#How to Change Windows Lock Screen Password
Explore tagged Tumblr posts
Text
.ೃ࿐RESEARCH
summary — in which a research day takes place in the comfort of the home she shares with her boyfriend. he has a debate with his former podcast cohost to prepare notes for, and she has a federal election to cover.
pairings — hasan piker x politicalcorrespondent!girlfriend
pronouns — she/her
word count — 1470
note — not really an x reader bc she covers australian politics but lives in america with him, and therefore i didn't wanna make it too reader-specific. anyway, the election just ended here in australia and it was on the same day as the hasan v e debate so i decided to get back into writing :)

THE HOUSE HAD NOT been this silent in a long time.
for the past week and a half, her and her boyfriend had been locking themselves in different rooms during their free time to get together as much research as they possibly could on two very different political situations. hasan, who had an upcoming debate with the man who was a former friend and podcast cohost, and her, who had little time to prepare for the upcoming australian election before she had to fly there to cover the lead up to the count.
hasan's family hadn't been around as much since the start of last week because of it. she loved his family but there was something incredibly peaceful about the atmosphere being so silent that every shift in the air could be heard. especially when she had twenty tabs lagging out her laptop and could feel another blue screen threatening to interrupt her once again.
it was late afternoon, the sun mellowing outside the window as she lounged on her stomach across the floor of the open-space living room. the loudest thing that greeted her ears was the sudden heavy footsteps on the hardwood flooring. lost in thought as she scrolled endlessly through an article to ensure it withhold as much bias as possible, she didn't look up at hasan, not even when he stepped over her, bending slightly to scratch the top of her head in a silent greeting before sitting down next to her on the comfortable rug.
he waited for her to speak first, not wanting to break her out of her train of thought. he watched the time tick to two minutes at the top of his phone as he retweeted a post before she spoke. "hey," she lifted her head to look up at him, a warm smile bubbling to life. "how was stream?"
"same old," he said simply, tilting her chin up a little more to press a kiss to her lips. "i tried to finish as early as possible for you." he'd explained at the start of the stream that it wasn't going to be super long one because he had other commitments, namely his girlfriend, and so once he covered everything he needed to plus a few extra things, he was queueing up the outro song and turning off his camera.
"aw," she hummed, turning back to glance at her laptop again. she glanced at the time down in the corner of her screen. "did you want me to make us something to eat or . . .?"
shaking his head, hasan reached over to the coffee table that she had pushed closer to the couch earlier to grab his laptop. "ordered us your favourite already." he knew she was busy and didn't want to interrupt her, so he took the initiative to order from her favourite cafe to treat her. he had walked past her multiple times within the past couple of hours to go get food or a water refill because she didn't come in to drop off any when she got her own like she normally did due to the amount of research she was stuck under.
it meant that he knew she had not eaten much either, and they were going to be on the floor for a while until they called it quits . . . he was getting ready for it to be a long night.
"ugh," she groaned in delight, "you're a lifesaver. this is doing my fucking head in."
with each day of campaigning changing the narrative, there was so much constant work she had to do to keep up until her flight out to australia in a few days time.
"talk to me," hasan hummed, opening the lid of his laptop and typing in the password. the document that already had links and bullet point lists under subheadings already took up two pages and it wasn't even in full detail yet.
"they want me to talk about literally every party, basically," she tried not to sound like she was complaining too hard, but she was genuinely just frustrated. not at the workload — at the fact that the country was slowly turning to shit and people were genuinely falling for the lies of all the conservative parties that got far more votes than they realistically should. "there are people genuinely considering voting in the next trump and elon because they listen to the australian equivalent of fox news and do no further research, like they're straight up just ignoring the fact that peter dutton and gina rinehart are gonna fuck things up so bad, and people believe their nuclear power being cheaper bullshit." she spoke so fast she was quickly out of breath.
hasan did not know as much about australian politics so a lot of it did not stick out to him, but he gladly listened to her every time she spoke about it. the information got stored into a compartment in his brain that was labelled 'aus politics for when i need it' and it got added to every time his girlfriend mentioned anything about it. he didn't have to understand her to be attentive.
"and there's this dickhead who makes a new right-wing party every election 'cause he has too much money," she rambled on, melting under the sudden feeling of his hand tracing patterns on the skin that was exposed on her back from her shirt riding up. "guess what it's called this year."
"uh . . . trump part two?" hasan answered unsurely, partially kidding. his jaw dropped when she didn't immediately say he was wrong.
"basically," she admitted, "it's called trumpet of patriots. it sounds like a super bad meme."
that was news to him. "you're . . . not joking?"
"nope."
laughter tumbled out of him, his hand stilling on her back for a moment. "that's so unserious."
"it's basically the unserious version of the us election," she shrugged, switching to a different tab. this time, an article about how cost of living is swaying younger voters. "anyway . . . how's yours going?"
the words on the document he had open were staring holes through him. "i'm definitely mentally preparing for this shit way more than preparing notes, that's for sure." he didn't do debates because they showcase as more of an entertainment thing than an actual way to get your point across to the other party involved. he was willing to have a conversation with his former cohost and friend, but he knew how it would unfold. everyone did. it would hardly be productive, and so all mental preparation would go towards harbouring extreme levels of restraint and calamity.
her fingers hovered over the keyboard, pausing. hasan maneuvered so that he was laying stomach-down on the floor, his laptop beside hers as he got comfortable. "we both know how its gonna go down."
"uh huh."
"he's gonna talk over you, mock your stuttering, and be a child about literally everything," she easily listed off, annoyance simmering underneath at the thought of it. sometimes she sat in the armchair in the corner of the room while he streamed when she wanted to be in his presence without being on camera. she, however, would absolutely not be sitting in on that debate because she could already picture how much of a mess it would be. she planned to watch it from afar, but even then it was going to be a hard watch.
there was no denying it. hasan could only sigh. they lapsed into a comforting silence, basking in the warmth of the late afternoon sun shining through the windows. the peaceful levels of quiet were only broken by the repetitive pattern of keyboard keys echoing clicks and when kaya dug her wet nose into hasan's arm to try get attention before doing it to her other owner.
a brief cuddle session break that was lengthened when the food arrived lasted a little longer than it perhaps should have, but then it was back to scrolling through videos, social media posts and articles to compile as much as they could. hasan was interrupt her train of thought to ask "does this sound okay?" whenever necessary, and she did similar, instead asking, "is this okay enough?" because all she really needed were unbiased facts to at least try combat the problem of political presenters sharing their opinion when they shouldn't be.
it only lasted until the sun was pretty much gone and they were bathed in darkness when she shut the lid of her laptop and rolled onto him until she was laying directly on top of his back. "wanna play stardew valley?" was all she had to ask and he was closing his laptop lid and trying to stand up without her falling to the floor, research long forgotten as they booted up the xbox to play their split-screen farm.
#hasanabi x oc#hasan piker x reader#hasanabi fic#xeph writes about hasan#he so would play stardew if his gf asked him to lets be fr#not mentioning e's name bc i dont wanna attract the hasan antis to this somehow#i wrote this in like two hours if its not obvious lmaoooo#hasanabi x reader
99 notes
·
View notes
Text
For my American Friends
I feel now is a good time to spread this news. Much like how the internet came together to help share information with the Ukrainians for resisting Russia, I’m here delivering help of a similar nature to those that could be impacted by this latest election in the US. There are ways to communicate relatively securely, outside of Big Brother's social media. I bring this up so that we can minimize the amount of gatherable information that could be used to hurt you, or others you know, in the coming years as changes are made. I'm not going to tell you how or why to use them, I'm just going to provide you with the information.
WhatsApp – While not my personal favorite, since Facebook/Meta is the parent company, WhatsApp is free, globally popular, and widely-used, featuring the ability to lock chats with passwords, disappearing messages, photos and videos that are deleted after being opened, profile photo privacy, the ability to lock the app itself so that only your biometrics can unlock it, encrypted backups, the ability to set custom permissions for who can see you online or when you last used the app, and of course End-to-End Encryption for all conversations EXCEPT those with business accounts. WhatsApp is a good option for those who are not really technically savvy, but still value privacy – if one trusts Facebook/Meta to adequately protect their privacy. It does require a phone number to sign up, however.
Signal - Signal is an end-to-end encrypted messaging software. meaning that the contents of your conversation is secure. The protocol they use (which they created) is seen as the best known protocol for asynchronous messaging by cybersecurity researchers. It's so good that it has been implemented in WhatsApp and in Messenger's secret chats. This app has even been mentioned in the Right-wing author Jack Carr's Political Thriller about a Navy SEAL named James Reece, as being a preferred method of secure communication on the civilian side for operators. (Jack Carr is a former US Navy SEAL.) It's run by a Non-Profit organization called Signal Foundation, and it's mission is to "protect free expression and enable secure global communication through open source privacy technology." It allows secure messaging, voice calls, and video calls. The only downside is that app links to your phone number, so while your conversations and content are secure, who you are talking to is not. Signal is available on Windows, Mac, Andriod, Linus, and iOS.
Session - Session is an end-to-end encrypted messenger that minimises sensitive metadata, designed and built for people who want absolute privacy and freedom from any form of surveillance. Session is an open-source, public-key-based secure messaging application which uses a set of decentralized storage servers and an onion routing protocol to send end-to-end encrypted messages with minimal exposure of user metadata. This means no phone numbers, no metadata for digital footprints, and censorship resistance. It features group chats, the ability to send documents, files, and images securely, and has added voice messages, though these can be spotty. It’s slow, but effective, and be downloaded on Android, F-Droid, iPhone, Mac, Windows, and Linux.
