#How To Use Static IP Address: Easy Way
Explore tagged Tumblr posts
Text
What is a Static Residential IP? A Guide to Proxy IPs
What is a Static Residential IP? A Guide to Proxy IPs
Static residential proxies (also known as static ISP proxies) are among the most popular types of proxies. They are also one of the best methods for hiding your identity and maintaining online anonymity. Why would you use residential proxies instead of just using regular proxy services? Below, I'll share the details.
What is a Static Residential Proxy? Let's first talk about residential proxies. A residential IP address is a real IP address issued by a legitimate Internet Service Provider (ISP) that belongs to a physical device with an internet connection.
Residential proxies are easy to find and allow websites or ISPs to monitor their online activities. Static residential proxy servers route user traffic through real IP addresses. IPFoxy’s static residential proxies are a combination of static and residential proxies, simulating an ISP proxy from a real consumer environment. ISP proxies allow you to browse the internet from the perspective of a genuine consumer, even gathering public data from the most challenging targets.
Why Use a Static Residential Proxy?
Avoid IP Bans IP bans are a common way for ISPs to block access to websites. They can be triggered by various factors, including using anonymous proxies that do not retain logs or IPs, attempting to bypass geo-restrictions, or simply using too many proxies at once. By using residential proxies, you can avoid IP bans since your computer's address remains unchanged, so it won't be flagged as suspicious.
Prevent IP Leaks IP address leaks are one of the main reasons services block users from accessing their content. This happens when the server sees your real IP address instead of the proxy’s fake one, leading to unencrypted leaks. This allows them to see your actual location and deny service if needed (which is why we recommend using only encrypted proxies). Leaking residential proxies prevent this issue because they never expose any details about your identity or location—only the specific information required by the website or service will be requested.
Advantages of Static Residential Proxies
High Speed Static residential proxies have available bandwidth suitable for business use, ensuring that they are always fast and stable.
Anonymity Since you are connecting to a real IP address, no one can detect that you are using a proxy (unless someone else is using the same residential connection).
Reliability Due to the use of real IP addresses (which are often assigned for years), static residential proxies are typically not blocked by websites.
Availability in Multiple Countries With coverage in 20+ popular countries, static residential proxies help expand market reach in real regions and improve geolocation accuracy.
Use Cases for Static Residential Proxies
The most common use cases for static residential proxies include:
Enterprise Network Access Companies can securely and stably access internal networks remotely through static residential proxies, protecting sensitive data exchanges.
Social Media Account Management When managing multiple social media accounts, static residential proxies can improve account authenticity and stability, ensuring account security.
Cross-Border E-commerce Operations E-commerce accounts often require pure, real IP addresses. Static residential proxies, with their fixed and real nature, ensure the account environment remains authentic, safeguarding the account.
Content Publishing and Data Scraping Content publishers and data scrapers can use static residential proxies to avoid account bans or access restrictions due to frequent IP changes.
Online Gaming Online gamers can use static residential proxies to maintain a stable gaming experience and reduce the risk of connection interruptions.
How to Configure a Static Residential IP
Choose the Right Proxy IP Provider Be careful not to choose free proxies, as they often come with risks. Select a reputable proxy service and use their free test quota to evaluate the service.
Obtain Proxy Information This typically includes proxy type, host, port, username, and password.
Configure the Proxy on Your Device Proxy IPs can be configured on various devices, such as fingerprint browsers, emulators, etc. Conclusion Static residential proxies play a vital role in network security and privacy protection. Whether for businesses or individual users, effectively utilizing static residential proxies can optimize network access, enhance efficiency, and ensure a secure browsing experience for both work and leisure. Choosing a reliable provider is key to successfully using static residential proxies.
0 notes
Text
Randomly thinking about small protocols or protocol changes that I think should exist.
Prime example is Static HTTPS: I think there should be a companion protocol to HTTPS for handling static requests. This would be great for caching, general performance, and even saving storage/bandwidth on things like ActivityPub.
The gist of it is that HTTPS uses a static set of keys to negotiate a dynamic set of keys and dynamically encrypts your entire conversation with the server. It's impossible to do any sort of caching on HTTPS without decrypting it first, but also there's no way to make it unique either without things like php sessions (requiring logins or backchannel confirmations).
How this would work, using the existing HTTPS keys, a request would be made similar to HTTP where the connection itself is unencrypted, but the host/url will specifically be encrypted and the payload of the data sent in return will be encrypted. If you were to cache it the same encrypted request will net the same encrypted data (unless the file behind it gets updated of course). If headers must be added then those can be encrypted separately as well, but also support unencrypted where not necessary... everything would be avoiding using headers in general for this, especially as the files are static.
(Optionally the html could also include a key explicitly for that file)
This means that anything in the middle can cache data without necessarily knowing anything about it. Meaning that something like Cloudflare could provide caching for an HTTPS website without also having to have the key.
Obviously in less secure cases where it doesn't include a special key in the html it will mean that if someone knows what site you're accessing (often an easy guess from IP unless it's something like a cloudflare protected site) they can potentially identify the file by matching to their own browsing... but these should be unimportant files anyways (ie. the google logo, css style sheets, etc), even if visible they'll be effectively signed and you'll know the site wasn't tampered with in transit.
But the really special case shines in things like the fediverse where when I make a followers-only post with a picture attached... right now either the picture is relying on obscurity (publically visible if you know the address) or it has to be embedded in the post as it's sent to the recipient.
This protocol would mean that the html of the post could include the key to the file. The receiving server wouldn't even need to support this protocol or have any change at all in ActivityPub standard to show this image, but the image would still be visible to the recipient so long as their browser or client supported it.
Example: <a href="shttps://foggyminds.com/images/123456" key="101010101"> (obviously the key would be much longer usually)
A backwards compatible call when privacy isn't a concern (ie. google logo): <a href="https://foggyminds.com/images/123456" shttps=1> (Browser with no shttps support would use https normally, but one with that support would see the shttps=1 on there and change the protocol automatically)
0 notes
Text
How Artificial Intelligence Efficiently Processes Data: The Critical Role of IP Proxies

In modern times, data is known as the “new oil” and its importance cannot be ignored. Artificial Intelligence , a powerful data processing tool, is changing the way we understand and utilize data. In this paper, we will look at how AI processes data and discuss the role that IP proxies play in this process.
1. Data collection
The first step in Artificial Intelligence is data collection.AI systems rely on large amounts of data to train and optimize models. This data can come from a variety of sources, including social media, sensors, databases, publicly available datasets, and user-generated content. The use of IP proxies becomes particularly important in this process. Through proxies, AI is able to collect data from different geographic locations, breaking through geographical constraints and ensuring comprehensive and diverse data collection.
When conducting market research, companies can utilize IP proxies to obtain user reviews and feedback from across the globe. This not only improves the representativeness of the data, but also provides a broader perspective for analysis. In addition, the use of IP proxies can circumvent the access restrictions of some websites, making the data collection process smoother.
2. Data Cleaning
Data cleaning is an indispensable step in AI processing. Raw data often contains noise, missing values, and inconsistencies, and AI automatically identifies and corrects these problems through algorithms to improve the quality of the data. At this stage, the IP proxy also plays a key role, as it can help the AI system access different data sources and collect more diverse data, thus improving the efficiency of data cleaning.
3. Data analysis
Once the data is cleaned, AI applies various algorithms to analyze it. Machine learning and deep learning are the two main analytical methods. By training models, AI is able to recognize patterns, make predictions and generate insights. The role of IP proxies in this process is seen in enhancing data accessibility and accelerating analytics. For example, organizations can use IP proxies to access competitors' market data to help AI models perform accurate analysis to develop more effective business strategies.
In addition, AI can combine real-time data for dynamic analysis, such as monitoring changes in public opinion on social media. By using IP proxies, AI is able to capture a large amount of social media data in real time in order to react quickly and help companies adjust their market strategies.
4. Data Visualization
Data visualization is the process of converting complex data into easy-to-understand graphs or charts. Through visualization, users can quickly identify trends and patterns. ai can automatically generate visual charts to make data more readable. The use of IP proxies in this process ensures access to multiple data visualization tools and platforms, helping organizations to present data results and make decisions.
5. Data security and privacy
When dealing with large amounts of data, data security and privacy is an issue that cannot be ignored. ai systems need to comply with relevant laws and regulations to ensure the security of user information. Through IP proxies, enterprises can hide the real IP address and protect privacy during data collection, thus reducing the risk of data leakage.
Especially in cases where sensitive user information is involved, IP proxies can provide organizations with an additional layer of security to ensure the safety of data during transmission and storage.
The power of AI lies in its ability to process data, and IP proxies provide key support in this process. Through IP proxies, AI can not only access richer data sources, but also realize efficient data processing while ensuring data security and privacy. As technology continues to advance, the combination of AI and IP proxies will bring more opportunities and challenges to various industries. Enterprises should pay attention to this combination and fully utilize its potential to enhance business efficiency and market competitiveness.
0 notes
Text
Understanding Static Residential Proxies: The Ultimate Tool for Secure and Reliable Web Access
In the ever-evolving digital landscape, maintaining anonymity, security, and efficiency is paramount for businesses and individuals alike. One of the most effective ways to achieve this is through the use of static residential proxies. In this article, Static Residential Proxies we'll dive deep into what static residential proxies are, why they are essential, and how they can benefit you or your business.
What are Static Residential Proxies?
Static residential proxies are a type of proxy that provides a fixed IP address sourced from real residential locations. Unlike data center proxies, which can be easily identified and blocked by websites, static residential proxies use IP addresses assigned by Internet Service Providers (ISPs) to homeowners. This makes them appear as legitimate users when accessing websites, reducing the risk of being flagged or blocked.
Benefits of Using Static Residential Proxies
High Anonymity and Security
Static residential proxies provide a high level of anonymity because they use genuine IP addresses from real residential locations. This makes them nearly indistinguishable from ordinary users, ensuring secure browsing and data collection without the fear of being detected or blacklisted.
Consistent and Reliable Performance
Since these proxies provide a static IP address, they are ideal for tasks that require a consistent and reliable connection. This includes activities like managing multiple social media accounts, web scraping, accessing geo-restricted content, and running automated bots. The static nature of these proxies ensures a stable connection without frequent IP changes.
Bypass Geo-Restrictions and IP Bans
Many websites impose restrictions based on the user's location or IP address. Static residential proxies allow users to bypass these geo-restrictions by masking their actual IP address with one from a different geographical location. This feature is particularly useful for accessing region-locked content or services.
Enhanced Data Collection and Web Scraping
For businesses that rely on web scraping for data collection, static residential proxies are a game-changer. They allow you to gather data from various sources without the risk of being blocked. Since they mimic regular user behavior, websites are less likely to detect and block the IP addresses used by static residential proxies.
Ideal for E-commerce and Competitive Analysis
In the e-commerce sector, businesses often use static residential proxies to monitor competitor pricing, track product availability, and optimize their own pricing strategies. These proxies provide a seamless way to access competitor websites without triggering security mechanisms that might block or limit access.
Why Choose Proxiware for Static Residential Proxies?
When it comes to selecting a provider for static residential proxies, quality and reliability are crucial. Proxiware stands out as a trusted provider in this space, offering high-quality static residential proxies tailored to meet your specific needs. With Proxiware, you get access to a vast pool of genuine residential IP addresses, ensuring secure, reliable, and high-performance proxy services.
Key Features of Proxiware's Static Residential Proxies:
Wide Range of IP Locations: Access IP addresses from various countries and cities worldwide.
High Uptime and Reliability: Enjoy stable connections with minimal downtime, ensuring uninterrupted access to your target websites.
Fast and Secure: Benefit from high-speed connections with enhanced security features to protect your data and online activities.
Easy Integration: Seamlessly integrate Proxiware's proxies into your existing systems and tools with user-friendly interfaces and support.
How to Get Started with Static Residential Proxies from Proxiware
Getting started with static residential proxies from Proxiware is simple and straightforward. Visit Proxiware's website to explore their proxy services and choose a plan that suits your needs. Whether you're a business looking to enhance your data collection efforts or an individual seeking secure and anonymous web browsing, Proxiware offers the right solutions.
Conclusion
Static residential proxies have become an essential tool for businesses and individuals who need secure, reliable, and anonymous web access. Static Residential Proxies They provide the perfect blend of anonymity, performance, and flexibility, making them an ideal choice for a wide range of online activities. With a trusted provider like Proxiware, you can leverage the power of static residential proxies to unlock new possibilities in the digital world.
Ready to enhance your online experience with static residential proxies? Visit Proxiware today and explore their range of proxy services designed to meet your unique needs.
0 notes
Text
WordPress SEO optimization
WordPress is very nice and handy, but simply ‘installing WordPress’ is not enough these days. You need to ensure that you offer your users an optimal user experience and have a lightning-fast website.
In this lesson, we’re going to look at how to optimize WordPress (for free) as much as possible and with which plugins you can do this.
Read in Dutch: WordPress SEO optimaliseren
The WordPress checklist
Even before you start installing a WordPress website, there are important things to think about. Let’s make a checklist of important points to go through both before and after installation.
Web Hosting
The first key to a successful WordPress platform is setting up web hosting.
I love managing my virtual private server (VPS) and backing up my data, but there are times when you just don’t have time — and times for which you absolutely must make time.
So, when it comes to time, resources, and a website that anyone can set up, I like to choose a hosting solution that I spend a little extra money on.
If my site is slow and not responsive, my bounce rate will increase and users will drop out.
There is a huge difference between a site that loads one second versus ten seconds, and if you have the latter, you are more likely to lose users.
Engineers at Google discovered that a load time of 0.4 milliseconds is already long enough for users to search less.
Before switching to a hosting service, ask yourself these questions:
Do they provide support for plugins?
What kind of backup support do they offer?
Is there a staging area?
What is the volume of the bandwidth?
What operating system are they using? Linux? Windows?
What other sites are in your IP range?
Why is IP range important do you think? Well, for example, because you don’t want to get backlinks to your blog from the same IP address.
Suppose I have a server that is my own. I installed 4 different blogs on it, and started linking to all of them among themselves. Google then sees that the IP address is the same and will not award you any points for these backlinks because they are not natural.
At worst, it could even be seen as spam.
Some popular WordPress hosting companies:
Kinsta
My.host
Flywheel
Digital Ocean
SiteGround
Cloudways
Cloud86
Hostinger
Junda
Xel
SEO benefits

