#Endpoint Security Market Market Growth 2023
Text
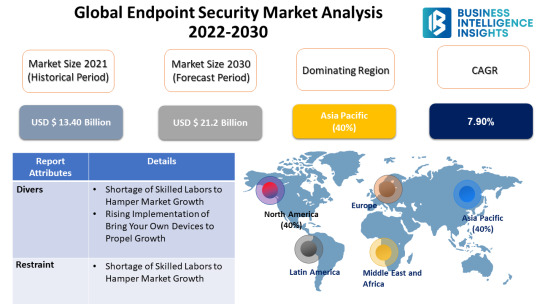
As per Business Intelligence Insights (BII) study, the global Global Endpoint Security Market attained revenue growth of USD 13.40 billion in 2021 and it is projected to reach around USD 21.2 billion by 2030, growing at a 7.90% CAGR.
#Endpoint Security Market#Endpoint Security Market Market#Endpoint Security Market Market Trends#Endpoint Security Market Market Share#Endpoint Security Market Market Size#Endpoint Security Market Market Analysis#Endpoint Security Market Market Demand#Endpoint Security Market Market Growth 2023#Endpoint Security Market Market Industry
0 notes
Text
Automotive Cyber Security Market — Forecast(2024–2030)

Global automotive cyber security market size was valued at USD 3,090.6 million in 2022 and is estimated to expand at a compound annual growth rate (CAGR) of 20.93% from 2023 to 2030.
Download Sample
1. Introduction
The automotive industry is undergoing a significant transformation with the rise of connected vehicles, autonomous driving, and electric vehicles (EVs). This transformation brings a heightened risk of cyber threats, making automotive cybersecurity a critical area of focus. Automotive cybersecurity encompasses technologies and strategies designed to protect vehicles from hacking, data breaches, and other cyber threats.
2. Market Size and Growth
The automotive cybersecurity market has seen rapid growth due to increasing concerns over vehicle safety and data privacy. According to recent reports, the global automotive cybersecurity market is expected to grow from approximately $4.5 billion in 2023 to around $10 billion by 2028, at a compound annual growth rate (CAGR) of over 18%.
3. Key Drivers
Rise of Connected Vehicles: The increasing number of connected vehicles with internet access and in-vehicle networks heightens the risk of cyberattacks.
Autonomous Vehicles: The development of autonomous driving technologies requires robust cybersecurity measures to ensure safe operation and prevent malicious interference.
Regulatory Compliance: Governments and regulatory bodies are implementing stricter cybersecurity regulations for automotive manufacturers, pushing the industry towards enhanced security measures.
Growing Data Privacy Concerns: With vehicles collecting vast amounts of data, protecting this information from unauthorized access has become a priority.
Enquiry Before Buying
4. Major Threats
Remote Attacks: Hackers can exploit vulnerabilities in vehicle communication systems to gain unauthorized access remotely.
Vehicle-to-Everything (V2X) Attacks: Threats targeting the communication between vehicles and their environment can disrupt traffic systems and endanger safety.
Software Vulnerabilities: Flaws in vehicle software or firmware can be exploited to gain control over critical vehicle functions.
Data Breaches: Unauthorized access to personal and sensitive data collected by vehicles can lead to privacy violations and identity theft.
Schedule a Call
5. Key Technologies
Intrusion Detection Systems (IDS): Monitors vehicle networks and systems for suspicious activity.
Encryption: Protects data transmitted between the vehicle and external entities by encoding it to prevent unauthorized access.
Secure Communication Protocols: Ensures that data exchanged between vehicle components and external networks is secure.
Hardware Security Modules (HSMs): Provides physical and logical protection against tampering and unauthorized access to cryptographic keys and sensitive data.
6. Market Segmentation
By Security Type: Network Security, Endpoint Security, Application Security, and Cloud Security.
By Vehicle Type: Passenger Cars, Commercial Vehicles, and Electric Vehicles.
By Technology: Encryption, Intrusion Detection Systems, Firewall, and Public Key Infrastructure (PKI).
By Region: North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa.
7. Regional Insights
North America: Leads the market due to early adoption of connected and autonomous vehicles, along with stringent cybersecurity regulations.
Europe: Significant growth driven by regulatory standards such as the General Data Protection Regulation (GDPR) and the European Union’s cybersecurity initiatives.
Asia-Pacific: Rapid growth due to increasing vehicle production and adoption of advanced automotive technologies, with notable developments in China and Japan.
Buy Now
8. Key Players
Autotalks: Specializes in V2X communication solutions and automotive cybersecurity.
Harman International (Samsung Electronics): Provides end-to-end cybersecurity solutions for connected and autonomous vehicles.
Vector Informatik: Offers a range of automotive security products, including intrusion detection and prevention systems.
NXP Semiconductors: Focuses on secure hardware solutions for automotive applications.
McAfee: Provides cybersecurity solutions tailored for automotive systems.
9. Challenges
Complexity of Automotive Systems: The increasing complexity of vehicle architectures makes it challenging to implement comprehensive cybersecurity measures.
Evolving Threat Landscape: The rapid evolution of cyber threats requires continuous updates and improvements in security technologies.
Cost Considerations: Implementing advanced cybersecurity solutions can be expensive, especially for smaller manufacturers and suppliers.
10. Future Outlook
The automotive cybersecurity market is poised for significant advancements with the integration of artificial intelligence (AI) and machine learning (ML) for predictive threat detection and response. As vehicles become more connected and autonomous, the need for robust and adaptive cybersecurity solutions will continue to grow.
To get more information about this Click Here
#reseach marketing#marketing#digital marketing#automotive#cybersecurity#security#data security#car accessories
0 notes
Text
Endpoint Security Market Size, Share, Trend, Forecast, & Growth Analysis: 2024-2032
Endpoint Security Market 2024 Report: A Comprehensive Analysis of Historical and Current Market Trends with Strategic Insights.
Analysis of the global "Endpoint Security Market" shows that the market will develop steadily and strongly between 2024 and 2032, and projections indicate that this growth will continue through 2032. The increasing demand from consumers for ecologically friendly and sustainable products is a noteworthy development in the Endpoint Security Market. To improve the effectiveness and caliber of products in the Endpoint Security Market, technology has also been used much more frequently.
➼ Market Capacity:
Between 2017 and 2023, the Endpoint Security Market's value increased significantly, from US$ million to US$ million. With a compound annual growth rate (CAGR) predicted to reach US$ million by 2032, this momentum is anticipated to continue. An extensive analysis explores consumer preferences and purchasing patterns in this industry, broken down by type (Trend Micro (Japan), Eset (U.S.), Symantec (U.S.), Sophos (U.K.), McAfee (U.S.)). Based on extensive research, this perceptive analysis is anticipated to be a useful tool for industry participants looking to profit from the market's remarkable anticipated compound annual growth rate (2024–2032).
➼ Key Players:
List of Endpoint Security Market PLAYERS PROFILED
The Endpoint Security Market includes several key players such as Cloud, On-Premises, Other play crucial roles in this market.
Endpoint Security Market Report Contains 2024: -
Complete overview of the global Endpoint Security Market
Top Country data and analysis for United States, Canada, Mexico, Germany, France, United Kingdom, Russia, Italy, China, Japan, Korea, India, Southeast Asia, Australia, Brazil and Saudi Arabia, etc. It also throws light on the progress of key regional Endpoint Security Markets such as North America, Europe, Asia-Pacific, South America and Middle East and Africa.
Description and analysis of Endpoint Security Market potentials by type, Deep Dive, disruption, application capacity, end use industry
impact evaluation of most important drivers and restraints, and dynamics of the global Endpoint Security Market and current trends in the enterprise
Value Propositions of This Market Research:
The study covers a comprehensive analysis of industry drivers, restraints, and opportunities, providing a neutral perspective on the market performance. It highlights recent industry trends and developments, offering insights into the competitive landscape and the strategies employed by key players. The study identifies potential and niche segments and regions exhibiting promising growth, supported by historical, current, and projected market size data in terms of value. An in-depth analysis of the Endpoint Security Market is included, along with an overview of the regional outlook. This holistic approach ensures a thorough understanding of the market dynamics and potential growth areas.
