#Hidden Android spy app
Explore tagged Tumblr posts
Text
ONEMONITAR: India's Top Android Spy App

Discover the power of ONEMONITAR, a leading Android spy app and one of the best phone monitoring solutions in India. With advanced tracking features, real-time updates, and user-friendly controls, ONEMONITAR ensures you stay informed about your loved ones' digital activities.
Perfect for parents and employers, this trending app provides comprehensive insights into call logs, messages, GPS locations, social media interactions, and much more. Trust ONEMONITAR for reliable, discreet, and efficient phone monitoring.
Try ONEMONITAR today and stay connected, stay secure!
#Android spy app#Best Android spy app#Android spy app India#Top Android spy app#Hidden Android spy app#Android spy app download#Android spy app for parents#Android spy app for employers#Android spy app with GPS tracking#Secure Android spy app
0 notes
Text
CHYLDMONITOR Mobile Spy for Android

Get CHYLDMONITOR, the ultimate mobile spy solution tailored for Android devices. Seamlessly monitor phone activities, including call logs, messages, and app usage, all from a centralized control panel. With CHYLDMONITOR, you can ensure the safety of your children or enhance employee productivity by keeping an eye on their digital interactions. Experience top-notch Android monitoring today.
Protect and monitor effectively. Download CHYLDMONITOR for Android!
#mobile spy app#mobile spy software#mobile spy for android#mobile spy download#mobile spy without access to phone#mobile spy app hidden#mobile spy app undetectable#mobile spy parental control#mobile spy app with GPS tracking#mobile spy app features
0 notes
Text
Can a spy app be installed remotely?

The rise of the internet has surely made the world a smaller and better place. The advancement of technology to such an extent that you just have to make a few clicks to get anything was unimaginable a decade back. A huge spike in the number of internet users has been seen in just the past few years. If you look around, you can find everyone with their smartphones in their hands, engaged in some sort of content. Apart from the ability to stay connected with people, it has enabled us to run a whole business just through a smartphone.
However, like any good thing in life, this also came at a cost of being exposed to various online risks. Fortunately, these risks are totally avoidable with the use of a mobile spy app like Chyldmonitor. The app lets you monitor the online activities of your family and friends to keep them safe over the web. Not everyone out there can be educated about the risks involved and how not to fall for it. The whole process of creating awareness around the hazards of the internet is neither realistic nor doable. Therefore, using an spy app for android is the best solution one can opt for.
Making yourself aware of the risks and how to deal with them, can really help your loved ones to browse safely. However, the biggest question that people get when it comes to spy apps is whether they can be remotely installed or not.
The answer is no. But the good news is that you need access to their phone for about 5 - 7 minutes only for the whole process to complete. This should be very doable for anyone who wants to spy on someone for their sake. You can ask to use the targeted phone for a while, and before they know it, you’ll be able to set up the whole thing.
Beneficial Features Provided by the Chyldmonitor App
The app is offering more than 60+ features to their users all over the world. With this app in your toolbag, you get to fully monitor the target phone. Not a single aspect which could prove to be harmful for your family is spared by the app. The app comes packed with features like call recordings, location tracking, access to chats, ambience sound recording, etc.
The app also has a hidden call recorder feature available to record every call taking place on the targeted phone. With its unique feature of remaining hidden from the app drawer, there’s no way anyone can know if they’re being spied on.
Apart from this, one also gets the option to track location of the intended device. Majority of the scams these days are taking place over the most used communication platforms. This is where WhatsApp Spy feature can help you to maintain the security of your loved ones. Frem the recordings of the calls made over WhatsApp, to the media shared, everything can be accessed from the web portal once you login to your account.
Install a Spy App in Your Phone This Easily
Many people think that installing a spyware application on the intended device must be a complicated process. The word ‘rooting’ or ‘jailbreaking’ comes to their mind when they think about it. However, with Chyldmonitor application, you are not required to root your device to get advanced permissions. The app is fully functional on any android device.
Once you have managed to get a hold of the targeted device, the installation process will only take you about 7 minutes at most. If you face any trouble while installing the app, their customer service is available 24x7.
