event System EventSystem COM+ System Application COMSysApp Computer Browser Browser Credential Manager VaultSvc Cryptographic Services CryptSvc DCOM Server Process Launcher DcomLaunch Desktop Window Manager Session Manager UxSms DHCP Client Dhcp Diagnostic Policy Service DPS Diagnostic Service Host WdiServiceHost Diagnostic System Host WdiSystemHost Disk Defragmenter defragsvc Distributed Link Tracking Client TrkWks Distributed Transaction Coordinator MSDTC DNS Client Dnscache Encrypting File System (EFS) EFS Extensible Authentication Protocol EapHost Fax Fax Function Discovery Provider Host fdPHost Function Discovery Resource Publication FDResPub Group Policy Client gpsvc Health Key and Certificate Management hkmsvc HomeGroup Listener HomeGroupListener HomeGroup Provider HomeGroupProvider Human Interface Device Access hidserv IIS Admin Service IISADMIN IKE and AuthIP IPsec Keying Modules IKEEXT Indexing Service CISVC Interactive Services Detection UI0Detect Internet Connection Sharing (ICS) SharedAccess IP Helper iphlpsvc IPsec Policy Agent PolicyAgent KtmRm for Distributed Transaction Coordinator KtmRm Link-Layer Topology Discovery Mapper lltdsvc LPD Service LPDSVC Media Center Extender Service Mcx2Svc Message Queuing MSMQ Message Queuing Triggers MSMQTriggers Microsoft .NET Framework NGEN v2.0.50727 clr_optimization_v2.0.50727 Microsoft FTP Service ftpsvc Microsoft iSCSI Initiator Service MSiSCSI Microsoft Software Shadow Copy Provider swprv Multimedia Class Scheduler MMCSS Net.Msmq Listener Adapter NetMsmqActivator Net.Pipe Listener Adapter NetPipeActivator Net.Tcp Listener Adapter NetTcpActivator Net.Tcp Port Sharing Service NetTcpPortSharing Netlogon Netlogon Network Access Protection Agent napagent Network Connections Netman Network List Service netprofm Network Location Awareness NlaSvc Network Store Interface Service nsi Offline Files CscService Parental Controls WPCSvc Peer Name Resolution Protocol PNRPsvc Peer Networking Grouping p2psvc Peer Networking Identity Manager p2pimsvc Performance Logs & Alerts pla Plug and Play PlugPlay PnP-X IP Bus Enumerator IPBusEnum PNRP Machine Name Publication Service PNRPAutoReg Portable Device Enumerator Service WPDBusEnum Power Power Print Spooler Spooler Problem Reports and Solutions Control Panel Support wercplsupport Program Compatibility Assistant Service PcaSvc Protected Storage ProtectedStorage Quality Windows Audio Video Experience QWAVE Remote Access Auto Connection Manager RasAuto Remote Access Connection Manager RasMan Remote Desktop Configuration SessionEnv Remote Desktop Services TermService Remote Desktop Services UserMode Port Redirector UmRdpService Remote Procedure Call (RPC) RpcSs Remote Procedure Call (RPC) Locator RpcLocator Remote Registry RemoteRegistry RIP Listener iprip Routing and Remote Access RemoteAccess RPC Endpoint Mapper RpcEptMapper SeaPort SeaPort Secondary Logon seclogon Secure Socket Tunneling Protocol Service SstpSvc Security Accounts Manager SamSs Security Center wscsvc Server LanmanServer Shell Hardware Detection ShellHWDetection Simple TCP/IP Services simptcp Smart Card SCardSvr Smart Card Removal Policy SCPolicySvc SNMP Service SNMP SNMP Trap SNMPTRAP Software Protection sppsvc SPP Notification Service sppuinotify SSDP Discovery SSDPSRV Storage Service StorSvc Superfetch SysMain System Event Notification Service SENS Tablet PC Input Service TabletInputService Task Scheduler Schedule TCP/IP NetBIOS Helper lmhosts Telephony TapiSrv Telnet TlntSvr Themes Themes Thread Ordering Server THREADORDER TPM Base Services TBS UPnP Device Host upnphost User Profile Service ProfSvc Virtual Disk vds Volume Shadow Copy VSS Web Management Service WMSVC WebClient WebClient Windows Audio AudioSrv Windows Audio Endpoint Builder AudioEndpointBuilder Windows Backup SDRSVC Windows Biometric Service WbioSrvc Windows CardSpace idsvc Windows Color System WcsPlugInService Windows Connect Now – Config Registrar wcncsvc Windows Defender WinDefend Windows Driver Foundation – User-mode Driver Framework wudfsvc Windows Error Reporting Service WerSvc Windows Event Collector Wecsvc Windows Event Log EventLog Windows Firewall MpsSvc Windows Font Cache Service FontCache Windows Image Acquisition (WIA) StiSvc Windows Installer msiserver Windows Live Family Safety fsssvc Windows Management Instrumentation Winmgmt Windows Media Center Receiver Service ehRecvr Windows Media Center Scheduler Service ehSched Windows Media Player Network Sharing Service WMPNetworkSvc Windows Modules Installer TrustedInstaller Windows Presentation Foundation Font Cache 3.0.0.0 FontCache3.0.0.0 Windows Process Activation Service WAS Windows Remote Management (WS-Management) WinRM Windows Search WSearch Windows Time W32Time Windows Update wuauserv WinHTTP Web Proxy Auto-Discovery Service WinHttpAutoProxySvc Wired AutoConfig dot3svc WLAN AutoConfig Wlansvc WMI Performance Adapter wmiApSrv Workstation LanmanWorkstation World Wide Web Publishing Service W3SVC WWAN AutoConfig WwanSvc Read the full article
0 notes
Link
Mobile devices are common. It now completely integrates with laptop, televisions and other smart digital assistants. With the advent of the mobile operating system such as Android, there is every possibility of the creation of mobile computing environments. Most people are used for personal, professional or smart office and home office environments. There has been consciousness to utilize computers. Most of the mobile users do not have such level of knowledge expertise and that proves to be the sole point of prime medium for hacking of mobile devices.
