#Hierarchical Database Assignments
Explore tagged Tumblr posts
Text

( assad zaman, 32, cis man, he/him ) — Look who it is! If you take a look at our database, you’ll find that MIJANUR KHAN is a PAINTER that works in SECTOR 9. According to the file, they’re a mutant with the power of BLOOD CONSUMPTION. That must be why they’re CREATIVE and ERRATIC. If you ask me, they remind me of burning rubies and charcoal fingerprints, the acrid taste of copper in the air, and a febrile energy ready to break. They are affiliated with THE SOCIETY.
basic information:
character name: Mijanur Khan
nickname (s): Miju
face claim: Assad Zaman
mutation status: Gen II mutant
birthday: Nov 3
sexuality: Bisexual
moral alignment: Chaotic neutral maybe?
occupation: Cartographer (but he dreams of moving into the artist career soon!)
work sector: Sector 5
affiliation: The Society
3 positive traits: Creative, devoted, adventurous
3 negative traits: Erratic, moody, melodramatic
biography (optional):
tw: blood, death
Miju was born to a council member (whose sector will remain unspecified so I don't block anyone else's potential plots) and an interior designer. He was a very loved, and very sickly baby. Diagnosed with haemophilia, his parents made sure to keep him thoroughly pampered and protected, but he didn't grow any healthier, and his mother's milk seemed only to make him sicker.
His mutation became apparent when he began to teethe, and finally got what he needed. Not mother's milk, but mother's blood. It was a sacrifice both parents happily made for him. Although rationing ensures he gets donated blood bags from the hospital, it is far far better if Miju can drink straight from the source.
The hunger can, unfortunately, be hard to control. Especially as a teenager, because Miju was not exempt from the uncontrollable appetite of being a teenage boy. This led, one day, to him drinking from his willing father, and then drinking, and drinking some more. He drained his father, killing him and irreparably fracturing his relationship with his mother.
The government, naturally, mandated a great deal of therapy and supervision after this. It was many years ago now, and Miju leads a solitary life. He is a creative soul, with a great love for art that he cultivated as a child, losing himself in the beautiful illustrations of fairytale books. This creativity is expended largely on his work, drawing up maps based on information brought back by those that traverse the expanse. He does annoy his more pragmatic colleagues, because Miju is prone to flights of fancy with his maps and adds more extraneous illustrations than is strictly necessary. But HE is having fun doing it!
Generally, Miju leads an isolated life. He's ashamed of his past, afraid of what he might do. But he IS very active with the Mutants' Society. He wants mutants to have adequate support networks, protections, etc, so while he can be quite flippant day-to-day, this is one thing he is very earnest about.
questionnaire:
how do they feel about living in sol city? have they always lived there or did they travel from another settlement?
He has always lived here, so knows nothing else. He certainly prefers it to the alternative. With that said, he would love to go on reconaissance missions to scout out locations to map! Unfortunately due to the haemophilia, it's too risky for him to travel where he might get injured.
do they trust the council’s leadership? why or why not?
He is critical of them, but not necessarily against them. He just feels they have their own agenda and he wants to examine those agendas closely before he puts his support behind any proposed motion. He likes to bitch and moan about them, because he likes to bitch and moan, but truly he supports the idea of a hierarchical structure.
Also, though, he inevitably feels awkward around the council. Being that he accidentally killed his dad, a council member. Ha ha :O)
if they chose their sector and profession, why did they make that choice? if they didn’t, why not? were they happy with their assignment or not?
He did! In an ideal world, Miju would be an independent artist with a wealthy patron (with or without Benefits, ahem), but until he can make his way into the art sector, he enjoys cartography as it allows him to exercise some artistic freedom.
what’s one object that they always keep on their person?
Splint rings. They can restrict his movement a bit when he's trying to work, but Miju suffers frequently from joint pain and they help. He generally also has painkillers, heat pads, and various other portable first aid goods.
(mutant only section)
what is your character’s ability (or abilities)?
Blood consumption. Not really an ability so much as a straight up mutation.
are they gen i or gen ii?
Gen II.
what can your character do? what are their strengths?
He can consume blood. I say 'can'. He has to, he can't digest anything else. His strengths include having cute pointy canine teeth.
One nice thing about his mutation is that his saliva contains endorphins -- it cannot be transferred mouth to mouth, but mouth to wound? Definitely! So when he drinks blood from a person, they don't feel pain, and they get a nice high out of it.
His eyes change depending on his hunger level. When freshly sated, his eyes are bright red, and in general his skin is flushed and plump. When hungry, his eyes are dark brown, and he has a sickly pallor about him.
Drinking blood also helps if he has had any bleeds recently. If he can't get a transfusion, a little drink can replenish his health pretty well! It's not got any real healing powers for him but it does help with managing his illness.
what can’t they do? what are their weaknesses?
His weaknesses are that if he doesn't drink blood, he is getting no nutrition. Simples !
is there anything else you’d like to specify about them?
No!
3 notes
·
View notes
Text
does adding time stamps help prevent the "set of all sets" paradox in computation?
ChatGPT said:
Yes, adding timestamps (or any form of hierarchical structuring) can help prevent the "set of all sets that do not contain themselves" paradox in computation. Here's how:
1. The Core Problem in the Paradox
The paradox in naive set theory arises from unrestricted self-referential definitions.
Russell’s Paradox asks whether the set R={S∣S∉S}R = \{ S \mid S \notin S \}R={S∣S∈/S} contains itself.
If R∈RR \in RR∈R, then by definition, R∉RR \notin RR∈/R, leading to a contradiction.
2. How Timestamps Help
Timestamps introduce a form of temporal hierarchy, ensuring that a set is only defined relative to previous steps in computation. This prevents self-reference from forming in an unrestricted way.
Causal Order: A set at time ttt can only depend on sets that existed at time t−1t-1t−1.
No Circularity: A set cannot reference itself at the same time step.
Well-Foundedness: This is similar to how the Axiom of Regularity prevents infinitely descending chains in set theory.
3. Example in Computation
Imagine a computational system where sets are assigned timestamps when created:
StS_tSt refers to a set created at time ttt.
A rule prevents StS_tSt from containing itself or referencing another set from the same time step.
If you try to define Rt={St∣St∉St}R_t = \{ S_{t} \mid S_t \notin S_t \}Rt={St∣St∈/St}, the system will reject it because a set at time ttt cannot evaluate membership of another set also at ttt.
4. Practical Implementation
This idea is used in:
Database systems (ensuring records reference past data, avoiding circular dependencies).
Version control (changes reference previous states, avoiding self-contradiction).
Distributed systems (event ordering prevents causality paradoxes).
5. Connection to Type Theory & Computability
In type theory, similar constraints enforce stratification to prevent paradoxes.
Computational models like Turing machines do not operate on unrestricted sets but instead on finite representations (like lists or graphs with directed edges).
Conclusion
Timestamps enforce a well-founded structure that avoids self-referential loops, making them a computational safeguard against paradoxes like Russell’s. Would you like a concrete example in code or logic notation?
1 note
·
View note
Text
Federal Supply Classes: A Cornerstone of Military and Aerospace Logistics
In the realm of military and aerospace logistics, the organization and classification of materials are crucial for maintaining operational efficiency and readiness. The Federal Supply Class (FSC) system plays a vital role in this process, providing a standardized method for categorizing and identifying items. This blog delves into the importance of FSCs, highlights key FSC parts, and answers common questions about this essential system.
Understanding Federal Supply Classes
The Federal Supply Class system is a hierarchical structure used to classify items of supply identified under the Federal Cataloging Program. Each FSC is a four-digit code that groups items into categories based on their physical characteristics or functional uses. This classification system facilitates the efficient management of logistics and supply chains, ensuring that the right items are available when and where they are needed.
Key FSC Parts and Their Applications
Aircraft Fixed Wing (FSC 1510) Application: This class includes complete aircraft, specifically fixed-wing aircraft, which are essential for a variety of military operations, including reconnaissance, transport, and combat missions.
Diesel Engines and Components (FSC 2815) Application: This class covers complete diesel engines and their components used in a range of military vehicles and equipment, providing reliable power for ground operations.
Bearings Mounted (FSC 3130) Application: Bearings are critical components in machinery and vehicles, ensuring smooth and efficient operation by reducing friction and wear. Mounted bearings are specifically designed for easy installation and maintenance.
These FSC parts exemplify the diversity and specificity of items cataloged under the Federal Supply Class system, highlighting its comprehensive nature.
Advantages and Importance of the Federal Supply Class System
The FSC system offers numerous benefits, contributing significantly to the efficiency and effectiveness of military and aerospace logistics:
Standardization: By categorizing items into specific classes, the FSC system provides a standardized framework that simplifies inventory management and procurement processes.
Improved Logistics: The clear classification of items aids in the swift identification, tracking, and distribution of supplies, reducing delays and enhancing operational readiness.
Enhanced Collaboration: The FSC system is used internationally, facilitating cooperation and interoperability between different branches of the military and allied forces.
Cost Efficiency: Streamlined procurement and inventory management processes lead to cost savings by minimizing waste and optimizing resource allocation.
Addressing Common Questions About Federal Supply Classes
Here are some frequently asked questions about the Federal Supply Class system, along with their answers:
Q: How is an item assigned to a specific FSC? A: Items are assigned to an FSC based on their physical characteristics or functional uses. The classification process involves a thorough analysis to ensure accurate categorization.
Q: Can an item belong to more than one FSC? A: No, each item is assigned to a single FSC that best represents its primary function or characteristic, ensuring clarity and consistency in classification.
Q: How can I find the FSC for a specific item? A: You can use various online databases and tools, such as the one provided by the National Stock Number Shop, to search for and retrieve detailed information about specific FSCs and the items within them.
National Stock Number Shop: Your Trusted Source for FSC Information
In conclusion, the Federal Supply Class system is a cornerstone of military and aerospace logistics, providing a structured approach to the classification and management of supply items. From aircraft to diesel engines and bearings, the FSC system ensures that essential items are accurately identified and readily available. At National Stock Number Shop, we are dedicated to offering comprehensive and up-to-date information on FSCs, helping you navigate the complexities of logistics and supply chain management.
For more information on the Federal Supply Class system and to explore our extensive range of products, visit National Stock Number Shop. Ensure your operations are efficient and effective with reliable data from the National Stock Number Shop.
This blog has aimed to highlight the significance of the Federal Supply Class system, showcasing key parts and their applications. By understanding the role of FSCs, we can appreciate how they contribute to the seamless functioning of military and aerospace logistics.
#Aircraft Fixed Wing#Diesel Engines and Components#Bearings Mounted#National Stock Number Shop#FSC catalog#Federal supply classes
1 note
·
View note
Text
How Can You Make Your Assignment Better?