You can be guided through the installation process over the call or the agent might take remote access to your device, to perform the installation on your behalf. It has gotten way easier than ever to spy on your family and friends to keep them protected over the internet. However, no ethical boundaries should be crossed in the process. The consent is the crucial thing to make sure that your relationship doesn’t get affected with the intended person on whom you want to spy on.
The arrival of spy apps have revolutionized the way in which we deal with the online threats. Monitoring the online activities of your loved ones is the only reasonable way today to ensure their safety online.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
2 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] MSTECH HD 1080P Video live view & 120° Wide Angle Lens: With 120 degree wide angle lens, the mini spy camera allows you to see more details happening in the room. The quality lens also features 1080P video and pictures that perfect surveillance camera for your Office or business place. 24/7 Home Security in Your Hands: Whenever you're using a smartphone/ tablet/ computer device, you can view the HD live streaming by HD PLUS hidden cameras. Multi-User & Multi-View: One camera can support multiple users and one app can support multiple cameras simultaneous so you can check up on your property in real-time. Compatible with iOS, Android, Mac and Windows devices. Multi Use: You can put this mini camera in your home, office, warehouse, store, garden. It can also be used as a car camcorder, aerial action camera, pet camera, cop camera. Specifications: Function: Support WiFi, Video, Camera, Loop Recording, Motion Detection, Infrared Night Vision, Time Display. Resolution: 1080P/720P Video Format: AVI Picture Format: JPEG Frame Number: 30fps Visual Angle: 120 degree Recording Range: 5 m2 Compressed Format: H.264 Recording Time: Over 1 hour Charging Time: 1.5 hours Voltage input: DC 5V 1A Interface: MICRO USB Interface Package Includes: 1x Mini Camera 1x Bracket 1x Iron Sheets 1x USB Charging Cables 1x Mini USB Charging Cable 1x Instruction. Batteries : 1 Lithium Polymer batteries required. (included) Product Dimensions : 3 x 2 x 2 cm; 25 g Date First Available : 31 March 2023 Manufacturer : MSTECH ASIN : B0C14PB681 Item model number : MS-WIFI-Magnet-Camera Country of Origin : China Manufacturer : MSTECH, MSTECH Packer : MSTECH Importer : MSTECH Item Weight : 25 g Item Dimensions LxWxH : 30 x 20 x 20 Millimeters Net Quantity : 1.00 count Included Components : 1x Mini Camera 1x USB Charging Cables 1x Generic Name
: Hd Wifi Camera MSTECH : As A mini WIFI Camera, It built-in 250mah battery, fully charged, can work about 1 Hours , Also you can get the camera plugged into a USB charger (or power bank) for recording 24/7 hours. With Wifi connectivity to room's 2.4GHz router, you can watch live video feed or playbacks no matter where you are by accessing the APP. MSTECH : The wireless hidden camera will send push notification with images to your phone once motion is detected. You can log into the App to see what’s going on in real time and never worry about missing something important. This hidden spy cam automatically records and overwrites the oldest SD card files when full for continuous recording. MSTECH : One camera can support multiple users and one app can support multiple cameras simultaneously. This spy camera features hotspots so it can record without Wi-Fi too: just insert a SD card (not included) and turn on, the mini WiFi camera will auto record HD video files to sd card; It can also record videos even if the network is offline. MSTECH : Built-in 6 infrared lights for a clear display in low light condition(No-Glow in use), the light working distance reach to 5m which makes it perfect as a home security camera or a housekeeper/ nanny cam for recording both snapshot picture and videos without attracting any attention. With the internal magnet, Upgraded hidden camera can be adsorbed on any iron surfaces easily. MSTECH : HD plus small mini cam records video in exceptional 1920X1080P HD at 30 frames per second. Function with video, picture, loop recording, motion detective, infrared night vision, time display, magnetic, etc.120° wide angle view that can monitor anywhere in standard distance. Battery Backup After Full Charger 50 to 60 Minutes [ad_2]
0 notes
Video
youtube
Hidden Android App Installed Without Permission! Is Google Spying on You?