The speed with which the flow of data comes and goes within mobile devices, has been enormous. It has been full of applications and most of these applications do have a huge repository of data and those data synchronized in the faster way through cloud servers and hackers always look out for such cloud mediums to find out more personal information to hack these accounts. Most mobile devices operate with the principle of no encryption. Even if the latest Android operating system does send and receive data in terms of encryption but for pure encryption it is important to do the users.
The sole problem with Android devices is that these provide every possibility with users. Even if some users do implement encryption of data but still those are extremely poorly implemented that it could provide ways and means for hackers to enter your devices easily. Most of the Android operating system does provide huge amenities for settings of making it most secure but it is also important for users to learn everything about it so that ultimately it is up to users to decide upon at which level he or she wants to deal with security options.
Most of these passwords are easily guessed and in the guise of the friend in social media link hacker could understand and get the idea of these and this could prove to be an extremely dangerous phenomenon and that makes entire security options of mobile very difficult to manage for users. Most of the android devices have to depend heavily upon the original equipment manufacturers to provide updates to the system. For this, it is important that certain updates even if android maker Google releases but still not being updated to many devices as most of these android devices are customized android devices, and most of the original equipment manufacturers have off late only concentrated on releasing upon new devices instead of updating older devices.
This makes the user most vulnerable and that creates difficulty for users to cope with the latest security vulnerabilities of Android devices has. Most of the Android applications run in the form of applications which are separated from the entire operating system command line environment. Unlike Windows operating system where we do find that all these applications need to be there in the same line as that of Windows system files and this make running and controlling of these applications very much easier possibility.
Apart from these internet enabled applications within desktop environments runs with these applications in specific web-browsers. For this it becomes super easy to counter these apps. Whereas in the case with android application environment most of these applications are platform-independent and does not depend upon specific system applications to run and in this, for every website such as beginning from Facebook to others we do see the presence of these apps. On the other side, it is also a boon for users as these applications are constantly updated from time to time and that makes many of the security holes that might exist within these application environments could possibly be plugged or patched.
With the advent of Android, we do witness the presence of an update of applications within a single month or even more than once in a single month. This makes it secure but another important factor is tantamount to update the application. If the user does not have any idea on how to update these applications ultimately, that could land the user in grave trouble of inviting viruses or hackers to creep into system resources. Google of late while realizing the constraints of users. Has been strengthening its application store. Google’s application store is known as ‘Google Play Store’ and it has a vast depository of applications.
It now scans every application and also checks whether these applications are being periodically updated or not. It also sees user’s reaction and responses from time to time to understand, what sort of experiences they have. It also has sandboxes application environment, where every application is constantly being scanned. Google Play services have been updated regularly with newer features to scan applications periodically and it installs these applications or downloaded application in the sandboxes environment similar to that what exists in Google’s own desktop browser.
All these tabs on Google Chrome are being sandboxes so that when one of these tabs got hanged due to some wrong decoding of website scripts still the user can use the other tabs normally.
This means each tab is completely being secluded from each other. Google implemented exactly the similar principle with android application environment. Now, each of application you download runs with a separate sandboxing environment, completely separate from system processes of Android operating system. If at all at any point in time, any virus stays within any application, with constant scanning by Google, it checks every application details and it could be uninstalled and disabled by Google automatically.
Even before complete removal of the application from android devices, application running in sandboxing environment which is the reduced privileged state, then the application would not be going to do any harm to the device. It is part of the most wonderful and sophisticated security systems which Google has implemented with android devices and that makes most of Android device completely secure until and unless user downloads these applications from Google Play store only and not from any other sources. You can encrypt connection of android so that every data that is there within Android are in the state of encryption and when hacker even if steal the data, that ultimately not going to produce any fruitful results as most of these data could not be encrypted and should be staying in the state of encryption.