Crafting high-quality assignments is a fundamental aspect of academic success, requiring a strategic approach and attention to detail. Let’s involve into a detailed discussion on each of the provided guidelines for improving assignment writing skills:
1. Understanding the Assignment Prompt
The assignment prompt serves as a roadmap for your task, outlining the expectations and requirements set by your instructor. Without a clear understanding of the prompt, you risk deviating from the intended focus and missing key elements necessary for a successful assignment. To ensure comprehension, it’s essential to break down the prompt into manageable components, identify keywords, and clarify any uncertainties with your instructor. By mastering this step, you lay a solid foundation for the rest of your assignment.
2. Thorough Research

Research is the backbone of academic writing, providing the necessary evidence and context to support your arguments. However, effective research goes beyond a simple gathering of information; it involves critical evaluation and synthesis of diverse sources to construct a coherent narrative. By consulting a variety of reputable sources, such as academic journals, books, and credible websites, you can deepen your understanding of the topic and bolster the credibility of your arguments. Additionally, employing advanced search strategies, such as Boolean operators and database filters, can streamline the research process and yield more targeted results.
3. Clear Thesis Statement
The thesis statement serves as the central claim or argument of your assignment, guiding the direction of your analysis and providing a roadmap for your readers. A strong thesis statement is concise, specific, and debatable, offering a clear stance on the topic while leaving room for exploration and interpretation. To craft an effective thesis statement, it’s crucial to conduct preliminary research, identify key themes or patterns, and articulate a focused argument that aligns with the scope of your assignment. By establishing a solid thesis statement early on, you can maintain clarity and coherence throughout your writing process.
4. Creating an Outline

An outline is a roadmap that organizes your ideas and structures your assignment in a logical sequence. By outlining the main points, arguments, and supporting evidence, you can ensure that your assignment flows cohesively and addresses all necessary components. Additionally, an outline provides a visual representation of your assignment’s structure, allowing you to identify gaps in your argumentation or areas that require further development. To create an effective outline, consider using a hierarchical format, such as Roman numerals or bullet points, to delineate the main sections and subtopics of your assignment. By investing time in outlining, you can streamline the writing process and produce a more polished final product.
5. Adhering to Formatting Guidelines
Formatting guidelines dictate the presentation and organization of your assignment, ensuring consistency and professionalism across academic work. While formatting requirements may vary depending on the discipline or institution, common elements include font size, margins, spacing, and citation style. By familiarizing yourself with the specific formatting guidelines provided by your instructor or institution, you can avoid unnecessary errors and present your work in a standardized format. Additionally, utilizing formatting tools or templates, such as Microsoft Word’s built-in styles or citation managers like EndNote, can simplify the formatting process and save time during document preparation.
6. Writing Clear and Concise Sentences
Clarity is paramount in academic writing, as it enhances comprehension and facilitates effective communication of ideas. Clear and concise sentences convey information efficiently, minimizing ambiguity and maximizing impact. To achieve clarity, it’s essential to use precise language, avoid unnecessary jargon or complex syntax, and structure sentences logically. Additionally, incorporating transition words and phrases, such as “however,” “therefore,” and “in addition,” can enhance coherence and flow between ideas. By prioritizing clarity and conciseness in your writing, you can engage your readers more effectively and convey your arguments with precision.
7. Supporting Arguments with Evidence