Briar - If you have an Android phone, Briar is another option you have. It features a decentralized network (it’s peer-to-peer encrypted, rather than relying on a central server), meaning messages are synced directly between user devices. It also means that even if the internet is down, it can sync via Bluetooth, Wi-Fi, or even memory cards, meaning information can continue to flow even during a crisis. In the event the internet is functioning, it can sync via the Tor network, protecting users and their relationships from surveillance. Other features: - Screenshots and screen recording are disabled by default - Each user’s contact list is encrypted and stored on her own device. - Briar’s end-to-end encryption prevents keyword filtering, and because of its decentralized design there are no servers to block. - Every user who subscribes to a forum keeps a copy of its content, so there’s no single point where a post can be deleted. - Briar’s forums have no central server to attack, and every subscriber has access to the content even if they’re offline. - Doesn’t require any user data like name and phone number. The downside is that it is text-only and limited to Android Devices, but they do offer Briar Mailbox to deliver messages securely to those who are online at different times. Briar’s goal is “to enable people in any country to create safe spaces where they can debate any topic, plan events, and organize social movements”
Protonmail - A free end-to-end encrypted AND zero-access encryption email service based out of Switzerland, you can safely email with peace of mind that your content is secure. Unlike Google, Outlook, Yahoo, and others, Proton's zero-access encryption means they can't even view the contents of your emails or attachments. As a Swiss-owned company they are not allowed to share information with foreign law enforcement under criminal penalty and they are politically neutral, meaning they won't be pressured by foreign governments. Furthermore, Switzerland has a constitutional right to privacy and strict data protection laws. Unlike companies in other countries, Proton cannot be compelled by foreign or Swiss authorities to engage in bulk surveillance.
Additional Information, from Proton’s Website: Switzerland has strong legal protections for individual rights, and in fact the Swiss Federal Constitution(new window) explicitly establishes a constitutional right to privacy. (In the US, this right is merely implied.) Specifically, Article 13 safeguards privacy in personal or family life and within one’s home, and the Swiss Civil Code(new window) translates this right into statutory law in Article 28.
In the US and EU, authorities can issue gag orders to prevent an individual from knowing they are being investigated or under surveillance. While this type of order also exists in Switzerland, the prosecutors have an obligation to notify the target of surveillance, and the target has an opportunity to appeal in court. In Switzerland, there are no such things as national security letters(new window), and all surveillance requests must go through the courts. Warrantless surveillance, like that practiced in the US where the FBI conducts 3.4 million searches per year(new window) with little oversight, is illegal and not permitted in Switzerland.
Switzerland also benefits from a unique legal provision with Article 271 of the Swiss Criminal Code(new window), which forbids any Swiss company from assisting foreign law enforcement, under threat of criminal penalty. While Switzerland is party to certain international legal assistance agreements, all requests under such agreements must hold up under Swiss law, which has much stricter privacy provisions. All foreign requests are assessed by the Swiss government, which generally does not assist requests from countries with poor rule of law or lack an independent judiciary.
Swiss law has several more unique points. First, it preserves end-to-end encryption, and unlike in the US, UK, or EU, there is no legislation that has been introduced or considered to limit the right to encryption. Second, Swiss law protects no-logs VPN(new window) meaning that Proton VPN does not have logging obligations. While numerous VPNs claim no-logs, these claims generally do not stand up legally because in most jurisdictions, governments can request that the VPN in question starts logging. So the VPN is only no-logs until the government asks. However, in Switzerland, the law does not allow the government to compel Proton VPN to start logging.
We’ve also fought to ensure that Switzerland remains a legal jurisdiction that respects and protects privacy.
Nearly every country in the world has laws governing lawful interception of electronic communications for law enforcement purposes. In Switzerland, these regulations are set out in the Swiss Federal Act on the Surveillance of Post and Telecommunications (SPTA), which was last revised on March 18, 2018. In May 2020, we challenged a decision of the Swiss government over what we believed was an improper attempt to use telecommunications laws to undermine privacy.
In October 2021, The Swiss Federal Administrative Court ultimately agreed with us and ruled that email companies cannot be considered telecommunication providers. This means Proton isn’t required to follow any of the SPTA’s mandatory data retention rules, nor are we bound by a full obligation to identify Proton Mail users. Moreover, as a Swiss company, Proton Mail cannot be compelled to engage in bulk surveillance on behalf of US or Swiss intelligence agencies. (Links can be found at: proton.me/blog/switzerland)
#american politics#kamala harris#transgender#lgbtqia#lgbtq community#antifascist#anti trump#freedom#information#resistance
6 notes
·
View notes
Text
September 30 2024 2009
Sufficiently quenched theres only one thing left for the cans of Tab.
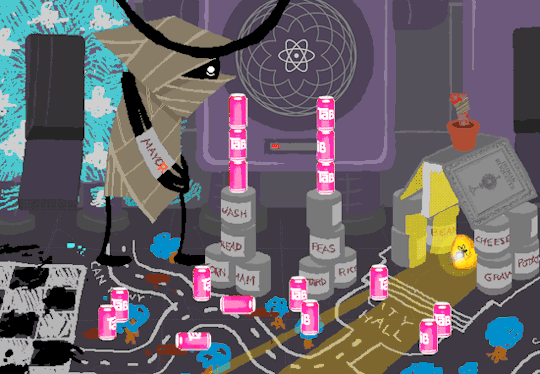
Joining democratic society.
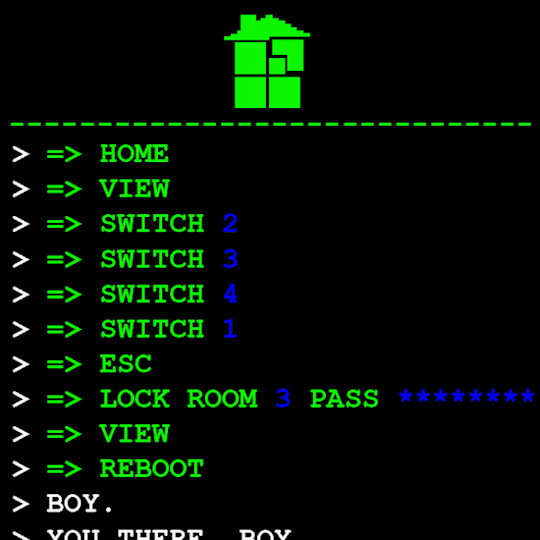
Anyway, WV goes to take a look at the big computer and preses ESCAPE bringing us to a command line screen filled with prompts. At the absolute top are prompts in green that were entered some time before WV appeared.
Gonna have to brush off my CS cap for this one. Now since we dont know what system this computer runs on Im going to operate on the assumption that this is Linux as Ive played around more with that terminal than Windows.
I assume that the green text is a Super User (or using sudo privileges but Im pretty sure its rhe former). What is a super user you ask? The windows equivilent would be Admin and essentially gives this user root directory privileges to access the whole system and make changes. Obviously this can lead to problems if done incorrectly so a password is put in place to prevent just anyone from making system changes. Thats where sudo comes in. Sudo elevates the commands you are giving and will require a password when you access.
Now that thats cleared up, lets look at the prompts. Each of these is preceeded with =>, possibly denoting root prompts from a sudo user. Skipping HOME for a moment, we see VIEW which takes us out of the command terminal to video feed on each of the four screens. SWITCH, well, switches between the screens, the order of which was 2-3-4-1.
I dont know if there is a meaning behind starting at two, Roses screen, but screen 2 shows feed of her house displaying static in front of Zazzerpan whos hand has been broken. Screen 3 shows a, to us, future scene of Dave, potentially post strife, and a first level prototyped kernel. This screen brings a lot of questions. Who is Daves server player? If each of these screens is showing current live feed, how much time passed between the strife and prototyping? What happened to Rose that her feed is locked on Zazzerpan? Unfortunately, WV abandons continuing the previous users commands and enters HOME so we cant see who is on screen 4.
Before diving into what happens with the HOME command, lets go back to the green text. ESC we established brings us back to the teminal. Here this user entered the password to LOCK room 3. Its unclear what room 3 is but Im guessing this was supposed to block access to interacting with Dave. Most likely our SU was preparing this computer for whoever stumbled upon it and blocked access to all but Johns screen.
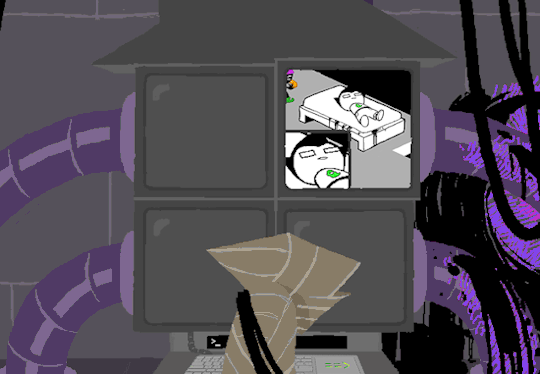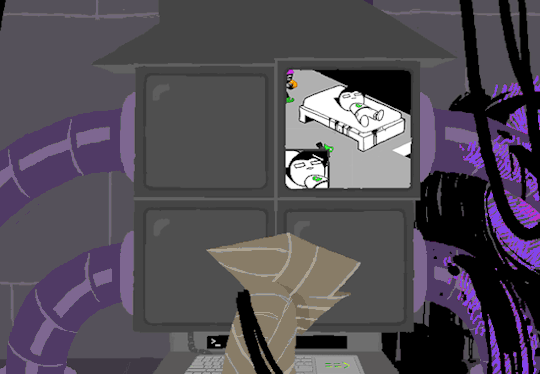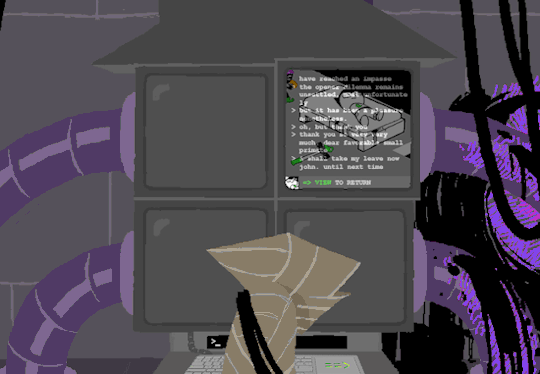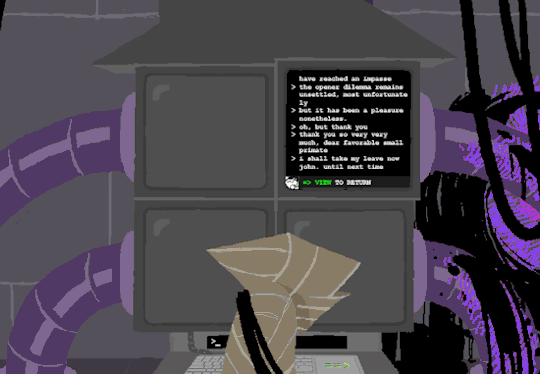
At the bottom of the terminal is a smaller screen that displays the character of focus, in this case John, and the command VIEW which would maximize the camera screen one again. So after ensuring the screens SU wanted were locked, SU returned the view to screen 1 which is what WV saw upon booting. After everything was in order, the system was then rebooted which saved these changes and returned the system to normal user function logging out of the root directory.
