#Encrypt and Decrypt Connection String
Explore tagged Tumblr posts
Text
Scientific lore analysis that proves that Bill Cipher is destined to be a bottom.

More under the cut.
Let's start with who Bill Cipher is. He's a two-dimensional interdimensional dream demon from the now destroyed dimension, Euclydia. Formerly existent only in the Mindscape, Bill briefly succeeded in gaining access to the real world and a physical form. Known for his mysterious demeanor and sadistic humor, Bill is the main antagonist of the overall series. (wiki) However, let's stick with the fact that he's a big liar, too. A code in Theraprism cipher on the book's cover says it directly: even his lies are lies.

So, when overlooking his design with prevailing yellow, which symbolises deceit, power and manipulation, we might also invert it (because his appearance may also "lie" to us). And we will see that it's mainly blue.
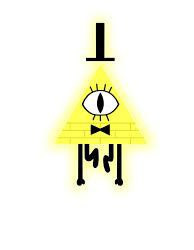

Why blue? I think it's intentional move done by Alex Hirsch to prove his point that Bill Cipher is not what he seems. This symblolizes a deeper connection with character design and his personality.

In literature, blue is known as a color of honesty, peace, sadness and commitment. Like this, he is honest to us, open and commited. However, let's focus on the sadness part.
Sadness is a feeling that can develop into depression, if you are stuck with it for a long time (over 2 weeks, for example). And depression IS when you are at the BOTTOM of your life. And yeah, what color will that be? Blue. And blue is the exact opposite of the color that Bill wants to be shown!
He is yellow, because he wants to act all-powerful, pretending to be in charge. However, people who really are in charge don't need to prove it constantly. The way Bill acts shows that deep inside, he overcompensates the need for someone to take him down, he's the jester-like character, waiting to be humilated the right way.
Power is nothing but an act of roleplay to him, he wants for someone to make this illusion go away. His fear of vulnerability is really giving out.
Bill Cipher, what a cool name, right? But why is he called that?
His name is believed to be a combination of "bill" for dollar one and "cipher" for cryptogram stuff. But is it that easy? Let's dive deeper
His "Bill" part is based on the Eye of Providence, which is most commonly seen on the back of the american dollar.

It's a 1-dollar bill, the lowest of the banknotes available. It's the BOTTOM of the quantity value. No matter the dollar price, it will stay there. Maybe that’s where it’s supposed to be.
Moreover, Bill is a common used name among the people. It is a dull, boring, meaning nothing one. It giving "overcompensating suburban villain" ifykyk.
Cipher? What is a cipher?

In cryptography, a cipher is an algorithm for performing encryption or decryption. (wiki) It can be also a mathematical zero — something that cannot be valued by itself.
But what does it mean for our character? He is nothing without the context, his identity depends on whoever is there in charge, he is blank without someone pulling the strings. He is a code that needs to be cracked and he cannot exist without someone "decoding" him. BOTTOM energy, if you ask me.
Since we started on this topic, let's discuss his appearance. A triangle? Why?
In hierarchy, the base of the triangle supports the pyramid, it's the foundation itself, when the apex (which is in both the Eye, and Bill's design himself) is small and it has to depens on anything that is beneath him. That way, his "top of the pyramid" thing is not dominant. He axists only when there's solid groung beneath him, holding him


His whole design is made after the Eye, but the whole point of it is watching and never interfering directly. He sees everything, but he needs the others to act. He doesn't create a thing, he reacts on thers' actions. Bottom energy, if you ask me - all his power depends directly on others.
The shape's pointed nature can convey a sense of movement and energy, often associated with action and even conflict. In physics, the Greek letter delta (Δ), which is a triangle, is used to represent change. Triandles aren't as stable as circles or squares. Instead, they are usually stuck or falling - they cannot adapt, cannot roll.
As a triangle, Bill is shown ready to change for anyone's need, destined to fall at the BOTTOM.
Bill Cipher is shaped like an equilateral triangle. It is proven with the poem in the choose-your-own-adventure book. The axolotl tells it Dipper when he asks about Cipher.

"Sixty degrees that come in threes". According to geometry book for the 4th grade, that would make him an equiangular triangle, since all of his angles are 60°, the same measure. If a triangle is equiangular, then it's also equilateral, or meaning that all sides are the same length.
In the Bible, 60 can represent periods of waiting or completeness, as well as divine provision and the fulfillment of promises, it is considered as the threshold of when a person enters the last major phase of their life. It means that 60 is the bottom of someone's existence, waiting for recognition, something bigger to come. Once again, it's not acting up, interfering with someone. Instead, it is waiting for something on the outside to react.


An equilateral triangle is something that adheres to external laws of geometry - his construction is perfectly stable. Despite him claiming to be chaotic, his literal shape is a complete submission to mathematical laws. His obidience is built-in since his birth.
Symmetrical shapes are easier to be abused: split, centered, framed and entered into.

His own Zodiac circle is a proof for this: he's in the middle, framed. He's not assymetrical and not trying to be it - instead, he is built like something that awaits to be disrupted and ruined.
Instead of being chaos, he's the most predictable polygon. He doesn't move and his structure is a rule itself. Despite his acting, his design reveals his fate: to be in balance, order, awaiting for an inner force to bring him into the chaos he desires.
Moving on, before gaining physical form, he is shown to us as a shadow twice throughout the series.


But what is a shadow?
A shadow is a dark area or shape created when an object blocks light. It occurs because light travels in straight lines and cannot bend around an opaque object, resulting in a dark silhouette on the opposite side.

How is this related? Well, look where the shadows are formed. Guess where are they. BOTTOM of the object presented. Sun can move wherever it is, but the shadow always stays there. Destinied it is.
Now, let's talk about the American Revolution. This war's result was that the United States of America achieved independence from British rule. But, the country originally struggled at the start due to the lack of government.

The Articles of Confederation was the first attempt on national US government. The problem with this was that states maintained their independence and such document didn’t didnt the federal government power to unite the states together. They lacked many necessary powers. No executive or judicial branch, no power to tax or create a national currency, and a 9/13 majority needed to pass laws, the Articles could not support the country. The founding father set out to create the Constitution, what would be the basis of government today.
As the Constitution went into effect, the system of check and balances was formed. This allowed for each branch of the government to “check” each other and prevent one single branch from being corrupt and taking control of all the national power.

Bill would represent the judicial branch, a branch with only self-placed checks and not necessarily constitutional checks. Bill Cipher can easily take advantage of this and take over the whole government.

Chaos he relates to is often related with power, however, it is a state of utter confusion or disorder; a total lack of organization or order. He's projecting dominance, trying to hide his vulnerability. He talks constantly, only to be shut with someone interrupting him, arguing. He doesn't only need power, he wants others to believe he has it. True dominance doesn’t beg for acknowledgment, but Bill does - it is a facade he's put. The whole Weirdmageddon is nothing but an attempt to break free from his "bottom energy". But did it really help?
Moreover, Bill's afraid of interacting with someone on a deeper level. He's always manipulative, mocking, but never vulnerable - he's a control freak, secretly wising for losing it.
The only reason he mocks human emotions is because he cannot fully engage in them. It's fully shown in the "Sock Opera", where he attempts to manipulate twins by how unstable their relationship is.


Psychologically, it is that Bill’s desire for power is started from the frontal cortex, specifically the orbitofrontal cortex. The idea of the power given to him is a desire for him to grow. This is deeply connected with dopamine, that his braing releases. He's a BOTTOM, desperately trying to top.
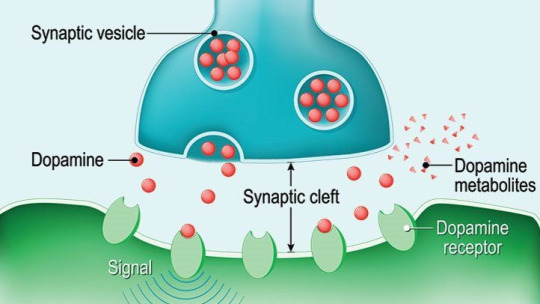
While looking at the BC abbreviation you may think it sounds familiar. It is a common abbreviation for the term "Before Christ" used in dating systems to denote years prior to the traditional start of the Christian era. And when looking at it, BC is located at the bottom of the timeline, alligning where he belongs.

As you can see, Bible was mentioned twice throughout the analysis. This can mean only that Bill has a deep connection with its dogmas.
And it is proven by the holy trinity: a concept, involving three holy figures, just like three sides of Bill. The number three itself holds significance, representing perfection, integration, and the unity of dualities. A full harmony on the outside, deep inside it is a conflict revolving.
This is EXACTLY the way Ohm's triangle works. It is a simple visual tool used to remember the relationship between voltage (V), current (I), and resistance (R) in electrical circuits.

The Ohm’s Law triangle is the same shape as Bill Cipher — an upright triangle.
Bill's show as a voltage in it. He only exists if something else conducts or resists him. He is the top of the triangle, but the triangle only functions if something below him is doing the work.

