#DoubleSpend
Explore tagged Tumblr posts
Text
Blockchain Bites: Clearing the Record on Yellen's Crypto Concerns and the Bitcoin Double-Spend Fracas
Blockchain Bites: Clearing the Record on Yellen’s Crypto Concerns and the Bitcoin Double-Spend Fracas
After dropping 13% yesterday, bitcoin is once again on the ascent. Meanwhile, Janet Yellen has offered a more nuanced view of crypto and small Ethereum mining pools are organizing a campaign against a potential network upgrade. Top shelf Miners revolt!Eight Ethereum mining pools amounting to around 30% of the network’s hash power have formed a quasi-cartel to push back against a proposed…

View On WordPress
0 notes
Photo

BCH Backer Claims Bitcoin Wallet Double-Spend Issue Hasn’t Been Fixed On July 2, crypto security firm ZenGo identified a double-spend exploit targeting several popular Bitcoin (
0 notes
Text
Organized ATM fraud, 112 double-spend transactions resulted in a loss of $195,000.
Organized ATM fraud, 112 double-spend transactions resulted in a loss of $195,000.
[ad_1]

Organized ATM fraud, 112 double-spend transactions resulted in a loss of $195,000.
[ad_2] View Reddit by transisto – View Source
View On WordPress
#Articles#ATM#ATM serine/threonine kinase#Automated teller machine#Business Finance#Crimes#doublespend#economy#Embedded systems#Entertainment Culture#Fraud#Loss#Organized#Payment systems#Property crimes#resulted#Tort law#transactions
0 notes
Text
Calvin is wrong, Nchain cannot prevent a split, all they can could do is doublespend (steal) thereby decreasing the value/utility of BCH. This is a permissionless network, even i could split tomorrow and theres not a damn thing craig could do (except 51 attack like BTG)
Calvin is wrong, Nchain cannot prevent a split, all they can could do is doublespend (steal) thereby decreasing the value/utility of BCH. This is a permissionless network, even i could split tomorrow and theres not a damn thing craig could do (except 51 attack like BTG)
[ad_1]

Calvin is wrong, Nchain cannot prevent a split, all they can could do is doublespend (steal) thereby decreasing the value/utility of BCH. This is a permissionless network, even i could split tomorrow and theres not a damn thing craig could do (except 51 attack like BTG)
[ad_2] View Reddit by millerbitcoincash – View Source
View On WordPress
#Attack#BCH#BTG#Calvin#Craig#damn#decreasing#DoubleSpend#nChain#Network#permissionless#Prevent#split#steal#tomorrow#valueutility#Wrong
0 notes
Text
The Double-Spend (What Bitcoin's White Paper Solved Forever)
The Double-Spend (What Bitcoin’s White Paper Solved Forever)
[ad_1]
Bill Barhydt is the founder and CEO of Abra.
This exclusive opinion piece is part of CoinDesk’s “Bitcoin at 10: The Satoshi White Paper” series.
I remember reading Satoshi Nakamoto’s bitcoin white paper for the first time a few weeks after it was released. I also remember the phrase that really grabbed my attention:
“We propose a solution to the double-spending problem using a…
View On WordPress
0 notes
Photo

Security Firm Identifies Potential Tether (USDT) Double-Spend Bug #BTC, #XRP, #DOGE, #LTC, #ETH, #Bitcoin, #Ripple, #Cryptocurrency SlowMist, a Chinese cybersecurity firm, has recently pointed out a transaction that should have some worried, as the user managed to double the value of 694 USDT.
0 notes
Text
ZenCash Suffers Suspected 51% Double-Spend Attack
ZenCash Suffers Suspected 51% Double-Spend Attack
[ad_1]
ZenCash is the latest cryptocurrency to suffer a suspected 51% attack in the last two months. Others like Electroneum, Verge, and Bitcoin Gold have also fallen victim to the 51% percent attack – the number one scourge of the poorly secured public blockchain network.