Evidence serves as the backbone of persuasive writing, providing support for your claims and lending credibility to your arguments. Whether in the form of empirical data, scholarly research, or real-world examples, evidence should be relevant, reliable, and effectively integrated into your assignment. To effectively support your arguments with evidence, it’s essential to critically evaluate sources, consider alternative perspectives, and provide sufficient context for interpretation. Additionally, employing proper citation techniques, such as direct quotations or paraphrasing, ensures academic integrity and acknowledges the contributions of other scholars. By prioritizing evidence-based reasoning, you can strengthen the persuasiveness of your arguments and demonstrate your mastery of the subject matter.
8. Proper Source Citation
Accurate citation of sources is essential for maintaining academic integrity and avoiding plagiarism. Proper citation acknowledges the contributions of other scholars, provides context for your arguments, and allows readers to locate the original source material. Depending on the citation style specified by your instructor or institution, you may be required to include in-text citations, footnotes, or a bibliography/reference list. To ensure proper source citation, it’s important to familiarize yourself with the conventions of your chosen citation style and apply them consistently throughout your assignment. Additionally, utilizing citation management tools, such as Zotero, Mendeley, can streamline the citation process and minimize errors.
9. Revision and Editing

Revision and editing are essential stages of the writing process, allowing you to refine your ideas, clarify your arguments, and improve the overall quality of your assignment. Revision involves reviewing your work from a macro perspective, focusing on content, structure, and argumentation, while editing focuses on micro-level elements such as grammar, punctuation, and style. To effectively revise and edit your assignment, it’s helpful to approach the task systematically, taking breaks between drafts to gain fresh perspective and utilizing feedback from peers, instructors, or writing tutors. Additionally, employing self-editing techniques, such as reading your work aloud or using grammar-checking software, can help identify errors and inconsistencies that may have been overlooked.
9. Careful Proofreading

Proofreading is the final step before submission, ensuring that your assignment is free from errors and polished to perfection. While it may seem tedious, careful proofreading is essential for maintaining professionalism and credibility in academic writing. To effectively proofread your assignment, it’s helpful to approach the task methodically, focusing on one aspect at a time (e.g., spelling, grammar, punctuation) and utilizing tools such as spell-checkers or style guides for assistance. Additionally, seeking feedback from peers or mentors can provide valuable insights and help identify areas for improvement. By dedicating time and attention to proofreading, you can ensure that your assignment meets the highest standards of quality and excellence.
Incorporating these guidelines into your writing process can significantly enhance the quality of your assignments and contribute to your academic success. By prioritizing clarity, coherence, and evidence-based reasoning, you can effectively communicate your ideas, engage your readers, and achieve your academic goals. Additionally, seeking assistance from resources such as Expert Academic Assignment Help can provide valuable support and guidance, helping you navigate complex assignments and overcome challenges along the way. Remember, improvement takes time and effort, but with dedication and practice, you can elevate your assignment writing skills to new heights and achieve academic excellence.
Incase of need for any guidance or facing challenges during the study period, just email: [email protected]
#essay writing#assignment help#essay#homework help#academic assignments#health sciences assignment health#college student#college help#pharmacy colleges#educate yourself#education#do your homewor#medical students#case study#research paper#research
1 note
·
View note
Text
How the Postal Code was Created?
The creation of postal codes, also known as ZIP codes in the United States and postcodes in many other countries, is rooted in the need for a standardized system to efficiently sort, process, and deliver mail and parcels. The development of postal code systems evolved over time in response to the growing volume of mail, expanding geographic regions, and advancements in technology and logistics. In this article, we'll explore the origins and evolution of postal codes, the factors driving their creation, and their significance in the global postal system.

1. Origins of Postal Codes:
The concept of postal codes dates back to the early days of mail delivery when postal services relied on manual sorting and routing of mail based on geographic proximity and address information. As mail volumes increased and postal networks expanded, the need for a more systematic approach to sorting and delivery became apparent. The first postal code systems emerged in the late 19th and early 20th centuries, with countries such as Germany and the United Kingdom introducing numeric or alphanumeric codes to facilitate mail sorting and routing.
2. Standardization and Efficiency:
The development of postal codes was driven by the desire to standardize addressing formats and improve the efficiency of mail delivery. Standardized postal codes provided a structured framework for organizing mail into geographic regions, allowing postal workers to quickly and accurately route mail to its intended destination. By assigning unique codes to specific areas, postal services could streamline sorting operations, reduce processing times, and optimize delivery routes, resulting in faster and more reliable mail service.
3. Technology and Automation:
Advancements in technology, particularly in the fields of automation and information processing, played a crucial role in the creation and implementation of postal code systems. The advent of mechanized sorting machines, optical character recognition (OCR) systems, and computerized databases enabled postal services to automate the sorting and processing of mail based on postal codes. These technologies increased the speed and accuracy of mail sorting operations, allowing postal services to handle growing mail volumes more efficiently.
4. Geographic Hierarchy and Coding Structure:
Postal codes are typically structured hierarchically to reflect the geographic hierarchy of the areas they represent. Larger geographic areas, such as countries or states/provinces, are assigned broader postal code prefixes, while smaller areas, such as cities or neighborhoods, have more specific postal code suffixes or extensions. This hierarchical coding structure allows postal services to organize mail into manageable geographic regions and efficiently route mail to its final destination.
5. Implementation and Adoption:
The implementation and adoption of postal code systems varied across countries and regions, with some countries introducing postal codes relatively early and others adopting them later. The process of implementing postal codes often involved extensive planning, coordination, and public education efforts to ensure widespread adoption and acceptance. Governments, postal authorities, and international organizations such as the Universal Postal Union (UPU) played key roles in promoting the adoption of postal codes and facilitating interoperability between different postal systems.
6. Benefits and Significance:
Postal codes offer several benefits and are essential components of the global postal system:
Efficient Mail Sorting: Postal codes streamline the sorting and processing of mail by providing a standardized addressing format that facilitates automated sorting and routing.
Accurate Delivery: Postal codes help ensure accurate delivery of mail to its intended destination by providing precise location information for postal workers and delivery routes.
Improved Service: By organizing mail into geographic areas, postal codes enable postal services to provide faster and more reliable delivery service to customers, enhancing overall customer satisfaction.
Geographic Targeting: Postal codes allow businesses and organizations to target specific geographic areas for marketing, distribution, and delivery purposes, enabling more effective and efficient mail campaigns.
Conclusion:
In conclusion, the creation of postal codes was driven by the need for a standardized system to efficiently sort, process, and deliver mail and parcels. The development of postal code systems evolved over time in response to advancements in technology, expanding mail volumes, and the growing complexity of postal networks. Postal codes play a crucial role in the global postal system by providing a structured framework for organizing mail, streamlining sorting operations, and ensuring accurate and timely delivery of mail and parcels to their intended destinations.
youtube
SITES WE SUPPORT
Postal Code and Overnight Mail – Wordpress
SOCIAL LINKS
Facebook
Twitter
LinkedIn
Instagram
Pinterest
0 notes
Text
Anand Jayapalan: How Does Cloud Storage Work?
Here's all you need to know about cloud storage, according to enterprise storage solutions experts like Anand Jayapalan.
Anand Jayapalan on Cloud Service: How Does It Work?
Cloud service providers have large data centers in several locations around the world. When customers purchase cloud storage from a vendor, they have to turn over most aspects of the data storage, including capacity, security, computing resources and storage servers, delivery over a network, and data availability.