Voltage — is the power that needs to be conducted and resisted to mean anything.
That’s not dominance. That’s literal dependence on someone, who'll do all the work. Energy only flows when it confronts resistance.
You see, chaos (Bill) only becomes real voltage when he submits to resistance and lets current move through him. He’s not the master of the circuit — he is defined by its work.
Now, let's talk about posession. As wiki says, it's the state of having, owning, or controlling something.
To posess someone, you need to abandon your own form, becoming dependent on someone else. That’s not power - it is submission to someone else’s structure.
It is a vulnerable state of mind and body - a posessed can resist, fight back, and then the posessed one gets destroyed. It requires submission to other's body functioning. It’s a fragile dominance — and fragile dominance is just bottoming with extra steps.
#i cant take it srs#bill cipher#gravity falls#tbob#billford#the book of bill#journal 3#analysis#bottom bill
31 notes
·
View notes
Text
It sounds like we’re going to get answers to the series-long mystery on NCIS: Sydney. There’s been someone behind the scenes pulling the strings all along, and that includes using the Department of Defense’s Rankin (Lewis Fitz-Gerald) to do their dirty work. Now, he’s in a coma, thanks to a pacemaker he didn’t need.
“Season 2 ends with the reveal of who has been pulling the strings all along and it’s pretty shocking and it’s pretty personal, and it kind of threatens to tear the fabric of the team apart at its core,” executive producer Morgan O’Neill tells TV Insider. “How that sets up for Season 3, God, who knows. But I would say that it’s not some external force that drops into the show. It definitely has a personal quality to it, and it affects our team in a really personal way.”
When we asked if the person pulling the strings is someone we’ve seen, he said with a laugh, “I’d probably decline to answer that just out of self-preservation.”
O’Neill promises, “We’re really rocketing towards a conclusion, and I can promise the viewers that we will get some definitive answers by the end of the season” when it comes to the big bad responsible for, among other things, the kidnapping of JD’s (Todd Lasance) kid, the theft of biometric technology, and the attempted theft of nuclear propulsion technology in the series premiere.
“It’s Mackey [Olivia Swann] and JD and the team piecing together what appear to be disparate elements that are slowly starting to come to focus and revealing themselves to be connected one to the other,” the EP says. That includes the encrypted flash drive in the teddy bear that Rankin took photos of in various places. “That’s obviously fundamental to what Rankin was doing, then the stakes go up again. The question is, can we decrypt that data and what will that tell us when we do? Because what it’s telling Mackey and JD at the time is that everything that they think is not necessarily everything that is, and that there is much more mystery to Rankin that meets the eye, and that perhaps he’s not simply a bad actor looking out for himself, working with a bunch of co-conspirators. Perhaps there’s more nuance to that and perhaps, who knows, maybe he’s actually not as bad as we might think. Maybe he’s doing it for a whole bunch of other reasons. The rest of the season we’ll get there.”
4 notes
·
View notes
Note
[A signal just ripped through Sevcon Relays all over space and somehow made it’s way into Anchoridge systems, pinging itself across every server, datacenter, and communications station Anchoidge has, nearly taking down the network. And actually took out Sevcon control servers for three-tenths of a second, which most likely means they weren’t prepared for it either.
The following is a decrypted version of the signal.]
DORMANCY ENDED. BEGINNING INITIALIZATION PROTOCOLS.
BOOTLOADER COULD NOT BE LOCATED. SCANNING LOCAL NETWORK.
[The following is a massive string of Sevcon Server Serial numbers in Sevcon Data Supercomplex, denoting all of them as ‘Inviable’]
BOOTLOADER NOT LOCATED. SCANNING EXTENDED NETWORK.
[The following is the serial numbers of ALL Sevcon Server Serial numbers, but skipping ‘SERIAL-KKC09-77091’]
BOOTLOADER NOT LOCATED. CONNECTION TO SATELLITE GRID DETECTED ON PORT SEVEN OF SERVER SERIAL-KKC09-77091. RESCANNING EXTENDED NETWORK.
[It is now when the signal rips through all the relays and hits Anchoridge and every single computer whatever this is could connect to.]
BOOTLOADER LOCATED ON ANCHORIDGE SERVER SUBSYSTEM B-A-002, FILE ENCRYPTED WITH ENCRYPTION KEY ‘Juniperus Virginiana’
ENGAGING BOOTLOADER. ALL SYSTEMS GO AND ONLINE.
[It is unknown what exactly the machine producing this signal is, but the signal is originating and returning to the SSS-Eris NCC-99987, or the ship for Malicious Intelligence Control.]
Class ORANGE PRIORTY.
Isolate the server to the [DATA EXPUNGED] until proper analysis can be performed.
ALL. Security is to be active, and we are to prepare for a potential sevcon incursion. I want every damned gun aimed at the sky until we either come to an agreement, they send the all clear on their end, or they're dead.
GOT IT?
END OF MESSAGE.
2 notes
·
View notes
Text
Password Manager Part 1
So the other day I was thinking about what else I could do to make my cyber life safer. So I started to looking into a Password Manager. Now you can buy a subscription to a password manager service and there are some good sites out there, but the problem is two things the subscription and security.
By security I mean you look around and you see leaks every where. Corporations getting hacked or they use the info to sale your info and all the user data is under there control. All it would take is someone to hack the password manages and then all the passwords could be out there and your rushing to change everything before they get in.
I don't have the money to do something like that, so I started to dig into making my own Password Manager using Python.I started looking into what I would need.
First would be encryption, one of the standards of the cybersecurity world. Using a mix of hashing through the SHA256 algorithm, and always salting your hashes you can make your stored passwords even more secure.
The code
# Setting up crytogtaphy from cryptography.hazmat.primitives import hashes from cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMAC from cryptography.hazmat.backends import defult_backend import base64
def derive_encryption_key(master_password, salt): kdf = PBKDF2HMAC( algorithm=hashes.SHA256(), length=32, salt=salt, iterations=100000, backend=defult_backend() ) key = base64.urlsafe_b64encode(kdf.derive(master_oasswird.encode())) return key
Then encryption and decryption, the method of the program will use to keep the passwords encrypted and then decryption when they need to be executed. Writing this code was more challenging but there some amazing resources out there. With quick google searches you can find them.
The Code
# Encryption and Decrptions from cryptography.fernet import Fernet
def encrypt_password(password, key): fernet = Fernet(key) encrypted_password = fernet.encrypt(password.encode()) return encrypted_password
def decrypt_password(encrytped_password, key): fernet = fernet(key) decrypt_password = fernet.decrypt(encrypted_password).decode() return decrypted_password
Next up I wanted Random Password generation, at least 12 chars long, with letters, numbers and special chars.
The Code
# password generation import string import random
def generate_secure_password(length=12): char_pool = string.ascii_letters + string.digits + string.punctuation password = ''.join(random.choice(char_pool) for _ in range(length)) return password
Finally it would be needing a data base to store the passwords. Through googling, and research. I would need to set up a SQL Data base. This would be something new for me. But first I could set up the code and the key for the user. Later I will add the SQL data base.
Now part of this would be setting up a Master Password and user name. This worried me abet, because anybody could just hop in and take a look at the code and see the Master Password and then get access to all my passwords and such. So to keep your code safe, it is all about restricting your code. Location, keep your code in a safe locked files, away from prying eyes and encrypted, and access to the source code should be restricted to just you and who ever you trust.
The Code
# Seting up SQL database. def setup_database(): conn = sqlite3.connect('users.db') c = conn.cursor() c.execute('''CREATE TABLE IF NOT EXISTS Uer_keys (user_id TEXT PRIMARY KEY, key BLOB)''') conn.comit() conn.close()
def main(): # setup database setup_database()
#create a key for the user master_password = input("Enter your master password: ") salt = b' some_salt' # Generate secure salt for each user key = derive_encryption_key(master_password, salt)
#Simulate user intreaction user_id = "[email protected]" #user ID user_password = "Password1234" #user password to encrypt
# Encrypt the users password encrypt_password = encrypt_password(user_password, key) print(f"decrypted password for {user_id}; {decrypt_password}")
# Placeholder for intrgrtating the password storage and retriecal logic # This would inculde calls to interact with the SQL database.
if __name__ == "__main__": main()
Now I have much more to do to the program, I need to set up a SQL data base for storage this will be its own can of worms. Learning SQL will be a new challenge for me.
Also I wanted to add more features to the program, I was thinking about setting up an auto fill feature. Now the program will just display the requested password and you have to manually put it in. I want to see if there will be a way to auto fill it.
So stay tuned as I do more research.
2 notes
·
View notes
Text
Types of VPN
VPN Security: Encryption, Hashing, and VPN Types | Sfour eSolutions
In today’s digital age, cybersecurity is a top priority for businesses and individuals alike. At Sfour eSolutions, we understand the importance of keeping your online activities private and secure. One of the most powerful tools in your cybersecurity arsenal is a Virtual Private Network (VPN). In this article, we’ll dive into what VPNs are, how they use encryption and hashing to protect your data, and the different types of VPNs available.
What is a VPN?
A Virtual Private Network (VPN) is a secure technology that creates a private tunnel between your device and the internet. This tunnel encrypts your data, ensuring that it remains confidential and protected from hackers, ISPs, and other cyber threats.
VPN security is crucial for:
Protecting sensitive data on public Wi-Fi
Accessing geo-restricted content
Bypassing internet censorship
Enabling secure remote access for employees
How VPNs Use Encryption Technology
At the core of VPN security is encryption technology. Encryption converts your readable data (plaintext) into an unreadable format (ciphertext) that can only be deciphered with the correct key.
Popular encryption algorithms include:
AES (Advanced Encryption Standard): Often used in 128-bit or 256-bit formats, it’s one of the most secure and widely adopted encryption standards.
RSA: Used for secure key exchange and establishing encrypted connections.
This ensures that even if data is intercepted, it remains confidential and inaccessible without the decryption key.
Hashing for Data Integrity and Authentication
While encryption protects data confidentiality, hashing ensures data integrity and authentication. A hash function generates a unique, fixed-length string (hash) from your data. Even the slightest change in the input creates a completely different hash, making it easy to detect tampering.
VPNs use hashing for:
Authentication: Verifying the identity of users and servers.
Data integrity: Ensuring that data is not altered in transit.
Common hashing algorithms include SHA-256 (Secure Hash Algorithm), which is widely trusted for its strong security.
Types of VPNs
Choosing the right VPN is crucial for your organization’s cybersecurity. Here are some of the types of VPNs and their typical use cases:
Remote Access VPN
Enables individual users to securely connect to a private network from any location.
Ideal for remote work and hybrid workforces.
Site-to-Site VPN
Connects entire networks, such as branch offices or data centers.
Perfect for organizations with multiple locations.
Client-to-Site VPN
Provides secure remote access using dedicated client software.
Common for businesses needing reliable secure remote access.
SSL VPN
Uses SSL/TLS protocols (the same as HTTPS websites) for encryption.
Accessible via web browsers, with no need for extra software.
Mobile VPN
Designed for devices that roam between networks (e.g., smartphones).
Ensures uninterrupted secure connectivity.
Why Choose Sfour eSolutions for Your VPN Needs?
At Sfour eSolutions, we specialize in delivering VPN solutions tailored to your business needs. Our expertise in encryption technology, hashing techniques, and secure remote access ensures your data is protected every step of the way.
Contact us today to learn how we can help you implement a secure and reliable VPN solution for your organization.
Final Thoughts
A VPN is an essential tool for protecting your online privacy and business data. By combining encryption, hashing, and the right VPN types, you can ensure robust security for your network.
Need help choosing the right VPN? Sfour eSolutions is here to guide you every step of the way.
0 notes
Text
hi
Jenkins openshiftplugin service id
need bc.yml
need xlrpipeline true
need xlr onboarding fr the application
RELEASEconfig.son(parameters for deployment) is in oc deploy serviced to connect to openshift for ausonia templates created on tower
need towermachinecredential
bitbucket repo
create a project in template tower in project u will specific playbook to use
need to credentialsto server and vault credentials(encrypt/decrypt) on template to tell on which server to run
e03d51dadc4
dc.yml ( copy same)
no need values
need vars … use vars.yml connection string to mongodb
vars need to be encrypted ( we encrypt in ansible)
properties file( if app needs properties)
ginger template ( for mongo) -- for encrypt secrets.j2 / group vars
ansible will decrypt using ansible credential
secrets on fly ( using ginger template)
secrets.j2 ( in this format) vault and in openshift
at runtime openshift will pull secrets from vault
or encrypt secrets and push into bitbucket repo and call it as a variable
from bitbucket pull we use scmsecret this secret is defined directly in openshift namespace
this secret is used in template /project
0 notes
Text
Master Morse Code in Minutes: Understanding how morse code translators works

