#CRISC Certification
Explore tagged Tumblr posts
Text
CRISC Certification: A Pathway to Leadership in IT Risk and Governance

In today’s rapidly changing technological landscape, managing IT risks effectively has become a top priority for organizations worldwide. With the increasing complexity of IT systems, the growing threats of cyberattacks, and the evolving regulatory landscape, businesses need professionals who can navigate these challenges with expertise and foresight. This is where the Certified in Risk and Information Systems Control (CRISC) certification comes in. Offered by ISACA, CRISC certification is specifically designed for professionals in the IT and risk management domains.
The CRISC certification is not only a validation of one’s skills in managing and mitigating IT risks but also serves as a powerful gateway to leadership roles in IT risk and governance. By acquiring this certification, professionals can open the door to a wide range of career advancement opportunities. In this blog, we will explore how CRISC certification can pave the way for leadership roles in IT risk management and governance.
What is CRISC Certification?
CRISC, or Certified in Risk and Information Systems Control, is a globally recognized certification offered by ISACA (Information Systems Audit and Control Association) that focuses on IT risk management and information systems control. It is designed for professionals who are responsible for managing, monitoring, and mitigating risks associated with information systems and technology.
The CRISC certification demonstrates that an individual has the knowledge and skills required to identify, assess, and manage IT risks, as well as to implement and monitor information systems controls. The certification is aimed at professionals working in roles related to risk management, IT governance, compliance, and cybersecurity, and it covers four key areas:
IT Risk Identification: Identifying and assessing risks that may affect IT systems and business operations.
IT Risk Assessment: Evaluating the potential impact and likelihood of identified risks.
Risk Response and Mitigation: Designing and implementing strategies to manage and mitigate risks.
Governance and Risk Management: Developing and managing risk management frameworks and ensuring alignment with business objectives.
With the growing importance of IT systems and the increasing threats posed by cyber risks, CRISC certification equips professionals with the skills to take on more senior and strategic roles in risk management and governance.
Why CRISC Certification is a Pathway to Leadership in IT Risk and Governance
Achieving CRISC certification provides professionals with the expertise and recognition needed to move into leadership positions within IT risk management and governance. Let’s explore how CRISC certification serves as a pathway to leadership roles:
Building Expertise in Risk Management
The CRISC certification ensures that professionals are well-versed in all aspects of IT risk management. In today’s organizations, leaders in IT risk management must have a comprehensive understanding of risk identification, assessment, response, and mitigation. CRISC training equips professionals with the skills to design, implement, and monitor risk management frameworks that safeguard the organization’s critical assets.
Aligning IT Risk with Business Objectives
One of the key aspects of effective IT risk management is ensuring that risk management practices are aligned with organizational goals. CRISC-certified professionals learn how to assess the business impact of IT risks and develop strategies that are aligned with the organization’s overall objectives. This ability to integrate IT risk management with business strategy is a crucial skill for leadership roles in risk and governance.
Enhancing Governance Practices
Good governance is essential for any organization to operate effectively and mitigate risks. The CRISC certification focuses heavily on governance frameworks and how they relate to IT risk management. Professionals with CRISC certification are equipped to oversee and implement governance practices that ensure risk management processes are consistent, transparent, and in line with industry standards.
Effective Communication and Leadership Skills
In any leadership role, the ability to communicate effectively with stakeholders, team members, and senior executives is essential. CRISC certification not only provides technical knowledge but also emphasizes the importance of communication skills. Professionals learn how to articulate complex risk-related issues in a way that is understandable to non-technical stakeholders, including board members, executives, and business leaders.
Advancing Cybersecurity and Compliance
Cybersecurity threats continue to grow in sophistication, and compliance with regulations such as GDPR, HIPAA, and SOX has become a critical aspect of business operations. CRISC certification provides professionals with the expertise to address cybersecurity risks, protect sensitive data, and ensure compliance with relevant laws and regulations.
Increasing Business Resilience and Continuity
One of the key responsibilities of IT risk leaders is ensuring business continuity in the face of potential disruptions, such as cyberattacks, natural disasters, or system failures. CRISC certification emphasizes the importance of business continuity planning and disaster recovery. By mastering these concepts, professionals can guide organizations in developing and implementing strategies that ensure resilience during disruptions.
How CRISC Certification Elevates Leadership Skills
While CRISC certification provides a deep understanding of risk management, it also cultivates key leadership skills that are essential for advancing in IT risk and governance roles. These include:
Strategic Thinking: The ability to think strategically and align risk management with business goals is crucial for leadership positions.
Problem-Solving: Effective leaders in IT risk management must be adept at identifying problems and implementing solutions to mitigate risks.
Decision-Making: CRISC-certified professionals are trained to make informed, data-driven decisions that protect the organization’s assets while supporting business objectives.
Stakeholder Management: Leaders must work closely with stakeholders to gain support for risk management initiatives and ensure that the organization is committed to protecting its IT systems.
Crisis Management: When disruptions occur, leaders need to guide the organization through the crisis while ensuring business continuity.
Conclusion
The CRISC certification is more than just a professional credential—it is a pathway to leadership in IT risk management and governance. By mastering the skills needed to identify, assess, and manage IT risks, as well as ensuring that risk management aligns with business goals, CRISC-certified professionals are poised to take on strategic leadership roles within their organizations.
At Unichrone, our CRISC certification training is designed to equip you with the knowledge and skills to excel in IT risk management and governance. Enroll today and take the first step toward advancing your career and becoming a leader in the IT risk management space.
0 notes
Text
What is CRISC Certification?
The Certified in Risk and Information Systems Control (CRISC) certification, offered by ISACA, is a globally recognized credential for IT professionals focused on enterprise risk management and control. CRISC certification demonstrates your expertise in identifying and managing risks, as well as implementing and maintaining information systems controls. Zoctech’s CRISC certification program is designed to provide you with the knowledge and skills needed to excel in this critical field.