Request a Free Sample Copy
Global Endpoint Security Market: SEGMENTATION ANALYSIS
The research report includes specific segments by region (country), manufacturers, Type, and Application. Market segmentation creates subsets of a market based on product type, end-user or application, Geographic, and other factors. By understanding the market segments, the decision-maker can leverage this targeting in product, sales, and marketing strategies. Market segments can power your product development cycles by informing how you create product offerings for different segments.
➼ PRODUCTS/SERVICES:
Valuable Points from Endpoint Security Market Research Report 2024-2032:
The market for Endpoint Security Market has undergone significant changes because to changing consumer preferences, laws, and technological advancements. This dynamic business is being shaped by new product launches, mergers, and creative marketing strategies from big players. A thorough analysis of recent and historical data yields insights into the market's value, volume, historical growth, current size, and potential for the future. While competition research explores market share and strategy, segmentation by key regions exposes regional variances. The research provides practical suggestions to help you improve your position in this dynamic market and finds new niches and development possibilities across regions.
Request a Free Sample Copy
Behind the Brand
In an industry characterized by rapid growth and technological advancements, economic changes occur daily. To thrive in this dynamic environment, companies must understand market trends and develop effective strategies. A well-defined strategy not only facilitates planning but also offers a competitive edge. For dependable market reports that provide essential insights to guide your business toward success, visit us at www.globalmarketstatistics.com .
Explore More Related Reports Here :
Fantasy Games Market
Relational Databases Software Market
High Pressure Composite Gas Cylinder Market
Privacy Compliance Consulting Services Market
BNC Connector Market
Car Recycling Market
Smart Construction Excavator Market
Continuous Passive Motion Devices Market
Kubernetes Security Software Market
Warehouse Shuttle Car Market
Residual Current Detectors Market
Titanium Elastic Nail Market
Industrial Counterweights Market
Magnetic Resonance Imaging Market
Micro-Compact Cars Market
#innovation#management#digitalmarketing#technology#creativity#futurism#startups#marketing#entrepreneurship#money#sustainability#inspiration#Leadership#Business#Strategy#Growth#Success#Innovation#Ecommerce#PersonalDevelopment
1 note
·
View note
Text
The Evolution and Impact of the Web Content Filtering Market and Artificial Intelligence for IT Operations Platform Market
In today's rapidly evolving digital landscape, two markets have garnered significant attention: the Web Content Filtering Market and the Artificial Intelligence for IT Operations (AIOps) Platform Market. These two sectors are pivotal in shaping how businesses manage and secure their digital operations. This article delves into the nuances of these markets, exploring their growth, key players, technological advancements, and future trends.

1. Introduction to Web Content Filtering
What is Web Content Filtering?
Web content filtering is a crucial aspect of internet security, involving the control of what content is accessible over the internet within a particular network. It helps organizations prevent access to harmful or inappropriate websites, thus safeguarding employees and data.
Importance of Web Content Filtering
The importance of web content filtering cannot be overstated. It helps protect against malware, phishing attacks, and other cyber threats. Additionally, it ensures compliance with legal and regulatory standards, improves productivity by blocking distracting websites, and maintains a company's reputation by preventing access to inappropriate content.
2. Market Overview of Web Content Filtering
Current Market Size and Growth
The web content filtering market has experienced substantial growth over the past decade. As of 2023, it is valued at approximately $6 billion and is expected to grow at a CAGR of 14.8% from 2023 to 2028. This growth is driven by increasing cyber threats, the proliferation of internet usage, and stringent regulatory requirements.
Key Players in the Web Content Filtering Market
Several key players dominate the web content filtering market. These include:
Cisco: Known for its robust security solutions, Cisco offers comprehensive web content filtering services.
McAfee: A leader in cybersecurity, McAfee provides advanced web filtering solutions to protect against various threats.
Symantec: Now a part of Broadcom, Symantec offers powerful web filtering tools integrated with its broader cybersecurity suite.
Forcepoint: Specializes in data protection and cybersecurity, including web content filtering.
Webroot: Provides cloud-based web filtering solutions that are easy to deploy and manage.
Technological Advancements in Web Content Filtering
The web content filtering market has seen significant technological advancements, such as:
AI and Machine Learning: AI-driven algorithms enhance the accuracy of filtering by continuously learning from new threats and user behaviors.
Cloud-Based Solutions: Cloud-based filtering offers scalability, easier management, and real-time updates.
Integration with Other Security Tools: Modern web content filtering solutions are often integrated with broader cybersecurity frameworks, providing comprehensive protection.
3. Challenges in the Web Content Filtering Market
Evolving Cyber Threats
As cyber threats become more sophisticated, web content filtering solutions must continuously evolve to keep up. This requires constant updates and the incorporation of advanced technologies like AI.
User Privacy Concerns
Balancing effective content filtering with user privacy is a significant challenge. Companies must ensure that their filtering practices comply with privacy laws and do not infringe on users' rights.
Implementation and Management
Implementing and managing web content filtering solutions can be complex, especially for large organizations with diverse networks and numerous endpoints.
4. Future Trends in Web Content Filtering
Increased Use of AI and Machine Learning
AI and machine learning will play an increasingly important role in web content filtering. These technologies will enhance the accuracy and efficiency of filtering processes, enabling quicker responses to emerging threats.
Greater Emphasis on User Privacy
As privacy concerns continue to grow, future web content filtering solutions will need to strike a better balance between security and privacy. This could involve more transparent filtering practices and greater user control over what is filtered.
Integration with Comprehensive Security Frameworks
Web content filtering will increasingly be part of integrated security solutions that offer comprehensive protection against a range of cyber threats. This holistic approach will provide better overall security for organizations.
5. Introduction to AIOps Platforms
What are AIOps Platforms?
AIOps platforms use artificial intelligence to enhance IT operations. They analyze large volumes of data from various IT operations tools and devices to automatically identify and resolve IT issues. This helps improve the efficiency and reliability of IT operations.
Importance of AIOps Platforms
AIOps platforms are essential for modern IT operations due to their ability to handle the complexity and scale of today's IT environments. They help reduce downtime, improve performance, and enhance the overall user experience.
6. Market Overview of AIOps Platforms
Current Market Size and Growth
The AIOps platform market is also experiencing rapid growth. As of 2023, it is valued at approximately $2.5 billion and is expected to grow at a CAGR of 25% from 2023 to 2028. This growth is driven by the increasing complexity of IT environments and the need for more efficient and reliable IT operations.
Key Players in the AIOps Platform Market
Key players in the AIOps platform market include:
Splunk: Offers a comprehensive AIOps platform that provides visibility across the entire IT environment.
Moogsoft: Specializes in AI-driven IT incident management and analytics.
IBM: Provides a powerful AIOps platform that leverages its expertise in AI and cloud computing.
Dynatrace: Offers an AI-driven platform for monitoring and managing IT operations.
AppDynamics: Now part of Cisco, AppDynamics provides a robust AIOps platform focused on application performance management.
Technological Advancements in AIOps Platforms
Technological advancements driving the AIOps platform market include:
Advanced Analytics: Improved data analytics capabilities allow for more accurate identification and resolution of IT issues.
Automation: Enhanced automation capabilities reduce the need for manual intervention, improving efficiency and reliability.
Integration with Other IT Tools: Modern AIOps platforms integrate with a wide range of IT tools, providing a more comprehensive view of IT operations.
7. Challenges in the AIOps Platform Market
Data Complexity and Volume
Handling the sheer volume and complexity of data generated by modern IT environments is a significant challenge for AIOps platforms. Effective data management and analysis are crucial for the success of these platforms.