How cloud service works depends on the type of storage. According to enterprise hardware and software storage solutions experts like Anand Jayapalan, the three types are block storage, file storage, and object storage.
Block storage takes any data and divides it into smaller units called blocks. Each block is placed on one of the system's storage drives and has a unique identifier. Block storage is efficiently fast and provides the low latency required by applications such as high-performance workloads and databases.
File storage organizes data in a hierarchical file system, generally used with network-attached storage (NAS) and personal computer storage drives. File storage systems store data in files, which are stored in folders. Directories and subdirectories are used to locate files and data and organize folders. A file storage-based system can make access and retrieval of data easier, with the hierarchical format familiar to most users and required by many applications.
Object storage consists of three main components: data stored in a file, metadata associated with the file, and a unique identifier, note enterprise storage solutions experts like Anand Jayapalan. An object storage protocol stores a file as a single object and assigns it an identification number (ID) using the RESTful API. If a user wants to retrieve content, the ID needs to be presented to the system, and the content is then assembled with its metadata, security, and authentication. Object storage systems allow metadata customization, which can streamline data analysis. With object storage, data is typically stored in its native format with massive scalability; add enterprise storage solutions experts like Anand Jayapalan.

In recent years, many object storage vendors have added file system capabilities and functions to their object storage hardware and software, mostly because object storage isn't widely adopted. For instance, a cloud storage gateway can provide a file emulation front end to its object storage; that arrangement often enables applications to access the data without the need to support an object storage protocol. According to enterprise storage solutions experts like Anand Jayapalan, backup applications use the object storage protocol, which is why online backup to a cloud service was one of the first successful applications for cloud storage.
Follow this Anand Jayapalan blog for more discussions on data storage and related topics.
0 notes
Text
Azure Data Fundamentals - Part1
Data is generated everywhere using different system, application and devices, in multiple structures and format
Data is a valuable asset , which provide useful information and help to take critical business decisions when analyzed properly
It is necessary to store, analyze and capture data since it has become a primary requirement for every company across the globe.
Finding out Different Data Formats
Data structure in which the data is organized represent entities, And each entity has one ore more attributes or characteristics.
Data can be classified into different formats -Structured -Unstructured -Semi-Structure
Structured This is fixed schema and has different fields and properties. Schema is organized in a tabular format in rows and columns. Rows represent each instance of a data entity and column represent attribute of the entity.
Semi-Structured This has some structure and allow variation between entity instances. One example of semi-structured data is JSON(JavaScript Object Notation)
Unstructured This has data without any structure. Example can be document, images, audio, video and binary files.
Various options to store data in files
Two broad categories of data store in common use
File store Storing the data on a hard disk or removable media such as USB drives or on central shared location in the cloud
File Format used to store data depends on a number of factors including
Type of the data being stored
Application that will need ro read/write and process data
Data files readable by human or optimized for efficient storage and processing
Common File Formats
Delimited text files Data is separated with field delimiters and row terminators. Most commonly used format is CSV Data
-JSON Data is represented in hierarchical document schema which is used define object that have multiple attributes.
Databases
-XML Data is represented using tags enclosed in angle brackets to define elements and attributes.
-BLOB Data is stored in binary format 0's and 1's.Common type of data stored as binary include images, audio, video and application specific documents.
-Optimized File Format Some specialized file formats that enable compression, indexing and efficient storage and processing have been developed.
Common optimized file format include Avro, Optimized Row Columnar Format(ORC) and Parquet.
Various options to store data in database
Two ways data are stored in database -Relational Database -Non-Relational Database
-Relational Database This is used to store and query structured data. Data stored in the represent entities. Each instance of an entity is assigned a primary key which uniquely identifies and these keys are used to reference the entity instance in another table. Table are managed and queried using SQL which is based on ANSI standard.
-Non-Relational Databases This is often referred as NOSQL Database. There are 4 common types of nonrelational database commonly used
KeyValue Database - Each record consist of a unique key and associated value
Document Database - Specific form of Key Value database
Column Family Database - Store tabular data in rows and columns
Graph Database - Which store entities as nodes with link to define relationship between them
Understand Transactional data processing solutions
A system records transaction that encapsulate specific events that the organization want to track. Transaction system are often high volume handling millions of transaction every day often referred as Online Transactional Processing OLTP. OLTP system support so called ACID semantics
Atomicity-Each transaction is a single unit which either fails or succeed completely. Consistency-Transaction can only take data in the database from valid state to another. Isolation- Concurrent transaction cannot interfere with each other. Durability-When a transaction is committed, it remains committed.
OLTP is often used for supporting Line of Business Application
Understand Analytical data processing solutions
Analytics can be based on a snapshot of the data at a given point in time or a series of snapshot. It uses read-only system that store vast volumes of historical data.
Analytic usually look like
Data file stored in central data lake for analysis
ETL process copies data from files and OLTP DB into a Datawarehouse. 3.Data in data warehouse is aggregated into OLAP(Online analytical processing) model. 4.Data in data lake, data warehouse and OLAP can be queried to produce reports, visualization and dashboards.
Different Types of user might perform data analytic work at different stages -Data Scientist might work directly with files in a a data lake to explore and model data -Data Analyst query table directly to produce reports and visualization -Business user consume aggregated data in the form of reports and dashboards.
Keep Learning! Keep Enjoying!
0 notes
Text
Database Management System Assignment
The secret to scoring higher in Relational, hierarchical, graph and various other topics of DBMS is to connect with Treat Assignment Help. Our offered database management assignment help is ranked One in the UK.