Similar is BitLocker encryption of windows devices which makes hackers to pay their money and with it, hackers realize that even if they hack these devices they are not going to recognize and understand these data as these data stays in the state of complete encryption. This is another fantastic way to control hacking of devices and in this way everything stays secure. It is very important for users to move towards all such countermeasures techniques so that ultimately. These could lead towards the most possible and pervasive interests in understanding what measures the best security possibilities of your devices as after all these contain most of these data.
It is equally important to buy devices from good original equipment manufacturers so that what do they provide with their devices and management of devices could be stronger than that of other original equipment manufacturers. There are many aspects of disc encryptions which users do need to understand and want to be making a move. It needs to have a good password selection process so that it should very difficult to decipher by hackers. Microsoft’s disc encryption software enables users to carry their passwords with a USB drive for additional hardware security.
If hackers able to find these passwords then there is nothing value to disc-encryption and for this it is important to understand to keep these passwords in a safer place and make it thin as the most valuable entity so that you should always remember to keep it in a safer and important place. Screen lock is essential part of any disc-encryption.
If you have not implemented any of hard secure key locks then for sure it is going to be the worst possible decision making of moving towards the fallacies of complete disc encryption. It is also important to understand no disc-encryption is full proof. True crypt developers have abandoned it and for this, there could have been any sort of security holes that could have led to you to the stage of complete null state.
Similarly, there have been many faults with Bit locker security but still it is managed by Microsoft and the security holes are time and again being updated and for this it is important to not only go with disc encryption but also keep all of these safeguarding options open for all the time so that you should always be aware to keep the absolute security maintenance and alertness with every single day.
0 notes
Text
Coding Boot Camps: Pluses, Minuses, and Alternatives
By: Kendra Moyer
THE GOOD
Computer software engineers design and maintain the digital products we use frequently , from social media apps, to the programs controlling our home appliances.. With the current digital revolution, there is an increased demand for skilled software engineers.
Coding Boot camps are short programs averaging 8-12 weeks that aim to teach newcomers the basics of computer software engineer
Coding boot camps offer students with little to no coding experience the opportunity to learn the basics of computer coding in a short space of time. These programs are often geared toward web development, but some are more complex and explore more complicated coding languages, including C++.
The average expense for a coding boot camp might be anywhere from $10-20K depending on the coding languages offered, and the level of difficulty of the courses
Coding boot camps allow employees to enhance their computer competency in software engineering, while having an access to an otherwise unavailable employment network . Many coding camps also offer employment placement, and are often marketed to lower income, non traditional demographics who seek to gain higher income through increasing their technical skills.
THE BAD
Controversy.
HB1 Visa Status
Coding boot camps are short term solutions to the perceived shortage of software engineers. Many software engineers have found their work either outsourced, or subject to the prevalence of HB1 Visa status immigrating computer programmers, who command lower salaries than American workers. Due to this competitive tension, the pay has begun to decrease as more coders jockey for the most coveted, Silicon Valley, positions.
Coding boot camps are often not affordable to the average working class person. Due the financial inaccessibility, these programs and have been criticized for increasing the participation of the groups currently dominating the software engineering industry. This has defeated the purpose of these camps, of bringing more diverse coders into the industry.
THE UGLY
Coding Boot camps fail to address the cultural attitudes prevalent in the software industry, which have resulted in an exodus of women in search of a less hostile and more supportive working atmosphere. The overly analytical, exacting nature of programmers is often a barrier to women and some lesser represented people of color entering the field.
The software engineering profession has earned a poor reputation due to the lack of representation that have plagued the industry’s attempts to diversify. Coding camps are no quick solution to deeply ingrained cultural attitudes and have not adequately addressed the lack of true inclusion for non traditional coders.
As many programmable devices become more intimately involved in the lives of all people who use them, these cultural attitudes are found to affect the outcomes of programmed devices.
The computer science industry has a preference for 4 year college degrees in computer science. Coding Camps are deemed by HR many recruiters as starter training camps that are insufficient for producing highly competent coders. The influx of boot camps have watered down the pool of applicants for entry level positions, with new coders threatening high salaries, creating greater supply against lesser demand. Coding Camp graduates struggle to be taken seriously in larger markets offering higher salaries.
Alternatives to Coding Camps
There are alternative routes to coding camps for people committed to this industry. As in many technical industries, coding is more of a hands-on path than a 4 year traditional training program. Experience, adaptation, and innovation are rewarded over traditional education. Many famous coders including Bill Gates and Mark Zuckerberg never earned college degrees, opting instead to become industry trailblazers. Innovative problem solving allows software companies to thrive in a tight markets.