Details of the Attack
According to a reporton the ZenCash blog, the attack occurred in the early hours (GMT) on June 3,…
View On WordPress
0 notes
Text
Cryptocurrencies (3/3)
What sort of security issues do we have?
Due to the distributed nature of cryptocurrencies, we have to consider the security in a number of different areas and from a couple of different angles. In terms of looking at historical flaws and their relative impacts, I would classify them under 3 main categories:
Blockchain itself - vulnerabilities relating specifically to the implementation of the blockchain (so in the nodes, mining, etc)
51% attacks (i.e. ETC 2019)
DDoS
Doublespend (i.e. The Finney attack)
Exchanges and wallets
Phishing
Bad hashes (i.e. IOTA)
Software bugs in cryptocurrency wallets
Software bugs in cryptocurrency exchanges
Client malware (i.e. changing address in clipboard)
Smart contracts - complexity of smart contract languages leading to bugs or poorly designed contracts (i.e. TheDAO)
As per the seminar, I will summarise a specific example of each of these categories.
Blockchain - 51% Attack
How does it work?
If you read my (1/3) article on cryptocurrencies, you will understand the process of mining in PoW and how multiple chains can form. Essentially, what we have happening in this attack is we have a miner (corrupted) with a large portion of the hash power deciding not to broadcast the block to the network when he as found a valid hash for the block. He will then continue to mine on his own chain in stealth; the original chain will continue to be built by other miners.
The corrupted miner will then spend all the bitcoin that he owns on the public chain, however he will choose NOT to do the same on his own secret chain. He will then continue to mine blocks on his own chain; however since he has majority hash power he will be producing blocks at a greater rate than the main chain. After a while he will choose to broadcast his chain to the rest of the Bitcoin network - the democratic governance process of the network enforces that the ‘longest chain’ is the correct one and the protocol will force the nodes to switch to the corrupted miner’s chain. This miner is then able to spend his bitcoins (that he spent earlier) all over again - this is why it is also referred to as a double-spend attack.
What security mechanisms are in place against it?
The main thing defending against a 51% attack is the sheer amount of resources required to perform it - on larger networks such as Bitcoin you need approximately $12.5 billion dollars worth of hardware which will cost you $8.6 million dollars per day to run in order to perform this attack. (from this site) This makes the risk associated with the costs in electricity, hardware and government prosecution not worth the reward of the attack.
Exchanges - Mt Gox
What happened in the first hack in 2011?
The computer of Mt Gox’s auditor was compromised which they then used to access the exchange and artificially modify the traded value of bitcoin down to 1 cent (i.e. by selling all the bitcoin from all the accounts). They could then buy a heap of these bitcoins at this low price (around 2000 BTC they got), and could transfer them from the exchange. As a result of the hack, Mt Gox resorted to utilising cold storage for the majority of their bitcoin - this means you cannot access a large proportion of the funds through the web server or any other computer.
The method in which this account was compromised is still somewhat debated - however it is suspected that the auditor account was compromised through an SQL injection on the Mt. Gox website which allowed the attacker to gain read-only access to the user database. The passwords were hashed with MD5 (retrospectively, we know is definitely poor) and accounts which hadn’t logged in prior to the chance in ownership of the exchange (by Tibanne Co. Ltd in March 2011) had unsalted password hashes used. You can read the Mt. Gox press release at the time on BitcoinTalk here.
How did the big second hack in 2014 occur?
In a short period of time in 2013, Mt Gox had become the largest bitcoin exchange in the world and was struggling to cope with the expansion. They had expended significant resources towards dealing with the lawsuits from former business partners (Coinlab) and investigations by the US Department of Homeland Security. We now also know from employee accounts that the security procedures were poor, the website source code was poor quality and a number of other operational issues existed.
