#Decryption
Explore tagged Tumblr posts
Text
The Crystal Bill from Alex says: SPOILERS BELOW
PREPARE FOR HIS COMING (link to B&N)
The audio base is interstitial music from "Monty Python and the Holy Grail" - "Intermission (Neil Innes) (EMI 1975)".
(UPDATED) MORSE inside the music cracked by Reddit: THREE SIDES TO EVERY STORY THREE SIDES TO EV
The common saying Bill is referencing here is "There are three sides to every story: your side, my side, and the truth. "
#the book of bill promo#gravity falls#//LOOKS LIKE CODES ARE BACK ON THE MENU BOYS#decryption#bill cipher#the book of bill spoilers
54 notes
·
View notes
Text

19 notes
·
View notes
Text
"Smmv mbmxg tcuhmx qt uqtj zw ctbmqr znm zxczn,
0d 0a 66 6f 72 20 74 72 75 74 68 20 77 69 6c 6c 20 6e 6f 74 20 6f 6e 6c 79 20 6d 65 6e 64 20 79 6f 75 72 20 70 65 72 73 70 65 63 74 69 76 65 2c 20 62 75 74 20 61 6c 73 6f 20 72 65 73 68 61 70 65 20 79 6f 75 72 20 72 65 61 6c 69 74 79 2e 2e 2e 22"
- The Resurrected
@googlyeyedsilly @crossover-enthusiast @totally-not-a-tickle-blog @jbwashere @townbully-hatzroy @itsnotmourn @sunny6677 @lottie-dottie-gal @lolipoptheclown @jacenotjason @ericvelseb666 @eatyourmaker @yalibat
D̸̢̮̫̰̥̗̘̱͉͙͙̺̫̏͒̅̌ẹ̷͓̺̰̽̍͛̉̐̔͋̓̚͜️c̸̛͕̯͂̐̓͗͊͛͝ŕ̶̛̰̱̈́̀́̑̿̾͛͂̈́͗̓̈́̒͘͝️y̷̧̰̲͍̝̘̗̩̑̇͐̾̽̏͊͑̇̃̉͜p̸̢̻͓͎̻͙͂͒̋͒̓̃͊̐̔͘͝t̵̏͛̃̍́̈̚͜͝i̵̢̢̡͚̩̞̥͕̜̻̫̩̐̈͘͜o̶̯͎̱͐̇͋̅̃̈́͋̽̊̀̓͊̃́͋̓️ṉ̵͓̬͈̞̥̭̥̇̓̔͋ i̵̢̢̡͚̩̞̥͕̜̻̫̩̐̈͘͜️ş̵̛̳̍̃̏͆̏̂̎͌͘͝͝͝͝ k̵̨̪̖͇͙͎̜͊̌͘͜ẹ̷͓̺̰̽̍͛̉̐̔͋̓̚͜y̷̧̰̲͍̝̘̗̩̑̇͐̾̽̏͊͑̇̃̉͜
#decrypt this... and your find the answer#[He's still here...]#watching...#waiting...#observing...#creepy#codes#horror#scary#alternate universe#code#decryption#uneasiness#uneasy#decrypt#analog horror
40 notes
·
View notes
Text
Part 2/4? - Ford's Alternate Cipher
Cracking the Book of Bill!
Part 1 - Cosmic Cipher
I explain how I differentiated between different ciphers, and solved this one completely from scratch, without knowing any of the translations to guide me.
Spoilers Below!!!
Seperating the Ciphers
I wasn't completely sure this wasn't a double encryption of either Ford's or Bill's ciphers from Journal 3 at first. After translating all of those that I could, I began to notice that the letter frequency was off for both of them, symbols that were supposed to be very uncommon kept popping up multiple times per sentence. After pulling out my copy of Journal 3, I realized that this was a completely different Cipher, and I had always assumed it was double encrypted because it pulled symbols almost exclusively from Ford and Bill's ciphers!
Some uses of this cipher in the journal replaced what had been used in the show, and I could still remember the translations, and could use that to get nearly a third of the symbols at once. However, I promised a good old-fashioned decryption, and that you shall get.
Beginning Decryption
When breaking a code from scratch, there are 3 absolute pillars that I use.
1: Short words. If it's got two or three letters, it will make it easier to notice patterns between them and recognize vowels.
2: Single Letters: those are almost always I and A, and if you've got an unusual circumstance it's often very easy to set aside.
3: Letter Frequency. Is. God.

