#change password in RDP
Explore tagged Tumblr posts
Text
Embracing the Remote Work Revolution with RDPExtra: Navigating the Future of Work

Remote Desktop Protocol (RDP) has emerged as a cornerstone technology for remote work, enabling seamless access to desktops and applications from any location. RDPExtra takes this functionality to the next level by providing a comprehensive suite of features tailored to the evolving needs of modern businesses. Whether it’s accessing Windows Server environments or managing Linux-based systems, RDPExtra offers a unified platform for efficient remote collaboration and productivity.
One of the key advantages of RDPExtra is its compatibility with both Linux and Windows Server environments. This versatility allows businesses to leverage their existing infrastructure while seamlessly integrating remote work capabilities. Whether you’re running a Linux-based development environment or a Windows Server deployment, RDPExtra provides a unified solution for remote access and management. This flexibility is especially valuable in today’s hybrid IT landscape, where organizations are increasingly adopting multi-platform environments to meet diverse business needs.
For businesses looking to buy RDP solutions, RDPExtra offers a cost-effective and scalable option. By providing a comprehensive set of features at competitive pricing, RDPExtra enables organizations of all sizes to embrace the remote work revolution without breaking the bank. With flexible licensing options and transparent pricing models, RDPExtra ensures that businesses can scale their remote work infrastructure according to their evolving needs, without being locked into rigid contracts or costly commitments.
Security is a top priority in any remote work environment, and RDPExtra takes this aspect seriously. With robust encryption protocols and advanced security features, RDPExtra ensures that sensitive data remains protected during remote access sessions. From encrypted communications to multi-factor authentication, RDPExtra provides multiple layers of defense against cyber threats, safeguarding businesses from potential security breaches and unauthorized access. Additionally, RDPExtra offers the ability to change passwords in RDP sessions seamlessly, enhancing security posture and compliance with industry regulations.
Beyond security, RDPExtra prioritizes user experience, ensuring that remote work remains efficient and seamless. With a user-friendly interface and intuitive controls, RDPExtra makes it easy for employees to access their desktops and applications from any device, without compromising productivity. Whether you’re working from a laptop, tablet, or smartphone, RDPExtra provides a consistent and responsive experience, enabling employees to stay connected and productive, no matter where they are.
In conclusion, RDPExtra is at the forefront of the remote work revolution, empowering businesses to navigate the future of work with confidence. By harnessing the power of Linux and Windows Server, coupled with the convenience of Windows RDP, RDPExtra offers a comprehensive solution for remote access and management. Whether you’re looking to buy RDP solutions or enhance the security of your remote work infrastructure, RDPExtra has you covered. With its flexible licensing options, advanced security features, and intuitive user experience, RDPExtra is the ultimate ally for businesses seeking to thrive in the era of remote work.
0 notes
Text
Top 5 Security Misconfigurations Causing Data Breaches

In the ever-escalating arms race of cybersecurity, headlines often focus on sophisticated malware, nation-state attacks, and zero-day exploits. Yet, time and again, the root cause of devastating data breaches isn't a complex, cutting-edge attack, but rather something far more mundane: a security misconfiguration.
These are the digital equivalent of leaving your front door unlocked, the windows open, or a spare key under the doormat. Simple mistakes or oversights in the setup of software, hardware, networks, or cloud services create gaping vulnerabilities that attackers are all too eager to exploit. Getting the basics right is arguably the most impactful step you can take to protect your assets.
Here are the top 5 security misconfigurations that commonly lead to data breaches:
1. Default, Weak, or Unmanaged Credentials
What it is: Using default usernames and passwords (e.g., admin/admin, root/root), not changing credentials after initial setup, or enforcing weak password policies that allow simple, guessable passwords. It also includes failing to disable old user accounts.
How it leads to a breach: Attackers use automated tools to try common default credentials, brute-force weak passwords, or leverage stolen credentials from other breaches. Once inside, they gain unauthorized access to systems, data, or networks.
Real-world Impact: This is a perennial favorite for attackers, leading to widespread compromise of routers, IoT devices, web applications, and even corporate networks.
How to Prevent:
Change All Defaults: Immediately change all default credentials upon installation.
Strong Password Policy: Enforce complex passwords, regular rotations, and most critically, Multi-Factor Authentication (MFA) for all accounts, especially privileged ones.
Least Privilege: Grant users only the minimum access required for their role.
Regular Audits: Routinely review user accounts and access privileges, disabling inactive accounts promptly.
2. Unrestricted Access to Cloud Storage Buckets (e.g., S3 Buckets)
What it is: Publicly exposing cloud storage containers (like Amazon S3 buckets, Azure Blobs, or Google Cloud Storage buckets) to the internet, often accidentally. These can contain vast amounts of sensitive data.
How it leads to a breach: Misconfigured permissions allow anyone on the internet to read, list, or even write to the bucket without authentication. Attackers simply scan for publicly exposed buckets, download the data, and exfiltrate it.
Real-world Impact: This has been the cause of numerous high-profile data leaks involving customer records, internal documents, proprietary code, and financial data.
How to Prevent:
Principle of Least Privilege: Ensure all cloud storage is private by default. Only grant access to specific users or services that absolutely need it.
Strict Access Policies: Use bucket policies, IAM roles, and access control lists (ACLs) to tightly control who can do what.
Regular Audits & Monitoring: Use cloud security posture management (CSPM) tools to continuously scan for misconfigured buckets and receive alerts.
3. Open Ports and Unnecessary Services Exposure
What it is: Leaving network ports open that shouldn't be (e.g., remote desktop (RDP), SSH, database ports, old services) or running unpatched services that are exposed to the internet.
How it leads to a breach: Attackers scan for open ports and vulnerable services. An exposed RDP port, for example, can be a direct gateway for ransomware. An unpatched web server on a commonly used port allows for exploitation.
Real-world Impact: This is a common entry point for ransomware attacks, network intrusion, and data exfiltration, often facilitating lateral movement within a compromised network.
How to Prevent:
Network Segmentation: Isolate critical systems using firewalls and VLANs.
Port Scanning: Regularly scan your own network externally and internally to identify open ports.
Disable Unnecessary Services: Remove or disable any services, applications, or protocols that are not strictly required.
Strict Firewall Rules: Implement "deny by default" firewall rules, only allowing essential traffic.
Patch Management: Keep all exposed services and applications fully patched.
4. Missing or Inadequately Configured Security Headers/Web Server Settings
What it is: Web applications and servers often lack crucial security headers (like Content Security Policy, X-XSS-Protection, HTTP Strict Transport Security) or are configured insecurely (e.g., directory listings enabled, verbose error messages, default server banners).
How it leads to a breach: These omissions can expose users to client-side attacks (Cross-Site Scripting - XSS, Clickjacking), provide attackers with valuable reconnaissance, or allow them to enumerate files on the server.
Real-world Impact: Leads to website defacement, session hijacking, data theft via client-side attacks, and information disclosure.
How to Prevent:
Implement Security Headers: Configure web servers and application frameworks to use appropriate security headers.
Disable Directory Listings: Ensure web servers don't automatically list the contents of directories.
Minimize Error Messages: Configure web applications to provide generic error messages, not detailed technical information.
Remove Default Banners: Conceal server and software version information.
Web Application Firewalls (WAFs): Deploy and properly configure WAFs to protect against common web exploits.
5. Insufficient Logging and Monitoring Configuration
What it is: Not enabling proper logging on critical systems, misconfiguring log retention, or failing to forward logs to a centralized monitoring system (like a SIEM). It also includes ignoring security alerts.
How it leads to a breach: Without adequate logging and monitoring, organizations operate in the dark. Malicious activity goes unnoticed, attackers can dwell in networks for extended periods (dwell time), and forensic investigations after a breach are severely hampered.
Real-world Impact: Lengthens detection and response times, allowing attackers more time to exfiltrate data or cause damage. Makes it difficult to reconstruct attack paths and learn from incidents.
How to Prevent:
Enable Comprehensive Logging: Log all security-relevant events on servers, network devices, applications, and cloud services.
Centralized Log Management (SIEM): Aggregate logs into a Security Information and Event Management system for correlation and analysis.
Define Alerting Rules: Configure alerts for suspicious activities and ensure they are reviewed and acted upon promptly.
Regular Review: Periodically review logs and audit trails for anomalies.
The common thread running through all these misconfigurations is often human error and oversight compounded by increasing system complexity. While cutting-edge AI and advanced threat detection are crucial, the simplest and most impactful wins in cybersecurity often come from getting the fundamentals right. Regularly auditing your environment, enforcing strict policies, and embracing automation for configuration management are your best defenses against these common, yet devastating, vulnerabilities. Don't let a simple oversight become your next breach.
0 notes
Text
PyRDP And Rogue RDP: Automating Malicious RDP Exploits