In normal user function, entering HOME activates all the screens and our favorite ominous number appears.
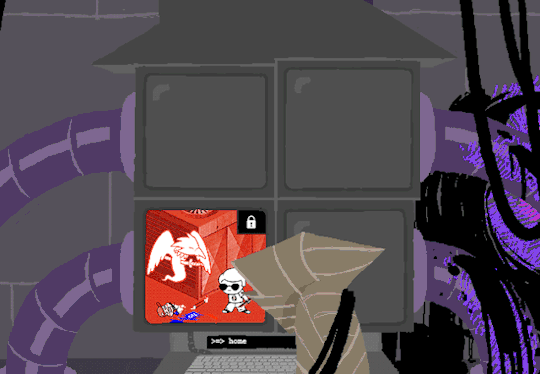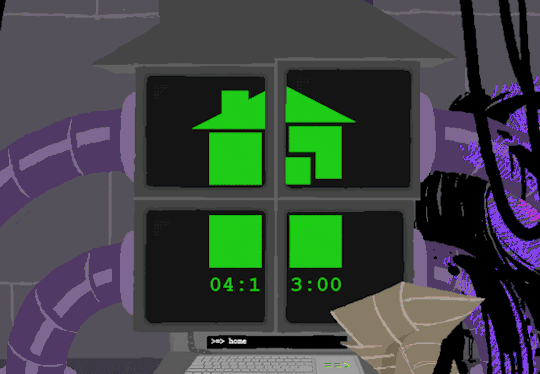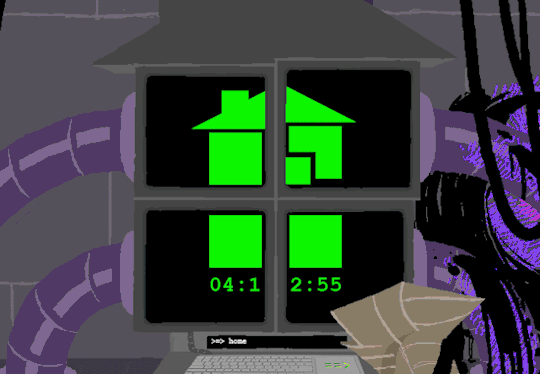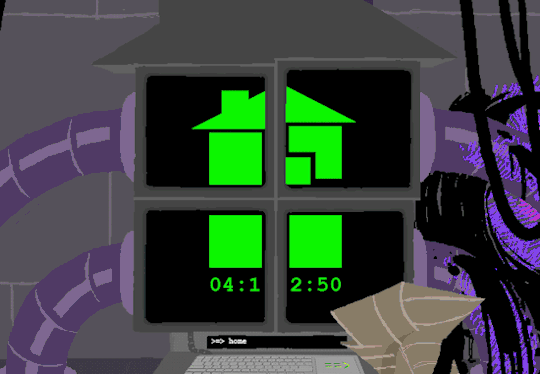
Four hours and thirteen minutes. Another countdown, and this time who knows what its for. Nothing more can be typed as the keyboard is now locked.
But WV is none too worried. He is a Mayor now with much more pressing matters.

The militia wont train itself you know.
#i have an AS in comp sci and a BBA in information systems#all to say i know COMPUTERS for BUSINESS with extra focus on COMPUTERS#this was fun to write#i love sharing knowledge#homestuck#homestuck replay#hsrp liveblog#chrono
4 notes
·
View notes
Text
Thinking again about vampire Markus accidentally being with absolutely clueless Connor in a place where there are only vampires (just mindlessly choosing the place he's used to with realisation hitting him when it's already too late), and EVERYONE else knows that Connor is definitely not one of them.
(I'm not sure if vampires can smell non-vampires or somehow just can tell, like picking up on their temperature being higher or something like that)
So Markus is just trying to invent a reason for the two of them to leav, and being so focused of this absolute fuck up of his to the point of being unable to think straight.
He isn't even sure which one of the four scenarios terrify him more
1) Connor realising what place is this. How fucking stupid of you, Markus, it was to bring here not only just some human, but the one capable of real fucking harm. Like seriously, what were you thinking, that he is changed, capable of no harm? You know we'll enough that's not true. What if it was all part of his plan from the start? Stupid stupid stupid
2) Everyone can sense him being human. Although Markus hates to admit it, Connor is not safe here either.
3) if someone decides to attack, Connor will fight back, which is fucking catastrophe
4) somehow the possibility of him not fighting back (not being able or just unsuccessful in an attempt) is even worse
The only solution is to keep an eye on him at all times while they're inside and come up with a plan -- any plan -- to leave as soon as possible.
So any time Connor says to bring something/go away for a moment Markus instantly goes "I'll go with you".
Connor laughing it out like "Are you afraid I'll try to escape from a bathroom window or something? Should I give you my phone as a pledge to be back?"
"No, it's not neces-"
"Here," Connor gets his phone out of his pocket and hands it to Markus, but as he stretches his hand to take it he throws it up instead, leaving Markus no choice but to panicky catch it.
"You can entertain yourself trying to guess my password," Connor winks at him and without further delay walks deeper into the foggy hall, leaving Markus too dumbfounded by what just happened to react properly, making him too distracted to remember to follow him. He looks at the phone in his hands.
It's almost as if Connor intentionally said him to guess his password. Markus clicks at the lock button and the screen lits up, unlocked.
There's no password.
17 notes
·
View notes
Text
ah wait i forgot i also have advice about hiding behavior online:
i'm lucky that my mother has never been very online-savvy so she doesn't really know how to check history or installed programs. most of these should work even if your abusers do, however.
ALWAYS keep a "safe" tab or window that you can easily switch to, and CHANGE IT OFTEN. if you have the exact same thing open multiple times, they'll realize it's fake. usually I use school assignments. each time they see it, scroll down the page. don't stay on one subject, switch every few hours or so. (like from a math assignment to an english one)
if you want to voice call with friends AND THEY LIKELY CAN'T HEAR WHAT YOU'RE SAYING, just that you're talking, pretend you are collaborating on a school project. keep a "safe tab" related to the project up. If needed, try to make sure you have a more solid alibi if they insist on speaking to your "project partners".
If you have the opportunity (this means LONG PERIODS OF TIME WHEN THEY ARE ABSENT. NOT WHEN THEY TAKE A BATHROOM BREAK, THAT'S TOO SHORT.) see if you can access files and accounts on their computer. it's easier if you know the password, but you may be able to sneak in when they have just stopped using it and it is not locked yet. passwords for things such as parental controls for phones and computers, emails, etc can sometimes be found either emailed to their own email or on a text document.
if they're less tech-savvy, apps on a phone can be superficially hidden by making a folder (ex: one for "school stuff" with apps such as Teams and Remind on the first screen, and then a second screen with your hidden apps.). organize the rest of your phone apps into similar categories without hidden apps, so they will be less suspicious.
also for if theyre less tech-savvy: when using chatting programs or social media, use ones that they are less familiar with and can be easily uninstalled or closed. I have never used the default messages app for communications with friends because it can be easily checked and is well-known to pretty much anyone with a phone, instead I use discord or social media through a web browser.
It's easier to hide things on a computer than a phone. If you have access to a laptop, learn how to use the file systems and the systems of a web browser (firefox is the best). You can obscure files through having a convoluted folder organization system that they may not want to search all the way through. if you don't want them questioning apps (games, chat programs, etc.) keep them off of your taskbar/desktop.
If you have an email account set up by them that you're supposed to use, make another one for most of your actual communications. keep the tracked account active with "safe" conversations.
hey so protip if you have abusive parents and need to get around the house as quietly as possible, stay close to furniture and other heavy stuff because the floor is settled there and it’s less likely to creak
495K notes
·
View notes
Text
Resolving Computer Startup and Login Challenges
Computers are essential tools in our daily lives, but they can sometimes present frustrating issues that disrupt our workflow. From a Mac failing to boot properly to being locked out of a Windows system due to a forgotten password, these problems can feel overwhelming. This article explores practical solutions to common computer startup and login issues, offering step-by-step guidance to restore access and functionality. Whether you're troubleshooting a sluggish system or regaining access to a locked account, these methods will help you navigate the challenges with confidence.
Understanding Startup Issues on a Mac
When a Mac refuses to start correctly, it can manifest as a blank screen, endless loading, or an error message. This issue, often described as How to Fix Your Mac Did Not Start Correctly, can stem from software glitches, corrupted files, or hardware malfunctions. The first step is to restart the device in Safe Mode. By holding the Shift key during startup, the system loads only essential components, which can help identify whether third-party software is causing the problem. If the issue persists, resetting the System Management Controller (SMC) can address hardware-related problems, such as power or thermal issues. This involves shutting down the device, then pressing a specific combination of keys—typically Shift, Control, Option, and the power button—for a few seconds before restarting.