Free and open source software packages offer the user the right through the GPL license to modify, borrow, or improve the code by identifying bugs and reporting or fixing these bugs through an repository of code such as GIThub. Once a coder is registered and begins to submit patches to broken software packages, reporting bugs, or other pushing out improvements, these coders slowly build up skills, practice hours, and create an international reputation for themselves as competent in their chosen field.
The most affordable route for budding coders, is to started with a simple language like PHP, HTML, or Python through You Tube, Code Academy, Hacker Rank, or Exorcism. These platforms allow for self paced training in the basics of coding without the expenses or pressure of rushing through difficult and detailed material.
There are also internships available for new and under represented coders such as The Outreachy Internship, sponsored by Red Hat Linux and the Free Software Conservancy. This internship offers a $5000 6 month internship with major corporations. Paid internships requiring that applicants have already done independent coding and submitted their work to Git hub, is a viable alternative.
There are currently more than 90 coding boot camps in the US and Canada.
Watters, A. (2017). Why Are Coding Boot camps Going Out of Business?. Hack Education. Retrieved 17 October 2017, from http://hackeducation.com/2017/07/22/bootcamp-bust
Coding school graduates: Are they worth hiring?. (2017). TechRepublic. Retrieved 17 October 2017, from http://www.techrepublic.com/article/coding-school-graduates-are-they-worth-hiring/
The Library Digital Privacy Pledge – Library Freedom Project. (2017). Libraryfreedomproject.org. Retrieved 17 October 2017, from https://libraryfreedomproject.org/ourwork/digitalprivacypledge/
Center, E. (2017). EPIC - EPIC Student Privacy Project. Epic.org. Retrieved 17 October 2017, from https://epic.org/privacy/student/
Digital Privacy Toolkit for Librarians, a LITA webinar – LITA Blog. (2015). Litablog.org. Retrieved 17 October 2017, from http://litablog.org/2015/10/digital-privacy-toolkit-for-librarians-a-lita-webinar/
James, Geoffrey. Why Coding Boot camps Don't Work. (2017). Inc.com. Retrieved 17 October 2017, from https://www.inc.com/geoffrey-james/why-coding-bootcamps-dont-work.html
Digital Privacy for Libraries
PUBLIC SERVICE NOTICE
The majority of sensitive data online is self contributed data. Law enforcement and hackers are no match for the average computer user offering personal information for no discernible reason. Self censorship is the best strategy for digital privacy.
PASSWORDS
The most basic form of digital security is secure passwords.. A less hackable password will be longer and will contain a combination of capitalized letters, numbers, and symbols. For example PW: peanutbutter might be spelled “P3@nutButt3r@ndJ3llyTim3”
Password managers such as 1Pass, KeeP, Last Pass are free services that create longer passwords that are harder to break
Make sure passwords are long, have no set patterns, and have complex symbols to make guessing harder. Periodically change passwords.
SOFTWARE UPDATES
Check regularly and maintain periodic software updates. Many security breaches happen in the gaps between these updates.
BROWSERS
What you Google becomes your identity. The Google Chrome Browser offers little to no privacy. Of that data that the user is viewing. The paranoid privacy advocate will understand there is a best time for each.
The best practice is that anything you would not want published about yourself, you would want to avoid Googling about yourself. Google Chrome is best used for public information. The TOR browser is an excellent alternative to Google Chrome.
Google Chrome has extensions including HTTPS Everywhere, safe browsing and other privacy features.
Google Chrome collects data for Google Analytics through cookies attached to sites that through end user agreements mine your personal browsing data. The Privacy Badger extension mitigates some of this data analytics collection, and will free up bandwidth from the unwanted scripts being run to collect your data.
HTTPS Everywhere ensures the maximum security while browsing sites. This extension was developed by the EFF (Electron Frontier Foundation) and is very useful blocking websites that are not secure due to malware, viruses, or intrusive data collection. Analytic software is notorious for running scripts in the backgrounds of websites and eating up bandwidth, slowing down the system.
Pay Attention to Security Warnings
Mobile Devices are more difficult to secure largely due to user habits and self contributions of personal information
A smart Smart Phone user interested would be encouraged to use the Signal App on Android. This app allowed users to text through encrypted channels.
The Guardian Project offers detailed information for journalists, students, and activists who use Android products.
This includes the Secure Drop Project allowing whistle-blowers to share sensitive data without unmasking their identity.
DISK ENCRYPTION
Disk encryption is another step in securing your personal hardware. Filevault, Bitlocker and Veracrypt are solutions to putting an added layer of security to a personal machine.
MALWARE Detection and Removal
Phishing, social engineering and other terms come to mind when we think of malware being installed maliciously onto a computer or into a system.
Malicious links can result in a system getting hacked with Ransomware, for which the hacker demands a high fee to remove. Ransom ware can be removed through doing a System restore at a time 48 hours or so before the computer was infected in Safe Mode.
ClamAV and Malwarebytes are excellent free software packages for detecting and removing malicious software.