PyRDP automates file exfiltration and clipboard theft for rogue RDP campaigns. This method allows unnoticed spying via hacked remote desktop sessions.
Remote Desktop Protocol?
The Windows service Remote Desktop Protocol (RDP) allows Terminal Servers and Clients to communicate. This system uses “virtual channels” to convey data from presentations, keyboard and mouse actions, clipboards, and serial devices. Traditional RDP security research has focused on how attackers with authentic victim credentials may get full GUI access to a machine.
Innovative New Campaign RDP Use
Google Threat Intelligence Group (GTIG) uncovered a new phishing campaign tied to UNC5837, a suspected Russian espionage actor, in October 2024. This effort targeted European military and political institutions using signed.rdp file attachments. Instead than stressing interactive sessions, this marketing ingeniously used two obscure RDP protocol features:
Resource redirection maps victim file systems to attacker servers.
RemoteApps: Giving victims access to attacker-controlled applications.
RDP proxy programs like PyRDP may automate dangerous actions like file exfiltration and clipboard gathering. This approach is called “Rogue RDP.” This effort focused on file theft and espionage.
Key RDP Features
.rdp configuration files: .rdp configuration files can change RDP session functionality by configuring IP addresses, display settings, and certificate options. These files setup an RDP session like the traditional GUI (mstsc.exe). The observed campaign used phishing emails with malware-signed.rdp file attachments. This file allowed the adversary to read and write all of the victim's discs and clipboard contents and create an RDP connection from the victim's computer.
The resource redirection capability lets remote desktop users utilise local peripherals and devices. This includes printers, keyboards, mouse, discs, serial connections, hardware keys, audio equipment, and clipboards. The observed campaign's malicious.rdp file sent all discs, printers, COM ports, smart cards, WebAuthn requests, clipboards, and POS devices to the attacker's C2 server. Microsoft's "virtual channels" allow resource redirection and RDP packet transmission.
RemoteApps: This optional RDP feature lets remote server apps run as windowed programs on the client (victim). Thus, a malicious remote program that isn't installed on the victim's PC may seem local. Malicious.rdp files in RemoteApp campaigns presented users with a fake “AWS Secure Storage Connection Stability Test” app.
This application was hosted on the attacker's RDP server and looked local. The session displays this application alone when remoteapplicationmode is 1. RemoteApp requires RDP server resources, yet mapped victim CDs allow RemoteApp access. This malware also received the victim's Windows environment variables as command-line arguments.
Function of PyRDP
PyRDP, an open-source Python-based MiTM RDP proxy toolkit, is used offensively. Even if its use in the claimed campaign is unverified, its automation makes it a feasible weapon for such attacks. PyRDP relays the victim-RDP server connection to boost capabilities:
Possible NTLM hash and plaintext password theft.
The RDP server executes commands, not the victim's machine.
Note the user's clipboard.
Mapping and maybe scraping drives.
Controlling, recording, and broadcasting RDP sessions.
PyRDP uses fine-grained control over built-in functionality rather than RDP protocol vulnerabilities. PyRDP might have been used in the campaign under observation to bypass the user login screen and reveal the malicious RemoteApp by giving credentials. Potential features include clipboard capture and automatic file exfiltration.
Security Risks and Effects
This campaign highlights unknown RDP security risks. It shows how attackers may employ lawful characteristics for evil, making identification and incident response harder due to fewer forensic artefacts than other attack routes. Even without direct command execution on target PCs, the attackers were able to access victim discs, steal files, collect clipboard data (including passwords), and steal environment variables. Signed.rdp files may bypass security alarms, reducing attack suspicion.
Advice for Defenders
The sources give several ways to fortify systems and identify these attacks:
Log Artefacts: Monitor registry keys (HKU\…\Microsoft\Terminal Server Client\Servers) and Windows Event Logs (Event IDs 1102, 1027, 1029) to comprehend an attacker's infrastructure. Increased logging (e.g., Sysmon) can track file write activity from C:\Windows\system32\mstsc.exe on redirected discs, however transient files should not be included. You may also use regex patterns to identify.rdp files run from email attachments.
System hardening: Network-level blocking of outgoing RDP traffic to public IPs, registry-based resource redirection disablement, and Group Policy-based granular RDP policy configuration (e.g., resource and clipboard redirection management, enforcing Network Level Authentication, and blocking.rdp file extensions as email attachments) can improve security.
Questionable RDP configuration files with a base64 encoded Let's Encrypt certificate or that allow resource redirection and RemoteApps can be identified using YARA criteria.
Final comments
The “Rogue RDP” campaign shows how to innovate with old tactics. The risk is dishonestly using actual RDP capabilities, not protocol weaknesses. To defend against such assaults and grasp PyRDP's potential, one must understand RDP features, notably resource redirection and RemoteApps.
#technology#technews#govindhtech#news#technologynews#cloud computing#PyRDP#Remote Desktop Protocol#Remote Desktop Protocol RDP#RDP proxy#RDP sessions#RDP#RDP feature
1 note
·
View note
Text
RDP to Windows Login Screen
I was recently resurrecting an old demo environment in AWS which consisted of a few EC2 virtual machines, however upon trying to login, I quickly realised that the account password had expired and by default Windows Remote Desktop doesn’t have an ability to change passwords since you’re not presented with the logon screen. We didn’t have console access nor was there any other remote access like…
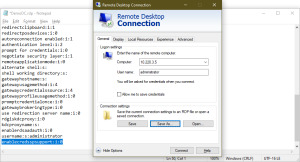
View On WordPress
0 notes
Text
The evolution of healthcare ransomware attacks - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-evolution-of-healthcare-ransomware-attacks-cybertalk/
The evolution of healthcare ransomware attacks - CyberTalk


By Zac Amos, Features Editor, Rehack.com.
In recent years, ransomware has emerged as a critical threat to the healthcare industry, with attacks growing in frequency, sophistication and impact. These cyber assaults disrupt hospital operations, compromise patient safety and undermine data integrity.
Understanding how ransomware tactics have evolved — from basic phishing schemes to complex, multi-faceted attacks — enables healthcare organizations to develop more robust defenses. Staying informed about the latest trends and techniques that cyber criminals use allows healthcare providers to safeguard their systems and ensure the continuity of care.
Initial ransomware attacks
Early ransomware tactics in healthcare were relatively rudimentary but still impactful. The first known ransomware attack — the PC Cyborg or AIDS Trojan — occurred in 1989 and targeted roughly 20,000 researchers and medical institutions. This attack involved distributing infected floppy disks that encrypted file names and paying a ransom to unlock them.
Although primitive by today’s standards, this attack highlighted the vulnerability of healthcare systems. Hospitals faced significant disruptions, affecting patient care and operations. This early incident underscored the potential havoc that ransomware could wreak on the healthcare sector. It set the stage for more sophisticated future threats.
Evolution of attack vectors
The evolution of ransomware in healthcare has seen a significant shift; from simple phishing attacks to sophisticated social engineering techniques. Initially, attackers used basic phishing emails to trick individuals into downloading malicious software.
However, as defenses improved, cyber criminals adapted by using more advanced social engineering tactics. These methods involve conducting detailed research on targets, the creation of personalized messages and placing phone calls, as to gain trust and infiltrate systems.
Alongside this, Remote Desktop Protocol (RDP) exploits have surged. These exploits allow attackers to access healthcare networks remotely by exploiting weak passwords and unpatched systems.
The healthcare sector has also seen a rise in exploited vulnerabilities in medical devices and the IoT. Cyber criminals have increasingly targeted these interconnected systems — which often lack robust security measures — to launch attacks.
This trend was particularly evident in the fourth quarter of 2023. The healthcare industry accounted for 16% of all ransomware attacks, making it the second-most targeted sector during this period. Exploitation of vulnerabilities can disrupt medical services and poses significant risks to patient safety. In turn, this highlights the urgent need for enhanced cyber security measures in healthcare.
Advanced encryption and evasion techniques
As ransomware has evolved, attackers have developed more complex encryption methods to secure healthcare data more effectively. One notable tactic is double extortion, where cyber criminals encrypt data and threaten to release sensitive information if the victim doesn’t meet their demands. This dual threat has increased the pressure on targeted organizations.
Further, 74% of Chief Information Security Officers believe that AI-powered cyber threats, including advanced ransomware, significantly impact their organizations. Attackers are also implementing polymorphic malware, which constantly changes its code to avoid detection by traditional security systems. Techniques like this make it challenging to combat sophisticated threats.
Targeting larger and more critical institutions
Ransomware attackers have shifted from targeting small clinics to targeting large hospitals and extensive healthcare networks, resulting in more significant disruptions and higher ransom demands than previously. Larger institutions have substantial financial resources, which makes them attractive targets for cyber criminals seeking substantial payouts.
The financial impact of the attacks on larger healthcare organizations is profound. In 2023, experts reported data breaches costing an average of $10.93 million each. This cost increase underscores ransomware’s severe financial strain on healthcare providers. It affects their ability to deliver essential services and invest in further security measures.
Ransomware-as-a-service
The rise of Ransomware-as-a-Service (RaaS) platforms has contributed to the proliferation of ransomware attacks in the healthcare sector. These RaaS groups operate on various business models, including monthly subscriptions, one-time license fees, affiliate programs or pure profit-sharing arrangements.
Offering user-friendly interfaces and comprehensive support, RaaS has lowered the barrier to entry for cyber criminals. It even enables those with zero technical expertise to launch sophisticated attacks. This democratization of ransomware has led to an increase in the frequency and diversity of attacks. It poses a more significant threat to healthcare organizations that must now defend against an extremely broad range of adversaries.
Collaboration and sophistication of cyber criminals
The formation of ransomware syndicates and partnerships has further expanded the threat landscape in healthcare. Cyber criminal groups now share resources and intelligence, enhancing their capabilities and effectiveness. In fact, some RaaS operators provide ongoing technical support and grant access to private forums where hackers exchange tips and information, fostering a collaborative environment.
This collective effort allows more sophisticated attacks, as cyber criminals leverage advanced threat intelligence and surveillance to identify vulnerabilities and tailor their strategies. Consequently, healthcare organizations face increasingly coordinated and informed adversaries, making securing their systems even more challenging.
Countermeasures and mitigation strategies
In response to the evolution of advanced ransomware, healthcare organizations have had to enhance their defensive measures. Adopting multi-layered security approaches — involving a combination of firewalls, intrusion detection systems, regular software updates and employee training — has become paramount.
Additionally, AI and machine learning are crucial in detecting and preventing attacks. These technologies can analyze vast amounts of data in real time and identify unusual patterns more accurately than traditional methods. Leveraging AI-driven tools lets healthcare providers anticipate and mitigate ransomware attacks more effectively than otherwise. It also helps bolster their overall cyber security posture.
Adapting to an evolving threat
The need for continuous adaptation in cyber security strategies is critical as ransomware threats evolve and become more sophisticated. The future landscape of ransomware in healthcare will likely see more advanced tactics. This makes it essential for healthcare organizations to stay vigilant and proactive in their defense measures.
For more insights from Rehack Features Editor, Zac Amos, click here. Lastly, to receive practical cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#2023#adversaries#affiliate#ai#AI-powered#analyses#attackers#barrier#Business#CNI#code#Collaboration#collaborative#Collective#comprehensive#compromise#continuous#critical infrastructure#cyber#cyber criminals#cyber security#Cyber Threats#cybersecurity#data#Data Breaches#data integrity#defense#defenses#democratization
0 notes
Text
Now Private RDP and Windows VPS with Windows Server 2022
In the realm of web hosting and server solutions, Windows Virtual Private Servers (VPS) have emerged as a dynamic and popular choice, offering a virtualized hosting solution running on the Windows operating system. The scalability of Windows VPS is a standout feature, allowing businesses and individuals to easily adjust allocated resources to meet evolving needs without paying for unused capacity
This adaptability aligns perfectly with the ever-changing demands of the digital world.
Use Cases for Windows VPS
Windows VPS caters to a wide range of needs across various scenarios
Web Hosting: Ideal for hosting websites, web applications, and content management systems with seamless scalability to handle traffic spikes.
Application Development: Provides an isolated environment for effective creation and testing of Windows-based applications.
Remote Desktop: Enables secure remote access to VPS from anywhere, facilitating convenient remote work and server management.
Data Backup and Storage: Vital for secure data storage and backup solutions within a dedicated VPS environment.
Game Servers: Illustrates substantial growth potential, as seen with E-Store Emporium experiencing a 50% boost in online sales within a year of adopting Windows VPS
Connecting to Windows VPS using RDP
Remote Desktop Protocol (RDP) is a crucial tool for remote access to computers or servers, allowing users to connect over a network connection and control the remote machine as if physically present
Cloudy offers reliable, high-performance RDP servers with minimal latency time, making it one of the best providers globally
Steps to Connect via RDP:
Open Remote Desktop Connection Software: Access the software through the Start Menu or by typing “mstsc” in the Run textbox.
Enter IP Address: Input the server’s IP address in the “Computer” field within the software.
Enter Username and Password: Provide your credentials in the prompted window to establish the connection
Choosing Between RDP and VPS
When deciding between Remote Desktop Protocol (RDP) and Virtual Private Server (VPS) for remote access needs, several factors come into play
Number of Users: VPS supports multiple users simultaneously, making it suitable for larger organizations.
Security: VPS offers a higher level of security with isolated virtual machines.
Cost: RDP is often more cost-effective than VPS.
Technical Knowledge: Setting up and maintaining a VPS requires more technical expertise.
Performance: RDP provides better performance for tasks requiring high processing power.
In conclusion, both RDP and VPS are viable options for remote access, with the choice depending on specific needs such as user numbers, security requirements, technical expertise, cost considerations, and performance demands
0 notes
Text
𝐄𝐦𝐩𝐨𝐰𝐞𝐫 𝐘𝐨𝐮𝐫 𝐃𝐢𝐠𝐢𝐭𝐚𝐥 𝐉𝐨𝐮𝐫𝐧𝐞𝐲 𝐰𝐢𝐭𝐡 𝐕𝐏𝐒 𝐑𝐃𝐏: 𝐔𝐧𝐥𝐞𝐚𝐬𝐡 𝐒𝐩𝐞𝐞𝐝, 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲, 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲

Discover the essential features of VPS RDP at VPS Proxies Inc, your go-to source for cutting-edge digital services, where speed, security, and accessibility converge to enhance your online experience.
𝐖𝐡𝐚𝐭 𝐢𝐬 𝐕𝐏𝐒 𝐑𝐃𝐏❓
VPS RDP, an acronym for Virtual Private Server with Remote Desktop Protocol, signifies a hosting solution seamlessly merging the attributes of a virtual private server (VPS) with the functionalities of desktop protocol (RDP). This powerful combination empowers users with dedicated resources, customization options, and remote accessibility, offering a versatile solution for various digital applications.
𝐇𝐨𝐰 𝐝𝐨 𝐈 𝐮𝐬𝐞 𝐕𝐏𝐒 𝐯𝐢𝐚 𝐑𝐃𝐏❓
🔄 𝐒𝐭𝐞𝐩 𝟏: 𝐎𝐛𝐭𝐚𝐢𝐧 𝐕𝐏𝐒 𝐃𝐞𝐭𝐚𝐢𝐥𝐬
Secure your VPS details, including the server’s IP address, username, and password, from a reputable hosting provider.
⚙️ 𝐒𝐭𝐞𝐩 𝟐: 𝐒𝐞𝐭 𝐔𝐩 𝐑𝐃𝐏 𝐂𝐥𝐢𝐞𝐧𝐭
Install an RDP client on your local computer for a seamless connection. Windows users can use “Remote Desktop Connection,” macOS users can opt for “Microsoft Remote Desktop,” and Linux users have various third-party options.
🔗 𝐒𝐭𝐞𝐩 𝟑: 𝐂𝐨𝐧𝐧𝐞𝐜𝐭 𝐭𝐨 𝐕𝐏𝐒
Launch the RDP client, enter provided details (VPS IP address, username), and ensure a secure connection with the required credentials.
⚙️ 𝐒𝐭𝐞𝐩 𝟒: 𝐀𝐝𝐣𝐮𝐬𝐭 𝐂𝐨𝐧𝐧𝐞𝐜𝐭𝐢𝐨𝐧 𝐒𝐞𝐭𝐭𝐢𝐧𝐠𝐬
Customize settings like display resolution and resource-sharing preferences in the RDP client for a personalized VPS interaction.
🖥️ 𝐒𝐭𝐞𝐩 𝟓: 𝐔𝐬𝐞 𝐕𝐏𝐒 𝐃𝐞𝐬𝐤𝐭𝐨𝐩
After a successful connection, your VPS desktop appears on your local machine, mirroring a standalone Windows desktop for easy task execution.
🔧 𝐒𝐭𝐞𝐩 𝟔: 𝐏𝐞𝐫𝐟𝐨𝐫𝐦 𝐓𝐚𝐬𝐤𝐬
In your virtual environment, seamlessly perform tasks such as software installation, configuration, and desktop navigation.
🚪 𝐒𝐭𝐞𝐩 𝟕: 𝐃𝐢𝐬𝐜𝐨𝐧𝐧𝐞𝐜𝐭 𝐚𝐧𝐝 𝐋𝐨𝐠𝐨𝐮𝐭
Gracefully close the RDP session on your local machine, and depending on your VPS OS, log out to ensure security and session integrity.
𝐖𝐡𝐚𝐭 𝐢𝐬 𝐭𝐡𝐞 𝐚𝐝𝐯𝐚𝐧𝐭𝐚𝐠𝐞 𝐨𝐟 𝐮𝐬𝐢𝐧𝐠 𝐕𝐏𝐒 𝐑𝐃𝐏❓
🔐 𝐃𝐞𝐝𝐢𝐜𝐚𝐭𝐞𝐝 𝐑𝐞𝐬𝐨𝐮𝐫𝐜𝐞𝐬: Ensure consistent performance with allocated resources dedicated to your virtual server.
🛠️ 𝐀𝐮𝐭𝐨𝐧𝐨𝐦𝐲 𝐚𝐧𝐝 𝐂𝐮𝐬𝐭𝐨𝐦𝐢𝐳𝐚𝐭𝐢𝐨𝐧: Full control over your virtual environment, allowing customization according to specific requirements.
🛡️ 𝐈𝐬𝐨𝐥𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲: Operate independently with added security; breaches on other VPS instances do not impact yours.
🌐 𝐑𝐞𝐦𝐨𝐭𝐞 𝐀𝐜𝐜𝐞𝐬𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲: Connect from anywhere using an RDP client, ideal for remote work scenarios.
🖥️ 𝐖𝐢𝐧𝐝𝐨𝐰𝐬 𝐄𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭: Run Windows-specific applications seamlessly for compatibility with a wide range of tools.
⚖️ 𝐒𝐜𝐚𝐥𝐚𝐛𝐢𝐥𝐢𝐭𝐲: Easily adjust resources as your needs evolve, ensuring adaptability to changing demands.
🚀 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞 𝐎𝐩𝐭𝐢𝐦𝐢𝐳𝐚𝐭𝐢𝐨𝐧: Dedicated resources contribute to optimized performance for resource-intensive tasks.
💰 𝐂𝐨𝐬𝐭-𝐄𝐟𝐟𝐢𝐜𝐢𝐞𝐧𝐜𝐲: Strike a balance between cost savings and performance benefits compared to dedicated servers.
🔧 𝐅𝐥𝐞𝐱𝐢𝐛𝐢𝐥𝐢𝐭𝐲 𝐢𝐧 𝐒𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐈𝐧𝐬𝐭𝐚𝐥𝐥𝐚𝐭𝐢𝐨𝐧: Install and run diverse software applications, catering to specific use cases.
🖥️ 𝐂𝐞𝐧𝐭𝐫𝐚𝐥𝐢𝐳𝐞𝐝 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭: Efficiently administer your virtual server through the remote desktop interface, handling tasks like updates and maintenance.
In the fast-paced landscape of digital services, prioritizing speed, security, and accessibility is crucial, and VPS RDP at www.vpsproxies.com stands out as an essential tool. This comprehensive guide unravels the intricacies of VPS RDP, showcasing its advantages such as dedicated resources, autonomy, security, and compatibility, making it an indispensable and versatile solution for diverse hosting and computing requirements.
𝐖𝐡𝐞𝐫𝐞 𝐏𝐞𝐫𝐟𝐨𝐫𝐦𝐚𝐧𝐜𝐞 𝐌𝐞𝐞𝐭𝐬 𝐏𝐫𝐞𝐜𝐢𝐬𝐢𝐨𝐧: 𝐯𝐩𝐬𝐩𝐫𝐨𝐱𝐢𝐞𝐬.𝐜𝐨𝐦 𝐟𝐨𝐫 𝐒𝐞𝐚𝐦𝐥𝐞𝐬𝐬 𝐕𝐏𝐒 𝐑𝐃𝐏.
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: live:.cid.79b1850cbc237b2a
#VPSRDP#RemoteDesktopHosting#VirtualPrivateServer#DigitalSecurity#TechSolutions#ServerPerformance#DigitalAutonomy#CloudComputing#RDPAccess#WindowsEnvironment#ScalableHosting#SecureConnections#OptimizedPerformance#TechInnovation#DigitalTransformation#FlexibilityInHosting#CostEffectiveHosting#CentralizedManagement#VPSHosting#DigitalExperience
0 notes
Text
Decoding the Anatomy of a Ransomware Attack

Ransomware is a multi-stage problem, that requires a multi-stage solution to effectively contain the attack at any stage. A typical ransomware attack goes through six distinct stages, and deconstructing each of these can help organizations strengthen their preparation and response strategies.
Ransomware attacks are increasing in size, frequency and complexity, with threat actors resorting to more aggressive methods, developing cross-platform functionality to be highly adaptive, and adding new toolsets to launch targeted attacks. Ransomware cost the world $20 billion in 2021, and this is expected to rise to $265 billion by 20311.What’s more alarming is the industry estimates which predict that ransomware is expected to attack a business, consumer or a device every 2 seconds by 2031, up from every 11 seconds in 20211.
Stages of ransomware attack:
Ransomware is a multi-stage problem, requiring a multi-stage solution to effectively contain the attack at any stage. Understanding the anatomy of a ransomware attack, therefore becomes essential to prepare for and respond to such events. A typical ransomware attack goes through six distinct stages, and deconstructing each of these can help organizations strengthen their preparation and response strategies.
Infiltration:
The first stage is when the attacker infiltrates the systems. This can be done in several ways such as sending out phishing email attacks, setting up malicious websites, exploiting weaknesses in RDP connections, attacking software vulnerabilities directly or employing zero-day exploits. Publicly exposed web applications and network devices with vulnerabilities such as VPN, RDP are exploited to infiltrate into the network. Servers and endpoints also get impacted in this stage.
Account Compromise:
Once the infiltration is complete, the next stage is when the account is compromised. This usually takes place when a local user or admin account is compromised, typically in cases where same local and admin passwords are applied across the organization. The malicious code will set up a communication line back to the attacker. The ransomware attacker may download additional malware using this communication line. At this point, the ransomware may lay hidden and dormant for days, weeks, or months before the attacker chooses to initiate the attack. Often, organizations could be completely unaware that their systems are compromised, and the attacker can wait for the optimal time to unleash the attack.
Privilege Escalation:
The third phase in the ransomware attack cycle is Privilege Escalation — a type of network attack used to gain unauthorized access to systems within a security perimeter. The most exploited service for executing this is Active directory. Active Directory is commonly referred to as ‘Keys to the Kingdom’. If Active Directory is compromised, attackers can gain access to domain admin/enterprise admin credentials, making it easy for ransomware actors to penetrate further into the network. Effective detection mechanisms are very critical to prevent AD compromise. Deploying a robust Privilege Access Management (PAM) solution along with an effective endpoint detection and response (EDR) tool can help prevent AD compromise.
Lateral Movement:
On successful completion of privilege escalation, the ransomware actors move on to performing lateral movement. They can now move freely within the environment across servers, virtual platforms, databases etc. and access the cloud, backup storage etc. Once they have obtained authority and presence within the digital estate, they then progress to the final stages of the attack. Modern ransomware has built-in functions that allow it to search automatically for stored passwords and spread through the network. More sophisticated strains are designed to build themselves differently in different environments, so the signature is constantly changing making it harder to detect by legacy solutions.
Data Exfiltration:
The fifth phase in the attack is data exfiltration which often, is a blend of data theft and extortion. A ransomware actor compromises an organization’s defenses and exfiltrates sensitive data of measurable value — financial records, intellectual property, trade secrets, business data, and so on. After offering the data for sale on the dark web to establish its value, the attacker then contacts the victim and demands a payment to prevent a sale. The attacker’s leverage in this case is the significant reputational damage, potential regulatory files, and other fallout that would result from the data’s release. A dangerous trend that is becoming widespread is triple extortion, wherein after extracting ransom from victim organizations, the ransomware actors reach out to the clients of victims and demand ransom from them.
Data Encryption:
The final phase in the kill chain is data encryption wherein the threat actors steal and encrypt the confidential assets of victims to extort money. Traditionally, ransomware encrypts the victim’s data and holds the decryption key for ransom. In recent times though, it is common among ransomware campaigns to exfiltrate victims’ data for extortion. This approach is becoming increasingly popular because it gives victims two reasons to pony up the ransom: they need to both regain access to their files and attempt to prevent leaks of their data.
Ransomware attacks are getting more targeted in scope and disruptive in impact as attackers constantly up the offensive using expanded toolset, emerging technologies, and new operating models. Addressing the threat of ransomware therefore requires adopting a multi-layered approach that includes securing critical infrastructure, viz., Active Directory, Backups, Network, Cloud and Office365. Enabling multi-factor authentication (MFA), deploying a robust endpoint detection and response (EDR) tool, implementing network segmentation and least privilege access, and running compliance audits, vulnerability scans and Pen tests are some of the recommended best practices that can help organizations protect against ransomware attacks.
To learn more about ransomware attacks and prevention strategies, watch our on-demand webinar on Outsmart Ransomware with SISA’s Key Prevention and Response Strategies or request for a Ransomware Prevention Learning Session.
#pci dss compliance#pci dss saq#pci software security framework#pci secure software standard#pci secure software lifecycle#iso 27001 audit#GDPR.risk assessment#vulnerability assessment
0 notes
Text
Unlocking Efficiency: 30% Off for Encoding RDP Users!