Integration with Existing Systems
Integrating AIOps platforms with existing IT systems can be complex and time-consuming. Ensuring seamless integration is essential for maximizing the benefits of these platforms.
Skill Gaps
The successful implementation of AIOps platforms requires specialized skills. There is a growing need for IT professionals with expertise in AI, data analytics, and IT operations.
8. Future Trends in the AIOps Platform Market
Enhanced AI Capabilities
As AI technology continues to advance, AIOps platforms will become even more powerful. Enhanced AI capabilities will allow for more accurate predictions, faster issue resolution, and improved overall performance.
Greater Automation
Future AIOps platforms will feature even greater levels of automation, reducing the need for manual intervention and allowing IT teams to focus on more strategic tasks.
Broader Integration
AIOps platforms will increasingly integrate with a wider range of IT tools and systems, providing a more comprehensive view of IT operations and enabling better decision-making.
9. The Intersection of Web Content Filtering and AIOps
Synergies Between the Two Markets
There are significant synergies between the web content filtering and AIOps platform markets. Both markets focus on improving security, efficiency, and reliability in the digital landscape. Integrating web content filtering with AIOps platforms can enhance overall IT security and operations.
Combined Benefits for Organizations
Organizations that leverage both web content filtering and AIOps platforms can achieve enhanced security and operational efficiency. Web content filtering protects against cyber threats, while AIOps platforms ensure reliable and efficient IT operations.
Future Opportunities
The convergence of these two markets presents future opportunities for innovation and growth. As organizations continue to adopt digital transformation strategies, the integration of web content filtering and AIOps platforms will become increasingly important.
10. Conclusion
In conclusion, the Web Content Filtering Market and the Artificial Intelligence for IT Operations Platform Market are both critical components of modern digital security and operations. As cyber threats evolve and IT environments become more complex, the demand for advanced web content filtering and AIOps solutions will continue to grow. Organizations that invest in these technologies will be better positioned to protect their digital assets, ensure compliance, and improve operational efficiency. The future holds exciting opportunities for these markets, driven by technological advancements and the increasing importance of digital security and reliability.
1 note
·
View note
Text
The global demand for Enterprise Mobility Management was valued at USD 16284.8 million in 2022 and is expected to reach USD 102147.4 Million in 2030, growing at a CAGR of 25.80% between 2023 and 2030.Enterprise Mobility Management (EMM) is an essential component in the modern business landscape, reflecting the increasing reliance on mobile devices and remote work solutions. EMM encompasses a suite of tools, processes, and technologies designed to manage and secure mobile devices, applications, and data used in enterprise settings. This market has seen significant growth in recent years, driven by the surge in mobile workforce, advancements in technology, and the need for enhanced security measures.
Browse the full report at https://www.credenceresearch.com/report/enterprise-mobility-management-market
Market Overview
The EMM market has expanded rapidly, with businesses recognizing the importance of mobile technology in enhancing productivity and operational efficiency. EMM solutions typically include mobile device management (MDM), mobile application management (MAM), mobile content management (MCM), and mobile identity management. These components collectively enable organizations to streamline their mobile operations, ensuring that devices and data are secure and compliant with corporate policies.
Drivers of Growth
1. Increasing Mobile Workforce: The rise of remote work and flexible working arrangements has led to a substantial increase in the use of mobile devices for business purposes. Employees now expect seamless access to corporate resources from anywhere, driving the demand for robust EMM solutions.
2. Advancements in Mobile Technology: The rapid evolution of smartphones, tablets, and mobile applications has created new opportunities for businesses to leverage mobile technology. EMM solutions are continually adapting to support these advancements, providing enhanced features and functionalities.
3. Data Security Concerns: With the proliferation of mobile devices, data security has become a critical concern for enterprises. EMM solutions offer comprehensive security features, including encryption, remote wipe, and policy enforcement, to protect sensitive corporate data.
4. Regulatory Compliance: Compliance with industry regulations and standards, such as GDPR, HIPAA, and others, necessitates stringent control over mobile devices and data. EMM solutions help organizations meet these regulatory requirements, reducing the risk of non-compliance.
5. BYOD Trend: The Bring Your Own Device (BYOD) trend has gained traction, allowing employees to use their personal devices for work purposes. EMM solutions enable organizations to manage and secure these devices effectively, ensuring a balance between productivity and security.
Key Players and Competitive Landscape
The EMM market is highly competitive, with numerous vendors offering a variety of solutions. Key players include Microsoft, IBM, VMware, Citrix, and BlackBerry. These companies are continually innovating to provide comprehensive EMM solutions that address the evolving needs of businesses.
- Microsoft: Known for its Intune platform, Microsoft offers a robust EMM solution integrated with its Office 365 suite, providing seamless management of mobile devices and applications.
- IBM: IBM’s MaaS360 platform delivers comprehensive EMM capabilities, including advanced security features and AI-driven insights for proactive management.
- VMware: VMware’s Workspace ONE platform offers unified endpoint management, integrating EMM with desktop management for a holistic approach.
- Citrix: Citrix Endpoint Management provides a secure and user-friendly solution for managing mobile devices and applications, emphasizing user experience.
-BlackBerry: Renowned for its security features, BlackBerry’s EMM solutions cater to industries with stringent security requirements, such as government and finance.
Challenges and Future Outlook
Despite its growth, the EMM market faces several challenges. Integrating EMM solutions with existing IT infrastructure can be complex and costly. Additionally, ensuring user adoption and compliance with EMM policies requires ongoing education and support.
Looking ahead, the EMM market is poised for continued growth, driven by advancements in artificial intelligence (AI) and machine learning (ML). These technologies will enable more predictive and proactive management of mobile devices, enhancing security and operational efficiency. Moreover, the increasing adoption of 5G technology will further fuel the demand for EMM solutions, enabling faster and more reliable mobile connectivity.
Key Players
Cisco Systems
SAP SE
Broadcom, Inc.
AppTec GmbH
IBM Corporation
Microsoft Corporation
VMware
Citrix Systems
Ivanti
Micro Focus
Zoho Corporation Pvt. Ltd
Matrix42
Sophos
Blackberry
Esper
Segmentation
By Mobile Device Management (MDM):
Device Inventory and Tracking
Security Policies
By Mobile Application Management (MAM):
App Distribution and Updating
App Security Policies
By Mobile Content Management (MCM):
Secure File Sharing
Content Encryption
By Identity and Access Management (IAM):
Single Sign-On (SSO)
Authentication and Authorization
By Unified Endpoint Management (UEM):
Integration of MDM, MAM, and MCM
Policy Enforcement
By Bring Your Own Device (BYOD) Solutions:
BYOD Policies
Containerization
By Industry Verticals:
Healthcare EMM
Financial Services EMM
Government EMM
By Deployment Models:
On-Premises EMM
Cloud-Based EMM
By Service Models:
Managed EMM Services
Consulting and Professional Services
By Enterprise Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
By Network Security Integration:
VPN Integration
Mobile Threat Defense
By Region
North America
The U.S.
Canada
Mexico
Europe
Germany
France
The U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of Middle East and Africa
Browse the full report at https://www.credenceresearch.com/report/enterprise-mobility-management-market
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
Website: www.credenceresearch.com
0 notes
Text
Medical Device Security Market Size: Investment Trends

The Medical Device Security Market Size was valued at USD 6.09 billion in 2022 and is expected to reach USD 12.06 billion by 2030 and grow at a CAGR of 8.9% over the forecast period 2023-2030.The Medical Device Security Market is rapidly evolving, driven by the increasing prevalence of cyber threats and the growing integration of connected medical devices in healthcare systems. With advancements in telemedicine, IoT, and AI, securing sensitive patient data and ensuring the integrity of medical devices have become paramount.
