#MalwareDetection
Explore tagged Tumblr posts
Text
AI-Powered Cybersecurity: How Machine Learning is Revolutionizing Threat Detection
Explore how machine learning is transforming cybersecurity with advanced threat detection techniques. Read More. https://www.sify.com/ai-analytics/ai-powered-cybersecurity-how-machine-learning-is-revolutionizing-threat-detection/
0 notes
Link
https://bit.ly/3tkCG80 - 🔒 Encrypted npm packages were found targeting a major financial institution, raising concerns about the intent behind these publications. Phylum's analysis revealed sophisticated malware-like behavior, with the packages containing an encrypted blob targeted at a specific organization's domain. The situation highlights the complexities in determining the true nature of such cybersecurity threats. #Cybersecurity #MalwareDetection #FinancialInstitutionTargeted 🔎 In early November 2023, Phylum began tracking suspicious npm package publications. These packages executed encrypted payloads using local machine information, suggesting a highly targeted attack. The decrypted payload revealed an embedded binary designed to exfiltrate user credentials to an internal Microsoft Teams webhook of the targeted financial institution. This indicated either an inside job, a red team simulation, or external threat actors with substantial network access. #TargetedCyberAttack #DataExfiltration #CyberThreatAnalysis 🕵️ The attack mechanism was sophisticated, starting with a postinstall hook in the package.json. The code was designed to collect system-related information and use it for AES encryption. The attacker's focus on specific strings and environment variables suggested a detailed knowledge of the target's internal systems. #CyberAttackTactics #EncryptionMethods #SystemVulnerability 👥 After decrypting the payload, Phylum contacted the targeted organization. They discovered that the packages were part of an advanced adversary simulation exercise by the company's red team. While the intent was benign, this incident underscores the importance of vigilance against software supply chain attacks. #RedTeamSimulation #SupplyChainSecurity #CyberDefense 📊 The attack methodology revealed that developers are high-value targets and software libraries are rarely vetted for malicious modifications. This incident shows the effectiveness of software supply chain attacks, even against well-prepared organizations. It emphasizes the need for comprehensive security measures to protect against such sophisticated threats. #DeveloperSecurity #SoftwareSupplyChain #CyberSecurityAwareness 💡 Phylum's analysis of this case highlights the challenges in open source security. Their automatic analysis of packages in open source registries underscores the importance of identifying risks in using these packages. The incident serves as a reminder that today's red team exercise could be tomorrow's genuine threat, urging organizations to be adequately prepared.
#Cybersecurity#MalwareDetection#FinancialInstitutionTargeted#TargetedCyberAttack#DataExfiltration#CyberThreatAnalysis#CyberAttackTactics#EncryptionMethods#SystemVulnerability#RedTeamSimulation#SupplyChainSecurity#CyberDefense#DeveloperSecurity#SoftwareSupplyChain#CyberSecurityAwareness#OpenSourceSecurity#PhylumAnalysis#CyberPreparedness
0 notes
Note
I often find myself coming back to your blog just to admire your work every once in a while! Love your artwork, hope you're doing okay! 💞
WAHHH I JUST DUSTED MY BLOG AND THIS MESSAGE..... ToT
THANK YOU THANK YOU!!! I'm so glad to know people still visits even thought it's not as active, I hope the third game bring out more ideas! <3
5 notes
·
View notes
Note
Happy birthday malwaredetected‼️ (fun little factaroonie, it's my bday too 😱)
!!! omg happy birthday!!!
11 notes
·
View notes
Text


ID: a set of two images. the first is of duncan from total drama with a white outline in front of the dyscalculia flag. the second is a blank flag. END ID
Duncan from Total Drama has dyscalculia!
For @malwaredetected !
4 notes
·
View notes
Text
Network and Server Support