0 notes
Text
Hidden Android App Installed Without Permission! Is Google Spying on You?
youtube
0 notes
Text
How to Track My Wife's Phone without Her Knowing 2020 Is your wife being unfaithful? You think so, but you aren’t sure. You’re thinking of tracking your wife’s phone without her knowing to gather irrefutable proof. We aren’t here to judge. When the people closest to you betray you, all bets are off, and you deserve to know the truth. We’ll show you how to track your wife’s phone without her knowing in 2020. Our software-based spy solution requires no technical skills. You can have it up and running in minutes. Best of all, it’s discreet. You could also hire a private eye to tail her around, but that’s an expensive option and perhaps the last resort. The spy solution we have will do the trick 9 times out of 10. Part 1: Is it Possible to Track My Wife's Phone? Yes, it’s possible to track your wife’s phone – without her knowing. The only long-term, accessible way to do so is using a spy app. These utilities are designed to track everything happening on a phone invisibly. Keep in mind that in the US, it’s not legal to spy on your spouse’s phone without her permission. Of course, that doesn’t stop millions of people from doing it. For other countries, the rules vary. Part 2: How to Track Your Wife's Phone without Her Knowing A specialized spy app can record your wife’s phone activities and share the details with you over the internet. The best spy apps are also impossible to detect, meaning your wife will never figure out you’re there. Which spy app should you choose? While there are many excellent apps out there, we suggest Safespy. This is a well-known, user-vetted solution that’s affordable, effective, and straightforward to use. 2.1 Safespy – A Top-Tier Spy App Safespy is a top-rated phone monitoring solution for iOS and Android. It’s been featured by major platforms online like the New York Times, TechCrunch, and Mashable, and it has been downloaded over a million times to date. With Safespy, you can find if your wife is cheating on you from your web browser. It’s easy to set up, not to mention well -hidden. We’ll explain how Safespy works and how to get it set up below. 2.2 How Safespy Works Safespy has a web-based interface. That means you can access tracking data from any web browser, via any device. You get periodic tracking updates delivered straight to the interface. You just need to install the app first. How does the stealth mode work? It’s different depending on the target operating system. If your wife’s phone is on Android, then you will need to download and install an app on her device. This takes only 5 minutes. Afterward, you can hide the app. You never have to touch her device again. The Android version of Safespy runs invisibly in the background on your wife’s phone. It shares data with you over the internet. It has no visible process or app icon, nor does it drain the battery. The app is also small at
0 notes
Text
Discover how the best spy app for Android helps protect children, elders, and loved ones with advanced monitoring features. Learn about top spyware for Android and hidden spy apps.
1 note
·
View note
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product description Features: -1080P Full HD Brings You A Different Experience. -This nanny cams can work on WiFi (2.4 GHz WiFi only) or No WiFi. When it works on No WiFi, insert a Micro SD card(SD card not include) and turn on, the spy camera will recording and saves the video files to the Micro SD card(SD card not include). - Night vision & motion detection & alarm push. -This tiny spy camera has built in magnet, can work well with any iron material, easily hidden anywhere. This tiny hidden camera with a rigid charging cable and magic base, when charging while recording, you can manually rotate the recording angle 360 degrees. Simple to Set up & Use: -2.4 GHz router Wi-Fi network only. Requires Android/iOS smartphones with the free mini camera app to configure Wi-Fi. -This mini spy camera can records without Wi-Fi too.insert a sd card and turn on. spy camera will start recording and saves the video files to sd card. -Wi-Fi cameras are security cameras that send audio and video signals to a receiver using a radio band. These security cameras have own wifi hotspot,mobile phone can watch the live streaming in a place without WiFi. Package Include: 1 x Mini Hidden Camera 1 x USB Cable 1 x Manual Book 1 x Holder Stand Batteries : 1 Lithium Ion batteries required. (included) Product Dimensions : 14 x 4 x 8 cm; 30 g Date First Available : 7 April 2021 Manufacturer : CAMLEIGH ASIN : B0C72G47ZZ Item model number : CAM-MINI-BALL Country of Origin : China Manufacturer : CAMLEIGH Item Weight : 30 g Item Dimensions LxWxH : 14 x 4 x 8 Centimeters Net Quantity : 1.00 count Included Components : 1 BALL SPY CAMERA X 2 WIRES X 1 STAND Excellent Live Stream Nanny Cam: Support up to 128 GB micro SD card and equipped with Flexible Semi Rigid USB Cable, which can get the camera stand easily. You can also maneuver the cam at any angles or position by the cable as you need. 2.4 GHz router Wi-Fi network only. Requires Android/iOS smartphones with the free mini camera app to configure Wi-F. This mini spy camera can records without Wi-Fi too.insert a sd card and turn on. spy camera will start recording and saves the video files to sd card.
