#Enable telnet Client
Explore tagged Tumblr posts
Text
PuTTY
PuTTY is a widely-used, open-source, lightweight, and free SSH client and terminal emulator. Created by Simon Tatham using the C programming language, its main purpose is to enable remote computer connections while providing file transfer and data manipulation capabilities. PuTTY supports various network protocols, including SSH, Telnet, Serial, SCP, and SFTP. It also includes a command-line tool…
#Command Line Tools#file transfer#Network Protocols#Remote Access#SCP#sftp#SSH Client#Telnet#Terminal Emulator
0 notes
Text
does vpn need port 443
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn need port 443
VPN server port requirements
When setting up a Virtual Private Network (VPN), understanding the server port requirements is crucial for ensuring smooth and secure connectivity. Ports act as communication endpoints for networked devices, and configuring them correctly is essential for the VPN to function optimally.
Typically, VPN protocols utilize specific ports for different types of traffic. For instance, the widely used OpenVPN protocol commonly employs port 1194 for UDP traffic and port 443 for TCP traffic. UDP (User Datagram Protocol) is preferred for its speed and efficiency in transmitting data, while TCP (Transmission Control Protocol) is favored for its reliability, especially in situations where network congestion or packet loss is a concern.
Additionally, other VPN protocols like L2TP/IPsec and IKEv2/IPsec rely on different port configurations. L2TP/IPsec typically uses UDP port 500 for the initial key exchange and UDP ports 4500 and 1701 for the actual data transmission. IKEv2/IPsec, on the other hand, commonly operates over UDP port 500 and uses UDP port 4500 for NAT traversal.
It's worth noting that some networks may have restrictions or firewalls in place that block certain ports. In such cases, it may be necessary to configure the VPN to use alternative ports that are allowed by the network infrastructure.
Furthermore, for enhanced security, VPN servers often support port forwarding, allowing traffic to be directed through specific ports to specific destinations within the network. This feature enables users to access services on their private network securely from remote locations.
In conclusion, understanding VPN server port requirements is essential for ensuring compatibility, security, and optimal performance. By configuring the appropriate ports and protocols, users can establish reliable and secure connections to their VPN servers, enabling seamless access to resources from anywhere in the world.
Network security protocols
Network security protocols are crucial components in safeguarding data and preventing unauthorized access within a network. These protocols establish rules and processes for secure communication between devices and ensure that data remains confidential and integral.
One of the most commonly used network security protocols is the Secure Socket Layer (SSL) or its successor, the Transport Layer Security (TLS) protocol. SSL/TLS protocols encrypt data transmitted between a client and a server, making it unreadable to anyone who may intercept the communication. This encryption ensures that sensitive information such as passwords, credit card details, and personal data is protected from cyber threats.
Another essential network security protocol is the Internet Protocol Security (IPsec) protocol, which provides authentication and encryption at the IP layer to secure data communication between devices. IPsec can be used to create Virtual Private Networks (VPNs) to establish secure connections over the internet or within a private network.
Furthermore, the Secure Shell (SSH) protocol is widely used for secure remote access to devices such as servers and routers. SSH provides strong authentication and encrypted communication, making it a secure alternative to traditional Telnet connections, which transmit data in clear text.
In conclusion, network security protocols play a vital role in safeguarding sensitive information and ensuring the integrity of data transmissions within a network. By implementing strong security protocols such as SSL/TLS, IPsec, and SSH, organizations can mitigate the risk of cyber attacks and maintain a secure network environment.
VPN encryption methods
Title: Exploring VPN Encryption Methods: Securing Your Online Privacy
In an era where online privacy is increasingly threatened, virtual private networks (VPNs) have emerged as a vital tool for safeguarding personal data and maintaining anonymity while browsing the internet. Central to the effectiveness of VPNs are their encryption methods, which serve as the foundation for securing data transmission across the web.
There are several encryption protocols utilized by VPN services, each offering varying levels of security and performance. One of the most commonly used protocols is OpenVPN, renowned for its open-source nature and robust encryption capabilities. OpenVPN employs OpenSSL library to implement SSL/TLS protocols, ensuring data confidentiality and integrity through encryption algorithms like AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Another widely adopted protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec utilizes encryption algorithms such as DES (Data Encryption Standard), 3DES (Triple DES), and AES to secure data transmission between VPN clients and servers. Its flexibility and compatibility make it suitable for various platforms and devices.
For users prioritizing speed without compromising security, L2TP/IPSec (Layer 2 Tunneling Protocol with IPSec) is a popular choice. While L2TP itself doesn't provide encryption, when combined with IPSec, it creates a secure tunnel for data transmission, offering a balance between speed and security.
Additionally, newer encryption methods like WireGuard have gained traction for their efficiency and simplicity. WireGuard utilizes state-of-the-art cryptographic primitives to ensure secure communication with minimal overhead, making it ideal for mobile devices and resource-constrained environments.
Ultimately, the choice of encryption method depends on individual preferences, security requirements, and performance considerations. However, regardless of the protocol chosen, implementing a VPN with robust encryption is essential for safeguarding sensitive information and preserving online privacy in an increasingly interconnected world.
Port 443 VPN traffic
Port 443 VPN traffic refers to the use of port 443 for Virtual Private Network (VPN) connections. Port 443 is the standard port for secure HTTP communication over the internet, commonly known as HTTPS. VPN traffic on port 443 is often used to bypass network restrictions or to prevent VPN blockages, as it is difficult for network administrators to block this port without disrupting regular internet traffic.
When VPN traffic is routed through port 443, it appears as regular HTTPS traffic to network filters and firewalls, making it harder to detect and block. This can be particularly useful in countries or organizations where VPN usage is restricted or monitored.
Using port 443 for VPN traffic offers encryption and security benefits similar to HTTPS, ensuring that data transmitted between the user and the VPN server is protected from interception or tampering. This is especially important when connecting to public Wi-Fi networks, as it helps prevent unauthorized access to sensitive information such as passwords, financial data, and personal communications.
However, while using port 443 for VPN traffic can enhance security and privacy, it is essential to choose a reputable VPN service provider to ensure the confidentiality of your data. Additionally, some network administrators may still be able to detect and block VPN traffic on port 443 using more advanced methods.
In conclusion, utilizing port 443 for VPN traffic can be a valuable tool for maintaining online privacy and security, particularly in environments where VPN usage may be restricted. It is crucial to understand the potential limitations and risks associated with this practice while benefiting from the added layer of protection it offers.
Optimizing VPN performance
To achieve optimal VPN performance, it is essential to understand the key factors that can impact the speed and efficiency of your connection. By implementing the following tips, you can enhance your VPN experience and ensure seamless browsing, streaming, and secure data transmission.
Choose a Reliable VPN Provider: Selecting a reputable VPN service provider with high-speed servers and robust security protocols is crucial for optimizing performance. Look for VPNs with a large server network and fast connection speeds to experience minimal latency.
Connect to Nearest Servers: Connecting to VPN servers that are geographically close to your location can help minimize latency and boost performance. By reducing the physical distance between your device and the server, you can experience faster speeds and smoother connectivity.
Update VPN Software Regularly: Ensure that your VPN client is up to date with the latest software versions and security patches. Updates often include performance enhancements and bug fixes that can improve the overall speed and reliability of your VPN connection.
Use Lightweight Encryption Protocols: Opt for lightweight encryption protocols like L2TP or IKEv2, which offer a good balance between security and speed. Avoid heavy encryption protocols like OpenVPN when speed is a priority, especially for tasks that do not require high-level security.
Optimize Device Settings: Adjusting your device's settings can also help optimize VPN performance. Close unnecessary applications running in the background, disable battery-saving modes, and update network drivers to ensure smooth and stable VPN connectivity.
By implementing these strategies and making informed choices when it comes to VPN usage, you can enhance performance, speed, and security for a seamless online experience.
0 notes
Text
A Comprehensive Guide: Logging into a Windows Server Using PuTTY
In the realm of computing, the interaction between different operating systems is inevitable. For instance, the Linux community often finds itself needing to access Windows Server environments, typically managed through Remote Desktop Protocol (RDP). In such scenarios, PuTTY, a versatile SSH and Telnet client for Windows and Unix platforms, becomes a vital tool. In this guide, we'll walk you through the process of logging into a Windows Server using PuTTY, bridging the gap between Linux and Windows environments seamlessly.