Why Choose CRISC Certification? Global Recognition: CRISC is one of the most respected certifications in the IT risk management and control domain. It is recognized worldwide, enhancing your professional credibility and career prospects. In-Demand Skills: Organizations across all industries need professionals who can effectively manage IT risks and ensure robust information systems controls. CRISC certification equips you with these high-demand skills. Career Advancement: Achieving CRISC certification can open doors to senior-level positions in risk management, IT security, and control. It positions you as a valuable asset to any organization. Comprehensive Knowledge: The CRISC certification covers a wide range of topics, including risk identification, risk assessment, risk response and mitigation, risk and control monitoring, and reporting. This comprehensive knowledge prepares you to handle complex risk management challenges. Why Choose Zoctech for CRISC Certification? Experienced Instructors: Our CRISC certification program is led by industry experts with extensive experience in risk management and information systems control. They provide practical insights and real-world knowledge to enhance your learning experience. Comprehensive Curriculum: Our course covers all four domains of the CRISC certification exam: IT Risk Identification, IT Risk Assessment, Risk Response and Mitigation, and Risk and Control Monitoring and Reporting. Each module is designed to build your knowledge progressively. Hands-On Learning: We emphasize practical learning with hands-on exercises and real-world scenarios. This approach ensures you can apply theoretical knowledge to practical situations effectively. Flexible Learning Options: Zoctech offers flexible learning options, including online and in-person classes, to suit your schedule and learning preferences. You can choose the mode that best fits your needs. Exam Preparation Support: We provide comprehensive exam preparation support, including study materials, practice exams, and tips to help you succeed. Our goal is to ensure you are fully prepared to pass the CRISC certification exam on your first attempt. Career Opportunities with CRISC Certification Earning your CRISC certification opens up a wealth of career opportunities in various sectors. Some of the roles you can pursue include:
IT Risk Manager: Develop and implement risk management strategies to protect an organization’s IT assets. Information Systems Auditor: Evaluate the effectiveness of an organization’s information systems and controls. Security Manager: Oversee the security measures and protocols to safeguard an organization’s information systems. Compliance Manager: Ensure that an organization’s IT practices comply with relevant laws, regulations, and standards. Risk Consultant: Advise organizations on identifying, assessing, and managing IT risks effectively. Conclusion The CRISC certification is a valuable credential for IT professionals looking to advance their careers in risk management and control. Zoctech’s comprehensive CRISC certification program, led by experienced instructors, provides the knowledge, skills, and support needed to succeed. By enrolling in our program, you can enhance your professional credibility, gain in-demand skills, and open doors to senior-level positions in the IT industry. Start your journey towards becoming a Certified in Risk and Information Systems Control professional with Zoctech today.
#crisc certification#crisc certification training#crisc training and certification#crisc certification exam#crisc training#isaca crisc certification#crisc#prepare for crisc certification#isaca crisc training#isaca crisc benefits#isaca crisc certification exam#crisc certification training online#crisc exam#isaca crisc#crisc introduction#crisc certification requirements#crisc areas of focus#crisc benefits#introduction to crisc#know what is crisc#crisc questions#certification
0 notes
Text

Advance your career with Spoclearn's CRISC Certification Training in Australia. Designed for IT and risk management professionals, this comprehensive program covers key areas such as risk identification, assessment, response, and control monitoring. Gain the skills to manage enterprise IT risk and enhance your organization's risk management capabilities. Our expert-led training offers flexible learning options, including virtual classrooms and self-paced modules. Achieve your CRISC certification and stand out in the competitive field of IT risk management. Enroll with Spoclearn today and take the next step in your professional journey.
Spoclearn is a global training provider and corporate certification training company, offering a wide range of over 100 certification and non-certification courses across various domains including ITSM, Project Management, Agile and Scrum, DevOps, Quality Management, Cybersecurity, Digital Marketing, Microsoft Office, Data Science, AWS, and Development & Testing. We are dedicated to transforming human talent and fostering a learning culture that meets complex market demands. Our vision is to be the Single Point of Contact for Learning needs worldwide, aiming to equip individuals and enterprises with the knowledge and skills needed to thrive in a dynamic business landscape.
For More Information
Call Us • USA : +1 (908) 2937144 • India : +91 83417-05065 • UK : +44 1313813655
Email Us • [email protected]
Addresses • United States - 3500 South DuPont Highway Suite DK 101, Dover, DE 19901, United States • India - No.8/2, Novel Office Centre, Halasuru Rd, Bengaluru, 560042, KA, INDIA
0 notes
Link
[ad_1] Exam fee: US$575, members; US$760, non-members Why it’s on our list: CISA is a highly regarded certification with strong industry recognition. It appears frequently on industry lists, and 45,775 job postings explicitly seek candidates with this credential. With over 151,000 certified professionals, CISA offers a vast networking pool of auditors and security experts and an average salary of $155,362. Certified Information Systems Security Professional (CISSP) If CRISC and CISA represent specialty certifications for the midcareer analyst, CISSP is a generalist cert, a logical progression from Security+ for someone who’s been around for a while. Advanced-level analysts interested in getting CISSP certified will need to know all the ins and outs of security and risk management, asset security, operations, security assessment and testing, and more. Offered by ISC2, the CISSP certification requires five years of full-time experience in at least two of its eight domains. The exam is adaptive, ranging from 100 to 150 questions, including multiple-choice and drag-and-drop formats. Candidates who pass at 100 questions have demonstrated mastery across all domains. Exam fee: US$749 Training fees: US$248.75, online self-paced training; US$720, online instructor-led bootcamp; and learners can inquire for pricing details on instructor-led classroom training Why it’s on our list: If you’re looking for a job, earning a CISSP can help you stand out. With over 70,082 job postings explicitly seeking this certification and an average salary of $168,060, it ranks as the most in-demand security credential and is frequently highlighted on industry lists. “The certification I get questions about the most is the CISSP,” says Tim Bandos, CISO at Digital Guardian. “I do believe this certification is a hot one, given its reputation in the cybersecurity industry.” Beyond its career benefits, CISSP boasts a strong professional network of 91,765 certified professionals. It provides a broad foundation in cybersecurity, and professionals can further specialize within the ISC2 ecosystem through certifications such as the CCSP for cloud security. For more, see “CISSP certification: Requirements, training, exam, and cost.” Certified in Risk and Information Systems Control (CRISC) CRISC certification centers on risk analysis and management. Candidates need to know how to balance the likelihood of a risk happening against the potential damage that would ensue if it does. Overall, the goal is to help understand an organization’s tolerance for risk, categorize it, and quantify it. As ISACA, the organization that offers the cert, puts it, you’ll be aiming for a career where you “build a well-defined, agile risk-management program, based on best practices to identify, analyze, evaluate, assess, prioritize and respond to risks.” This is an area of security analysis that offers a promotion path to the top of the org chart — but it’s not for beginners, as CRISC requires three years of experience across two of four domains. The exam features 150 multiple-choice questions, testing IT risk management and control implementation skills. Exam fee: $50 application fee, $575 (ISACA members) / $760 (non-members) Training fee: ISACA offers four resources: online review course, US$895; annual subscription to question bank, US$399; print or digital review manual, US$139; discounts available for ISACA members Why it’s on our list: CRISC is the most cited certification focused explicitly on IT risk management and mitigation. Often pursued after CISA, CRISC commands the highest average salary among ISACA certifications at $165,890 and an average pay premium of 10%. With a strong community of 30,000 certified professionals, it is a top choice for those specializing in risk and control. For more, see “CRISC certification: Exam, requirements, training, potential salary.” Cisco Certified