This all led to the events which unfolded in February 2014, as follows (according to CoinTelegraph article):
7th - withdrawals frozen due to an “apparent bug” in the Bitcoin network relating to modification of transactions
17th - press release regarding a solution they had found to solve this “bug” which would be applied shortly
23rd - the CEO of Mt. Gox, Mark Karpeles, resigned from the Bitcoin Foundation and disappeared from Twitter
24th - trading was suspended and an internal document leaked claiming they were insolvent; missing 744,408 bitcoins (it was a crisis strategy draft)
28th - Mt. Gox filed for bankruptcy protection in Tokyo and in the US on March 9th
They haven’t been particularly transparent regarding the cause of the second hack, however some information has been pieced together. It is believed that Mt. Gox’s hot wallet private keys were stolen from a wallet.dat file near the end of 2011. Throughout 2012 and 2013, the hacker emptied the wallets associated with the private keys, however Mt. Gox’s systems interpreted this is deposits for some reason. Towards the end of 2013, the hacker had stolen over 600,000 BTC; a large proportion of this ended up on BTC-E. This exchange was essentially responsible for laundering half the funds associated from the hack; it was taken down in 2017 by the US Justice Department.
Smart Contracts
What is a smart contract?
A contract is an agreement between two parties which will be binding in some point in the future. The difference in the case of smart contracts with blockchain is that it makes the execution of the contract trustless - we don’t need a third party. Some restrictions are imposed when we make them decentralised; they need to be unable to access data outside the program (to prevent malicious activity) and they need to be deterministic (so nodes in the network can still verify blocks).
Why are these contracts so prone to errors?
The majority of smart contracts we know today are built upon the Ethereum blockchain; it uses a Turing-complete smart contract language known as Solidity. This differs from traditional contracts in the sense you are to solve any reasonable computational problem. It also comes at the cost of increasing complexity; there is an increasing number of ways the flow of the contract can occur and thus they are very difficult to get right. We already know that writing ‘secure’ code is hard, but when you have money directly on the line it becomes even more important.
What was the DAO?
The DAO (Decentralised Autonomous Organisation) was an organisation built on top of Ethereum which ran completely through smart contracts on the platforms. In the token offering, users were able to send ETH to a particular address and receive DAO tokens in return. Anyone was able to make a pitch to the community, and people could vote with their DAO tokens whether to make an investment. If a project was successful as a result of the DAO, it would then return profits to the investors.
How was the smart contract code in the DAO exploited?
One of the developers announced on the 12th of June that they had discovered a recursive bug call in the DAO contract, however emphasised that no funds were at risk. An attacker managed to find a way on the 18th of June to abuse this recursive bug call to continuously send funds to a child DAO under their control. The process was as follows (source):
(1) Propose a split and wait for the voting period to expire
(2) Call splitDAO()
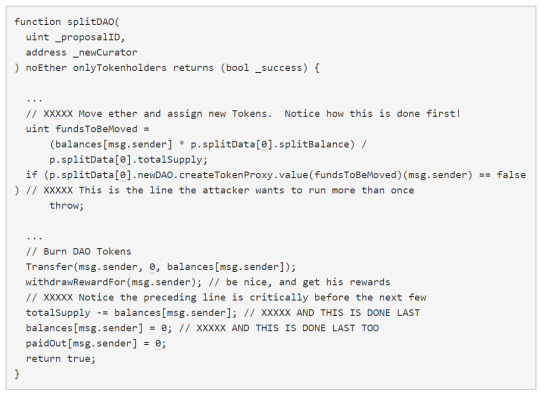
(3) Let createTokenProxy() send your new DAO its share of tokens
(4) Ensure the DAO calls withdrawRewardFor() before updating your balance and after doing (3)

(5) Call splitDAO() again with the same parameters while (4) is occurring
(6) DAO will repeat steps (3) and (4) to give you the child tokens again
(7) Go back to (5) as many times as you like
So in summary, the problem all stems from the fact that you get your reward in the child DAO before subtracting from the original balance. The stack was actually limited to 128 on Ethereum at the time, so he wasn’t able to continue these calls forever. The attacker managed to get around this by using the handy transfer() function, so he could quickly move the funds out to another account he controlled. Then he could move it back into the original account and repeat the process.