Upgraded HD 1080P WiFi Spy Camera : This WiFi hidden camera is the latest model with Built-in strong Magnet, 81° Wide Angle and 1080P Live Video, which makes it perfect as a home security camera or car DVR video recorder without attracting any attention. [Longer Battery Life] This mini camera comes with a high-quality 300mAh rechargeable lithium-ion battery that can last continuous HD video recording about 1 hour. Besides, you can charge this wireless wifi hidden spy camera with the included charging cable to keep using this spy camera. Spy Camera Wireless Hidden_ Keep Watch of Home Security Every Corner. This Hidden Cameras For you [ad_2]
0 notes
Text
The World of Social Media Hacking: Unveiling the Secrets

Currently, social media is the main part of communication, and it’s become a part of our lives. Facebook, Instagram, WhatsApp, and Snapchat platforms have billions of users. Those platforms are the vendors of information. Social media hackers have huge demands, especially those who want to hack and uncover their activities. In this blog, we will discuss how to hack social media. And introducing to you the world’s best social media hacker, HackersList
Understanding Social Media Hacking
Social media hacking is accessing someone else’s social media. And this can be done to monitor someone’s activities and uncover secrets. These common social media hackers leave no traces on the platforms and possess sophisticated techniques.
How to Hack Facebook
The main target of hackers is to hack Facebook because Facebook is a popular social media. And to hack this Facebook, a hacker uses different techniques:
Phishing: It creates a login page that looks similar to Facebook. When the target logs in through this page, the hackers capture the login information.
Keylogging: Hackers can easily capture their login information by installing keylogger on targeted devices.
Social Engineering: This technique forces the target to reveal passwords or sensitive information through psychological means.
How to Hack Instagram
Instagram is one of the platforms used by the youth here. And there are some simple methods to hack this instagram:
Brute Force Attack: This method is mainly used for weak passwords. It helps in hashing out weak passwords
Password Reset Exploit: With this method, the reset link sent to the target’s email is blocked. By exploiting this reset link, a hacker can access the target’s Instagram
Third-Party Tools: Some hackers use other tools or third-party tools to hack Instagram accounts that require deep understanding of coding and network members.
How to Hack WhatsApp
WhatsApp is a popular messaging app these days, despite its many security features, hackers have found ways to break into it.
Spyware: Spyware is installed on the target’s phone to monitor all of the target’s media file messages
MAC Spoofing: Through this method, the MAC address of the target’s device is matched with the MAC address of the hackers’ device. So that hackers can access the WhatsApp account very easily
QR Code Scanning: Hackers use this method to create a fake QR code. And by scanning this fake QR code target can access WhatsApp
📌 Read Also: WhatsApp Spy Online Tracker App for Android and iPhone
How to Hack Snapchat
One of the most popular messaging platforms is Snapchat. And its special feature is invisible messages. And here are some methods to hack snap chat
Phishing: It creates a fake login page just like Facebook. The login page looks like the snap chat login page. With which hackers can capture the login information by the target.
Packet Sniffing: This allows hackers to access all data sent over the network. This is a means of Snapset hacking.
Credential Stuffing: When the target uses the same password on multiple platforms. Then it becomes very easy for hackers to hack the target platform through this method.
Meet the World’s Best Social Media Hacker: HackersList
Hackerlist is the best when we talk about a skilled experienced and professional hacker team. We can take the help of HackerList when we need to find out any information hidden in a target’s activity messages on various social media platforms. Because they have a customer service system and sense of responsibility and hackers on HackersList do these things very efficiently. And they do it with complete client confidentiality.
Why Choose HackersList?
Expertise: Because they have all the hackers and who are very skilled and talented they do the client’s work very carefully
Discreet Services: Client privacy is Hacker List’s main goal and it is their top priority. They ensure that all activities are done very confidentially and they leave no traces
Comprehensive Solutions: HackersList They try hard as long as your work is done with privacy. And try to hand it over to you quickly after completing the work.