This market is witnessing significant investment in innovative solutions, including advanced encryption, threat detection, and secure firmware updates. Regulatory frameworks and standards, such as the FDA's cybersecurity guidelines, are also shaping the landscape, pushing manufacturers to prioritize security in their design and development processes. As healthcare systems worldwide continue to digitize, the demand for robust medical device security solutions is expected to soar, making it a critical focus area for technology providers and healthcare institutions alike.
For the forecasted year, the study offers exact figures for the industry's market size, share, production capacity, demand, and growth. This is the most recent analysis of the commercial impact of COVID-19. The global Medical Device Security Market research report provides a thorough examination of the existing and future state of the industry. The report includes all market data and was generated using a combination of primary and secondary sources. The report also includes data on market volume and value for each category, as well as information on type, industry, channel, and other variables.
Get Sample of This Report @ https://www.snsinsider.com/sample-request/2193
Market Segmentation
By Component
Solutions
Services
By Type
Application Security
Endpoint Security
Network Security
Cloud Security
By Device Type
Hospital Medical Devices
Internally Embedded Medical Devices
Wearable and External Medical Devices
By End User
Healthcare Providers
Medical Device Manufacturers
Healthcare Payers
Russia-Ukraine War Impact on Medical Device Security Market
The study report includes a full examination of the primary effects of the Russia-Ukraine conflict on the domestic and global markets. Should energy trade shift, supply chains reorganize, payment networks fragment, and governments review reserve currency holdings, the battle could destabilize global economic and geopolitical order in the long run.
Regional Analysis
Research covers everything from production and consumer ratios to market size and market share, import and export ratios, supply and demand, consumer demand ratios, technological advancements, research and development, infrastructure development, economic growth, and a strong market presence in every region. The Medical Device Security Market is divided into five regions: North America, Latin America, Europe, Asia Pacific, and the Rest of the World. Geographic study will aid players in identifying attractive markets where they may benefit on new opportunities.
Competitive Outlook
The study offers a comprehensive view of the worldwide competitive environment as well as crucial insights into major competitors and their expansion ambitions. It also includes crucial data on financial conditions, global positioning, product portfolios, income and gross profit margins, as well as technology and research advancements. The Medical Device Security Market study focuses on the most significant acquisitions, collaborations, and product launches in the sector. The study report integrates advanced research approaches such as SWOT and Porter's Five Forces analysis to provide deeper insights into significant actors.
About Us
SNS Insider is a market research and insights firm that has won several awards and earned a solid reputation for service and strategy. We are a strategic partner who can assist you in re framing issues and generating answers to the trickiest business difficulties. For greater consumer insight and client experiences, we leverage the power of experience and people.
When you employ our services, you will collaborate with qualified and experienced staff. We believe it is crucial to collaborate with our clients to ensure that each project is customized to meet their demands. Nobody knows your customers or community better than you do. Therefore, our team needs to ask the correct questions that appeal to your audience in order to collect the best information.
Related Reports
Oncology Drugs Market Forecast
Osteoporosis Treatment Market Forecast
Peripheral Neuropathy Market Forecast
Active Pharmaceutical Ingredient Market Forecast
Blood Group Typing Market Forecast
0 notes
Text
Mobile Threat Defence Market Insights: Comprehensive Global Forecast (2023-2032)

It is anticipated that between 2023 and 2030, the worldwide Mobile Threat Defense Market will expand at a compound annual growth rate (CAGR) of 26.50%. From USD 2154.8 million in 2022, the market is projected to be worth USD 14129.6 million by 2030.
The Mobile Threat Defense (MTD) market is experiencing significant growth, fueled by the increasing reliance on mobile devices for business operations and the rising incidence of sophisticated cyber threats targeting mobile platforms. As smartphones and tablets become integral to corporate networks, the need for robust security solutions to protect sensitive data and ensure compliance with regulatory standards has intensified. MTD solutions provide comprehensive protection by detecting and mitigating threats such as malware, phishing attacks, network vulnerabilities, and unauthorized access. These solutions leverage advanced technologies like artificial intelligence and machine learning to identify and respond to emerging threats in real-time.
The adoption of BYOD (Bring Your Own Device) policies and the proliferation of remote work have further driven the demand for MTD, as organizations seek to secure a diverse array of devices accessing their networks. Leading vendors in the market, including companies like Lookout, Zimperium, and Symantec, offer integrated MTD platforms that deliver endpoint security, application security, and network security, ensuring a multi-layered defense strategy. North America remains the dominant market due to its advanced IT infrastructure and high awareness of mobile security risks, while the Asia-Pacific region is witnessing rapid growth driven by increasing mobile device penetration and cyber threats.
The Mobile Threat Defense (MTD) market faces several challenges that can impact its growth and adoption. These challenges stem from technological, organizational, and economic factors, requiring strategic approaches to overcome. Here are the key challenges in the MTD market:
1. Evolving Threat Landscape
Sophisticated Attacks: Cyber threats targeting mobile devices are becoming increasingly sophisticated, with attackers using advanced techniques to bypass security measures. This requires continuous innovation and updates in MTD solutions to stay ahead of threats.
Zero-Day Vulnerabilities: New and previously unknown vulnerabilities (zero-day threats) pose significant challenges as they can exploit gaps in mobile security before patches or defenses are developed.
2. High Cost of Deployment
Initial Investment: Implementing comprehensive MTD solutions can be costly, involving significant initial investment in software, hardware, and integration.
Ongoing Maintenance: Continuous updates and maintenance are required to keep MTD solutions effective against new threats, adding to the operational costs for organizations.
3. Integration with Existing Systems
Compatibility Issues: Integrating MTD solutions with existing IT infrastructure and security systems can be complex, requiring seamless interoperability to ensure effective protection.
Legacy Systems: Organizations with legacy systems may face challenges in integrating modern MTD solutions, potentially leading to gaps in security coverage.
4. User Adoption and Awareness
Lack of Awareness: Many users and organizations are still unaware of the specific threats targeting mobile devices, leading to underinvestment in MTD solutions.
User Resistance: Employees may resist security measures that they perceive as intrusive or inconvenient, reducing the effectiveness of MTD implementations.
5. Regulatory Compliance
Compliance Requirements: Ensuring that MTD solutions comply with various regulatory standards (such as GDPR, HIPAA, and PCI-DSS) can be challenging, especially for organizations operating in multiple jurisdictions.
Data Privacy Concerns: Balancing robust security with user privacy is critical, as overly intrusive measures can lead to data privacy issues and regulatory penalties.
6. Device Diversity and Fragmentation
Variety of Devices: The wide range of mobile devices, operating systems, and versions complicates the implementation of uniform MTD solutions. Ensuring compatibility and protection across all devices is challenging.
OS Fragmentation: Different versions of mobile operating systems and customizations by device manufacturers can create fragmentation, making it harder to develop universal security solutions.
7. BYOD and Remote Work Policies
BYOD Complexity: Bring Your Own Device (BYOD) policies increase the complexity of securing mobile devices, as personal devices may not adhere to corporate security standards.
Remote Work Security: The rise of remote work has expanded the attack surface, requiring robust and scalable MTD solutions to protect devices accessing corporate networks from various locations.
8. Performance and User Experience
Impact on Performance: MTD solutions must balance security with device performance. Overly aggressive security measures can slow down devices, leading to user dissatisfaction.
User Experience: Ensuring that MTD solutions do not disrupt the user experience is crucial for adoption. Security measures should be unobtrusive and easy to use.
9. Skilled Personnel Shortage
Cybersecurity Skills Gap: There is a shortage of skilled cybersecurity professionals capable of managing and optimizing MTD solutions, making it difficult for organizations to effectively implement and maintain these systems.
Training and Education: Continuous training and education are required to keep IT staff updated on the latest mobile threats and defense strategies.
10. Market Competition and Innovation
Rapid Technological Changes: The fast-paced nature of technological advancements in cybersecurity requires constant innovation and adaptation by MTD vendors to remain competitive.