This shows how, even though not all letters are used, their rank in standard English and in the cipher is usually going to be pretty similar, almost all of them were within 2-3 places of their standard English counterparts.
I always start with letter frequency, and line my symbols up on the wall in order from most to least common. I went back through journal 3 to help me out, as mathematically the more data with a pattern you have, the less random it appears. One symbol appeared 81 times, another only once. If I was cracking on just one sentence, that'd be a lot harder to see.
Keeping an eye on the two symbols that were either I or A, I started grouping up and looking at the short words with very common letters.

The word in the middle was the most frequent of the 3-letter words, and the double-triangle and dotted-I appeared together pretty often. Comparing their frequency to the frequency of English letters, and other similar unknown words, I could be confident this was the word: "THE" and underneath it was "HE" The mushroom symbol had to be some sort of vowel, and even before T i was guessing these were the words "TO" and "TOO."
I went back to the source material to look for shorter words comprised primarily of these letters, and found "TH_T," the blank being one of the symbols that was either I or A. By making "THAT" I now had the letters T, H, E, O, A, and I, some of the most frequent. From there, it became fill in the blank.
the same symbol appeared in "_OT THAT" and at the end of a longer word "TIO_." Filling in N was enough to guess the entirety of Dipper's taunt to Bill, with some consultation to the other uses of the symbols "I _AN __ITE _O_ES TOO ITS NOT THAT HA__" became "I CAN WRITE CODES TOO ITS NOT THAT HARD!"
(ouch dipper, right in my pride)
Filling in "WHATS _ICTION AND _HATS REA_" gained me L and W, and "RE_E__ER _S" was filled in to give me M, B, and U.
the last ones gave me K, Y, and G, from the sentence "SHAKE YOUR GRANDMA," and P from "FORGET THE PAST"

Even though this cipher has been used before, it was new to me and the perfect one to demonstrate my decryption method! I can probably comb back through the journal for some of the uncommon letters. Hope you enjoyed, and check out the one I did that was unique to The Book Of Bill
#book of bill#the billble#buy bills book#bill cipher#gravity falls#buy the book of bill#gravity falls bill#stanford pines#ciphers#decryption#gravity falls spoilers#book of bill spoilers#spoilers#journal 3#gravity falls dipper#dipper pines#gravity falls journal
15 notes
·
View notes
Text
Look all I'm gonna say about CX-2 is he has more screen time this season than Echo.
I really struggle to believe he won't pop back up in the finale. Probably as Tech. Maybe not. But he's definitely not just gone, not anymore than those other CXes are (one of whom could easily be Wolffe).
#star wars#the bad batch#tbb tech#I would deeply prefer Tech be in a box#on ice#the M-count transfer attempt#but like I think the writing is#on the wall#'who are you' 'domicile'#ship sig scrambling#standing on the wall in that spot#waterfall flop#decryption#staring at Phee
25 notes
·
View notes
Text
Oh yes ah baby ooh misappropriate my funds harder baby

#beat em up#dog girl#Mustard gravy#Kentfield#knives chau#defect#von herder#decryption#defective turret
3 notes
·
View notes
Text
Matrix Breakout: 2 Morpheus
Hello everyone, it's been a while. :)

Haven't been posting much recently as I haven't really done anything noteworthy- I've just been working on methodologies for different types of penetration tests, nothing interesting enough to write about!
However, I have my methodologies largely covered now and so I'll have the time to do things again. There are a few things I want to look into, particularly binary exploit development and OS level security vulnerabilities, but as a bit of a breather I decided to root Morpheus from VulnHub.
It is rated as medium to hard, however I don't feel there's any real difficulty to it at all.
Initial Foothold
Run the standard nmap scans and 3 open ports will be discovered:
Port 22: SSH
Port 80: HTTP
Port 31337: Elite
I began with the web server listening at port 80.

The landing page is the only page offered- directory enumeration isn't possible as requests to pages just time out. However, there is the hint to "Follow the White Rabbit", along with an image of a rabbit on the page. Inspecting the image of the rabbit led to a hint in the image name- p0rt_31337.png. Would never have rooted this machine if I'd known how unrealistic and CTF-like it was. *sigh*
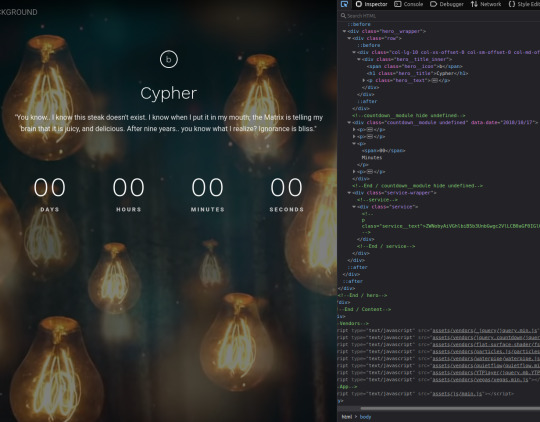
The above is the landing page of the web server listening at port 31337, along with the page's source code. There's a commented out paragraph with a base64 encoded string inside.
The string as it is cannot be decoded, however the part beyond the plus sign can be- it decodes to 'Cypher.matrix'.