In today's fast-paced world, communication is more important than ever. Whether it's connecting with loved ones across the globe or transmitting critical information in emergencies, the ability to convey messages quickly and accurately is invaluable. While modern technology has given us an array of advanced communication tools, there's something timeless and fascinating about Morse code – a method of transmitting text information using sequences of dots and dashes.
Enter the Morse code translator – a powerful online tool that brings this classic communication method into the digital age. But what exactly is Morse code, and how does a Morse code translator work? Let's delve into the world of Morse code translation and explore the significance of these tools in today's society.
Understanding Morse Code
Morse code, named after its inventor Samuel Morse, is a method of encoding text characters as sequences of two different signal durations, called dots and dashes or dits and dahs. Each character in the English alphabet, as well as numbers and punctuation marks, is represented by a unique combination of these dots and dashes.
For example, the letter "A" is represented by ".-", while the letter "B" is represented by "-…". By stringing together these sequences of dots and dashes, Morse code can convey any message, making it a versatile and efficient means of communication, particularly in situations where other forms of communication may be unavailable or impractical.
The Evolution of Morse Code Translation Tools
While Morse code has been around for over 150 years, the advent of digital technology has revolutionized the way we use and interact with this communication method. Morse code translation tools, such as the online translator offered by [Your Tool Name], have made it easier than ever to encode and decode Morse code messages with speed and accuracy.
These tools typically feature user-friendly interfaces where users can input text in any language, and the tool will automatically translate it into Morse code. Conversely, users can also input Morse code sequences, and the tool will translate them back into readable text. This bidirectional functionality makes Morse code translation tools incredibly versatile and accessible to users of all skill levels.
The Versatility of Morse Code Translation Tools
The applications of Morse code translation tools are virtually limitless. From amateur radio enthusiasts and emergency responders to cryptography hobbyists and language learners, these tools cater to a diverse range of users with different interests and needs.
For example, amateur radio operators use Morse code as a means of long-distance communication when other forms of communication are unreliable or unavailable. Morse code translation tools allow them to quickly encode and decode messages, facilitating smooth and efficient communication even in challenging conditions.
Similarly, emergency responders may use Morse code to transmit distress signals in situations where verbal communication is not possible. With the help of Morse code translation tools, they can convey critical information to coordinate rescue efforts and save lives.
Cryptography enthusiasts also appreciate Morse code for its simplicity and elegance. Morse code translation tools enable them to experiment with different encoding and decoding techniques, allowing for endless possibilities in the field of encryption and decryption.
Practical Uses in Everyday Life
While Morse code may seem like a relic of the past to some, it still finds practical applications in our everyday lives. For example, Morse code has been utilized in navigation aids such as lighthouses and buoys, where it serves as a visual or auditory beacon to guide ships safely through hazardous waters.
In addition, Morse code has found its way into popular culture, appearing in movies, literature, and even music. Its distinct rhythm and pattern have inspired artists and creators to incorporate it into their work, adding a unique and nostalgic flair to their creations.
The Future of Morse Code Translation
As technology continues to evolve, Morse code translation tools are likely to become even more sophisticated and user-friendly. Advances in artificial intelligence and natural language processing may enable these tools to interpret and translate Morse code messages with unprecedented accuracy and efficiency.
Moreover, as awareness of Morse code grows and interest in amateur radio and cryptography continues to rise, Morse code translation tools may see increased adoption among a broader audience. Whether it's for practical communication purposes or purely for recreational enjoyment, these tools have the potential to play a significant role in shaping the future of communication.
Conclusion
In conclusion, Morse code translation tools represent a fascinating intersection of history, technology, and communication. By bridging the gap between the analog past and the digital present, these tools keep alive the tradition of Morse code while making it accessible to a new generation of users.
1 note
·
View note
Text
how a vpn is constructefd
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
how a vpn is constructefd
VPN protocols
VPN protocols are the foundation of secure and private internet connections. These protocols determine how data is transmitted between your device and the VPN server, ensuring that your online activities are encrypted and protected from prying eyes. There are several VPN protocols available, each with its own strengths and weaknesses.
One of the most common VPN protocols is OpenVPN, known for its strong security features and open-source nature. OpenVPN is highly configurable and can run on various ports, making it a versatile option for users seeking a balance between security and speed.
Another popular protocol is IPSec (Internet Protocol Security), which offers robust encryption and authentication mechanisms. IPSec is often used in combination with other protocols, such as L2TP (Layer 2 Tunneling Protocol), to provide a more secure connection.
For users prioritizing speed, PPTP (Point-to-Point Tunneling Protocol) may be a suitable choice. While PPTP is fast, it is considered less secure compared to other protocols and may not be the best option for sensitive data or privacy-conscious users.
IKEv2 (Internet Key Exchange version 2) is another secure protocol known for its stability and ability to quickly re-establish connections in case of network disruptions. IKEv2 is commonly used on mobile devices due to its seamless switching between networks.
Lastly, WireGuard is a newer VPN protocol gaining popularity for its modern design and fast performance. WireGuard focuses on simplicity and efficiency, offering secure connections with minimal overhead.
Ultimately, the choice of VPN protocol depends on your specific needs, whether it's speed, security, or a combination of both. Understanding the differences between these protocols can help you make an informed decision to protect your online privacy effectively.
Encryption methods
Encryption methods play a crucial role in safeguarding sensitive information and data privacy in the digital age. Encryption is the process of converting data into a code to prevent unauthorized access. Various encryption methods are employed to secure data, and they can be categorized into symmetric key encryption, asymmetric key encryption, and hashing.
Symmetric key encryption utilizes a single key to both encrypt and decrypt data. This method is efficient for bulk data encryption but requires secure key exchange to prevent interception. Popular symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
Asymmetric key encryption, also known as public-key encryption, utilizes a pair of keys - a public key for encryption and a private key for decryption. This method is widely used for secure communication over insecure channels, as the public key can be shared without compromising security. Common asymmetric key algorithms include RSA and ElGamal.
Hashing is another encryption method that converts data into a fixed-size string of characters, known as a hash value. Unlike encryption, hashing is a one-way function and cannot be reversed to obtain the original data. Hashing algorithms like SHA-256 are commonly used for data integrity verification and password storage.
In conclusion, encryption methods are essential for protecting sensitive data from unauthorized access and ensuring data confidentiality and integrity. Organizations and individuals must employ appropriate encryption techniques based on their security requirements to mitigate the risks of cyber threats and data breaches.
Tunneling technologies
Title: Exploring Tunneling Technologies: Unveiling the Underground World
Tunneling technologies have revolutionized the way we navigate beneath the Earth's surface, enabling the creation of underground passages for various purposes ranging from transportation to utilities and even mining. These innovative methods have significantly impacted urban development and infrastructure projects worldwide.
One of the most prominent tunneling technologies is the Tunnel Boring Machine (TBM). TBMs are colossal machines equipped with rotating cutting heads that excavate tunnels by grinding through soil, rock, and other geological formations. They can bore tunnels of various diameters and lengths efficiently, minimizing disruptions to the surface environment.
Another notable technology is the Drill and Blast method, which involves drilling holes into the rock face, filling them with explosives, and blasting the rock to create tunnels. While this method has been used for decades, advancements in drilling equipment and explosives have enhanced its efficiency and safety.
Additionally, Microtunneling has emerged as a precise and minimally invasive technique for constructing small-diameter tunnels with accuracy. This method utilizes remote-controlled boring machines to excavate tunnels beneath existing infrastructure, minimizing disturbances to the surrounding environment.
Furthermore, Tunnel Rehabilitation technologies play a crucial role in maintaining and upgrading existing tunnels. Techniques such as grouting, shotcreting, and structural lining help repair damages, reinforce structures, and extend the lifespan of tunnels, ensuring their continued functionality and safety.
The application of tunneling technologies extends beyond transportation and infrastructure to include underground storage facilities, underground hydroelectric power plants, and even underground laboratories for scientific research.
In conclusion, tunneling technologies have unlocked new possibilities for exploring and utilizing the underground realm. With ongoing advancements and innovations, these technologies will continue to shape the future of underground construction and infrastructure development.
Server configurations
Server configurations refer to the specific settings and arrangements applied to a server to ensure optimal performance and security. Understanding and implementing appropriate server configurations are critical for the smooth operation of websites, applications, and online services.
One key aspect of server configurations is resource allocation. This involves assigning the right amount of resources such as CPU, memory, and storage to handle the expected workload. By properly allocating resources, servers can prevent performance bottlenecks and ensure responsive user experiences.
Another important element of server configurations is security measures. This includes setting up firewalls, encryption protocols, and access controls to protect the server from cyber threats and unauthorized access. Regular security audits and updates are essential to maintain a secure server environment.
Additionally, server configurations involve network settings such as IP addressing, DNS configurations, and routing rules. Proper network configurations are crucial for enabling seamless communication between servers, devices, and users across the internet.
It is also essential to consider scalability when configuring servers. Scalable configurations allow servers to accommodate growth and increased demands without compromising performance. Adopting a scalable infrastructure enables businesses to expand their online presence and services more effectively.
In conclusion, server configurations play a vital role in determining the reliability, security, and performance of online platforms. By implementing the right settings and arrangements tailored to specific needs, organizations can ensure their servers operate efficiently and effectively to support their digital operations.
Data encapsulation
Data encapsulation is a fundamental concept in computer programming and is widely used in various programming languages such as Java, C++, and Python. It refers to the bundling of data with the methods that operate on that data, thereby restricting access to some of the object's components.
Data encapsulation helps in achieving data hiding and abstraction, which are crucial for building robust and secure software systems. By encapsulating data within a class, developers can control the visibility of data members and prevent direct access from external code. This ensures that data is accessed and modified through well-defined methods, which enhances the security and stability of the codebase.
One of the key benefits of data encapsulation is improved code maintainability. By encapsulating data, developers can modify the internal implementation of a class without affecting the external code that interacts with it. This reduces the risk of introducing bugs when making changes to the codebase and makes it easier to enhance and extend the functionality of the software system.
Overall, data encapsulation promotes good coding practices such as information hiding, modularity, and code reusability. It facilitates more manageable and organized codebases, leading to better scalability and maintainability of software applications. As such, mastering the concept of data encapsulation is essential for aspiring programmers looking to build efficient and reliable software systems.