Trust Century Solutions Group for 24/7 management of your network equipment, systems, and applications, ensuring robust data network security and seamless performance on cloud servers.
Learn more: https://centurygroup.net/managed-it-solutions/server-network/
#networksupportspecialist #networksupport #datanetworksecurity #itservices #serversupport #networking #networksecurity #cloudcomputing #itsupport #techsupport #servermaintenance #cybersecurity #hardwaresupport #hardwaremaintenance #supportservices #servermanagement #manageditservices #malwaredetection #securityaudit
#Network and Server Support#Network Support Specialist#Data Network#Server Support#IT Services#managed it services#managed it solutions#cloud technology services
1 note
·
View note
Text
Definition and Detection of Fileless Malware ⚖️
In the ever-evolving landscape of cyber threats, malware continues to be a significant concern for organizations and individuals alike. Among the numerous forms of malware, file-less malware has emerged as a stealthy and sophisticated threat, evading traditional security measures.
Read on 👉 https://www.valevpn.com/post/definition-and-detection-of-fileless-malware
FilelessMalware #CyberSecurity #MalwareDetection #StealthThreats #MemoryBasedAttacks #CyberThreats #CyberDefense #EndpointSecurity #SecurityAwareness #PreventCyberAttacks

0 notes
Link
#365TotalProtection#ComplianceFilter#ContentControl#Hornetsecurity#LiveTracking#MalwareDetection#Microsoft365#Office365#Outlook#PGP#S/MIME#SpamDetection#Websafe
0 notes
Photo

#searchengines for #hackers #Googlehacking #database #hackingtools #incidentresponse #incidentinvestigation #malwareanalysis #informationsecurity #informationtechnology #cyberdefense #securityandrisk #malwaredetection #technolgy #redteam #blueteam #cybersecurity #bhusa #privacy #infosec #datasecurity #cyberattack #dataprotection #makingworkfun #kudos #cybercrime #phishing #databreach #ransomwareattack https://www.instagram.com/p/CG_ZS68AnWU/?igshid=mk1xj0gzz1gh
#searchengines#hackers#googlehacking#database#hackingtools#incidentresponse#incidentinvestigation#malwareanalysis#informationsecurity#informationtechnology#cyberdefense#securityandrisk#malwaredetection#technolgy#redteam#blueteam#cybersecurity#bhusa#privacy#infosec#datasecurity#cyberattack#dataprotection#makingworkfun#kudos#cybercrime#phishing#databreach#ransomwareattack
0 notes
Photo
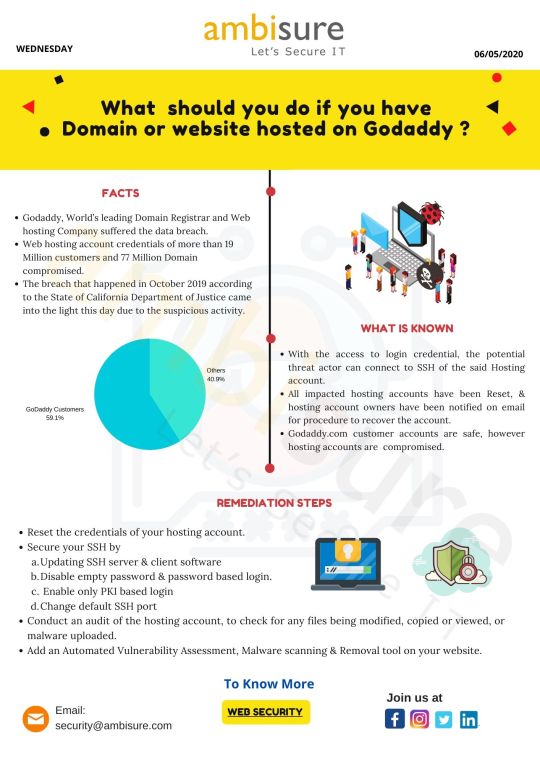
suffered a major breach. What should you do if you are affected? For more details on Website Security download from here: https://qoo.ly/35vvs4
#website#ambisure#skills4future#infosec#cybersecurity#malwaredetection#ssl#websitesecurity#cyberresilient#upgradeyourself#GoDaddy
0 notes
Photo