This is a file on the web server at port 31337 and visiting it triggers a download. Open the file in a text editor and see this voodoo:
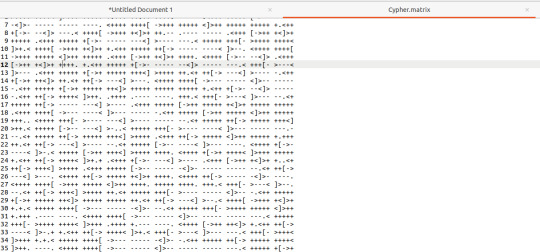
Upon seeing the ciphertext, I was immediately reminded of JSFuck. However, it seemed to include additional characters. It took me a little while of looking around before I came across this cipher identifier.

I'd never heard of Brainfuck, but I was confident this was going to be the in-use encryption cipher due to the similarity in name to JSFuck. So, I brainfucked the cipher and voila, plaintext. :P
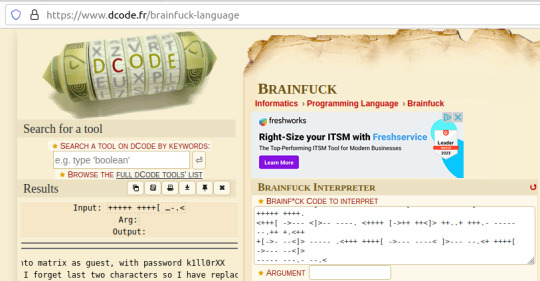
Here, we are given a username and a majority of the password for accessing SSH apart from the last two character that were 'forgotten'.
I used this as an excuse to use some Python- it's been a while and it was a simple script to create. I used the itertools and string modules.
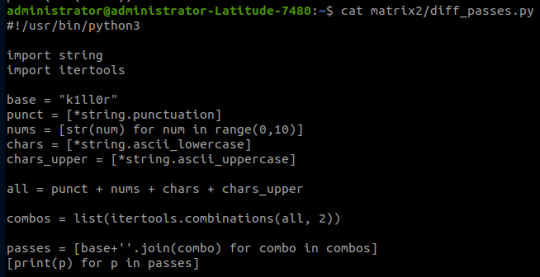
The script generates a password file with the base password 'k1ll0r' along with every possible 2-character combination appended. I simply piped the output into a text file and then ran hydra.
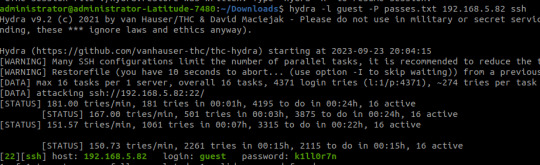
The password is eventually revealed to be 'k1ll0r7n'. Surely enough this grants access to SSH; we are put into an rbash shell with no other shells immediately available. It didn't take me long to discover how to bypass this- I searched 'rbash escape' and came across this helpful cheatsheet from PSJoshi. Surely enough, the first suggested command worked:

The t flag is used to force tty allocation, needed for programs that require user input. The "bash --noprofile" argument will cause bash to be run; it will be in the exec channel rather than the shell channel, thus the need to force tty allocation.
Privilege Escalation
With access to Bash commands now, it is revealed that we have sudo access to everything, making privilege escalation trivial- the same rbash shell is created, but this time bash is directly available.

Thoughts
I did enjoy working on Morpheus- the CTF element of it was fun, and I've never came across rbash before so that was new.
However, it certainly did not live up to the given rating of medium to hard. I'm honestly not sure why it was given such a high rating as the decoding and decryption elements are trivial to overcome if you have a foundational knowledge of hacking and there is alot of information on bypassing rbash.
It also wasn't realistic in any way, really, and the skills required are not going to be quite as relevant in real-world penetration testing (except from the decoding element!)
#brainfuck#decryption#decoding#base64#CTF#vulnhub#cybersecurity#hacking#rbash#matrix#morpheus#cypher
9 notes
·
View notes
Text
My feelings are encrypted in my head but he knows how to decrypt them, put them in words and make it easy for me to understand myself.