VPN (Virtual Private Networks)
A VPN offers an added layer of security and masking for patrons who wish to browse privately. VPN send data through a series of servers masking traffic’s origin. These software programs may not be installed on library computers, however a patron visiting with their own machine may have this option within the limitations of the library. Bitmask is a popular free VPN. Some paid services are considered even more secure.
OPERATING SYSTEMS (OS)
GNU/Linux free and open source software operating systems such as Ubuntu, Debian and Open Suse offer top security and are most likely to be used by security professionals. These OS models are free, as in freedom, not free as in free beer. They serve to provide the user with maximum protection against State Surveillance. Additionally, public institutions may save on licensing fees through adopting these operating systems.
The Tails Linux distribution offers a TOR browser that may be plugged in as a USB drive and then removed, eliminating the need to install an entire Linux OS
Sources
Anon. Library Freedom Project – Making real the promise of intellectual freedom in libraries.. (2017). Libraryfreedomproject.org. Retrieved 24 October 2017, from https://libraryfreedomproject.org/
Anon. Privacy toolkit for librarians – Library Freedom Project. (2017). Libraryfreedomproject.org. Retrieved 24 October 2017, from https://libraryfreedomproject.org/resources-01/privacytoolkit/.
0 notes
Text
Tutti i servizi di Windows in inglese e in italiano - traduzione

Vi è mai capitato di perdere un sacco di tempo a cercare un servizio di Windows che conoscete benissimo in italiano su un'installazione in lingua inglese? E il contrario? Visto che a me capita in continuazione, ho pensato di realizzare la seguente tabella, mediante la quale è possibile individuare in pochi istanti la traduzione corretta. Oltre al Display Name in italiano e in inglese ho aggiunto anche lo Short Name di sistema, ovvero il nome univoco con cui il servizio è noto al sistema operativo. I servizi elencati sono quelli disponibili sulle principali versioni di Windows e Windows Server, con alcune mancanze che sto ancora cercando di colmare: se ne trovate qualcuno da aggiungere, sentitevi liberi di scrivere il nome in italiano e in inglese nei commenti a questo post, così provvederò ad aggiungerlo! Display name (in inglese) Nome del servizio Display name (in italiano) ActiveX Installer (AxInstSV) ActiveX Installer (AxInstSV) AxInstSV Adaptive Brightness Luminosità adattiva SensrSvc Application Experience Verifica compatibilità applicazioni AeLookupSvc Application Host Helper Service AppHostSvc Application Identity Identità applicazione AppIDSvc Application Information Informazioni applicazioni Appinfo Application Layer Gateway Service Servizio Gateway di livello applicazione ALG Application Management Gestione applicazione AppMgmt ASP.NET State Service aspnet_state Background Intelligent Transfer Service Servizio trasferimento intelligente in background BITS Base Filtering Engine BFE (Base Filtering Engine) BFE BitLocker Drive Encryption Service Servizio di crittografia unità BitLocker BDESVC Block Level Backup Engine Service Servizio modulo di backup a livello di blocco wbengine Bluetooth Support Service Servizio Supporto Tecnico Bluetooth bthserv BranchCache BranchCache PeerDistSvc Certificate Propagation Propagazione certificati CertPropSvc Client for NFS NfsClnt CNG Key Isolation Isolamento chiavi CNG KeyIso COM+ Event System COM+ Event System EventSystem COM+ System Application Applicazione di sistema COM+ COMSysApp Computer Browser Browser di computer Browser Credential Manager Gestione credenziali VaultSvc Cryptographic Services Servizi di crittografia CryptSvc DCOM Server Process Launcher Utilità di avvio processi server DCOM DcomLaunch Desktop Window Manager Session Manager Gestione sessione di Gestione finestre desktop UxSms DHCP Client Client DHCP Dhcp Diagnostic Policy Service Servizio Criteri di diagnostica DPS Diagnostic Service Host Host servizio di diagnostica WdiServiceHost Diagnostic System Host Host sistema di diagnostica WdiSystemHost Disk Defragmenter Utilità di deframmentazione dischi defragsvc Distributed Link Tracking Client Manutenzione collegamenti distribuiti client (anche: Distributed Link Tracking Client) TrkWks Distributed Transaction Coordinator Distributed Transaction Coordinator MSDTC DNS Client Client DNS Dnscache Encrypting File System (EFS) EFS (Encrypting File System) EFS Extensible Authentication Protocol Extensible Authentication Protocol