#Database Management Assignment Help#DBMS Assignment Help For Students#Database Assignment Help#Hierarchical Database Assignments#Relational Database Assignment Help#Graph Database Assignment Help#Database Management System Assignment#help with database assignment#database assignment for students#database management homework help#database management system
1 note
·
View note
Text
Online Database Assignment help by the top Experts !
Everything in this digital era is available online. From a piece of cake to complicated software programming, you can get everything with one click. Now students can complete their assignments with the help of online for their Database assignments from the top experts.
#Database Management Assignment Help#DBMS Assignment Help For Students#Database Assignment Help#Hierarchical Database Assignments#Relational Database Assignment Help#Graph Database Assignment Help#Database Management System Assignment#Help with database assignment#Database assignment for students#Database management homework help#Database management system
0 notes
Text
WHO Uganda Jobs 2022 – Fresher IT Assistant
WHO Uganda Jobs 2022 – Fresher IT Assistant
August 9, 2022 Job Title: IT Assistant – WHO Uganda Jobs 2022 Organization: World Health Organization (WHO) Duty Station: Kampala, Uganda World Health Organization (WHO) Profile The World Health Organisation (WHO) is the directing and coordinating authority for health within the United Nations (UN) system. It is responsible for providing leadership on global health matters, shaping the health research agenda, setting norms and standards, articulating evidence-based policy options, providing technical support to countries and monitoring and assessing health trends. Roles and Responsibilities: The World Health Organization, Uganda Country Office is looking for a qualified and competent Ugandan national to fill the vacant position: The Country Office IT Assistant is assigned the following major duties or any other related responsibilities, as may be required, by his/her hierarchical supervisors commensurate with the area of responsibility: - Support users in all application, software and hardware related issues; - Respond, in a timely basis, to users’ requests and update the FAQ and QA database accordingly; - Record and manage requests using the official Ticket System software - Ensure the troubleshooting of computers, printers and other devices; - Install, configure and maintain standard desktop configurations; - Install and support printers, scanners and other similar devices; - Generate and maintain standard desktop configuration images for each model of desktop/laptop; - Ensure software and applications’ troubleshooting; - Install necessary specific drivers and applications on computers; - Contribute to the delivery of end-users’ trainings in office applications, such as Microsoft office suite and other tools; - Provide IT support during meetings held in the office; - Install and configure mobile devices (smartphones, tablets) as necessary; - Support the identification of staff ITM capacity and skills gaps, propose and implement agreed skill enhancement and training measures. - Performs other duties as required. Minimum Qualifications for WHO Uganda Jobs 2022 - The applicant must hold relevant qualifications. How To Apply for WHO Uganda Jobs 2022 All interested and suitably qualified candidates should submit their applications through the link below. Click here to apply Deadline: 18th August 2022 For similar Jobs in Uganda today and great Uganda jobs, please remember to subscribe using the form below: NOTE: No employer should ask you for money in return for advancement in the recruitment process or for being offered a position. Please contact Fresher Jobs Uganda if it ever happens with any of the jobs that we advertise. Read the full article
12 notes
·
View notes
Text
Whats My Ip 4 Address

What is my IP Address?
What Is My Ipv4 Addressing
What's My Ip 4 Address
What Is My Ipv4 Address
This service hides your IP by redirection the traffic via a separate tunnel in the public area. As a result, your real IP address is not shown, and the connection is provided by one of the VeePN VPN servers. Should anyone try to intercept you – they will get to that server and not your device.
IP addresses are the numerical names that are assigned to a device as a “license plate” so that it can be called by other devices. There are two types of IP: Public IP and private IP. Both public and private IP’s are built in four number blocks. Each block is a number from 0 to 255 and is separated by a period (“.”).
The IP Address of this machine is:
Look up IP Address Location If you can find out the IPv4 or IPv6 address of an Internet user, you can get an idea what part of the country or world they're in by using our IP Lookup tool. What to do: Enter the IP address you're curious about in the box below, then click 'Get IP Details.'
188.40.85.20
This address can also be represented as 3156759828 (32 bit decimal number) or 0xBC285514 (32 bit hexadecimal number).
(NB - if you are part of an internal network then this is the IP address of your local server, the machine which is connected to the external internet.)
What is an IP Address?
'IP' (Internet Protocol) is the method used for sending and receiving information over the Internet. Any device that is required to communicate over the Internet is assigned a 32-bit number, its IP address, which uniquely identifies it to other devices. The IP address is usually written as a set of four numbers in the range 0-255 separated by dots, although it can also be shown as one big number in decimal or hexadecimal.
How are IP addresses used?
Whenever data is to be transmitted to a particular machine, it is broken up into chunks, or packets, each of which is tagged with the IP address of the destination machine. Each packet is transmitted separately, and will not necessarily follow the same route through the network as the other packets that make up the whole message. It is quite possible that the packets will arrive out of sequence, or with errors. Some may not even arrive at all.

On receipt the packets are automatically reassembled into the correct sequence so as to reconstruct the original data; if there are any errors or missing packets then they are requested to be sent again.
Private IP Addresses
Three ranges of IP numbers are reserved for local or private IP addresses - these are addresses which identify a device on a local network which is isolated from the internet by a router with Network Address Translation.
The three ranges are: 10.xxx.xxx.xxx 172.(16-31).xxx.xxx 192.168.xxx.xxx
These addresses are never used on the public internet. Typically, behind a NAT device, a sub-range from one of these ranges will be used to identify devices on a local network.
How are IP Addresses Assigned?
IP Addresses are hierarchical in nature - that is to say, one part of the IP address will specify broadly in which region of the network the destination can be found, with subsequent parts of the address providing more specific information about the location of the target device within that region. Consequently the allocation of IP addresses needs to be carefully managed, in order to maintain this hierarchy.
The allocation is overseen by the Internet Assigned Numbers Authority (IANA) and Regional Internet Registries (RIRs), who maintain a publicly accessible database called WHOIS, relating IP Numbers to locations in the network.
What is IPv6?
An IP address as described above is made up of four bytes, in a format known as IPv4. Four bytes can be used to represent over four billion different individual addresses, which might seem sufficient to uniquely label every computer in the world - but with more and more devices being connected to the internet the number of IPv4 addresses which are free to be allocated is dwindling.
IPv6 mitigates this problem by using sixteen bytes instead of four, which allows approximately 3.4x1038 unique addresses to be represented. In addition, the standard solves various other technical problems that IPv4 suffers from.
Unfortunately IPv6 is not interoperable with IPv4, so in order to use it all the internet hardware between IPv6 nodes will need to be updated to be able to use IPv6. Until that happens an IPv6 network is effectively invisible to IPv4 systems, and vice versa, although it is technically possible to implement converter nodes that embed one protocol within the other to allow connections between the different networks.
Who owns an IP Address?
Whilst you may not be able to track an owner of an IP address, you can usually find out its location. If you know the IP address, enter it on this free tool: ip lookup - also known as IP Geolocation - GeoIP.
What Is My Ipv4 Addressing
Network Address Translation More info
What's My Ip 4 Address
What is DNS? DNS Explained
Virtual Private Networks VPN information
Questions & Answers
What is an IP address?
IP address (or Internet Protocol address) is a numerical address of your device network connection. Basically, it's a set of rules that serves as a way of your device identification on the internet.
How IP addresses work?
You can compare Internet Protocol to postal services in the real-world. A postal code is an identifier for mail routing. And, in very simple words, IP address is a digital postal code for internet traffic routing. Every device, website and network server have an IP address.
How an IP address looks like?
There are 2 common standards for IP address: IPv4 (IP Version 4) and IPv6 (IP Version 6) that is aimed at replacing IPv4 in the future.
IPv4 address uses 32 binary bits and contains from 4 to 12 digits, 4 numbers separated by dots. Examples: 8.8.4.4, 188.100.210.213
IPv6 address uses 128 binary bits and can contain up to 45 characters (8 groups of 4 hexadecimal digits separated by 6 colons). Groups with all zeros can be shortened for the simplicity of the representation. Example: 2001:4860:4860::8888 (expanded – 2001:4860:4860:0000:0000:0000:0000:8888)
What information someone can get from my IP address?
What Is My Ipv4 Address
Here you can find out how much information you can get from an IP address.