1 note
·
View note
Text
Ransomware Response Procedures
Ransomware is a type of malicious software that encrypts your files and demands a ransom to restore them. It can cause serious damage to your data, your privacy and your finances. If you discover that your computer has ransomware, you need to act quickly and follow these 10 steps: Disconnect your computer from the internet and any other devices. This will prevent the ransomware from spreading to…
View On WordPress
3 notes
·
View notes
Text
Review: Before Bletchley Park – The Codebreakers of The First World War – by Paul Gannon
I have previously read a lot of material on World War 2 codebreakers and the likes of Alan Turing and their critical work against Enigma and the invention of modern computing during that period. Of course, codebreaking and cryptography is not a new science and has been a critical part of both war and diplomacy since ancient times and has only increased in significance as time progresses. World…

View On WordPress
#aircraft war#Alan Turing#Allies#America#Atlantic#Bletchley Park#Britain#British Navy#cables#Caesar cipher#codebreaking#compuers#crossword#cryptanalysis#cryptography#cybersecurity#decryption#Enigma#ENigma Machine#Four Four Cyber#gchq#Geran codebooks#german#German military#German Navy#Germany#Horseguards Parade#israel#Italian#Kaiser
5 notes
·
View notes
Text
//I MIGHT be seeing things but I don't think we should rule out rune cipher in this image just yet. Look closely at the grass at the bottom of the image.
Like I said I MIGHT be seeing things but I thought I saw a bow tie there in the leaves... which might be a marker to other code characters nearby.

32 notes
·
View notes
Text
Cryptography is a method used to secure communication and information between two parties by encrypting it using keys so that only the sender and intended receiver can read and comprehend the message. This ensures the confidentiality, integrity, and security of digital data from unauthorized users, often known as adversaries.
0 notes
Text
"IkZvciB0aGUgVmVzc2VsIG9mIExpZ2h0IGhhcyB0cmFuc2Zvcm1lZCBtZSw=
R hszoo iveviv rg, vevm ru rg ivjfrivh nb ldm hzxirurxv..."
- The Resurrected
Part 1
@googlyeyedsilly @crossover-enthusiast @totally-not-a-tickle-blog @jbwashere @townbully-hatzroy @itsnotmourn @sunny6677 @lottie-dottie-gal @lolipoptheclown @jacenotjason @ericvelseb666 @eatyourmaker @yalibat
#creepy#codes#horror#scary#alternate universe#code#decryption#uneasiness#uneasy#decrypt#analog horror
10 notes
·
View notes
Text
Part 1/4? - The Cosmic Symbol Cipher
Cracking the Book of Bill!
Translations for all uses Part 2 - Ford's Alternate Cipher
Spoilers below, in perpetuity.
Alright welcome to the hyperfixation station I'm about to special interest all over the place, let's get started.
The book of Bill contains at least 4 distinct symbol ciphers, perhaps more. I'll be starting out with what I've decided to call the Cosmic Cipher

Mainly because so many of the symbols look like stars, moons, and zodiac signs to me.
So far I've found 22 distinct symbols, and I think this will be relatively easy. My first clue was a inscription on a tree matching up one of the symbols to equal A. However, I think I'll be able to do about 8 more symbols right away.

See it?

How about now?
Doubt it's coincidence, because even though letter frequency isn't going to be needed much here, they're aligning well. (Ex. The symbol I matched to B is much less frequent then the one corresponding to H)
With 9/22 symbols marked down, the others are just a matter of filling in the blanks.

For the inscription on the inside cover, the arrow has been super common, and is definitely the letter S. I'm guessing the other two would then be V and N, coming out to "EVEN HIS LIES ARE LIES." Appropriate, considering the contents of this book.

RE__RN spells out RETURN pretty clearly to me, and making the word on the end T_ has to be the word TO. "I_ LOST RETURN TO BILL" Based on the contents of the page, it's probably "I'M LOST", so I'll hesitantly mark that down for later to double check.
AHA! I've found the true M!

The page mentioned Optometrists, so I'm much more confident in this one. All the other vowels are taken, so the triple triangle has to be the Y. Full sentence has to be "MY OPTOMETRIST NEVER SAW IT COMING"
3 symbols left, the much more rare ones. Now knowing that it can't be M, the partially completed sentence from earlier must be "IF LOST RETURN TO BILL"
The two last symbols will be X, Q, Z, J, K, or D. They're both annoyingly part of names, but thankfully at least two of them are normal.

And here we are folks :)

Click here to see all the uses in The Book of Bill Translated!
#book of bill#the billble#buy bills book#bill cipher#gravity falls#buy the book of bill#gravity falls bill#stanford pines#ciphers#decryption#gravity falls spoilers#book of bill spoilers#spoilers
14 notes
·
View notes