What happened after the hack?
The attacker managed to steal ETH worth up to 250 million USD; they actually stopped after draining around 1/3 of the DAO’s funds. It started a big debate among members of the Ethereum community as to how they could respond to this attack. One side fought for the immutability (’code is law’) of the blockchain and argued that we shouldn’t fork to take away the funds from the attacker. The other side wanted to fork the chain to return all the funds. The miners were divided on the proposals (a contentious hard fork) so we ended with two chains - Ethereum Classic (ETC) and Ethereum (ETH).
6 notes
·
View notes
Text
Crypto Seminar Summary
Week 1 Our group consisted of 4 members and we quickly set up a Facebook group chat to discuss the presentation. We decided to give ourselves some time to become familiar with the concept of cryptocurrency before deciding on a time to meet up and discuss the presentation further next week.
Week 2 Unfortunately, one of the members left the group due to some technical difficulties, and now we were 3. Most members of the group were actually quite busy this week, so we settled on a meeting time for next week.
Week 3 Not sure how this happened but our Open Learning group now has 16 people in it?? We were extremely confused about this and it was a surprise because I guess we don’t get notified when people join the group or post in it. We posted a link in the group to our chat so people who were going to be participating could join and help us out. We decided to postpone the meeting until everyone was part of the group and we could discuss a more appropriate time for everyone to meet up.
It turned out that a lot of people who joined the group weren’t aware it was for the 6841 seminar and thought it was just a study group! Our group ended up having 8 people. We settled on a meeting time for next week.
Week 4 We finally got to meet up and basically we just discussed how we were going to structure the presentation and what content we would discuss. This is the basic layout we have;
Intro to crytpo
Benefits vs a centralised system
PoW vs PoS
How cryptocurrency achieves security
Blockchain
Incentives providing security
Why do we have so many different cryptocurrencies, usages
Privacy
zkSnarks, zcash, monero
Historical flaws in blockchain itself
51% attack (i.e. ETC 2019)
DDoS
Doublespend (i.e. The Finney attack)
Historical flaws in Wallets
Phishing
Bad hashes (i.e. IOTA)
Wallet & exchange software bugs (MtGox, Bitfinex)
Historical flaws in Smart contracts
Bad programming pretty much (i.e. TheDAO)
Future practicality, threats, viability in terms of personal private key storage
If all devices we own really are that secure should we be placing the trust in ourselves for protecting our own money really?
Quantum computing threats in 15-20 years
Developers pushing bad code without auditing
We also had some ideas for a demo;
Showing some buggy smart contracts
Hash brute forcing
We estimated the entire presentation to run for approx 40mins.
We also delegated each section to people and organised a meeting time for next week to check up on progress.
Since this meeting was before the lecture this week, after this week’s seminar, Richard mentioned they should only be 25mins long. Hence we knew we needed to restructure the presentation and decided to not do as many case studies, focusing only on the 51% attack and briefly giving an overview of the others.
Week 5 Everyone seemed to be doing pretty well and most of the research was done. The presentation still seemed like it would go over time so we decided to cut out the demo, especially since we hadn’t really finalised what demo we would even do. The idea from before about brute forcing a hash we are going to use as the homework exercise. Since the midsem was this week, we decided slides should be completed by Monday next week. Somehow this meeting went way off track though and we ended up just talking about cryptocurrency in general for about half an hour?? Nonetheless, it was an interesting point of discussion.
Week 6 Slides were finalised so we met up before the lecture this week to run through the presentation. Somehow we ended up again in a discussion about cryptocurrency in the media and privacy concerns! We made some final edits to the slides and gave each other feedback on each of our presentations, which I found really useful.