Network Professional (CCNP) Security Cisco offers a Cisco Certified Network Professional (CCNP) Security certification that focuses on security concepts and architecture, user and device security, network security, assurance, and cloud application management. While there are no prerequisites for the CCNP, in Cisco’s leveling professional-level certifications such as this one are meant to build on associate-level certifications. Cisco advises that most candidates in the certification have between three to five years of experience in network security. By demonstrating expertise with this credential, graduates can succeed in numerous roles, including security engineer, security analyst, and network security engineer. This certification is valid for three years and can be renewed by retaking the exam before its expiration or by taking continuing education credits. Training fees: Professionals can avail of instructor-led training from Cisco and accredited partners (prices vary), or a US$6,000 annual subscription to Cisco U All Access, which provides learning pathways for professional-level certifications. Exam fees: Professionals must take a core exam for US$400, plus one of seven exams for a concentration area for US$300. Why it’s on our list: As with AWS in cloud computing, Cisco is the undisputed leader in computer networking, holding an even greater market share at 76%. For security professionals seeking a vendor-specific certification in networking, Cisco certifications open doors. Additionally, Cisco offers a progressive learning curve: Professionals can start with an associate-level certification, such as the Cisco Certified Network Associate (CCNA) — which has a straightforward pass-or-fail exam — before advancing to the CCNP. Professionals with the CCNP earn an impressive average salary of $168,159. CompTIA Advanced Security Practitioner (CASP+) CompTIA’s Advanced Security Practitioner, which is being rebranded SecurityX, spans four domains: security architecture, operations, engineering and cryptography, and governance, risk, and compliance. The program is ideal for advanced cybersecurity professionals, such as senior security engineers or architects who wish to progress toward better lateral or vertical opportunities, including CISO. The current 165-minute exam, set to expire on CASP’s rebranding to SecurityX, consists of 90 multiple-choice and performance-based questions. Certificate holders must renew every three years with 75 continuing education units (CEUs) from CompTIA’s Continuing Education program. The certification carries a significant industry cache: It was developed in partnership with Target, GDIT, RICOH, and ExxonMobil and is approved by the Department of Defense to meet 8140.03M requirements. While there are no enforced prerequisites, CompTIA recommends 10 years of IT experience, with at least 5 years in security. Exam and training fees: US$509, exam; US$955, exam, study guide, exam practice, and retake; US$1,485, exam, study guide, exam practice, retake, and on-demand content and hands-on lab training Why it’s on our list: CASP+ recommends several certifications as prior experience, including Security+. Professionals can use Security+ as a stepping stone to CASP+, earning two blue-chip certifications in succession. Among CompTIA’s most respected credentials, CASP+ ranked as the second most frequently cited after Security+, highlighting its strong industry recognition. CompTIA Security+ The CompTIA Security+ certification teaches risk analysis and automation across five domains: security concepts, operations, architecture, program management, and threats, vulnerabilities, and mitigations. Numerous enterprises have contributed to the development of Security+, including Microsoft, Deloitte, and Zoom. The Security+ cert opens up varied opportunities, including network security analyst, penetration tester, and security architect. The 90-minute exam consists of a maximum of 90 multiple-choice and performance-based questions; candidates must score 750 on a scale of 900. Certificate holders must renew the cert by taking 50 CEUs through CompTIA’s Continuing Education program within three years. Note: CompTIA will likely retire the exam by 2026. Training and exam fees: US$404, exam; US$581, exam, retake, study guide; US$1,111, exam, retake, study guide, hands-on lab training, exam prep, e-learning Why it’s on our list: CompTIA Security+ is a highly respected cert, tying with ISACA’s CISM for the most mentions on industry lists. With 63,260 job postings explicitly seeking Security+ as a qualification and a large alumni base of 265,992 certified professionals — comparable to a large university — it provides strong job demand and a built-in professional network for career growth. For more, see “CompTIA Security+: Prerequisites, objectives, and cost.” GIAC Security Essentials (GSEC) The GIAC Security Essentials certification offers a curriculum comparable to CompTIA Security+. Topics covered include everything from cryptography and the cloud to incident handling and endpoint security. GSEC is suited for security administrators, forensic analysts, and penetration testers who have an IT background but need to validate their knowledge as a practitioner. Candidates must score 73% or more on the four-hour, 106-question exam, which can be administered with a proctor online or onsite. Professionals must take the 36 continuing professional education credits within four years to renew GSEC, a standard consistent for all GIAC certs. Training fees: On-demand and in-person options priced at local rates Exam fees: US$999; retakes, US$899 Why it’s on our list: GIAC is one of the most respected certifying bodies in cybersecurity, with 36,878 job listings explicitly seeking a Global Information Assurance Certification (GIAC). Out of all GIAC certifications, the GSEC certification was the most frequently cited. As a practitioner certification in the GIAC ecosystem, GSEC provides a strong knowledge base, making it an excellent starting point for a successful cybersecurity career. While not an official prerequisite, GSEC can also provide foundational knowledge for GIAC Cloud Security Automation (GCSA), GIAC Network Forensic Analyst (GNFA), and GIAC Reverse Engineering Malware (GREM), each of which offers an average pay premium of 10%. Offensive Security Certified Professional (OSCP+) To earn the OffSec Certified Professional certification, candidates must complete the affiliated course, Penetration Testing with Kali Linux, and pass the subsequent exam. The course covers 10 modules, including information gathering, vulnerability scanning, client-side attacks, and fixing exploits. Certificate holders will have shown mastery of penetration testing methodologies ideal for new roles, such as ethical hacker, incident responder, or threat hunter. The OSCP exam is hands-on; test-takers must compromise systems within a lab environment. OffSec does not enforce prerequisites but recommends candidates be familiar with TCP/IP networking, scripting in Bash and Python, and Linux and Windows, which they can learn through its Network Penetration Testing Essentials Learning Path. Training and exam fees: US$1,749, Kali Linux course plus exam Why it’s on the list: After the C|EH, OSCP+ was the second most frequently cited OffSec certification on industry lists. As of Nov. 1, 2024, OSCP was rebranded to OSCP+ to reflect a more rigorous exam format. The new 24-hour hands-on assessment requires candidates to exploit a vulnerability in a lab environment, followed by an additional 24 hours to submit a comprehensive penetration testing report. The exam also now includes an updated Active Directory (AD) section with an assumed compromise scenario. Penetration Testing with Kali Linux is also recommended preparation for PEN-300: Advanced Evasion Techniques and Breaching Defenses — one of three courses required for the Offensive Security Certified Expert (OSCE) certification, which offers an average pay premium of 11%. Systems Security Certified Practitioner (SSCP) The ISC(2) SSCP certification covers seven domains: security concepts, access control, incident response, cryptography, network security, systems and application security, and risk identification, monitoring, and analysis. It is ideal for various professionals, including security analysts, systems engineers, network analysts, database administrators, and security consultants. The three-hour exam consists of 125 multiple-choice questions; candidates must earn 700 out of 1,000 points to pass and undergo a process validating their professional experience. Those who earn the SSCP must abide by ISC(2) ‘s code of ethics and pay an annual maintenance fee that supports the organization and its initiatives, including its members-only network of cybersecurity pros. To qualify, the SSCP requires one year of experience. Those without the experience requirement can bypass it with a relevant undergraduate or graduate degree in computer science or a related subject. Training fees: Free, exam outline, flashcards, a practice quiz, and a study app; US$90 for 90-day access to on-demand training Exam fee: Varies by country (US$249 for candidates in North and South America) Why it’s on our list: SSCP is often featured on industry lists and is a strong foundation for those pursuing CISSP or CCSP. [ad_2] Source link
0 notes
Text
Djamgatech PRO: Ad-Free Certification Mastery
Unlock 100+ Professional Certifications with Premium Features
🚀 Why Upgrade to PRO?
