#DHCP Server
Explore tagged Tumblr posts
Text
Comprehensive Guide to Install DHCP Server on Windows Server
The DHCP Server service automates the configuration of TCP/IP on DHCP clients, providing essential information to computers when connecting to an IP network. In this Comprehensive Guide to Install DHCP Server on Windows Server 2022, we will discuss the post configuration as well as configuring the DHCP Scope. Please see how to create and delete a DHCP reservation in Windows Server 2019 and How to…

View On WordPress
#Configure DHCP Scope#DHCP#DHCP Options#DHCP Post Configuration#DHCP Scope#DHCP Server#Microsoft Windows#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
environmental storytelling (currently looking up wi-fi issues)

#i keep getting all sorts of wi-fi error messages. it's been like a year. i am TIRED#usually it's 'dhcp server isn't repsonding' or 'can't connect to dhcp server'#but sometimes it's 'the driver for your realtek <numbers and letters> isn't responding'#or 'your wi-fi is turned off' (no it isn't)#or some other random bullshit and it is driving me INSANE.#the connection is always dropping in and out and it's worse in some rooms than others but it seems to have#zero correlation with where my router actually is. it seems utterly arbitrary.#and it happens when I'm back at home too so it's almost definitely a me problem.#reddit says that that the WLAN adapter that comes with my type of computer (?) is just notoriously trash#so i'm trying to follow that lead before giving in and going to my bestbuy bestie about it.#he's so nice though. i was having phone issues over the summer and i posted about it when it happened but tldr#my phone model is old and needed a new battery that they didn't have anymore#so this one employee went and actually drove to the next bestbuy over to buy it from them to put in my phone#and it was a whole thing but he got it sorted out. god bless the people at (redacted town) best buy.#i feel like most of them would have gone 'idk. we don't have it. sorry' but my bestie david at bestbuy had my back 👏#i don't actually remember his name but I think it started with a D lol
4 notes
·
View notes
Text
Setting up a Raspberry Pi is always an adventure, and our latest project has been no exception! We've been diving deep into the world of network configuration, and after a bit of head-scratching (and a few "aha!" moments), we've made some significant progress in understanding how to get our Pi to share its internet connection.
Initially, like many, we fell into a common trap. Our goal was to share the internet connection from our Raspberry Pi, and our first thought was to assign a static IP address to wlan0 – the wireless interface. The logic seemed sound: wlan0 is how the Pi connects to the internet (via a hotspot, in our case), so surely that's where the magic needed to happen, right?
Not quite!
After some experimentation and a healthy dose of troubleshooting, we realized a crucial distinction. While wlan0 receives the internet connection, it's not the ideal interface for sharing it in the way we envisioned. Think of it this way: wlan0 is like the person receiving a package at the door. They've got the package, but they're not the ones distributing it to everyone else in the house.
This led us to eth0 – the trusty wired Ethernet port. And that's where the real breakthrough happened! We had a lightbulb moment: eth0 is perfectly suited for sharing the connection.
Here's why eth0 is our new best friend for internet sharing:
* Dedicated Connection: eth0 allows for a direct, dedicated connection to another device, like a router or even another computer. This is ideal for creating a stable and reliable shared network.
* Logical Separation: By using eth0 to share, we can keep the wlan0 interface focused on its primary job: connecting to the internet. This simplifies the network topology and makes it easier to manage.
* Foundation for a Robust Setup: With eth0 as our sharing interface, we can now configure it to act as a DHCP server, enable IP forwarding, and set up Network Address Translation (NAT). These are the essential ingredients for turning our Raspberry Pi into a powerful internet gateway.
So, what's the plan moving forward?
Our focus has now shifted to configuring eth0. We'll be looking at:
* Assigning a static IP address to eth0: This will be the gateway for any devices connected to it.
* Enabling IP forwarding: This is the key to telling the Pi to route traffic between our wlan0 internet source and our eth0 shared network.
* Setting up a DHCP server (like dnsmasq) on eth0: This will allow devices connected to eth0 to automatically get an IP address from our Pi.
* Configuring iptables for NAT: This crucial step will ensure that devices on our eth0 network can access the internet through our wlan0 connection.
This project has been a fantastic learning experience, highlighting the importance of understanding the fundamental roles of different network interfaces. We're excited to get eth0 fully configured and unlock the full potential of our Raspberry Pi as an internet sharing hub.
Stay tuned for more updates as we continue to build out this network!
- I used ai for this post.