Post Seminar Overall I think the seminar went really well and I’m really proud of our group for putting it together! I was glad to see that the students were actually engaged with the talk and asked us to go over one of the points again at the end (51% attack). Out largest difficulty was definitely the 25min time constraint as near the end we did have to rush to get everything in.
Participation in this taught me a lot about the technical side of cryptocurrency which was really interesting and I’m glad I put in the research. It was also good practice to be able to work in a team and collaborate our ideas because they taught me a lot through their opinions on privacy etc, that I probably wouldn’t have thought of otherwise. I was also really glad to have an opportunity to present to such a large audience because this year I’ve been trying really hard to practice my presentation skills as it was a weakness for me last year. At first it was daunting but this whole thing was really just such a good learning experience.
Here is a reflection on the seminar from one of the group members: https://comp6841.tumblr.com/post/186399764439/roundup-for-week-6
3 notes
·
View notes
Text
December 14, 2018 Week in Ethereum News
News and Links
Layer 1
[Eth 2] Danny Ryan’s state of the spec
[Eth 2] Latest Eth 2 implementers call. Agenda to follow along.
[Eth 2] What’s New in Eth2
[Eth 2] Latest Prysmatic dev update
[Eth 2] Lighthouse dev update
[Eth 2] Coindesk profiles the teams building Eth2
[ewasm] Latest Ewasm call.
[1 -> 2] When stable, the beacon chain to finalize the POW chain
[Eth1] State Rent proposal update
[Eth1] How types of contracts would handle contract state-root-plus-witness architecture
NEAR: Unsolved problems in blockchain sharding
Boneh, Bünz, Fisch: Batching Techniques for Accumulators for stateless chains
Justin Drake Ethereum 3.0 tweet
Layer 2
Storj is planning to use Raiden for its payments. Raiden v0.19
Building MixEth as a state channel dapp with Counterfactual
Celer’s team to play their state channel Gomoku game for real Eth
gas payment abstraction in layer 2
prime numbers to transactions instead of coins?
should fraudulent exit bonds be partially burned?
Demo snark for Plasma Cash and Cashflow history compaction
SKALE releases architecture of their sidechain network
Stuff for developers
Ethereum on ARM. Constantinople-ready images
registry-builder: A modular approach to building TCRs from LevelK
7 uses cases with 3box.js
Gnosis Apollo to create your own prediction market interface or tournament
Schedule your token transfers on MyCrypto using Ethereum Alarm Clock
BudgetBox from Colony. Binary choices turned into budget percentages, and can be done onchain. Github
web3j v4.1 for Android
You can now integrate Gitcoin’s Kudos into your app. Gitcoin also hit 500k in issues.
A quick Austin Griffith tutorial on Commit/Reveal
Matt Tyndall’s counterfactual loan repayment for Dharma
Linkdrops: let people send crypto embedded in URLs without gas/wallets
Panoramix decompiler using symbolic execution instead of static analysis
Streamr’s cold chain monitoring tutorial
Dennis Peterson: Spam protection with probabilistic payments and cheap doublespending protection
How to debug with Tenderly and Truffle
A teaser for Harvey fuzzer from ConsenSys Diligence
Automated Eth code exploiter and similar how to scan and steal ETH
Hard fork enabled client releases
Geth v1.8.20 - hard fork enabled, Puppeth improvements, etc
Parity Ethereum 2.2.5-beta and Parity Ethereum 2.1.10-stable hardfork enabled
Trinity v0.1.0-alpha.20 Constantinople support and genesis file support
Ecosystem
Opera releases native Eth wallet and dapp browser for Android. Download. Slick and well worth checking out.
How I learned Solidity basics for free as a noob dev
Uncle rate keeps falling. Time to start nudging up the gaslimit?
Monetary policy chart of historic and future Ether issuance
All the impressive ETHSingapore submissions and winners. Some of Josh Stark’s favorites.