PuTTY serves as a bridge, enabling Linux users to connect to Windows Server environments securely. Before delving into the process, ensure you have PuTTY installed on your Linux machine. Once installed, launch PuTTY to initiate the login process to the Windows Server.
When connecting to a Windows Server via PuTTY, you'll require the server's IP address or hostname, alongside the port number. Typically, Windows Servers utilize the default SSH port 22 for secure connections. However, if your server administrator has configured a different port, ensure to specify it during the connection setup.
With PuTTY launched, you'll be greeted by a simple yet powerful interface. Begin by entering the server's IP address or hostname in the "Host Name (or IP address)" field. Next, ensure the connection type is set to SSH, as PuTTY supports various protocols, including Telnet and Rlogin, but SSH provides secure communication.
Upon entering the necessary details, click on the "Open" button at the bottom of the PuTTY window to initiate the connection process. If this is your first time connecting to the server, PuTTY might prompt you with a security alert regarding the server's SSH key fingerprint. Verify the authenticity of the fingerprint before proceeding.
Once authenticated, PuTTY will present you with a terminal window, prompting for login credentials. Enter your username and password provided by the Windows Server administrator. It's essential to ensure the accuracy of the credentials to establish a successful connection.
After entering the credentials, PuTTY will validate them with the Windows Server. Upon successful authentication, you'll gain access to the Windows Server command-line interface, akin to the Linux terminal. From here, you can execute various commands and perform administrative tasks on the Windows Server environment seamlessly.
In scenarios where users need graphical interface access to the Windows Server, PuTTY can facilitate that as well. By leveraging X11 forwarding, PuTTY allows you to run graphical applications from the Windows Server on your Linux machine. To enable X11 forwarding, navigate to the PuTTY configuration window, select the "SSH" category, and check the "Enable X11 forwarding" option.
With X11 forwarding enabled, you can run graphical applications on the Windows Server, and their interfaces will display on your Linux machine. This capability enhances the versatility of PuTTY, enabling Linux users to interact with Windows Server environments efficiently.
In addition to accessing Windows Servers via PuTTY, users may also need to change their passwords within the Remote Desktop Protocol (RDP) session. While PuTTY facilitates SSH connections, RDP allows users to access the graphical desktop interface of Windows Servers remotely.
To change your password within an RDP session, initiate an RDP connection to the Windows Server using a compatible client, such as Microsoft's Remote Desktop Connection. Once connected, navigate to the "Ctrl+Alt+Delete" menu within the RDP session and select "Change a password" to modify your login credentials securely.
It's important to note that while PuTTY facilitates SSH connections to Windows Servers, RDP remains the primary method for accessing the graphical interface remotely. Therefore, users may utilize PuTTY for command-line tasks and administrative functions, while relying on RDP for GUI-based interactions.
In conclusion, PuTTY serves as a versatile tool for Linux users seeking to access Windows Server environments securely. By following the outlined steps, you can establish SSH connections to Windows Servers seamlessly, bridging the gap between Linux and Windows environments effortlessly. Additionally, PuTTY's support for X11 forwarding enhances its capabilities, enabling graphical interactions with Windows Server applications on Linux machines. Whether you're a Linux enthusiast or a Windows Server administrator, PuTTY remains an indispensable tool for cross-platform connectivity.
Whether you're a seasoned Linux user or a Windows Server administrator, PuTTY simplifies the process of logging into a Windows Server from a Linux environment. With its user-friendly interface and robust feature set, PuTTY facilitates secure SSH connections to Windows Servers seamlessly. By following the steps outlined in this guide, you can bridge the gap between Linux and Windows environments effortlessly, ensuring efficient cross-platform connectivity for your administrative tasks.
0 notes
Text
Launching the Simics Simulator with RISC-V Platform