EapHost Fax Fax Fax Function Discovery Provider Host Host provider di individuazione funzioni fdPHost Function Discovery Resource Publication Pubblicazione risorse per individuazione FDResPub Group Policy Client Client di Criteri di gruppo gpsvc Health Key and Certificate Management Gestione chiavi e certificati di integrità hkmsvc HomeGroup Listener Listener Gruppo Home HomeGroupListener HomeGroup Provider Provider Gruppo Home HomeGroupProvider Human Interface Device Access Accesso dispositivo Human Interface hidserv IIS Admin Service Amministrazione di IIS IISADMIN IKE and AuthIP IPsec Keying Modules Moduli di impostazione chiavi IPSec IKE e Auth-IP IKEEXT Indexing Service Servizio di indicizzazione CISVC Interactive Services Detection Rilevamento servizi interattivi UI0Detect Internet Connection Sharing (ICS) Condivisione connessione Internet (ICS) SharedAccess IP Helper Helper IP iphlpsvc IPsec Policy Agent Agente criteri IPsec PolicyAgent KtmRm for Distributed Transaction Coordinator KtmRm per Distributed Transaction Coordinator KtmRm Link-Layer Topology Discovery Mapper Mapper individuazione topologia livelli di collegamento lltdsvc LPD Service LPDSVC Media Center Extender Service Servizio Media Center Extender Mcx2Svc Message Queuing Message Queuing MSMQ Message Queuing Triggers Message Queuing Triggers MSMQTriggers Microsoft .NET Framework NGEN v2.0.50727 Microsoft .NET Framework NGEN v2.0.50727_X86 clr_optimization_v2.0.50727 Microsoft FTP Service ftpsvc Microsoft iSCSI Initiator Service Servizio iniziatore iSCSI Microsoft MSiSCSI Microsoft Software Shadow Copy Provider Provider di copie shadow software Microsoft swprv Multimedia Class Scheduler Utilità di pianificazione classi multimediali MMCSS Net.Msmq Listener Adapter NetMsmqActivator Net.Pipe Listener Adapter NetPipeActivator Net.Tcp Listener Adapter NetTcpActivator Net.Tcp Port Sharing Service Servizio di condivisione porte Net.Tcp NetTcpPortSharing Netlogon Accesso rete Netlogon Network Access Protection Agent Agente protezione accesso alla rete napagent Network Connections Connessioni di rete Netman Network List Service Servizio Elenco reti netprofm Network Location Awareness Riconoscimento presenza in rete NlaSvc Network Store Interface Service Servizio Interfaccia archivio di rete nsi Offline Files File non linea CscService Parental Controls Parental Controls WPCSvc Peer Name Resolution Protocol Protocollo PNRP PNRPsvc Peer Networking Grouping Gruppi reti peer p2psvc Peer Networking Identity Manager Gestione identità reti peer p2pimsvc Performance Logs & Alerts Avvisi e registri di prestazioni pla Plug and Play Plug and Play PlugPlay PnP-X IP Bus Enumerator Enumeratore bus IP PnP-X IPBusEnum PNRP Machine Name Publication Service Servizio di pubblicazione nome computer PNRP PNRPAutoReg Portable Device Enumerator Service Servizio enumeratore dispositivi mobili WPDBusEnum Power Alimentazione Power Print Spooler Spooler di stampa Spooler Problem Reports and Solutions Control Panel Support Segnalazioni di problemi e soluzioni nel Pannello di controllo wercplsupport Program Compatibility Assistant Service Servizio Risoluzione problemi compatibilità programmi PcaSvc Protected Storage Archiviazione protetta ProtectedStorage Quality Windows Audio Video Experience Servizio audio/video Windows di qualità QWAVE Remote Access Auto Connection Manager Auto Connection Manager di Accesso remoto RasAuto Remote Access Connection Manager Connection Manager di Accesso remoto RasMan Remote Desktop Configuration Configurazione Desktop remoto SessionEnv Remote Desktop Services Servizi Desktop remoto TermService Remote Desktop Services UserMode Port Redirector Redirector porta UserMode di Servizi Desktop remoto UmRdpService Remote Procedure Call (RPC) RPC (Remote Procedure Call) RpcSs Remote Procedure Call (RPC) Locator RPC Locator RpcLocator Remote Registry Registro di sistema remoto RemoteRegistry RIP Listener iprip Routing and Remote Access Routing e Accesso remoto RemoteAccess RPC Endpoint Mapper Agente mapping endpoint RPC RpcEptMapper SeaPort SeaPort Secondary Logon Accesso secondario seclogon Secure Socket Tunneling Protocol Service Servizio SSTP (Secure Socket Tunneling Protocol) SstpSvc Security Accounts Manager Sistema di gestione degli account di sicurezza (SAM) SamSs Security Center Centro sicurezza PC wscsvc Server Server LanmanServer Shell Hardware Detection Rilevamento hardware shell ShellHWDetection Simple TCP/IP Services simptcp Smart Card Smart Card SCardSvr Smart Card Removal Policy Criterio rimozione smart card SCPolicySvc