CDN (Content Distribution Network).
For anyone who wants to give their website that extra bit of speed, the power of a CDN (Content Delivery Network) is well known.
A CDN changes the way your site handles static content such as images, JavaScript, and CSS. CDN stores your static content to load pages faster, have shorter response times, and generally a faster website — which helps you rank higher in search engines.
Sounds cool? It sure is. I love anything that makes my site look faster than the effort I put into it.
After extensive testing, I have found that having a CDN is the easiest and fastest way to make your site look fast for search engines.
Some popular CDNs:
Cloudflare
MaxCDN
Amazon AWS
Google Cloud
Fastly
KeyCDN
Microsoft Azure
SEO benefits

An SEO-friendly theme
Let’s face it: Most of us are not concerned with finding the most SEO-friendly WordPress theme.
It would be nice, but in reality you probably spend more time picking out the most beautiful theme. Great appreciation for the business owners who make the effort to find an SEO-friendly theme.
Some points a good theme should meet:
Clean and fast code: With a clean code structure, you can reduce page load time and increase the crawlability of your pages.
CSS and Javascript files: With Google, less is more, and a limited number of CSS and Javascript files helps. Plus, you don’t have to worry about minimizing them later.
Simple layout: Simple design makes it easy for users to navigate from page to page.
Responsive: As we know, Google prefers responsive sites when searching from mobile devices, so choosing a responsive WordPress theme will give you a better overall user experience.
Schema Markup: Schema Markup tells search engines where the most relevant content is in your theme.
Some popular themes for WordPress are:
Divi
Genesis
Astra
Neve
OceanWP
TheGem
SEO benefits

Cache Plugin
A caching plugin transforms your website (especially on mobile) from “This is sloooooooow” to “Wow, that’s fast!” with one simple click.
Unlike most plugins, a caching plugin is rarely considered an unnecessary download.
This plugin takes your page load time to the next level, with improved website performance and converting dynamic content to static.
It may seem like a lot to handle (especially if you are not normally a plugin user), but this is one of those things for which you need to adjust your approach.
Some popular caching plugins are:
WPRocket
W3 Total Cache (My favorite)
Cache Enabler
WP Super Cache
WP Fastest Cache
SEO benefits

Permalinks
Permalinks in WordPress are great for many things — structuring your URLs with keywords, creating short links, increasing search rankings, and more.
Whether you just like to look at SEO-friendly URL structures, consider changing your URLs, or want to give a little boost to your search rankings, WordPress offers endless options for updating it.
Example of an SEO-friendly permalink:
googleseocursus.nl/how-to-optimize-wordpress/
Example of a not-so-SEO-friendly permalink:
googleseocursus.nl/?p=2043
The default WordPress setting is not SEO friendly according to Google, so adjust your settings accordingly.
The ‘Message name’ option is a safe choice because it makes URLs short
If you have a larger site, you may want to add dates or categories before the ‘Message Name’ option
Omit characters such as “&,” “?,” and “!” from the URL
Use hyphens (-) instead of dashes (_)
SEO benefits

Use an SEO plugin
Using an SEO plugin can take a lot of time off your hands, as many things are done automatically, and otherwise can be set up simply via a few clicks.
I always recommend using an SEO plugin, whether it’s the paid or free version.
Some popular SEO plugins are:
Yoast SEO
Rank Math
AIOSEO
Premium SEO pack
SEMrush
Squirrly SEO
Comments on articles
Newer versions of WordPress provide links in comments with a ‘nofollow’ attribute which is good news. This is because outbound links from your website to another website give off ‘link-juice’ and you don’t want this. So always make sure outbound links have a ‘nofollow’ attribute unless you want to pass on link-juice.
Spammers can also harm your Web site. For that matter, an abundance of spam comments in one blog post that offers nothing relevant to the topic can also harm your site. So keep spammers at bay.
Ultimately, your website will not perform well with spam comments.
Some steps you can take:
Do not allow anonymous posting
Use CAPTCHAs to prevent automated spamming
Use the ‘nofollow’ attribute
Do not allow hyperlinks
Use the Askimet plugin to monitor spam responses.
SEO benefits

Meta titles and description
It is incredibly important to have powerful titles and meta descriptions. This drives more traffic because people are more likely to click on your link in a search engine’s search results.
In WordPress, unfortunately, out of the box, you cannot enter meta descriptions. With a plugin like Yoast, however, you can. Yoast has a free version that lets you do everything you need already.
Make sure each article you write has a unique name and description to maximize your findability.
SEO benefits
Using a powerful title and description correctly makes users more likely to click through to your website.
XML sitemap
Having a sitemap is a necessary evil for SEO. A sitemap contains a list of all your posts and pages that search engines can easily interpret.
So make sure you always have a sitemap, so Google can index all your pages and not overlook any pages.
Depending on whether or not you use a plugin, and which plugin you use, you can usually find your sitemap in one of the following locations:
https://jouwsite.nl/wp-sitemap.xml
https://jouwsite.nl/sitemap_index.xml
Also, don’t forget to add your sitemap to Google Search Console. In the menu on the left, click on “Sitemap” and then enter the URL to your sitemap and that’s it.
Link to deeper pages on your website
Link as naturally as possible for the reader
Use a reasonable number of links (for example, 50 internal links for a 1,000-word blog is not reasonable)
SEO benefits

Internal links
Creating internal links is incredibly important for a host of reasons. Four of the most important reasons are:
It provides a clear structure within your website
You help search engines find your pages more easily
You provide the visitor with relevant information
You answer the user’s question to the best of your ability
Instead of creating links manually, you can also use a super handy plugin called “Internal Link Juicer.” You add your keyword to the page and the plugin will automatically create an internal link to that page in all other blog posts where the keyword appears.
Super convenient because you no longer have to search and spend time generating internal links yourself, this is done completely automatically for you.
SEO benefits
Internal links create a nice website architecture which makes it easy for users and search engines to find the different pages.
Also, with internal links, you pass on the “link-juice” and all pages will be considered “important.
Make use of alt tags
The beauty of WordPress is that you don’t need to know complicated HTML to edit your image alt tags.
Not only can you optimize images with a simple click, but you can also do this without adding a plugin.
Image alt tag recommendations:
Give your image file a name rich in natural keywords
Write a descriptive alt tag description for your image
Complete the alt attribute description of the image with your brand name if relevant
Make the alt tag no longer than 10 to 12 words
SEO benefits

Make use of header tags
It is incredibly important to use header tags. Not only does this make your text more visually appealing, but it also gives clarity to the visitor and to search engines that like to know what a piece of text is about.
Always provide your text with one H1, a few H2s, and other headers where relevant. Consider the semantics of the headers, so don’t:
<h2>Part</h2>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h1>Page title</h1>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p>
But just nesting neatly in order:
<h1>Page title</h1>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h2>Part</h2>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h3>Subcomponent</h3>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h3>Subcomponent</h3>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h2>Part</h2>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p> <h3>Subcomponent</h3>. <p> Lorem ipsum dolor sit amet. Vel omnis quisquam qui veniam rerum hic alias fugiat rem obcaecati error. Non consequatur accusamus eos autem pariatur et atque nulla! </p>
Also, remember to use your most important keywords in the headers and throughout your text. Use these keywords naturally and where relevant, don’t start writing to fit the keywords as often as possible.
SEO benefits
Using headers correctly makes for a more readable article. Users can quickly scan and understand what any part of the text is about.
It also allows you to create more “user engagement.
Use the canonical tag
No one likes having their content stolen by scrapers or other bloggers.
To combat this, you can enable the rel=”canonical” tag for pages on your blog. This tag tells search engines where to find the original URLs of the content on the site. This prevents problems with duplicate content.
When you use a WordPress SEO plugin such as Yoast, for example, this is already automatically done for you.
SEO benefits
Adding a canonical tag helps prevent duplicate content.
Create a Robots.txt
For those unfamiliar with the term, robots.txt is a file that tells search engines which parts of your site they should and should not view.
On search engines like Bing and Google, where websites abound, this method of directing the SERPs (Search Engine Results Pages) can save you a lot of time and money.
Block access to wp-admin in your robots.txt file
Allow all other quality content to be indexed in the robots.txt file
Add your sitemap to the bottom of your robots.txt file
Edit your Robots.txt file via the Yoast SEO plugin
Tools and then Editor
SEO benefits
You can prevent duplicate content with this. You can also specify exactly which robots can and cannot crawl, and which directories and files can and cannot be crawled.
Fix broken links
There is nothing more irritating than getting a 404 page when you think you have found the important piece of information you were looking for. Fixing broken links on your website is not only good for user-friendliness, but also shows Google that your website is of quality.
Use tools such as Google Search Console, Screaming Frog, Ubersuggest, or another good tool to find broken links.
SEO benefits
Fixing broken links improves the user experience, but Google also thinks it shows professionalism when you don’t have broken links.
Enable breadcrumbs
SEO beginners and professionals alike know that breadcrumbs are often forgotten, even though they add a lot of value.
If you have the Yoast SEO plugin installed, you can implement breadcrumbs in less than 2 minutes.
Simply go to Yoast SEO > Search Appearance > Breadcrumbs > Enabled.

Duplicate content problems in WordPress
WordPress simplifies life for small businesses, bloggers, and large news sites. In many cases, best practices are automatically applied, such as canonical links, and there are plugins for just about everything else you need.
But with the ease of publishing content and designs also comes a new problem: Duplicate content.
Duplicated content is a common reason why a WordPress website does not rank well.
While it differs from what we traditionally know in SEO as duplicate content (an exact copy of content, from text to code), it is similar and should be addressed.
Here are the four most common types of duplicate content problems in WordPress and how to fix them.
Tags
Tags are a big problem for many WordPress websites. When you tag an article, you create a unique page filled with other content you deem relevant.
The page shows snippets of articles or full articles. If the tag is the same as a category or main page on your main website (assuming it is not a blog), then you have now created a competitor for that page on your own site.
Tags are also often modified versions of themselves, leading to very similar content competing with themselves.
When this happens, none of the pages will rank well and can potentially reduce the value of the site.
Good news! Here’s a simple solution. You can either remove the tags completely, or you can add a meta-robots noindex dofollow tag.
The noindex dofollow tag indicates to search engines that this is a page with little content, but that they should follow the links and continue to crawl and index your site.
That way, search engines know that the page is not as useful as others and you have shown them how to discover your good content — the individual posts and pages.
Categories
Category pages often look like tags because they contain many posts and articles.
They have H1 tags that are the same as the articles, they do not always answer a question or provide a good solution since they are article excerpts, and they may not be suitable for people looking for answers.
Therefore, they are often considered content of little value.
However, there is an exception. For example, a WordPress website where the categories are dedicated to channels and niches within a channel.
A user looking for general information about a channel may find a category page very useful. Therefore, approach this differently than you would with a tag.
In this case, add a meta-robot index and dofollow tags, but also create unique titles and copy for the category to introduce it — and, if relevant, add schema as well.
Now you’ve helped define the types of searches and people to whom the page should be shown.
You may be rewarded by the search engines. Just make sure they do not compete with your core website pages if you are a business.
Competing Topics
A common problem when auditing WordPress sites is the lack of unique content.
Take food bloggers, for example. Yes, recipe outlines and other things can help differentiate recipes, but what if you don’t use them or didn’t know them to begin with?
If you have 20 recipes for apple pie, chances are many of them use similar wording and ingredients, which can cause competition.
Each recipe is unique and may serve a different purpose, but if you don’t make that extra effort, they may not stand out because they compete with each other.
In this case, you may want to create a category or subcategory for the cakes. If you can’t, revise them and add modifiers (e.g., traditional, modern twist, gluten-free, for parties, for large groups).
Next, start adding text (not necessarily at the top, because you want to quickly deliver the actual recipe to the user) about the final product. Make sure the text stays relevant to the topic and shows why, how, and where it is unique from the others.
Need other examples?
Have you ever made a themed gift guide or holiday post? Has anything changed except the year? Craft ideas for Mother’s Day? Romantic Valentine’s Day gifts for XYZ?
These are not unique enough. If you have multiple posts, they can all compete.
If you add a year to your title (e.g., 2016, 2017), people may skip you in search engines because you are not relevant this year. That’s where the strategies above can help.
Searches (Search Box)
You won’t encounter this problem as often, but searches on WordPress sites can generate URLs.
If someone externally links to one of these URLs, or if search engines can crawl and find them, they may be indexable.
Although you could try to automatically add a meta-robots noindex dofollow as with tags, this probably does not cover everything.
To address this problem, find the unique identifier that the search box URLs have in common. This is usually a “?” after the main URL.