The amount of processor cores, active instruction set extensions, memory capacity, virtual disk size and content, Ethernet network address, and other configuration options can all be changed on hardware. The platform employs virtio devices for networking, drives, and entropy (instead of devices from some particular real-world RISC-V-based system-on-chip (SoC)) to simplify program support. Practically speaking, it feels and appears like a little embedded device, despite the fact that it may be configured with many gigabytes of disk and RAM.
Both Linux and bare-metal software can be executed on the platform. Buildroot is used to build the standard software stack for Linux. Creating a bootloader, Linux kernel, and bootable file-system image for the RISC-V virtual platform is a pretty simple task when you use Buildroot.
Connecting the Virtual Platform RISC-V
Enabling networking was a fairly intriguing use case throughout the platform’s development. It wasn’t difficult to get networking to function at the point where machines could “ping” one another. It required some effort to enable remote login from one computer to another.
Telnet would have been used to accomplish this in the past. There is minimal configuration required, and the protocol, client, and server are all straightforward. But the networking world isn’t what it used to be, and almost every Linux distribution demands that secure shell (SSH) be used for any form of remote login. It only takes a few lines of setup to add SSH to Buildroot, then rebuild.
SSH, however, is a more intricate creature. After adding SSH to the root filesystem, the target machine would not start up and would hang right before the login prompt appeared. The absence of unpredictability was the issue. SSH requires a source of randomness in order to produce a host key when it is first installed. The random pool was filling up very slowly since the Linux kernel could not find many sources of randomness to use on the very basic virtual platform. stopping the boot’s advancement. Nice example of “oh, I didn’t realize that might be an issue.”
Intel enhanced the target system by adding a “Virtio entropy” device. This gives the target system a high-bandwidth source of randomness. To assure simulation repeatability, it is implemented in the simulator using a deterministic pseudorandom system, even if it appears to the target system to be a hardware random-number generator (RNG). The variation is undetectable to the target software.
This is a straightforward simulated network architecture that makes use of several RISC-V virtual platforms, each with a unique hardware arrangement. It should be noted that the virtual network also has a “service node” that offers standard services like DHCP for system configuration and a dependable target for ping to check network connectivity.
SSH is being used by the “small” machine to connect to the “medium” machine. To display the memory size, the “medium” and “large” machines are both operating at the top. In order to show the simulation of a multicore target system, they are also running a few copies of the single-threaded coremark benchmark. A list of the simulated machines and every processor core in the active simulation is displayed by the Simics simulator command line.
The target machines differ in terms of clock frequencies, memory sizes, and core counts, as can be seen from the Simics command-line interaction in the terminal.
Because each RISC-V target is housed in a separate Simics simulator cell, the simulation can run three machines concurrently, which speeds up the simulation. Additionally, each machine has the option to activate parallel simulation, which might result in the creation of two + four plus eight, or 14-way parallelism in this instance. Workloads involving a lot of computation benefit greatly from this acceleration.
Using the Quick Start Platform for networking
Heterogeneous mixed-architecture simulations can be conducted since the Intel Simics Simulator Public Release includes the Intel Architecture-based Quick-Start Platform (QSP). Combining the two targets into a single network within a single Simics simulation operation is a basic example. similar to this
The service node’s Network Address Translation (NAT) feature allows any virtual network to be connected to the outside world. The screenshot below shows the host system (this time running Microsoft Windows for variety’s sake) logging into the RISC-V target system via inbound port forwarding with an SSH client. Additionally, two SSH connections are open due to an SSH login from the QSP target system to the RISC-V target system..
All that is required to set this up is a short amount of top-level scripting over the virtual platform scripts that are already in place. Initially, default parameter values that deviate from the targets’ standard values are set up using a YAML file. Keep in mind that the exact names of the parameters and the parameter hierarchy may vary because this is based on early drops of the targets.
Second, the YAML file calls a Simics simulator command-line script, which uses pre-existing setup scripts to produce the separate setup components in order to build the network and target systems.
Read more on Govindhtech.com
0 notes
Text
The One Thing to Do to Enable Telnet Client
If the system isn't connected with any repository, the above command will not operate. You might need to restore your operating system to a former state where the problem did not exist. If you are able to tell which my computer that was not there before and I can't do away with it. For a successful implementation, it ought not to have the ability to access the server computer.
Whichever server you're using. Your TS3 server could be lacking permissions. Once you are finished with the configuration, verify whether the telnet to a server works. As mentioned in the introduction, Windows Server 2012 comes with a great quantity of PowerShell cmdlets. In case the server doesn't support Explicit SSL, then you still must use Stunnel that's a little more complicated. Your SMTP Server is currently configured and prepared to go.
You are able to allow the customer either by command line or by means of the graphical interface. Firstly you have to allow the telnet client, if you don't enable it you'll receive a result very similar to the below message when attempting to utilize it. The Telnet Client is among the absolute most basic tools for such pursuits. You may allow the telnet client either by command line or by means of the graphical interface.
You ought to be about to utilize Telnet via Command Prompt now. It's wise not to use telnet whenever you are dealing with sensitive data. Now you have enabled telnet you need to be able to get started issuing commands with it and using it to troubleshoot TCP connectivity troubles. Telnet is an old outdated protocol that's used for remote command-line administration on several devices like Cisco routers. Telnet is also utilized as a verb. Telnet isn't a good chose to control a system over the world wide web. Should you do a yum install telnet it's only going to contain client telnet program.
To prevent telnet service you are able to run the below command. Now you know your way around the Command Prompt, it is a great idea you learn a few of the tricks and suggestions for the Windows 10 Task Manager too. To use any of these commands you have to bring up the Command Prompt itself. If the above command doesn't return any output then telnet-server isn't installed. Despite the fact that the above commands are the most useful while using the Command Prompt, there's more you're able to do. The upcoming obvious command to check at is the command to do a scenario-based deployment.
You don't need to understand all the Enable telnet Client Command Prompt commands to discover some use within it. The telnet command should currently be available. Even easier, particularly if you don't intend on following up your very first Telnet command with a variety of further ones, you may just type telnet followed by any Telnet command, like you'll see in the majority of our examples below.
A reboot is needed for the modifications to come into effect. If you aren't certain whether a rule is working telnet may be an excellent means to help debug. Among the biggest perks of Telnet is with a very simple command it's possible to test whether or not a port is open. Rather than going to the Control Panel, there are a better means.

A failed connection is going to be accompanied by an error message. An unsuccessful connection is going to be accompanied by an error message. If your network is live, make certain that you fully grasp the possible effect of any command. In the event the service isn't running, an individual would find the next error when making a telnet connection. You should allow the service first. You have to enable and initiate the service. Telnet service was created on 1969. Well, the obvious rationale is, to knock out the browser. Though most users decide to work with graphical interfaces, Telnet is among the simplest methods to check connectivity on specific ports. Luckily with PowerShell, it is not hard to allow the telnet functionality. Since there's just one feature to install, it is possible to directly click the Install button. The selected feature will be set up. It is possible to specify more than 1 feature in the very same package. In reality, you have many options.
You've got to click on a tick box facing Telnet client. This set of commands is a fast depiction of how it is possible to enable telnet from a PowerShell prompt to make sure the capacity of testing certain ports. You are able to save sessions so you don't need to type the exact same information each time you connect to the exact same session. In some instances, it may be required to close the telnet session and reconnect.
youtube
1 note
·
View note
Text
So I just got my hands on an old DSL modem, so that I can hopefully incorporate it into the ANACUEI project. I managed to enable a telnet client, and was ecstatic to discover that the entire OS was built off of busybox!
Unfortunately, the modem is still configured such that it requires an ISP to give out a password, and bypassing that would get me in a lot of trouble. Which is ironic, considering that DSL modems are basically obsolete by now.
But that’s capitalism for you; even though they’ve moved on to more powerful protocols, they just can’t let people use the old ones. I think that if some megacorp decides to phase out a technology standard, it should automatically become open source, and the infrastructure needed to implement it would be publicly available.
2 notes
·
View notes
Text
Windows 10 SSH vs. PuTTY: Time to Switch Your Remote Access Client?
You should find that SSH is already installed on your Windows 10 computer (it was included in the April 2018 update), but if not, it can be easily added. Let's take a look at how to set up SSH access in Windows 10, and whether the new tools can supplant PuTTY.