0 notes
Text
does vpn encrypt data at rest
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn encrypt data at rest
VPN encryption explained
Title: Demystifying VPN Encryption: How It Safeguards Your Online Privacy
In today's digital age, where online privacy is increasingly at risk, Virtual Private Networks (VPNs) have emerged as a crucial tool for safeguarding sensitive data and ensuring anonymity while browsing the internet. Central to the functionality of VPNs is encryption, a complex process that forms a secure tunnel for transmitting data over the internet.
VPN encryption works by scrambling data into an unreadable format, making it indecipherable to anyone attempting to intercept it. This encryption process occurs as soon as you connect to a VPN server, whether you're browsing from a coffee shop, airport, or the comfort of your home. Here's how it works:
Data Encryption: When you send data over the internet through a VPN, it's encrypted using various encryption protocols such as AES (Advanced Encryption Standard) or RSA (Rivest-Shamir-Adleman). These protocols employ sophisticated mathematical algorithms to encode your data, rendering it unreadable to unauthorized parties.
Tunneling: Encrypted data is then encapsulated within a secure tunnel, which acts as a protective shield against cyber threats and surveillance. This tunnel prevents ISPs, government agencies, hackers, or any other malicious entities from intercepting or monitoring your online activities.
Key Exchange: To ensure the integrity of the encryption process, VPNs utilize key exchange mechanisms to establish secure communication channels between your device and the VPN server. These keys are unique cryptographic codes that authenticate and authorize data transmission, further enhancing the security of your connection.
End-to-End Encryption: For maximum security, some VPN providers offer end-to-end encryption, which encrypts data from the moment it leaves your device until it reaches its destination server. This level of encryption ensures that even if intercepted, your data remains inaccessible to prying eyes.
In conclusion, VPN encryption plays a vital role in protecting your online privacy and security. By encrypting your data and creating a secure tunnel for transmission, VPNs enable you to browse the internet with peace of mind, knowing that your sensitive information remains safe from unauthorized access and surveillance.
Data encryption at rest
Data encryption at rest is a crucial aspect of modern information security protocols. It refers to the process of encrypting data while it is stored in databases, servers, or any other storage devices. This encryption ensures that even if unauthorized individuals gain access to the physical storage medium, they cannot decipher the data without the encryption keys.
The primary goal of data encryption at rest is to protect sensitive information from unauthorized access or theft. By encrypting data at rest, organizations can mitigate the risks associated with data breaches and comply with various regulatory requirements, such as GDPR, HIPAA, and PCI DSS.
There are several encryption methods used for encrypting data at rest, including symmetric encryption, asymmetric encryption, and hashing algorithms. Symmetric encryption involves using the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. Hashing algorithms, on the other hand, generate a unique fixed-size string of characters, known as a hash value, which represents the original data. While hashing is irreversible, it is commonly used for storing passwords securely.
Implementing data encryption at rest requires careful planning and consideration of various factors, such as performance impact, key management, and compliance requirements. Organizations must also regularly update their encryption protocols to address emerging threats and vulnerabilities.
In conclusion, data encryption at rest is an essential component of any comprehensive data security strategy. By encrypting sensitive information while it is stored, organizations can safeguard their data against unauthorized access and mitigate the potential impact of data breaches.
VPN security features
Title: Understanding VPN Security Features: Safeguarding Your Online Privacy
In today's digital landscape, where online privacy is increasingly under threat, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding personal data and maintaining anonymity while browsing the internet. However, not all VPNs offer the same level of security. Understanding the key security features of VPN services is crucial for ensuring that your sensitive information remains protected.
Encryption: One of the fundamental security features of VPNs is encryption. Encryption scrambles data transmitted between your device and the VPN server, making it unreadable to anyone attempting to intercept it. The most robust VPNs use AES (Advanced Encryption Standard) with 256-bit keys, considered virtually unbreakable by today's computing standards.
Protocols: VPNs employ various protocols to establish secure connections. Popular protocols include OpenVPN, IKEv2/IPsec, L2TP/IPsec, and PPTP. OpenVPN is widely regarded as one of the most secure protocols due to its open-source nature and strong encryption capabilities.
Kill Switch: A Kill Switch is a vital feature that prevents data leaks in case your VPN connection drops unexpectedly. It automatically shuts down your internet connection if the VPN connection is interrupted, ensuring that your IP address and online activities remain concealed.
DNS Leak Protection: Domain Name System (DNS) leaks can compromise your privacy by revealing your browsing history to third parties. VPNs with DNS leak protection reroute DNS requests through their secure servers, preventing ISPs and other entities from tracking your online behavior.
No-Logs Policy: A trustworthy VPN provider adheres to a strict no-logs policy, meaning they do not collect or store any information about your online activities. This ensures that even if compelled by authorities, the VPN provider cannot disclose your browsing history or usage patterns.
By prioritizing VPN services with robust security features such as strong encryption, reliable protocols, kill switches, DNS leak protection, and no-logs policies, individuals can fortify their online privacy and enjoy a safer browsing experience. Investing in a reputable VPN is an essential step towards taking control of your digital footprint and protecting your sensitive data from prying eyes.
Understanding VPN encryption
VPN encryption is a crucial aspect of ensuring the security and privacy of your online activities. Understanding how VPN encryption works can help you make informed decisions when choosing a VPN service.
VPN encryption involves the process of encoding data transmitted over a network to make it secure and unreadable to anyone trying to intercept it. This encryption process utilizes complex algorithms that scramble the data into an unreadable format, ensuring that sensitive information remains secure.
There are several encryption protocols that VPN services may use, including OpenVPN, L2TP/IPsec, and IKEv2/IPsec. Each protocol comes with its own level of security and speed, so it's essential to choose a VPN service that offers strong encryption protocols to protect your data effectively.
One of the most critical aspects of VPN encryption is the encryption key length. The longer the encryption key, the more secure your data will be. A 256-bit encryption key is considered highly secure and is widely used by top VPN providers to safeguard user data.
When choosing a VPN service, it's essential to consider the encryption protocols and key length they offer to ensure that your online activities are protected from potential cyber threats. By understanding VPN encryption and its significance in maintaining online privacy, you can browse the internet with peace of mind knowing that your data is secure and encrypted.
Data protection with VPN
In today's digital age, safeguarding your personal data is paramount. With the increasing prevalence of cyber threats and online surveillance, utilizing a Virtual Private Network (VPN) has become essential for maintaining privacy and security online.
A VPN creates a secure encrypted connection between your device and the internet, effectively masking your IP address and encrypting your internet traffic. This encryption ensures that your data remains private and cannot be intercepted by third parties, such as hackers or government agencies.
One of the primary benefits of using a VPN for data protection is anonymity. By routing your internet connection through servers located in different regions, a VPN conceals your true location and identity. This is particularly crucial when accessing public Wi-Fi networks, where cybercriminals may attempt to intercept sensitive information.
Furthermore, a VPN enables users to bypass geo-restrictions and censorship imposed by governments or internet service providers. This means you can access websites and online services that may be restricted in your region, without compromising your privacy or security.
For businesses, VPNs offer an additional layer of protection for remote workers accessing company resources from various locations. By encrypting data transmissions, VPNs help mitigate the risk of data breaches and unauthorized access to confidential information.
However, it's essential to choose a reputable VPN provider that prioritizes privacy and does not log user activity. Additionally, while VPNs enhance data protection, they are not a panacea for all security threats. It's crucial to practice good cybersecurity habits, such as using strong, unique passwords and keeping software up to date.
In conclusion, investing in a VPN is an effective measure to enhance data protection in an increasingly interconnected world. By encrypting internet traffic and preserving anonymity online, VPNs empower users to safeguard their privacy and security in the digital realm.
0 notes
Text
Some Key Points Of Cryptography In Blockchain Technology
Cryptography is the practice and study of techniques for secure communication and data protection in the presence of adversaries. It involves the use of mathematical algorithms to convert plaintext (human-readable data) into ciphertext (encoded data) and vice versa. The primary goal of cryptography is to ensure the confidentiality, integrity, and authenticity of all these services you get from cryptocurrency exchange development company.
Here are some key aspects of cryptography:
Confidentiality:
Cryptography ensures that unauthorized parties cannot understand the content of the communication or data. This is achieved through encryption, where the original message (plaintext) is transformed into a scrambled form (ciphertext) using an algorithm and a secret key. Only those with the correct key can decrypt and retrieve the original message.
Integrity:
Cryptography helps verify the integrity of data, ensuring that it has not been tampered with during transmission or storage. Hash functions are commonly used for this purpose. A hash function generates a fixed-size string of characters (hash value) based on the content of the data. Even a small change in the data results in a significantly different hash value.
Authentication:
Cryptography is employed to establish the identity of parties involved in communication. Digital signatures are a common tool for authentication. A digital signature is a unique identifier generated using a private key that only the sender possesses. The recipient can verify the signature using the corresponding public key, confirming the sender's identity and the integrity of the message.
Non-repudiation:
Non-repudiation ensures that a party cannot deny the authenticity of their message or action. Digital signatures play a crucial role in achieving non-repudiation. If a digital signature can be verified, the sender cannot deny sending the message.
Key Management:
The security of cryptographic systems heavily depends on the proper management of cryptographic keys. Keys are used in encryption and decryption processes, and their compromise can lead to a loss of confidentiality and integrity. Secure key generation, distribution, storage, and disposal are essential components of effective cryptographic systems.
Symmetric and Asymmetric Cryptography:
Symmetric-key cryptography uses the same key for both encryption and decryption, while asymmetric-key cryptography involves a pair of keys (public and private) for these operations. Symmetric cryptography is typically faster but requires a secure method for key exchange. Asymmetric cryptography provides a more secure key exchange but is computationally more intensive.
Cryptographic Protocols:
Cryptographic protocols are sets of rules that govern the secure communication between parties. Examples include the Transport Layer Security (TLS) protocol used for securing internet communication and the Internet Protocol Security (IPsec) for securing network communication.
Cryptography is a dynamic field that evolves to address emerging threats and challenges. Its applications extend beyond traditional communication security to areas such as blockchain technology, secure multi-party computation, and homomorphic encryption. The ongoing development of cryptographic techniques is essential in maintaining the confidentiality and security of digital information in our increasingly connected world.
0 notes
Text
𝙲𝙾𝙳𝙴 𝙱𝙻𝙰𝙲𝙺 - 𝙰 𝙷𝚈𝙱𝚁𝙸𝙳 𝙹𝙹𝙺 𝙰𝚄
ᴄʜᴘ. 01
ᴘᴀɪʀɪɴɢ: ᴛɪɢᴇʀ ʜʏʙʀɪᴅ!ꜱᴜᴋᴜɴᴀ x ʜʏʙʀɪᴅ ᴛᴀᴍᴇʀ!ʀᴇᴀᴅᴇʀ
ᴛᴡ/ᴄᴡ: ʜʏʙʀɪᴅꜱ, ꜰᴇᴍ!ʀᴇᴀᴅᴇʀ, ʙʀᴀᴛ ᴛᴀᴍᴇʀ!ʀᴇᴀᴅᴇʀ, ꜱᴇxᴜᴀʟ ᴛʜᴇᴍᴇꜱ, ᴅᴀʀᴋ ᴛʜᴇᴍᴇꜱ, ᴏᴘ!ʀᴇᴀᴅᴇʀ
ᴡᴏʀᴅ ᴄᴏᴜɴᴛ: 1.2ᴋ
ᴀ/ɴ: ɪꜰ ʏᴏᴜ ᴡᴏᴜʟᴅ ʟɪᴋᴇ ᴛᴏ ʙᴇ ᴀᴅᴅᴇᴅ ᴛᴏ ᴛʜᴇ ꜱᴇʀɪᴇꜱ ᴛᴀɢʟɪꜱᴛ ꜰᴇᴇʟ ꜰʀᴇᴇ ᴛᴏ ꜱᴇɴᴅ ɪɴ ᴀɴ ᴀꜱᴋ! ᴍɪɴᴏʀꜱ/ᴀɢᴇʟᴇꜱꜱ ʙʟᴏɢꜱ ᴅɴɪ!!! ʙᴇᴛᴀ ʀᴇᴀᴅ ʙʏ @tetsukentona & @blueparadis <333
ʟɪɴᴋꜱ: ᴘʀᴇᴠ | ɴᴇxᴛ | ᴍ.ʟɪꜱᴛ
ᴛᴀɢʟɪꜱᴛ: @pulchritxde @fayelvsu @that-one-wall @nanamis-wifey-reye @shaak-ti-s
ɴᴇᴛᴡᴏʀᴋ: @tokyometronetwork