A comparison of ETHSanFrancisco and EOS SF hackathons
Ethereum product management interviews. Also, video of Eth PMs call
Alethio’s EthStats block explorer
Ecosystem job listings
Web3Foundation, Validity Labs and Status working on Whisper alternative
Live on mainnet
OriginTrail: data exchange in supply chains protocol
Enterprise
Quorum v2.2.0
Cheddar suggests Facebook wants to do its own basechain and is recruiting
Why Enterprise Ethereum is way more than DLT
See OriginTrail above
Governance and Standards
ProgPOW testnet block explorer
A quick case study on Aragon’s AGP1 proposal
Evolution of a security token standard
ERC1643: Document Management Standard
ERC1644: Controller Token Operation Standard
ERC1666: Decentralized Autonomous Zero-identity Protocol
ERC1613: Gas stations network
Application layer
Cellarius first anthology released. Free to MetaMask users.
Golem’s Graphene-ng demo part2
XYO Network to launch satellite named EtherX on SpaceX’s Falcon9 in next few months
Data auditing and repair with Storj
The Fluidity stack to allow liquid secondary markets
Vitalik tweetstorm on non-financial apps
Onchain mutual insurance to return insurance to its origin: communities sharing risk
p2p loan offers on Bloqboard using Dharma
Ujo Portal out of beta and in version1.
KyberNetwork’s monthly update - new reserves, wBTC updated
Liquality offers crosschain swap of testnet Eth for Bitcoin. You can also get a good price buying Eth with Summa’s crosschain swap
GnosisSafe users can pay gas fees in OWL.
Maker proposal to reduce stability fee from 2.5% to 0.5%. Vote Dec 17
Augur’s controversial US House elections market has been reported as Republican. This is obviously nonsense because no one would have bet on that market and it makes no sense to encourage wordsmith trickery. This is a huge test of Augur and will be interesting to watch. Also, v1.8.4 out with new node endpoint. And a nice Augur 2018 review from Guesser
Interviews, Podcasts, Videos, Talks
All Devcon4 videos and photos
Arthur Falls uploads some Joe Lubin Devcon3 video footage
Video: a Wolfram language platform for Ethereum
Zero Knowledge ETHSingapore episode
Open Block Explorers community call
Blockchain Insider with Vitalik Buterin
Grid+ Alex Miller and Karl Kreder on Hashing It Out
Prysmatic’s Preston Van Loon and Raul Jordan on Into the Ether
Andrew Keys talks ConsenSys2.0 with Laura Shin
Tokens / Business / Regulation
Chris Burniske argues Ether and Bitcoin prices are undervalued based on fundamentals
4 eras of blockchain computing: degrees of composability from Jesse Walden
CFTC requests input. EthHub and Brooklyn Project are both crowd sourcing responses
Basecoin/Basis quits after raising ~130m and returns money to its VCs, blaming the SEC. I feel there may be more to come with this story.
MythX (formerly Mythril) decides against its announced token
Don’t think there was any doubt, but Coinbase is listing tokens. 30 assets up for consideration
Bonding curve intuition and parameterization
Harberger taxes in action on r/ethtrader banners
Simon de la Rouviere: Desire paths and recommendation markets
General
Zero-Knowledge Proofs Starter Pack
Support starving Venezuelans by buying NFT Christmas cards through Giveth. Easy onboarding for your non-crypto friends.
Results of Bounties Network paying local to participate in Manila Bay beach cleanup. Some interesting UX lessons.
Terra-Bridge: Transfer between Ethereum and Bitcoin protocol
CMEGroup puts up an Intro to Ether course
Zilliqa testnet v3 is live and in feature freeze ahead of January mainnet release. It also got an AWS case study
Boerse Stuttgart and SolarisBank say in next 6 months they’ll launch crypto trading platform in Europe
The state of Surveillance Capitalism is dire: your apps are tracking your location and selling it. It’s very easy to figure out who you are from your location. Bring on web3!