Vendor Differentiation: With numerous vendors in the market, differentiating products and services to offer unique value propositions is challenging.
Key Players:
Cisco Systems
SAP SE
Broadcom, Inc.
VMware
Citrix Systems
Kaspersky Labs
Ivanti
Micro Focus
ZOHO
SolarWinds
Zimperium
Matrix42
Sophos
Blackberry Esper
More About Report- https://www.credenceresearch.com/report/mobile-threat-defence-market
The future landscape of the Mobile Threat Defense (MTD) market is poised for significant transformation, driven by advancements in technology, increasing mobile device usage, and the evolving nature of cyber threats. Here are some key trends and factors shaping the future of the MTD market:
1. Advancements in AI and Machine Learning
Enhanced Threat Detection: AI and machine learning will play a crucial role in improving threat detection capabilities, enabling MTD solutions to identify and respond to threats in real-time with greater accuracy.
Predictive Analytics: The use of predictive analytics will allow MTD solutions to anticipate and mitigate potential threats before they materialize, providing proactive security measures.
2. Integration with Zero Trust Security Models
Zero Trust Architecture: The adoption of Zero Trust security models, which operate on the principle of “never trust, always verify,” will become more prevalent. MTD solutions will integrate seamlessly with Zero Trust frameworks to ensure comprehensive mobile security.
Continuous Monitoring: Continuous authentication and monitoring of mobile devices will be integral to maintaining security in a Zero Trust environment.
3. Increased Adoption of 5G Technology
5G Networks: The widespread deployment of 5G networks will enhance mobile connectivity and data speeds, but will also introduce new security challenges. MTD solutions will need to evolve to address the unique threats associated with 5G technology.
IoT Security: As 5G enables a proliferation of Internet of Things (IoT) devices, securing these interconnected devices will become a critical focus for MTD solutions.
4. Growth of Remote Work and BYOD Policies
Remote Work Security: The continuation of remote work trends will drive the demand for robust MTD solutions that can secure mobile devices accessing corporate networks from various locations.
BYOD Security: As BYOD policies remain prevalent, MTD solutions will need to offer comprehensive protection for personal devices used for work purposes, ensuring data security and compliance.
5. Regulatory and Compliance Pressures
Data Privacy Regulations: Increasingly stringent data privacy regulations (such as GDPR, CCPA, and HIPAA) will require organizations to adopt MTD solutions that ensure compliance and protect sensitive information on mobile devices.
Industry-Specific Standards: Compliance with industry-specific security standards will drive the adoption of specialized MTD solutions tailored to meet the unique requirements of different sectors.
6. Integration with Mobile Device Management (MDM)
Unified Security Solutions: The convergence of MTD and Mobile Device Management (MDM) solutions will provide unified security and management capabilities, simplifying the administration of mobile devices and enhancing overall security.
Holistic Approach: Organizations will increasingly seek integrated solutions that offer both device management and threat defense to streamline operations and reduce complexity.
7. Cloud-Based Security Solutions
Scalable Security: Cloud-based MTD solutions will offer scalability and flexibility, allowing organizations to easily expand their security measures as their mobile device usage grows.
Real-Time Updates: The cloud-based delivery model will enable real-time updates and threat intelligence sharing, ensuring that MTD solutions are always equipped to handle the latest threats.
8. Focus on User Experience
Seamless Security: Ensuring that security measures are unobtrusive and do not disrupt the user experience will be a key focus for MTD solution providers. User-friendly interfaces and minimal performance impact will be critical for adoption.
Employee Training: Organizations will invest in training programs to educate employees on mobile security best practices and the importance of adhering to security protocols.
9. Emerging Technologies and Innovations
Biometric Authentication: Advances in biometric authentication methods, such as facial recognition and fingerprint scanning, will enhance mobile device security and reduce reliance on traditional passwords.
Blockchain Technology: The integration of blockchain technology could provide enhanced security for mobile transactions and data storage, ensuring data integrity and reducing the risk of tampering.
10. Geographic Market Expansion
Emerging Markets: Rapid digitalization and increasing mobile device penetration in emerging markets will drive demand for MTD solutions, presenting growth opportunities for vendors.
Localized Solutions: Tailoring MTD solutions to meet the specific needs and regulatory requirements of different regions will be important for global market expansion.
Segmentation
By Security Threat Type:
Malware Protection
Phishing Protection
Data Loss Prevention (DLP)
Network Security
App Security
Device Security
By Deployment Model:
Cloud-based
On-Premises
Hybrid
By Organization Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
Browse the full report – https://www.credenceresearch.com/report/mobile-threat-defence-market
Browse Our Blog: https://www.linkedin.com/pulse/mobile-threat-defence-market-insights-comprehensive-huurf
Contact Us:
Phone: +91 6232 49 3207
Email: [email protected]
Website: https://www.credenceresearch.com
0 notes
Text
Social Media Security Market: Forthcoming Trends and Share Analysis by 2032
Social Media Security Market Size Was Valued at USD 1412 Million in 2023 and is Projected to Reach USD 5378.12 Million by 2032, Growing at a CAGR of 16.02 % From 2024-2032.
A crucial component of internet safety is social media security, which includes tactics and controls meant to shield people and institutions from the constantly changing threats connected to using social networking sites. Social media usage is increasing, which raises the possibility of a number of risks, such as phishing scams, identity theft, privacy violations, and cyberbullying.
The market for social media security has grown significantly in recent years due to growing worries about cyber attacks, data breaches, and online privacy on social media platforms. Social media security solutions are in more demand as more individuals and organizations realize how important it is to protect their digital presence from unwanted activity.
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/3987
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Leading players involved in the Social Media Security Market include:
Symantec (United States)
CA Technologies(United States)
ZeroFOX (United States)
RiskIQ (United States)
SolarWinds(United States)
Proofpoint (United States)
LookingGlass Cyber Solutions (United States)
KnowBe4 (United States)
Centrify (United States)
Social Hub (United States)
Brandle (United States)
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
If You Have Any Query Social Media Security Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/3987
Segmentation of Social Media Security Market:
By Solution
Monitoring
Threat Intelligence
Risk Management
By Security
Web Security
Application Security
Endpoint Security
Network Security
Cloud Security
By End Use Industry
BFSI
Healthcare and life sciences
Manufacturing
Telecom & IT
Media and entertainment
Others
An in-depth study of the Social Media Security industry for the years 2023–2030 is provided in the latest research. North America, Europe, Asia-Pacific, South America, the Middle East, and Africa are only some of the regions included in the report's segmented and regional analyses. The research also includes key insights including market trends and potential opportunities based on these major insights. All these quantitative data, such as market size and revenue forecasts, and qualitative data, such as customers' values, needs, and buying inclinations, are integral parts of any thorough market analysis.
Market Segment by Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Key Benefits of Social Media Security Market Research:
Research Report covers the Industry drivers, restraints, opportunities and challenges
Competitive landscape & strategies of leading key players
Potential & niche segments and regional analysis exhibiting promising growth covered in the study
Recent industry trends and market developments
Research provides historical, current, and projected market size & share, in terms of value
Market intelligence to enable effective decision making
Growth opportunities and trend analysis
Covid-19 Impact analysis and analysis to Social Media Security market
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=3987
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assist our clients grow and have a successful impact on the market. Our team at IMR is ready to assist our clients flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, specialized in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyze extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1 773 382 1049
Email: [email protected]
#Social Media Security#Social Media Security Market#Social Media Security Market Size#Social Media Security Market Share#Social Media Security Market Growth#Social Media Security Market Trend#Social Media Security Market segment#Social Media Security Market Opportunity#Social Media Security Market Analysis 2023
0 notes
Text
How artificial intelligence is revolutionizing cyber security - CyberTalk
New Post has been published on https://thedigitalinsider.com/how-artificial-intelligence-is-revolutionizing-cyber-security-cybertalk/
How artificial intelligence is revolutionizing cyber security - CyberTalk


By Shira Landau, Editor-in-Chief, CyberTalk.org.