0 notes
Text
morally it is sometimes okay to lie on your job application/resume/etc to get a job if you know you can do the work to do said job (i lied on mine about how good i am at excel, fuck pivot tables all to hell, ive watched nth youtube videos on those when i need them) but it's never hindered me from doing my job.
BUT MAN someone lied real big on their resume and application and she had her interview on Friday and it was such a hot mess. my boss asked her so many questions that she had zero answers to. What's DHCP, what's DNS (these aren't necessarily things that she should know, but she confidently stated to him she did know them but then couldn't tell him what they were, I was mopping the floor in the back and I could hear her voice raise and she was panicking and trying to laugh off the fact that she didn't know it, it was wild).
When asked how to enroll a user in Entra, she couldn't explain that process either despite her experience listing that she had enrolled users in Entra before (even I know how to do that by virtue of reading my coworkers' notes on the process).
My boss asked her if she had experience with firewalls, she confidently said yes and when he asked her what types, she told him "oh the standard ones".
There aren't really "standard" firewalls? I mean. People have their preferences. I know more about Fortigates because that's what we have at work and deploy to customers. (I don't deploy them, but I deal with their security service renewals so I know the ins and outs of that nonsense). But she couldn't even name one. Cisco. Checkpoint. WatchGuard. SonicWall.
When asked if she could stage a user on a desktop, she didn't really have a clear process for it, despite her resume saying she had 10+ years of workstation staging experience. This is a muddy question tho, we aren't looking for the process as much as, do you know how to set up a user in AD, do you know how to set up their email, do you know the basics? Do you know how to join a computer to the domain and things of that nature.
She didn't know the difference between Windows Home and Windows Pro.
Which, all of this was a huge red flag to my boss when he started questioning her. And like kudos to her for thinking she could somehow pull the wool over our eyes on this but??? We aren't like most IT companies, each tech has a very hands on job where you have to know that a computer needs to be upgraded to Windows Pro in order to be joined to the domain, you have to know how to add a user to Entra when an onboarding comes in, you should know to have DHCP set up on a server so it doesn't make things weird, and you can't just lie your way through it. You have to have the practical knowledge or you're going to be found out really really fast. (in this case 10 mins into the interview.)
Like 😩 if you don't know something then say you don't know it and move on. Don't lie.
2 notes
·
View notes
Text
Pi-Hole debug log
I'm thinking about writing up a nice guide so let me know if that would be useful to anyone but in the meantime, some notes about difficulties I ran into setting up a pi-hole
First off, I do want to say that this is actually pretty technically complicated? Like it's been floating around tumblr for a while, lots of people have done it, you can too, but when OP on that viral post said they took 2 hours and don't know anything, I think they mean they don't know anything in the same way I do (I have a whole degree in computers I have used a terminal before, but I hadn't used a raspberry pi before)
Rest below the cut
Gathering Materials Good news: there's lots of viable options for a raspberry pi that works with pihole! The minimal requirements are really very minimal. You need some computer that you're willing to devote to blocking your internet. (Theoretically you could do this on a computer also used for different stuff but that would suck and make you have no ram.) In practice, unless you've got a spare working laptop floating around for some reason, you are going to want that to be a raspberry pi. Bad news: now you have to make decisions. The "official" pihole kit has been sold out for ages, so that's not an option. I said fuck it and bought kit for the raspberry pi 4 off of one of the licensed distributors linked from raspberrypi.com (because it had all the requirements) but that was ~$100 with shipping and there ARE cheaper options. It looks like the raspberry pi zero barely hits the RAM requirements and is $15 at a licensed distributor so that's likely as low as you can go. And if you're not just buying a kit you'll need at a minimum a power supply, a microsd card (the pihole requirement is 4GB but everything I was seeing was way bigger anyways), and a way to read a microsd card (either a USB microsd reader or if your laptop already has an sd card reader you'll need one of those microsd to normal sd card converters which idk where you get but a USB microsd reader is very cheap). You don't need but may want an hdmi cable that will connect to the pi
Setting Up and Using a Raspberry Pi You may notice for notes that aren't a guide (yet) this is going into Great Detail about the early parts of the setup. As someone who hadn't used a raspberry pi before, I found all the pihole guides I was looking at skipped the basics I needed and most of my setup time was trying to figure out what was going on with my raspberry pi, not actually doing the pi-hole thing. The raspberry pi getting started page actually had all the information I needed in conjunction with their pihole setup guide if I'd read it thoroughly enough but since I didn't a general overview: first you plug the sd card into your personal computer to image it; then once it's imaged you take it out and put it in your raspberry pi; then after it's blinked at you a bit you ssh to your raspberry pi while on the same wifi network you just set up in the imaging step. This is running your raspberry pi "headless" which means you don't need a monitor/hdmi cable but does make it harder to debug if you can't ssh. Also if you're on windows apparently you NEED to download a different terminal because windows command prompt for all that it's gotten better over time cannot connect to unix operating systems (which raspbian is).