Linux: Elevating Productivity with Encoding RDP
Linux users are no strangers to the power and flexibility this operating system offers. However, remote desktop access can sometimes pose challenges. With Encoding RDP, accessing your Linux environment becomes a breeze. Whether you’re managing servers, developing software, or handling data analysis tasks, our RDP solutions ensure smooth navigation and efficient performance. Take advantage of the 30% discount to streamline your workflow and maximize productivity effortlessly.
Windows Server: Unleashing Potential with Encoding RDP

For businesses relying on Windows Server environments, optimizing remote access is crucial for maintaining operations and fostering collaboration. Our Encoding RDP solutions offer a seamless bridge to your Windows Server setup, enabling you to connect securely from anywhere, anytime. Whether you’re managing user accounts, deploying applications, or configuring network settings, our RDP services ensure a hassle-free experience. Don’t miss out on the opportunity to buy RDP at a discounted rate and enhance your Windows Server workflow today.
Windows RDP: Empowering Remote Work with Encoding RDP
In today’s distributed work landscape, remote access solutions like Widows RDP play a pivotal role in enabling seamless collaboration and productivity. With Encoding RDP, you can take your remote work experience to the next level. Our RDP solutions offer robust security features, intuitive user interfaces, and lightning-fast performance, empowering you to work efficiently from any location. Whether you’re accessing corporate resources, attending virtual meetings, or collaborating with team members, our RDP services ensure a smooth and reliable experience. Take advantage of the 30% discount to invest in your remote work setup and unlock unparalleled efficiency.
Change Password in RDP: Strengthening Security with Encoding RDP
Security is paramount when it comes to remote desktop access. With Encoding RDP, you can rest assured that your data and systems are protected against unauthorized access and cyber threats. One essential security practice is regularly changing passwords to prevent potential breaches. Our RDP solutions make it easy to change passwords securely, ensuring that your accounts remain protected at all times. By incorporating robust encryption protocols and multi-factor authentication, we prioritize the security of your remote access environment. Invest in Encoding RDP today and strengthen your security posture while enjoying the benefits of seamless remote access.
In conclusion, optimizing remote desktop access is essential for modern businesses and professionals alike. Whether you’re a Linux aficionado, a Windows Server user, or rely on Widows RDP for your daily tasks, Encoding RDP offers tailored solutions to meet your needs. With our exclusive offer of 30% off for Encoding RDP users, now is the perfect time to invest in enhanced remote access capabilities. Don’t miss out on this opportunity to streamline your workflow, maximize productivity, and strengthen security. Get started with Encoding RDP today and unlock the full potential of remote desktop access.
0 notes
Text
Decryption_Error: “The Server Room, Part I”
Summary: Elliot is locked in the server room by a few of his colleagues to stop him from ruining their Memorial Day weekend. Y/N, Elliot’s manager, finds him and comes up with a solution to fix the broken servers, but because of Elliot’s injuries and his refusal to go to a hospital, Y/N makes him stay at her place for the long weekend. As Elliot and Y/N bond for the first time outside of work, something a little more than friendship starts to emerge.
Summary/Mood Board
Word Count: 5800
Disclaimer: I know 0 things about technology and want to cry real tears for making my narrator Elliot’s boss. I sincerely apologize to anyone I offend for my whack tech references--please let me know if you need me to fix something because it’s awful and I will credit you for saving me some embarrassment!
Tags: @sherlollydramoine @rami-malek-trash @teamwolf2411 @thingsfandom @limabein @lovie-rami @txmel @hopplessdreamer @ouatlovr
Warnings: Physical injuries/blood, language, **=heavily paraphrased from a monologue on Robot
Author’s Note: I won’t be able to update this story as quickly as Remnants because my life is about to get crazy busy. However, I will do my best so y’all don’t lose interest : ) Special shoutout to @alottanothing for helping me get this story organized and underway! Thanks for being my cheerleader 💕