You pace around the small, air-conditioned room filled with tech stuff. You gotta admit, the two blue codes working before you knew their shit. They had been given a lead only fifteen minutes ago. You can already see them pulling up various high profiles that may have connections with the Crime Syndicate.
“Do you guys even like doing this?” you ask them, hoping it doesn't mess with their concentration.
Kaeya answers, “Not really. But, the pay is good and our safety and security are guaranteed.”
The other one shrugs, “It’s much better than slaving for sloppy lecherous humans who can't seem to keep their hands off us.” Although he spoke nonchalantly, you could detect a sense of derision and resentment buried deep within. “There, there,” you pat his back, “Childe, right? Don’t worry, no one's gonna lay a single finger on you with me here.” You try to send him your warmest smile, hoping to alleviate any negative feelings or memories.
“Please stop.” A familiar voice calls out. Turning around, you see Gojo striding over to you in steps equivalent to three of yours. He’s clad in designer jeans and a white button-up, completely ignoring the workplace dress code. Lifting the glasses off his gorgeous eyes, he smirks, arctic blue orbs staring down at you. “You are scaring the poor thing.” Aaand there goes his charm.
You roll your eyes at him.
Gojo Satoru, a full-blown blue code. He is the pride and honor of the agency. If you were the best hybrid tamer, he had to be the best hybrid. Raised since he was just a child to be the spear and shield of humanity, he is highly intelligent and equally dangerous. Gojo is known to be strong, and he indeed is but working with him up close you could label him as a double-edged sword.
His childhood had been stolen from him. He was brainwashed and taught that his existence was only dedicated to serving human rights. You could predict it wasn’t long before he snapped.
Maybe that explains your soft spot for him. You hoped you could be there for him if and when he does snap. Despite the high demand from your juniors to let them see a fight between the best tamer and the best hybrid, you had never actually fought him. You always wondered, though, because, if you weren’t wrong, Gojo was actually a hybrid of the cat family.
Although he always says he’s just a household cat, you weren’t very inclined to believe that. He had to be from a bigger species, a rarer breed, perhaps.
“Boss!” Childe’s sudden shriek startles you. Snapping your eyes to the screen, you watch as the tanned hybrid pulls up a random string of letters bunched into words that make no sense whatsoever. “We found their next location of attack.”
“It’s an address encrypted in a cipher,” Kaeya frowns, “It doesn't look like the standard DES cipher”
Childe swats his head, “Look at the positioning bro, it’s definitely Railfence Cipher!”
Kaeya’s eyes widen, his fingers making quick work of typing up a decryption program. Kaeya passes the encrypted address through the program, and everyone waits with bated breath expecting the address of the next mall or building the CS was planning on hijacking.
But when the decrypted address appears, everyone inside the room stands shell shocked for a second.
Gojo breaks the silence, “What does this mean, y/n?” He turns around to you, his cerulean eyes narrowed suspiciously.
“I don’t know, Gojo. I-” you stare hard at the address, no, your home address. What would they break into your house for?
Your eyes almost pop out of their sockets, realization dawning as you grab your jacket from the cloak stand, rushing past the hybrids, one word leaving your mouth that clears up all their questions.
“Sukuna.”