AT&T hates internet configuration Now we're getting to the part that's specific to me. My internet is on AT&T, which has overall been pretty okay (and they've had great technicians for setup and repair), but AT&T fiber does not let you set your own DNS. The non-annoying backup is to make the pi-hole your DHCP server instead of your DNS server, which IS in every setup guide but is NOT very detailed. (Possibly if I wasn't on AT&T this whole paragraph would be complaining about the level of detail of guides about making your pi-hole your DNS.) To get DHCP working, I found a different, slightly outdated guide from someone else on AT&T fiber which was pretty useful but had some pitfalls because it is a bit out of date: https://otter-security.com/how-to/ht_post/28/
Key points for setting up a pihole as DHCP server:

Set up your pihole normally/following the raspberry pi guide for the prompts
You still need to allocate a static IP for your pihole. For AT&T, this is on the IP allocation of the Home Network tab of the advanced settings page. That static IP should be the same as whatever the IP the IPv4 one the pihole install configured.
Disable DHCP on the subnets & DHCP tab. THIS IS THE STEP THAT BREAKS YOUR INTERNET: without DHCP available only some sites will work. This will be fixed by enabling DHCP on the pi-hole
Disable IPv6 (more about this later)
Enable DHCP on the pi-hole admin page: this is just a checkbox under settings->DHCP. The router ip address should be the one listed on the back of your router/the one used to get to the advanced settings (probably already correct)
Let all devices connect to the pi-hole under Settings->DNS on the pi-hole admin page (this is the step that was outdated or possibly just different because it was wired on the guide)

Don't You Forget About Mesh More details about my particular internet setup: we extend our internet with a mesh network. This kept getting in my way as I was doing the setup because I treat them largely interchangeably but it's important to put the raspberry pi and your computer on the SAME internet to do a local ssh, where the mesh vs the router are different here. I wanted to put the raspberry pi ssh on the router not the mesh because my initial setup attempt did break the mesh, but I'm not sure that that matters? Also I don't think anything connected to the mesh is getting the pihole filtering right now? Possible fixes required are either changing the mesh DNS to the pi-hole IP or seeing if the mesh has DHCP enabled.
IPv6: Still Broken So in the DHCP setup step I disabled IPv6. I couldn't get my DHCP to be forced to the pi-hole on IPv6 and I'm not sure why. I did set up my pi-hole to be IPv6 enabled and try disabling just IPv6 DHCP on my router, but it didn't seem to be hitting the pihole. Reading a help thread on this has convinced me that my best option is to leave it disabled until such a time as I want to learn things about networking again (a class I liked but also worked very hard to get a B in)
Why is my computer sad?? So I've declared pihole "working" in that our internet isn't broken and it's blocking at least some ads from some computers... but my mac is now giving ominous no internet connection warnings.

This would be a Big Problem except that I definitely can in fact reach the internet just fine. I'm on the internet right now! I don't know why my mac is sad and I am struggling to google it because it's specifically a false warning and I'm only getting results about the real problem. My hazy guess is it's ipv6 related? I could test this by disabling pihole/re-enabling DHCP on my router while keeping ipv6 off... but not in the middle of the day on a Friday
Adguard vs Pi-Hole: A Mystery Pi-Hole is no longer new technology and in the ~12 hours that it's been set up here hasn't made a dramatic difference in my life, mostly because I already had adblockers on my laptop. You can add more blocked sites and I've been looking at finding more adlists, but one alternate option is instead of running pi-hole on your raspberry pi, you run a commercial network level adblocker called AdGuard Home. I haven't tried the AdGuard option but it might do more comprehensive blocking? On the downside, it's commercial, not open source, so I do worry about them switching to break your internet if you don't give them money...
#mostly notes to self#I've been writing docs for work so suddenly my personal notes got detailed but you will need to click through to a real guide to use this#what is a blog for if not just putting your technical notes on the internet#computing things#pihole
4 notes
·
View notes
Text
diy router update
installed the pihole software. its working fine. finally have adblocking back on the things i cant easily change the dns server for. (i had the dns server on my old router set to nextdns but the new router doesn't have the option to change the dns server)
all the configuration files i worked so hard on for dnsmasq are not neciecery anymore because of pihole's built in dhcp server but thats fine i needed to get everything working under the most basic configuration possible before i started making things more complicated.
still gotta sort out that slow wifi issue. the slow ethernet is fine its basicly at the limit of my switch anyway, but the wifi is far slower than it should be.