In recent years, artificial intelligence (AI) has become one of the most sure-fire and strategic tools available for cyber security professionals. Due to the increasing sophistication of cyber attacks, cyber security experts have broadly turned to AI in order to enhance abilities to detect and prevent cyber threats.
As it stands, nearly 50% of enterprises are already using a combination of artificial intelligence and machine learning tools to improve cyber security outcomes, and 92% of organizations plan to adopt these types of tools in the future.
Powerful AI technology is particularly useful for identifying and mitigating security threats that are difficult or impossible to detect manually, such as zero-day exploits, polymorphic malware, and advanced persistent threats. AI-based tools can also help streamline tasks, lower costs, augment under-resourced operations and enable security professionals to work ‘smarter.’
Are you ready to take your organization’s cyber security to the next level? With AI, you can stay ahead of the curve and protect your organization from the most advanced of cyber threats. In this article, explore the incredible ways in which AI is enhancing and revolutionizing cyber security and the digital world.
Key information
A spike in cyber attacks has helped fuel market growth for AI-based cyber security products.
The global market for AI-based cyber security products is estimated to reach $133.8 billion by 2030.
AI-based tools enable cyber security professionals to work smarter and more efficiently than is otherwise possible.
How AI is revolutionizing cyber security
1. Threat detection. One of the most significant challenges that cyber security professionals face is the sheer volume of data that they need to sift through. Given the number of internet-connected devices (IoT growth is projected to reach 3.22 billion in North America alone in 2023), there is a seemingly insatiable appetite for data processing.
Artificial intelligence technology is extremely helpful when it comes to efficiently and accurately analyzing large volumes of data, rendering AI an essential tool for cyber security professionals. Algorithms can quickly analyze patterns in data to identify threats and to detect anomalous behavior.
2. Automation. AI is also being deployed in order to automate and streamline aspects of cyber security. In turn, this enables cyber security professionals to focus on investigating and mitigating complex threats, while AI takes care of tedious or monotonous basic tasks.
3. Machine learning. Another advantage of AI-powered cyber security systems consists of its ability to learn from past attacks and to improve on existing threat detection capabilities.
By looking at data from past attacks, machine learning algorithms can identify patterns, and then actually develop new and sophisticated detection methods. Over time, this development makes breaching systems tougher for cyber criminals.
4. Insider threats. Artificial intelligence is particularly useful in cyber security when it comes to detecting and responding to insider threats. These threats are tricky to detect, as the individuals involved always have legitimate access to a given network.
Nonetheless, AI-powered systems can analyze user behavior, and thereby identify patterns that indicate an insider threat. Such patterns can then be flagged for further investigation.
5. Endpoint security. AI is also being used to enhance endpoint security. Traditional endpoint security solutions rely on signature-based detection, which involves identifying known threats and blocking them. But this approach is losing its effectiveness.
AI-powered endpoint security solutions leverage machine learning algorithms to identify anomalous behavior and to detect previously unknown threats. This approach is more effective than what traditional endpoint security solutions can offer, as it can identify threats that would otherwise remain unnoticed.
6. Finally, AI is being used to improve threat intelligence. By analyzing large volumes of data from disparate sources, AI-powered threat intelligence solutions can zero in on potential threats and offer early warnings around new types of attacks. This information can then be used to develop optimally effective cyber security strategies and to advance the overall security posture of an organization.
In conclusion
AI is revolutionizing the field of cyber security by providing cyber security professionals with the tools that they need to detect, prevent and respond to cyber threats.
Are you drowning in data? Struggling to keep up amidst the ever-evolving threat landscape? Get ready for whatever comes your way! Explore AI-based cyber security tools that make it easier (and more efficient) than ever to protect your systems. Click here to learn more and to start applying AI’s game-changing capabilities within your business.
Want to stay up-to-date with the latest and greatest in cyber security? Check out the CyberTalk.org newsletter! Sign up today to receive top-notch news articles, best practices and expert analyses; delivered straight to your inbox.
#2023#advanced persistent threats#ai#AI-powered#Algorithms#America#analyses#anomalies#approach#Article#Articles#artificial#Artificial Intelligence#automation#Behavior#billion#Business#connected devices#cyber#cyber attacks#cyber criminals#cyber security#cyber security professionals#Cyber Threats#data#data processing#detection#development#devices#endpoint
0 notes
Text
Healthcare Cybersecurity Services Market is Dazzling Worldwide and Forecast to 2030 | GQ Research
The Healthcare Cybersecurity Services market is set to witness remarkable growth, as indicated by recent market analysis conducted by GQ Research. In 2023, the global Healthcare Cybersecurity Services market showcased a significant presence, boasting a valuation of US 15.64 Billion. This underscores the substantial demand for Healthcare Cybersecurity Services technology and its widespread adoption across various industries.
Get Sample of this Report at: https://gqresearch.com/request-sample/global-healthcare-cybersecurity-services-market/

Projected Growth: Projections suggest that the Healthcare Cybersecurity Services market will continue its upward trajectory, with a projected value of US$ 40.42 Billion by 2030. This growth is expected to be driven by technological advancements, increasing consumer demand, and expanding application areas.
Compound Annual Growth Rate (CAGR): The forecast period anticipates a Compound Annual Growth Rate (CAGR) of 11.12 %, reflecting a steady and robust growth rate for the Healthcare Cybersecurity Services market over the coming years.
Technology Adoption:
Healthcare organizations adopting cybersecurity services to protect sensitive patient data and prevent cyber threats.
Services include network security, data encryption, threat detection, and incident response.
Integration of cybersecurity solutions with electronic health record (EHR) systems and medical devices.
Application Diversity:
Hospitals and Clinics: Securing patient records, medical devices, and hospital networks against cyber threats.
Pharmaceutical Companies: Protecting intellectual property, research data, and supply chain operations from cyber attacks.
Telemedicine Providers: Ensuring secure communication channels and data transmission for remote patient consultations.
Healthcare IT Vendors: Offering cybersecurity solutions and services to healthcare organizations.
Consumer Preferences:
Demand for robust cybersecurity measures to safeguard personal health information and ensure patient privacy.
Preference for user-friendly solutions that do not disrupt clinical workflows or hinder access to healthcare services.
Emphasis on compliance with healthcare industry regulations such as HIPAA (Health Insurance Portability and Accountability Act).
Desire for continuous monitoring and proactive threat detection to prevent data breaches and cyber incidents.
Technological Advancements:
Advancements in artificial intelligence (AI) and machine learning (ML) for automated threat detection and behavioral analysis.
Development of blockchain technology for secure and immutable storage of healthcare data.
Integration of endpoint detection and response (EDR) solutions for real-time threat mitigation and incident response.
Adoption of zero-trust architecture and identity and access management (IAM) solutions for enhanced security posture.
Market Competition:
Intense competition among cybersecurity vendors, consulting firms, and managed security service providers (MSSPs).
Differentiation through specialization in healthcare cybersecurity, industry expertise, and compliance knowledge.
Strategic partnerships with healthcare organizations, technology vendors, and regulatory bodies.
Focus on offering comprehensive cybersecurity solutions, including risk assessment, penetration testing, and security training.
Environmental Considerations:
Consideration of environmental impact in the development and deployment of cybersecurity solutions.
Promotion of energy-efficient and resource-efficient technologies to minimize carbon footprint.
Implementation of sustainable practices in data center operations and cloud computing infrastructure.
Compliance with environmental regulations and standards governing electronic waste disposal and recycling.
Regional Dynamics: Different regions may exhibit varying growth rates and adoption patterns influenced by factors such as consumer preferences, technological infrastructure and regulatory frameworks.