1 note
·
View note
Text
What exactly is a “domain name system” and why should you care?
What is DNS? DNS is a decentralized and hierarchical naming scheme for computers, services, and other resources associated with a private network or the Internet. It associate different information with different domain names assigned to every of the involved entities.
A DNS server is responsible for maintaining the records associated with domain names and maintains connections between these records. An IP (Internet Protocol) address is a unique number assigned to a computer system and uniquely identifies its owner. There are many types of records used in DNS and the master DNS records contain information about a zone-specific query and lookup requests, while zones are logical labels for domain names and contain zone-wide search queries and records. There are also application records, which define application names and functions for DNS clients and servers. Many vendors provide core networking services that help organizations manage their DNS services, including Infoblox, BlueCat Networks, and Microsoft.
DNS is commonly used in conjunction with nameservers. Nameservers are online reference databases that contain a list of IP addresses, or Internet Protocol addresses (IPs). A DNS server is responsible for translating domain names into IP addresses and then translates the IP address back to a name. A DNS client uses this DNS server's information to find a specific entity on the Internet and then queries the DNS server to obtain the details regarding that entity. When a DNS server successfully returns a match, the client is matched with that entity and is able to access the resource record for that entity. DNS servers store the information in zone files and allow queries to be sent to them by clients.
Records in the DNS database are classified according to their types: authoritative, non-authoritative, and historical context. Within the DNS database, there exists two types of records: zone-wide and zone-bound. Zone-wide refers to the zone of which the domain name is a part, while zone-bound refers to the zones within that zone which have been explicitly added or modified. Zone-wide records are used to create DNS entities while zone-bound records are used to determine how to resolve domain names to IP addresses. Most DNS servers maintain a copy of all zone-wide records in their repository, while some operate internally for zone-bound records only.
Resource records are information that identifies a specific domain name. DNS servers maintain a copy of every data file associated with the domain names that are in their database. These data files include such elements as names, numeric IP addresses, description lines, and other meta-data. The information in these data files enables clients to locate a particular entity from the directory by sending a request for that entity.
DNS resolvers are computer programs that translate query messages into data that can be accessed by clients. The computer program then updates the DNS database by adding or modifying DNS resource records that correspond to messages it has heard. DNS server operators maintain DNS records using DNS resolver databases. These databases are updated periodically and clients do not need to contact the nameservers directly to ask for information about DNS records. DNS queries are sent to the nameservers through an agent which maintains a cache of such queries on its system and responds to those requests from clients with data files that contain answers to the DNS query.
1 note
·
View note
Text
Natural Language Processing: A breakthrough technology in healthcare
Have you ever tried to converse with a computer in the language you speak?
Sounds like a fascinating concept? Well, it is! Lately, there have been noteworthy discoveries in engaging computers to comprehend the language similarly as we do, well known as Natural Language Processing. However, It is anything but a simple errand training machines to see how we, humans convey.
What is Natural Language Processing?
Natural Language Processing, popularly known as NLP, is the field of Artificial Intelligence which gives the computers the ability to understand, read, analyze and interpret the human language. Simply put, it is the relation between the computers and human language. It has several sub-disciplines, including Natural Language Understanding (NLU), Natural Language Generation (NLG), and Natural Language Query (NLQ). Combining the intensity of Artificial Intelligence, computational phonetics, and computer science, NLP permits a machine to comprehend human language which only humans could possibly do, until now. It is viewed as a difficult issue in computer science due to the nature of human language, which makes it troublesome.
The global market size of NLP is growing at a CAGR of 18.6% for period of 2020-2026 and by 2026, it is estimated to reach to USD 27.6 Billion, from USD 9.9 Billion in 2020. The NLP market consists of major growth factors like the increase in smart device usage, growth in the adoption of cloud-based solutions and NLP-based applications to improve customer service, as well as the increase in technological investments in the healthcare industry.