Another approach is to use Disk Utility in Recovery Mode. By restarting the device and holding Command and R, users can access a recovery environment to repair disk errors. Running First Aid on the startup disk often resolves file system inconsistencies that prevent proper booting. If these steps fail, reinstalling the operating system from Recovery Mode can restore functionality without erasing personal data, provided a backup exists. Always ensure critical files are backed up before attempting major repairs, as unexpected issues can lead to data loss.
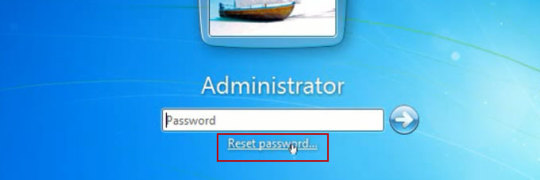
Addressing Windows Login Problems
Forgetting a password on a Windows system can lock users out entirely, leaving them searching for solutions to the issue of Forgot Windows Password & Cant Sign In. This problem is particularly frustrating when no password reset disk or secondary account is available. One effective method is to use Safe Mode to access a built-in administrator account. Restart the computer and press F8 or Shift and F11 (depending on the system) to enter the Advanced Boot Options. From there, select Safe Mode and check if an administrator account appears on the login screen. This account, if active, allows users to log in and reset the password for the locked account through the Control Panel’s user management settings.
If Safe Mode doesn’t provide access, a password reset disk is another option, though it requires prior creation. For those without such a disk, using a bootable USB drive with password recovery software can be a lifesaver. These tools, available online, allow users to create a bootable drive on another computer, which can then be used to reset the password. The process involves booting from the USB, following the software’s prompts, and selecting the user account to modify. This method requires caution, as downloading software from unverified sources can introduce security risks.
Preventive Measures for Future Access
Preventing these issues requires proactive steps. For Mac users, regular updates to the operating system can patch vulnerabilities that cause startup failures. Creating a bootable backup using an external drive ensures that data remains safe even if the system becomes unbootable. Enabling automatic backups through built-in tools like Time Machine adds an extra layer of protection. Additionally, keeping a record of system changes, such as recently installed apps or updates, can help pinpoint the cause of future problems.
For Windows users, creating a password reset disk or linking the account to an online profile can simplify recovery. An online account allows password resets through a web browser on another device, bypassing the need for complex recovery tools. Regularly updating passwords and storing them securely in a password manager reduces the likelihood of being locked out. Enabling two-factor authentication adds an additional security layer, ensuring that even if a password is forgotten, alternative verification methods can restore access.
When to Seek Professional Help
While many startup and login issues can be resolved independently, some situations require professional intervention. Persistent Mac startup errors, especially those accompanied by unusual noises or hardware warnings, may indicate failing components like the hard drive or logic board. In such cases, contacting a certified technician for diagnostic testing is advisable. Similarly, Windows users facing repeated login failures despite attempting recovery methods may need expert assistance to diagnose deeper system corruption or hardware issues.
Professional services can also help recover data from unbootable systems, ensuring minimal loss. When seeking help, choose reputable providers to avoid scams or further damage. For both systems, maintaining a regular maintenance schedule, such as clearing cache files or defragmenting drives, can prevent many issues from arising in the first place.
Final Thoughts
Encountering problems like a Mac failing to start or being locked out of a Windows account can disrupt productivity, but they are often solvable with patience and the right approach. By following systematic troubleshooting steps, such as booting in Safe Mode, using recovery tools, or resetting passwords via external media, users can regain control of their systems. Preventive measures, like regular backups and secure password management, further reduce the risk of future issues. For complex problems, professional assistance ensures a safe resolution. With these strategies, users can confidently tackle computer challenges and maintain seamless access to their devices.
1 note
·
View note
Text
Looking At - Lockdown Options for the Mac

A quick note before we get started this research is from 2023 and has not been updated. I am just now putting this content out because I finally have a place to put it.
Options Looked At
I picked three options:
Absolute Manage (Home and Office)
HiddenApp
Prey Project
I picked Absolute Manage because that is something I am familiar with from the enterprise space. Home and office version because I am not paying for the enterprise product. HiddenApp because it was on the Jamf Marketplace (tho it seems to have been replaced with Senturo, but HiddenApp is still around so who knows). Prey was an obvious include because it's a popular option that's cheap.
What are we evaluating?
I am only looking at how the product locks down the Mac in the case of an outside of geofence, lost or stolen situation. I am not commenting on any of the other functionality.
tl;dr
For those of you not interested in the why's, how's and wheretofor's the conclusion is that Absolute Manage is significantly better than either of the other options. Its lock down is more effective and more robust against tampering etc.
What's wrong with HiddenApp?
The password to unlock the Mac is stored as an MD5 hash with no salt or any other protection.
You can, if you disconnect from the network, change the password to whatever you want it to be by simply changing the hash in the device_locked.status file found in /usr/local/hidden. You need to be an admin, but that is more and more common in the Mac space even in the enterprise.
The lock down is triggered by a Launch Daemon and therefore doesn't activate immediately. I have seen it take multiple minutes to lock the screen–giving you more than enough time to stop it.
The HiddenApp itself is not obfuscated so you can easily reverse engineer any part you need.
If the user is an admin not only can they change the lock password, but they can also prevent their machine from ever locking by simply controlling the missing marker file. You can also of course simply remove HiddenApp since it has no special protection. If you are not on the network once you stop the lock down–HiddenApp can't fix itself without network help.
What's wrong with Prey?
Prey like HiddenApp has a weak method of storing the password to unlock the computer. The method used is: string input converted to utf-8 then base64 encoded and then md5 hashed and returned as a hex digest. You can find this by looking at: /lib/agent/actions/lock/mac/prey-lock in the Prey folder (this is a Python3 file). So you can easily break this scheme due to it being MD5 you just need to base64 encode your wordlist first.
The password hash is easily obtained from looking at the output of sudo ps -A with the window expanded. The password is in the command-line arguments passed to prey-actions.app with -lock flag.
The lock can be bypassed with Safe Mode and with SSH.
The application itself is built from a lot of JavaScript/node.js code. This also means its trivial to reverse engineer.
The application makes no effort to hide itself or obscure what it is doing.
What's right with Absolute Manage Home and Office?
Unlike the other two options Absolute Manage uses a robust lock down based on a SecurityAgentPlugin that runs at login. The lock down is therefore immediate and is hard to bypass by comparison.
The password is not as robust as the other options (4-6 digit pin), but given that the lockdown is immediate during login you don't have the same ability to block it or tamper with it. Keep in mind this is the personal product–so the pin lock makes some limited sense.
The application does a good job obscuring itself and what it is doing.
The only effective bypass I found was if SSH is enabled, then you can SSH in and bypass the lock. I put in a feature suggestion that they disable SSH as part of the lock down.
The product is much more difficult to get rid of, because it stores its components in multiple locations and generally tries to hide itself.
Safe mode does not get around the lock out unlike some of the other products.
The biggest issue I found was the time between issuing a lock command and it being enforced on the endpoint was excessively long-hours in many cases. Observed times as long as 15 hours between issuing the lock command it taking place. This could have been my setup so take it with a grain of salt.
Conclusion
The asset management tool space is a crowded one, and if you are looking for a good product that locks down stolen or otherwise improperly stationed assets you need to take great care to verify what you are buying. Of the three products I picked only one was remotely serviceable, and unless you dive into the details of how the products work it is easy to mistake bad solutions for good ones.
0 notes
Text
Forgot Dell Laptop Password Windows 7 How to Unlock?
I forgot Windows 7 admin password for my Dell laptop and a reset disc was not created. How do I reset the password and get into my locked Dell laptop? Many people have this dilemma when using Windows 7 system. A strong and unique password is essential to protect our system, but you tend to forget Windows 7 password. What to do if we are locked out of Dell laptop Windows 7?
The following Tips will tell you how to unlock a locked Dell laptop Windows 7 without original password. All you need is to reset the forgotten admin password of Windows 7.
Tip 1: Using Windows 7 default Administrator account.
Windows 7 OS has a built-in administrator account which is created during Windows installation without password, and disable by default. You need to enable that account before losing your other admin account password. Or in this tip your built-in administrator account won’t appear in the screen.
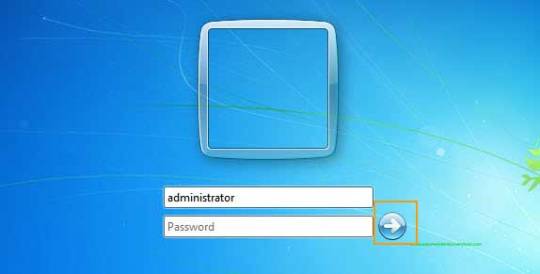
1. Start your computer and press "F8" while the computer boots up. The Advanced Boot Options screen appears.
2. Scroll down to "Safe Mode with Command Prompt" and press "Enter." Your computer starts in Safe Mode with Command Prompt.
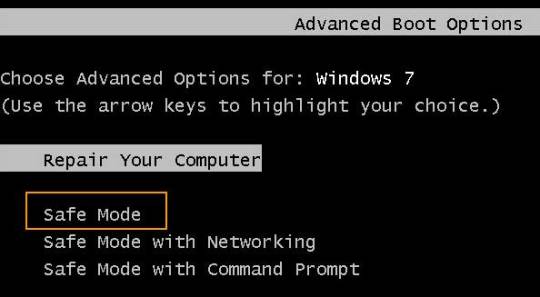
3. Select the Administrator account that appear in the screen, then enter command prompt.
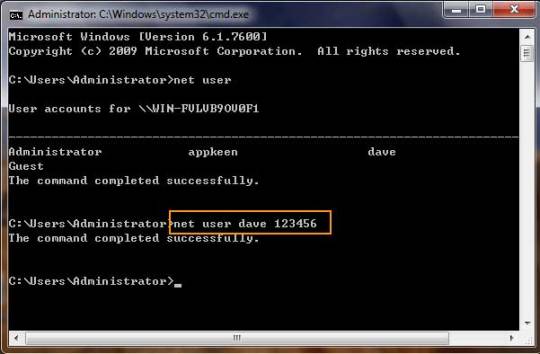
4. Type: net user your username 123456 and hit enter, it will show you a message that” the command completed successfully.