Reduce photos
Google thinks it is super important that your website is super fast. Load times should be as short as possible to keep the user experience as high as possible.
You can resize your photos manually by using TinyJPG or TinyPNG, for example. Of course, you can also use popular plugins such as:
ShortPixel
Smush
EWWW Image Optimizer
Optimole
Imagify
WP Optimize
Finally, I want to point you to a very popular plugin. The plugin has more than 17 million installs and a high rating, so the quality is undeniably good.
In addition to cleaning up and optimizing your databases so they function better, WP-Optimize also offers:
Scheduled automatic cleanups of revisions, spam responses, content moved to the trash, etc.
Defragmentation of MySQL tables
Overview of database statistics
Image compression
Detailed control over specific optimizations
Reducing files so load times improve
0 notes
Text
How to Connect Visual Studio Code (VSCode) with AWS Lightsail using Remote SSH
In this article, we will explore how to connect Visual Studio Code (VSCode) with AWS Lightsail using Remote SSH. AWS Lightsail is a simple and cost-effective way to launch and manage virtual private servers in the cloud, while VSCode is a popular and versatile code editor. By combining the power of both, developers can enhance their productivity and collaborate seamlessly on AWS Lightsail instances. Let's dive into the step-by-step process of setting up this connection. Ready
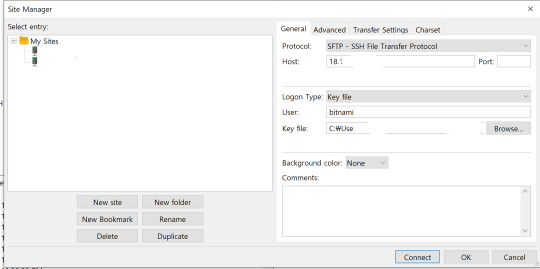
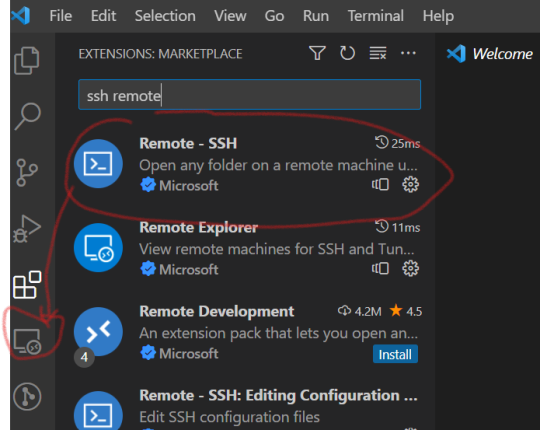
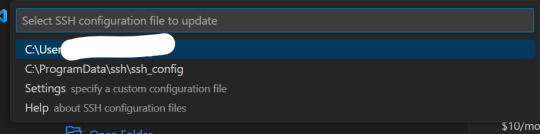
filezila HOST : You can find the host address in AWS Lightsail, and make sure to set a static IP. Key File : You can download the key file from AWS Lightsail. How? 1. Remote - Download SSH Extension from VScode Remote - When you download SSH, Remote Explorer is activated on the left.
remote ssh 2. Specify emails and folders in Remote Explorer For remote configuration, specify the folder to install e-mail and settings. Any email can be set, and the folder can be added by default, ` C:/User/...(username)/.ssh/config`. Let's set the folder and open the folder with Vscode.
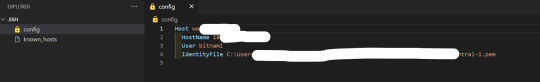
3. Config file settings If you open the above folder (.../.ssh/config), the config file is set. Enter values for HostName, User, and IdentityFile in the configuration file as shown below . Host xxxx.com HostName 18.XXX.XX.XX - AWS Lightsail 고정 IP User bitnami - (AWS Lightsail default username) IdentityFile C:UsersXXDocumentsGitHubXXXLightsailDefaultKey-eu-central-1.pem - Location where the Security Key obtained from AWS Lightsail is stored
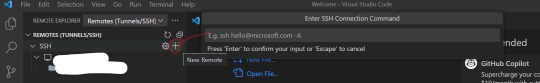
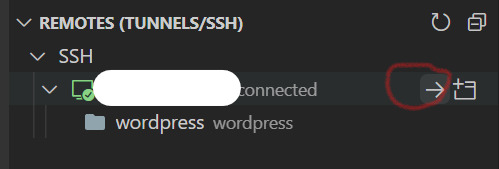
config 4. Remote folder connection If you click Remote Explorer on the left again, SSH is successfully connected. Click the connected SSH Host to open the relevant SSH. At this time, specify a folder. In my case, I found the folder location where Wordpress was installed and opened Wordpress.
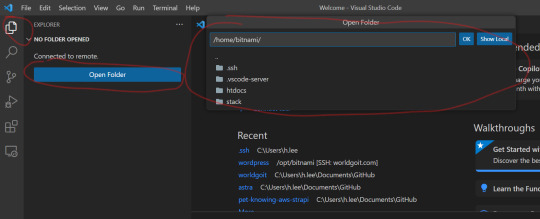
wordpress folder 5. Done In my case, by opening the folder where Wordpress is located, I can open Wordpress in Vscode through SSH connection. Because of this, it has the advantage of being able to easily find code or find files instead of the existing Filezilla.