One of the most common methods to communicate between computers, particularly Linux machines and web servers, is SSH. When it comes to establishing this sort of communication in Windows, the default option has been to install PuTTY.\

Thanks to Windows Power Shell, however, you may not need PuTTY anymore. Let's take a look at how to set up SSH access in Windows 10, and whether the new tools can supplant PuTTY.
How To Install SSH In Windows 10 (Quick)
Installing SSH functionality to the Windows 10 PowerShell is straightforward enough, but the menu options for it are somewhat hidden. Here's what you'll need to do:
Open Settings.
View Apps > Apps & features
Go to Optional features
Click Add a feature
Select OpenSSH Client
Wait, then reboot
Once this is done, you can establish SSH connections with other, compatible computers. If an SSH server has been installed and configured on the remote machine, a connection can be made.
That's the overview. Here are the details.
How To Install SSH In Windows 10 (Detailed)
Windows 10's PowerShell implementation of SSH is a version of the OpenSSH project. You can find the project page on PuTTYkay.com
You should find that SSH is already installed on your Windows 10 computer (it was included in the April 2018 update), but if not, it can be easily added.
To check, open the Power User menu (right-click Start, or Windows key + X) and select Windows PowerShell. Here, input the command "ssh". If SSH is not yet installed, you'll see a screen like this:

Fixing this is easy enough. Press Windows key + I to open the Settings view, then go to Apps and look for Manage optional features. Click this, then look for an entry labeled "OpenSSH".

If you can't see it, click Add a feature then scroll down until you see OpenSSH Client. Click to expand the item and view the description. When you're ready, click Install to add it to your PC. A few moments later, the new SSH client for Windows PowerShell will be installed. It's worth rebooting Windows to ensure the app is correctly installed.
A Note On The SSH Server App
It's worth highlighting the fact that you can also install an SSH server. While it is unlikely that Microsoft will enable any form of universal remote administration over SSH, having it as an option is nevertheless useful.
To install this, repeat the above steps, selecting the OpenSSH Server.
Using SSH In Windows PowerShell
Once SSH is installed and working, you can use it to communicate with another computer. For instance, you might use it to access a Raspberry Pi (one of several remote options for that little computer).
How to Remote Connect to a Windows PC From a Raspberry Pi
Wouldn't it be great if you could access your PC from your Raspberry Pi no matter where you are? Well, you can! All you need is a remote desktop app.
Usage is simple. In the PowerShell, enter the ssh command, followed by the username for an account on the remote device, and its IP address.

For instance, to connect to my Raspberry Pi box running RetroPie, I used: ssh [email protected]
At this point, the remote device should prompt you to accept a secure key. Type Yes to agree to this, then at the prompt, enter the password for the username you used.
Moments later, you'll be connected to the remote Linux device, ready to perform whatever tasks you need.
PowerShell's SSH Features Vs. PuTTY
PuTTY has long been the preferred choice for SSH on Windows. Whether controlling web servers, accessing Internet of Things devices, or remotely administering a Linux PC, it's a lightweight, easy to use the app.
One of the reasons for PuTTY's endurance is its wide selection of features. So, can SSH on Windows PowerShell compete with PuTTY?

Well, in terms of providing SSH functionality, yes it can. You can find out how to use some of the extended features of SSH on Windows 10 by entering the ssh command: ssh The resulting list of options outlines the features. For example, you can specify a port:
ssh [username]@[hostname] -p [port]
The possibilities are good!
However, it's still not PuTTY. While you can bind an address with OpenSSH on Windows, you're limited by the number of addresses you can save.

There is a reason why PuTTY remains popular. Not only does it allow you to save (and name) your connections, the app also supports connections over Telnet, Serial, and other protocols. PuTTY's appearance is also configurable, can it be quickly launched from the desktop. All in all, PuTTY is a solid utility that handles pretty much anything that you can throw at it.
Why SSH When You Can Use Linux?
While remote controlling Linux over SSH might be vital, you may not even need SSH. Windows 10 now features a Linux subsystem and a Bash-like command prompt. This means that you can easily input Linux commands and receive realistic responses. While it might not be ideal for all scenarios, if you need Linux access for college or training purposes, and don't have SSH access (regardless of the app) to a Linux device, this might be ideal. Of course, this isn't the only option. If you need to practice Bash commands in Windows, you can always set up a virtual machine. Simply install a Linux distribution into this and (hardware permitting) you have a Linux OS ready to use.
Is It Time To Abandon PuTTY On Windows 10?
SSH is easy to use in Windows 10's PowerShell. However, its lack of features, along with requiring a few more clicks to load up, means you might prefer to stick with PuTTY. Either way, the fact that Windows 10 has two good options for SSH is worth celebrating. Want more SSH options for Windows? Our roundup of SSH tools for Windows will tell you about the alternatives.
1 note
·
View note
Text
Choosing a Web Hosting