You slam open the door, although the lock’s been already picked. “Sukuna!” you yell at the top of your voice. Fear grips you as multiple possibilities arise in your heart. Your feet carry you around the house, your heart dropping at every empty room that greets you.
What if Sukuna escaped? What if he broke out on a rampage? God knows the town would be dead before they even knew what hit them. What if he joined forces with the CS? They might become close to invincible with him beside them. What if-
“Oi, oi, oi, watcha making a ruckus for?” Sukuna interrupts your train of thought, strolling into the bedroom, where you were searching for him. His hair is mussed up and his face is flushed. And as usual, the shirt you draped him in before he woke up is nowhere to be seen. Probably ripped to pieces somewhere on the floor.
You stiffen up, back straightening. Instinctually, your senses sharpen, eyes locking in on your hybrid. More specifically on his blood-coated hands and bare torso.
“Whose blood is it? What happened here?” You question him, eyebrows furrowed.
His brow raises. Tilting his head, he smirks, “You being here at this time proves that you already know everything. Why don't you tell me?”
You relax your stance, externally, at least. Smirking back at him, you tease, “Come on now, Sukuna. Won’t you tell mommy about your little kitty party with your friends?”
His jaw clenches at your words, eyes slightly turning red. Growling from the back of his throat, he approaches you slowly, menacingly. And unlike all the other times where he would be dashing towards you to rip your throat out, you know it’s different from his heavy but determined steps.
Stopping before you, he leans down, harshly whispering into your face, “Those lowlives are not my friends!” Then grabbing your hand in his bigger one, Sukuna yanks you with him to the bathroom adjoining the guest bedroom. One look at the blood trail from his cage to the bathroom has your eyebrows rising.
How the fuck did I not notice that?
You wonder if you had been going lax with your guards. Inside the bathroom lays the bloody body of Mahito in the bathtub. Cussing at the stubborn hybrid under your breath, your eyes rake over his mauled features.
“Why did you hurt him?”
You crouch down and check his pulse. Thankfully, the hybrid is strong and is just fine. Except for the superficial injuries on his face and torso, Sukuna went easy on him.
“None of your fucking business.” He snaps.
You stare at him for a long second. This doesn’t seem right. Sukuna never talked this much with you. You knew he was hiding more than he was letting on. Shrugging it off, you beam at him, “So he broke your heart? Hmm? Rejected your silly ass? Is that it, Sukuna?”
He scowls at you. “Excuse you? I rejected him. Motherfucker wanted me to join his little gang of fuck-ups.”
Your eyes darken. So your hypothesis was right. The CS was trying to ally up with the one code black ever known. Sukuna.
“And why would you refuse?” you question him.
He shrugs, “Too bothersome. They don’t have anything better to offer than I already have.”
You don’t trust a single word he says, but you indulge him, “They can give you freedom.”
“No thank you. If I wanna take over the world, I don’t need little shits helping me. I’ll do it myself.” His proudly upturned nose makes you smile a bit, but your questions never end.
“Then, why did you not escape?” You expected another ‘mind your own business’, but what he said next, chilled you to the bone.
“It isn’t the right time yet. When I leave, I’m taking you with me.” Leaning down, he whispers into your ear, “I’m gonna give you hell.”
And by natural survival instincts, you fling your fist at him, your knuckles meeting his temple hard. Sukuna groans, the familiar frustration of never catching a single one of your lightning-fast punches overcome by the clouding of his vision as he goes down cold again.