3 notes
·
View notes
Text
The public IP address displayed below, also known as 'my IP,' is visible to the outside world. Depending on your connection type, you may have an IPv4, an IPv6 or both. If you are behind a router, the IP shown is your router’s public IP, while your device receives a private IP from a DHCP server. To answer 'What Is My IP,' this tool reveals your network’s external identity. https://proxyv6.net/what-is-my-ip/
2 notes
·
View notes
Text
fuck it i'm gonna buy a new router and i'm gonna wait to get a modem another time. it should still work if i force the xfinity box to just work as the modem and then i can set the pi to be dhcp server? i think.
and then i can set the whole network to route the dns requests through the pi and block all the ads
idk how well it'll work on youtube ads which is what i really want it for because it seems like a good bit of them are actually hosted the same place as the video so it's not a separate dns address and won't get blocked but even if it reduces the frequency while i watch youtube on my tv i'll be happy with it
2 notes
·
View notes
Text
Microsoft broke DHCP for Windows Server last Patch Tuesday
http://securitytc.com/TLQYBD
0 notes
Text
diy router update:
finally got it to assign ip addresses to wifi! the problem was that for some reason the wifi adapter on the computer had no ip address therefore nothing could use it. this might be because i was trying to have second ethernet and wifi on the same subnet and apparently that might not be allowed? i sure hope i can find a way around that. networking between computers on different subnets is complicated.
but now nothing can connect to the internet. but now that ive figured out how to fix the problem that was causing it to not work i can go back to the first thing i was trying and set it up again. i was trying a different dhcp server today. its more complicated but it's error messages are more verbose as well. i might even be able to try the pihole software again and use it's built in dhcp server instead.
2 notes
·
View notes
Text
I tried setting this up but my router doesn’t support custom dns servers, so I just allocated all the DHCP adresses to the pihole computer. It does break a few things, like the espn app, but reddit always has the domain to whitelist

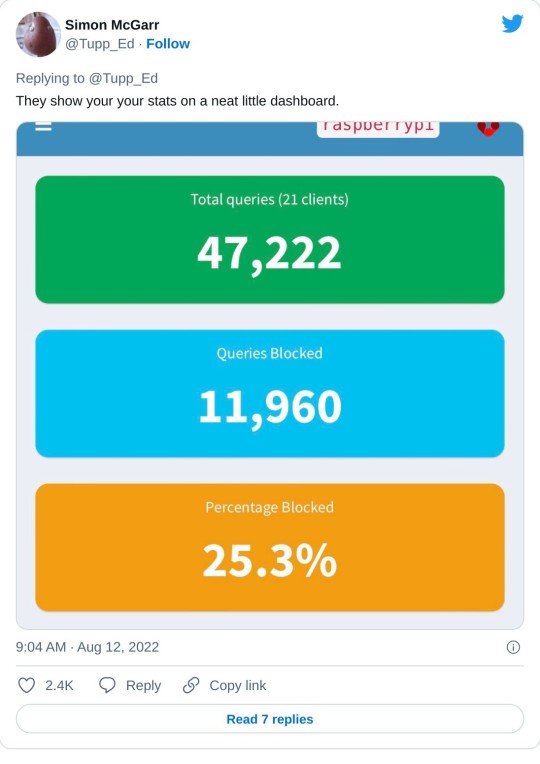
>First, we’ve discovered that about a quarter of all the internet connection in or out of the house were ad related. In a few hours, that’s about 10,000 out of 40,000 processed.
>We also discovered that every link on Twitter was blocked. This was solved by whitelisting the https://t.co domain.
>Once out browsing the Web, everything is loading pretty much instantly. It turns out most of that Page Loading malarkey we’ve been accustomed to is related to sites running auctions to sell Ad space to show you before the page loads. All gone now.
>We then found that the Samsung TV (which I really like) is very fond of yapping all about itself to Samsung HQ. All stopped now. No sign of any breakages in its function, so I’m happy enough with that.
>The primary source of distress came from the habitual Lemmings player in the house, who found they could no longer watch ads to build up their in-app gold. A workaround is being considered for this.
>The next ambition is to advance the Ad blocking so that it seamlessly removed YouTube Ads. This is the subject of ongoing research, and tinkering continues. All in all, a very successful experiment.
>Certainly this exceeds my equivalent childhood project of disassembling and assembling our rotary dial telephone. A project whose only utility was finding out how to make the phone ring when nobody was calling.