For fuck’s sake! I thought as I changed out of my swimsuit and into a pair of shorts and a t-shirt, shoving my still wet feet into a pair of sandals.
I had made it to my family’s place for Memorial Day weekend for the first time in years only to be called back to work because something happened to the servers. My boss, Miles, was out of town like everyone else in the goddamn city, and he trusted me as the Senior Manager to handle the situation.
CIStech Cybersecurity had been my life for the past four years. Starting as an Analyst really fostered my affinity for data and subsequently put me on the fast-track to become management. I liked working hard, and when I first started at CIStech, I would be mystified when I realized it was 10 pm, everyone had gone home, and I had skipped dinner (again) because I was 5,000 clicks deep into testing a contingency plan I created for scenario 11/1,000 in the event of a security breach.
My relationship with my job was complex--I knew I worked too much, but I needed those long days to help quell my anxiety; data gave me a focus and helped me make sense of a world that seemed to be drifting further and further into shades of grey, a place where evil and good barely served as separate entities anymore.
This long weekend was an important test for me—I needed to prove to myself that I could step away from the office and the world wouldn’t end, nor would my mental stability.
Except that I did step away from the office and the world did end—sort of. So much for convincing my brain that taking time off was a good thing.
For the first three quarters of the drive into the city, I had gone over about 30 scenarios in my mind and just as I was about to drive myself crazy, I shook my head and cranked up the music. There was only so much I could mentally prep for until I knew whether the problem was physical or within the network.
Because everyone in the city had fled to escape the rising humidity, I was able to park on a side street about a half of a block from work. I swiped my badge to get into the lobby of CNC Precision Machining, our host company, then said a quick hello to the head of night security, Lance. I swiped my badge again to activate the elevator, and as I rode up to the 18th floor, my anxiety curled into a lead ball and made itself at home in my stomach. Something did not feel right, and I almost, almost went back downstairs to ask Lance to radio a guard.
But, how often do we actually act on our anxiousness? For me, I had to talk myself out of so many horrors a day that I always felt silly when I gave in to whatever idea had made itself at home in my mind.
I talked myself down, thinking, It’s almost 11 pm, and all I have to do is check the servers. Maybe one of the fans broke. Maybe a plug fell out. I can fix it and still get back to Mom and Dad’s by 2.
Once again, I swiped my badge. I entered CIStech’s wing, but as I opened the door to the cybersecurity offices and turned to deactivate the alarm, I saw it had never been set. My mouth fell open, and again the idea of turning back flitted through my mind, except being pissed overtook my apprehension.
Whoever was the last to leave was getting a letter of reprimand. Sure, the building itself was secure, but to not set the alarm in a company’s tech security office? Inexcusable.
Since I was now fuming, the unset alarm compounding with my ire over my ruined start to the weekend, I grumbled away my nagging thoughts as I quickly walked to the server room, swiped my badge and scanned my fingerprint to open the door.
The harsh lights were on an automatic switch, so they popped to life as I stepped a few inches into the room; however, the crunch of plastic and the popping of glass made me stop, one foot poised in the air as I looked down to see what I stepped on.
The remnants of a server, or more than one server, were littered across the ground, and as I scanned for the source of the damage, the last thing I expected to find was a body. Immediately, my mind wondered if this was a trap, and then I wondered if the body was even alive.
My voice emitted a sort of strangled groan which caused the body on the floor to move—and when I saw that it wasn’t just a random body, my heart sank.
It was Elliot, my employee and my friend.
***Eight Months Ago***
“Next up is Elliot Alderson. Recent grad. Bachelor’s in Computer Engineering from Stevens Institute of Tech. This is the guy with the impressive skill set, knowledgeable in everything we use. His portfolio backs it up, too.”
“Mmm, I remember reading through it and thinking if even half of it is legit, he’s smarter than everyone in that room put together,” Colin said, gesturing in the direction of the office floor.
“I tested his work on the headless Raspberry PI he sent with his portfolio—worked like a charm.”
“That could save us a lot of headaches,” JaLeah said, clicking through the description in Elliot’s portfolio again.
“Did you notice how streamlined his portfolio is? It’s masterfully organized and aesthetically pleasing,” I said, leaning over to look at JaLeah’s screen.
She hummed in agreement.
“Jayne? Bring in Mr. Alderson, please,” I said as I pressed the button on the wireless intercom.
At CIStech, we strived to maintain a comfortable atmosphere. Instead of a panel of interviewers, it was just myself and my two Supervisors. Instead of interviewing in our board room, we interviewed in my office, the three of us seated at a round table so when the applicant joined us, they felt less on-the-spot.
However, when Elliot Alderson walked in the room, his unease was so palpable I doubted anything would alleviate his nervousness.
“Mr. Alderson,” Colin began, extending his hand. “I’m Colin Greene, Supervisor.
Elliot paused long enough for me to give him a onceover, and peripherally, I saw JaLeah do the same.
“I’m Y/N Y/L/N, Senior Manager,” I said, shaking Elliot’s hand, his grip light as if the last thing he wanted to do in the world was touch me.
As JaLeah introduced herself, I took another quick inventory of Elliot Alderson. He was dressed well, although in clothes that were a bit too big on his small frame. His haircut, however, was immaculate, cut in a close fade on the sides with a mop of styled black hair on top.
His big, greyish eyes were moving around the room as if he were searching for the exit; and then, suddenly they stopped. It was like he reminded himself to pick a spot and focus.
“Go ahead and take a seat,” JaLeah said, sliding over the piece of paper that listed our interview questions.
As Elliot pulled out the chair and settled in, I explained what would happen during the interview, the goal to once again ease the nerves of the applicant.
“So, Mr. Alderson, I’m going to explain the process for this interview. First, we will give you a few minutes to read over the questions on the paper in front of you. When you are ready, let us know and we will take turns asking those questions. Once the Q&A portion is complete, we will connect our laptops to the one right here via RDP, and we will ask you to complete a specific task. Any questions so far?”
Elliot shook his head no.
“Excellent. Please take a few minutes to read over the questions, feel free to jot down notes in the spaces provided, then let us know when you are ready to begin,” I explained, ending with a smile.
Elliot did not return my smile; instead, his eyes dropped to the interview questions. As I watched him scan the paper, I had to remind myself not to stare. There was something about him that drew me in. His eyes were unlike any I had ever seen, and I couldn’t stop thinking about that damn, overquoted line from one of Walt Whitman’s poems: “I contain multitudes.”
Looking at Elliot, it was clear he contained depths, and I wanted to know everything there was to know about him. I could count on one hand the number of times I felt so immediately intrigued by another person.
After a minute or two, Elliot looked up, his eyes flickering between the three of us, and said, “Okay.”
Colin began, asking Elliot to tell us about his schooling and his professional experience.
Elliot answered carefully, reciting his academic and professional history. His voice was deep, a soothing monotone that was more like a raspy rattle than a melodious note.
“Thank you,” I said once he had finished speaking. “Question two asks about the steps you would take to secure a server. Walk us through that process, please.”
Once again, Elliot’s answer was correct and succinct.
“To secure a server, you use the SSL protocol for data encryption and decryption. Establish a secure password for your root and administrative users. Create the new users in the system. Remove remote access from the default root accounts. Configure your firewall rules for your remote access.”
I watched Elliot as he answered, his eyes focused on a spot over my shoulder. I made my notes as JaLeah moved on to the next question.
“What are the most common types of cyberattacks? Explain which attack you feel is most common and why it is most common.”
Elliot listed off the usual attacks with ease—phishing, malware, DDoS, password attacks, malvertising, man in the middle, but it was his answer to the second part of the question that allowed us to see a glimpse under his carefully crafted façade.
“People. People are the only reason cyberattacks happen and people are the ones who make it easy for hackers to execute any attack. The most common cyberattack in a large corporation is phishing—people are all too willing to provide information without first checking the origination. People who work in companies operate on autopilot, running their daily programs, usually without interruption, and in order to avoid a runtime error, people will click a link, enter their password, and by then, they have you.”**
We were all quiet for a moment and Elliot looked a bit surprised, as if he couldn’t believe what he just said aloud.
“Excellent answer, Mr. Alderson,” JaLeah said, narrowing her eyes and nodding, still mulling over Elliot’s response. “If only we knew how to prevent human error—but I supposed that would be a billion-dollar answer,” she finished, flashing him a smile.
He shrugged his shoulders and gave her a tiny smile in response.
That was the only real glimpse of Elliot’s personality we got for the rest of the interview, but he absolutely nailed the task, finding each vulnerability we set up in our system and fixing it in record time.
“Do you have any questions for us, Mr. Alderson?” I asked as we closed out the interview.
“I’ve already found out everything I needed to know,” Elliot replied, his eyes meeting and holding my gaze.
I smirked and nodded.
“I wouldn’t expect anything less, Mr. Alderson. You’ll hear from HR within 24 hours, either way,” I said as I hit the intercom.
“Please see Mr. Alderson out, Jayne.”
Elliot left as nervously as he entered, not bothering with any attempt at casual conversation to make his interview a bit more memorable.
As soon as the office door clicked shut, Colin leaned back in his chair and said, “No way. Guy’s weird.”
“Weird?” I questioned. “Since when is being nervous the same as being ‘weird’?”
“He didn’t make eye contact with me once—and not like in an ‘on the spectrum way.’ More like, he has a secret and no one can know it way. I’m not trying to be a dick—I just got a bad vibe.”
“Well, you are being a dick,” I said. “There are a thousand reasons why people struggle with eye contact, Colin. Don’t stereotype. Give me something factual if you really didn’t like him for the position.”
“And I remember a time when you couldn’t look me in the eye, Colin,” JaLeah said, her dark eyes flashing.
Colin rubbed his hands over his face and sighed.
“He didn’t elaborate on any of the questions—he spit back text-book answers on every one, except for JaLeah’s question about cyberattacks. I felt like he wasn’t hungry for this job—he acted like he didn’t really want it.”
I nodded my head.
“I wish he would have elaborated, too. However, I think his tech skills far outweigh any subpar people skills.”
“I agree with Y/N,” JaLeah said. “But I do see Colin’s point—remember when we had those interns? We ended up hiring Steph because she was able to build a rapport with everyone here. Granted, they all had about the same skill set, but her ability to communicate set her apart.”
“Doesn’t it also work in reverse, though--tech skills over people skills?”
Colin nodded in agreement. “It does.”
“So, let me make you both a deal: if any of the remaining candidates perform as well or better than Elliot Alderson on the task, we hire them. If not, we go with Alderson.”
“Works for me,” JaLeah said. “For the record, I did like him. He really spit some fire on that answer about human error.”
I smiled at JaLeah and nodded while Colin rolled his eyes.
“Alright—who’s up next?” he said, already accepting the idea that he was probably not going to win this one.
* * * * *
I closed my eyes and rolled my neck, listening to the bones pop and crunch. It was time to get up and take a lap around the office before the blood decided to pool in my calves and send me to an early grave.
It was nearly 8 pm, so when I saw the illumination of a computer screen reflected in a set of big grey eyes, I was a bit surprised. Elliot Alderson had accepted our offer and started at CIStech three weeks ago. He was proving to be an excellent engineer, and once he settled in, I wanted to assign him to the white hat team.
However, Colin saw fit to initiate a trial by fire and made Elliot the project manager for the development of a new code that could counter a DDoS flooding attack.
Colin may have done it to be an asshole, but I permitted it out of curiosity to see if my hire had what it took to climb. It was already clear that Elliot’s skills were unmatched. If he could pitch, he would be on the fast-track to becoming my boss one day.
When he saw me approach, his fingers immediately stilled and a look of apprehension crossed his features.
“Hey, Elliot. Working late?” I asked, surprised at the butterflies in my stomach as I initiated a conversation with him.
“I’m sorry if I disturbed you, Ms. Y/L/N. I didn’t realize how late it was,” Elliot said in his deep voice, his words rolling out in that gentle monotone.
“Y/N. It’s Y/N—we don’t do that Mr. and Ms. stuff once you’re hired. Call me crazy, but I like to think of all 50 or so of us as a family. Distant and dysfunctional, sure. But whose family isn’t?” I finished with an awkward chuckle at my own joke.
Elliot looked at me, his expression unreadable, and said nothing for what felt like an obscene amount of time. I’m certain my cheeks colored at my failed attempt at a joke and his subsequent silence. I began to feel an urgent need to fill the quietness with this almost-stranger I just called “family” when Elliot finally spoke.
“That’s . . . nice.”
I laughed and said, “You’re not much of a talker, are you?”
Elliot gave me a tiny smile, if you could even call the fleeting upturn of his lips before they drew back into a straight line a smile.
“No. I’m not.”
I thought for a few seconds, wanting my first one-on-one interaction with Elliot to be right. A thousand things to say barreled through my mind like Shanghai’s Maglev, and I saw Elliot’s attention turn back to his computer, his fingers twitching, probably wondering if it would be rude to go back to work.
“Do you know what I wish, Elliot?” I said, my words rushed as I reigned in the speeding train of my thoughts.
“No,” Elliot said, looking at me with genuine confusion.
“I wish we had a code we could input to just automatically cut out the bullshit of small talk. Imagine if our minds could input all of that information—we’d know right away whether or not a person was to our liking, whether they would be someone who could become our friend.”
Elliot looked at me, his eyes shining from the monitor in the dark of the office, his mouth a bit agape; he looked at me as if I were either the first human he’d ever seen or the last human he’d ever see—I couldn’t make up my mind on the former or the latter.
“Is that totally crazy?” I asked.
“It’s the least crazy thing I’ve ever heard,” Elliot said, his voice breaking with its normal monotone to convey honesty.
I smiled, and the butterflies in my stomach finally settled. I moved around Elliot’s desk and leaned on the edge. He scooted his chair back so he could angle it toward me, his hands fidgeting, unsure what to do without a keyboard underneath of them.
“I’m willing to pretend that code is real—we’ve scanned each other, determined we’re cool, and can now proceed along the route of friendship. At least, that’s what my data has output.”
Elliot grinned, and the fucking butterflies came back in full force. There was no part of my 8 pm afterwork self that was equipped to handle how damn good-looking this guy was.
“My data reads the same,” he said, his smile turning shy, his eyes flickering away from my face and toward the floor.
“Excellent. So, as emerging friends, I want to confess that, believe or not, I’m not much of a talker either.”
“I—I don’t think we are the same kind of not-talkers,” Elliot said, frowning up at me.
“Do me a favor. Tomorrow, pay attention after you pitch the DDoS counter plan. Once the pitch is out, everyone shoots off their own ideas and if they don’t have an original thought, they’ll turn to criticism. I won’t say a word—I never do.”
“Why?” Elliot asked, clearly interested because his response was immediate.
“Because I listen. People are so consumed by a need to have self-validation that they talk just to talk, hoping something that comes out of their mouth is what sparks someone else’s path to self-validation. It’s a . . . circle jerk, if you don’t mind me speaking in my ‘off the clock’ tongue.”
Elliot’s mouth had dropped open a little again as he listened, his brows drawn in as he gave it some thought—well, a lot of thought because once again, the silence bordered on oppressive before he spoke again.
“I thought people only said things like that inside their minds. Especially bosses.”
“Did I reveal an inherent human truth you were unaware of?”
Elliot chuckled, a gravelly rumble, and it was the cutest damn thing I had ever heard.
“No—I’ve thought the same thing for as long as I can remember.”
“See? Our data chose well. Now, do you want to sit there and tell me more about how unalike we are or are you ready to trust me enough to help you with whatever is plaguing you about pitching tomorrow?”
“How did you—” Elliot began before sighing and popping off of his chair to stalk over to the window. It took me by surprise that a little piece of his mask was so readily falling away.
I stayed where I was, even though his form was little more than a shadow that moved against the backdrop of the lighted city.
“I am not good with people,” Elliot said, his voice sounding harsh and too loud in the quiet office. “I don’t know how to talk to them one-on-one, so I sure as hell don’t know how to talk to them in a group. All I can think of when I get in front of anyone is how much of an idiot they think I am. I even typed up a letter of resignation,” Elliot said, his voice returning to its normal murmur with his confession.