✔ Zero Ads – Distraction-free studying
✔ Unlimited Tests – No daily limits
✔ Priority Support – Get expert help within 24 hours
✔ Advanced Analytics – Track performance across 20+ metrics
✔ 100+ Certifications – Expanded library including rare credentials
🔥 EXCLUSIVE PRO FEATURES
1. AI-Powered Study Assistant
Get personalized explanations in real-time
"Explain Like I’m 5" mode for complex concepts
2. 75+ Expert-Curated Study Paths
Structured 30/60/90-day plans for exams like:
AWS Specialty (Advanced Networking, Machine Learning)
CISSP Concentrations (ISSAP, ISSEP)
Niche Certs: CIPP/E, CRISC, OSCP
3. Premium Question Bank
15,000+ questions (vs. 5,000 in free version)
Includes simulated PBQs (AWS, Cisco, PMP)
4. On-Demand Tutoring (Add-On)
1:1 sessions with certified professionals
📊 CERTIFICATION COVERAGE
Cloud & DevOps
AWS (12 certs) | Google Cloud (9) | Azure (7) | Kubernetes (CKA, CKAD)
Cybersecurity
CISSP & Concentrations | OSCP | CEH | CCSP | CISM
Project Management
PMP | PgMP | PMI-ACP | PRINCE2 | Scrum Master
Finance & Law
CPA | CFA | FRM | CIPP/E | Patent Bar
Healthcare IT
CPC | CCS | RHIA | Epic Certifications
💎 PRO BENEFITS
✓ Download All Content – Study completely offline
✓ Unlimited Custom Quizzes – Focus on exact weak areas
✓ Early Access – New features 2 weeks before free tier
✓ Certificate Generator – Validate skills for employers
🔍 TOP SEARCH TERMS WE RANK FOR
"best ad-free aws certification app"
"premium pmp practice test 2024"
"cissp pro version with pbqs"
"unlimited cpa questions app"
"offline google cloud certification prep"
📈 USER RESULTS
"PRO's PBQs helped me pass AWS Solutions Architect in 3 weeks!" ★★★★★
"Worth every penny – the 90-day PMP plan got me certified first try." ★★★★★
"Finally, an app with CIPP/E materials!" ★★★★★
💰 SPECIAL LAUNCH OFFER
▶ 7-Day Free Trial – Cancel anytime
▶ 50% Off Annual Plan (Limited Time)
Download Djamgatech PRO Today – Your Career Upgrade Starts Here!
Try it FREE today: https://djamgatech.web.app
iOS download: https://apps.apple.com/ca/app/djamgatech-ai-cert-master/id1560083470
Android: https://play.google.com/store/apps/details?id=com.cloudeducation.free&hl=en_GB
Stay ready. Stay certified. #Djamgatech #AI #Certification #EdTech #CareerGrowth
0 notes
Text
10 Project Management Certifications to Lead Successful Projects in 2025

1. Project Management Professional (PMP)
The PMP certification, offered by the Project Management Institute (PMI), is one of the most recognized and respected credentials in the industry. It validates your ability to manage projects, lead teams, and deliver results. With a PMP certification, you demonstrate your expertise in project management methodologies and best practices.
2. Certified ScrumMaster (CSM)
For those focusing on Agile methodologies, the Certified ScrumMaster (CSM) certification is a must-have. Offered by the Scrum Alliance, this certification equips you with the skills to facilitate Agile teams and ensure successful project delivery. CSMs are in high demand, especially in software development and IT sectors.
3. PRINCE2 Practitioner
PRINCE2 (Projects IN Controlled Environments) is a widely adopted project management methodology. The PRINCE2 Practitioner certification, offered by AXELOS, is ideal for professionals looking to enhance their project management skills. It provides a structured approach to managing projects and is highly valued in both public and private sectors.
4. Certified Project Manager (CPM)

Explore AICERT’s wide range of AI certifications, and don’t forget to use the code NEWUSERS25 for a 25% discount on all courses. Click here to start your journey into AI Project Manager today!
“Have questions or are ready to take the next step in your AI certification journey? Reach out to us at AI CERTs — our team is here to guide you every step of the way!”
5. Agile Certified Practitioner (PMI-ACP)
The PMI Agile Certified Practitioner (PMI-ACP) certification is another credential offered by PMI. It focuses on Agile principles and practices, making it ideal for professionals working in Agile environments. The PMI-ACP certification demonstrates your ability to apply Agile methodologies to projects, ensuring flexibility and efficiency.
6. Certified Associate in Project Management (CAPM)
The Certified Associate in Project Management (CAPM) certification, also offered by PMI, is perfect for those starting their project management career. It provides a solid foundation in project management principles and practices. The CAPM certification is a stepping stone to more advanced credentials like the PMP.
7. Lean Six Sigma Green Belt
Lean Six Sigma is a methodology that combines Lean and Six Sigma principles to improve processes and eliminate waste. The Lean Six Sigma Green Belt certification is ideal for project managers looking to enhance their process improvement skills. It equips you with the tools to lead projects that drive efficiency and quality.