>Update: All4 on the telly appears not to have any ads any more. Goodbye Arnold Clarke!
>Lemmings problem now solved.
>Can confirm, after small tests, that RTÉ Player ads are now gone and the player on the phone is now just delivering swift, ad free streams at first click.
>Some queries along the lines of “Are you not stealing the internet?” Firstly, this is my network, so I may set it up as I please (or, you know, my son can do it and I can give him a stupid thumbs up in response). But there is a wider question, based on the ads=internet model.
>I’m afraid I passed the You Wouldn’t Download A Car point back when I first installed ad-blocking plug-ins on a browser. But consider my chatty TV. Individual consumer choice is not the method of addressing pervasive commercial surveillance.
>Should I feel morally obliged not to mute the TV when the ads come on? No, this is a standing tension- a clash of interests. But I think my interest in my family not being under intrusive or covert surveillance at home is superior to the ad company’s wish to profile them.

>Aside: 24 hours of Pi Hole stats suggests that Samsung TVs are very chatty. 14,170 chats a day.
>YouTube blocking seems difficult, as the ads usually come from the same domain as the videos. Haven’t tried it, but all of the content can also be delivered from a no-cookies version of the YouTube domain, which doesn’t have the ads. I have asked my son to poke at that idea.
205K notes
·
View notes
Text
Understanding 10.24.1.53: A Deep Dive

In the digital world, IP addresses play a crucial role in how devices communicate with each other. One such IP address, 10.24.1.53, often appears in private networks—but what exactly does it mean, and why is it important? This blog breaks it down for beginners and tech enthusiasts alike.
What is 10.24.1.53? The IP address 10.24.1.53 falls under the private IP range (10.0.0.0 to 10.255.255.255) as defined by the Internet Assigned Numbers Authority (IANA). This means it’s not routable on the public internet and is typically used for internal networking within homes, businesses, or organizations.
Why is it Used? Private IP addresses like 10.24.1.53 are used for devices within a local area network (LAN) to communicate with each other securely without accessing the internet. Routers assign these IPs through DHCP (Dynamic Host Configuration Protocol) to enable seamless connectivity.
Benefits of Private IPs
Enhanced network security
Conserves public IP address space
Simplifies internal communications
Cost-effective networking
Common Uses of 10.24.1.53 You might find 10.24.1.53 in use for:
Office printers
Internal servers
Smart devices in homes
Admin consoles for routers and switches
Conclusion Understanding IP addresses like 10.24.1.53 is essential for managing secure and efficient local networks. Whether you're a system admin or a curious user, knowing how these addresses function can enhance your grasp of networking fundamentals.
0 notes
Text
Mastering Windows Server 2019 Administration: A Guide for IT Professionals
Windows Server 2019, Microsoft’s robust and versatile server operating system, has become a cornerstone for organizations across various industries. Released as an evolution of the popular Windows Server 2016, it brings a suite of powerful features aimed at improving security, efficiency, and ease of management. Effective Windows Server 2019 administration involves understanding its capabilities, configuring its key settings, and leveraging its tools to meet organizational needs. This article explores the essentials of Windows Server 2019 administration, covering crucial components, best practices, and tips to help administrators make the most of this powerful system.
Key Features of Windows Server 2019
Windows Server 2019 builds upon its predecessors with several new features designed to optimize performance and security in modern data centers. Here are a few highlights that make it a standout choice for administrators:
Hybrid Cloud Support: With Azure integration, Windows Server 2019 offers seamless hybrid capabilities that allow administrators to connect on-premises servers with cloud services. This provides flexibility in managing workloads and extends the reach of IT infrastructure beyond physical boundaries.
Enhanced Security: Security remains a core focus of Windows Server 2019, with advanced features like Shielded Virtual Machines, Windows Defender ATP, and enhanced threat detection through Windows Defender Exploit Guard. These tools help protect against modern cybersecurity threats while reducing system vulnerabilities.
Improved Hyper-Converged Infrastructure (HCI): The HCI improvements in Windows Server 2019 enable administrators to manage storage, networking, and compute resources within a unified infrastructure, simplifying the management of virtualized environments.
Linux Integration: In recognition of the growing presence of Linux in enterprise environments, Windows Server 2019 offers built-in support for Linux containers, which allows administrators to run Linux-based applications and tools directly on Windows Server.
Storage Migration Services: Migrating servers to a new OS can be challenging, especially when dealing with critical data. The Storage Migration Service in Windows Server 2019 makes it easier to move servers from older systems by automatically transferring files, shares, and security configurations.