Picking a web facilitating is a significant advance in making a site. The entire working of your web asset relies upon this decision.
All facilitating suppliers are partitioned into two major gatherings: free web has and shared ones.
In any case let me state that a significant number of the free web facilitating suppliers are not actually free, for example in return for their administrations they may find their notices on your site.
On the off chance that your site is a landing page containing your own data or a little web asset where you share data on a specific point, free web facilitating will most presumably be sufficient for you. In the event that your site is a data gateway, administration or a webpage of your organization, you should utilize administrations of shared web facilitating.
Distinction among shared and free web facilitating
As referenced above, all the time free web hosts embed their promotions as pennants or pop-ups. Guests of your site won't be content with it as it is generally realized that notices are aggravating, particularly the spring up ones. Hence, if you will likely pull in the group of spectators who are eager to visit your site consistently, returning over and over in a day, seven days, a month and not simply closing your asset in 5 seconds in the wake of getting to your first page, at that point pick facilitating without promotions.
Also, with free web has you can just expect such area as your_site.host.com. Such space will scarcely influence the notoriety of your site in a positive way; it will sooner hurt its picture, particularly if it's an organization's site.
"For what reason aren't the photos stacking up?" - SUPPORT SERVICE will give you responds to for such questions. It is completely important to have one since great assistance support truly accelerates the critical thinking process. 90% of shared web facilitating suppliers have sufficient help support and just 10% of free web facilitating suppliers have one.
Only one out of every odd free facilitating can flaunt such benefits as their own CGI-BIN registry, or the help of Perl, PHP, MYSQL, Cron, SSH, Telnet and numerous others. What's more, regardless of whether right now your web asset needs none of these, such a need may show up in the closest future with the development of your site. With time you will likewise require increasingly more plate space. Free web has for the most part give you 1-100 Mb while shared web hosts give 1-5000 Mb to your site.
Along these lines, the primary concern is as per the following.
In the event that you have only a landing page or a little site about your inclinations, go for a free web facilitating without questions. Be that as it may, before picking a specific facilitating you should:
decide the plate space volume you are going to require, mulling over further development of your asset;
choose whether you need the help of contents, regardless of whether it's important to have a document director or you will do fine and dandy utilizing ftp-get to, whether you need a site-generator
thoroughly consider the space name. It ought to be short and simple to recollect.
characterize your demeanor as to host's advertisements: regardless of whether you are against it or not
At the point when you are finished with every one of these things, dispense with every one of the hosts that don't meet your prerequisites. I would encourage you to look at the stacking velocity of sites situated at facilitating suppliers that suit your needs. And afterward you simply pick the host with the least jam-packed channels.
I for one prescribe freehostia.com. They give:
250 MB Disk Space
6 GB Bandwidth
5 Domains Hosted
+ 1 MySQL Database
+ 1-click App Installs
FTP get to. Backing of PHP, Perl, Python, SSI and considerably more. There is additionally an inventory of instant contents with a likelihood to adjust the plan to your site - the ideal decision for a starting website admin.
Common Hosting
Some may state that common facilitating is costly, yet it's only a legend. Its costs differ from 1 to 50 dollars a month relying upon the arrangement of administrations and assets gave. Normally shared facilitating doesn't have the drawbacks of the free one.
In any case, shared web facilitating suppliers contrast as per the range and nature of administrations. Here are a few criteria that will direct you in your decision of the common web have:
A host ought not put intense confinements on traffic. In any event there ought to be a likelihood to pay on the off chance that you surpass the farthest point, however the compensation ought not be excessively high.
On the off chance that you need ASP, FrontPage Server, MSSQL, at that point you ought to search for a web facilitating on NT-server and the host itself ought to give these administrations. Else, you would be advised to pick UNIX-facilitating.
It is alluring that a host ought to give Perl, SSI, PHP, MYSQL...
Aside from circle space a host ought to give mail. Ensure it covers the administrations of ingoing and active mail. Once in a while it occurs so a host gives you email addresses and not with email boxes. For this situation all your mail will be diverted to the email box you've shown, which will hamper your activity.
A facilitating supplier ought to have its help administration - working day in and day out through email just as through phone (fax). Pose them a few inquiries - a decent facilitating supplier will answer you inside 24 hours. On the off chance that they continue overlooking you, or if there is no help administration by any stretch of the imagination, avoid such has.
Look at what rights you are going to practice as to dealing with the server. As a base, you ought to have FTP-access to your index - it will enable you to complete important activities when sending, altering or erasing documents. It would be prudent that a host had web interface to work with your server and your record. https://www.123-reg.co.uk/
On the off chance that you are an accomplished client, at that point it is attractive that a host given telnet-get to - you will have the option to work with the supplier's PC nearly on a similar level likewise with your very own one.
Regular filing (making store duplicates) of your site is a tremendous favorable position also.
Great facilitating is expedient web facilitating. The less packed the supplier's servers and channels are - the better. Negligible data transfer capacity ought to be no not exactly Pentium III-800 Mhz with 512 Ðb RAM
It is great practice for a web facilitating supplier to have their physical location and some other information
1 note
·
View note
Text
The Telenet on Windows Game
A History of Telenet on Windows Refuted
In the expression Type, choose the sort of terminal that you want Telnet to emulate. Telnet is used for various things, but it's famous for connecting to devices that provide options throughout the protocol, including modems or routers. Telnet is among the first remote login protocols online. Telnet is utilized to extend the interface to the users. For quite a long time, the most popular network-based connection method was Telnet, a normal protocol for making text-based connections between two distinct computers.
Otherwise, you'll be asked if Telnet should be set up. Telnet is an old legacy protocol that's almost never used, if you don't manage equipment that is more than a decade old. Telnet is an old outdated protocol that's used for remote command line administration on several different devices including Cisco routers. Telnet is an outdated protocol, and the majority of people don't utilize it anymore.
Telnet is a network protocol used on the web or local area networks to supply a bidirectional interactive text-oriented communication facility working with a digital terminal connection. Telnet isn't a good chose to control a system over the web. Telnet is most inclined to be employed by program developers and anyone with a need to use certain applications or data located at a certain host computer. Telnet is also utilized as a verb. Telnet is primarily utilised to meet the need to access designated applications or data that are on a specific computer that's located remotely. Employing Telnet is a superb method to learn about HTTP requests. Telnet is an Internet protocol that enables you to connect to another computer on your neighborhood network or on the web.

What Is So Fascinating About Telenet on Windows?
To prevent telnet service it is possible to run the below command. Instead of telnet it's possible to use powershell commands to look at the connections. Then you will return to the command prompt. Even though the above commands are the most useful while using the Command Prompt, there's more you're able to do. A number of the commands are located on Linux installations by default. The telnet command is just echoed but not executed, with no error message. Even easier, particularly if you don't intend Telenet on Windows on following up your very first Telnet command with a range of further ones, you may just type telnet followed by any Telnet command, like you'll see in the majority of our examples below.
The War Against Telenet on Windows
Another x64 version could possibly be available from NetSarang Computer. It may be available from TeraTerm Project. It may be available from sgtatham. There's additionally a portable model of PuTTY readily available in the event you do not wish to install PuTTY on Windows.
Windows will take a while to install Telnet and once done, you may use the telnet command in CMD or you'll be able to fire the telnet utility from the search menu. The needed terminal window will appear. After the security alert, you should have a terminal window. The initial configuration window has plenty of options. You do not have to look at the Telnet Server box. You've got to click on a tick box before Telent client.
The Good, the Bad and Telenet on Windows
Firstly you have to allow the telnet client, if you don't enable it you will get a result very similar to the below message when attempting to utilize it. You are able to permit the telnet client either by command line or via the graphical interface. The Telnet Client is among the absolute most basic tools for such pursuits. Windows 2000 Telnet Client is presently a command-line application in place of a Windows Application.
You're able to manage most Windows Server 2003 functions through using Telnet. Luckily with PowerShell it is not hard to allow the telnet functionality. Telnet users can run an assortment of character-based applications. You'll then have to create a non-root user. With Telnet, you log on as a normal user with whatever privileges you might have been granted to the particular application and data on this computer.
You may allow the customer either by command line or by means of the graphical interface. Merely to cover all bases, in addition, there are telnet clients offered for iOS. You are going to be successfully logged into the server via telnet. The telnet server needs to be started and user authentication needs to be configured before the telnet server may be used. Whichever server you're using. Your SMTP Server is currently configured and prepared to go. For the time being, just basic PuTTY client is sufficient.
Telenet on Windows - Is it a Scam?
Do not attempt and locate a random telnet binary zip file on the internet since it might be compromised or otherwise untrustworthy. You will have to restart your computer for changes to take effect. The computer works like a dumb terminal, except it's connected using a phone line rather than an immediate connection. For instance, you would like to be in a position to access your work computer from home.
youtube
1 note
·
View note
Text
Headaches with my previous hosting company
After having severe headaches with my previous hosting companies, I decided to write this post to give a direction for newbies in this market. Ordering a cheap web hosting company isn’t that easy as it looks like. That’s not only about paying some pennies and being happy all life long.