8. Certified in Risk and Information Systems Control (CRISC)
The Certified in Risk and Information Systems Control (CRISC) certification, offered by ISACA, is designed for professionals managing IT and business risks. It validates your ability to identify, assess, and manage risks, ensuring successful project outcomes. CRISC is highly valued in industries where risk management is critical.
9. Project Management in IT Security (PMITS)
The Project Management in IT Security (PMITS) certification, offered by the EC-Council, is tailored for professionals managing IT security projects. It covers essential project management concepts and practices specific to IT security. PMITS certification is ideal for those looking to lead projects in the cybersecurity domain.
10. Certified Construction Manager (CCM)

Conclusion
Earning a project management certification in 2025 can significantly boost your career and ensure you lead successful projects. Whether you are just starting or looking to advance your career, these certifications offer valuable skills and recognition in the industry. Choose the certification that aligns with your career goals and take the next step towards becoming a successful project manager.
0 notes
Text
CISM vs. Other Security Certifications: What Makes It Unique?
In today’s ever-evolving cybersecurity landscape, organizations are constantly seeking professionals with advanced skills to protect their data and infrastructure. Among the plethora of security certifications available, the Certified Information Security Manager (CISM) stands out as a highly sought-after credential for those aspiring to lead and manage information security programs. But what makes CISM Certification distinct from other popular certifications like CISSP, CISA, or CompTIA Security+? Let’s explore how CISM differentiates itself and why it might be the right choice for your career.
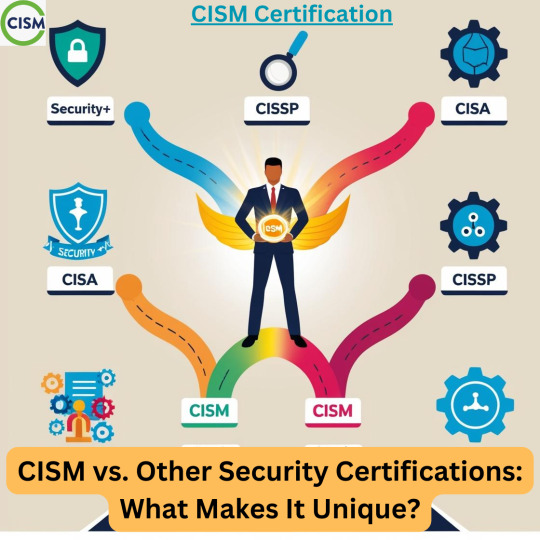
Understanding CISM: An Overview
Administered by ISACA, CISM is specifically designed for professionals focused on the management of enterprise information security. It emphasizes governance, risk management, compliance, and strategy rather than hands-on technical skills. This makes it ideal for mid-to-senior-level professionals aiming for roles such as information security manager, risk consultant, or CISO.
CISM validates expertise across four critical domains:
Information Security Governance: Aligning security initiatives with business goals.
Risk Management: Identifying, analyzing, and mitigating risks.
Information Security Program Development and Management: Designing and overseeing security programs.
Incident Management: Managing and responding to security incidents.
CISM vs. CISSP: Management vs. Technical Depth
One of the most common comparisons is between CISM and the Certified Information Systems Security Professional (CISSP), offered by (ISC)². While both certifications are highly regarded, they cater to different professional profiles.
CISM: Focuses on leadership and strategy. It’s tailored for those managing security teams, policies, and compliance at an enterprise level.
CISSP: A broader, more technical certification, covering topics like cryptography, security architecture, and network security. It’s often seen as ideal for hands-on practitioners such as security engineers or analysts.
In short, if your career goal involves overseeing security programs and aligning them with business objectives, CISM is the way to go. Conversely, CISSP suits those looking to excel in deeply technical roles.
CISM vs. CISA: Security vs. Audit
Another popular ISACA certification, the Certified Information Systems Auditor (CISA), focuses on auditing, control, and assurance. While CISM and CISA share some overlap, their core purposes differ significantly.
CISM: Prioritizes building and managing security frameworks to protect an organization’s assets.
CISA: Centers on evaluating and ensuring the effectiveness of those frameworks through audits.
Professionals working in security management gravitate toward CISM, whereas those in compliance and auditing often pursue CISA.
CISM vs. CompTIA Security+: A Question of Experience
The CompTIA Security+ certification is often considered a foundational credential for cybersecurity professionals. It covers basic concepts in risk management, network security, and cryptography. While Security+ provides an excellent entry point into the field, CISM is a much more advanced certification tailored for experienced professionals with at least five years of work experience in information security management.
In essence:
Security+: Ideal for beginners seeking a technical grounding in cybersecurity.
CISM: Designed for those looking to step into leadership roles.
CISM vs. CRISC: Security vs. Risk Management
The Certified in Risk and Information Systems Control (CRISC) certification, another ISACA offering, often overlaps with CISM when it comes to risk management. However, their primary focus areas differ:
CISM: Encompasses a broader scope, including governance, program development, and incident management, in addition to risk management.
CRISC: Specializes in enterprise risk management and mitigation, making it ideal for roles like risk manager or business continuity specialist.
If your career aligns more with security leadership, CISM is a better fit. For risk-centric roles, CRISC may be the superior option.
Why Choose CISM? The Unique Edge
1. What truly sets the CISM course apart is its emphasis on bridging the gap between technical cybersecurity measures and business strategy. Here’s why CISM is unique:
Business Alignment: Unlike purely technical certifications, CISM ensures that security practices are aligned with an organization’s broader goals, making it invaluable for decision-makers.
Global Recognition: With ISACA’s strong reputation, CISM is recognized worldwide, especially in industries like finance, healthcare, and technology.
Leadership-Centric Approach: The certification prepares professionals to lead teams, manage budgets, and communicate effectively with stakeholders.
Focus on Risk Management: Risk management is central to CISM, a vital skill for today’s threat landscape where risks must be proactively identified and mitigated.
High Demand for CISM Holders: Many organizations prioritize hiring CISM-certified professionals for roles like CISO and security program manager, as it demonstrates a blend of technical understanding and business acumen.
When to Choose CISM Over Other Certifications
CISM is ideal if you:
Have significant experience in cybersecurity and want to transition to a management or leadership role.
Are interested in policy creation, risk management, or strategic planning.
Aim to work closely with C-suite executives and board members to shape security strategies.
If you prefer a hands-on technical role or are new to cybersecurity, certifications like CISSP or Security+ might be more appropriate as a starting point.