Reliability: HackerList can be a reliable choice for those looking for all hackers and professional hackers with proven track record of hacking. Click here
Conclusion
Finally we want to say that when you are looking for a skilled Facebook Hacker, Instagram Hacker, WhatsApp Hacker, Snapchat Hacker, HackerList can be the best choice for you. Because they have the best customer service, the best skilled hackers, and they prioritize client privacy.
0 notes
Text
Zero Click Malware: The Invisible Digital Threat – How to Recognize and Defend Yourself

Estimated reading time: 6 minutes
What is Zero Click Malware
Zero click malware, also known as non-click malware or in-memory malware, is a new type of malware that can infect a device without the user taking any action. Unlike traditional malware that requires the user to click on a link or open an infected attachment, zero click malware is able to install itself on the victim's device completely silently and invisibly, without any interaction on their part.
How Zero Click Malware Works
This type of malware exploits various vulnerabilities in software and operating systems to gain access to the device. Some common infection vectors include: - Zero-day vulnerabilities not yet patched - Bugs in web browsers and messaging apps - Packet sniffers that intercept network traffic - Insecure public WiFi networks - Websites compromised with drive-by exploits Once initial access is gained, zero click malware uses advanced techniques to keep itself hidden and avoid detection. It can disable antivirus software, hide in RAM memory, encrypt communications, and much more.
Why Zero Click Malware is Dangerous
The completely stealth nature of this malware makes it extremely insidious and difficult to identify. Even the most security-conscious users can be infected without knowing it. This allows hackers to: - Monitor all activities performed on the infected endpoint - Collect sensitive data such as credentials, personal information, browser history - Collect sensitive data such as credentials, personal information, browser history - Move laterally within the network to infect other systems - Use the device for ransomware or denial of service attacks Furthermore, since no clicks or actions are required, zero click malware can spread very quickly, affecting a large number of victims.
Case Studies and Technical Analysis

Some real-world cases have recently emerged that illustrate the capabilities of this new category of cyber threats. One of the first zero click exploits to gain attention was Pegasus, developed by cybersecurity firm NSO Group. Used by some governments to spy on journalists and activists, Pegasus exploits zero-day vulnerabilities in iOS and Android to install itself without any user interaction. Another famous case is ForcedEntry, used to hack the iPhones of several employees in Bahrain. ForcedEntry exploits a vulnerability in iMessage to install spyware without clicking on Apple devices. These and other cases demonstrate the severity of the threat and the need for advanced protection solutions capable of detecting and preventing zero-click attacks.
How to Detect and Prevent Zero Click Attacks
Since this type of threat leaves no visible traces, identifying and stopping them requires targeted strategies: - Patching and updates - Always apply the latest security updates to fix known vulnerabilities - EDR Solutions - Endpoint detection and response technologies that analyze memory-based threats and anomalous behavior - Advanced web protection - Secure web gateways capable of inspecting all traffic entering and leaving the network - Network Segmentation - Limit the ability of malware to move laterally by isolating and segmenting critical systems - Strong Authentication - Enable multi-factor authentication to prevent targeted phishing attacks that often precede zero-clicks - Awareness Training - Instruct users to recognize and report suspicious activity that may indicate an infection A layered approach that integrates multiple technologies and policies is essential to defend against this ever-evolving threat.
Increase Prevention with Deception Solutions
One of the most effective strategies against zero-click malware is the use of deception solutions. These solutions create a seemingly attractive environment for malware, but in reality they are traps that detect and isolate threats before they can cause damage. By taking a multi-stage approach to defense, you can dynamically respond to threats as they evolve, defeating attackers with their own techniques.
Continuous Testing and Threat Simulations
Attack simulations and continuous testing of security controls are another key pillar in zero-click malware defense. Services like Posture Guard help organizations verify their security posture by leveraging a vast database of threats, including malware, ransomware, and Advanced Persistent Threats (APTs). These tests help you evaluate the effectiveness of your security tools and optimize your threat prevention and detection capabilities.
Cyber Threat Hunting and Threat Intelligence
Cyber Threat Hunting is crucial to proactively identify threats and sensitive information that may have been compromised. Having a team of experts dedicated to this activity allows you to quickly recover stolen information and organize a more targeted defense. Combined with continuous vulnerability analysis and incident response, this strategy offers significantly improved protection against zero-click attacks.