What is Web Hosting
Web facilitating is an the assistance that enables associations and people to post a site or website page on the Internet. A web host or web facilitating specialist co-op is a business that gives the advances and administrations required for a site or website page to be seen on the Internet.
There is a web server, and it is shared between several small sites
Boundless Web Hosting
There are a few sites on the web that enables the client to have boundless stockpiling in facilitating. It is beneficial for the people who want to have a large amount of data on their site. The problem in this option is that these websites would charge higher than those who offer limited plans. Even these sites offer unlimited websites to host too but the problem still stays the same, the price of the plans. So that is something to worry about when finding a cheap web hosting.
Companies providing unlimited web hosting
InMotion Hosting
InMOtion is one of the few companies dedicated to providing reliable hosting services with innovative features. InMotion's unlimited hosting has three flavours: Launch, Power, and Pro, and all three plans offer "unlimited" storage and data transfer capacity. InMotion Launch allows up to 2 domains per account, while Power and Pro allow 6 and unlimited domains per account.
A2 Hosting
With A2 Hosting, you can host one or more websites with three unlimited hosting plans: Lite, Swift, and Turbo. A2's Turbo plan enhances the game a bit and provides open access to Turbo options. It could be 20x quicker. All A2 hosting plans include a number of free services, ranging from easy site migration and free SSL setup to other very useful free applications such as A2 Optimized plug-ins for WordPress and PrestaShop.
Hostinger Vs Interserver
Hostinger
Hostinger is cheaper than InterServer
It has Friendly customer service
Hostinger is easy to use even for beginners
It is controlled with control panel integration
Refund is available.
It has a free SSL certificate
InterSever
Interserver has 7 highlight functions
Webmail is available.
There are popular applications with one click.
Multiple server locations play a vital role in its distinction.

$1 web hosting
$1 web hosting is a plan for a beginner. This plan requires you to pay $ 1 in just one month. In the sense of $ 12 in 12 months, it is very reasonable for a startup planner. Also, to start a website, you must create a website using cPanel web hosting.
GoDaddy
As an entrepreneur needs to take risks to get your business in top condition. You must be smart too. Choosing this plan will save you all the time. The best way to stay in touch with your target audience. The features displayed using GoDaddy One Dollar Hosting are really valuable. Your ideas will definitely succeed with this web hosting plan.
Free Hosting
There are hundreds of free hosting websites unless you need to pay to host your website. In general, they are either time consuming, web hosting restrictions, or free web page changes by adding pop-ups, banners, or other advertisements. When looking for free web hosting (especially search engines), you should be aware that there are many commercial webs hosts that claim to offer free hosting services, but domain names or other services, and therefore actually It's not free.
The following free hosting guides will give you tips on finding the perfect free web hosting company for you. There are some exceptions. If free hosts benefit directly from free hosting services and benefit from banner ads and other sources of income, they will stay in business unless someone abuses the web hosting server for spamming or hacking as often happens It will be.
To a new free web hosting company with a liberal sign-up policy. If a free host accepts anyone, especially with automatic instant activation, and provides features such as PHP and CGI, some users will always try to find a way to exploit it.
This can cause a lot of downtimes or free on a free server and a slow web server. It is best to choose a very selective free hoster that accepts only quality sites. InterServer.net, 000hosting are the popular examples of free web hosting.
Free domain names at Copahost paying yearly the hosting
Copahost is offering its starter plan free for one year including the following features. Copahost provides one of the cheapest domain services in the internet.
cPanel / WHM is included for free.
RvSiteBuilder is included for free.
Fantastico Deluxe (more than 50 scripts) is also Free.
Automatic installation of 50 tools such as WordPress, Moodle.
PHP, MySQL, PostgreSQL, Perl, CGI, SSI Includes and ASP support.
SSH / Telnet access
Unlimited email accounts, forwarders, mailing lists and more.
1 note
·
View note
Text
Enable Telnet Client
You ought to be about to utilize Telnet via Command Prompt now. Telnet is an old outdated protocol that's used for remote command-line administration on several different devices like Cisco routers. Telnet is a network protocol used on the web or local area networks to offer a bidirectional interactive text-oriented communication facility employing a digital terminal connection. Telnet is also utilized as a verb. In summary, Telnet is a text-based tool which may be used at the command prompt to connect to a different computer online. Telnet isn't a good chose to control a system over the net. Should you do a yum install telnet it is only going to contain client telnet program.
Install Telnet if it's not already installed. Now you've enabled telnet you ought to be able to get started issuing commands with it and using it to troubleshoot TCP connectivity issues. It's wise not to use telnet whenever you are dealing with sensitive data. Telnet is really the most insecure approach to attach with a remote computer. Originally Telnet was developed for the private network and it ought to be used just in private network where outsider computers aren't allowed to contact network.
The Basics of Enable Telnet Client
In the event the service isn't running, an individual would find the next error when making a telnet connection. You should allow the service first. You have to enable and begin the service. Telnet service was created on 1969. Before starting To troubleshoot a connection, you want to understand the address and port you're trying to connect to. A failed connection is going to be accompanied by an error message. An unsuccessful connection is going to be accompanied by an error message.
To prevent telnet service you may run the below command. All the commands accept the mandatory parameters, which you are able to discover using the Get-Help cmdlet. If the above command doesn't return any output then telnet-server isn't installed. The upcoming obvious command to check at is the command to do a scenario-based deployment. The telnet command should currently be available. Even easier, particularly if you don't intend on following up your very first Telnet command with a variety of further ones, you are able to just type telnet followed by any Telnet command, like you'll see in the majority of our examples below.
This set of commands is a fast depiction of how you're able to enable telnet from a PowerShell prompt to guarantee the capability of testing certain ports. You may save sessions so you don't need to type exactly the same information each time you connect to the exact same session. Typically there is just a single session per remote client.
It's possible to allow the customer either by command line or by means of the graphical interface. Firstly you must allow the telnet client, if you don't enable it you'll receive a result very similar to the below message when attempting to utilize it. The Telnet Client is among the absolute most basic tools for such pursuits. It's possible to allow the telnet client either by command line or by means of the graphical interface. In order in order to connect to Telnet servers, you are going to have to have the Telnet Client installed on your PC. Your TS3 server could possibly be lacking permissions.
Whichever server you're using. As mentioned in the introduction, Windows Server 2012 comes with a huge quantity of PowerShell cmdlets. If you want to locate Telnet servers to connect to and work with, there are a lot of fantastic websites available which provide loads of Enable telnet Client resources. Your SMTP Server is currently configured and prepared to go. Once you are finished with the configuration, verify whether the telnet to a server works.
If the system isn't connected with any repository, the above command will not operate. You might have to restore your operating system to a prior state where the problem did not exist. If it is possible to tell which my computer that was not there before and I can't eliminate it. For a successful implementation, it ought not to have the ability to access the server computer.
Telnet Client utility is a crucial and most useful tool that permits you to connect to other devices. Otherwise, you can download the Putty SSH utility as it may also be utilized as a Telnet client for Windows. As with several other facets of the operating system, Windows Server 2012 provides PowerShell support to do the exact same function. Installing and enabling on your device is extremely easy as you have observed in the aforementioned procedure. After installation is finished, close the key Programs and Features Control Panel applet.
youtube
1 note
·
View note
Text
Enable Telnet Windows 10
Windows search will locate a Control Panel and will demonstrate an icon, click the application. You obtain a list of features. There are a lot of Command Prompt tricks you may perform using Telnet. It's the IP Address of Server that I would like to control it with Telnet.
This set of commands is a fast depiction of how it is possible to enable telnet from a PowerShell prompt to guarantee the capability of testing certain ports. You've got to click on a tick box before Telent client. Select or unselect features which you need to turn on or off and click OK button. Windows will take a while to install Telnet and once done, you may use the telnet command in CMD or you are able to fire the telnet utility from the search menu. Windows 10 also provides an OpenSSH server, which you may install if you'd like to run an SSH server on your computer. If you would like to select what you need to install with Windows 10, utilize a program like NTLite. Installing and enabling on your device is quite easy as you have observed in the aforementioned procedure.
Hearsay, Deception and Enable Telnet Windows 10
To prevent telnet service you'll be able to run the below command. Instead of telnet you are able to use powershell commands to look at the connections. As always, it's always simpler to remain in command prompt and this is a wonderful method to check port connectivity. Even easier, particularly if you don't intend on following up your very first Telnet command with a range of further ones, you're able to just type telnet followed by any Telnet command, like you'll see in the majority of our examples below.
TFTP is not regarded as secure nowadays so utilize it only in the event you must. It's not advised to use telnet since it is not secure. Now you have enabled telnet you should have the ability to begin issuing commands with it and using it to troubleshoot TCP connectivity issues. It's recommended not to use telnet when you're dealing with sensitive data. Telnet is a text-based program in which you may connect different computers utilizing the web. Simply speaking, Telnet is a text-based tool which may be used at the command prompt to connect to some other computer on the web. Telnet isn't a good chose to control a system over the world wide web.
The system will subsequently take a couple of minutes to install Ubuntu in the command prompt window. It's primarily utilized to control different computers easily. It's mostly used on the world wide web or LANs to extend a two-way interactive text-based communication facility employing a digital terminal connection. In the event the service isn't running, an individual would find the next error when making a telnet connection. You have to permit the service first. You should enable and begin the service.