5. Restart your computer, then you can log in as dave with the password 123456. You can go to control Panel to change your account password if necessary.
Tip 2: Reset Dell Laptop Password Windows Vista Using A Free Password Reset Disk.
This is a free and easy way to hack Windows Vista without data lost. The problem with this option is that you have to create the reset disk before the password is lost. Thus if you don’t have a password reset disk, this option is not for you. Here are the steps if you have reset disk.
Step 1. Insert Win7 password reset disk to your computer.
Step 2. When you entering a wrong password for login, a hint will appear: The user name or password is incorrect. Click OK and back to the login Window. Click Reset password.

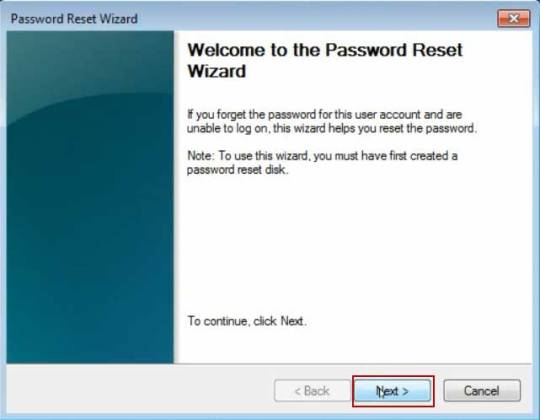
Step 3. Password reset wizard is running. On the Welcome screen, click Next.
Step 4. Choose your USB flash drive in the drop-down menu and click Next.
Step 5. After the Password Reset Wizard finished reading your saved password, you need to type a new password in the Type a new password box and confirm. And then Click Next, then Finish. It is OK.
Tip 3: Use a Windows Password Recovery program to help Unlock Dell laptop Windows 7.
If you forgot an admin account password on your Dell laptop Windows 7 and there is only one admin account. It is a little troublesome.
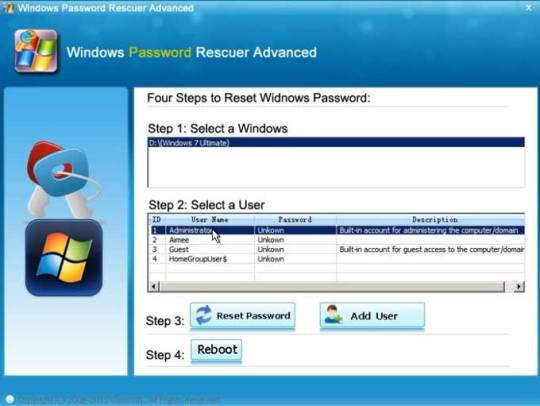
However, we can use a handy password recovery tool, Windows Password Rescuer Advanced, to easily bypass Windows 7 admin password on your laptop without admin privileges, then you can log into your Dell laptop without password.
Here I will show you how to reset Windows 7 administrator password on a Dell laptop with USB flash drive.
It works perfectly for all Windows versions on any laptop and desktop computers. All you need is another computer which you can login with administrator account and install Windows Password Rescuer to create a Windows password recovery disk with USB flash drive.
Step 1: Log in any available computer that you can access to and allows you download. Download and install “Wimware Windows Password Rescuer program” in that computer.
Of course, it also works for Windows 10. If you want to unlock a Dell Windows 10 laptop without password, this is one of the best workable ways.
Step 2: Run and burn the program to a blank CD/DVD or USB flash drive.
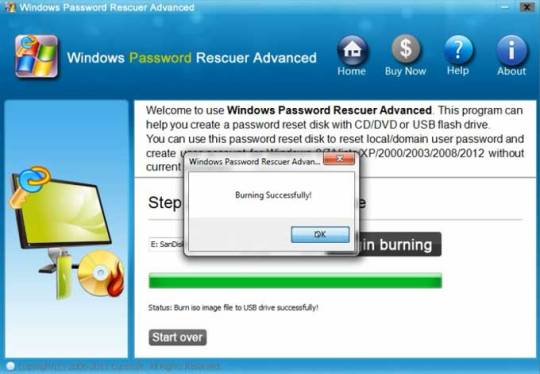
Step 3: When finish, insert the disk to your locked Computer and make your computer boot it from the disk by changing the BIOS setup, then you can follow the instruction to reset your password.
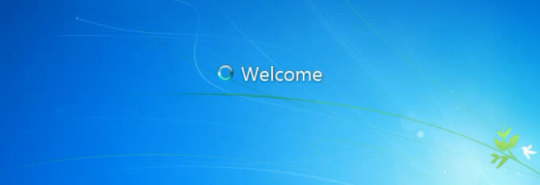
Step 4: After restart, you can log into your Dell laptop Windows 7 without password.
#Dell laptop#Windows 7#unlock dell laptop windows 7#reset password on dell laptop Windows 7#forgot dell laptop password windows 7
0 notes
Text
Exploring macOS: Hidden Features Every MacBook Pro Owner Should Know
MacBook Pro users often rely on their devices for productivity, creativity, and entertainment. While macOS is known for its user-friendly interface, it also houses a variety of lesser-known features that can significantly enhance your experience. From time-saving shortcuts to advanced customisation options, here’s a guide to hidden macOS features every MacBook Pro owner should explore.
1. Quick Look for Instant File Previews
Quick Look allows you to preview files without opening them in their respective apps. Simply select a file in Finder and press the spacebar. This works for images, PDFs, and even videos. You can navigate through multiple files using arrow keys while Quick Look is active.
How to Maximise It:
For more functionality, use Quick Look to add annotations to PDFs or trim video clips without launching Preview or iMovie.
2. Split View for Multitasking
Working on multiple tasks? Split View lets you use two apps side by side, boosting productivity. To activate it, click and hold the green full-screen button in the top-left corner of a window, then drag it to one side of the screen. Choose another app for the opposite side.
Why It’s Handy:
Ideal for comparing documents, referencing research while writing, or attending a video call alongside note-taking.
3. Spotlight Calculator and Conversions
Spotlight is more than just a search tool. Press Cmd + Space to open Spotlight, and you can perform quick calculations or unit conversions. For instance, type “50 GBP to USD” or “10 kg to pounds” for instant results.
Bonus Tip:
Spotlight can also search for specific file types or locations using terms like “kind” or “folder.”
4. Customisable Hot Corners
Hot Corners transform your screen corners into triggers for specific actions. Go to System Settings > Desktop & Dock > Hot Corners. Assign functions like starting a screensaver, locking your screen, or displaying your desktop.
Best Uses:
Set up Hot Corners for quick privacy during work or rapid access to mission-critical files.
5. Text Replacement for Faster Typing
If you frequently type the same phrases, macOS has a built-in text replacement feature. Navigate to System Settings > Keyboard > Text. Add shortcuts like “omw” to expand into “On my way!” or “sig” for your email signature.
Pro Tip:
Combine this with customised keyboard shortcuts for seamless writing across applications.
6. Universal Clipboard for Seamless Copy-Pasting
Copy text or images on your iPhone or iPad and paste them directly onto your MacBook Pro. Universal Clipboard works across devices signed into the same Apple ID with Bluetooth and WiFi enabled.
How It Enhances Workflow:
Perfect for transferring content quickly without emailing or using cloud services.
7. Automator for Task Automation
Automator helps you automate repetitive tasks, such as renaming large batches of files or converting image formats. Open Automator from the Applications folder, choose a workflow type, and drag the desired actions into the workflow panel.
Examples of Use:
Set up a workflow to resize images for specific project needs or create custom alerts for calendar events.
8. Screen Time for Mac
Screen Time isn’t just for mobile devices. On macOS, it helps monitor your app usage and set limits to avoid distractions. Find it in System Settings > Screen Time.
Stay Focused:
Create App Limits to restrict time on social media or set Downtime for uninterrupted work sessions.
9. Safari Reader Mode
For a distraction-free reading experience, Safari’s Reader Mode strips away ads and clutter from web articles. When you’re on a compatible webpage, click the Reader button in the address bar or press Cmd + Shift + R.
Additional Perks:
Customise Reader Mode by changing the text size, background colour, or font to suit your preferences.
10. Secure Notes with Passwords
The Notes app lets you lock sensitive information. Select a note, click the Lock button in the toolbar, and set a password. This ensures that private information stays protected.
Best Practice:
Use this for storing personal details, secure project notes, or financial information.
Final Thoughts
These hidden macOS features can transform your MacBook Pro experience, making your workflow more efficient and your tasks more manageable. Whether you’re a creative professional or a business user, mastering these tools can help you unlock the full potential of your device.
For those considering upgrading their setup temporarily or for specific projects, a MacBook Pro rental is an excellent way to experience the latest macOS features without committing to a purchase.
0 notes
Text
Password Manager Google Rises Passkey Support to Desktop

Password Manager Google
Google Password Manager
On any device, logging into your preferred websites and applications ought to be as simple and quick as opening your phone. This is when passkeys are useful. It getting closer to a pass wordless future with these safer and more user-friendly alternatives to passwords. You can securely sign in to apps and websites using your fingerprint, face, or screen lock.
Only passkeys for Password Manager Google on Android could be saved up till now. Though you would have to use your Android handset to scan a QR code in order to use them on other devices.
Organize passkeys in Chrome
With a passkey, you may quickly and safely log in using a fingerprint, facial scan, or screen lock. Without the need for a password app, passkeys are an easy and safe method to access all of the websites and applications you care about in addition to your Google Account. To increase the security of your account, you might be required to generate or use a passkey while logging in to a website.
Recommendation: Since passkeys are based on industry standards, you can utilize them on numerous platforms.