SNMP Service SNMP SNMP Trap Trap SNMP SNMPTRAP Software Protection Protezione software sppsvc SPP Notification Service Servizio di notifica SPP sppuinotify SSDP Discovery Individuazione SSDP SSDPSRV Storage Service Servizio di archiviazione StorSvc Superfetch Ottimizzazione avvio SysMain System Event Notification Service Servizio di notifica eventi di sistema SENS Tablet PC Input Service Servizio di input Tablet PC TabletInputService Task Scheduler Utilità di pianificazione Schedule TCP/IP NetBIOS Helper Helper NetBIOS di TCP/IP lmhosts Telephony Telefonia TapiSrv Telnet TlntSvr Themes Temi Themes Thread Ordering Server Server di ordinamento thread THREADORDER TPM Base Services Servizi di base TPM TBS UPnP Device Host Host di dispositivi UPnP upnphost User Profile Service Servizio profili utente ProfSvc Virtual Disk Disco virtuale vds Volume Shadow Copy Copia shadow del volume VSS Web Management Service WMSVC WebClient WebClient WebClient Windows Audio Audio di Windows AudioSrv Windows Audio Endpoint Builder Generatore endpoint audio di Windows AudioEndpointBuilder Windows Backup Windows Backup SDRSVC Windows Biometric Service Servizio di biometria Windows WbioSrvc Windows CardSpace Windows CardSpace idsvc Windows Color System Sistema colori Windows WcsPlugInService Windows Connect Now – Config Registrar Windows Connect Now – Registro configurazioni wcncsvc Windows Defender Windows Defender WinDefend Windows Driver Foundation – User-mode Driver Framework Windows Driver Foundation – Framework driver modalità utente wudfsvc Windows Error Reporting Service Servizio Segnalazione errori Windows WerSvc Windows Event Collector Raccolta eventi Windows Wecsvc Windows Event Log Registro eventi di Windows EventLog Windows Firewall Windows Firewall MpsSvc Windows Font Cache Service Servizio cache tipi di carattere Windows FontCache Windows Image Acquisition (WIA) Acquisizione di immagini di Windows (WIA) StiSvc Windows Installer Windows Installer msiserver Windows Live Family Safety fsssvc Windows Management Instrumentation Strumentazione gestione Windows Winmgmt Windows Media Center Receiver Service Windows Media Center Receiver Service ehRecvr Windows Media Center Scheduler Service Windows Media Center Scheduler Service ehSched Windows Media Player Network Sharing Service Servizio di condivisione in rete Windows Media Player WMPNetworkSvc Windows Modules Installer Programma di installazione dei moduli di Windows TrustedInstaller Windows Presentation Foundation Font Cache 3.0.0.0 Cache tipi di carattere Windows Presentation Foundation 3.0.0.0 FontCache3.0.0.0 Windows Process Activation Service WAS Windows Remote Management (WS-Management) Gestione remota Windows (WS-Management) WinRM Windows Search Windows Search WSearch Windows Time Ora di Windows W32Time Windows Update Windows Update wuauserv WinHTTP Web Proxy Auto-Discovery Service Servizio rilevamento automatico proxy WinHTTP WinHttpAutoProxySvc Wired AutoConfig Configurazione automatica reti cablate dot3svc WLAN AutoConfig Configurazione automatica WLAN Wlansvc WMI Performance Adapter Scheda WMI Performance wmiApSrv Workstation Workstation LanmanWorkstation World Wide Web Publishing Service Servizio Pubblicazione sul Web W3SVC WWAN AutoConfig Configurazione automatica WWAN WwanSvc Read the full article
0 notes
Text
AOMEI Partition Assistant - Review and Test Drive

As you most likely already know, disk partitioning (also known as disk slicing) is the process of creating of one or more regions within a disk storage (such a HDD or SSD drive) so that each region can be managed separately. The disk stores the information about the partitions' locations and sizes in an area known as partition table, which is read by the system before any other part of the disk and - depending on what is found there - will determine what your PC will actually load on each boot: the operating system also reads the partition table before anything else, giving the user the chance to access the various regions (if they are formatted with a supported filesystem standard) to read and/or write stuff. The various "partitions" can be created using the operating system built-in tools or via third-party software - usually called partition editors, partition managers and so on: these tools can be used to create, resize, delete, and otherwise manipulate the partitions. The most widespread partition editor tools available in the past years are EaseUS Partition Master, Paragon Partition Manager and AOMEI Partition Assistant, which we'll be testing and reviewing in this article.