This time, it was my turn to nurse the quiet. I thought about saying, Bullshit—you’re talking to me. You can do anything you put your mind to! But Elliot wasn’t someone who needed a pep-talk. He was deeper than that—probably even deeper than I could ever comprehend. “I’m not gonna bullshit you. You could walk out of here and get hired just about anywhere in any one of these buildings with your skill set. But I’d like to believe that you care, maybe just a little, that I am the one who extended you an offer—gave you a shot at your first ‘real’ job. So, yeah, you can run. But you’ll hurt my feelings if you do.” Whatever Elliot was expecting me to say, it wasn’t that. He walked back to stand in front of me and he blinked those big eyes that were once again a reflection of the light blue of the desktop.
“You don’t even know me enough to be affected by anything I do. I’m just another cog in the wheel.” I thought we were on a path to friendship, but if this was Elliot’s response to my admission I cared about whether or not he quit, I knew he was hiding, deep, deep inside of himself. “What makes you think you’re unworthy of general human concern? You are human, aren’t you?” I said, once again making an awkward joke for myself to softly laugh at. “I—I didn’t mean that I—" “Careful, Elliot. You intrigue me. And when people intrigue me, I have to figure them out. Have to.”
Elliot took off toward the window again, pacing as he struggled to convey his fear.
“Like I said, I’m not much of a talker and I’m not very good with people. I can do anything with a computer, but people. I just . . . can’t.”
“Mmm, until I see a T-800 running around and declaring “I’ll be back,” I will disagree with you that you can do ‘anything’ with a computer.”
Elliot stopped pacing and turned to face me, his head comically turned to the side as he decided whether or not to finally laugh at one of my jokes.
This time, he did laugh, a soft little chuckle as he shook his head and shoved his hands in his pants’ pockets.
“Let me make you an offer—”
“An offer I can’t refuse?”
I giggled and shook my head.
“Yes! He jokes! We really are on the path to friendship. . . which means, I want to help you: Fill me in on the details of what you’ve designed, and we can practice. Come on—we’ll go in the meeting room.”
“I can’t ask you to—”
“You did not ask. I gave you a command. All you have to do is type Y,” I said in a sing-song voice, smiling before pushing off the edge of his desk and walking toward the meeting room.
I turned after a moment to see Elliot grab his laptop and follow me.
When we crossed the office to the meeting room, I paused with my hand on the door.
“Actions help us believe what our minds have convinced us not to believe—if I truly thought you were nothing more than a cog, would I give my time to you? Tell me—what’s more valuable than time?”
Elliot didn’t answer me. Instead, he smiled at me, his expression conveying his gratitude.
I turned the knob and walked toward the sofa, plopping onto the cushion.
“So, fill me in.”
* * * * *
Elliot and I passed many nights like this, and I quickly realized Elliot wasn’t going to follow in my footsteps and climb up the management ladder. After his DDoS proposal, Colin followed my recommendation and moved Elliot to the white hat hackers, a small team of ten. The white hats worked a little more in isolation than the other techs, which is what Elliot wanted.
So, we worked. We talked. We listened. We ate too much take-out and spent too many late hours at the office.
Our data was compatible, which would be Elliot-speak for saying, “We became friends.”
***Present***
“Elliot! Elliot, what happened?” I asked as I dropped to my knees and rolled him the rest of the way onto his back.
His eyes snapped open and darted around the room, looking everywhere but at me. Elliot scooted away and backed up to the wall, pulling his knees up to his chest and crossing his arms over his legs. He looked like a trapped, feral animal, trying to make itself as small as possible to avoid capture.
I noticed the cuts and the trails of blood that smeared across his hands, and I saw that there was blood on the floor where he had been laying. As I looked him over, I also saw a gash across his forehead that ran into his hairline. Blood was still trickling down the side of his face.
“Elliot,” I said again in a soft, calm voice.
He still didn’t react; instead, he looked around the room and started mumbling, thumping the back of his head off the wall.
I got up and quickly moved to drop down in front of him, placing my hand between his head and the wall. It looked like he already had a concussion and I didn’t want him to hurt himself anymore.
“Elliot. Hey. It’s Y/N. You’ve gotta focus, sweetheart. Focus on my voice.”
I kept repeating myself in the same soothing tone. After a few moments, I slowly reached out and grasped his shoulder, running my thumb over the material of his light grey dress shirt.
Slowly, Elliot stopped moving his head and his eyes stopped darting. I still had no idea what he was mumbling and if it weren’t for the vibrations of his chest and the very subtle movements of his lips, I wouldn’t have known he was speaking.
When Elliot finally fixed his eyes on my face, his brows contracted into confusion.
“Y/N?” he said, his voice raspy, like someone who had been talking too loudly over music or who had smoked too many cigarettes in a night.
“Hey,” I said smiling and removing my hand from his shoulder.
“Shit! The servers!” Elliot said, and tried to dart up, but I held him back.
“No. Don’t move. Your head is bleeding and so are your hands. I need to get you to a hospital.”
Once again Elliot’s eyes began to look everywhere but my face and he tried to scramble up. This time, he broke free from my grasp and I found myself flat on my ass as he bolted up from the floor.
He didn’t get very far because after about three steps he swooned and crashed into one of the broken servers. I scrambled to my feet and helped him sit back down on the floor.
“See? Hospital. Now.”
This time Elliot looked right at me, his eyes filled with tears as he begged me not to take him to a hospital. The display of pure emotion was a shock for me—even though Elliot and I spent a lot of time together, he was always very careful in his interactions and remained emotionally distant. To see him so vulnerable made me rethink my insistence.
“Shh, okay. Okay. Listen—I don’t know if you’re concussed or what, but can you tell me anything about what happened? Or when this happened? If the tapes never went out. . .” I trailed off, unable to even imagine the repercussions.
“The courier left at 4:48.”
I raised my eyebrow at Elliot’s precise answer.
“Okaaaay.”
“I remember the time because—” Elliot broke off and looked away.
“Because why?”
“That’s when they locked me in here,” he mumbled, his voice barely audible over the buzzing of the air conditioning that kept the server room so cool.
My phone rang, startling both of us. As I talked, Elliot retreated further into himself again, his knees pressed to his chest once more, his eyes fixed firmly on the floor.
“Yes, I’m at work, Miles.”
“Uh-huh. Yeah.”
“We definitely have a problem, but everything’s been backed up—the tapes were couriered out this afternoon.”
“No—you don’t need to come in.”
“Uh, it’s a problem with the a few of the servers themselves, some broken parts. Listen, I promise—I’ll take care of it and everything will be up and running on Tuesday like nothing ever happened.”
“You’re welcome—enjoy your night.”
“I will. Bye.”
I hung up the phone and stood up, leaving Elliot to himself for a moment. I surveyed the damage that was apparently done by Elliot himself. My mind couldn’t even grasp the idea that people I supervised, many of whom I had hired myself, would do something so inhumane.
It was no secret that people avoided Elliot, even his white hat teammates—he was closed off, smarter than most of them, and worked harder than all of them. I wasn’t blind to the way he was he treated, but I also knew him in a different way; I knew he kept to himself because it was so difficult for him to socialize with people he considered strangers.
I also knew Elliot didn’t mean to do this.
After I surveyed the damage, I began thinking outloud, “Towers 2, 3, 6, and 7 are fucking toast, but the rest are untouched. I need to synchronize the traffic to the secondary servers and synch the databases. Since it’s Memorial Day weekend, the traffic is light enough that no real damage should have been done. I have a friend who might be able to get us new towers.”
Elliot was watching me as I talked and figured out how to fix his mess.
“I can—” he began, but I cut him off.
“I have to tell them how this happened, Elliot. I’m not making any promises, but if I can fix it by Tuesday morning, you might be able to keep your job. And I can promise you, the fucking assholes that did this to you won’t.”
Elliot looked to the floor again, his face filled with sadness.
“Sit—do not move while I grab some papertowels and ice.”
Elliot gave me a barely perceptible nod, and I went off to gather what I needed to ice his head and clean up the blood.
When I came back, Elliot was sitting at the desk in the server room, his fingers poking over the keys on the keyboard.
“Damnit, Elliot! I said not to move.”
“This is all my fault. I have to fix it. I have to fix it. I have to—”
I cut him off by lifting his arms away from the keyboard and scooting the rolling chair back. Elliot turned his bloodshot eyes to mine, the rims lined with red and I wondered if he’d been crying.
I sighed and placed my hands on both of his shoulders.
“This is not your fault,” I said firmly, my eyes flickering between his, refusing to release him from my gaze until he listened to me.
Elliot opened his mouth, then closed it, choosing not to fight me.
“Hold this on your head,” I said, tearing my eyes from his face, and reaching for the ice pack I had set on the desk.
Elliot complied, and I turned back to the desk to finish synchronizing the servers. Once I was done, I wiped up the blood on the floor with the wet papertowels, then unplugged the damaged servers.
“Now, let’s get out of here. Your head is still bleeding,” I said as I made a final lap to check for damage.
I helped Elliot up by wedging my hand under his elbow, careful to avoid his fucked up hands. For a moment, the two of us were face-to-face. His eyes lifted up to look into mine and I sighed, reaching up to grasp his chin and turn his head to look at the gash.
“Head wounds are the worst. Never can tell how deep they are,” I whispered, looking closely at his cut.
“I’m sorry, Y/N.”
“I know, El. Come on.”
Elliot followed me out of the server room and I locked the door. After throwing away the bloodied papertowels in the bathroom, I came out to see Elliot at his desk, struggling into his hoodie, hissing as his bleeding and bruised hands slid through the fabric.
“I’ll get your backpack,” I said as I approached and reached under his desk to pull it out. “Is there anything else you need?”
Elliot shook his head no and I shrugged into his backpack. He stayed close as I set the alarm and waited for the elevator, neither one of us wanting to talk.
“Good night, Lance,” I called toward the front desk as I kept walking.
“Eh, Ms. Y/L/N? Do you need me to call—”
“Nope—all is well! Sorry you’re stuck here tonight, though,” I said with a wave.
“Me, too,” Lance answered, chuckling a little.
I led Elliot to the passenger door of my SUV, opening it and then waiting for Elliot to get in. Once I made sure he was settled, I shut the door and opened up the back door to take off his backpack and place it onto the seat.
I got in, buckled up, and put the key in the ignition. The radio started belting out the Britney Spears song I was rocking to on the way in, and I quickly turned it down after Elliot and I both jumped.
“Now you know my darkest secret,” I said shaking my head.
Elliot looked at me, the hint of the smallest smile in the universe turning up one corner of his mouth.
“I’m taking you to my place and I don’t want an argument. I have a friend who is a PA and I’m going to call her. She’s going to look at your head and if she says you need to go to the hospital, you are going to go. Is that clear?”
Elliot frowned and his eyes looked to the door as if he was contemplating whether or not he could escape.
I quickly put the SUV in gear and swerved out into the street to prevent him from making a move.
“Ok,” he said quietly, knowing he had no other choice.
#Elliot Alderson#elliot alderson x reader#female reader#elliot x reader#elliot alderson fanfic#rami malek#rami malek character#mr robot#mr robot fanfiction
133 notes
·
View notes
Text
What is RDP? Also, how to utilize it?
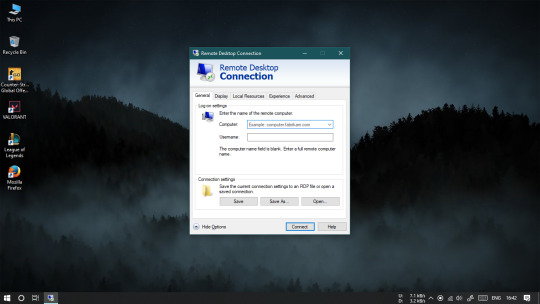
We take a top to bottom look a the MS's Remote Desktop Protocol (RDP) and how to utilize it. We additionally incorporate recommend the most hearty option RDP devices.
The Windows Remote Desktop Connection instrument enables clients to associate with a far off Windows PC or worker over the web or on a nearby system, giving them full access to the devices and programming introduced on it. This is made conceivable by Microsoft's own Remote Desktop Protocol (or RDP for short).
All Windows PCs and workers can utilize RDP to interface with another Windows gadget, yet just certain forms of Windows permit RDP associations. This restrictive convention equals the open-source Virtual Network Computing (VNC) convention usually utilized on Linux and different stages.
What is RDP?
The Remote Desktop Protocol permits far off clients to see and use Windows on a gadget in another area. Key peripherals like your console and mouse are imparted to the far off machine, permitting you to utilize and control it as though you were sat directly before it.
For RDP associations with work, you need two parts—a RDP worker and a RDP customer. A regular RDP worker is the Windows PC or worker you're associating with and will control. The customer is a PC or cell phone with a RDP customer application introduced, from which you control the worker. Microsoft offers its own customer for Windows, macOS, Android, and iOS, with different outsider choices accessible for Linux and different stages.
RDP is a Windows-just convention, and you can just set up distant associations utilizing RDP with Windows PCs and Windows Server establishments that help it. Not all forms of Windows do—Windows 10 Home, for example, must be utilized as a customer to associate with different Windows Remote Desktops, not the reverse way around.
You can just build up a solitary association with Windows PCs that have far off work area empowered. To associate numerous clients without a moment's delay, you'll need a Windows worker with the Remote Desktop Services (RDS) part introduced and empowered.
In the event that you need to set up RDP associations with a protected undertaking system from a far off area, you'll additionally require the Remote Desktop Gateway administration introduced and designed on a reasonable Windows Server establishment. This additionally offers expanded security, swapping the requirement for an inner virtual private network (VPN).
Step by step instructions to empower Remote Desktop associations on Windows
To utilize RDP to associate with another Windows PC or worker, you'll first need to empower it on the far off worker or PC. Fortunately, designing Windows to empower Remote Desktop is a genuinely direct procedure.
To empower Remote Desktop on Windows PCs:
Open the Windows Settings menu. To do this, click the Start button, at that point press the Settings symbol. From here, press System > Remote Desktop.
Press the Enable Remote Desktop slider to move it to the On position. The slider will turn blue when Remote Desktop has been empowered.
Of course, the Microsoft account you use to sign in will be the record you use to associate with your PC distantly. To permit extra clients to interface, press Select clients that can distantly get to this PC. In the Remote Desktop Users window, press Add and quest for the client account.
To take into account RDP associations over the web, you'll ordinarily need to permit approaching and active associations with TCP/UDP port 3389 on your system, except if port sending is essentially.
Tips for building up secure Windows Remote Desktop associations
Any sort of distant work area arrangement opens a gap that can possibly be abused. RDP is the same, and the RDP (port 3389) is notable and routinely checked for abuses. In the event that you intend to utilize Windows Remote Desktop over the web, you need a methodology set up to make sure about it.
Undertaking clients can utilize Remote Desktop Gateways to help give a protected method to interface with a RDP worker, however standard Windows clients don't have this extravagance. Rather, you'll have to utilize some good judgment answers for build up secure RDP associations. A few hints for building up a safe RDP association include:
1.Try not to permit open RDP associations over the web. On the off chance that you have to utilize Windows Remote Desktop over the web, set up your own virtual private system (VPN) or utilize a RD Gateway to make a protected passage to your nearby system first. Permitting an open RDP association over the web is incredibly hazardous, so don't leave it to risk.
2.Empower Network Level Authentication (NLA). This ought to be empowered as a matter of course in Windows 10, Windows Server 2012, and more current, yet in case you're utilizing more established variants of Windows, you should empower this—it guarantees that an association can possibly happen when it is appropriately verified and a privilege username and secret phrase is given.
3.Confine RDP associations with non-overseers. You should just permit non-director client records to distantly interface with Windows PCs. Standard client accounts can't change settings, introduce programming, and have restricted access to records. This should confine the harm that any potential rebel association could make.
4.Breaking point secret word endeavors. You should restrict the quantity of off base passwords on a record before it is bolted out, which should confine any harm from a disavowal of administration assault.
5.Utilize perplexing, secure passwords. Utilizing secure passwords is a word of wisdom for any circumstance, yet particularly for Windows Remote Desktop associations. Try not to utilize a similar secret phrase for various records, and utilize a blend of letters, numbers, and images.
6.Set RDP for most extreme encryption. As a matter of course, RDP associations will consistently attempt to utilize the most noteworthy conceivable degree of encryption. To guarantee that the most elevated level of encryption is constantly utilized, notwithstanding, you can set the default encryption level utilizing the Group Policy Editor (Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security > Set customer association encryption level > Enabled > High Level).
1 note
·
View note
Text
What to Do if You’re Hit by Ransomware
Ransomware attacks usually hit large companies or government systems to make as much money as possible. Any ransomware can cripple your systems and put a total lockdown on them if you are not careful enough.
In this article, we will give you a few pointers if you are ever hit by a ransomware attack.