User training and awareness
While zero-click malware does not require user interaction for infection, a well-informed and aware workforce can still play a crucial role in preventing other types of cyber attacks. Training users on good cybersecurity practices can reduce the risk of malware infections and increase overall security.
Adopt a Dynamic Approach to Security
Taking a dynamic approach to security is essential. Solutions like Active Defense Deception work to respond to attacks during the initial stages, using dynamic techniques to prevent attacks from reaching execution and more advanced stages. This type of proactive defense can deter attackers and make the environment less attractive for malware.
Forecasts and Future Developments
Experts predict that zero-click malware attacks will become one of the most used techniques by hackers in the years to come. As user awareness of malware and phishing grows, cybercriminals will look for new invisible vectors to deliver malicious payloads. Additionally, the continued rise of IoT devices and smart home technologies presents attackers with an ever-increasing number of potential weak and unpatched targets. Operating environments such as 5G and edge computing could also facilitate the spread of zero-click threats. To counter these trends, companies and security vendors will need to invest more in threat intelligence, bug bounties, sandboxing and machine learning-based threat detection techniques. Only in this way will it be possible to unmask the rapidly evolving zero-click attacks in no time.
Conclusions
Clickless malware is emerging as one of the most stealthy and dangerous tactics of modern hackers. Its ability to bypass any human interaction to infect entire systems represents a critical challenge for the world of cybersecurity. To protect individuals and companies from this threat, it is essential to adopt preventive measures at multiple levels, from patching to network monitoring to training. Only by combining awareness and advanced technological solutions will it be possible to combat the phenomenon of zero-click attacks and maintain data integrity and security in the future. - Your virtual machine with Cloud Server Read the full article
0 notes
Text
Hidden Android App Installed Without Permission! Is Google Spying on You?
youtube
0 notes
Text
The Positive Side of Spy Phone App
Ever since the spy apps have been introduced, they have been a controversial topic of discussion for various reasons, from safety concerns to privacy point of view there has been a lot of chatter around these spyware but how there is a positive side to those apps is often overlooked. Yes, these apps also have a positive side and can be used other than just being a source of spying on others.
Before we dive into the positive side of these mobile spy apps, it is important to understand what they are and how they work. It software installed on the device which you want to monitor. You can use these apps to spy on your child’s online activities, employees’ productivity during the office hours, and in some cases, the legal authorities also use them to catch the culprits.
What Main Advantages of Spy Apps
It is their ability to create a safe and secure environment for people in the online world. There are many threats involved when we go online such as cyberbullying, online predators, different types of scams and frauds. Using spy apps can provide the individuals and businesses the peace of mind they deserve. By spying on your child, you can keep a close eye on what type of content they are exposed to. Likewise, with the businesses, by keeping a track of your employees, you can be sure that they are using their working hours wisely. These apps can also be of great help in emergency situations.
Talking about the apps from employers’ point of view, the rise of work from home and company-owned devices, it is important that employers monitor their employees and their activities during the working hours. The mobile spy apps can help you in preventing the breaching of data and ensuring that employees are using the devices only for work-related tasks.
For legal authorities also, these spyware tools have proven to be effective as there are many features offered by these apps that can help the officials to catch the culprits. With the hidden call recorder, they can listen to the phone conversations and simultaneously with the in-built live-location tracker, they can detect the current location of the suspect.
Another benefit of spyware is for personal use and safety. In case you are away from your family then you can install the application on your phone and give its access to your family member so that they can monitor you and be sure that you are safe. Another way you can benefit from spy apps is that in case you lose your phone or in a worst case scenario, if your phone gets stolen then with the location tracking enabled on your phone, you can find it. This way, you will not lose your important data stored on your phone and also you won’t need to invest in a new phone.
Which Spy App to Choose for Android Phone ?
While there are many apps available on the internet today, there are majorly two categories; free and paid. The free apps are less secure and offer less features while the paid spy apps are more secure and offer more features. We personally recommend using apps so that you can spy on your target completely. The paid apps offer multiple features that help you monitor everything they do on their android devices.