Standard and Professional
AOMEI Partition Assistant comes in two different versions: Standard (freeware) and Professional (trialware). Standard Features The standard version, which is free for personal use, comes with the following features: Basic Partition Management: Create, Format, Delete, Label, Check, Hide, Unhide Partitions, Set Active Partition, Change Drive Letter. Disk Partition Utilities: Rebuild MBR, Wipe Disk or Partition, Change Partition Type ID, Check Bad Sector. Change Partition Size: Extend, Shrink and Move Partitions, Merge Partitions or Unallocated Space Copy Data Disk & Partition Migrate OS from MBR Disk to MBR SSD or HDD Convert Data Disk between MBR and GPT Styles Convert File System between NTFS and FAT32 Create Windows PE Bootable CD/USB Professional Features The professional version covers all the standard stuff plus the following advanced features: Recover Lost or Deleted Partitions Copy System Disk from MBR to GPT, GPT to MBR and GPT to GPT Advanced Data Migration features: OS from GPT Disk to GPT/MBR SSD or HDD Advanced Convert features: System Disk between MBR and GPT; Dynamic Disk to Basic Disk (and Vice Versa); Partition Type between Primary and Logical Align Partition to Optimize SSD Performance Allocate Free Space from one Partition to another Extend Partition Wizard to Enlarge NTFS System Partition without the need of a reboot Advanced Partition Split features, such as spliting one large Partition into two or more smaller ones Command-Prompt mode, to be used within batch files and scripts Dynamic Disk Management: Resize, Move, Create, Format Dynamic Volumes SSD Secure Erase Wizard 24/7 VIP Technical Support Sector-level Data Protection AOMEI Partition Assistant embeds a proprietary sector-level data protection technology to ensure safer partitioning operations even with large drives (> 2 TB).
Supported OS, FS and Storage Devices
Both Standard and Professional versions supports the following: Operating Systems Windows 10 Windows 8.1/8 Windows 7 Windows Vista Windows XP Windows 2000 Pro SP4 File Systems NTFS FAT32/FAT16/FAT12 exFAT/ReFS * Ext2/Ext3/Ext4 * Bitlocker and other encrypted file systems * * These file system cannot be resized, but you can still move and clone them. Supported Storage Devices Traditional hard disk drives, solid-state drives (SSD) and SSHD, etc. (MBR disk and GPT disks) of any size External hard drives (USB drives), PC cards, all Flash Drives and Thumb Drives and other removable media All storage devices recognized by Windows, such as RAID, etc As for the maximum supported size, there seems to be no limit: we tested the Standard version against a 16 TB HDD and we got no issues.
Installation and EULA
The Standard Edition has an installer file of just 22 Megabytes with a typical installation wizard, which briefly mentions the Professional edition, giving you the chance to Try it now! but doesn't suggest or force anything else (no third-party software sponsored advices). Before running the program, you get the choice to Join the User Experience (UX) Improvement Program, which is the usual anonymous info-collecting feature used by most modern softwares to gather info regarding their end-users - hardware, usage, and so on. The Program is also briefly mentioned in the End-User Licence Agreement, which is indeed a good thing because they let you know what will be going on before accepting. Here's the relevant excerpt: In order to understand our user's needs, and deliver better products and services to our user, we invite you to join our User Experience Improvement Program. If you choose to join the program, you will not be interrupted by additional messages when using your computer, and the operation of the program will not decrease the performance of your computer. AOMEI collects anonymous information about your computer hardware configuration, how you use our products and problems you might have with our products. We respect your privacy. No personally identifiable information will be collected, like your name, address, phone number, or keyboard input. The program is voluntary. You can opt in/out the program at any time by checking/unchecking Menu » Settings » Other » Join the User Experience Improvement Program.
User Interface
The software comes with a easy-to-use interface, much similar to other AOMEI products. You are immediately prompted for the preferred language (we chose English among the 20+ supported ones) and then the main control screen will load:

As we can see, there's no introductory dashboard - we're immediately brought into action thansk to a full-featured control panel which already contains everything we can do. With a single click we can start to work on our partitions, migrate OS to SSD, start the recovery wizard, and so on. This is a great approach for practical people such as the vast majority of System Administrators - which are the ones that will actually use the product anyway. As you can see, some of the available Disk Operations do have an orange "Pro" label on them: it goes without saying that those will require the Professional version. Similarily, there are other features (such as the "Disk Backup") that do require other AOMEI products, such as AOMEI Backupper:

That's nice to know, but maybe it would've been better to place a label on them as well.
Overall Performances
During our test-drive we performed the following activities: Disk Partition on a 16 TB Hard-Disk Drive (create, split, merge and delete) Disk Copy from a 256GB SSD Drive to another identical 256GB SSD Drive. Wipe Hard Drive on that same 16 TB Hard-Disk Drive that we partitioned early on. Rebuild MBR from a damaged HDD with Windows 7 Home Premium. The software performed really well on each task, with no nag screen, no delays and better performances compared to the aforementioned competitors. We found nothing to complain about, therefore we can only praise the overall results. We also checked our Task Manager to analyze the impact on system resources during the various tasks, and we found no significant issues there as well: needless to say, the software will ask you to reboot to ensure that your Operating System will reckognize the changes, but it's not mandatory - as long as you can live with the partition misalingments.
Conclusion
AOMEI Partition Assistant is definitely a great free partition manager tool which we can recommend it for any personal use. If you plan to use it on your company or business activity, the fair price of the Professional version ($49.95 at the time of writing, with lifetime free upgrades included) makes it a highly affordable choice for every business size. Read the full article
0 notes