Core Responsibilities of Windows Server 2019 Administrators
Effective Windows Server 2019 administration requires a combination of technical skills and a solid understanding of organizational needs. Below are some of the primary responsibilities for administrators.
1. Setting Up and Configuring Servers
Setting up Windows Server 2019 begins with proper installation, followed by configuring network settings, Active Directory (AD), and role-based access. Administrators need to define specific roles for each server, such as DNS, DHCP, or file servers, to ensure streamlined operations. They also configure AD Domain Services to manage networked resources and enable centralized user management.
2. User and Access Management
One of the most critical aspects of server administration is managing user accounts and permissions. Windows Server 2019 simplifies this process through Active Directory, where administrators can create, modify, and control access for users, groups, and devices within the network. Properly setting up permissions and implementing Group Policies ensures that users have the right access levels while protecting sensitive data.
3. Implementing Security Protocols
Windows Server 2019 includes multiple layers of security to safeguard data and network resources. Security features such as Windows Defender, Credential Guard, and Exploit Guard help protect against threats. Configuring firewall settings, setting up intrusion detection, and implementing multi-factor authentication are all part of a comprehensive security protocol for ensuring data integrity and preventing unauthorized access.
4. Monitoring and Maintaining Performance
Performance monitoring is an ongoing task for Windows Server administrators. Using built-in tools like Windows Performance Monitor and Task Manager, administrators can track CPU usage, memory, disk activity, and network performance. Windows Admin Center provides a centralized dashboard for monitoring server health and performance, allowing administrators to identify issues and bottlenecks before they impact users.
5. Managing Backup and Recovery
Data backup and recovery plans are crucial for any organization, especially when downtime can lead to significant financial losses. Windows Server 2019 provides administrators with robust tools like Windows Server Backup and Volume Shadow Copy Service to schedule regular backups. In case of data loss or corruption, these tools enable quick recovery of data, minimizing downtime and ensuring business continuity.
6. Implementing Virtualization and Containerization
With Hyper-V, Windows Server 2019 supports extensive virtualization capabilities, allowing administrators to run multiple virtual machines on a single physical server. This enables efficient use of hardware resources and reduces operational costs. Additionally, container support allows administrators to deploy applications in isolated environments, making it easier to manage dependencies and streamline deployment.
Best Practices for Windows Server 2019 Administration
To ensure smooth and efficient server management, administrators should follow these best practices:
Regular Patching and Updating: Regular updates help keep the system secure and enhance performance. Using Windows Update and Windows Server Update Services (WSUS) ensures that servers are protected with the latest security patches.
Monitor Log Files: Log files can provide valuable insights into system health, user activities, and security events. Regularly monitoring logs can help detect unauthorized access attempts and resolve issues before they escalate.
Automate Routine Tasks: Automation tools like PowerShell scripts allow administrators to streamline repetitive tasks, such as user account management and data backups, saving time and reducing human error.
Create a Disaster Recovery Plan: Having a well-documented disaster recovery plan is crucial. This should include steps for data recovery, server restoration, and emergency contact information.
Conclusion
Windows Server 2019 is a powerful platform that offers extensive capabilities for managing and securing enterprise IT environments. Effective administration requires a deep understanding of its features, from hybrid cloud support and virtualization to advanced security and user management. By mastering these core components, administrators can ensure their organization’s infrastructure is reliable, secure, and scalable.
Adopting best practices, such as regular patching, automation, and disaster recovery planning, will further enhance an administrator’s ability to manage the server environment effectively. As businesses continue to rely on digital resources, Windows Server 2019 administrators play a crucial role in ensuring that the backbone of these systems is well-managed, resilient, and prepared for the future.
0 notes
Text

If you are on mobile and hate that there are fewer good ad-blocking options, but you're willing to try something slightly more complicated, you can set up a **Pi-Hole** as your own **Domain Name Server** (DNS). DNS is how your computer translates a URL like analytics.carmax.com into 104.121.122.102 or whatever (we call this "resolving" the URL). Most DNS providers will resolve any URL that comes their way, but a Pi-Hole is a DNS that you control, and it's built to deliberately fail to resolve URLs for advertisers.
The steps are pretty simple:
Get a Raspberry Pi with enough horsepower to run the software (this kit is $110, but cheaper ones can still do the job)
Install the OS and software. I thought this would be a nightmare but the prompts are well written and mostly explain the consequences of what they're asking you to choose.
Configure your phone, laptop, etc. to use the Pi-Hole as their DNS when they're on your home Wi-Fi.
Optionally, go into your Wi-Fi router and have it make _everyone's_ DNS the Pi-Hole. (Super optionally: use the Pi for DHCP. I prefer not to do this.)
