#C2Framework
Explore tagged Tumblr posts
Link

#reverse shell#RedTeaming#C2#PostExploitation#payloads#CobaltStrike#MITRE#ATT&CK#exploit#pentester#C2Framework#ProcessInjection#AVbypass#RAT
3 notes
·
View notes
Text
EvtMute - Filter Events Being Reported By Windows Event Logging
EvtMute - Apply A Filter To The Events Being Reported By Windows Event Logging #Apply #C2Framework #Event #Events
This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging. Usage Grap the latest verison from here. EvtMuteHook.dll contains the core functionality, once it is injected it will apply a temporary filter which will allow all events to be reported, this filter can be dynamically updated without having to reinject. I’ve written…

View On WordPress
1 note
·
View note
Photo

EvtMute – Filter Events Being Reported By Windows Event Logging | MrHacker.Co #apply #c2framework #event #events #evtmute #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
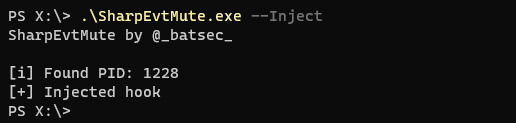
EvtMute – Filter Events Being Reported By Windows Event Logging | MrHacker.Co #apply #c2framework #event #events #evtmute #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo
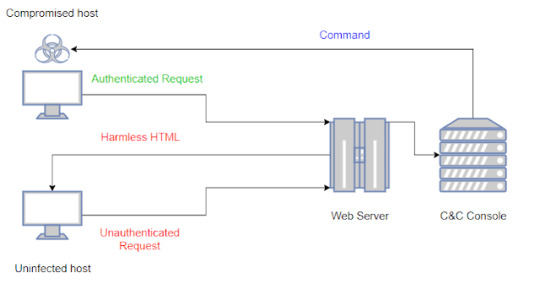
LOLBITS – C2 Framework That Uses Background Intelligent Transfer Service (BITS) #background #bits #c2framework #c2server #communication #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
LOLBITS - C2 Framework That Uses Background Intelligent Transfer Service (BITS)
LOLBITS - C2 Framework That Uses Background Intelligent Transfer Service (BITS) #Background #BITS #C2Framework
[sc name=”ad_1″]
LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS)to establish the communication channel between the compromised host and the backend. The C2 backend is hidden behind an apparently harmless flask web application and it’s only accesible when the HTTP requests received by the app contain a valid authentication header. Since this tool is…
View On WordPress
#Background#BITS#C2 Framework#C2 server#communication#Dinvoke#Direct#EDR#evasion#Flask Application#Framework#Hooking#Intelligent#LOLBITS#Netcat#Payload#PowerShell#protocol#python#python3#reverse shell#Service#Syscalls#Transfer#UserMode#v200#windows
0 notes