Which is Best Free Antivirus Software for 2019 | Protect PC from Virus
Which is the best free antivirus? Compare the features and choose the right one to protect against Trojans, viruses and malicious codes. Download Now!
A good Free Antivirus Software must feature: - Ability to identify suspicious files - Feature instant malware removal - Offer proactive defense mechanism against any kind of malware - Ensure efficient system performance - Rapid, instant cloud-based scanning - Instant updates on the new and up-to-date virus definitions - User-friendly interface and real-time protection - Automatic scanning of files, as and when downloaded from the internet - Provides security while connected to the internet
Related Resources - Antivirus for Windows 10 - Antivirus for Windows 8 - Antivirus for Windows 7 - Antivirus for Linux - Antivirus for Mac
Contact Details:
Tel: +1 (888) 551-1531 Tel: +1 (973) 859-4000 Fax: +1 (973) 777-4394
Inquiries:
Website: https://antivirus.comodo.com/faq/which-is-the-best-antivirus.html
#FreeAntivirus#FreeAntivirusSoftware#BestFreeAntivirusSoftware#malwareremoval#Antivirus#malwaredetection
0 notes
Link
https://bit.ly/3QVvTe0 - 🔐 A sophisticated new variant of the Jupyter information stealer, also known as Yellow Cockatoo, Solarmarker, and Polazert, has been increasingly targeting users of Chrome, Edge, and Firefox browsers. This malware is capable of backdooring machines and harvesting a variety of sensitive data, including credentials, cookies, and information from browser password managers. #JupyterMalware #CyberSecurity #DataTheft 🕵️ VMware's Carbon Black researchers have observed this variant using PowerShell command modifications and digitally signed payloads to evade detection. The malware's advanced evasion techniques and use of legitimate-looking certificates are of particular concern, as they allow it to bypass malware detection tools. #MalwareDetection #Infosec #VMwareCarbonBlack 🌐 Other cybersecurity firms like Morphisec and BlackBerry have identified Jupyter's diverse capabilities, including functioning as a full-fledged backdoor and acting as a dropper for other malware. Its sophisticated methods include hollowing shell code to evade detection and executing PowerShell scripts. #CyberThreats #BackdoorMalware #Morphisec #BlackBerry 💳 The malware operators have employed various distribution techniques, including search engine redirects, drive-by downloads, phishing, and SEO poisoning. Recent attacks have seen the use of valid certificates to sign the malware, making it appear legitimate and tricking users into downloading it. #MalwareDistribution #DigitalCertificates #Phishing 📈 The rise in infostealers like Jupyter follows a trend of increased remote work. Infostealers are being used more frequently to gather credentials that enable access to enterprise networks. Firms like Red Canary and Uptycs have reported a significant rise in such attacks, emphasizing the opportunistic nature of these malware campaigns. #RemoteWorkSecurity #InfostealerTrend #RedCanary #Uptycs 🌐 The impact of Jupyter and other infostealers is severe, with stolen data often sold on the dark web, posing significant risks to both organizations and individuals. The increasing sophistication and frequency of these attacks highlight the need for advanced cybersecurity measures.
#JupyterMalware#CyberSecurity#DataTheft#MalwareDetection#Infosec#VMwareCarbonBlack#CyberThreats#BackdoorMalware#Morphisec#BlackBerry#MalwareDistribution#DigitalCertificates#Phishing#RemoteWorkSecurity#InfostealerTrend#RedCanary#Uptycs#CyberRisk#DarkWeb#DataSecurity
0 notes
Text
#malware android#malware#hacking#malwareaimodels aimodelsmalware machinelearning malwaredetection#hacker#growth hacking
1 note
·
View note
Note
no baldshark likes everything its someone else
omg malwaredetected🤨🤨🤨
7 notes
·
View notes
Text
BrandLock

BrandLock is the first ever conversion optimization suite for online businesses, that offers a consumer-side malware solution and equips you with smart insights, and tools to increase your on-site conversions. Read the full article
0 notes