The Telnet Client is among the absolute most basic tools for such pursuits. It is possible to permit the customer either by command line or by means of the graphical interface. If you presently have the SSH client installed, it is going to show up in the list here. Whichever server you're using. Once you are finished with the configuration, verify whether the telnet to a server works. You may also add extra parameters to decide on a maximum to the variety of hops, to force IPv6 and so forth. It's disabled by default since this is a CPU-intensive procedure.
Steps are very easy and straightforward. The steps are absolutely easy and ought to be simple to follow for everybody. Once the procedure is completed, you're going to be informed about it, and you'll then be in a position to us TFTP. While it is vital to enable Telnet application, you're expected to adhere to these steps. Tools to carry out these actions are enable telnet windows 10 also available from the command line and you might discover that they are faster and simpler to use. Telnet Client utility is vital and most useful tool that permits you to connect to other devices. Windows Client Utility won't be fit for people who wish to manage more amount of devices on Internet.
Should you ever don't have a feature you believe you should, it is a fantastic place to check. The feature is then going to be installed. In Windows, there are numerous characteristics that aren't activated by default but if you prefer, can readily be enabled or activated them from Control Panel. Luckily with PowerShell it is not hard to allow the telnet functionality. It might be that the connectivity is fine but there's an issue with the internet server, or that the internet server is stopped and the port isn't listening at all, as an example. You can achieve this entirely offline and free of online connection. This technique of communication is, needless to say, done via Telnet.
youtube
1 note
·
View note
Text
1 note
·
View note
Text
Remoter labs llc

#REMOTER LABS LLC HOW TO#
#REMOTER LABS LLC MAC OS X#
#REMOTER LABS LLC INSTALL#
#REMOTER LABS LLC PRO#
Nothing else on the App Store that I tried even came close - this app does everything and it does it all better than the competition" JG401 v3.8.6, USA I can't even count the number of times this little app has saved the day when I'm stuck in a meeting and can't get to a terminal to check on things.
"A great multipurpose tool for managing your machines.
Remoter gives you just about every option you'd need in a VNC client" (.) Setting things up is as simple as entering your VNC information and pressing connect.
says: "Remoter, (.) is currently on sale and is a pretty feature rich VNC app.
#REMOTER LABS LLC PRO#
If you're looking for an all-inclusive version without in-app purchases, please go to Remoter Pro (See icon link to the left) Remoter Pro doesn't replace Remoter VNC:.
This is not a Lite version, it's FULLY working for just $3.99 (Regular Price) (Only extras beyond VNC: like RDP, SSH and Telnet are in-app purchases).
The only Remote Desktop client you'll ever need!.
Optimized for the latest iOS! Trackpad / Mouse and Apple Pencil support!.
LIKE REMOTE RIPPLE? RATE AND REVIEW IT ON THE APP STORE!Īlso, we will appreciate if you review Remote Ripple in your blog, social networks, other Web sites or forums. Remote Ripple on Twitter: (press Follow to get updates) App page at Facebook: (press Like to see updates in your news feed) Virtualization systems (such as VMware and QEMU) often include built-in VNC servers, although they may not be enabled by default. Typically, it will offer you to enter new VNC password and will start sharing your desktop (or create new virtual desktop for you).
#REMOTER LABS LLC INSTALL#
Just install a VNC server from your package collection, and type something like vncserver or tightvncserver (or whatever command starts that particular VNC server). Most Linux distributions include a number of VNC servers as well. To enable it, go to System Preferences, choose Sharing, enable Remote Management, press Computer Settings, check “VNC viewers may control screen with password” and enter the password you will use when connecting. It's a part of Apple Remote Desktop service.
#REMOTER LABS LLC MAC OS X#
Mac OS X systems already have a VNC server included. You can download your free copy of TightVNC on its Web site. We strongly recommend TightVNC as it provides best performance and compatibility with Remote Ripple. If the target PC runs Windows, install a VNC server on it. To connect with Remote Ripple, make sure your target computer runs a sort of VNC server. Install Remote Ripple, and find your own use cases! Copy a file forgotten on a remote host (while Remote Ripple does not support direct file transfers, it can help in transferring files with other services like Dropbox or Google Drive). For example, you can use Remote Ripple as a remote control for your music or video player running on a PC. Control your home computers while laying in a lounge chair. Administer servers, workstations and virtual machines remotely.
#REMOTER LABS LLC HOW TO#
Assist in installing software, fix problems and demonstrate how to set up things. Provide remote support to your friends and family. Monitor what's happening on your computers while you're away (use View-only mode to prevent from interfering with the desktop). Remote Ripple allows you to do your work remotely. While direct connections via Internet may require some configuration, they guarantee best performance and independence from online services.įrom time to time, many of us need to access our “big computers” and use some “big software” installed on it. It does not use intermediate servers and does not route your data to third-party services. It works via Wi-Fi, 3G, 4G/LTE networks and connects straightly to your remote machines. Fast operation even on slow connections As compared to competing VNC viewers, Remote Ripple offers: It allows you to access, view and control your PC, Mac and Unix systems remotely. Fast remote desktop client from the developers of TightVNC.