Conclusion
Choosing the right certification is a pivotal step in shaping your cybersecurity career. While there are several excellent certifications available, CISM’s focus on leadership, risk management, and business alignment makes it a standout choice for professionals aspiring to lead security teams and align security programs with organizational objectives.
Ultimately, the best certification for you depends on your career goals, experience, and the type of role you envision. If you’re aiming for a managerial path with a focus on strategy and governance, CISM could be the key to unlocking your potential.
#CISM Certification#CISM Course#CISM Training#CISM#CISM Certified Professional#CISM Certified Benefits#CISSP
1 note
·
View note
Text








WhatsApp :- https://wa.link/08zn68 Hurry up Get 50% OFF 💯% passing guarantee and pay after pass exam Note: Booking with clearance available at best price WhatsApp :- https://wa.link/08zn68 Hello guys If are you interested in below certifications passing help WhatsApp :- https://wa.link/08zn68
PMP, PMI-ACP, CAPM, RMP
AWS
AZURE
GCP
COMPTIA SECURTIY
CISCO(CCNA,CCNP, CCIE)
TOGAF
ISACA ( CISA, CISM , CGEIT, CRISC)
PEGASYSTEM ( CSA, CSSA)
CBAP
CIA
EC COUNCIL (CEH V11/V12)
KUBERNETES( CKA & CKAD )
TERRAFORM
ISTQB
SCRUM MASTER / AGILE
SAFe WhatsApp :- https://wa.link/08zn68 and ALL IT Certification. please DM me WhatsApp :- https://wa.link/08zn68 💯% passing guarantee and pay after pass exam Note: Booking with clearance available at best price Hurry up Get 50% OFF
1 note
·
View note
Text
Achieve Six Figure Salaries with Cybersecurity Jobs
Want a lucrative career in cybersecurity? WiseCyberForce 365 offers a unique opportunity to secure multiple six-figure jobs in just 60-120 days, without the need for prior IT experience, coding skills, a degree, or additional certifications.

Why Enroll in WiseCyberForce 365?
Proven Methodology: Efficiently achieve your dream job through our reverse-engineered process.
GRC Training: In-depth Governance, Risk, and Compliance training for various jurisdictions.
Practical Experience: Hands-on training with real job scenarios.
Community Access: Join a network of cybersecurity professionals.
Professional Branding: Optimize your resume and LinkedIn profile.
Interview Preparation: Excel in interviews with our coaching.
Certification Training: Prepare for CISA and CRISC certifications.
Onboarding Assistance: Get support during your transition into a new role.
Ongoing Development: Continue to grow with additional professional development resources.
Transform Your Career with WiseCyberForce 365!
WiseCyberForce 365 LLC is dedicated to developing cybersecurity experts through effective training programs. We aim to be the leading provider of workforce development in cybersecurity, helping our mentees become valued professionals in the industry.
0 notes
Text
0 notes
Text
Protecting your brand in the age of AI - CyberTalk
New Post has been published on https://thedigitalinsider.com/protecting-your-brand-in-the-age-of-ai-cybertalk/
Protecting your brand in the age of AI - CyberTalk


Mark Dargin is an experienced security and network architect/leader. He is a Senior Strategic Security Advisor, advising Fortune 500 organizations for Optiv, the largest pure-play security risk advisory organization in North America. He is also an Information Security & Assurance instructor at Schoolcraft College in Michigan. Mark holds an MS degree in Business Information Technology from Walsh College and has had dozens of articles published in the computing press. He holds various active certifications, including the CRISC, CISSP, CCSP, PMP, GIAC GMON, GIAC, GNFA, Certified Blockchain Expert, and many other vendor related certifications.
In this timely and relevant interview, Senior Strategic Security Advisor for Optiv, Mark Dargin, shares insights into why organizations must elevate brand protection strategies, how to leverage AI for brand protection and how to protect a brand from AI-based threats. It’s all here!
1. For our audience members who are unfamiliar, perhaps share a bit about why this topic is of increasing relevance, please?
The internet is now the primary platform used for commerce. This makes it much easier for brand impersonators, and counterfeiters to achieve their goals. As a result, security and brand protection are essential. According to the U.S. Chamber of Commerce, counterfeiting of products costs the global economy over 500 billion each year.
Use of emerging technologies, such as artificial intelligence (AI) and deepfake videos — which are used to create brand impersonations — has increased significantly. This AI software can imitate exact designs and brand styles. Deepfake videos are also occasionally used to imitate a brand’s spokesperson and can lead to fraudulent endorsements.
Large language models (LLMs), such as ChatGPT, can also be used to automate phishing attacks that spoof well-known brands. I expect for phishing attacks that spoof brand names to increase significantly in sophistication and quantity over the next several years. It is essential to stay ahead of technological advancements for brand protection purposes.
2. How can artificial intelligence elevate brand protection/product security? What specific challenges does AI address that other technologies struggle with?
Performing manual investigations for brand protection can require a lot of time and resources to manage effectively. It can significantly increase the cost for an organization.
AI is revolutionizing brand protection by analyzing vast quantities of data, and identifying threats like online scams and counterfeit products. This allows brands to shift from reacting to threats to proactively safeguarding their reputation.
AI can increase the speed of identifying brand spoofing attacks and counterfeiting. Also, it can dramatically shorten the time from detection to enforcement by intelligently automating the review process and automatically offering a law enforcement recommendation.
For example, if a business can identify an online counterfeiter one month after the counterfeiter started selling counterfeit goods vs. six months later, then that can have a significant, positive impact on an organization’s revenue.
3. In your experience, what are the most common misconceptions or concerns that clients express regarding the integration of AI into brand protection strategies? How do you address these concerns?
If used correctly, AI can be very beneficial for organizations in running brand protection programs. AI technologies can help to track IP assets and identify infringers or copyright issues. It is important to note that AI is an excellent complement to, but cannot fully replace, human advisors.
There are concerns amongst security and brand protection leaders that AI will cause their investigative teams to rely solely on AI solutions vs. using human intuition. While tools are important, humans must also spend an adequate amount of time outside of the tools to identify bad actors, because AI tools are not going to catch everything. Also, staff must take the time to ensure that the information sent to the tool is correct and within the scope of what is required. The same goes for the configuration of settings. At a minimum, a quarterly review should be completed for any tools or solutions that are deployed.
Leaders must ensure that employees do not solely rely on AI-based tools and continue to use human intuition when analyzing data or identifying suspicious patterns or behaviors. Consistent reminders and training of employees can help aid in this ongoing process.
