#EncryptionMethods
Explore tagged Tumblr posts
Link
https://bit.ly/3tkCG80 - 🔒 Encrypted npm packages were found targeting a major financial institution, raising concerns about the intent behind these publications. Phylum's analysis revealed sophisticated malware-like behavior, with the packages containing an encrypted blob targeted at a specific organization's domain. The situation highlights the complexities in determining the true nature of such cybersecurity threats. #Cybersecurity #MalwareDetection #FinancialInstitutionTargeted 🔎 In early November 2023, Phylum began tracking suspicious npm package publications. These packages executed encrypted payloads using local machine information, suggesting a highly targeted attack. The decrypted payload revealed an embedded binary designed to exfiltrate user credentials to an internal Microsoft Teams webhook of the targeted financial institution. This indicated either an inside job, a red team simulation, or external threat actors with substantial network access. #TargetedCyberAttack #DataExfiltration #CyberThreatAnalysis 🕵️ The attack mechanism was sophisticated, starting with a postinstall hook in the package.json. The code was designed to collect system-related information and use it for AES encryption. The attacker's focus on specific strings and environment variables suggested a detailed knowledge of the target's internal systems. #CyberAttackTactics #EncryptionMethods #SystemVulnerability 👥 After decrypting the payload, Phylum contacted the targeted organization. They discovered that the packages were part of an advanced adversary simulation exercise by the company's red team. While the intent was benign, this incident underscores the importance of vigilance against software supply chain attacks. #RedTeamSimulation #SupplyChainSecurity #CyberDefense 📊 The attack methodology revealed that developers are high-value targets and software libraries are rarely vetted for malicious modifications. This incident shows the effectiveness of software supply chain attacks, even against well-prepared organizations. It emphasizes the need for comprehensive security measures to protect against such sophisticated threats. #DeveloperSecurity #SoftwareSupplyChain #CyberSecurityAwareness 💡 Phylum's analysis of this case highlights the challenges in open source security. Their automatic analysis of packages in open source registries underscores the importance of identifying risks in using these packages. The incident serves as a reminder that today's red team exercise could be tomorrow's genuine threat, urging organizations to be adequately prepared.
#Cybersecurity#MalwareDetection#FinancialInstitutionTargeted#TargetedCyberAttack#DataExfiltration#CyberThreatAnalysis#CyberAttackTactics#EncryptionMethods#SystemVulnerability#RedTeamSimulation#SupplyChainSecurity#CyberDefense#DeveloperSecurity#SoftwareSupplyChain#CyberSecurityAwareness#OpenSourceSecurity#PhylumAnalysis#CyberPreparedness
0 notes
Text
Txt Dosyasını Veritabanı Olarak Kullanmak
<?php // Verileri okuyan ve şifresini çözen fonksiyon function oku($fileName, $secretKey, $encryptionMethod) { $fileContent = file_get_contents($fileName); $fileData = json_decode($fileContent, true); $iv = base64_decode($fileData['iv']); $decryptedData = openssl_decrypt(base64_decode($fileData['data']), $encryptionMethod, $secretKey, 0, $iv); return json_decode($decryptedData, true); } //…

View On WordPress
0 notes
Text
Announcing RDFP for Zeek - Enabling Client Telemetry to the Remote Desktop Protocol
Jeff Atkinson, Principal Security Engineer, Verizon Media
We are pleased to announce RDFP for Zeek. This project is based off of 0x4D31’s work, the FATT Remote Desktop Client fingerprinting. This technique analyzes client payloads during the RDP negotiation to build a profile of client software. RDFP extends RDP protocol parsing and provides security analysts a method of profiling software used on the network. BlueKeep identified some gaps in visibility spurring us to contribute to Zeek’s RDP protocol analyzer to extract additional details. Please share your questions and suggestions by filing an issue on Github.
Technical Details
RDFP extracts the following key elements and then generates an MD5 hash.
Client Core Data
Client Cluster Data
Client Security Data
Client Network Data
Here is how the RDFP hash is created:
md5(verMajor;verMinor;clusterFlags;encryptionMethods;extEncMethods;channelDef)
Client Core Data
The first data block handled is Client Core Data. The client major and minor versions are extracted. Other information can be found in this datagram but is more specific to the client configuration and not specific to the client software.
Client Cluster Data
The Client Cluster Data datagram contains the Cluster Flags. These are added in the order they are seen and will provide information about session redirection and other items - ex: if a smart card was used.