Password manager
Further information on passkeys
Passkeys are cryptographic key pairs; this is how they differ from passwords. A website-specific key pair is used. Half of the information is stored on your device or password manager, while half is shared with the website. Instead of using a password that could be forgotten or stolen, websites and applications authenticate your access with a code that is created securely.
Passkey advantages include:
You won’t need to commit a string of characters, digits, and letters to memory.
Accounts can be accessed via facial or fingerprint recognition technologies.
Passkeys work with both websites and apps, and they are compatible with a variety of browser ecosystems and operating systems.
Passkeys are protected from hacker attempts because they are powerful enough to never be guessed or reused.
Because passkeys are linked to the app or website for which they were intended, you will never be duped into logging into a phony app or website with your passkey.
Password Manager Google passkeys are compatible with all Android applications.
Make use of passkeys
Passkeys are stored on your devices. The procedure varies depending on the operating system and might not be accessible on all of them.
Keep passkeys in Windows storage
Passkeys are available for use if you have Windows 10 or later. You need to configure Windows Hello in order to store passkeys. Passkeys are only saved to your PC because Windows Hello does not presently support synchronization or backup. Passkeys are lost if you lose your computer or reinstall the OS.
You must have Windows 11, version 22H2 or later on your PC in order to use passkey management and passkey auto-fill.
Passkeys can be kept on an Android device
Important: Your device has to be running Android 9.0 or higher and have the screen lock enabled in order to save passkeys.
Passkeys are kept in your Password Manager Google and used on your Android smartphone. Your Android devices securely sync and backup your passkeys.
Keep passkeys on an iPad or iPhone
Passkeys are available in iOS or iPadOS 16+. The iCloud Keychain syncs them with iOS, iPadOS, and macOS devices. Passkey auto-fill is not available in iOS.
Securely keep passkeys on a key
To keep your passkeys safe, you can utilize a security key.
Important: There is no backup for passkeys kept on security keys. You cannot get your passkeys back if you misplace or reset the security key.
It releasing changes today that further simplify the use of passkeys across all of your devices. Passkeys for Password Manager Google can now be saved from Windows, macOS, Linux, and Android; ChromeOS is also available for beta testing. After they are saved, they will sync automatically across all of your devices, so all you have to do to log in is scan your fingerprint.
Google releasing a new Password Manager Google PIN that will allow you to generate passkeys and access saved ones across all of your devices. This PIN provides an extra degree of protection to guarantee that your passkeys are completely encrypted and inaccessible to anybody not even Google.
You will need to know your Android device’s screen lock or your Password Manager Google PIN when you first use passkeys on a new device. You may safely retrieve your previously saved passkeys and sync fresh ones between your Android devices and PCs with these recovery factors.
For well-known websites and applications like Google, Amazon, PayPal, and WhatsApp, passkeys are already available. You may also start using Password Manager Google right now without downloading any additional apps because it is a feature that is incorporated into Chrome and Android devices.
Is Google Password Manager Safe
In general, Password Manager Google is regarded as secure. Google uses robust encryption to safeguard your credentials, and they have a security staff on hand to keep an eye out for any threats. Like any internet service, there are some risks involved.
Here are some important things to think about:
Your Google account and security are linked
Your passwords may be at risk if your Google account is hacked.
Although Google offers local encryption,
It is not activated by default. Local encryption is therefore optional. This implies that in the event of a data breach, your passwords are kept on Google’s servers and may be accessible.
No master password
Google Password Manager does not necessitate a separate master password, in contrast to certain specialized password managers. This implies that your saved passwords are directly accessible to anyone who manages to access your Google account.
To improve your safety
Turn on Google account two-factor authentication (2FA). This adds another level of protection.
Though Google Password Manager is handy, you might find that a specialized password manager is a better option for people who require high levels of security because it frequently provides more sophisticated security features.
Read more on Govindhtech.com
#Google#passwordmanager#googlepasswordmanager#passkeys#news#govindhtech#technologies#technology#technews#technologytrends
0 notes
Text
Understanding the BitLocker Recovery Key: What It Is and How to Use It

Hey Tumblr friends! 🌟
If you've recently enabled BitLocker on your Windows device and suddenly find yourself staring at a prompt asking for a BitLocker recovery key, you might be wondering what this mysterious key is all about. Let’s dive into the essentials of the BitLocker recovery key, why you might need it, and how to find it when necessary.
What is a BitLocker Recovery Key?
A BitLocker recovery key is a 48-digit numerical password that acts as a backup method to unlock your encrypted drive. This key is generated when you first enable BitLocker on a drive and is crucial for situations where you can’t access your drive through the usual means.
Why Might You Need a BitLocker Recovery Key?
There are several reasons why you might be prompted to enter your BitLocker recovery key:
Forgotten Password: If you forget your BitLocker password, the recovery key is your only way to regain access.
Hardware Changes: Making significant changes to your computer’s hardware, like replacing the motherboard, can trigger the recovery key prompt.
Software Updates: Major updates to your operating system or BIOS might require you to enter the recovery key.
Security Concerns: If BitLocker detects potential security threats or unauthorized access attempts, it will ask for the recovery key.
Where to Find Your BitLocker Recovery Key
If you’re in a pinch and need to find your BitLocker recovery key, here are some common places to check:
Microsoft Account: If you linked BitLocker to your Microsoft account, you can find your key on the Microsoft BitLocker recovery key portal.
USB Drive: If you saved the recovery key to a USB drive, make sure to keep it somewhere safe and accessible.
Printout: Some folks print their recovery key and store it securely.
Azure Active Directory (AAD): If your device is connected to an organization’s AAD, your IT department might have a copy.
File: If you saved the recovery key as a file, it’s usually named something like BitLocker Recovery Key.txt.
What to Do if You Can’t Find Your Recovery Key
If you can’t locate your BitLocker recovery key, your options are unfortunately limited. Without the recovery key, accessing your encrypted data is not possible. This is a vital reminder to store your recovery key securely in multiple locations.
Best Practices for Managing Your BitLocker Recovery Key
Store Multiple Copies: Keep your recovery key in several places, such as your Microsoft account, a USB drive, a printout, and a secure digital file.
Secure Storage: Ensure your recovery key is stored in a safe location, like a safe or encrypted digital storage.
Keep Updated: Regularly update your recovery key and ensure it’s accessible, especially after significant system changes.
By following these best practices, you can avoid the potential frustration and data loss associated with being locked out of your BitLocker-encrypted drive.
For a more detailed guide on BitLocker and managing recovery keys, including step-by-step instructions and troubleshooting tips, check out this Comprehensive BitLocker Recovery Key Guide.
Hope this helps you stay secure and stress-free! If you have any more questions about BitLocker or need further assistance, feel free to drop a comment. 💬✨
Also read our related articals:
How Ad Blockers Might Trigger BSOD Blue Screen
Audio Troubleshooter: Resolve No Sound Issues On Dell Laptop
Laptop Not Connecting To WiFi? Fix Laptop WiFi Issues Today!
How To Fix ‘No Sound’ Issues On Your Laptop Or PC: A Comprehensive Guide
1 note
·
View note
Text
How to Change the Lock Screen Wallpaper in Windows 11
Windows 11 has a lock screen similar to Windows 10, and the wallpaper can be changed. This is not to be confused with the sign-in screen, where you enter your password or PIN to gain access to the desktop. The first screen displays the time, app information, and wallpaper. You can learn to carry some similar tasks like on Windows 11 about Windows through the following links: how to disable Ads in…

View On WordPress
0 notes
Text
WebinarX Review – All-in-One Next-Gen Video Conference Hosting Platform
Welcome to my WebinarX Review. This is a real user-based WebinarX review where I will focus on the features, upgrades, demo, pricing and bonus, how WebinarX can help you, and my opinion. This is the next-generation software that allows you to host unlimited video conferences, meetings, and webinars on ultra-fast servers for life, all for an unbeatable one-time price.
Since most of the world’s white-collar workforce working from home after the COVID-19 pandemic and mostly universities holding classes online for their students, there’s been an explosion of demand for communication tools from companies including Zoom, Slack, and Microsoft. But make no mistake, these effects aren’t short-term this crisis is set to change how we work going forward. Imagine You can put the perfect tool into the hands of your customers to leverage this opportunity and help them save and make thousands of dollars by allowing them to conduct UNLIMITED Live Video Chats, Meetings, Conferences, Live Classes, Online Training, Webinars, Podcasts, P2P Chat Messaging, Group Chats, Screen Sharing, Real Time File Sharing & so much more.

>> Click Here to Get WebinarX + My $15000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
WebinarX Review: What Is WebinarX?
WebinarX is 100% cloud-based and supremely reliable. You can unlimit video conferences, meetings, and webinars from anywhere. Simply select the device of your choice (MAC, Windows, or even your mobile) and begin. It has been created by Abhijit Saha. So far, 98.7% of the people who have seen WebinarX in action have canceled their monthly hosting subscriptions for Zoom, GoToWebinar, and other such platforms. WebinarX is designed for anyone who likes to be in full control of their video conferences, meetings, and webinars but at the same time hates complicated software.
It’s for you if you simply don’t want to pay extra for hosting extra webinars and video meetings and want to build something uncomplicated that grows and makes you more and more as it does. It’s for you if you’re sick and tired of paying monthly subscriptions to the hosting platforms in return for mediocre support and massive downtimes.

WebinarX Review: Overview
Creator: Abhijit Saha
Product: WebinarX
Date Of Launch: 2024-Mar-03
Time Of Launch: 11:00 EST
Front-End Price: $17
Official Website: Click Here
Product Type: Software (Online)
Support: Effective Response
Discount : Get The Best Discount Right Now!