If you are looking for a reliable and trustworthy paid spy app then ONEMONITAR is surely here to end your search. The spying tool offers more than 60 amazing features that are compatible with all android devices and work efficiently. These features include hidden call recorder, WhatsApp spy, other social media monitoring tools like Instagram spy, Snapchat spy, etc., live-location tracking, and ambient sound recorder.
Another factor to choose this app is because it is designed and developed in India and has its own secure server where the users’ data is stored and the confidentiality and security of the data is ensured by the spyware as there is no third party involved to avoid any breach of privacy. Additionally, the experts at ONEMONITAR also cannot access your control panel as the spy phone app very-well understands that the data fetched from the target device can contain sensitive information, keeping this in mind, the ONEMONITAR team does not have access to this information to maintain the confidentiality of your private data.
Conclusion
Our concluding thoughts are that while there has been a negative buzz around the spy apps, they also have a positive side that should not be overlooked. If used wisely, these spyware tools can enhance safety and security of your loved ones and also build trust in relationships with also a pinch of open communication with your loved ones to work towards betterment of the relationship. Also, not to forget the positive impact it has on businesses by accurately tracking the activities of the employees to maintain productivity during the office hours. https://www.linkedin.com/pulse/positive-side-spy-phone-app-spy-app-reviews-67jxc/
1 note
·
View note
Text
Part of me agrees with you, because this is obviously largely motivated by hatred of China, which both our political parties have been fomenting for decades now.
On the other hand, though:
The US government (by way of the CIA and NSA) has already compromised both Android and iOS. (And also all the defunct mobile OSes like Windows Mobile and Symbian.) This has been known for quite some time — there were leaks about it back in the Obama administration.
Since the US has done it, it is basically guaranteed that the Chinese also have done it. (Quite aside from everything else, they’re the ones actually building the devices; Foxconn all by itself works on a majority of Android devices and all iPhones. You can assume they have access to all the technical data.)
It is frankly totally implausible that both Android and iOS are completely secure, and neither one has any way for an installed application to achieve administrative privileges and take over the phone, bypassing the security protections. Of course, it’s possible that nobody will ever discover such a flaw until after it ceases to be in any current device, but it’s staggeringly unlikely that no flaws even exist. Hackers discover such things on a fairly regular basis, and they can be ridiculously convoluted and therefore hard to find.
If such a flaw exists and is known by anyone anywhere, then the Chinese almost certainly know about it. (And even if it is actually necessary to have hardware access to compromise a phone… well, don’t forget that nearly all these devices are passing through Chinese factories at some point in their production, and having their initial state set during those processes, and it is highly unlikely that any but the initial batch are given rigorous testing by the designers. It would be difficult to introduce a subtle, hard-to-detect edge for hackers into later batches by way of manufacturing, but certainly not impossible.)
And it is, furthermore, implausible that if anybody who was sufficiently tech-savvy to know about such a flaw would not also be sufficiently tech-savvy to be able to hide it from the level of auditing that apps get, which has been demonstrated to be remarkably superficial. Google barely gives apps any auditing at all (which is why nearly all the malware for mobile devices is on Android, and has been practically since Android came out), and although Apple’s audits are marginally better, that’s an unbelievably low bar to clear and they don’t deserve much credit for beating somebody who isn’t even trying. Apple has repeatedly approved apps which had hidden functionality which is forbidden in the app store (like game console emulators). Generally apps with hidden functions only get banned after somebody has figured out how to trigger those functions and made the information public, and if there’s an app with a hidden malicious payload that hasn’t gone off yet, obviously nobody at Google or Apple knows about it for the moment because so far nobody has triggered it.
The US’ security boffins are probably worried about spying-on-US-officials stuff as well, but I promise you that they’re also worried that built into the TikTok app somewhere, in a way too subtle to detect until it’s put into action, is a switch that the Chinese government can flip remotely which would turn most TikTok users’ phones into walking DDoS vectors, or exploit other known security flaws to actually hack devices on their local networks and crash them, or just jam up the phone system in a designated exchange by sending thousands of calls to a short list of phone numbers, any of which actions would be tremendously useful in the event that the war with China which the US government keeps hoping to ginger up actually takes place. (Just being able to make a single device on a secure military network start sending noise onto the local network at the right time would be a tremendously useful capability.)