Training in identifying and reporting malicious use of the brand name and counterfeiting should be included for all employees. It is not just the security team that is responsible for protecting the brand; all employees should be part of this ongoing plan.
4. Can AI-based brand protection account for regional, local or otherwise business-specific nuances related to brand protection and product security? Ex. What if an organization offers slightly different products in different consumer markets?
Yes, AI brand protection solutions can account for these nuances. Many organizations in the same industry are working together to develop AI-based solutions to better protect their products. For example, Swift has announced two AI-based experiments, in collaboration with various member banks, to explore how AI could assist in combating cross-border payments fraud and save the industry billions in fraud-related costs.
We will continue to see organizations collaborate to develop industry-specific AI strategies for brand protection based on the different products and services offered. This is beneficial because attackers will, at times, target specific industries with similar tactics. Organizations need to account for this. Collaboration will help with protection measures, even in simply deciding on which protection measures to invest in most heavily.
5. Reflecting on your interactions with clients who are exploring AI solutions for brand protection, what are the key factors that influence their decision-making process? (ex. Budget, organizational culture, perceived ROI).
From my experience, the key factor that influences decision-making is the perceived return on investments (ROI). Once the benefits and ROI are explained to leaders, then it is less difficult to obtain a budget for investing in an AI brand protection solution. Many organizations are concerned about their brand name being used inappropriately on the dark web and this can hurt an organization’s reputation. Also, I have found that AI security solutions that can help aid an organization in achieving compliance with PCI, GDPR, HITRUST, etc., are more likely to receive approval and support from the board.
Building a culture of trust should not begin when change is being implemented; but rather in a much earlier phase of planning or deciding on which changes need to be made. If an organization has a culture that is not innovative, or leaders who do not train employees properly on using AI security tools or who are not transparent about the risks of it, then any investment in AI will face increased challenges.
AI’s high level of refinement means it can reduce the time and increase the scope of responsibility for individuals and teams performing investigations, enabling them to focus on other meaningful tasks. Investigations that were once mundane become more interesting due to the increased number of unique findings that AI is able to provide.
Due to the time saved by using AI in identifying attacks, investigators will have more time to pursue legal implications; ensuring that threat actors or brand impersonators are given legal warnings or charged with a crime. This can potentially discourage the recurrence of an attack from the specific source that receives the warning.
6. Could you share insights from your experience integrating AI technologies designed for brand protection into comprehensive cyber security frameworks? Lessons learned or recommendations for CISOs?
Security and brand protection leaders are seeing criminals use artificial intelligence to attack or impersonate brand names and they can stay ahead of those threats by operationalizing the NIST AI Risk Management Framework (AI RMF), and by mapping, measuring, and managing AI security risks. The fight moving forward in the future is AI vs AI. It is just as important to document and manage the risks of implementing AI as is to document the risk of attackers using AI to attack your brand name or products.
Leaders need to start preparing their workforce to see AI tools as an augmentation rather than substitution. Whether people realize it or not, AI is already a part of our daily lives, from social media, to smartphones, to spell check, to Google searches.
At this time, a task that was a challenge before can be done a lot faster and more efficiently with the help of AI. I am seeing more leaders who are motivated to educating security teams on the potential uses of AI for protecting the brand and in preventing brand-based spoofing attacks. I see this in the increased investments in AI-capable security solutions that they are making.
7. Would you like to speak to Optiv’s partnership with Check Point in relation to using AI-based technologies for brand protection/product security? The value there?
Attackers target brands from reputable companies because they are confident that these companies have a solid reputation for trustworthiness. Cyber criminals also know that it is difficult for companies, even large companies, to stop such brand impersonations by themselves, if they do not have appropriate tools to aid them.
Optiv and Check Point have had a strong partnership over many years. Check Point has a comprehensive set of AI solutions that I had the luxury of testing at the CPX event this year. Check Point offers a Zero-Phishing AI engine that can block potential brand spoofing attempts, which impersonate local and global brands across multiple languages and countries. It uses machine learning, natural language processing, and image processing to detect brand spoofing attempts. This provides security administrators with more time to focus on other security-related tasks or can alert them when something suspicious occurs within the environment.
The value in using AI solutions from vendors such as Check Point is the reduction in time spent detecting attacks and preventing attacks. In effect, this can empower organizations to focus on the business of increasing sales.
8. Can you share examples of KPIs/metrics that executives should track to measure the effectiveness of AI-powered brand protection initiatives and demonstrate ROI to stakeholders?
Generative AI projects concerning brand protection should be adaptable to specific threats that organizations may have within their environments at specific times. KPIs related to adaptability and customization might include the ease of fine-tuning models, or the adaptability of protection safeguards based on a specific input. The more customizable the generative AI project is, the better it can align with your specific protection needs, based on the assessed threats.
Organizations need to measure KPIs for the AI brand protection solutions that they have deployed. They should track how many attacks are prevented, how many are detected, and how many are successful. These reports should be reviewed on a monthly basis, at the least, and trends should be identified. For example, if successful attacks are increasing over a span of three months, that would be a concern. Or if you see the number of attacks attempted decreasing, that could also be something to look into. In such cases, consider investigating, as to ensure that your tools are still working correctly and not missing other attempted attacks.
9. In looking ahead, what emerging AI-driven technologies or advancements do you anticipate will reshape the landscape of brand protection and product security in the near future? How should organizations prepare? What recommendations are you giving to your clients?
Attackers will be increasing their use of AI to generate large-scale attacks. Organizations need to be prepared for these attacks by having the right policies, procedures, and tools in place to prevent or reduce the impact. Organizations should continually analyze the risk they face from AI brand impersonation attacks using NIST or other risk-based frameworks.
Security and brand leaders should perform a risk assessment before recommending specific tools or solutions to business units, because this will ensure you have the support needed for a successful deployment. It also increases the chance for approval of any unexpected expenses related to it.
I expect that there will be an increase in the collaboration between brands and AI-capable eCommerce platforms to jointly combat unauthorized selling and sharing of data and insights, leading to more effective enforcement. When it comes to brand protection, this will set the stage for more proactive and preventative approaches in the future, and I encourage more businesses to collaborate on these joint projects.
Blockchain technologies can complement AI in protecting brands, with their ability to provide security and transparent authentication. I expect that blockchain will be utilized more in the future in helping brands and consumers verify the legitimacy of a product.
10. Is there anything else that you would like to share with our executive-level audience?
As the issue of brand protection gains prominence, I expect that there will be regulatory changes and the establishment of global standards aimed at protecting brands and consumers from unauthorized reselling activities. Organizations need to stay on top of these changes, especially as the number of brand attacks and impersonations is expected to increase in the future. AI and the data behind it are going to continue to be important factors in protecting brand names and protecting businesses from brand-based spoofing attacks.