Disconnect from the Network Immediately
The first step after discovering a computer that is infected by ransomware is isolating it from other systems and getting it off the network to reduce the potential damage.
“Disconnect infected computers from all cables and Wi-Fi,” says Ed Cabrera, chief security officer at enterprise security firm Trend Micro. “Begin the mitigation process as soon as possible.”
This won’t save the infected computer, but it could possibly keep other systems from also getting the infection.
Determine the Scope of the Attack
After getting help, assessing the damage that has been done and understanding the attack is the next priority.
“Determine the scope of the incident, what systems were impacted, the initial attack vector, and whether there are active backdoors deployed,” advises Charles Carmakal, chief technology officer for security firm FireEye Mandiant. “What is the scope of the incident? How many systems have been impacted?”...get more info at - Toolbox.

Find out what kind of ransomware you have
First, you'll need to determine whether you've been hit by encrypting ransomware, screen-locking ransomware or something that's just pretending to be ransomware. See whether you can access files or folders, such as the items on the desktop or in the My Documents folder.
If you can't get past the ransom note you see on your screen, you're likely infected by screen-locking ransomware, which is not so bad. If you see a notice claiming to be from the police, the FBI or the IRS that says you've been caught looking at pornography or filing false taxes and must pay a "fine," that's usually screen-locking ransomware, too.
If you can browse through directories or apps but you can't open your regular office files, movies, photographs or emails, then you have encrypting ransomware, which is far worse.
If you can both navigate the system and read most files, then you're probably seeing something fake that's just trying to scare you into paying. You can ignore the ransom note. Try closing your web browser. If you can't, then hit the Control, Shift and Esc keys at the same time to open Task Manager, choose the Application tab, right click the browser application and select End Task...visit - tom’s guide for more info.

UNDERSTAND WHAT'S CONNECTED TO YOUR NETWORK
PCs and servers might be where your data resides, but they aren't the only devices you have to worry about. Thanks to the office wi-fi, the Internet of Things and working from home, there's now a wide variety of devices connecting to the company network, many of which will lack the kind of built-in security you'd expect from a corporate device. The more devices, the greater the risk that one will offer hackers a backdoor into your network, and then use that access to move through your systems to more lucrative targets than a badly secured printer or a smart vending machine. Also, think about who else has access to your systems: are your suppliers aware of the potential risk of ransomware and other malware?
CHANGE DEFAULT PASSWORDS ACROSS ALL ACCESS POINTS
Clicking on a bad link in an email is probably the best known way of getting infected with malware, but it's far from the only way. Nearly a third of ransomware was distributed via brute force and remote desktop protocol (RDP) attacks, according to research by F-Secure. Brute force attacks are attempts by hackers to access servers and other devices by trying as many passwords as possible, usually with the aid of bots, in the hopes of hitting the jackpot...read more at - zdnet.com

Should you pay the ransom?
Of course, though, ransomware attacks have not dropped to zero. If you’re ever hit with a ransomware attack, you need to consider every possible avenue, one of which being — should you pay the ransom? The majority of companies say they would never consider paying a ransom (66 percent). However, in reality, about 65 percent do end up pay the requested amount.
The current advice is, understandably, to not pay the ransom. This simply creates more of a market for ransomware, encouraging attackers to continue. However, the hackers often ask for a sizable ransom but one that is still much lower than losing the data. They also often offer discounts for quick payment so companies pay without having time to consider all options...get more info at - Techgenix.

Conclusion
Malware and Ransomware are not going away soon and are here to stay. To make sure that your data is safe against these attacks, you will need good malware and ransomware protection service as the last line of defense to protect against phishing. User education is also very important. Always make sure that you look at links and avoid suspicious emails and websites.
1 note
·
View note
Text
How to Use Microsoft Remote Desktop