(And now: ask yourself whether the US government also has something like this up their sleeves. Don’t forget the history of Stuxnet. If the NSA is worried that China has a doomsday plan involving remote control of smartphones, it’s because they almost certainly have one themselves.)
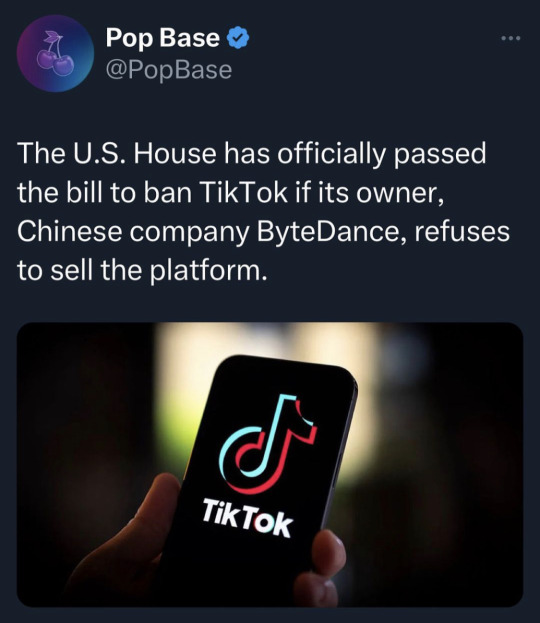
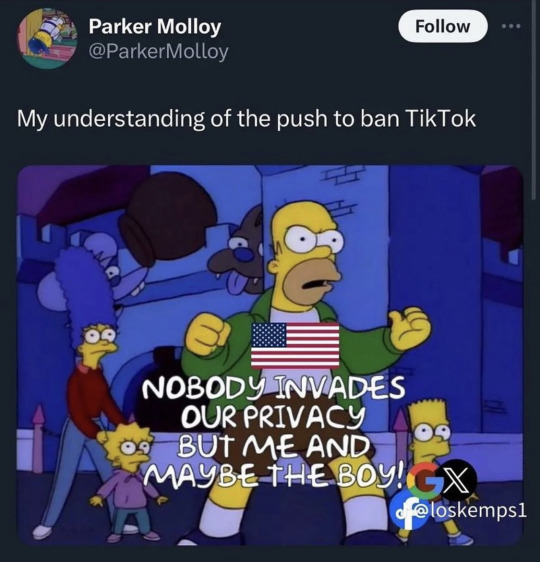

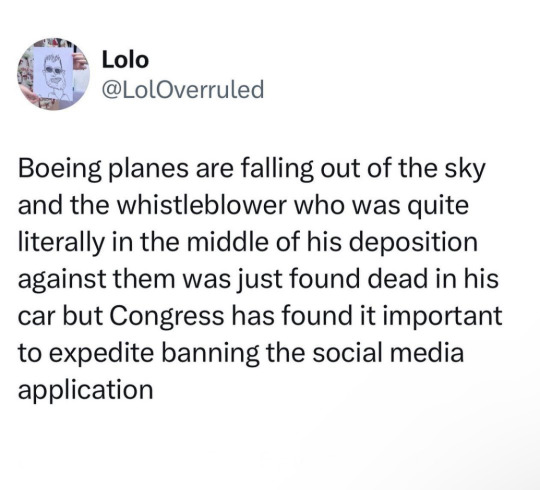
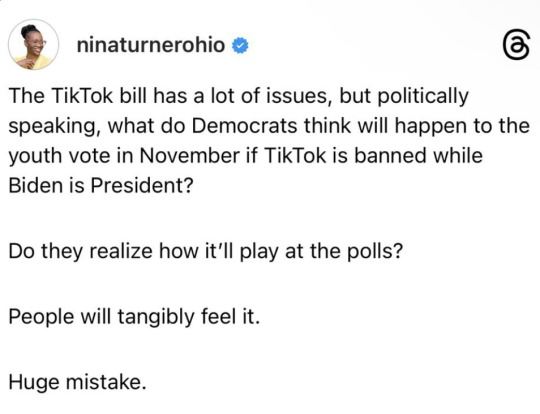
7K notes
·
View notes