Conclusion By connecting Visual Studio Code using AWS Lightsail and remote SSH, developers have the opportunity to efficiently code, collaborate, and deploy applications. Combining the simplicity of AWS Lightsail with the powerful editing capabilities of VSCode increases productivity and streamlines the development process. Its easy setup and user-friendly interface make it accessible to developers of all levels. Connect your favorite code editor, Visual Studio Code, with AWS Lightsail to get all the benefits of remote development. Take advantage of cloud-based infrastructure, secure connectivity and collaboration capabilities to further enhance your development workflow.
Frequently Asked Questions
- Can I connect to multiple AWS Lightsail instances simultaneously using VSCode remote SSH? - Yes, you can connect to multiple AWS Lightsail instances simultaneously. Each instance has its own VSCode window. - In addition to AWS Lightsail, is the VSCode remote SSH extension available on other cloud platforms? - Yes, you can use the VSCode remote SSH extension on other cloud platforms that support AWS Lightsail. - Is the Remote SSH extension available in the free version of Visual Studio Code? - Yes, the Remote SSH extension is available in both the free and paid versions of Visual Studio Code. - Are there any additional charges for connecting to AWS Lightsail via remote SSH? - No, there is an additional charge for connecting to your AWS Lightsail instance via remote SSH. Read the full article
0 notes
Text
How to Use a Static IP Address: The Easy Way
This article will guide you through the process of using a static IP address on your device. A static IP address is a fixed address that you assign to your device, which remains the same every time you connect to the network. It is different from a dynamic IP address, which changes every time you connect to the network. Using a static IP address has many benefits, including improved security, easier remote access, and better performance for certain applications. In this article, we will show you how to set up a static IP address on your device, whether it's a Windows PC, a Mac, or a mobile device. We'll also cover some common troubleshooting tips to help you if you encounter any issues along the way. By following the steps in this article, you'll be able to set up a static IP address on your device in no time, and enjoy the many benefits that come with it.
0 notes
Note
mingi + mafia au + you shouldn't have done that
mingi x gender neutral reader, 1.5k, thank you!!!!!!!!!!!
Part 2
you were meant to do great things. at least that’s what your parents, your teachers, even your best friend used to tell you over and over and over, beaming at you and whatever your newest accolade of the moment was. you had ranked number one in your class all throughout high school. you had your pick between the top three universities in the country. at graduation, you were on top of the world.
and then, things went downhill and never really stopped.
you’re still not quite sure when you’ll hit rock bottom, when you’ll finally get to turn your life around. or maybe, you missed that chance long ago. your father grew incredibly ill and your mother fell into debt. you worked too many part time jobs to help pay it off and your grades slipped. eventually, your father passed away and your mother was too busy dealing with grief and debt to really be a mother. you failed one too many classes and got kicked out of university. you still felt like you needed to help your mother pay off the crippling amount of debt and you indulged yourself in people you would have never given the light of day. and, to top it all off, your best friend slowly stopped answering your calls and your texts, drifting out of your life as if he hadn’t been there since you were both children, as if all those years and late nights and time spent together meant nothing.
it’s been years since then, but the mere thought of him still brings tears to your eyes, still makes your stomach curl with guilt, still makes you wonder what the hell you did wrong. during your brief phone calls with your mother, she would ask about him, and you never had the heart to just tell her. but, maybe she noticed your short answers because, nowadays, she’s stopped. nowadays, she’s even stopped asking for details about your job.
you’re grateful for that, really, because how the hell are you supposed to tell your sweet, tired mother that you work as a freelance hacker for an underground network of crime syndicates? it’s a bit of a mouthful, really, and you don’t think your poor mother’s heart can take such news.
sometimes, you wonder if this is your rock bottom. especially when you catch sight of yourself in the blackness of your screen before you boot up your laptop. the debt hasn’t stopped and you don’t think it ever really will because interest is a fucking bitch, but it’s become manageable. sometimes, you think about how you could go back to school. you could get decent work in an office somewhere.
but, you kind of like the thrill of this. you could go back, but you won’t. you know you won’t. you enjoy the rush of adrenaline when you receive a notification from one of your clients instructing you to extract information for them. you never ask too many questions about the whos. you only really care about the compensation. and this particular task has a price tag of several million won.
you raise your brow, stretching your fingers and cracking your back, already thinking about all the things you plan on buying with the extra money, grinning because the task in question is easy. almost too easy. you just need to root out a location from within a shit ton of security walls, as if whoever built it absolutely does not want anyone to find them. you grin and get to work.
~.~.~.~.~
you’ve seen your fair share of security systems over the course of your career and you’d rank this one as one of the tougher ones. still, you get in. you always get in.
and, for a moment, the IP address appears on your screen. the tension falls from your shoulders as you sit back admiring your work. for a moment, all is well.
until it isn’t.
your screen turns red, filling with white static, and it’s fucking terrifying. especially when it starts keening, high pitched, shrill, ringing in your ears, until it goes black.
you freeze, slowly peeking out from behind your chair, eyeing the computer in concern. you wonder if it’ll explode. white symbols fill the screen, cursor blinking. it takes a moment to register the message and when you do, your heart drops into the pit of your stomach, your breath catching in your throat. it’s your full name and your current location, written out in full, almost as if it’s mocking you. a chill runs straight down your spine and, for a moment, you’re frozen in your spot, crouched behind your computer chair. you were always cautious. you switched between VPNs constantly, you kept your work computer clear of anything and everything relating to your identity. this shouldn’t be happening. holy shit, you need to go. you shoot up, rummaging through your closet for the getaway bag you made long ago, just in case. you knew you needed a contingency plan when you started this. you just never expected to actually need it. but, now, you need to get out. you need a burner phone and cash and -
knock, knock.
the things in your hand slip, clattering all over the floor, and you flinch at the loud noise, glancing between the laptop and the door. you contemplate jumping out the window, but you’re on the third floor and you doubt that -
beep. beep. beep. click.
the front door sits ajar and the hairs at the back of your neck stand on end. for a beat, you are so terrified you aren’t sure if you can even move. then your brain jumps into overdrive. you need something to defend yourself with, though. you’re frantic when you yank the lamp off the table beside the couch, scurrying into the kitchen.
it’s so quiet you could hear a pin drop and you hate it. you swear your own heartbeat can be heard in the quiet of your apartment. there is no force used, you notice, as if your brain is clinging to the tiniest details as a way to keep calm and collected. nothing about the knocking at your door nor the technical break-in is forceful or loud, and it’s somehow worse than if someone had just kicked your door down and stuck a gun in your face. you lift the lamp over your head, just as you hear the creak of the front door opening and the faintest of whispers. you hear footsteps, slow and measured, so fucking casual, echoing throughout your apartment and your grip on the lamp tightens. it doesn’t take long for the footsteps to approach the kitchen. you don’t even try to catch a glimpse of the intruder; the moment they step into reach, you bring the lamp down over their head with a loud thud.
a man cries out in pain - the loudest noise you’ve heard yet this evening, the sound making you flinch - and you back out of the kitchen, nearly tripping on your own feet, not even bothering to watch the man crumple to his knees. you just hope he stays down.
but, you didn’t account for the other voice, the other footsteps.
you yelp when you run face first into a sturdy wall of a person, thrashing as their fingers wrap around you, holding you steadfast with such ease. you think, holy shit, holy shit, I don’t want to die, while you’re being dragged and tossed onto the floor of your living room. you hit your head too hard, vision swimming, pain shooting through your skull, but you manage to put space between you and where you think the intruders are. you stare, wary, terrified, thinking, thinking, thinking. you open your mouth, ready to scream, but there’s a pretty boy with dark eyes and sharp features staring down at you, head tilted, a gun cocked in his hands.
he says, “scream and i’ll shoot.”
you didn’t account for three intruders, the man with the gun, the one you hit over the head with the lamp, and whoever is helping him up. your eyes flicker past the kitchen entrance, frantically searching over the man’s shoulder for an opening. you notice the lack of face coverings - from what you’ve picked up throughout your years of working in the underground, you know that is not a promising sign, it usually means they don’t plan on letting you live long enough to expose their identities - and you scoot further back until your back hits the wall. the man’s eyes and gun follows you, a kind smile playing on his lips, out of place in a situation like this. it’s just as unsettling as the lack of force behind their break in, the silence with which they work under.
two people emerge from your kitchen, the man you presumably hit over the head grumbling under his breath while the other one holds him up, towering over him. the man with the gun speaks up, pulling your attention back to him, “now, tell us.” he steps forward and you have nowhere to go. “why exactly were you trying to hack into our systems? who put you up to this?”
“I…I don’t know.” your voice comes out steadier than you expected and you’re grateful for that. the man with the gun sighs. you glare, you can’t help it. “I really don’t know. I make it a point not to know who my clients are.”
the man sighs, yet again, and somehow that angers you. you watch as he steps back from you, gun still directed at you, turning his torso to face his friends. your gaze flickers up to them and you -
“holy shit.” your fingers dig into your palms, your eyes locked on him.
because it’s song mingi.
memories that you have spent years trying to forget floods into the forefront of your mind. birthdays spent with him, his soft smile, the first memories you’ve had with him, playing tag in your parents’ house. the way he sometimes insisted you be the big spoon when the two of you cuddled, laughing at the way you could barely contain his long limbs in your arms. the way he cried into your shoulder when his family dog had to be put down. the promises of forever he made with you. his laugh, the way his eyes would scrunch up and his smile would get so big. memories and feelings and everything just floods through you and you can feel tears prickling at your eyes, your chest heavy, words stuck in your throat.
he has red hair now, his arm curled around the man you hit over the head. still, he hasn’t changed much. he’s taller, broader, older, but he is the same in so many ways. his eyes, though, are different. the light and love they always held has dimmed and there’s something dark about his gaze, something ancient and sad and irredeemable, something broken. your breath catches at the sight, at the way his eyes widen ever-so-slightly, before they narrow, at the way you can’t read his face easily like you used to be able to.
“mingi?” you speak, then, your voice less steady than before, barely audible really, if it wasn’t for how quiet the apartment had become. both his friends startle at that, but your eyes are on him. there is a mix of anger and relief and yearning that curls in your chest. you’ve missed him, you realize. you’re angry because he left you so long ago, that he is standing here now, on the side of the man with the gun pointed at you, and you should be mad, should be screaming, but you missed him. maybe this is your rock bottom.
for a moment, mingi softens, eyes returning to the way he used to look at you before. for a moment, you can pretend he still cares about you.
but, only for a moment.
his gaze steels, his lips pressing into a thin line. he slips his hands off his friend, stepping towards you and there is an aura surrounding him that is unfamiliar and, frankly, terrifying.
he crouches, until he is at eye level with you. you hold your breath. he says, “you’ve built a very notorious reputation for yourself you know. makes sense, though, you’ve always been the greatest at whatever you put your mind to.”
there’s something so very foreboding about the way he says that. you blink, manage to respond, “why are you…what do you want from me? what are you…what are you going to do to me?”
mingi looks at you like you are a stranger and you think, no, this is your rock bottom. he leans in close, red hair falling over his unreadable eyes, elbows resting on his knees. the world falls away and all that is left is you and mingi, mingi and you.
he breathes, “hacking into our systems? you really shouldn’t have done that, sweetheart.” then he tilts his head and stares you down. you cannot breathe as he tacks on, “now we have to make an example out of you.”
#song mingi#ateez#ateez angst#ateez scenarios#mingi angst#requests#i hope u like it!! maybe i want to make a part 2 but idk TT#Anonymous
179 notes
·
View notes
Text
Control | Jihoon | Part 1
a.n. originally posted on my shared blog, but moving everything here to my main blog.
// unedited
1 | Next
The static of the radio echoed throughout the room as the blinking computer lights filled your eyesight. Typing away at your computer, the exaggerated sigh left Mingyu’s lips.
“Are you even smart enough to do this?” You scoffed.
You? Smart enough to hack into the opposing mafia’s database to secretly download their mission plan for the next two months. Of fucking course, you were smart enough. You were Jeon Wonwoo’s younger sibling for god sake.
It had been a thing since you were younger that, whatever Wonwoo did, you followed. So you learnt a lot of stuff whilst growing up, but once you found out more about computers and their systems you did everything you could, to learn everything you could.
“Shut Up Mingeww and let me focus” you sniggered, you knew the use of that nickname would just piss him off more.
“I swear to god if you weren’t Wonwoo’s younger siblings I would have decked you by now” Mingyu stresses, crossing his arms over his chest and tapping his foot against the floor. Rolling your eyes, you let the comment pass over your head as you knew Mingyu never would do that, especially not to someone on his own side as well.
“I have to find a backdoor in their systems, make sure if they do even notice that someone’s hacked in that it jumps to at least a 1000 different IP address very ten minutes or so, so it can’t be tracked back to us” You explained, you threw a look over your shoulder at Mingyu and raised an eyebrow. “And let me guess, you want me to try and put some sort of spyware into their system too”
Mingyu blinked for a moment, he almost looked confused- before snapping out of it and nodding his head.
“If you can do it without getting caught then sure” You let out a sigh, before linking your fingers and cracking them in front of you.
“It ain’t going to be easy, but trust me, I’m the one for the job” Mingyu clicked his tongue as he ruffled your hair.
“You really are Wonwoo’s sibling aren’t you?”
“Without a doubt my dude, without a doubt”
“Minghao will probably be by later to check up, Wonwoo is still out with DK checking things out” you hummed, waving your hand up.
That was his queue to leave. To leave you to do what you do best. Hack the shit out of the rival mafia’s database. Mingyu rolled his eyes at you but leaves quietly anyways. Shutting the door behind him, he lets out a small sigh.
“You better get this right kid”
You had spent your whole life in the mafia, yours and Wonwoo’s father was the leader of the South Side Mafia, but when an argument between your father and his right-hand man caused your father to get shot and killed, the mafia got split into two. The side that supported your father and the side that supported his right-hand man.
Wonwoo quickly took over your father’s position, growing up quickly considering he was still only 18 at the time, whereas you were 16 at the time. Wonwoo, for the most part, tried to hide you well from people outside the Mafia. It was safer for you to stay secrete than to be in harm’s way.
You understood that, if anything, staying secrete helped you with your job of hacker/computer expert.
The other side, on the other hand, got taken over by Choi Seungcheol, the too cocky for his own good son of your father’s right-hand man. Seungcheol was handsome, he knew that too well. He had an ego the size of a double-decker bus. Even though it had been three years since the initial split of the Mafia, the war- if you could even call it that- was still ongoing.
After a few hours, you managed to bypass their firewall and not long after that, you bypassed all their sensors. You raised an eyebrow to yourself as you clicked through some of the files. You bite your lip as you continued, the whole process seems too easy.
You loved an easy job, but this? This was too easy and too easy was risky.
You continued on, cautiously of course. Clicking through files and going through walls of security, you start to locate the file of their plans for the next few months.
The door opens behind you, which doesn’t surprise you and Minghao appears beside you with two large cups of coffee.
“Thought you need this” He chuckles, placing a coffee next to you and moving to the small couch of coffee table that was in the room. Humming, you send him a smile and quickly pick up the large cup and sip at it.
“Thanks, Hao” After you place it back down and go back to work. Letting out a sigh, you turn your head to Minghao and send him a look. “Hao, I think there’s something off about this”
He raises an eyebrow and pulls up a chair to sit next to you.
“What do you mean?”
“This was so easy to hack into, this was more than easy, it was easy and quick and for hacking that isn’t always a good thing,” Minghao chuckles slightly, sending you a look.
“You have a way with words don’t you” With a blank you stare at him.
“This really isn’t the time Hao” Chuckling again, he motions you to continue. “Most big organisations, have their things to the most part un-hackable, but your favourite person here isn’t just anyone, so normally things like this can take at the least a day or two to hack into, because of their firewalls and their systems, but do you know how long this took to hack into?” You asked, pointing at him. He raised an eyebrow.
“Half a day?”
“No! Three hours!” You hold up three fingers to exaggerate.
“Maybe you’re just too good at hacking” You laughed, flicking some hair over your shoulder.
“I may be good, but I’m not that good” Minghao keeps silent and I soon continue to talk. “Anyways, this is way too quick to be able to hack in a big organisation like this, especially a mafia”
“Yeah, I understand what you’re saying”
“I think something’s up, I can upgrade the amount of IP address it switches to so it never gets back to us, but I still think something’s fishy about this” Minghao nods, agreeing.
“Upgrade the amount of IP addresses, if you can get what you came for and get out of it, make sure there’s no way to trace back to us” You nod at what Minghao was staying and quickly get on it.
“I’ll get it done before you can say My I”
“Okay then, M-” You cut Minghao off with a laugh and lean back in your chair.
“Done!” Minghao looks at you with a shocked expression and you send him another blank look. “What? You think I couldn’t really do it?” Chuckling, he shakes his head.
“You amaze me every time”
“Well you amaze me too” Turning back to your computer, you finishing doing your final things and kept the machine next to your computer that changed the IP address on. Once you had successfully shut everything off, you turned back to Minghao and smiled at him. “Now where’s my brother?”
Seungcheol raised the cigarette to his lips and took a long drag. He sat with his feet up on his desk and a pair of sunglasses covering his eyes. To most, this would seem unprofessional, but to the rest of the mafia, this was just your typical Tuesday lunchtime.
Seungcheol was professional when needs are, but on days like today, when he had no meetings some time to himself in the office, well he was going to do it his way.
Jihoon sat across from him, a blood stain on his collar and his gun holstered on his hip. He had unbuttoned his waistcoat once he had gotten back to Seungcheol’s office and leant his head back to look at the ceiling.
Seungcheol leant forward, offering Jihoon a drag from his cigarette with Jihoon declined. Seungcheol scoffed slightly as he chuckled.
“You can kill people, but smoking is what you say no to” Jihoon raises his head to look at him.
“Because you’re letting the stick kill you and you know I only go for the people who deserve it" Seungcheol takes a long drag again and releases it slowly.
”But my younger assassin friend, who can you tell who deserves it or not?“ This time Jihoon scoffs, sending a judging look to Seungcheol.
”Like you’re one to talk, you know I get most of my jobs from you right?“ Seungcheol waves him off as he takes another drag.