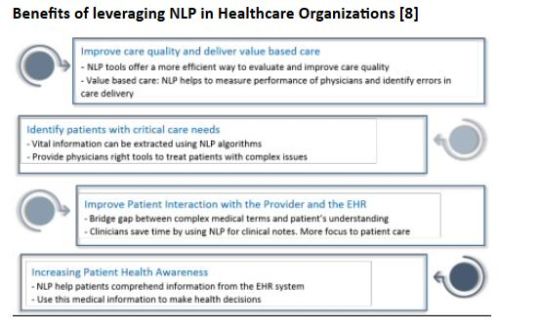
NLP in Healthcare Natural Language Processing is rapidly being adopted in Healthcare industry. It has realized the potential of this cutting edge technology in streamlining the processes. Healthcare industry is quick in understanding the significance of information, gathering data from EMRs/EHRs and other sources. Huge volumes of unstructured patient data is inputted into EHRs on a daily basis, but it’s hard for a computer to help physicians aggregate that critical data. Structured data like claims or CCDAs / FHIR APIs may help determine disease burden, but gives us a limited view of the actual patient record. With the fragmented nature of the healthcare industry, large amount of data is collected in silos having as much as 80 percent of data unstructured and of poor quality. This brings us to a pertinent challenge of data extraction and utilization in the healthcare space through NLP in Healthcare. This unstructured data will take a lot of time and effort if humans try to structure it manually, making the data unusable. This hinders us from taking effective decisions through analytics because of the form of our data. Therefore, NLP can help to leverage this unstructured data as we make a shift gradually from fee for service model to value based care. For healthcare and life sciences, by 2025 the global market size of NLP is assessed to reach USD 3.7 billion from current size in 2020 that is USD 1.5 billion. Also, it is growing at CAGR of 20.5%. The healthcare and life sciences NLP market include the factors such as increasing use of predictive analytics to enhance health outcomes and growing demand for improving Electronic Health Record (EHR) data usability to enhance patient care. The worldwide healthcare and life sciences NLP market consists of important vendors such as the vendors from United States of America include 3M, Lexalytics, AWS, Google, Nuance, Microsoft, IBM and others. Clinithink is a vendor from Georgia. From Germany, Averbis is a major vendor. Linguamatics is a vendor from the United Kingdom. Use Cases Primarily, this technology is helping the healthcare in the following ways 1. Comprehending human speech and extracting its meaning 2. Unlocking unstructured data in databases and documents by mapping out essential concepts and values and allowing physicians to use this information for decision making and analytics Likewise, some of the Use cases in healthcare can be broadly highlighted in the following 3 groups: 1. Mainstay Use Cases for NLP which has a proven ROI A. Speech Recognition: NLP allows the transcription of huge amount of clinical notes from speech to text. This reduces the task of physicians to dictate notes and therefore, saves time by avoiding duplication. Many companies are working in medical transcription space like Acusis, SmartMD, IKS Health, Aquity and many more B. Clinical Documentation: NLP helps the physicians freeing up from the manual and complex structure of EMRs allowing them to focus more on patient care. Nuance and M*Modal have technologies that work in tandem with their speech recognition technologies to capture structured data at the point of care and standardized terminologies for future use In the future, NLP tools could be applied to social media and other public data sets to determine social determinants of health (SDOH) as well as the effectiveness of wellness-based programs and initiatives. C. Computer Assisted Coding (CAC): Computer-assisted coding extracts information about procedures and therapies to capture every code and maximize claims D. Data Mining: NLP helps to mine the unstructured patient data allowing organizations to reduce the levels of subjectivity in decision-making and improve the quality of patient care 2. Emerging Use cases of NLP A. Clinical Trial matching: Using NLP and machine learning in healthcare to identify patients for a clinical trial with the help of NLP engines for trial matching B. Pharmacovigilance: IQVIA is trying to apply machine learning with natural language processing to transform many Pharmacovigilance functions for greater accuracy and speed [10] C. Prior Authorization: NLP modules can be used by Payer to determine prior authorization rapidly. Companies like IBM Watson and Anthem are working on these NLP modules D. Clinical Decision Support (CDS): CDS help physicians to make better decisions. Also, it is being used to aid clinicians in checking symptoms and diagnosis E. Risk Adjustment and Hierarchical Condition Categories (HCC): HCC relies on ICD-10 coding to assign risk scores to each patient. NLP can help assign patients a risk factor and use their score to predict the costs of healthcare 3. Next gen Use cases of NLP A. Ambient Virtual Scribe: NLP can be used to develop a speech recognition software for clinical documentation giving rise to Virtual scribes limiting the need for human scribes B. Precision Medicine: NLP can be used for Computational Phenotyping and Biomarker Discovery C. Population Surveillance: An application of NLP to EMRs can be identifying a subset of an ethnic or racial group for eventually documenting and mapping health disparities
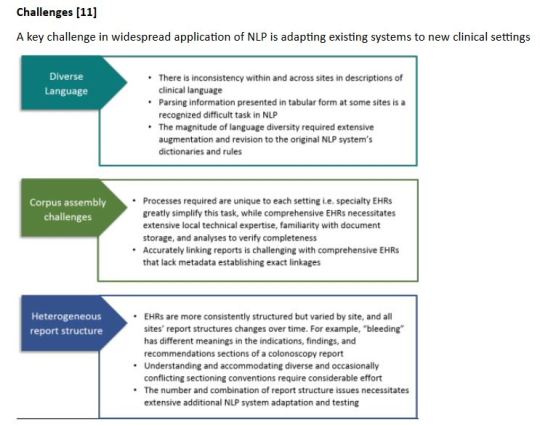
Challenges A key challenge in widespread application of NLP is adapting existing systems to new clinical settings
The Future
NLP technologies finds its applications for a range of purposes in Healthcare and Research, including Clinical documentation, medical transcription, clinical trials, Decision Support System and many more. However, the real-life implementation is still facing obstacles. Even though, NLP has the potential to revolutionize with their breakthrough technology and change the landscape of healthcare industry. It is creating new and exciting opportunities in healthcare delivery and patient experience. Natural Language Processing is here to stay, a technology that gets smarter with time, as it empowers the providers to positively influence the health outcomes.
1 note
·
View note
Text
6 Reasons Why You Should Go for Custom Software Development
We should take a gander at why custom software development in Canada, turns into the most ideal alternative for businesses. This goes for new companies just as endeavors the same, for settling complex business issues alongside improving tasks. Presently, you need to recollect, that each business is totally remarkable. Obviously, they may all have basic business issues. In any case, every one of them has a special story behind the manner in which they handle their business issues and emerge from it.

With regards to bundled software, it is an insufficient one to determine the battles of workers. Nor is it ready to eliminate the intricacies of the cycles or meet the inclinations of customers that are available across the enterprises. Employing custom software development administrations in Canada would address such sorts of hierarchical difficulties with regards to new businesses just as undertakings.
Prior to delving further into this subject, we should cause you to comprehend what custom software development is. As a remarkable custom software development company in Canada, Spring time software will work effectively at causing you to comprehend this better.
We as a whole realize that innovation space is flighty, and is automatically making the market serious as innovation impacts the inclinations of representatives just as customers both. The unconventionality squeezes the businesses and asks them to rapidly change as per the new market patterns. The additional time a business takes to change, the more costly it becomes for it.
This is exactly why numerous organizations are taking the assistance of custom software development benefits in San Antonio for building a natural just as an easy to understand software item, that is customized to their one of a kind business prerequisites.
Examine the 6 top explanations behind picking custom software development:
1. Single Software and Databases need Completing Complex Business Tasks
All the organizations that utilization bundled software have one significant burden. This disservice is that they can't play out all the given business assignments on a similar software. Single Software and Databases need to utilize different sorts of software to play out a wide scope of business errands. In the end, there turns into a likelihood that this may cause commitment just as security issues. In this manner, the significant effect of utilizing numerous sorts of software just as information bases is that they aren't equipped for producing understanding into business tasks.
2.The Deficiency of Visionary Software
At the point when a business is continually developing just as putting resources into an off-the-rack software, it would imply that the business is being confined of its development and is being restricted to a specific arrangement of capacities. With custom software development, the business would get the adaptability choices, just as the methods, and the capacities in addition to abilities of the software to develop as the business develops. In this market, there is a major insufficiency of versatile, visionary software items, that could be scaled by the individual necessities of the customers.
3.Capabilities of Integration
With regards to an incredible custom software development company in San Antonio, it has the ability to give a scope of choices to incorporate various kinds of APIs. With regards to the bundled software, a large portion of them are contrary with different projects. Accordingly, incorporating another software for upgrading its capacities would not be conceivable. This turns into another purpose behind numerous organizations to incline toward custom software development benefits in San Antonio.
4.Benefits that are Personalized for You
A significant benefit is personalization, with regards to putting resources into restrictive frameworks. A custom software development company in San Antonio, that is dependable, has the ability of building software applications that are explicit to the necessity of a given business. Along these lines, the application can carefully be customized to a bunch of cycles that are trailed by the association. Also, with such a plan, business pioneers can be given full access just as control.
5.Security of the Application
At the point when you consider the internet, you promptly realize that it has an intricate danger climate. Subsequently, application security turns into a critical worry for current businesses. This is valid, regardless of their sizes. Any application on the Internet today is continually presented to security penetrates. Every single company is taking proportions of defending its software items against any sort of abuse by programmers. Notwithstanding, the current circumstance is as yet not a gorgeous one. Subsequently, when an association draws in with a presumed just as qualified custom software development company in San Antonio, they can take added measures for keeping their information from programmers just as from displeased workers.
6.Saves Your Precious Time and Money
In the event that software development is certifiably not a significant piece of your business profile, any sort of convoluted IT task is for the most part burning through your group's time. There are many specific firms that take on your software development project, tailor it to your exceptional necessities, and execute it speedier, just as in a superior way. They are additionally more practical than your in-house IT division. The underlying expenses of custom software development may be debilitating, however as time passes, they would end up being awesome. At the point when you streamline the business cycles to be consistent and lean, they will actually want to shave off a wide range of superfluous costs, way more productively, when contrasted with any mass-delivered software.
In case you're as yet not ready to persuade yourself regarding employing custom software development benefits in San Antonio, at that point you should connect with the specialists at Spring time software. Not exclusively can they persuade you, however you won't need to take a gander at some other company for these administrations.
1 note
·
View note
Text
Amazon Web Service - a Summary of How Everything Works