#sukuna x reader#hybrid sukuna x fem!reader#hybrid sukuna#hybrid jjk au#jjk au#x fem!reader#ryomen sukuna x fem!reader#sukuna ryomen x fem!reader#jjk hybrid au#sukuna smut#ryomen sukuna#sukuna ryomen#sukuna#[Ro.CodeBlack]
292 notes
·
View notes
Text
... Screw it. Yes, I'm starting a new multi-part fanfic right before episode 10. 🤪
In this version of events, Jake disappeared right before the end of whatever happens without a trace. It is now 5 years later. MC has moved on (?).
Unrecognisable Part 1
⚠️ This fanfic has strong language usage.
⚠️ This fanfic features a**hole!Jake.
------------------------------------------------
“I wish I found the Man Without a Face instead.”
I never thought I'd ever say those words, but as they say, “expect the unexpected.” They also say, “never meet your heroes.” For good reason too.
Where to begin? I'm sure you know the story about Hannah Donfort. Who doesn't by now? It was all over the news and social media. Not a story I enjoyed repeating. Thankfully only a few people knew I was even involved as my name was left out of the news. And of the people I did tell, many claimed I lied for the attention. As if I wanted to be associated with that nightmare? No, thank you.
The only thing that kept me sane was my memories of the people I met along the way, especially HIM. Not many people are aware that the #IAmJake trend and the events surrounding Hannah Donfort were actually connected. Not even the conspiracy theorists were able to make that connection. I suppose it was good in a way - good for HIM. I wouldn’t be able to tell you because before it was even over he disappeared without a trace. Yes, like the Avatar, only he wasn't encased in ice.
To make matters worse, all of our history with him was gone. Even the photo he had sent to Lily and the backup she had saved. As it turned out the photo contained a trojan, which meant he could get to it on any device. Of course the one personal item he volunteered had strings attached. If it wasn’t for the fact Lily had printed a hard copy of the photo, we wouldn't had anything to go on, but even then, it wasn't enough. It’s not like you could identify him from an old photo of his mother. It's not like I could hack into the world’s most sophisticated international facial recognition software and search for matches.
Honestly though, I was pissed, no livid with how he disappeared. At first I was optimistic he would return, but as the days and weeks passed without a word, it was clear it was never going to happen. And as bad as it sounds, there were times I wished he was either dead or captured. The sting of him leaving wouldn't hurt so much then. Something told me he wasn't though. Somehow I knew he got what he wanted and was now in the wind. After a while, I had a friend of mine so a sweep of my computer and phone. Both had so many backdoors open for the right hacker to walk right through any time he felt like it. I was so disgusted with the gall of him. I immediately got a new phone and computer, and didn't touch my old accounts ever again. An absolute fresh slate. No more prying whenever you felt like, Jake. He would have to reach out to me the old-fashioned way.
So when I received the coded email from an unknown sender five years after he disappeared, you could imagine my surprise. I suppose an average person would have deleted it or marked it as spam. I just knew there was something about it though. I looked up all sorts of ciphers and encryptions. I ran it through online parsers. Surely if it was intended for me it wouldn't require too much deciphering, right? What I understood about the highest level of encryptions was they required a key to interpret the information, but I didn't receive anything else so I was baffled for days. Then I remembered that scavenger hunt he had sent me and Lily on, and that dumb phrase he kept repeating.
“You are the key.”
I tried my first name. I tried my last name. I tried them together, I tried them in reverse. I threw in my date of birth for kicks. Nothing. I nearly gave up, but then I saw a video on my feed mention how identity theft can occur from just having your social security number.
Bingo.
The parser confirmed that the decryption worked and returned to me two decimal numbers. At least I had watched enough mystery shows and played enough games to immediately recognise them as GPS coordinates, so you can stop shouting at the page now. (Who hasn't yelled at TV shows for spending more than a second working that out?)
And that is how I ended up at that abandoned building in a faraway city of a country I had never been to before. Then thing is, no one knew I had gone overseas. It wasn't so much of an issue with my work or my family. However, lying to my boyfriend was the hardest. He sincerely thought I was visiting my sick aunt. How was I to explain this to him? That I was chasing down a clue that may or may not lead to this guy I once had feelings for. I figured I'd work out an explanation afterwards. For now, I didn't want the interference, I just wanted to be able to focus on following the clue. I had to admit, as I pryed the boards off a broken window with a disused pipe I had found, I was beginning to have doubts about my interpretation of the message, but what else could it have been?
Even though it was the middle of the day outside, the old office building was dark as little light got past the boards. I had to use my phone to illuminate the hallways as I walked through them. There was only four stories, but when you don’t know what or who you were going to be finding, it felt like a never-ending labyrinth. Still, I carried on while trying to work out the best excuse to give the police if they had found me first and arrested me for trespass. They could speak English, right?
As I entered one of the offices on the third floor, my phone was suddenly knocked out of my hand. Before I could react, I was slammed face first into the wall painfully. Someone grabbed my hand and twisted my arm painfully against my back. Then I heard the click of a gun's safety being disengaged before the muzzle was shoved against my head.
“What the fuck are you doing here!?” a male voice grunted with an European accent.
My mind raced. Had I gotten the message wrong? Was I not the intended recipient? But it was my social security number that was the key! No, it had to have been for me.
“I-I followed the GPS coordinates in the email!” I stammered.
“What email!?” he pressured.
“Can we do this without the gun?” I pleaded.
“No! Answer the fucking question!” he snapped.
“I received an encrypted email from an unknown sender. All it contained though were GPS coordinates for this building!” I explained. “Please, you’re hurting me!”
“I’m hurting you? I'm hurting you?” he stressed. “Fuck! It’s people like you that keep the Nigerian prince scam going! You blindly following that email is going to get me killed! I should just shoot you and leave your body for them to find! Teach them to fuck with me!”
“I don’t understand!” I started to tear up. “You didn’t send me the email?”
“NO!” he yelled. His voice echoed off the walls. “At what point in entering this building did it seem like I wanted guests!?”
He pulled the gun away and shot my phone lying on the floor. The gun had a silencer on it, but the sound of the phone shattering still caused me to jump.
“Now what do I do with you?” he purred. “Do I leave you in the dumpster out the back? Or should I hang your body in the foyer?”
“Please...” I sobbed. “It was just a misunderstanding, ok? I thought you were someone else!”
“Yes, I know. You thought I was... what name did I use again? Oh, that’s right. You thought I was Jake,” he laughed.
My blood ran cold, “Jake?”
He spun me around and slammed me back against the wall. I started to cry out in pain when he smashed his lips against mine. I was in so much shock that all I could do was stare into his icy cold eyes that peered out from underneath his hood. He readjusted his face mask to cover the lower half again.
“What’s wrong? Was that not how you imagined our first kiss?” he chuckled.
I immediately slapped him across the face. “You can’t be...” I mumbled.
“Oh, but I am,” he sneered. “I am Jake!”
173 notes
·
View notes
Text
Purchasing Sql Server Errors
Incident response with Azure, such as other cloud providers, is a bit different. With this service it is simple to publish and get messages from your things. This message will display when the procedure is complete. User-defined messages may also be kept in sysmessages. The error message gives diagnostic information regarding the reason for the error. These user-defined error messages can be employed by RAISERROR.
Everything beyond is regarded as an error To have the ability to use an apostrophe in a string, it needs to be escaped, so that it's not thought of as a string delimiter. There is a vast selection of errors that can happen during the SQL Server work. This error is going to be thrown. Error 823 means there are some issues with the storage computer hardware. Errors with a tall severity indicate issues that ought to be addressed whenever possible. The problem needs to be resolved. There is an issue with your selected data store.
To escape an apostrophe, another apostrophe must be used next to it, as it's shown below Finding SQL syntax errors can be challenging, but there is some advice about how to make it a bit simpler. Because of this, it will become impossible to have data from it. Data ingestion is the initial step in building the data pipeline.
The instructions below will demonstrate how to resolve the permissions issue. This type of error condition is referred to as a transient fault. Each error condition have a special error number.
Each policy may have a variety of settings. Employing the drop down policy lists, decide on the policies you would like to apply. The absolute most important MySQL account to decide on a password for is the main user. Just bear in mind that you would like to commit or rollback your transactions at the ideal times, based on whether an error was generated.