Dates of Note
Upcoming dates of note (new in bold):
Dec 17 - vote to reduce Maker stability fee
Jan 10 - Mobi Grand Challenge hackathon ends
Jan ~15 - Constantinople hard fork at block 7080000
Jan 29-30 - AraCon (Berlin)
Feb 7-8 - Melonport’s M1 conf (Zug)
Feb 15-17 - ETHDenver hackathon (ETHGlobal) next hacker application round closes December 31st
Feb 23-25 - EthAustin hackathon (EthUniversal)
Mar 4 - Ethereum Magicians (Paris)
Mar 5-7 - EthCC (Paris)
Mar 27 - Infura end of legacy key support (Jan 23 begins Project ID prioritization)
Apr 19-21 - ETHCapetown
If you appreciate this newsletter, thank ConsenSys
This newsletter is made possible by ConsenSys.

I own Week In Ethereum. Editorial control has always been 100% me. If you're unhappy with editorial decisions or anything that I have written in this issue, feel free to tweet at me.
Housekeeping and random Twitter banhammers
One of my best friends launched Stoop, an Android/iOS newsletter reader. It uses a dedicated email and clean design experience to keep your information diet healthy. If you subscribe to newsletters, you will like it.
Link: http://www.weekinethereum.com/post/181120057303/december-14-2018-week-in-ethereum-news
I’m sure that I missed things for this newsletter due to Twitter’s banhammer last week. Sorry! Plenty of folks in Ethereum got random Twitter banhammers this week. :(
If you’re wondering “why didn’t my post make it into Week in Ethereum?”
Did you get forwarded this newsletter? Sign up to receive the weekly email
1 note
·
View note
Text
This fucker is threatening to 51% attack any chain that doesnt follow his tyranny. He has to be stopped at all costs, patents, doublespends, 51% threats. @rogerkver SPEAK THE FUCK OUT!
This fucker is threatening to 51% attack any chain that doesnt follow his tyranny. He has to be stopped at all costs, patents, doublespends, 51% threats. @rogerkver SPEAK THE FUCK OUT!
[ad_1]

This fucker is threatening to 51% attack any chain that doesnt follow his tyranny. He has to be stopped at all costs, patents, doublespends, 51% threats. @rogerkver SPEAK THE FUCK OUT!
[ad_2] View Reddit by millerbitcoincash – View Source
View On WordPress
#Attack#chain#Costs#doesnt#doublespends#Follow#Fuck#fucker#patents#rogerkver#speak#stopped#Threatening#Threats#tyranny
0 notes
Text
Huobi On Air: #Bitcoin FUD, Huobi Launches, Crypto #Memes!

youtube
Articles referenced are below; https://www.coindesk.com/bitcoin-double-spend-that-never-happened https://www.theblockcrypto.com/linked/92028/yellen-treasury-senate-cryptocurrencies https://www.coindesk.com/janet-yellen-says-cryptocurrencies-are-a-concern-in-terrorist-financing
Huobi Campaigns: Filecoin: https://www.hpt.com/announcement/cu INJ Launch: https://support.hbfile.net/hc/en-us/articles/900004193486 BADGER:https://support.hbfile.net/hc/en-us/articles/900005159183 Huobi Futures: https://support.hbfile.net/hc/en-us/articles/900005135203 BRL Fiat: https://huobiglobal.zendesk.com/hc/en-us/articles/900005168083 MASS:https://support.hbfile.net/hc/en-us/articles/900004217706 REEF:https://support.hbfile.net/hc/en-us/articles/900005185323
#coindesk #theblockcrypto #bitcoin #yellen #doublespend #Bitcoin
The post Huobi On Air: #Bitcoin FUD, Huobi Launches, Crypto #Memes! appeared first on BLOCKPATHS.
source https://blockpaths.com/exchanges/huobi-on-air-bitcoin-fud-huobi-launches-crypto-memes/
0 notes
Text
Why Bitcoin Mining Concentration May Be Harmless
The answer is that bitcoin’s design doesn’t assume mining power is widely distributed. It’s simply not a requirement. Instead, it only assumes miners are rational, which is something completely different. Rationality means agents do what is best for them, even if that means colluding with other miners to attack the system.