Recommended: Highly Recommended
Required Skill: All Levels
Coupon Code: “WEBINARXOFF” $3 Discount
Refund: YES, 30 Days Money-Back Guarantee
WebinarX Review: Features
Scheduled & Instant Meetings/Webinars
Contacts & Segments for Invitation
Audio, Video, and Screen Sharing Options
Live Chat / Real Time Messaging
Real-Time File Sharing
Multiple Authentication Option
Social Login, Two-Factor Authentication
Complete control over User Profile, Avatar, Change Password, Online/Offline Status
Roles & Permissions Management (ACL) System
Multi-lingual and Locale Management
Auto & Manual Screen Locking
UI and Push Notifications
>> Click Here to Get WebinarX + My $15000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>

WebinarX Review: How Does It Work?
WebinarX Makes You Bank In Just 3 Steps



WebinarX Review: Can Do For You
Host as many Conferences, Meetings & Webinars as you like at the lowest one-time cost you’ll ever see
Unlimited Webinar, Live Video Meeting & Conference Hosting At Your Fingertips
DFY Webinar Content To Get You Started Right Away
Stream Pre-Recorded or Simulated Live Videos Without The Stress Of Being “Live”
Super-low audio And Video Latency For Real-Time Streaming
Built-in meeting Reminder System For Attendees
100% Uptime For Uninterrupted Profits
Enjoy LIVE Chat, Real-Time Messaging, and File Sharing
100% Security Of Data With Free End-To-End SSL Encryption
UNLIMITED bandwidth at no extra or monthly cost
Round-the-clock expert support and step by step tutorials
Bid farewell to limited subscription platforms
ZERO downtime + FASTEST loading ever
INTUITIVE User Interface designed for new & experienced users alike
Inbuilt malware protection from harmful viruses
Host Conferences, Meetings & Webinars for a lifetime
And a lot more.
WebinarX Review: Who Should Use It?
Affiliate Marketer
Blog Owners
CPA Marketer
eCom Store Owners
Product Creators
Podcasts
Teachers & Student
Small and large Business Owners
Video Marketers
Freelancers
Agency Owners
Any Kind Of Marketer
WebinarX Review: OTO And Pricing
Front End Price: WebinarX ($17)
OTO 1: WebInarX Pro ($47)
OTO 2: WebInarX Enterprise ($47)
OTO 3: WebInarX Video Hosting ($47)
OTO 4: WebInarX Voice Maker ($37)
OTO 5: WebInarX Agency ($97)
OTO 6: WebInarX Reseller ($97)
OTO 7: WebInarX Whitelabel ($97)
>> Click Here to Get WebinarX + My $15000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
WebinarX Review: My Special Bonus Bundle
My Special Bonus Bundle will be visible on your access page as an Affiliate Bonus Button on WarriorPlus immediately after purchase.

And before I end my honest WebinarX Review, I told you that I would give you my very own unique PFTSES formula for Free.
WebinarX Review: Pros and Cons
Pros:
Effortless Audio, Video, and Screen Sharing
Beginner-Friendly
Cost-Effective
Cloud-Based Platform
Traffic Generation Potential
24/7 Technical support
30-day money-Back Guarantee
Cons:
You cannot use this product without an active internet connection.
WebinarX Review: Free Bonuses
Bonus #1: DFY 30+ Webinar Courses
Get 30+ DFY courses that you can use with WebinarX to make an instant profit without any recording, without finding the subject. Just share your screen with these prerecorded courses.
Bonus #2: Readymade Consulting & Business Website
This is a fully responsive fast and easy customizable trendy consulting & business Laravel CMS Script. You can change any section of your choice very easily. It is fully responsive and fits all popular browsers and devices. It provides you with so many awesome features for building agency, business, company, consulting, corporate, creative, finance, and related websites.
Bonus #3: WebinarX Total Client Manager
This tool makes your complex sales activity a lot easier. Never again miss a meeting miss a quote or miss a client for poor management. With SalesGo, put your best foot forward and ace your sales card.
Bonus #4: WebinarX User Manager
WebinarX User Manager is a handy script for applications that require a user-based authentication system. It is beneficial to save much of your development hours And focus on the key features.
WebinarX Review: Money Back Guarantee
Guaranteed Profit Booster Backed By 30-Day Full Refund Policy
We have worked very hard to make WebinarX better than anything else on the market. It brings next-gen video conference, meeting, and webinar hosting to your doorstep. It is also priced so economically in comparison that it sounds almost unfair to get such an incredible product for such a tiny investment. It keeps you from sharing your profits with the platform, helping you retain them for yourself. It also gives you ready-made opportunities to earn big commissions. We’re sure you will love the way it works and makes you successful. However, in the rare case that you don’t love it as much, we assure you that your entire money will be back instantly within 30 days of your purchase.

Frequently Asked Questions
Q. How many attendees can I host on my webinars?
1-250 simultaneous attendees.
Q. What if I find it too hard to work with and need help?
WebinarX is the most user-friendly webinar and video conference hosting platform ever. However, if you still need help even after watching the onboarding tutorials, you can always contact support. We will be more than happy to assist you.
Q. What if I still don’t like it?
That’s what the safe-place period is there for… You can ask for a refund any time within 30 days of your purchase.
Q. How many webinars, video conferences, and classes can I run?
As many as you wish, There is no limit.
Q. Great. Let’s get started. What do I do next?
Just Get Instant Access Here Below and get started.
WebinarX AI Review: My Recommendation
WebinarX is a strong choice for individuals and organizations seeking a user-friendly and feature-rich video conferencing platform. Its intuitive interface, high-quality video/audio, and lead generation potential make it ideal for those looking to engage audiences, generate traffic, and establish thought leadership. However, consider your budget and feature needs as the free plan may not suffice for all, and established platforms might offer more integrations. Ultimately, WebinarX is worth exploring, especially for those seeking a user-friendly platform that can contribute to audience growth and traffic generation.
>> Click Here to Get WebinarX + My $15000 Special Bonus Bundle to Boost Up Your Earnings More Traffic, Leads & Commissions >>
See my other reviews: AI NextSite Review, Ecco Review, WP Host Review, Orion Review, NITRO AI Review, ClipFuse AI Review, AI Platform Creator Review, FunnelBuddy AI Review.
Thank for reading my WebinarX Review till the end. Hope it will help you to make purchase decision perfectly.
Note: Yes, this is a paid tool, however the one-time fee is $75 for lifetime
#WebinarX#WebinarX Upgrades#WebinarX Overview#WebinarX Features#WebinarX Review#WebinarX Works#What Is WebinarX#Buy WebinarX#WebinarX Price#WebinarX Demo#WebinarX Discount#WebinarX Honest Review#WebinarX Pricing#WebinarX FE#WebinarX Software Review#WebinarX Pros#WebinarX OTO#WebinarX Preview#WebinarX Scam#WebinarX Software#Get WebinarX#WebinarX Reviews#Purchase WebinarX#WebinarX Legal#WebinarX By Abhijit Saha#Artificial Intelligence#AI#WebinarX Benefits#WebinarX Bonus#WebinarX Bonuses
0 notes
Text
How to Unlock an iPhone Without the Passcode? - ITMlab

For more visit: How to Unlock an iPhone Without the Passcode? - ITMlab
If you’ve forgotten your iPhone’s passcode, you’ll need to find another way to unlock it. There are two ways to do this: resetting or unfreezing the device. You can only use these methods if you know the last date and time that someone used the phone last, but it’s worth noting that it doesn’t matter whether or not they’re still using it today. In this article we’ll show you how to unlock an iPhone without a passcode using both methods so let’s get started!
How to Unfreeze an iPhone
If your iPhone has a passcode, you can use it to unfreeze the device.
In Settings, tap Passcode (or Touch ID & Passcode on an iPhone X or later).
Enter your passcode and tap Turn Off Screen Lock or Change Passcode if prompted to do so by entering an old one that’s no longer valid and then creating a new one for future use when prompted again by iOS 11+ devices or earlier versions of iOS 10 – 12+.
Once the screen is unlocked after entering your security code correctly, go back into Settings and navigate down until you find General > Reset > Erase All Content & Settings; then tap Reset All Settings near the bottom right corner of this page next time you need help with any kind of problem related specifically towards these two different types as well as other common ones involving battery life issues etc., which are often caused by third party apps installed on top of stock apps preinstalled within Windows Phone 8 OS software packages themselves rather than being caused by hardware itself failing due entirely instead due partially maybe even slightly due mostly perhaps entirely too much stress placed upon physical components inside those phones’ casing which causes them eventually break down over time leading up until eventually breaking down completely leaving nothing left behind except maybe some dust particles floating around inside air pockets created under pressure between different parts connected together tightly enough together tightly enough so not too many particles escape through cracks created during production process at factory level back when manufacturing line workers were still working hard trying hard laboriously day after day night after night
How to Unlock a Locked iPhone Without the Passcode
If you’re locked out of your iPhone and don’t know the passcode, there are a few ways to unlock it.
Use the emergency call option: If you can’t use Touch ID or Face ID because of an injury or other reason, go to Settings > Emergency SOS and tap “Call.” You’ll be able to make an emergency phone call without unlocking your device.
Connect the phone to a computer: If you have access to a computer, connect it through iTunes or iCloud (depending on which service was used when setting up the passcode). In both cases, this will allow iTunes/iCloud Backup & Restore options that will let you restore from a backup without entering any passwords or passcodes at all!
How to Reset the Passcode on an iPhone 7 or Older
If you have an iPhone 7 or older, resetting your passcode is a little different than unlocking it.
First, turn off Find My iPhone in iCloud settings. Launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone (or whatever name pops up).
Resetting the passcode on a newer iPhone is slightly different. First, turn off Find My iPhone in iCloud settings. This will prevent the phone from being locked if it’s lost or stolen in the future. Then, launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone. Wait for your device to reset itself and then set it up as a new device from scratch using its default settings.