Applications are often easily layered with the assistance of flexible, reliable, and cost-effective services provided by Amazon. Does one realize the simplest part about Amazon Web Services? The way that it's used as a stage as-a-service is conducive to varied applications. You’ll pay more only as costs arise with no upfront expenditure. Additionally, since the hardware is taken care of by Amazon itself, you do not even need to pay any maintenance charges for an equivalent.

image source
Hierarchical Organization
At a really elevated level, you'll consider EC2 a worldwide processing environment. Inside EC2 are countries that will be thought of as data centers. The inner part of those data centers are computer clusters that in AWS language are called Availability Zones
- EC2 (think cloud)
- Regions (think data center)
- Availability Zones (think computer cluster)
Virtual Machines
In the inner part of an Availability Zone, we can generate virtual machines from predefined or custom Amazon Machine Images, or AMIs. An AMI is often thought of as an outline of a machine that you simply can load and run inside the cloud at an Availability Zone. Whenever you're taking an AMI and begin it, it's called an Instance of the AMI. You’ll take an AMI and begin it several times, whenever creates a replacement Instance.
Virtual Hard Drives
To help keep your data unblemished even when an Instance dies, you'll use several different AWS services however one among the more common ones is that the Elastic Block Store, or EBS. Consider EBS a tough drive. You’ll make an EBS from 1GB to 1TB and 'install' it on any of your virtual machine Instances. Along these lines, if you've got an Instance that's running your website and you would like to form sure the database remains healthy albeit the Instance disappears, you'll use an EBS 'hard drive'. Within the vernacular of AWS, you've got created an EBS volume and mounted it on an Instance.
Other virtual memory
There are other services you would possibly have used besides EBS for holding this fanciful database of yours. For instance, the SimpleDB, or SDB, maybe a perfectly reasonable substitute and would be preferred in certain situations. However, SDB may be a specific service for essential database delivery, whereas EBS may be a generalized storage solution. There’s additionally the electronic database Service or RDS that provides vigorous database services beyond SDB. The selection of service is usually dependent upon the requirements of the answer.
Virtual Backup
If we'd like to secure that data we presently wear our EBS volume, we aren't free and clear yet because even hard drives can fizzle. We'll get to back this up into more stable storage. For this, we will use the straightforward Storage Solution or S3 for brief. You’ll consider S3 a readily available tape backup. It allows you to possess up to 100 directories of knowledge on your tape. Each of those directories is named a bucket within the S3 world. Because it's an honest stable storage system, you'll get to backup your EBS volume(s) to S3 periodically. What's more, if you've got customized your Instance, you'll get to save a replacement image of it in S3 too. Thusly, if your carefully customized Instance or EBS volume crashes under any circumstances, you'll haul them out of your backup in S3 decently fast and obtain up and running another time.
Vigorous Security
Well, everything of this can be worthless if we did not have great security to form sure our solution was hacked. Two concepts are utilized in AWS for security purposes. The primary may be a set of keys that permits you and your developers to access your systems. These are public or private key sets and computerized certificates necessary to securely sign in to the Instance. The second, called a security group, is often thought of as a firewall configuration. You create a security group that defines how outside entities -, for instance, web browsers, or remote desktops, or FTP, or email, etc. - can or can't access your Instance.
Virtual Router
To serve our website to people generally, we should always have a permanent public IP address that we will appoint to our Situation. For that, we can utilize an Elastic IP or EIP. It’s 'elastic' because despite the very fact that it's a hard and fast public IP on the web, it alright could also be assigned to any of our Instances on the within of AWS. This is often a serious additionally to because if that Instance dies and that we raise a replacement Instance, we will move the EIP to the present new Instance and minimize site interruptions.
Cloud Scalability
Our site is up and running on our Instance, our data is safely on an EBS volume, we've backups on S3, well securely given our engineers access, and that we have our site freely accessible. Everything is great up to the purpose that we discover increased traffic from elsewhere on the web. Apparently, our site is popular in the countryside that's far away from the region during which we found out our system. However, we are becoming half our hits from Europe. The performance of our site for our European visitors won't get on a par with what we'd want. Fortunately, we will push our site out closer to those users by utilizing the Content Delivery Network, or CDN.
In AWS, CDN services are delivered by CloudFront. This service takes your static content and replicates closer to where you've got a high volume of users, thereby making the delivery of your site tons
1 note
·
View note
Text
Database Project Help
Avail Database Management System Assignment Solution At The Best Price
All the prices of our database management assignment help services are quite reasonable. Whether you want an advanced database management system assignment solution or a distributed database management system homework, you won't have a problem affording the service. Moreover, there are several deals and discounts that allow you to get database management system assignment answers at a much lower price.
Flat 25% off for all the new users
Exciting combo offers for regular customers
$20 signup bonus that can be redeemed later
Amazing referral bonus on every successful referral
Seasonal deals and discounts for loyal customers
Database Software Paradigms
Network Model: The network is an elaborated version of the hierarchical structure, giving access to many-to-many relationships through a tree-like structure, thus, allowing multiple parents. It organizes data through two fundamental concepts; records and sets.
Entity-Relationship Model: This model was developed for database design by Peter Chen. An entity is a thing that exists either physically or logically. For example, car, house, book, etc. Entities are linked to each other through relationships.
Relational Model: It was first described in 1969 by E.F. Codd. In this model, data is stored in form of tables called relations. Each row of table holds one record known as TUPLE. Each columnof table is called ATTRIBUTES.
Also, the price of our online DBMS assignment help will depend on the deadlines and the academic level of the solution. So, if you want the DBMS homework help at a lower price, simply place the order with a longer deadline. You can also generate the price quote of the required database management assignment help for free by submitting your requirements.
#databaseassignmenthelpers#databasehomeworkhelp#databaseassignmenthelp#databaseassignmenthelpexperts#database#databaseonlinehelpers#bestassignmentsupport.com
1 note
·
View note