”Let’s not think about that right now and let’s just contemplate the meaning of life or something“ Jihoon raised an eyebrow.
”What drugs are in your cigarette?“ He asked, making Seungcheol laugh.
”Nothing is in there, I promise“ He hands out the cigarette ”you can even try it yourself to see" Jihoon just rolled his eyes and denied.
“Yeah, no thanks"
”Your loss“ Seungcheol mutters, leaning back in his chair.
The door swings open and Soonyoung pops his head through the gap in the door. His usual large smile covered his face and his brown hair fell to just above his eyes. Seungcheol moved his feet from off of his desk and turned to Soonyoung’s direction.
”What do you want?“ Soonyoung’s smile for bigger as he laughed.
"I hate to break the party, but you’ll never guess what our software just picked up” Seungcheol gasped, putting out his cigarette in the ashtray on his desk.
“You haven’t"
”Oh, but Boss, we have“ Soonyoung smirked.
”We caught the fly in the trap“ Seungcheol’s smile dropped and he hissed throwing a hand up in Soonyoung’s direction.
”Come on Hosh, what have I told you about using those codes“ Soonyoung sighed, looking away.
”Not to use them“
”And what do you keep doing?“ Seungcheol asks, pushing his lips into a straight line. Soonyoung just sighs as he replies.
”Using them“ Jihoon covers his mouth as he coughs, looking between the two.
”You were on about Hosh?“ Soonyoung’s eyes widen and he nods his head dramatically.
”Ah yes!! Our systems picked up something earlier and I think you’ll want to see what“ Seungcheol picked himself up out of his chair and raises his hands to the roof.
”Then let’s get going shall we?“ He turned his head to Jihoon. ”Ji, you come with"
Jihoon doesn’t bother to argue and just stands up. Running a hand through his dyed red hair, he waits for Seungcheol’s orders.
“Boys, this might be our day!” Seungcheol cries happily, slapping Jihoon on the back and they follow Soonyoung out of the room.
“Isn’t every day our day though?” Soonyoung asks confused and Seungcheol just sighs.
“That it is Hosh, that it is”
They quickly made their way to their tech room, where Soonyoung was normally centred. Soonyoung was their tech guy, their number one hacker. He could spot a bug from a mile away and decode it and send it back in less than ten minutes. Jumping into his chair and crossing his legs, Soonyoung turns himself to his computers. He started to click on some files before a large black document with a bunch of long different codes in red appears on the screen.
“What’s this?” Jihoon asks, leaning against the back of Soonyoung’s chair.
“Well this you see my assassin best friend is a map"
”A map?“ Jihoon asks, unconvinced. Soonyoung hums.
”Well you see, a few days ago I created and set up this trap, which I call the fly trap by the way, and basically what it does is it makes it seem easier to hack into our systems when in actual fact it’s all false!“ Soonyoung explained, ”from what I heard about their hacker, they should have noticed this straight away, but for some reason they didn’t, maybe they weren’t as smart as I thought they were“ Soonyoung pouted.
”Just get on with it Soonyoung“ Seungcheol panned and Soonyoung nodded his head.
”On it boss, anyways I basically set up a fake system to trick them and I set up all fake documents for them to take and tada!“ Soonyoung cries, clicking on a few buttons and the screen changes into a large map. ”We are in the process of knowing where they are“ Seungcheol clicks his finger and pats Soonyoung on the shoulder.
”God Soonyoung you’re amazing“ Soonyoung smiles, proud of himself.
”They set up so many IP addresses to bounce around, but so it might take a while to directly locate their main source of tech“
”Damn Hosh, you’ve really outdone yourself“ Jihoon compliments.
”It’s all in a day’s work of Hoshi Prince“ Seungcheol and Jihoon just stare at him.
”You know no one calls you that but you right?“ Seungcheol asks, to which Soonyoung nods his head.
”That’s what makes it even more awesome“ Seungcheol shook his head, before turning to Jihoon.
”If anything comes of this-…” Soonyoung cuts him off with a whine.
“This will work!” Seungcheol sighs, rolling his eyes before continuing to talk.
“Soonyoung here will call you with the address, I expect you to take care of this” Jihoon stays silent, just watching Seungcheol as he thinks.
“I’ll get back to you on it,” Jihoon says, waving him off and turning to walk away. After a few steps, Seungcheol calls after him.
“You know if you don’t do this I’ll just get someone else to” Jihoon sent a look over his shoulder.
“And I said I’d get back to you on it, so see you later”
“So you know what you’re doing?” Wonwoo asks, you simply reply by nodding your head and sipping an ice tea.
“I know what I’m doing brother, don’t worry about it” Wonwoo looked blankly at you. You noticed his fist tightened slightly.
“You know I worry about you and you can’t stop me from worrying” You sighed quietly, placing the ice tea down on his desk. You moved slightly so you were sitting on the edge of your seat and placed a hand on his.
“Won, I’m 19 now, I’m not a child you can trust me"
”I know I can trust you, but I just don’t want anything bad to happen to you“ You smiled as you gently squeezed his hand.
”I’m strong, I can fight off anything“ you giggle, releasing his hand and bringing up your fists in a fighting stance. ”They’re going to wish they never tried to go against me“ Wonwoo laughed, shaking his head before running a hand through his hair.
”You really are our father’s daughter“ Wonwoo chuckles, sending you a smile which you return.
”And you are our mother’s son“ Wonwoo sighs, standing up from his chair and motioning to the door.
”You should get back now and start working“ you nodded your head and stood up too.
”Okay Won“ Pulling your big brother into a hug, you both stand there for a moment before pulling away. ”I’ll get right on it“ He patted your head and smiled down at you.
”I’ll come to see you later okay,“ He says. ”I’ll have Mingyu drive you home“ You roll your eyes and huff slightly.
”Mingyu seriously? Why him?“ Suddenly the door opens and Mingyu enters the room.
”Hey! It’s not like I want to drive you back either, so shut up pip-squeak“ You make a face, sending him a look.
”It’s not like I’m short, you’re just freakishly too tall" Mingyu let’s out a whine, rolling his eyes and looking to Wonwoo.
“Why are you asking me to do this?” Wonwoo laughs, as he watches you both.
“Because you’re my best friend and their my younger sibling, who else would I want to look after them?” Mingyu rolled his eyes again, before muttering a reply.
“I’m only doing this because you said I’m your best friend” Mingyu grabbed onto your wrist before dragging you out of the room. “See you later Won"
”Bye guys“ he laughs, waving you off and going back to sit in his seat.
”Ow! Ow! Ow!“ You repeat, tugging at your wrist. ”Oh wait,“ you ask, getting Mingyu to sigh and stop, also making him let go of your wrist. ”Can we go to McDonald’s on the way back?“
”Oh my god,“ Mingyu says, it was evident in his tone he wasn’t the slightest bit impressed. Happy that your wrist had freedom again, you skip next to him with a large smile on your face.
”Well can we? Can we? Can we?“
”Maybe if you shut up“
You silently giggle to yourself and link your fingers together behind your back. You and Mingyu silently walk until you reach the main elevator and he clicks the call to buttons. For the next few moments, silence continues until the pleasant ding of the elevator arriving is heard.
The doors part and your mouth drops slightly at the sight.
A young looking man, with seemingly dyed red hair and he, had a pair of large sunglasses that covered his eyes. He had on a white button-down shirt, and black trousers with a black waistcoat to match.
You blinked as he nodded his head to Mingyu and looked at you for a single moment before walking past and heading down the hallway. Your mouth dropped more as you gaze followed him. Mingyu just rolled his eyes and grabbed onto your wrist again.
”Oh come on“ You opened and closed your mouth a few times before turning to Mingyu. He leant over and clicked the ground floor.
”Who was he?!“ You felt your cheeks blush. Mingyu shrugged, crossing his arms over his chest.
”I don’t know, probably just someone to see Wonwoo, why?“
”Because, he was the most beautiful person I’ve ever seen“ you gasp, looking at Mingyu with wide eyes. He scoffs, motioning to himself.
”Sorry, but you must be blind as I’m the most beautiful person you’ve ever seen“ You clicked your tongue and sent him a look.
”Oh hunny, I think you’re going blind“ you patted him on the shoulder. ”I think you need to go get your eyes checked“ He forcefully moved his shoulder and your hand fell.
”No, I think you’re the one who needs their eyes checked“
Wonwoo raised his head at the sound of a powerful knock at his office door. Clearing his throat, he spoke.
“Come in” The redhead pops his head through the gap in the door and cracked a smile. Closing the door behind him, he sat in the seat across from Wonwoo. “Ah, Jihoon, what are you here for?”
Jihoon didn’t say anything for a moment, he just silently undid his waistcoat and leant his head back and let out a deep sigh. Wonwoo raised an eyebrow, but knowing his friend, he didn’t think too much of it.
“So, what’s going on now?” Picking his head back up, Jihoon stared at Wonwoo letting out another sigh.
“Soonyoung’s a lot smarter than he seems” Jihoon chuckles, “He’s designed this new tech that fakes a software to make it seems like its easier to hack and with that, he can get passes the IP scrambler” Wonwoo gulped as Jihoon continued. “And you know what that means? He can get original IP addresses and could you take a wild guess at who their first target is?”
“(Y/N)” Jihoon clicks his fingers and points at Wonwoo.
“Bingo” Wonwoo sighs, running a hand through his hair. “I’m lucky they haven’t even noticed that I know you”
“Wait,” Wonwoo says, looking up at Jihoon. “Do they know it’s them, or who they are?” Jihoon shakes his head.
“Not yet, they don’t know it’s them yet and I doubt any of them remember you have a sibling” Wonwoo becomes silent, he had a thousand thoughts rushing through his head at a mile a minute.
“Why are you telling me this?” Jihoon didn’t reply instantly, he just fiddled with his fingers until he found the words.
“Because when Soonyoung finds out their location Seungcheol wants me to do whats in my job description” Jihoon explains. Wonwoo’s hands turn to fists on his desk table.
“Would you, would you do it?” Wonwoo asks, sending a look to his friend.
“You know if I don’t do it, Seungcheol will just send someone else” Jihoon responds, his voice showing all of his emotions.
“You know that doesn’t answer my question” Jihoon stays silent again, a frown covering his face which matched Wonwoo’s. “Jihoon…”
“If there’s a way to get out of it then sure, I would get out of it, but you know how thorough Seungcheol makes everything and how he checks everything, it wouldn’t be easy to get past him” Wonwoo’s face changes from a frown to a smirk.
“But it’s not impossible” Jihoon’s mouth opens slightly in shock, he blinks for a moment.
“Wonwoo, what are you planning in your head?”
“A full fi-...” Wonwoo got cut off by the sudden bang of the door slamming open and Mingyu panting as he stands there. Both suddenly both standing, they turn to him. “Mingyu, what’s going on?”
“(Y-Y/N),” He gasps for breath, “They’re hacking their computer” Wonwoo’s eyes go to Jihoon and he shrugs in response.
“That’s probably Soonyoung, once he has their address he’s meant to call me with the details” Mingyu scoffs, now with his breath back.
“See this is the problem with you and being on both sides, you’ll do whatever you’re told” Jihoon scoffs too, rolling his eyes before spitting an answer.
“I’m here to warn your fucking asses about them so shut your face” Mingyu scoffed again, rolling his eyes and crossing his arms over his chest. Wonwoo hissed.
“This isn’t the time for you two to be arguing right now, we’re going to them and we are finding a way to get away with fooling Seungcheol any way we can” Wonwoo explains, picking up his gun from the drawer and putting it into the holster on his back. “And if either of you tries to argue I’m shooting you myself”
You typed at lightning speed as you did whatever you could to keep whoever was trying to hack you from hacking you. You chewed on your lip as you concentrated and didn’t try to move an inch in case you lost focus.
“Whoever you are you fucking piece of shit-…” You mumbled to yourself until you got cut off.
“Watch your language” You hadn’t noticed the door open and Wonwoo, Mingyu and Jihoon appear.
“Well if this piece of shit didn’t try and hack my computer I wouldn’t have to call them a piece of shit now would I?!” You spat. It was easy to tell you were annoyed- more than annoyed, extremely pissed off. Jihoon chuckled and you raised an eyebrow at the unfamiliar chuckle. Only moving your eyes you saw the head of red hair and gasped. “Mingyu, you fucking asshole, why did you bring the hot guy, do you want me to lose focus?!”
Jihoon covered his mouth to try and cover up his laughter as Mingyu rolled his eyes and sent a glare to the back of your head.
“I’m sorry that I make you lose focus” Jihoon laughs, this time making you roll your eyes.
“Not the time hot guy” Jihoon tried not to laugh again and Wonwoo just sighed, facepalming.
“This really isn’t the time for this” Wonwoo says.
“Hate to break it to you big brother, but I pretty much just said the same thing,” you shrugged. “Just different phrasing”
“Anyways,” Wonwoo starts, “Can you stop Soonyoung from hacking you?” You ran your tongue over your teeth in annoyance as you spoke.
“So this bastard is called Soonyoung then huh” A smirk covered your face and you started typing quicker than the pace you were typing before. “You want a fucking show Soonyoung, I’ll give you one”
“Don’t do anything too stupid now” Wonwoo says, making you laugh.
“When have I ever done anything stupid?” Wonwoo raised an eyebrow and sent you a look.
“Do you really want me to answer that question?” You took in a deep breath but responded.
“Yeah, you probably shouldn’t”
The room went silent- well as silent as it could go with how fast you were typing away and you giggled to yourself as you repeatedly hit a few buttons. Mingyu sent a look to the back of your head and looked to Jihoon and Wonwoo, with both of them shrugging in responses, he spoke.
“What are you giggling at?”
“He wanted a show, so I sent him a bunch of jumpscare clips to try and slow him down” Mingyu gave you a stank glare, judging you completely.
“Couldn’t you think of something better than jumpscares?”
“Mingyu,” You started, your tone evident for him to be wary of what he said next. “Shut the fuck up before I spread your internet history online”
“Better do what they say” Jihoon laughs and Mingyu only sends him a glare.
After another few minutes of silence, you hit your keyboard, but still, continue to type.
“No! No! No!” You yell as large black box appears on your screen. You gasp, moving away from your computer. “H-He hacked in, h-how did he?” You stuttered, before trying to do whatever you could to get your computer working again. “I have no control”
You turn to the three boys and see they mirror the same expression you’re wearing. Wonwoo’s eyebrows furrowed together and he let out a sigh. Quickly turning to Jihoon, Wonwoo grabbed his arm.
“How long will it be until he calls you?” You didn’t understand what Wonwoo was going on about and just like how he had grabbed Jihoon’s arm, you grabbed his.
“What are you on about?” Wonwoo turned to you and moved his arm so you’d release it.
“Not now (Y/N)” He then turned back to Jihoon. “Well?”
“I don’t know, it could be anytime now” Your eye flicked between the two as your brain raced to try and put together the puzzle of what could be going on.
“We need to do something now” Wonwoo responds
“It’s not going to be easy, you have to know that”
“What’s going on?!” You yell sending your brother the worst look you could muster. “I swear to god if you don’t tell me right fucking now” Wonwoo went pale as he turned to you, you raised both of your eyes and let out a sigh. “Just tell me please”
“Soonyoung, who’s apart of the other side made a new software and that was to catch us- you- in a trap to be able to locate you and to try and overtake us” Wonwoo explained and it left like all the air left your lungs. “They’re planning on killing whoever is behind the screen”
“W-What?”
With that, Jihoon’s phone rang, the loud music blared through the deafening silence. Jihoon took the phone from his pocket and stared at it for a moment before nodding to Wonwoo.
Incoming call; Hoshi Answer Decline
”Who is that? Why is this happening?“ You rushed, but before you could say any more, Mingyu rushed to your side and covered your mouth with his hand. Your cried became muffled against Mingyu’s hand and Wonwoo placed his hands on your shoulders to try and calm you down.
”You need to stay silent, you need to trust me" You went silent, no matter what happened, no matter what your brother said or did you always trusted him. He turned to Jihoon and nodded. Jihoon picked up the phone and placed it next to his ear.
“Hello?”
“Woozi! Dude! I think this has been the most fun time hacking I’ve had in a while!” Jihoon sighed and rolled his eyes.
“Hosh, just get to the point already”
“Oh yeah yeah sure okay, anyways I hacked in and got the address for you, make sure to get it done by the end of the day, you know what Cheol’s like,” Soonyoung said.
“Sure, just send it here”
“Will do, talk to you later” Soonyoung cheered before clicking off the call. Making sure the call had ended, it wasn’t a second later until Jihoon’s phone beeped again and the text from Soonyoung appeared.
“By the end of the day” Jihoon looked at Wonwoo "that doesn’t give us much time“ Running a hand through his hair, Wonwoo starts to mutter to himself.
”We have to find a way,“ Wonwoo says, before repeating it. ”We have to find a way“
With Mingyu’s hand still covering your mouth, you blinked rapidly as you felt your eyes begin to well up. You hated seeing your brother so frantic, especially over you. Especially now over what might be the lead up to your death. Feeling the tears run down your cheeks and onto his hand. Mingyu turns you around and sends you a look.
”Nothing is going to happen to you, don’t worry so much pip-squeak“ Mingyu chuckles to try and brighten your mood, but you just nod.
You already knew who Jihoon was, who he is. It didn’t take long for it to click into your brain after he got the phone call, you knew he was the one they were planning on sending to kill you, but he was here, he had been all this time so sure he wasn’t going to… right?
Everything was going to work out like Mingyu had said. Everything was going to be fine. Wonwoo clicked his fingers and looked at Jihoon with a smile.
”I think I figured it out, I think I know a way this could work“ Jihoon blinks and motions for him to continue. ”Seungcheol will never realise a thing“
Jihoon waited for the elevator to ding once it reached the top floor and let out a silent breath of air as it did. Looking up to the camera in the corner of the elevator he winked, knowing Soonyoung would probably be watching.
Exiting the elevator, he swiftly makes his way to Seungcheol’s office, knowing twice before entering.
Seungcheol was sat like he usually was, his feet up on his desk and a cigarette in between his fingers.”Ah! Jihoon! My assassin friend!“ Jihoon chuckled, raising an eyebrow as he sat down in the chair across from him.
”What are you on now?“ Seungcheol smiled, taking a long drag before puffing out the smoke quickly.”Its new in from out west, it’s beautiful stuff“ Seungcheol laughed, before holding his hand out for Jihoon to take. ”Want some?“
”No thank you“ Jihoon declines, making Seungcheol roll his eyes.
”Always the same old Jihoon“ Another drag. Another puff of smoke released. Sitting up and moving his position, he stares at Jihoon for a moment. ”I notice you’ve dyed your hair again“ Jihoon nods, running his free hand through his hair.
”You know my routine,“ He says simply.
Dying his hair after every kill.
”So that means you’ve done it?“ Seungcheol asks and Jihoon responds by throwing a file onto his desk. Seungcheol chuckled, picking up the folder and flicking through it.
”That what you mean?“
”You’re simply amazing, Ji, this is why you’re the best in the business,“ Seungcheol said, picking up one of the photos and holding up as he examined it. ”Your work is honestly perfect“
”Well, I do what I know best“ Jihoon laughs. ”And this is what I know best“
”It certainly is“
Jihoon silently unbuttoned his waistcoat and leant his head back as he let out a sigh. He sat like that for some time, just thinking. It wasn’t too much time before Seungcheol coughed, making Jihoon lift his head.
”Jihoon, you can go now, I have a new business meeting to attend about the new drugs from out west“ Seungcheol explained, he sent a smirk Jihoon’s way. ”If you want any, all you gotta do is ask“Jihoon rolled his eyes, which Seungcheol accepted. He declined anyways.
”Seriously no thanks, I don’t care how good the stuff is, you know I don’t do any of it“ Seungcheol hummed, nodding his head.
”I know, I was just testing you“ Jihoon raised an eyebrow.
”Testing me? For what?“ Seungcheol shrugged, getting up from out of his seat.
”Oh Nothing, just nothing“ Getting up, Jihoon stayed silent. He seemed like he should just go by what Seungcheol was saying and take this as his queue to leave.
”Okay then, I guess I best be going…“ Jihoon starts, ”Call me if you need or want anything, you know that dude“ Seungcheol smiles
.”Same back“
Once he shut the door behind him, he walked quickly, without seeming to look suspicious to the elevators and waited for it to arrive. Entering it and clicking the ground floor, Jihoon let out a sigh.
The ground floor soon arrived and Jihoon exited the elevator and left the building, this time running to his dark car that was parked in the car park outside. Getting in and turning on the engine, he let out another sigh and clicked on the fourth-speed dial number on his car phone system.
”Jihoon?“ Your voice called out from through the speaker.
”Pack your things, I’ll be there soon"
#jihoon#lee jihoon#woozi#jihoon au#jihoon scenarios#jihoon fluff#jihoon angst#jihoon imagines#woozi scenarios#woozi fluff#woozi angst#woozi imagines#woozi au#seventeen au#seventeen fluff#seventeen angst#seventeen imagines#seventeen scenarios#seventeen#seungcheol#s.coups#jeonghan#joshua#wonwoo#jun#hoshi#soonyoung#mingyu#minghao#the8
24 notes
·
View notes
Text
Can Someone Find Your Ip Address From Youtube