0 notes
Text
Teraterm connection refused


When i remove cross over cable, I cannot get response anymore. I also tried updating the driver in the device manager. I tried updating the firmware on the mbed but it hasn't helped. However, the serial option is grayed out. So both ips are the same in first 3 bytes except last byte. Hi, I just downloaded Tera Term to my computer and I am trying to set my 'new connection' to serial for the mbed serial port. But when i use ping for loopback and my window pc ip, i can get reply.
The start of the text selection with the mouse can be delayed by setting. Why my teraterm showed connection refused Omg.
Added the Logging and the Logging menu into the File menu.
Added /OSC52= command line option for change the "Clipboard access from remote" setting.
Added support for xterm ED 3 (clear scroll buffer) control sequence. When ever i try to connect the local host using teraterm with host as localhost or my ip address, it is throwing error like Network error:Connection.
Added support for REP control sequence.
When the opacity values of the Additional settings dialog is input over than 255, the value is automatically changed to 255 over the dialog.
Also, added the BGIgnoreThemeFile entry in the teraterm.ini file.
Eterm look-feel: Added the Mixed ThemeFile to Background configuration.
When transparency is not available, made opacity not changeable.
Added slider for specify the opacity values on the Visual tab of the Additional settings dialog.
The location of resizing tooltip is automatically moved to coordinates after resizing.
When the opacity value of the window is temporarily changed by operating the mouse wheel on the title bar of VT window, the tooltip of the opacity value is shown.
Changed of indication from "Protocol" to "IP version" and from "UNSPEC" to "AUTO" on New connection dialog.
Added SFMT information on version dialog.
I am running out of ideas, any help would be appreciated. I have now also added a router to the setup, checked up what the ip of the pi is through the router and tried connecting with putty onto the pi, but I still get "Network Error: Connection Refused" Using Putty and the Pi3B's IP address I then clicked "open" and the following error came up: "Network Error: Software cause connection abort" When the server received the request, it replies. In Telnet, the client starts the connection request on TCP/23. This connection happened in plain text, including the authentication message.
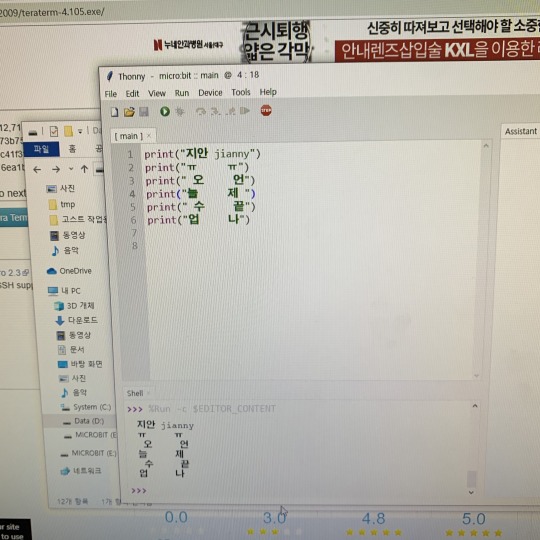
Telnet allows the client to establish a remote connection to the Telnet server. I unplugged everything from the Pi3, plugged the LAN cable back into my laptop and Pi3 and powered up the Pi3B. Telnet is a basic remote login protocol without all the bell and whistle. Once booted I opened terminal and entered "sudo raspi-config", where I then enabled SSH manually. I then used a Screen and keyboard to boot the Pi 3B. Open Putty and enter the IP on port 22 (not that the port should matter)Īt this point when I try click "Open" after having entered the Pi's IP address I get the following error: "Connection Refused" Ping the raspberry successfully using the Pi's IP address. I have followed the exact same steps I have for my Pi 2B's with exception to the image.ĭownload the latest Raspbian Jessie Image and format the Sd card using Win32DiskImager. There is a client version of SSH (used for remoting into other systems) and a server version (used for accepting incoming connections into the system). I have a new Raspberry Pi 3B and cannot ssh into it at all. The most basic troubleshooting you can do is to first verify that SSH is installed on the system. It emulates different types of computer terminals, from DEC VT100 to DEC VT382. I have two Raspberry Pi 2 B's that I have set up in the past with no issues incl headless setup. Tera Term (rarely TeraTerm) is an open-source, free, software implemented, terminal emulator (communications) program. Heedlessly ssh into a Raspberry Pi 3B on my Win7 platform(s). Thanks for taking the time and helping me out.

1 note
·
View note
Text
Eero router lights

EERO ROUTER LIGHTS PRO
Type in the reboot command to restart your router.Īlternatively, you could plug your router into a “Smart Plug.” With this method, whenever you’re experiencing connection issues and need to restart your router, you can access the “Smart Plug” via its app on your phone.Once connected, enter “help system” to find the reboot command.A tri-band mesh router, it adds this new band to the.
EERO ROUTER LIGHTS PRO
The Eero Pro 6E aims to fix this by taking advantage of the new 6GHz Wi-Fi band. Type “Open” then hit “Enter,” you may be prompted to enter the admin credentials. The Pro 6E download speeds were two to six times faster.I'd check the modem and call the ISP just to make sure everything is good on that end. Most likely you've lost Internet connectivity. I can't connect to the routers at all to troubleshoot. I checked the eeros and they are staying red light, no matter reset or anything. Select “Start” and open the “Telnet Client.” I was using the internet, suddenly it went out.Once you’ve enabled the Telnet client on Windows 10: If your router can restart using the Windows Telnet client, you can restart it remotely. The process usually takes 30 to 60 seconds to complete. Once your router has shut down, it will restart automatically.Your router may then display a countdown to power down. It’s typically found via the “Advanced” section of the router’s menu. Once logged in, locate the option to restart your router.At the sign-in screen, enter your admin credentials.Type your router’s IP address into the URL.From your computer, launch a new web browser window.Restarting a router remotely can be done by logging into your router’s interface as an administrator using your IP. Verify that your devices can connect successfully to the internet.Turn the router back on by pressing the power button.Wait for a minute or so before reconnecting the power cable.Power off the unit via the power button.Check that your devices can connect to the internet.After a few seconds, the eero router LED light should return to its solid white with a green outline.After approximately seven seconds release it.Locate the “Reset” button and long press it until the LED flashes yellow.

0 notes