Once it's working, whenever your device tries to load an ad online, the web page will ask your local network "hey, where can I get a shitty ad ?" and your Pi Hole will reply "nah, don't worry about any of that, internet don't have no shitty ads no more."
I don't like ads
for anyone who doesn't know how to use tumblr without ads, the easiest way is to open firefox or whatever browser you use, download an adblocker extension, and log into tumblr through the browser. it will work on mobile as well. there are some other great extensions too like tumblr savior and xkit rewritten, but a basic ad blocker should work just fine :>
4K notes
·
View notes
Text
Hiring Entry-Level Cyber Talent? Start with CSA Certification
In today's increasingly digital landscape, the threat of cyberattacks looms larger than ever. Businesses of all sizes are grappling with sophisticated threats, making robust cybersecurity defenses not just a luxury, but a necessity. At the forefront of this defense are Security Operations Center (SOC), and the unsung heroes within them: SOC Analysts.
However, a critical challenge many organizations face is bridging the talent gap in cybersecurity. The demand for skilled professionals far outstrips the supply, particularly at the entry-level. This is where strategic hiring practices, coupled with valuable certifications like the Certified SOC Analyst (C|SA) certification, become paramount.
The Ever-Growing Need for SOC Analysts
The role of a SOC analyst is pivotal. They are the frontline defenders, tirelessly monitoring an organization's systems and networks for suspicious activity, detecting threats, and initiating rapid responses to mitigate potential damage. From analyzing logs and alerts to investigating incidents and implementing containment measures, their work is continuous and critical.
The job outlook for information security analysts, which includes SOC analysts, is incredibly strong. The U.S. Bureau of Labor Statistics projects a 33% growth from 2023 to 2033, a rate significantly faster than the average for all occupations. This translates to approximately 17,300 job openings each year, highlighting the immense demand for these professionals. As cyber threats evolve in sophistication and frequency, and as businesses increasingly embrace digital transformation and remote work, the need for skilled SOC analysts will only intensify.
What Does an Entry-Level SOC Analyst Do?
An entry-level SOC analyst, often referred to as a Tier 1 analyst, serves as the first line of defense within a Security Operations Center. Their primary responsibilities include:
Monitoring Security Alerts: Continuously observing security alerts generated by various systems such as SIEM (Security Information and Event Management), IDS/IPS (Intrusion Detection/Prevention Systems), and endpoint protection1 tools.
Initial Triage and Prioritization: Assessing the severity and legitimacy of alerts, distinguishing between false positives and genuine threats, and prioritizing them for further investigation.
Log Analysis: Examining logs from different sources (servers, workstations, network devices) to understand security events and identify indicators of compromise (IoCs).
Following Playbooks: Executing established procedures and playbooks for common security scenarios and incident response.
Documentation: Meticulously documenting findings, actions taken, and the progression of security incidents.
Escalation: Escalating confirmed or complex threats to higher-tier SOC analysts (Tier 2 or Tier 3) for deeper investigation and remediation.
While a bachelor's degree in computer science or a related field can be beneficial, it's not always a strict prerequisite for entry-level SOC roles. Many successful SOC analysts enter the field through dedicated cybersecurity courses, bootcamps, or relevant certifications.
Key Skills for Aspiring SOC Analysts
To excel as an entry-level SOC analyst, a combination of technical and soft skills is essential:
Technical Skills:
Network Fundamentals: A solid understanding of network protocols (TCP/IP, DNS, DHCP), network architecture, and common network devices (firewalls, routers).
Operating System Knowledge: Familiarity with various operating systems (Windows, Linux) and their security configurations.
Security Technologies: Practical knowledge of security tools like SIEM systems, intrusion detection/prevention systems (IDS/IPS), antivirus software, and vulnerability scanners.
Log Analysis: The ability to effectively analyze security logs from diverse sources to identify anomalies and malicious activities.
Incident Response Basics: Understanding the fundamental steps of incident response, including detection, containment, eradication, and recovery.
Threat Intelligence: An awareness of current cyber threats, attack methodologies, and indicators of compromise.
Basic Scripting (Optional but beneficial): Familiarity with scripting languages like Python can help automate tasks and analyze data more efficiently.
Soft Skills:
Analytical and Problem-Solving: The ability to think critically, analyze complex information, and identify root causes of security incidents.
Attention to Detail: Meticulousness in examining logs and alerts to avoid missing crucial details.
Communication: Clear and concise written and verbal communication skills to document incidents and collaborate with team members and other departments.