Can Someone Find Your Ip Address From Youtube Video
How Do I Find Someone Ip
How To Find Someone Else's Ip Address
Your IP address gives websites, and people that you have connected with online, more than just a number—more than your IP address. It also gives them the ability to trace that IP address back towards you if they wanted to.
Can Someone Find Your Ip Address From Youtube Video
I am also getting a different ip address than the regular 192.168 etc, I'm getting this ip address that says 10.22.248.1. They have ran a coax cable from the pole all the way into my house and into the modem, and that didn't fix anything.
So, when you use a static IP address like many other cases at home, you left a trace about the IP in your emails or whatever you do online, in this case, yes, your cell phone IP can be traced and even, located exactly or approximately on the map if someone has advanced technologies and network algorithms.
27 Dec 2010

Many people on the internet ask this question, so today; I am going to answer it for once and for all.
So… Can people find out who you are through your IP Address? The simple answer is yes. But first, let’s understand what an IP Address is, the different types of IP Addresses, and then how people can find out your home address through your IP.
What Is An IP Address?
Under IPv4, an IP Address is a bunch of numbers that is in the format of XXX.XXX.XXX.XXX. For example: 124.136.56.164. However, since the world is running short of IP Addresses (we’ll probably run out by the end of 2011), IPv6 has been created in which IP Addresses are displayed as group of four hexadecimal digits separated by colons. For example: 2001:db8:1f70::999:de8:7648:6e8. For more information about IPv6, visit Wikipedia.
What are IP Addresses Used For?
How Do I Find Someone Ip
IP Addresses are used to connect computers to each other. For example, your ISP will assign you either a static or dynamic IP Address which you will use to connect your computer or home network to the internet. If your home network has more than one computer in it, your ISP will not assign each of your computers an IP Address. Your router will assign each computer in your network a LAN IP. This IP Address is a little different as it will usually start with a 192.168.x.x or 10.x.x.x.
Static IP? Dynamic IP? What’s the Difference?
Basically a Static IP Address never changes, whereas a Dynamic IP Address does change. Businesses usually require a static IP Address so they can host servers such as web servers, so when you visit a domain name, the DNS server (Domain Name Server) finds out what the IP Address is and directs you to that server. Imagine if you had a dynamic IP Address that always changes, you wouldn’t be able to locate that server or website.
Most residential customers will be assigned dynamic IP Addresses by their ISP. The reason being is that they don’t need to run servers and it’s easier to manage.
What’s better – Dynamic or Static?
It’s really depends on what you require as each have their pro’s and con’s. For example, if you want to host a web server, a static IP Address will be better suited, but a dynamic IP will be better if you constantly get blocked by a firewall as you can reset your modem and get a new IP Address and re-access the site. But you can’t do that with a static IP Address as your IP Address remains the same.
So can people find out my home address through my IP Address?

How To Find Someone Else's Ip Address
If someone wants to find out where you live, first, they will need to know your IP Address and the date and time when you accessed something (it’s easy to get, read below). Every time you visit a website, the website would probably record your IP Address. That being said, to identify you from the other 10000 visitors can be a bit tricky, so if you log into an account, they will most probably have your username or address recorded so they can associate your account details to your IP Address.
But by someone just having your IP Address, it is possible to track down who you are from your IP Address, but for privacy issues, not many people can do it. If someone wants to find your address, they will need a court order or a warrant to access the information from your ISP. With this, your the ISP can lookup who used what particularly ISP at a given time and date. They will then look up your billing and account details to find out what address you have.
Also, each ISP and countries are assigned with a particular IP range, thus you can use services like Trasir to find out who your ISP is and what country and region you are from.
So that is how people can find your address from your IP Address. Please keep in mind, to find legally get your personal details from your IP Address, they will need to go through some form of court order to receive permission to get these details.
Please be aware, that there maybe people who work with these agencies (ISP, Police etc) that may be able to attain these details through inside information.
So Where Do I Find My IP Address? What is my IP?
It is very easy to find your IP Address, and if I go to a services like CanYouSeeMe.org it will get my IP Address for me and display it. When you visit it on another computer on another network, it will show you your IP Address you are using to connect to the internet. Other services like You Get Signal will show a geophysical map of your location in which your IP Address is assigned, which can be used as an extremely useful tool to track IP Addresses and to trace IP locations.
IP Addresses Can Be Disguised
It is important to note, that IP addresses can be spoofed. Someone in one country, can mask their IP address to show that they are in another country. When someone does this, it makes it much more difficult to track where that person is actually located. I suggest you read “How To Use a Fake IP Address & Mask Yourself Online” and “6 Tips On How To Unblock A Web Page From Behind A Firewall“.

1 note
·
View note
Text
Vpn For Mac Os X Server

VPN Host Name: The Fully Qualified Domain Name you can use to access your VPN server. ( Requires properly configured DNS.) Shared Secret: Used as a way for VPN.
Buy OS X Server. Just like that, your Mac is a powerful server. MacOS Server brings even more power to your business, home office, or school. Designed to work with macOS and iOS, macOS Server makes it easy to configure Mac and iOS devices. It’s also remarkably simple to install, set up, and manage.
I'm configuring a Mac as a server with a VPN service. So, I opened the ports listed as used by VPN in Apple documentation: UDP 500 - 500 (+ESP and AH) UDP 4500 - 4500; Any UDP - 1701 (I got to these configs setup by the router wizard to setup the VPN ports) Now, problem number 1: I cannot connect to my VPN.
Home > Articles > Apple > Operating Systems
␡
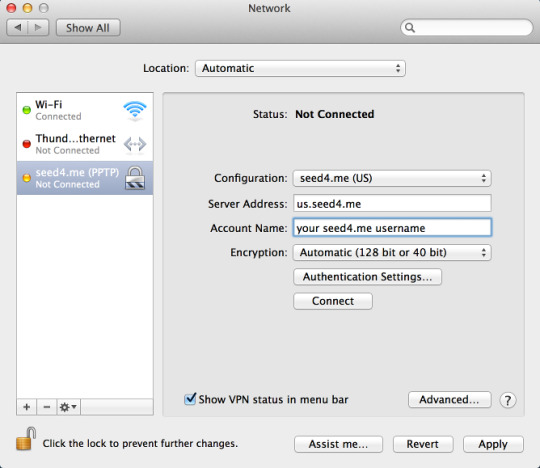
Configuring L2TP Access
Page 1 of 5Next >
In Part 1 of his series on VPN solutions for Mac OS X, Ryan Faas illustrated the process of connecting a Mac to a remote network using VPN. Ryan now continues the discussion from the other end of the spectrum by showing you how to enable, configure, and control VPN access to your network using Mac OS X Server.
Like this article? We recommend
Real World Mac Maintenance and Backups
Like this article? We recommend
Like this article? We recommend
Part 1 of this series looked at how to connect a computer to a remote network using VPN. This article continues the discussion of VPN services for Mac OS X from the opposite perspective, that of configuring Mac OS X Server’s VPN service. The VPN service of Mac OS X Server supports both the L2TP over IPSec and PPTP protocols commonly used by both Macs and Windows PCs. It also integrates with Open Directory, enabling you to configure VPN access based on individual users and groups as well as offering various additional security and authentication methods.
To configure the VPN service, launch Server Admin and select VPN in the Computer & Services list for the appropriate server. If you are using NAT on your network, remember that the VPN server must have a public IP address to accept connections from outside your network as well as an internal IP address. Also make certain that the ports for the appropriate VPN protocols (1701 for L2TP, 1723 for PPTP) are open in your firewall configuration. After the VPN service is configured, you use the Start Service button in the Server Admin toolbar to start the VPN service.
As you can see in Figure 1, the VPN service contains four primary panes for which there are tabs at the bottom of the window: Overview, Log, Connections, and Settings. Overview enables you to see the status of both VPN protocols and the number of connections. Log allows you to view the VPN service log. Connections displays information for all current VPN connections, including the user who is connected, the remote IP address from which they are connected, the internal IP address assigned to them by the VPN service, which VPN protocol they are connected by, and how long they have been connected. The Settings Pane, which is shown in Figure 1, is where you configure the VPN service.
Figure 1 VPN Service Settings pane in Server Admin
Configuring L2TP Access
The VPN Settings pane includes four tabs: L2TP, PPTP, Logging, and Client Information. The L2TP and PPTP tabs allow you to enable and configure each of the two VPN protocols (you can opt to use either or both protocols). The L2TP tab, shown in Figure 1, includes a checkbox to enable the service as well as a starting and ending IP address field and radio buttons for selecting an IPSec authentication method. As discussed in Part 1 of this series, L2TP offers additional security over PPTP by allowing the server to ensure that the computer requesting a VPN connection is a trusted computer by the use of security certificates or a shared secret (a string of text entered on both the server and remote computer).
If you are using a shared secret instead of a security certificate for L2TP, enter it in this field. If you are using a shared secret, remember to make it as secure as possible and to change it on a regular basis (informing users that connect using L2TP) as a precaution against the secret becoming available to individuals other than authorized VPN users. Using security certificates, which can be generated using the General Server information pane of Server Admin is inherently more secure than using a shared secret. If you choose to use a certificate, select the appropriate radio button and then select your certificate from the pop-up menu.
The IP address fields are used to assign the IP address pool for each protocol. These IP address ranges function much like a DHCP scope and are used to assign internal network IP addresses to each computer that connects using VPN. You must create VPN IP address ranges that are unique from your DHCP scope(s) and static IP addresses to avoid IP address conflicts within the network. You should also make certain that you assign ranges large enough to accommodate all the VPN users that you need to support.
The PPP Authentication pop-up menu allows you to choose what method will be used for verifying users’ names and passwords when they attempt to establish a VPN connection. You can choose to use either Kerberos or MS-CHAPv2. Kerberos is a more secure option, but it does require that your VPN server and remote computers be bound to the same Open Directory domain and that Kerberos be properly configured for that domain to function. MS-CHAPv2 exchanges usernames and passwords in solidly encrypted form and is more broadly supported and can be easier to troubleshoot. If you are supporting Windows PCs as remote computers, you should choose MS-CHAPv2.
Mac Os X Server Vpn L2tp Ports
Related Resources
Book $55.99
Mac Os L2tp Vpn
eBook (Watermarked) $55.99
Mac Os X Server Vpn Not Responding
Web Edition $55.99

1 note
·
View note
Text
What are the application scenarios for static IP? How to get a static IP?
In the network world, “static IP” is often mentioned, it is a kind of fixed IP address, applicable to a variety of professional scenarios. So what are the specific application scenarios of static IP? And how to get it? Below is an in-depth understanding of the application and acquisition of static IP.