It is essential to embrace innovation and collaboration in brand protection and to ensure that authenticity and integrity prevail, given the various threats that organizations face. Let’s be clear that one solution will not solve all problems related to brand protection. Rather, the use of various technologies, along with human intuition, strong leadership, solid processes, and collaboratively created procedures are the keys to increased protection.
#ai#ai security#AI security tools#ai tools#AI-powered#America#amp#Articles#artificial#Artificial Intelligence#assessment#assets#attackers#authentication#billion#Blockchain#board#brand image#brand protection#brand spoofing#brands#Building#Business#CCSP#Certifications#challenge#change#chatGPT#Check Point#CISOs
0 notes
Text
Unveiling the CRISC Certification: Navigating Risk Management Excellence and Examining the Cost of CRISC Certification
Introduction:
In the ever-evolving landscape of information systems and technology, effective risk management has become a paramount concern for organizations. The Certified in Risk and Information Systems Control (CRISC) certification, offered by ISACA (Information Systems Audit and Control Association), has emerged as a gold standard for professionals seeking to enhance their expertise in risk management within the realm of information systems. This article delves into the key components of CRISC, the value it brings to the field of risk management, and a closer look at the costs associated with obtaining this prestigious certification.
Understanding CRISC:
Defining CRISC:
CRISC, short for Certified in Risk and Information Systems Control, is a specialized certification designed for professionals involved in managing and mitigating risks associated with information systems. It encompasses a comprehensive framework for identifying, assessing, and responding to risks in alignment with business objectives. Target Audience:
CRISC is tailored for a diverse range of professionals, including risk managers, IT professionals, business analysts, and compliance officers. It is particularly relevant for those responsible for ensuring that information systems align with organizational goals while effectively managing potential risks. Cost of CRISC Certification:
Exam Registration Fees:
The CRISC certification process begins with exam registration. As of my last knowledge update in January 2022, the cost for ISACA members is typically lower than for non-members. However, these fees can vary, and it is advisable to check the official ISACA website or contact them directly for the most current fee structure. ISACA Membership Fees:
ISACA membership is not mandatory for CRISC certification, but members often enjoy reduced exam fees. Membership benefits also include access to valuable resources, networking opportunities, and ongoing professional development. Membership fees are separate from exam fees. Training and Preparation Costs:
CRISC candidates often choose to undergo training and preparation courses to enhance their knowledge and readiness for the certification exam. These courses may be offered by ISACA or third-party providers, and their costs can vary. Exam Retake Fees:
In the event that a candidate does not pass the CRISC exam on the first attempt, there may be additional fees associated with exam retakes. It's essential for candidates to factor in potential retake costs when planning for the certification. Value of CRISC in Risk Management:
Holistic Risk Management Expertise:
CRISC equips professionals with a holistic understanding of risk management within the context of information systems. This expertise is invaluable for identifying, assessing, and responding to risks in a proactive and strategic manner. Alignment with Business Objectives:
CRISC-certified professionals are adept at aligning information systems with business objectives. This ensures that risk management strategies contribute directly to the achievement of organizational goals. Global Recognition:
CRISC is globally recognized as a mark of excellence in risk and information systems control. This recognition enhances the professional credibility of individuals and demonstrates a commitment to high standards in the field. Conclusion:
In the dynamic landscape of risk management, the CRISC certification stands as a beacon of excellence, providing professionals with the knowledge and skills needed to navigate the complexities of information systems risk. While there are costs associated with obtaining CRISC certification, the investment is justified by the enhanced expertise, industry recognition, and career advancement opportunities it brings. As organizations continue to prioritize effective risk management, CRISC-certified professionals play a pivotal role in safeguarding information systems and contributing to the overall success of their organizations.
0 notes
Text
The Premium ISACA CRISC & CISM Certification Training Bundle for $49
Expires October 10, 2024 06:59 PST Buy now and get 35% off ISACA Certified Information Security Manager (CISM) KEY FEATURES The Certified Information Security Manager (CISM) course, championed by the globally recognized ISACA, is a testament to excellence in the rapidly evolving realm of digital security. This course is not merely a pathway to certification – it’s an immersive experience into…

View On WordPress
0 notes
Text
Career in Cyber Security A to Z Guide

Career in Cyber Security: A profession in cyber security is a extraordinary preference for everyone who's interested by protective information and systems from cyber threats. Cyber safety is a booming enterprise that offers lots of roles and opportunities for growth. According to the United States Bureau of Labor Statistics, the variety of cybersecurity jobs is expected to boom by using 35 percent among 2021 and 2031.
Some of the common cybersecurity career paths are:
Engineering and architecture: This involves designing and implementing security systems and infrastructure to prevent and mitigate cyber attacks. You may work as a security engineer, security architect, or security consultant. You will need strong technical skills, such as programming, networking, system administration, and risk assessment. Some of the common certifications for this path are CompTIA Security+, Systems Security Certified Practitioner (SSCP), Certified Information Systems Security Professional (CISSP), and Google Professional Cloud Security Engineer. Incident response: This involves responding to and managing security incidents, such as breaches, malware infections, or denial-of-service attacks. You may work as an incident responder, forensic analyst, or malware analyst. You will need skills in digital forensics, malware analysis, threat intelligence, and incident management. Some of the common certifications for this path are GIAC Certified Intrusion Analyst (GCIA), GIAC Certified Incident Handler (GCIH), and GIAC Certified Forensic Analyst (GCFA). Management and administration: This involves overseeing and coordinating the security policies, procedures, and operations of an organization. You may work as a security manager, security administrator, or security auditor. You will need skills in leadership, communication, project management, compliance, and governance. Some of the common certifications for this path are Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA), and Certified in Risk and Information Systems Control (CRISC). To get started in cybersecurity, you will need to develop some core IT skills, such as programming, networks and systems administration, and cloud computing. You may also benefit from having some form of structured training or education in cybersecurity, such as a degree or a certificate program. The Microsoft Cybersecurity Analyst Professional Certificate is one example of a program that can help you prepare for an entry-level role as a cybersecurity analyst.
Read More: Queryiest Read the full article
0 notes
Text
CRISC - Certified in Risk and Information Systems Control
ISACA’s CRISC certification (Certified in Risk and Data Systems Management) is ideal for professionals in their mid-career, such as IT/IS audit, risk, and security. Register now for the latest CRISC exam to demonstrate your knowledge and abilities in victimization governance best practices, as well as ongoing risk monitoring and news.
0 notes