Adaptability: The cybersecurity landscape is constantly evolving, so the ability to learn new technologies and adapt to emerging threats is vital.
Teamwork: SOC operations are often a collaborative effort, requiring effective communication and coordination with colleagues.
The Value of SOC Certifications for Entry-Level Talent
For individuals looking to break into the cybersecurity field as a SOC analyst, and for employers seeking to identify qualified entry-level talent, SOC certifications play a crucial role. These certifications validate a candidate's foundational knowledge and practical skills, providing a standardized benchmark of competence.
While several certifications can aid an aspiring SOC analyst, the Certified SOC Analyst (C|SA) certification by EC-Council stands out as a strong starting point, particularly for those targeting Tier I and Tier II SOC roles.
Why CSA Certification is a Game-Changer for Entry-Level SOC Hiring
The Certified SOC Analyst (C|SA) certification is specifically engineered to equip current and aspiring SOC analysts with the proficiency needed to perform entry-level and intermediate-level operations. Here's why the C|SA certification is a significant asset for hiring entry-level cyber talent:
Tailored for SOC Operations: Unlike broader cybersecurity certifications, C|SA is designed with the explicit needs of a Security Operations Center in mind. Its curriculum covers the end-to-end SOC workflow, from initial alert monitoring to incident response and reporting.
Comprehensive Skill Development: The C|SA program delves into critical areas such as:
Security Operations and Management: Understanding the principles and practices of managing a SOC.
Understanding Cyber Threats, IoCs, and Attack Methodology: Gaining knowledge of common cyber threats, indicators of compromise, and attack techniques.
Incidents, Events, and Logging: Learning about log management, correlation, and the significance of various security events.
Incident Detection with SIEM: Mastering the use of Security Information and Event Management (SIEM) solutions for effective incident detection.
Enhanced Incident Detection with Threat Intelligence: Integrating threat intelligence feeds into SIEM for proactive threat identification.
Elaborate Understanding of SIEM Deployment: Gaining practical insights into deploying and configuring SIEM solutions.
Hands-On, Practical Learning: The C|SA program emphasizes practical skills through lab-intensive sessions. Candidates get hands-on experience with incident monitoring, detection, triaging, analysis, containment, eradication, recovery, and reporting. This practical exposure is invaluable for entry-level professionals who often lack real-world experience.
Real-time Environment Simulation: The labs in the C|SA program simulate real-time SOC environments, allowing candidates to practice identifying and validating intrusion attempts using SIEM solutions and threat intelligence, mirroring actual job scenarios.
Compliance with Industry Frameworks: The C|SA certification aligns 100% with the National Initiative for Cybersecurity Education (NICE) framework, specifically under the "Protect and Defend (PR)" category for the role of Cyber Defense Analysis (CDA). This alignment ensures that C|SA-certified individuals possess skills recognized and valued across the industry.
Global Recognition: Accredited by EC-Council, a globally recognized authority in cybersecurity certifications, the C|SA credential enhances career prospects and demonstrates proficiency to potential employers worldwide.
Clear Career Pathway: For aspiring SOC analyst professionals, the C|SA serves as the foundational step, providing them with the necessary skills and knowledge to enter a SOC team at Tier I or Tier II level. This creates a clear and achievable career path.
Beyond Certification: What Else to Look For
While the C|SA certification is an excellent indicator of a candidate's readiness for an entry-level SOC analyst role, employers should also consider other factors during the hiring process:
Passion and Curiosity: Cybersecurity is a rapidly evolving field. Look for candidates who demonstrate genuine enthusiasm for continuous learning and a strong desire to stay updated on the latest threats and technologies.
Problem-Solving Aptitude: Assess their ability to think critically and approach challenges systematically.
Communication Skills: Strong communication is vital for collaborating within the SOC team and explaining technical issues to non-technical stakeholders.
Any Relevant Experience: Even internships, personal projects, or volunteer work in cybersecurity can demonstrate practical application of skills.
Cultural Fit: A candidate's ability to integrate into the team dynamics and contribute positively to the SOC environment.
Conclusion
As the cybersecurity landscape continues to grow in complexity and threat sophistication, the demand for skilled SOC analysts will only intensify. For organizations seeking to build a robust and responsive security team, investing in entry-level talent is crucial. The Certified SOC Analyst (C|SA) certification offers a highly relevant and practical pathway for aspiring professionals to gain the necessary skills, making them a valuable asset from day one. By prioritizing candidates with foundational certifications like C|SA, employers can confidently onboard individuals who are not just theoretically knowledgeable, but also practically equipped to contribute to their security operations and safeguard their digital assets.
0 notes