Satoshi addressed this matter directly in the white paper:
The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.
Let’s unpack this a bit. It is the incentive in the form of new coins and transaction fees that motivate the majority to “stay honest.” Satoshi realized that the only way to prevent a “greedy attacker” from taking over is to make it more profitable to play by the rules than to attack the system.
This is the key to bitcoin’s assurances and at the same time the most widely misunderstood aspect of bitcoin’s design.
Economist Paul Sztorc even says he is “most comfortable just assuming that everyone is always in perfect collusion with everyone else. Specifically that all of the hashpower is actually owned-and-operated by one guy, whom we might call “Mr. Greed.” [...] Why doesn’t Mr. Greed doublespend, you ask? (He can reorganize the chain at any time.) Well, Mr. Greed prefers to keep all of the new coins for himself, rather than undermine the system (and the validity of his own wealth).”
I must admit, I was not comfortable with what I perceived bitcoin’s security model to be initially. If bitcoin were vulnerable the moment a group of colluding miners obtains 51 percent of hash power, how could we possibly monitor – let alone prevent – this? Moreover, why are smaller forks like BCH and BSV not constantly under attack, given that several individual mining pools in BTC control more hash power than their entire networks?
The dissonance disappeared when I realized that hash power concentration doesn’t actually matter. Bitcoin is secure not because it is impossible to attack, but because it is costly to attack.
https://www.google.com/amp/s/www.coindesk.com/no-concentration-among-miners-isnt-going-to-break-bitcoin%3famp=1
0 notes
Photo

Researchers Are Developing A Nearly “Zero Energy” Bitcoin Alternative #bitcoin #bitcoinalternative #bitcoinalternativenewalgorithm #bitcoinmining #cryptocurrency #doublespending #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Text
Seminar Organisation
We finally managed to (all 8 of us) meetup for an hour before the lecture on Tuesday to go through the structure we would use for the seminar. We expanded on some of the things we would like to discuss and tried to have a more specific focus on security regarding cryptocurrency. I’ll briefly outline our structure in its’ current form:
(1) Introduction - broad overview regarding blockchain and cryptocurrency, benefits vs centralised systems, types like PoW vs PoS, usage & practicality
(2) Generalised mechanics - cryptographic principles and incentives which provide network security
(3) Different types - why we need them and what added benefits they provide over traditional
(4) Privacy - how blockchain can provide confidentiality and some issues associated; zkSnarks, zCash, Monero, etc
(5) Vulnerabilities associated with the blockchain - 51% attacks (i.e. ETC 2019), DDoS, doublespend (i.e. Finney attack)
(6) Vulnerabilities associated with users and wallets - phishing, crappy hashes (i.e. IOTA), wallet and exchange software bugs (MtGox, Bitfinex), etc
(7) Flaws associated with Smart contracts - bad programming pretty much and issues associated with languages such as Solidity (i.e. TheDao, Parity wallet, etc)
(8) Future practicality, threats and viability in the long-term - should we trust individuals with their own money security; quantum computing threats
I think we have outlined a pretty decent structure (and order) for the presentation and the work is fairly well distributed. We’re collaborating via Google Docs for the presentation at this stage - I’m working on the privacy component, so I will definitely try and make some good progress this week. I’ll try and see that we have a meetup perhaps same time next week to discuss progress on research and the presentation. (should set some deadlines too) We definitely need to do a run through in the days before the actual seminar - this may be difficult, considering we are just after the mid semester exam.
1 note
·
View note
Photo

The original doublespend attack via /r/bitcoinmemes
0 notes