Remote Desktop allows you to access a Windows desktop from another computer in your local network or over the Internet. You can use it to run applications, send and receive data, and even print documents. Microsoft Remote Desktop is available as an app, a web browser, and as a client for Windows. If you want to use it, you'll need to download the app to your device, install it, and agree to its terms and conditions.
To start a remote desktop session, you first need to launch the Remote Desktop Connection tool. This tool is available for Windows, Mac, and Android devices. Upon opening the tool, you'll need to type in your username and password. Then, you'll need to add the computer that you're connecting to.
Once you've added the PC, you can customize its connection settings. These settings include how the application will display the screen, and what type of access you'll need to it. In addition, you'll be able to set a lockout policy. When you're finished, you'll be able to save the settings, and they'll automatically save.
Before you can start a remote session, you'll need to enter the credentials that you'll use to login to the desktop. You can also configure an IP address "white list" if you wish to limit the number of people that can access your PC. Be sure to check out this website at http://www.huffingtonpost.com/brian-de-haaff/is-that-product-manager-s_b_13730938.html for more info about software.
Once you've entered the credentials, you'll be prompted to confirm the settings you selected. A black panel will appear on the side of the screen. Click the Select users at DirectDeals.com that can remotely access this PC tab.
After you've confirmed the settings, click the Save Desktops tab. A preview of the remote desktop will be added to the visual queue. If you want to terminate the session, simply click the three-dotted menu button. Alternatively, you can minimize the window to the taskbar.
Depending on the configuration of your device, the RDP protocol will not always detect the remote display correctly. If you notice that the remote display is not being detected properly, you'll need to change the settings on your device. It may be possible to fix the problem by changing the connection resolution. However, this is not recommended unless you know the issue.
Alternatively, you can create a separate user account for each person you want to allow to access your PC. The different accounts can have different permissions, so you can give one user access to a particular file, while another can use the same file but have limited access.
If you need help, you can use the built-in Remote Desktop Connection tool, or you can open the Remote Desktop app on your phone. You can download the app from the Microsoft Store. As a downloadable application, it is available on Windows, Mac, and Android.
Remote Desktop is an excellent way to connect to a PC. You can easily access files, print documents, and even plug in devices. But you need to be careful with how you set up your connection, and you should also make sure to keep up with the latest security updates. Be sure to linked here!
0 notes
Text
Rdp is a protocol that provides an administrator with a secure way to manage multiple remote desktop sessions from one location. Administrators use Rdp to connect to and manage servers, workstations, and other devices on their network. Moreover, here you will learn how you can create a free RDP. Google Cloud offers free RDP access for creating Windows VPS instances. Keep reading this post to find out how to set up your Google Cloud account for RDP access and create a Windows VPS instance. What Is Google Cloud Platform: Google Cloud Platform (GCP), offered by Google, is a set of cloud computing services that operates on the same infrastructure that Google uses personally for its end-user products, such as Google Search and YouTube. GCP's features include machine learning, Big Data, and general computing capabilities. In addition, GCP offers storage, networking, Big Data, and computing solutions for business and enterprise customers. Google Cloud Platform's main products are: Compute Engine: A virtual machine service that is comparable to Amazon EC2. App Engine: A platform-as-a-service that allows developers to build and run applications on Google's infrastructure. Cloud SQL: A managed relational database service compatible with MySQL, PostgreSQL, and Microsoft SQL Server. Cloud Storage: An object storage service that offers high durability and availability. Cloud Bigtable: A NoSQL big data storage service. Free Rdp Create A Windows Vps On Google Cloud: Creating free RDP on Google Cloud is simple and easy. Follow the procedure steps below to set up your Google Cloud account for RDP access and create a Windows VPS instance: Visit the official page of Google Cloud Platform and sign in with your Google account. If prompted, enter your account information. To use this option, you must input your payment card information. Google, however, makes it very clear that there isn't an auto-charge after the free trial period. Once you have finished creating your google cloud account, go to the Google cloud console main page. Select Computer Engine from the menu in the upper left, then choose VM instances. In the upper-right corner of your screen, select CREATE INSTANCE. Configure the following three options on this page: name, the boot disk, and a firewall. For the boot disc settings, click "Change" next to the boot disc, and various boot disc options will appear.Specify the size of 50 GB and the "Windows Server 2012 R2 Datacenter" option; if you are on Windows 10, then you can specify depending on your requirements.Select and create an instance by clicking.Return to the page for VM instances and select the newly created VM instance. Here, you must follow these two steps in order: By selecting "Set Windows password," you may set the username and password. To get the RDP file, click RDP. The ability to connect to the server is made possible by this RDP file, which is crucial. Therefore, preserve it in a secure location in case you need to use it again in the future. Congratulations! You have successfully launched a free web server on the Google cloud platform with a Windows server installed. How Does Remote Desktop Works: A free RDP means accessing your computer from a remote location; the most common use for RDP is to allow someone to access their work computer from home or another remote location. Many software programs enable you to do this, but the most common is Microsoft Remote Desktop. When you set up a free RDP connection, you create a VPN (a virtual private network). This connection will encrypt all the data sent between your computer and the remote computer. This ensures that no one can eavesdrop on your conversation or see what you are doing. The free RDP software will also provide a way to connect to your work computer from anywhere in the world. This can be extremely useful if you travel frequently or work from home.
As mentioned in the previous step, setting up a free RDP connection is relatively simple. However, it is essential to remember that you follow all instructions correctly. If you do not, you may end up with an unstable connection, or worse, you could end up damaging your computer. What Are The Features And Advantages Of RDP: Remote Desktop Protocol or RDP offers many features to system administrators. It is a client-server protocol that provides users with a consistent graphical interface (GUI) regardless of the type of client device they are using. RDP also offers security measures, such as encryption, to protect data transmitted between the client and server. Some of the advantages and features of RDP include: Accessed Unattended: When no one is physically available at the remote end, you might frequently need to establish a connection to a client's computer as remote assistance professional. Or if you frequently need to assist a particular customer. In either scenario, unattended access can be useful. Thanks to this functionality, you won't need to interrupt the client to grant control each time they request help or continually guide them through the connection procedure. Instead, you'll appreciate always having remote one-click access to the client's PC. Multi-Window Control: The protocol enables you to view a remote computer in its entirety and lets you open multiple windows within that desktop for different purposes. For example, you may want one chat window with the client while another is used to fix their issue. Another advantage of this feature is that each window can be sized differently so that you can make the most of your screen space. Having multiple windows open allows you to work on several tasks at once without constantly switching between them. File Transferring: In addition to providing a graphical interface, RDP also offers a way to transfer files between the client and server computers. This can be extremely useful if you require to send a file or document to the client quickly or if you need to receive a file from them. To transfer files, you need to open the file on the server computer and then save it to the client computer. Alternatively, you can pick and drop the selected file into the RDP window. Either way, the file will be transferred securely and will only be accessible to those who have the necessary permissions. Printing: RDP also offers the ability to print documents and files remotely. This can be extremely useful if you need to print a document for the client but do not have a printer available. To print a document, you need to open it on the server computer and then select the Print option from the File menu. The selected document will then be sent to the client's computer and printed on their printer. Security: Network security is supported by Remote Desktop Protocol in a number of ways. RDP brings in more experts in charge of protecting the server's integrity. This includes ensuring you are protected from the most recent security risks. Furthermore, every piece of information sent across the network is continuously encrypted. This safeguards against hackers attempting to access important data transmitted over the internet. Remote Desktop Protocol protects against data loss because numerous screens can be shared and because backups simplify file recovery. Last but not least, sensitive information comprising financial records or private customer information can be blocked from view by any remote employee by marking it off. Auto Reboot & Reconnect: One of the key functions of a remote desktop program is the capacity to restart a remote computer and instantly rejoin. By emptying caches, flushing the RAM, and enabling you to start over, a reboot aids in returning the computer to a comparatively clean state. The auto-reboot feature is necessary for technical support sessions since this "clean-sheet" is frequently needed when a computer's performance is erratic or in need of repair.
Additionally, technicians frequently apply software upgrades and patches that need to be rebooted thereafter. Such tasks would otherwise necessitate ending the support session and beginning a fresh one after each reboot without the remote reboot option. Log Off/Log On & Switch User: When you need to work on computers with several Windows User accounts, logging on as a different user on a remote computer is highly useful. In a corporate setting where many individuals may only use their unique Windows accounts, you might run into this situation on shared PCs. You can install programs or updates for each person's remote user using the log off/log on capability. Otherwise, starting a new session under each Windows user would be necessary, which would greatly slow down and complicate the task at hand. Additionally, this capability can come in handy if you frequently need to carry out tasks that call for admin access. By connecting to a limited user account in this manner, you can elevate to the admin account and carry out administrative actions, like installing software or altering settings that have an impact on other users. Enable Cost Saving: The cost-effectiveness of RDP is another advantage. Any business or individual using the technology will save money. Technicians can quickly fix machines from a distance if they are enabled for the Remote Desktop Protocol. This alone lowers the expense of maintaining a device. An organization can anticipate a strong return on investment by investing in the Remote Desktop Protocol. It is more efficient to have more work done remotely and potentially even hire certain remote workers on a full-time basis. This enhances production and boosts the company's return on investment. RDP provides a lot of advantages and costs savings for businesses of all sizes. It is important to work with a trusted provider to get the most out of this technology. Investing in the right tools and training for your team can make all the difference in how well RDP works for your company. Freedom to Work from Anywhere: The RDP gives you the freedom to work from almost everywhere in as much as you have a computer with an internet connection. You can work from anywhere and at any time, which is great for those who want to be their own boss or have a flexible work schedule. All you need is an internet connection and a computer, and you're good to go! There are a few things to keep in mind when using the RDP though. The first is that you'll need to have a reliable internet connection. If your internet goes out, so does your work! Additionally, because you're working remotely, you won't have the same level of support that you would if you were working in an office. Be sure to have a plan in place for how you'll stay connected and get help if you need it. Overall, the RDP is a great way to work from anywhere. It's flexible, efficient, and can be a great option for those who want to be their own boss or have a more flexible work schedule. Just be sure to have a solid internet connection and a plan for how you'll stay connected and get help if needed. Final Words: Google Cloud Platform is a great option if you're looking for a more affordable way to get started with Windows VPS hosting. You can use the free RDP tool to create a Windows server in minutes, and the platform provides a wide range of features and pricing plans to fit your needs. With Google Cloud, you get the power of the Google infrastructure behind your VPS, making it a great choice for businesses that need reliability and performance. Hope you have found this post on free RDP create windows VPS on google cloud helpful and useful if you have any concerns related to this post, then please feel free to leave your candid feedback in the below-given box. FAQs:
0 notes
Text
Streamline Your Windows Server Connection: Save Login Credentials

Linux administrators often find themselves working across various platforms, including Windows Server environments. While Linux offers robust security features, integrating it seamlessly with Windows RDP can pose challenges, particularly when it comes to remote desktop connections. However, with the right approach, you can simplify this process and enhance cross-platform collaboration.
Windows Server provides Remote Desktop Protocol (RDP), a powerful tool for remotely accessing servers and workstations. However, logging in each time can be tedious, especially when dealing with multiple servers. By saving your login credentials securely, you can bypass this step and establish connections swiftly, improving efficiency and workflow.
When you buy RDP services or manage existing ones, ensuring secure access is paramount. Saving login credentials doesn’t mean compromising security; rather, it involves using encryption and other protective measures to safeguard sensitive information. By adhering to best practices, such as regularly changing passwords in RDP sessions and implementing multi-factor authentication, you can mitigate potential risks and maintain a robust security posture.
Changing passwords in RDP sessions is essential for maintaining security hygiene. Regular password updates help thwart unauthorized access and enhance overall system resilience. Additionally, enforcing complex password policies further strengthens your defenses against potential threats, safeguarding critical data and resources.
Implementing these strategies not only enhances security but also streamlines your workflow, allowing you to focus on essential tasks without unnecessary interruptions. By optimizing your Windows Server connection, you can improve productivity and efficiency, empowering your team to achieve more in less time.
In conclusion, leveraging the capabilities of Windows Server and RDP can revolutionize how you manage server connections. By saving login credentials securely and adhering to best practices, such as changing passwords regularly, you can enhance security while streamlining your workflow. Whether you’re a Linux administrator or a Windows enthusiast, these techniques offer valuable insights into optimizing your server management experience.
In today’s fast-paced business environment, every second counts. By adopting these strategies, you can unlock the full potential of your Windows Server environment, maximizing productivity and driving business growth. So, why wait? Start implementing these tips today and experience the transformative power of streamlined server connections.
0 notes
Text
Mobile mouse pro always right click

Mobile mouse pro always right click how to#
Mobile mouse pro always right click pro#
Mobile mouse pro always right click password#
Optionally disconnect/disable your keyboard and test your mouse buttons. Open your Keyboard Viewer and make sure that your Control key is not stuck. G903 mireless mouse works fine, but it suffers from stuttering constantly.
Mobile mouse pro always right click pro#
I've been looking at Barracuda and Meraki. Go to: Apple > System Preferences > Keyboard & Mouse > Mouse and check to make sure that your Primary Mouse Button is set to Left. G Pro wireless skipping out/stuttering Right-click on Windows or Start. We are a business about 500 users, we have 9 locations, main datacenter is at the headquarters and about 50 VPN/remote users. Strangely, the mouse forward button is always working properly. This is the same with the mouse back button. However, if pressed one more time, the backward function is executed. When i press the first right mouse button, it works properly. Navigate to the Webroot SecureAnywhere application and double-click it. Yes, pressing the right mouse button or the back button executes the backward function. Wondering what type of firewall/next-gen everyone would recommend. Webroot Mobile Security scans apps for malware and viruses and keeps you safe.
Firewall for medium busines with multiple locations Security.
Find Related settings section in the right pane. Most USB receivers for wireless mice and keyboards operate in the 2 4Ghz band VIA SCIENTIARUM Expand Mice and other pointing devices then Right-click and. Navigate to the Mouse option from the left pane. Press Start + I on the keyboard to open Settings panel.
Mobile mouse pro always right click how to#
While "It's not a bug, it's a feature," is a fairly well known joke, did you know that back on September 9, 1945, the first actual. How to Fix When Right Click Menu Pops up Automatically Solution 1: disable ClickLock. It has been a week of ups and downs but we have finally made it to Friday!
Snap! KEV catalog updates, Data Center Alley, GIFShell, Harvest Moon, Babylon 5 Spiceworks Originals.
Mobile mouse pro always right click password#
When I ask why they didn't changed the password they said. Now, I can move around the screen, but it keeps selecting everything since my computer thinks I'm clicking down the mouse. I didn't do anything out of the ordinary, and yesterday I noticed that the mouse button never popped back up as it should after you click. Hi,I have a lot of users confronting login problems with their AD and VPN accounts (vpn is synchronized with AD account), because their password expires and they don't change the password on time. I've recently noticed that there is a problem with my mouse.
How to make password expiration notification permanet until password change? Windows.
I was thinking perhaps setting up a jump box or bastion host with MFA. MFA sounds like a good start but I'm not sure the best options are to do this. Hello,I am looking for recommendations on how to secure RDP for access to Windows Servers.

0 notes