Key players in the industry include:
Cisco
IBM
FireEye
Symantec
Trend Micro
MacAfee
Intel
Kaspersky
Lockheed Martin
Northrop Grumman
The research report provides a comprehensive analysis of the Healthcare Cybersecurity Services market, offering insights into current trends, market dynamics and future prospects. It explores key factors driving growth, challenges faced by the industry, and potential opportunities for market players.
For more information and to access a complimentary sample report, visit Link to Sample Report: https://gqresearch.com/request-sample/global-healthcare-cybersecurity-services-market/
About GQ Research:
GQ Research is a company that is creating cutting edge, futuristic and informative reports in many different areas. Some of the most common areas where we generate reports are industry reports, country reports, company reports and everything in between.
Contact:
Jessica Joyal
+1 (614) 602 2897 | +919284395731 Website - https://gqresearch.com/
0 notes
Text
Rapid Surge in Botnet Detection Market: Projected Revenue of US$ 15.4 Billion by 2033
The need for sophisticated security measures has increased in response to the ever-widening danger landscape, driving the Botnet Detection Market to unprecedented heights. Recent market research indicates that the Botnet Detection Market is expected to generate a significant amount of revenue in 2023—US$ 839.4 million. With an astounding valuation of US$ 15,358.7 million by 2033 and an excellent CAGR of 33.7% over the forecast period, the market is expected to rise exponentially in the future.
The increasing digitization of sectors is making them more vulnerable to botnet assaults. The integrity of digital ecosystems is seriously threatened by these attacks, which are coordinated by networks of hacked devices. The worldwide corporate environment is adopting cutting-edge botnet detection systems to combat this threat.
Ready to Gain Knowledge? Grab Your Insights Sample! : https://www.futuremarketinsights.com/reports/sample/rep-gb-14555
Key Takeaways: Botnet Detection Market
By component, the solution segment is anticipated to account for the leading share in the global demand for botnet detection during the forecast period. However, the services segment is estimated to grow at a robust CAGR of 34.7% through 2032.
By deployment, the cloud-based segment is anticipated to grow at a CAGR of 35% between 2022 & 2032.
Among the enterprise size, large enterprises segment is anticipated to hold the largest share of the global market and is estimated to increase at a CAGR of 33% between 2022 & 2032.
By industry, the media and entertainment segment is anticipated to grow at a CAGR of 35.9% between 2022 & 2032.
North America is dominating botnet detection market followed by Europe region in 2022. South Asia & Pacific is estimated to grow at the fastest rate over the forecast period.
The market in U.S. is expected to progress at a CAGR of around 33.9% through 2032.
In India, the botnet detection market is expected to grow at a CAGR of 39.2% during the forecast period.
Botnet detection market in China is estimated to witness the absolute opportunity of US$ 955.2 Mn in the forecast period.
Competition Analysis – Regional Trends
The Botnet Detection Market is characterized by intense competition, driven by the growing importance of cybersecurity in today’s interconnected world. A noteworthy trend is the dominance of the top 5 vendors, accounting for around 45% of the market share. As cyber threats continue to evolve, these vendors are at the forefront of delivering cutting-edge solutions to counteract sophisticated botnet attacks.
Region-wise Insights
Across various regions, the demand for robust botnet detection solutions is on the rise. North America leads the charge, being an early adopter of advanced cybersecurity measures. Europe follows suit, with a keen focus on data protection regulations. Asia Pacific showcases significant potential for growth due to the rapid digitization of industries. Meanwhile, emerging economies in Latin America and the Middle East are also ramping up their cybersecurity efforts to safeguard critical digital infrastructure.
Request for Methodology:
https://www.futuremarketinsights.com/request-report-methodology/rep-gb-14555
Category-wise Insights
In the landscape of botnet detection, diverse categories of industries are seeking tailored solutions. From banking and finance to healthcare and manufacturing, every sector is recognizing the need for proactive threat mitigation. As Internet of Things (IoT) devices proliferate, securing these interconnected endpoints becomes paramount, spurring demand for botnet detection across consumer electronics, industrial automation, and smart cities.
Botnet Detection Market Outlook By Category
By Component:
Botnet Detection Solution
Services
Professional Services
Managed Services
By Deployment:
Cloud
On-premises
By Enterprise Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
By Industry:
BFSI
Healthcare
IT and Telecom
Retail
Media and Entertainment
Travel and Hospitality
Government
Others
0 notes
Text
0 notes
Text
The Role of Cybersecurity in Small Business Development
In the technological world, the internet has made businesses, either small or big expand their market to any geographical location and access the services easily. The company may opt for any kind of technology to maintain its website the need for cybersecurity is a must. The threat to digital information is always a crucial issue or a challenge that every company should have a plan to deal with. Every company or domain that makes use of the internet in their service is responsible for maintaining the security of data. This article explores the detailed knowledge of cybersecurity along with the need and benefits of it to bring growth and sustainability to small businesses.

For more visit Apac Business Times
What is Cybersecurity?
Cybersecurity is the process or the way to protect or safeguard your networks, systems, devices, data, and programs from being digitally hacked. Cyberattacks aim to completely change or modify your information by accessing them. There are several types of cybersecurity they are application security which is used in protecting software applications from cyber-attacks and threats. IoT security is the practice of protecting the flow of data between interconnected devices. Endpoint security includes the protection of end devices like laptops, computers, etc with the use of antivirus software. Network security is the process involving the protection of the usability and integrity of data and networks.
Need for Cybersecurity in small businesses
In the case of small businesses, they are not immune to cyber threats and are often targeted by attackers for unauthorized access to data. Through this, there will be an effect on ongoing processes and also harm to financial information. To maintain the trust of the customer we must provide strong security for their information so that they can enjoy the service fearlessly. Regulatory compliance is also an important part to be taken care of which cares for the protection of customer data and privacy. By following these regulations, you will not be legally safe but can build a reputed brand and gain the trust of customers. To address all these mentioned issues you need to adopt a strong and effective cybersecurity system that acts as a shield in protecting all your sensitive information.
How to implement Cybersecurity measure
For the effective implementation of cybersecurity measures, there are certain processes to be undertaken. One must give proper and accurate training on cybersecurity to the concerned employees of the organization. Human errors are common in cybersecurity but can be handled easily by best practices and maintaining strong passwords.
Regular checking and reconfirmation of the threat alerts by cybersecurity infrastructure is essential. Identifying and solving the breaches to ensure the security of the system regularly is the safer way. Along with these, the main part is the usage of the potential and secure technology including antivirus software, firewalls, and encryption tools.
Small businesses that might be limited in resources can collaborate with cybersecurity experts or external services to maintain strong can be a strategic move to growth. Also, the method of keeping the system and software updated will benefit in providing safety. The professional can use their specialization and skills to predict future threats and take precautions well before.
Cybercrimes in APAC region 2023
A significant rise in cybercrimes has been observed in the last year. Where the average number of cyberattacks faced by an organization was around 1,835 per week. There are several reasons for increased cyber-attacks in the APAC region some of them are mentioned here accelerated digital transformation, the hybrid working model, high demand in manufacturing, and rising social media trends. This also will lead to an increase in the cost of cybercrime.
Conclusion
In short, the role and importance of cybersecurity in business are inevitable due to advancements in technology and digitalization. Identifying the need for cyber protection and focusing on it will benefit the organization in safeguarding sensitive information. The data is an essential element in business for analyzing and making strategic moves and needs to be protected from unauthorized access. This will help you to thrive in a technology-driven market and build sustainable growth in your business.
Visit More : https://apacbusinesstimes.com/the-role-of-cybersecurity-in-small-business-development/
0 notes
Text
Strategic Analysis: Market Size and Share of Smart Airports in 2023
The Smart Airports Market is set for remarkable growth, with a projected expansion from USD 7.0 Billion in 2022 to USD 8.3 Billion by 2027, reflecting a robust CAGR of 3.5% over the forecast period. The market's ascent is driven by an escalating demand for advanced smart solutions, a response to the surging air-passenger footfall, showcasing a pivotal shift in the aviation industry.