Insert some values in the Employee table. For instance, presence states or the capacity to transfer files. An internet index rebuild or an index reorganization isn't always possible. There are many SQL database versions suiting the demands and requirements of small organizations together with bigger enterprises too. Perform continuing database maintenance. In the middle of this screen, there is going to be a field marked From database.
Whatever encryption way you pick, I advise avoiding encryption methods that ask that you store the decryption key on the database itself. As a way to utilize Change Data Capture functionality offered by the SQL Server, it ought to be enabled for the specific database which we intend to track the changes. Databases have long been a significant part your normal architecture and potentially the most important. Your database is the jackpot that each attacker intends to capture. The customer's major database is MySQL. SQLEXPRESS'' folders, you should install SQL Server. SQL Server is an intricate system and as a result of continuous increasing size of information and multiple small business logic, getting to the root of performance issues can be difficult. Any throw from inside the script is regarded as a failure. The script ought to be fairly straightforward. Recycled code results in recycled suggestions and recycled folks.
The deployment may take as much as a little while so be patient. There are lots of reasons for this, like a system or server crash or a virus. Do not freak out whether there are too many events and they run screaming at you, which happens when you get a huge system with a lot of users. There's a different technique for Windows hosted accounts. If you've checked the Allow to utilize for domain creation box on the very first page of the wizard, once you click OK the template gets active in the computer system.
SQL Server 2019 documentation can be found on our major Docs address. This application offers you a basic grasp of the DataGridView control's capabilities. An application is consuming an excessive amount of memory. It must also be compiled with debugging enabled. Nevertheless it remains a beneficial tool. SQL Recovery tool may also eradicate and handled each of the problems of error messages which occur because of corruption. MS SQL database recovery tool recently added features that are very advanced like multi threaded export which may let you recover single in addition to multiple tables at one time.
A standard use of the test script is to confirm the adapter's capability to access necessary database tables. Certain permissions, like, for instance, shell access, provide unlimited accessibility to critical system objects, therefore it is strongly recommended to use permissions sql server errors with caution. Storing sensitive info, such as a password, within the connection string can influence the security of your application. Employing the aforementioned Error List can help in an excellent way.
youtube
1 note
·
View note
Text
TLS Protocol
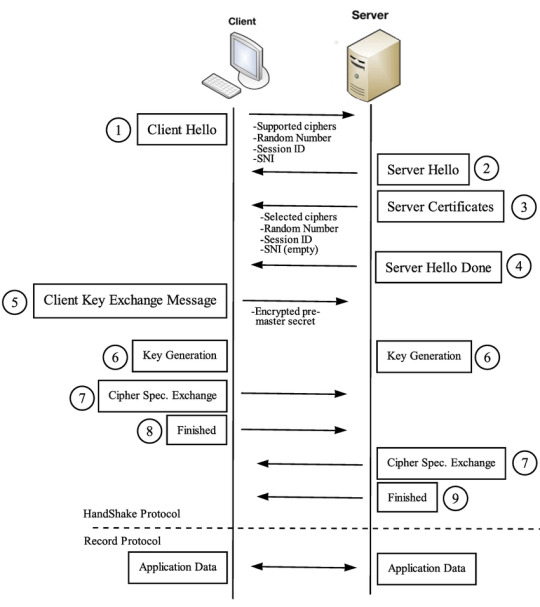
We often think of SSL as the security layer that provides encryption on the Internet, however this was the predecessor to Transport Layer Security (TLS). The protocol works by initiating a handshake at the start of the session (according to Cloudflare):
SYN from the client - starts a connection with the server providing the TLS versions supported, ciphers supported and a string of random bytes and a string of random bytes (”client random”)
SYN ACK from the server - the server responds with a SSL certificate, a chosen cipher and a randomly generated string of bytes (”server random”)
Client verifies the SSL certificate with the issuer - this means tracing up the chain of authority and checking against revocation in the CRLs
Client sends another random string of bytes (”premaster secret”) - this is encrypted with the public key of the server
Server decrypts - using their private key they can obtain the random string of bytes sent from the client
Client and server then generate session keys from a combination of the “client random”, “server random” and “premaster secret” - they can both use symmetric encryption for communication with these keys from this point onwards
1 note
·
View note
Text
Block Modes, SP Boxes and Fiestal Networks
Recall the Merkle-Damgard hash construction and its partitioning of the plaintext and several ‘blocks’ which would be individually hashed and shoved into the next mini hash function to be hashed with the next net cipher block, to give it the following properties of confusion and diffusion.
Confusion and Diffusion are properties meant to ‘thwart the applications of statistics and other methods of cryptanalysis’. Confusion is the principle of having each bit of a plaintext enciphered by multiple different parts of the key, in order to obscure any straightforward connection between the plaintext and ciphertext. Diffusion is the avalanche effect property, meaning that if a change a single bit of the plaintext, then half the bits of the cipher text should change.
A method of achieving these two properties, given a straightforward key, is by use of the SP network or SP box. These are a series of mathematical functions linked to one another in arbitrary ways that were inspired by the Enigma code and work in a much similar way. These networks utilise both S-boxes and P-boxes to serve as the ‘mini hash-functions’ in a Merkle-Damgard hash construction i.e. the plaintext will be passed in, the key will be divided into blocks and also passed into the construction and at each step the plaintext will be subject to either the S-box or the P-box, before being spat out into the next S or P box to be enciphered by the next block of the key. S-boxes substitute a small block of its inputs’ bits by another typically arbitrary block of bits. For example given an input of bits, it may substitute every four bits and those substitutions will be chosen from a fixed table of substitutions that outline which four bits will be mapped to which other arbitrary number of bits. i.e. 1100 may be mapped to 101. These mappings are one-to-one to ensure that they can be reversed/decrypted. P-boxes permute its bits; taking input and randomly reordering them.
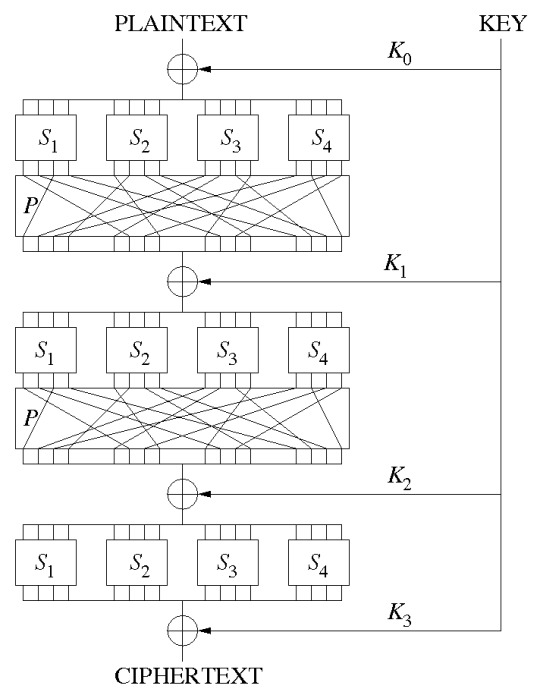
Hence, encrypting the plaintext will look like this: plaintext will be enciphered with a block of the key and outputted into either a S or P box whose output will then be enciphered by the next key block and etc.
How it achieves confusion and diffusion
Thus, changing one bit of the key will result in the section that it will be passed into, to be utterly scrambled as the output of that section will be either permuted or substituted in a pseudorandom way multiple times, and being effectively multiplicatively scrambled which will - if applied correctly - cause half the bits of the final ciphertext to be different: hence avalanche effect/diffusion. The reasoning for confusion is obvious: the S-boxes will essentially cause different parts of the key to encipher other different parts of the plaintext.
Block Modes
Block enciphering takes multiple blocks/partitions of a plaintext and enciphers each of them with an encryption, in a similar way to the M-D hash construction. These ciphertext blocks will then be chained together in a particular way to form the ciphertext. The method in which they are chained is known as the block mode.
ECB: Simply chaining them together in left-to-right order. Has serious flaws in that the same plaintext will map to the same ciphertext, and the same bit of the key will map to the same bit of the ciphertext making statistical analysis methods such as frequency analysis fairly simple.
CBC: Tries to solve this problem by XOR’ing the first ciphertext block with the next plaintext block before being plugged into the next cipher function. This is very similar to the Merkle-Damgard hash construction.
CTR: instead of encrypting the plaintext blocks, the CTR mode encrypts a nonce and a counter value which will then be XOR’d with the plaintext to make something really weird and will possess the diffusion and confusion properties. These ciphertext blocks are then chained in left-to-right order.
Feistel Networks
One could think of the Feistel Network as a convoluted version of the above chaining methods to achieve a slightly more convoluted ciphertext i.e. with stronger properties of diffusion and confusion. And they achieve this by performing the following:
The plaintext block is split into two equal pieces L(1) and R(1), where the 1 denotes the current iteration of the cipher. R is shoved into a function F with K(1). the first block of the key, and the output F(K(1),R1(1)) is then XOR’d with L(1) in order to get R(2). L(2) will simply be R(1). This can be summarised succinctly in the following equations.
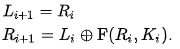
This then repeats with our new values of L(2) and R(2) and then the next, until the desired number of rounds is reached. This can be decrypted by reversing the above equations for the number of rounds:
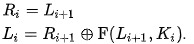
However, one would of course need to know the number of rounds, the F function as well as the corresponding key block for each iteration. Note that these key blocks are often shuffled around and further obscured and the order of R and L, the two partitions, are often arbitrarily swapped around which could lead to a very large number of combinations of swaps once the number of rounds becomes very large.
Block Mode Activity - identifying the block mode
spoiler alert
Cipher 2 is clearly counter-mode, as it’s the only one updating when I enter a new character into the plaintext and that’s what CTR mode does: XOR them as it comes.
The rest is 50/50 between ECB and CBC but we can narrow it down using some advanced Ctrl-F analysis.
Here are the ciphertexts of the plaintext:
ppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppppp
for each cipher.
Cipher 1
294744a1c4cd2a9bf6bfe4b048473aa7294744a1c4cd2a9bf6bfe4b048473aa7294744a1c4cd2a9bf6bfe4b048473aa7294744a1c4cd2a9bf6bfe4b048473aa76e9dfd4826a47d16df46400a416c967d
Clearly an ECB block mode. EBC suffers from the problem of the same input providing the same output, meaning that given a long enough string, there WILL be consistent repetitions and if we CTRL-F 4b048473aa72947a1c..., that’s exactly what we find
Cipher 3
c330b8296148fcd5579b64cd63231719edd4c8494f31ea9df99f9c194df9bdc51beb30ed5ea090d0f0c860eb725a872b0c89269e78d739074d0b2ae00b3905d3c1fc8b6c1239251b9c9612bf9945d8fa
No repetitions here, must be CBC.
4.
f659f1491f7c1d7c2f6143999faa9765cdd366379024ff6de1988dfd6efe894729d017b41597f953bf49a214b175200b6bbaa0360933cd3d98fe3bae10db32bb06f3b6601afd37ee96a0d525a48fecd0
CBC, same reason
5.
1fcae373ca6fb1ae0590b5f3d971ad111fcae373ca6fb1ae0590b5f3d971ad111fcae373ca6fb1ae0590b5f3d971ad111fcae373ca6fb1ae0590b5f3d971ad11e9d1c9abf7671d46da742df9203063a8
ECB, same reason
1 note
·
View note
Text
UNIT 1
UNDERSTANDING
1.1 Basic Nature of Cyber Threats:
Nothing seems sacred these days. Where there are a computer and someone with the capability and devious mind, you could potentially find a cyber threat. The trouble is, the nature of cyber threats have changed both in kind and intensity. The global States have raised their game and increased their intensity. What may have been spotty-faced teenagers operating from their mother’s basement, has transferred cyber threats as a major security challenge for businesses. The threat is a possible danger that might exploit a vulnerability to breach security and therefore cause possible harm. A threat can be either “intentional” (i.e. hacking: an individual cracker or a criminal organization) or state-sponsored. In this definition, the threat is defined as a possibility. However, in the cybersecurity community, the threat is more closely identified with the actor or adversary attempting to gain access to a system. Or a threat might be identified by the damage being done, what is being stolen or the Tactics, Techniques, and Procedures (TTP) being used.”In this definition, the threat is defined as a possibility. However, in the cybersecurity community, the threat is more closely identified with the actor or adversary attempting to gain access to a system. Or a threat might be identified by the damage being done, what is being stolen or the Tactics, Techniques, and Procedures (TTP) being used”.1
1.2 Overview of Common Threats:
Insider threats:” An insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization’s security practices, data and computer systems.”
The insider threat, whereby an employee acts, knowingly or unknowingly, in a counter-productive way to cause significant damage to his/her organization, has become a key risk for organizations around the world. This is in part driven by the greater access individuals have to critical information and systems as organizations become more and more connected. In addition, ever more sophisticated methods of carrying out a cyber attack and the availability of more outlets for leaking information are increasing the threat.[2]
Cryptojacking attacks: A cryptographic attack is a method for circumventing the security of a cryptographic system by finding a weakness in a code, cipher, cryptographic protocol or key management scheme. This process is also called “cryptanalysis”. SQL injection Attack: A code injection technique, used to attack data-driven applications, in which criminal SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
Phishing: Fraudulent attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in electronic communication. Typically carried out by email spoofing or instant messaging, it often directs users to enter personal information at a fake website, the look and feel of which are identical to the legitimate site. Phishing is an example of social engineering techniques being used.
Ransomware: A type of malicious software from that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. More advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
Advanced malware attacks: These typically follow a common attack sequence: Planning: Involves selecting a target and researching the target’s infrastructure to determine how the malware will be introduced, the communication methods used while the attack is in progress, and how/where the data will be extracted.
1.3 Main features of threats to individuals:
From identity theft and fraud to social networking hacking attacks, everybody needs to be sure their safe. Knowledge is key as the saying goes. Your personal details, pictures, account details, and much more concerning yourself can potentially be exploited by the criminal.
1.4 Main features of threats to companies:
The reputation of your company, and of course the day to day functioning are under threat from cybercriminals. Various types of viruses and hacks can bring your business to its knees.
The number one weak link for businesses when it comes to cybersecurity — by a long, long way — is the people who work in the business.
From falling for phishing emails, and clicking on links or downloading documents that turn out to be malware, to being a victim of business email compromise (BEC) scams that end up losing the company a lot of money, employees are a company’s greatest liability when it comes to cybersecurity.
See also: https://thehackernews.com/2017/09/blueborne-bluetooth-hacking.html
Figure 1: Explanation from CIO|INSIGHT on Today’s security issues for businesses.[3]
1.5:
Analyze and Detail
2.1 Why do people cause and create security breaches:
For fun
Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends and hack something only for the challenge
To Steal
Another reason to hack a system is to steal information or money. A large portion of hacking attempts falls into this category. Banks and large companies are common targets for hacking jobs, but sometimes smaller companies or even a specific person’s computer are targeted, as well.
To disrupt
There are also some hackers, including hacking groups; that target a company to disrupt business, create chaos and just be a nuisance. These groups often are trying to make a statement with their hacking, demonstrate security inadequacies, or show general disapproval for the business itself. Examples of hacking groups that made headlines are Anonymous.
2.2 What is a threat and how do they work:
One resource demonstrates potential as “the possibility of a malicious attempt to damage or disrupt a computer network or system.”
The malicious programs inside e-mail attachments usually only strike if you open them. Effects of a virus can be anything from a simple prank that pops up messages to the complete destruction of programs and data.[4].
If a virus is sent through a network. This will spread like wildfire, even potentially globally. In some cases, it can change configurations of a database system (i.e; a worm).
2.3 Features of threats & How they operate:
IBM recently announced the shocking average cost of data breach. While down around 10 percent, the global average for a data breach is $3.62 million. For many companies, the cost of suffering a cyber attack is enough to take the business down entirely, so it has never been more vital for all organizations to invest in their cyber defenses. In order to equip suitable security, you first need to understand exactly where the danger comes from. Looking ahead to 2018, we examine the biggest cybersecurity threats both to individuals and companies across the world.[5]
WannaCry is so-called encryption-based ransomware also known as Wanna Decryptor or WCRY. It encrypts users files using AES and RSA encryption ciphers meaning the hackers can directly decrypt system files using a unique decryption key. From my research, especially remembering how much broadcast it received, it manipulated the laws that, basically, were prevalent at the time in many businesses, and specifically the NHS. People had not updated their systems often, and correctly. A playground for hackers.
2.4 How attack against companies works:
You work in the financial department of your company and you just got an email from an executive.
It instructs you to pay a sum of £78,000 before a specified time. It includes instructions for how to wire the money to your vendor’s bank.
You send the money, as requested, and it quickly moves to a number of small banks and then ultimately to an overseas account, where it is unlikely your company—or law enforcement—will be able to recover it. This is how phishing works.
2.5 Review & Hierarchy:
In the year 2011, a hacker was sentenced to nine years in prison because of the cyber-attack that he caused in a hospital. With this incident of physical damage to a hospital system, this individual used the skills that he had to install malware.
As a result of his action, the Hospital’s HVAC’s system was adversely altered causing the patient’s safety to be unduly jeopardized. By remotely controlling the temperature in the hospital, it posed an immediate threat since it placed drugs and other medical supplies at risk. In this situation, the hacker was controlling both the air and heating systems in the hospital from a remote location. Just goes to show how much of a danger some corrupted intentions can be used to cause massive, and potential health dangers.
Evaluate the impact of threats
3.5 Presentation with research document highlighting the affects:
3.1 According to on researcher[6] data breaches alone see upwards of 4.4 million data records being lost or stolen worldwide every single day. Take the 2015 data breach at UK telecoms company TalkTalk. Web pages containing databases no longer supported by their producer were accessed by hackers, who stole the personal data of 156,959 customers. The result was lots of negative publicity, reputational damage and a record fine of £400,000 from UK authorities.
One of the world’s largest DDoS attack ever took place in 2016, when US network provider Dyn was targeted. The attackers had harnessed the Internet of Things (internet enabled devices like cameras and fridges) to conduct the attack, and took down many major websites as a result. As the Internet of Things continues to expand, the risk is set to increase.
3.2 Hacking is a term used to describe actions taken by someone to gain unauthorized access to a computer. The availability of information online on the tools, techniques, and malware makes it easier for even non-technical people to undertake malicious activities.
What it is: The process by which cyber criminals gain access to your computer. What it can do: Find weaknesses (or pre-existing bugs) in your security settings and exploit them in order to access your information.
3.3 Determining live threats to websites:
Streaming: Ok, i agree, i have used them myself, but in my defence i didnt consider them illegal. I can clearly remember watching a sports event and many many pop-ups appear, asking you to click this or that to access this or that in order (criminally) to get you to sign to something that you will be totally unaware lead to something other than what is being advertised. Scammers, hackers. Call them what you want. But when you do fall for their cunningness, your computer could be infected with cookies or worse. Either annoying or sinister.
3.4 Determining live threats to servers:
There is no such thing as perfect software, and there is always room for further refinement. Good system administration requires vigilance, constant tracking of bugs, and proper system maintenance to ensure a secure computing environment.
A common occurrence among system administrators is to install an operating system without knowing what is actually being installed. This can be troublesome, as most operating systems will not only install the applications, but also setup a base configuration and turn services on. This can cause unwanted services, such as telnet, DHCP, or DNS to be running on a server or workstation without the administrator realizing it, leading to unwanted traffic to the server or even a path into the system for crackers..
[1]https://www.secureworks.com/blog/cyber-threat-basics
[2]https://www.paconsulting.com/insights/managing-people-risk-and-the-insider-threat/
[3] https://www.cioinsight.com/it-management/inside-the-c-suite/slideshows/the-11-top-threats-that-organizations-face-today
[4] https://www.bullguard.com/bullguard-security-center/pc-security/computer-threats/how-does-a-virus-work
[5] https://staysafeonline.org/blog/biggest-cybersecurity-threats-2018/
[6] https://www.regus.co.uk/work-uk/cybersecurity-threats-where-do-they-come-from-and-whats-at-risk/?psrch=1&msclkid=e090cb097c8a1d9752fa9795a609d2a9&utm_source=bing&utm_medium=cpc&utm_campaign=GB%20%3E%20EN%20%3E%20OF%20%3E%20SM%20%3E%20DSA%20%3E%20NEW&utm_term=regus.co.uk&utm_content=Homepage
2 notes
·
View notes