1. What is static IP?
A static IP is a fixed IP address assigned by an Internet Service Provider (ISP). Unlike a dynamic IP, a static IP remains unchanged after a user disconnects from the network or reboots the device. This means that every time you access the Internet, your device communicates with the outside world through the same IP address.
2. Application Scenarios of Static IP
Static IP is often used in network scenarios that require high reliability and stable connectivity due to its invariance and predictability. Common static IP application scenarios include:
Remote server access: In scenarios such as remotely managing servers, network storage devices, etc., using a static IP ensures that the device can be accessed at any time through the same address, making it easy to maintain and manage.
Hosted websites: If you host your own website, a static IP ensures that the website is always accessible via a fixed IP address, avoiding potential access disruption issues caused by frequent IP address changes.
Mail servers: Static IPs are very important when running mail servers, especially in ensuring the stability and security of mail sending and receiving, and can reduce the risk of mail being marked as spam.
Webcams and Surveillance Systems: With a static IP, users can remotely access their webcam or surveillance system at any time without having to worry about access problems caused by IP address changes.
VPN Connections: When setting up a Virtual Private Network (VPN), static IPs help to maintain a stable connection, which is especially important in internal corporate network access scenarios.
Gaming Server: Static IP provides stable connection support for online gaming servers, especially in multiplayer games, which ensures that players seamlessly connect to the same IP.
3. How to get a static IP?
There are usually several ways to get a static IP.
Contact an Internet Service Provider (ISP): The most common way is to contact your ISP and ask them to assign a static IP address. Usually, ISPs charge an additional fee as a price for providing static IP services.
Use proxy service: Proxy service providers (e.g. 711Proxy) provide static IP service, which is especially suitable for scenarios requiring high reliability and anonymity, such as crawlers and cross-border business, etc. 711Proxy not only provides high-quality static IP resources, but also ensures the security and stability of the connection, which helps users to expand their business smoothly.
Self-constructed server or purchasing VPS: When self-constructed server or purchasing Virtual Private Server (VPS), some service providers will provide static IP by default, which is especially suitable for personal website hosting or small business applications.
Static IPs play an important role in networks, especially in scenarios that require high reliability, stability and remote access. Choose 711Proxy, which can provide you with high-quality static IPs worldwide and guarantee the efficient operation of your business.
0 notes
Text
Protect Your Browsing/Data Sharing
For free, because in this house I don’t believe in making people pay for basic human rights.
I’ve decided to share my browsing protecting tips here. Digital security is usually quite expensive, but it doesn’t have to be! In this day and age, you’ll be told to watch out for home-born hackers and ‘hacktivists’ accessing your data, but I gotta tell you, what your own governments and ISPs are doing makes this more important (aka: they’re worse).
I know with all the TIKTOK IS SPYING ON YOU stuff, a lot of my friends have come to me seeking some advice on this. This is also great if you don’t want parents checking your browsing >_> just sayin’
If anyone has questions - drop me an ask! I’ll always answer for this topic. I am also happy to ‘expand’ on one of these suggestions if they’re unclear :)
Note: This works under the assumption you have your default ISP provided router and can’t get another one for whatever reason. I will advise that if you can get an additional router, do so! Try to avoid the one the ISP has provided to you.
Additional Note: This is not ‘optimal’. There is no such thing in security – everything has a backdoor.
Let’s get cracking! This is a long, and thorough post, but I _do _have a pdf somewhere if you want it because it looks nicer :*)
Use Tor to browse.
There you go, there’s my advice leaves
https://support.torproject.org/ to Download/Install/Run.
Don’t change anything, except maybe using Tor in ‘bridge’ mode.
Okay, you can use other browsers (see: Chrome/Firefox), but they are not as secure as Tor.
USE A VPN IF YOU ARE GOING TO USE TOR! I prefer Firefox (extensions + good security)
________________________________________________________________
Install the following extensions if you have Chrome or Firefox:
Privacy Possum
Stops tracking cookies. PSA: Cookies are not evil, certain cookies can be.
Firefox: https://addons.mozilla.org/nl/firefox/addon/privacy-possum/
Chrome: https://chrome.google.com/webstore/detail/privacy-possum/ommfjecdpepadiafbnidoiggfpbnkfbj
Ghostery
Stops tracking adverts and cookies. Why do I need this in addition to Privacy Possum? Ghostery specifically looks at tracking cookie ads. It’s like adding MOAR POWAH to Privacy Possum.
Firefox: https://addons.mozilla.org/nl/firefox/addon/ghostery/
Chrome: https://chrome.google.com/webstore/detail/ghostery-%E2%80%93-privacy-ad-blo/mlomiejdfkolichcflejclcbmpeaniij?hl=nl
HTTPS Everywhere
Enforces HTTPS. If you look next to the URL in your browser, you’ll see the little lock which indicates the specific URL is secure and uses HTTPS. Many websites still use the old HTTP, which is not as secure and you should NEVER EVER VISIT AN HTTP SITE ITS LIKE READING A BOOK OVER SOMEONE’S SHOULDER, thank you.
Firefox: https://addons.mozilla.org/nl/firefox/addon/https-everywhere/
Chrome: https://chrome.google.com/webstore/detail/https-everywhere/gcbommkclmclpchllfjekcdonpmejbdp?hl=nl
Adblock Plus
Foff, ads.* Firefox: https://addons.mozilla.org/nl/firefox/addon/adblock-plus/
Chrome: https://chrome.google.com/webstore/detail/adblock-plus-free-ad-bloc/cfhdojbkjhnklbpkdaibdccddilifddb
________________________________________________________________
DNS Settings
Ideally, you should change this on your router. ISPs use a default DNS – you don’t want to use anything those bastards say you should use.
Use Cloudflare or OpenDNS:
Cloudflare is more secure overall and keeps up to standards in addition to not storing your data, whereas OpenDNS is great at avoiding malicious websites, just take your pick really 😊There are a ton of other options, feel free to google ‘free DNS servers’. Google has it’s own as well, but, yaknow, it’s Google.
Cloudflare
Primary Server: 1.1.1.1
Secondary Server: 1.0.0.1
OpenDNS
Primary Server: 208.67.222.222
Secondary Server: 208.67.220.220
Add these to your router settings:
In a browser, go to http://192.168.1.1/ or http://192.168.1.0/ (it varies per router). This will lead to your router’s configuration portal. Don’t have a router with a configuration portal? Throw it in the trash and tell your ISP they suck for giving it to you.
Login to the admin portal. If you have not configured this or set a password, try the default combinations: usernames are usually ‘admin’ or blank, the passwords are usually blank, ‘admin’, or ‘1234’.
Each router is different, navigate to where it asks for DNS values or servers, and enter the above addresses. You will see ‘Static’ near the DNS options, select it. This also ensures you’re in the right place. If you’re not sure what to do, look up the model/make of your router and check how you can change DNS.
Whilst you’re at it, change your WiFi password from the default one, and create a proper password for the WiFi portal login. If these two things are kept as default, all these protection methods are pointless as it is easy to crack your router passwords.
Can’t do this on your router because your parents are ds?* No worries! This can be done on your device! :) Yeah, I know how parents work.
Windows OS
Go to Control Panel <Network and Internet < Network and Sharing Center
Click on the link next to “Connections:”* Click “Properties” in the dialogue that pops up.
Select Internet Protocol Version 4 < Click Properties < Select “Use Following DNS Servers” < Enter the primary and secondary server addresses
Do this again for Internet Protocol Version 6 in the list.
Boom. Windows is so nice to make this easy.
Mac OS
Go to Apple Menu < System Preferences < Network
Select the Network you’re connected to
Click Advanced
Select DNS Tab
Click the + button < Enter chosen DNS < Save
Linux OS
I’m going to assume if you’re using Linux, you know how to use the terminal and are using a modern Linux system. Enter these line by line. There are many ways to do this (Google is your friend)
· sudo apt update
· sudo apt install resolvconf
· sudo systemctl status resolvconf.service (check that it is running)
· sudo systemctl start resolvconf.service (to start it, use ‘enable’ instead of ‘start’ to enable)
· sudo nano /etc/resolvconf/resolv.conf.d/head
· nameserver YOUR.DNS.ADDRESS.HERE
· nameserver YOUR.SECOND.DNS.ADDRESS.HERE
· sudo systemctl start resolvconf.service
Android
Oh yeah, you can do this on phones too wiggles eyebrows. Note, if you’re using a VPN it will lock you out of editing this. Turn it off, edit your DNS, turn it back on. This can be tricky with mobile devices that have not been jailbroken (I don’t advise doing that if you have no clue what you’re doing).
Go to Settings < Connections < WiFi
Select the gear icon next to your current WiFi
Select Advanced < Ip Settings drop-down < Static
Enter chosen DNS options under “DNS 1” and “DNS 2”
iPhone
Go to Settings < Wi-Fi
Select the arrow button next to your current WiFi
Select DHCP tab, scroll down to DNS
Select DNS, and enter your DNS servers
TEST YOUR DNS IS WORKING:
OpenDNS: https://welcome.opendns.com/ (You’ll see a “Welcome to OpenDNS” message”
Cloudflare: https://www.cloudflare.com/ssl/encrypted-sni/ (You’ll see check marks for all fields)
________________________________________________________________
Turn of WPS on router. Enable encryption on router.
If you can access your router portal, find any sort of toggle or field that says “WPS” and disable it. WPS= bad.
Wherever there is an option for WPA2 (or higher) to enable, enable it.
Enable the firewall on your router and Operating System – ALWAYS. If you disable this, you’re disabling an additional layer of security. Firewalls are confusing things and a royal pain in the ass to configure, but having the default is better than having nothing.
________________________________________________________________
Configure your browsers.
Browsers have most things enabled by default, including tracking your location, turning your microphone on etc. Let’s disable that nonsense and make them ask you for permission because it’s 2020.
I’m using Chrome as an example below because it is INFAMOUS for this. Essentially, go through your browser and scroll through settings you don’t like.
Go to the little menu icon < select “Settings”
Sign out if it’s linked to your Google account. Let’s not give Chrome a reason to track your browsing history for your account >_>* Disable EVERYTHING:
Here, I turned off everything I would find annoying except autocomplete because I’m lazy.

NICE TRY GOOGLE, YOU CANT SAVE MY CREDIT CARD. (Seriously, don’t ever EVER autosave passwords/payment info).