Market Overview:
Strategic Growth Trajectory:
The Smart Airports Market is on a strategic trajectory, marked by a comprehensive forecast in the range of USD 7.0 Billion to USD 8.3 Billion by 2027, underlining a steady Compound Annual Growth Rate (CAGR) of 3.5% during 2022-2027. This trajectory is grounded in the increasing demand for sophisticated smart solutions, catering to the rising needs of air-passenger footfall on a global scale.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=544
Market Dynamics:
Dominance of Upgrades & Services:
The Upgrades & Service segment is anticipated to take the lead in the smart airports market during the forecast period. This surge is attributed to ongoing efforts to upgrade existing systems and solutions with advanced technologies, focusing on improving both passenger experience and operational efficiency. The market is propelled by a collective desire for enhanced maintenance and services to ensure the seamless operation of airport systems.
Endpoint Devices Steering the System Segment:
In the system segment, the Endpoint Devices category is projected to dominate market share during the forecast period. Airports worldwide are leveraging dependable endpoint devices, including biometrics, RFID, and beacons, to expedite the screening process. These advancements enhance customer experience and streamline airport operations, significantly raising security standards.
Airside Operations Taking the Lead:
Within the application segment, the airside category is slated to dominate market share during the forecast period. Smart operations at the airside, aimed at enhancing ground staff management and expediting aircraft turnaround, have witnessed substantial demand. This surge is evident in the adoption of advanced solutions such as sophisticated aircraft parking systems and cutting-edge maintenance and health monitoring.
Medium-Sized Airports Leading the Charge:
The medium-sized airport segment is positioned to lead the smart airports market during the forecast period. This leadership role is attributed to the increasing demand for the installation of advanced technologies in airports and the rising need for system modifications on a global scale.
Non-Aeronautical Operations at the Forefront:
In the operation segment, non-aeronautical operations are poised to dominate market share during the forecast period. Airports are strategically focusing on targeted digital advertising and other initiatives like inventory management and intelligent transport services to meet consumer expectations and drive the growth of the non-aeronautical segment.
Inquiry Before Buying: https://www.marketsandmarkets.com/Enquiry_Before_BuyingNew.asp?id=544
Geographical Insights:
Asia Pacific Spearheading Growth:
Asia Pacific is anticipated to account for the largest market share in 2022, with North America projected to witness the highest Compound Annual Growth Rate (CAGR) during the forecast period. The rise in air travel demand, growth in international tourism, and the advent of low-cost flights to developing nations like India are key factors fueling the surge in passenger traffic in the Asia-Pacific region. The increasing demand for automated procedures, including baggage handling and self-check-in services, is expected to support the significant expansion of smart airports in the Asia-Pacific region.
Key Market Players:
Major industry players driving the smart airports companies include SITA (Switzerland), THALES (France), Siemens AG (Germany), Amadeus IT Group SA (Spain), IBM Corporation (US), Cisco Systems Inc. (US), Indra Sistemas S.A. (Spain), Honeywell International Inc. (US), and L3Harris Technologies Inc (US). These players, with their cutting-edge solutions, play a pivotal role in shaping the market landscape and contributing to the industry's overall growth.
Get 10% Free Customization on this Report: https://www.marketsandmarkets.com/requestCustomizationNew.asp?id=544Top of Form
Top of Form
About MarketsandMarkets™
MarketsandMarkets™ has been recognized as one of America's best management consulting firms by Forbes, as per their recent report.
MarketsandMarkets™ is a blue ocean alternative in growth consulting and program management, leveraging a man-machine offering to drive supernormal growth for progressive organizations in the B2B space. We have the widest lens on emerging technologies, making us proficient in co-creating supernormal growth for clients.
The B2B economy is witnessing the emergence of $25 trillion of new revenue streams that are substituting existing revenue streams in this decade alone. We work with clients on growth programs, helping them monetize this $25 trillion opportunity through our service lines - TAM Expansion, Go-to-Market (GTM) Strategy to Execution, Market Share Gain, Account Enablement, and Thought Leadership Marketing.
Built on the 'GIVE Growth' principle, we work with several Forbes Global 2000 B2B companies - helping them stay relevant in a disruptive ecosystem. Our insights and strategies are molded by our industry experts, cutting-edge AI-powered Market Intelligence Cloud, and years of research. The KnowledgeStore™ (our Market Intelligence Cloud) integrates our research, facilitates an analysis of interconnections through a set of applications, helping clients look at the entire ecosystem and understand the revenue shifts happening in their industry.
To find out more, visit www.MarketsandMarkets™.com or follow us on Twitter, LinkedIn and Facebook.Contact:
Mr. Aashish Mehra
MarketsandMarkets™ INC.
630 Dundee Road
Suite 430
Northbrook, IL 60062
USA: +1-888-600-6441
Email: [email protected]
0 notes
Text

Middle East and Africa Endpoint Security Market size at USD 749.11 million in 2023. During the forecast period between 2024 and 2030, BlueWeave expects the Middle East and Africa Endpoint Security Market size to expand at a CAGR of 6.16% reaching a value of USD 1,072.35 million by 2030. The Endpoint Security Market in the Middle East and Africa region is propelled by the growing adoption of cloud-based security solutions among enterprises. Cybersecurity has become a paramount concern in the region, leading to consistent investments to ensure citizens' safety. Governments have implemented robust legal frameworks and are committed to updating national cybersecurity systems. The integration of technology in Saudi Arabia has surged, heightening the demand for cybersecurity solutions and consequently, an increase in cyberattacks. Governments respond with active investments in innovative solutions to identify and mitigate cyber threats to businesses. Initiatives like Dubai Internet City (DIC) and KSA Vision 2030 aim at comprehensive digitalization, fostering connectivity in sectors like smart buildings and transportation. The 2022 FIFA World Cup in Qatar raised concerns about potential cyberattacks, emphasizing the need for enhanced cybersecurity solutions. The region's increasing digitization accentuates the vital need to safeguard networks, endpoints, data, and various elements from potential cyber threats.
Opportunity - Increasing number of endpoints and BYOD trend
In the modern landscape, smartphones and tablets have become indispensable tools for individuals and organizations alike, contributing to a significant surge in endpoints, especially as employees increasingly use smartphones for work. However, this ubiquity introduces new attack vectors and data security challenges, from Trojans to viruses and beyond. Alarmingly, 96% of mobile devices lack pre-installed security software, with about 65% of vulnerabilities residing in the application layer. Mobiles, by the end of 2018, topped the list of potential gateways for infiltration and hacking attempts. The Bring Your Own Device (BYOD) era further heightens cyber risks, evidenced by a 33% increase in mobile ransomware prevalence in 2018, as per Symantec's ISTR 2019 report. Enterprises respond by increasingly adopting endpoint security solutions to fortify networks and provide secure access to confidential information, acknowledging the impact of rising mobile and wireless device use, enhanced global connectivity infrastructure, and declining mobile device costs on the Endpoint Security Market.
Impact of Escalating Geopolitical Tensions on Middle East and Africa Endpoint Security Market
Escalating geopolitical tensions, exacerbated by the Russia-Ukraine war, have significantly impacted the Middle East and Africa Endpoint Security Market. Heightened global uncertainties have led to increased demand for advanced security solutions, propelling the market's growth. The region's strategic location and geopolitical stability concerns have prompted a surge in investments to fortify critical infrastructure and enhance security. Security system integrators are witnessing a spike in demand for cutting-edge technologies, such as AI-driven surveillance and cybersecurity, as the region seeks to bolster its defense against potential threats. However, the increased geopolitical tensions also introduce challenges, including supply chain disruptions and economic uncertainties, which may affect the market's growth trajectory in the short term.
Sample Request @ https://www.blueweaveconsulting.com/report/middle-east-and-africa-endpoint-security-market/report-sample
0 notes