Client Security Data
The Client Security Data datagram provides the encryptionMethods and extEncryptionMethods. The encryptionMethods details the key that is used and message authentication code. The extEncryptionMethods is a specific flag designated for French locale.
Client Network Data
The Client Network Data datagram contains the Channel Definition Structure, (Channel_Def). Channel_Def provides configuration information about how the virtual channel with the server should be set up. This datagram provides details on compression, MCS priority, and channel persistence across transactions.
Here is the example rdfp.log generated by the rdfp.zeek script. The log provides all of the details along with the client rdfp_hash.
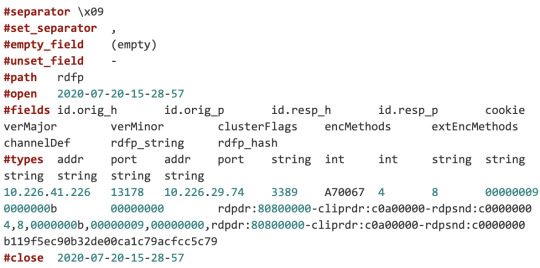
This technique works well, but notice that RDP clients can require TLS encryption. Reference the JA3 fingerprinting technique for TLS traffic analysis. Please refer to Adel’s blog post for additional details and examples about ways to leverage the RDP fingerprinting on the network.
Conclusion
Zeek RDFP extends network visibility into client software configurations. Analysts apply logic and detection techniques to these extended fields. Analysts and Engineers can also apply anomaly detection and additional algorithms to profile and alert suspicious network patterns.
Please share your questions and suggestions by filing an issue on Github.
Additional Reading
John B. Althouse, Jeff Atkinson and Josh Atkins, “JA3 — a method for profiling SSL/TLS clients”
Ben Reardon and Adel Karimi, “HASSH — a profiling method for SSH clients and servers”
Microsoft Corporation, “[MS-RDPBCGR]: Remote Desktop Protocol: Basic Connectivity and Graphics Remoting”
Adel Karimi, “Fingerprint All the Things!”
Matt Bromiley and Aaron Soto, “What Happens Before Hello?”
John Althouse, “TLS Fingerprinting with JA3 and JA3S”
Zeek Package Contest 3rd Place Winner
Acknowledgments
Special thanks to Adel, #JA3, #HASSH, and W for reminding me there’s always more on the wire.
1 note
·
View note
Video
youtube
Azure Server - Configuring Connections with Talend Open Studio
In this tutorial, we will learn "How to configure connections with Talend Open Studio ETL tools" to connect with Azure SQL database or Azure SQL data warehouse from Azure SQL Server. You have to followings- 1. Configure Client IP 2. Configure Connection String with access credentials 3. Connect DbVisualizer with credentials with Azure 4. Pull your data from database or data warehouse
Note: You don't use your Azure login ID to connect to the SQL service. You use the new credentials that are specific to the SQL database you've created via the Azure SQL Data Service console. Also, you must specify "encryptionMethod=SSL". Required for all communications with SQL Azure.
To Learn more, please visit us at - http://www.sql-datatools.com
0 notes
Video
youtube
Azure Server - Configuring Connection with Excel
In this tutorial, we will learn "How to configure connections with MS EXCEL " to connect with Azure SQL database or Azure SQL data warehouse from Azure SQL Server. You have to followings- 1. Configure Client IP 2. Configure Connection String with access credentials 3. Connect DbVisualizer with credentials with Azure 4. Pull your data from database or data warehouse
Note: You don't use your Azure login ID to connect to the SQL service. You use the new credentials that are specific to the SQL database you've created via the Azure SQL Data Service console. Also, you must specify "encryptionMethod=SSL". Required for all communications with SQL Azure.
To Learn more, please visit us at - http://www.sql-datatools.com
#azure#microsoft azure blog#sql#oracle sql#sql tutorial#sql server#learn sql#database#data#data warehouse#data modelling
0 notes
Video
youtube
Azure SQL Server - Configuring Connection with DbVisualizer
In this tutorial, we will learn "How to configure connections with DbVisualizer tools " to connect with Azure SQL database or Azure SQL data warehouse from Azure SQL Server. You have to followings- 1. Configure Client IP 2. Configure Connection String with access credentials 3. Connect DbVisualizer with credentials with Azure 4. Pull your data from database or data warehouse
Note: You don't use your Azure login ID to connect to the SQL service. You use the new credentials that are specific to the SQL database you've created via the Azure SQL Data Service console. Also, you must specify "encryptionMethod=SSL". Required for all communications with SQL Azure.
To Learn more, please visit us at - http://www.sql-datatools.com
0 notes