The trick is to balance ease of use with security. These may vary from person to person, in general though, if there’s a setting ‘ask before etc.’ select that over ‘allow’.
As a rule of thumb:
NEVER ENABLE FLASH (not even an ‘ask before’), NEVER ENABLE LOCATION (ask before is fine, but at your own risk), NEVER ENABLE CAMERA (ask before is fine, but at your own risk, use the desktop version of an application over the browser version), NEVER ENABLE MICROPHONE (same as camera)
________________________________________________________________
Additional Tipss
Check every single social media setting. You should disable anything that accesses your privacy, if possible.
Cover your camera with a sticker. Disable it unless it’s needed
Disable your mic unless you need it.
Turn off Bluetooth/NFC when you don’t need it.
Have two separate networks/Wi-Fi for smart devices and personal devices.
Always use two/multi-factor-authentication for every single app, site, device etc. that you can.
Biometrics are preferable and the usual chosen default (fingerprints, retina scan, NOT FACE OR VOICE THIS IS SO EASY TO IMMITATE BRO PICTURES ARE A THING)
SMS (try to avoid if you can, please)
App ‘token’ authentication. A good choice if done well.
Hard physical key or token. The best option (Google: Yubikey, for some information on how this works).
Passwords
I know you use the same password for everything – get a centralized password manager, and start using different ones. Examples include PasswordSafe, Keeper, Bitdefender etc. Try go for a Cloud provider, and pay a little bit for the extra security and backup. If they’re compromised, then you will know, and you’ll be able to change everything. You can tie password managers to a token too.
USE PASSPHRASES, 17 characters is a good average length, use a mix of characters, uppercase, lowercase, numbers, ascii etc.
It doesn’t matter if your password is ‘complex’, it matters if it is complex and long. Servers and computers these days are jacked up on tech steroids and can bruteforce many things, given enough time.
Anti-virus.
EVERYONE SHOULD HAVE ONE, ON EVERY DEVICE. If you have a device that can add AV, add it. This goes for phones, PCs, smartTVs, you name it.
Free versions are okay, some free ones I like are Bitdefender, Kaspersky, McAfee, Avast (hate their fihsfirstg89ewjg9srjgrd ads though).
Sorry Mac users, that belief that you don’t need one is from 2008. Windows has more security built in than Mac, which means Mac devices should 100% make sure they are adding an AV.
VPN
Ahhhhh. The great VPN. A tricky one. Most free versions I find incredibly slow, but give them a try – play around! A VPN is an excellent addition and these days, I’d argue it’s an absolute must. Many AV solutions include a VPN package with their deal. If you want to make sure those sites don’t share your data, this is the thing that will hurt the most - a good VPN will make it a jumbled mess.
Updates - just do them.
There is no complete security in this day and age – it really is just a matter of time. If you use social media, you’re traceable, be it by the company, ISP, some bored 10 year old, or your ex, your data is out there circulating. Once it’s on the internet, it’s there forever, so don’t worry too much and try to make sure it’s all complex binary trash so that they open it and go “WTF” 😊
#tiktok#security#it security#data#data privacy#private browsing#facebook#google#data theft#third party ad#ads#secure browsing#protect data
12 notes
·
View notes
Text
5 Ways To Speed Up Vps Hosted Websites
Virtual Private Servers (VPS) are just one of the most effective hosting services for expanding sites, providing comparable features of a dedicated server at a portion of the cost. Whilst VPS give good, total performance straight out of the box, the majority of people do not know that with a couple of straightforward optimisations, for instance, readjusting default setups and also lowering load, they can dramatically enhance just how their website does. Right here are 5 suggestions to assist your VPS hosted website run efficiently.
1. Optimise Apache settings
The setups you use on your Apache setup can considerably influence the performance of your VPS and also website. Occasionally, the default setups may not be optimal for the platform your website operates on, and also this can trigger Apache to use up much of the server's resources, decreasing the performance of every various other process you are trying to run.
KeepAlive
First of all, make certain that your KeepAlive setup is looked to 'On'. The only reason you should not do this is if your VPS gets synchronised demands from multitudes of IPs or if you have a tons balanced server. Following this, set your MaxKeepAliveRequests to 100. Lastly, ensure that the KeepAliveTimeout value is evaluated 5.
StartServers
The StartServers setup dictates the variety of youngster server processes that the VPS produces when started. This worth should coincide as the MinSpareServers setting, which, for VPS is 5.
MaxClients
The MaxClients setting puts a restriction on the quantity of requests that can be offered at any one time. On a VPS, the recommended MaxClients limit must be 150. If you obtain connection efforts beyond this number, they will be queued.
MaxRequestsPerChild
Similar to the setup above, the MaxRequestsPerChild setup places a limitation on the number of demands that a specific kid server procedure will certainly embark on. The kid process will certainly end if the quantity of requests reaches the optimum specified. For VPS, the suggested optimum is 300.
2. Update MySQL
For both performance and security factors, it is very important to keep your MySQL software program as much as date. The present version is 5.7, which supplies the very best read/write workloads as well as action times. Version 5.6 is also an acceptable version. If you have a previous version of MYSQL, it can be beneficial to upgrade. If the version you are making use of is no more sustained, it is suggested to update asap.
Do note, nevertheless, that upgrading to a brand-new MySQL version is not an easy procedure to perform as well as does demand some rather comprehensive technological knowledge. You should seek professional help if you don't have the required experience. If you are a WHUK VPS customer, contact our consumer support who will certainly be able to provide you all the technological help you need.
3. Make use of a CDN
Although data trips at phenomenal speed, it still requires time to obtain from A to B. The additional it requires to take a trip, the longer it considers your website to tons. This means that site visitors to your site from additional afield might not be getting rather as excellent a user experience as those nearer to where your VPS is based.
This concern can be addressed if you utilize a content shipment network which stores your website's static data on a series of servers around the world. In this manner, when a person brows through your website, they receive much of the data from their closest server. Although dynamic data still needs to find directly from your VPS, this can be done promptly as it is not needing to send out all the data required for the page to lots. Consequently, the visitor obtains their website much quicker - which benefits them and for you.
4. Material optimisation
For your website to be rendered on a user's web browser, a great deal of material requires to be sent out from your VPS to the individual's device. You might have a manuscript hefty motif or great deals of plugins, each with their own scripts, all of which need to be filled prior to your website can function. The loading of these can decreased also much more by the size of the pictures on your website, too.
Your VPS can do the sending out of this data a lot more efficiently if the web content of your website is optimized for performance. There are a variety of things you can do optimize your web content, yet these depend significantly on the themes, plugins as well as web content you have.
Prior to making any adjustments, the very first point you should do is determine which points are reducing your loading times one of the most. The simpler method to do this is to utilize the cost-free, Google PageSpeed Insights tool. Merely kind in your URL and you'll be provided with an in-depth record revealing you how you can enhance site speed by making adjustments to your server settings and website configuration. You'll obtain this for your site's performance on both desktop computer as well as mobile browsers.
5. Use Caching
Caching is a well-known strategy for accelerating the filling times of websites and can be made use of with VPS in a comparable very same way to exactly how it is utilized on other web servers. Without caching, the constant demands for fixed files can place hefty needs on your resources and reduce your website. Caching these static files to RAM quickly minimizes the needs on your server, accelerating other procedures as well as lowering website filling times.
Caching can be achieved via the installment of a series of third-party software application products. These consist of Memcached, an in-memory caching program, made for internet sites which depend on data sources, for instance, WordPress websites, and also Varnish, a program that boosts the speed of vibrant websites.
Conclusion
If you have actually been having concerns with the speed of your VPS organized website or you are seeking means to make your website perform much better, hopefully, the guidance provided in this post will certainly have revealed you just how that can be attained. Readjusting the settings on Apache, upgrading your MySQL version, making use of a CDN, optimising your web content and also caching can all improve the performance of your VPS held website.
If you are using shared looking and also hosting to upgrade to VPS, take a look at our excellent variety of Linux VPS and also Windows VPS plans.
1 note
·
View note
Text
8 Tips For Troubleshooting A Commercial Wi-Fi Network
Personal variety enables the gadgets to assign IP addresses inside 1 network. It is ideal to write down or back again up the options of your router. MAC (Media Accessibility Manage) will be used. If someone is able to wireless connect to your network from the road, near by parking lot, or adjacent house here are some things to consider. If they use your Internet connection for illegal activity, YOU are liable, not them. Also, once they are on your network, they may be able to open, delete, or change every file on your computers. There is also the possibility that the unauthorized user could spread viruses without them even realizing it.
First of all, you can try using different combinations of usernames and passwords which can be found on the Internet. You would be surprised to find out than you can easily find the default username and password for your router. Sometimes it is enough to know who is the manufacturer, and in other cases we can search for default login details for a specific router model. In most cases, the combination of usernames and passwords for routers with a default IP of 192.168.1.1 is admin, admin; admin, password; blank, admin. Please note that the bolded words are the usernames and the others are passwords. Hopefully one combination will work. If not, search the Internet.
So, how do you know the MAC address of the wireless card of the computer you use? It is very simple! Open a command editor by typing cmd command in Start -> Run window. Then, type ipconfig /all. From the output, search for your wireless card name and you will see the MAC address after a small number of lines.
There are many ways to secure your connection. We are focusing on wireless security, so we will make a simple adjustment to your router. The simplest way to secure your connection is by using WEP (Wireless Encryption Protocol). Before I go any further, many hackers can find ways around this protection. It is not the best choice for large businesses (over 100 employees), but for home and small business users, this will work just fine.
If you plan to purchase a repeater to use with a mixed network (both wired and wireless), be sure to buy a repeater using wireless standard 802.11b/g. This standard should be the same as the standard on your modem, although some repeaters are compatible with more than one standard (check the paperwork with the repeater to find out).
For most of us, the install instructions need to be user friendly and easy to follow as this saves time and frustration when installing your new repeater. Generally, manufacturers these days provide easy to follow instructions. If the instructions are more complex, or you need them simplified, you might need a computer professional to perform the installation.
This IP 192.168.0.1 address is found as a default in case of D-Link router meant for its built-in webpage access. From this place you can access the modem's settings by default and play with WEP, address filtering, MAC, LAN network settings and so on.
Usually, your router forwards incoming packets on it's own, but if you do not specifically set it up, there is no guarantee that incoming connections on port 25 will be transferred to your PC.
NIC: - Network Interface cards are required for you PCs. Here also you have option to get a card of 10/100 or 10/100/1000Gbps speed. Again it depends on your requirement and budget. One end of network cable will connect to NIC in your computer and another end will go to switch. Note: - Most of the computers these days comes with built in network card so you don't really need to purchase NIC if you already have one on your computer's motherboard.
For the last step, when your connection sharing is enable, the LAN adapter will be set in using the IP address 192.168.0.1. The computer may lose the connectivity with the other computers on your network. If the other computers have the static IP address, it will be great idea in setting them obtain the IP addresses automatically.
2 notes
·
View notes
Text
Simple Approaches to Prepare for UPSC Current Affairs
The Best Way To Handle Current Affairs for Civil Services: Are you currently trying to find advice on current affairs for upsc ? Appropriate, you will get the most effective answer here. Recently the importance of current affairs has proportionally increased with the analytic development of issues as well as with the increased weightage of setting and science. There is no specific trend in which UPSC has asked questions from current events. Their volatile character could be thought from last year report where many direct questions from current events were picked.
Current Events plays a key role in all the three phases of UPSC planning, especially in the Mains and Interview. It covers a wide selection of matters which overlaps with the CORE matters like Geography, Polity, Economics, History and Dynamic topics like environment, technology and technology. Henceforth, it is hard to categorize issues below a particular heading/topic. Here is the purpose, why most of the aspirants are of the notion that, not many questions have already been requested from current activities in the recent years (from Prelims perspective).
To create in more quality with this part, we would illustrate with several examples. Now every candidate who aspire to become an IAS or IPS Official and want to get ready or get yourself ready for UPSC Civil Service Examination might know the significance of current affairs and just how much weightage provided for current functions in the prelims and mains exam. So, Continue reading to learn more about how exactly to examine current affairs for UPSC prelims & mains. For the data, This is actually the number of these crucial events or affairs :
1. which become the headlines of the magazines and editorial are written. 2. which may have a negative/positive consequences on the society. 3. which remain in subject or debate in society and persons for an extended time. 4. which discover a special interest in reputed magazines for a lengthy time. 5. which may have a quality to make examination oriented records below national/international dilemmas and Bilateral Relation.
Don't allow any institute or anyone inform you usually! Reading the paper EVERYDAY is essential for the preparation. I browse the documents each day for the small amount of time I'd for my preparation. After I decided to appear for the examination, the first step I needed was to sign up to the Hindu and consistently dedicate two hours day-to-day in examining it conclusion to end. I think, reading the report yourself not just helps in greater retention, it also ensures that you will be finding your way through the Mains simultaneously.
My habit of examining the documents was a great help not merely in the Prelims but in addition throughout the answer writing in Mains. I would remember details and numbers from the news headlines that I'd study and applied that in questions wherever I'd small information to frame an effective answer. Also the editorials were of great aid in composition form questions. Therefore my most significant advice will be that you begin studying the paper from the day you determine to seem for the examination, and read it everyday in order to not need backlogs.
Easy Methods to Make for UPSC Current Affairs
One has to be clear about their purpose while reading the news. While you might know which piece of news is worth addressing, you have to also have the ability to dissect the news headlines to determine the areas you will need to retain. While I did so see the documents earlier in the day also, it had been more of a relaxing task and no exercise. Like if I was examining about a scheme, I didn't trouble concerning the Ministry which was employing it or the number of districts it had been to gain etc. I would only be aware that this kind of scheme existed.
But after I began the prep and had the prior year's documents, I knew what precisely to consider in an item of news. That know-how is an essential part of examining the paper. Aimlessly reading the entire report is futile and is likely to be counter-productive. So have the prior year's papers and realize the structure of the questions, then read accordingly. Also, adhere to the syllabus in front of you in order to avoid deviating and losing time.
Also in the event that you sign up for a newspaper, it removes the necessity to make notes on current affairs because most of it is covered by them. I built notes initially however seen that the journal had previously looked after that task for me. I did produce records next but only as factsheets listing important systems for rapid revision during Mains.
Taking an on the web quiz/test day-to-day at night was another important element of my current affairs preparation. I'm glad I used that habit as it served me consolidating and cementing all that I'd read throughout the day. It ensured that I kept more and forgot less. You can find sufficient everyday checks available on the web that you can subscribe to.
I observed the news headlines of all days within my preparation. Rajya Sabha TV was my personal favorite for its simple and unbiased content. I made it a point to watch the debates on this system RS Vishesh. They helped me understand more things in lesser time and were an excellent source of info on burning issues. I applied to view TV throughout dishes to save lots of time.
A lot of instances you should come across fixed parts of one's syllabus in the news. For example, the headlines of a bi-election or perhaps a new countervailing duty required on an item of import. All the instances it will be for topics like polity and economics, so do keep an eye out for such media articles as they might be combined with a static notion and requested in the paper.
Give current affairs its due value as it today forms an important percentage of the paper. So hold abreast with this adjusting development and devote adequate time to it. Whilst it is neither recommended or probable to examine each issue each and every day, current affairs is definitely an exception. The only way to ace it's to follow the news headlines, not need backlogs and get revision tests. Do not get bogged down by the total amount of time it will take to consistently browse the paper. It'd take me 2-2.5 hours initially but gradually I surely could bring it down to 1 hour through the Mains and 45 moments throughout the interview preparation period. As you hold studying, you'll realize that many of media is a follow-up of the pre-existing one. Therefore it will take you reduced time once you become standard at it.
If you wish to prepare for current affairs , you need to visit our internet site at drishtiias.com to get current affairs. They're the perfect easy ways to get ready for current affairs section of UPSC Syllabus for Civil Solutions IAS Exam, follow these often to obtain an upper hand in that area. Thank you for study our material, hope you all success to prepare for UPSC Exam.
1 note
·
View note