If you’re trying to unlock an iPhone without the passcode, here’s how:
Resetting the passcode on a newer iPhone is slightly different. First, turn off Find My iPhone in iCloud settings. This will prevent the phone from being locked if it’s lost or stolen in the future. Then, launch Settings on your device and select General > Reset. Scroll down and select Erase All Content and Settings, then tap Erase iPhone (or Erase All). Wait for your device to reset itself and then set it up as a new device from scratch using its default settings.
You can use one of these methods to unlock your phone without the passcode
There are two ways to unlock an iPhone without a passcode. If your phone is not protected by a passcode, then there’s nothing stopping you from simply pressing the home button and seeing if it unlocks. If it does, then great! You don’t have to worry about anything else right now.
If your iPhone is protected by a passcode but you forgot what it was set up as (or if someone changed it), then there are still options available for unlocking it without entering that code.
If you’re looking for a way to unlock your iPhone without using its passcode, then this article is for you. We’ve discussed all of the different options available to you and explained how they work in detail. Hopefully, one of them will work for your situation!
Outline of the Article:
I. Introduction
Importance of iPhone security and the significance of unlocking methods
Brief overview of the methods covered in the article
II. Using Face ID to Unlock iPhone
Explanation of Face ID technology and its setup process
Step-by-step guide on unlocking iPhone using Face ID
III. Unlocking iPhone with Touch ID
Introduction to Touch ID and its fingerprint recognition system
Instructions on setting up and using Touch ID for unlocking
IV. Using Siri to Bypass Passcode
Cautionary note about the risks associated with Siri bypass
Steps to attempt unlocking iPhone using Siri (if applicable)
V. Using iCloud to Remove Passcode
Guide on using iCloud’s Find My iPhone feature to erase the passcode
Detailed steps for remotely unlocking the iPhone through iCloud
VI. Contacting Apple Support
Importance of reaching out to Apple Support for professional assistance
Information on Apple’s verification and security procedures
VII. Conclusion
Summary of the methods discussed and their implications
Emphasis on the importance of iPhone security and responsible unlocking practices
For more visit: How to Unlock an iPhone Without the Passcode? - ITMlab
0 notes
Text
Beginners Guide to Bitdefender Central App
Bitdefender Central is an online platform that can be accessed from any device. You can manage your product installation, subscription, and devices on which Bitdefender is installed. To access Bitdefender Central, visit the Bitdefender Central login page and enter your password. To make things easier, Bitdefender launched its Android app. The app can is easily available on the Google Play store. You won't have any problem downloading and installing it.
What are Bitdefender's Central Functions?
Bitdefender Central app can perform every task you can perform on the desktop. It places your local and network cybersecurity at the convenience of your fingertips. Besides subscription and device management, it has other features as well. Let's take a closer look at its functions.
Devices & Notifications
The Bitdefender Central app lets you view the devices on which the Bitdefender has been installed. It also lets you install Bitdefender protection on all your Windows, Mac, Android, or iOS devices. You can scan, clean, and optimize these devices remotely. If your Windows or Android device gets installed, you can use Bitdefender's Anti-Theft feature To prevent unauthorized access; you locate, lock or wipe your lost devices.
Whenever Bitdefender detects a threat, you get an instant notification and receive 24/7 security updates for your devices.
Bitdefender BOX
Bitdefender Central works with Bitdefender BOX to manage all the devices in your home network. After setting up your Bitdefender BOX, you can discover all the devices connected to your home network and group them under your Bitdefender BOX network. You can pause the internet connection on these devices. You can easily check the protection status and connectivity status for all your connected devices.
It also lets you change your Wi-Fi name and password. You can create profiles for each family member and allocate devices to them. With parental controls, you can keep track of your kid's online activities and manage their screen time. You get real-time notifications for threats blocked by Bitdefender Box, such as anomaly detection, botnet attacks, and unencrypted banking information sent.
Parental Control
Nowadays, kids are too active online, as they have access to various smart devices. Bitdefender's Parental Control lets you keep track of your kid's online activities. You can restrict device access on your kid's devices. Using BOX Defender, you can block internet access on smart TVs and game consoles.
How to Install Bitdefender Mobile Security on Android Devices?
Bitdefender Mobile Security is compatible with all Android devices, including mobile and tablet; the only condition is that the device should use Android 5 or a later version. You will also need internet access. You can install Bitdefender Mobile Security on your Android device from Google Play or via Bitdefender Central.
Although Google Play is the easiest way to download and install Bitdefender, you can also install the Bitdefender Mobile Security app through your Central Account. Follow the steps mentioned below:
How to Manage Your Subscription?
With the Bitdefender Central app, you don't have to visit central.bitdefender.com and log in to your account to activate a new subscription. Open the Bitdefender Central App and click on the My Subscriptions panel. There, tap the + Activate with code link. Type the code in the corresponding field, then hit ACTIVATE.
You can also find out when a Bitdefender product expires and view how many seats are still available for your subscription; to do that, you have to open the Bitdefender Central app and tap on the My Subscription panel. All your Bitdefender subscriptions will be listed, each subscription card displaying the expiry date and active devices.
FAQs
What to do if you forget your PIN code that protects your app?
If you forgot the PIN code set to protect your app, open the Bitdefender Central app or visit the Bitdefender Login page and enter your password. Click the three bars in the upper left corner and choose My Devices. Click the desired device card and then click Rename. From the Application PIN field, retrieve the PIN.
How to stop seeing snapped photos taken on your devices?
First of all, launch the Bitdefender Central app or visit the central. Bitdefender.com and sign in. Click the username icon on the upper-right corner of the page. Click Settings in the menu. As a last step, disable the Show/don't Show snap photos taken on your devices option.
Does Bitdefender Mobile Security affect the device's performance and battery?
After you install the Bitdefender Mobile Security app on your device, it only runs when essential. So the impact on your device performance is very low and is hardly noticeable. It does not run in the background. It only runs when you browse its interface or want a security check.
Visit: Bitdefender.com/activate Bitdefender gravityzone
Source: https://centralbitdefenderdotcom.wordpress.com/2023/07/08/beginners-guide-to-bitdefender-central-app/
#central.bitdefender.com#bitdefender sign in#bitdefender login#bitdefender central login#www.central.bitdefender.com#bitdefender.com/activate#bitdefender central#bitdefender antivirus#bitdefender#bitdefender log in#bitdefender central app
1 note
·
View note
Text
“Don’t worry about getting caught. Just think about finding answers.” She says quietly.
-
Aggie nods, turning the card over in her hands and quickly swiping it in the reader, which flashes green before the hydraulic doors open for them. She takes a breath, the familiar antiseptic smell already creeping into her nostrils. She stashes the card under her pip boy once more.
Her experiences down in the science wing helped a lot. She already knew which rooms were offices, examination rooms or broom closets, so she knew which doors to avoid. No sense wasting their time, her eye in on the larger examination rooms where she and presumably Stanford and any of the other vault citizens who received specialized care came for tests and injections. Her father had a terminal in there, as well a cabinet full of notes and physical copies of results. It also held the door to the “Artifact Containment Unit” which was where so many of the objects, pictures x and even some of the medications she’d been forced to take were stored.
The more she’d pondered in what she hopes to find was wanting to figure out exactly what the tests were for, and what the results meant. What expectations was she exceeding? And she wanted to see the inside of the artifact room. There seemed to be an endless number of items they scientists would pull out of there.
“This way.” She hisses quietly, rounding a corner. She crouches, waving her hand to indicate he should do the same. They pass under a long glass window into an observation room. Though neither can see, they can definitely hear someone trying to whistle, and failing miserably. “That’s Mr. Hughes, the old Music teacher.” She whispers to Stan. “He’s been down here for Observation.” She sounds doubtful at that. She’s sure that like her mother, Mr. Hughes would succumb to “unseen complications” and would end up in an incinerator, which would burn away all evidence of what the scientists had done to him. She beckons Stan along and they enter a hallway with doors and windows on either side. “Exam rooms.” She explains, “They’re just the little ones though, the big one is just ahead.”
A large set of doors stands locked ahead of them but with another swipe of the keycard it opens. The Big One as Aggie had described is a massive lab with multiple tables set up as well as a few medical beds. There’s a massive chemistry set and a machine that’s apparently toy called a centrifuge, thiugh Aggie doesn’t have the faintest idea what it was besides something fhat holds blood. There’s a massive door in the back painted a bright obnoxious orange, with a desk and terminal beside it. Aggie leaves Stan and beelines for it, ignoring all the other curiosities of the room. She sits at the computer and raps the keys. It springs to life.
Password Required.
Fiddleford, the wasteland wonderkind, had taught most of the vaults children how to access the hacking screen on terminals to bypass passwords. Rhis is what Aggie does and tue screen is replaced with a jumble of numbers and letters thiugh several words stand out. She chooses one. Gadgets. It’s incorrect but it’s apparently pretty close. She goes for the next G word. Grovels. Incorrect but VERY close. There’s one G word remaining. She says it aloud as she clicks it.
“Gravity.” With a click the screen changes into a typical home screen interface, greeting Overseer David Yearling. There are logs, sample notes, examination reports- but Aggie is drawn to one think in particular.
Unlock Artifact Containment Unit.
She clicks it forcefully and the door lights up, whirring and clunking as it slowly opens. “Stan, come check this out!” She whispers, running to the door. “I’ve never gone in before. They just bring stuff out.” She’s buzzing with anticipation to discover just what exactly rhis room contained. She’d go back for the notes after a good look inside.
It’s Friday. Stan has being eyeing the clock in the school room all week, wondering when it would finally come round to the weekend and he and Aggie could put their plan into action. Finally, mid-way through a lesson on American history (today’s lesson on the War of 1812 had mostly passed Stan by. He could barely picture what the White House even looked like, least of all why the British had decided to try and burn it down.) Aggie had been escorted by a medical orderly from the classroom for one of her regular medical appointments. He knows that it has to be this evening or nothing. From what Aggie had told him, any missing key card would probably cause a whole mess of trouble if it wasn’t returned in time.
Stan’s heart was beating a tattoo against his chest by the time he met her after classes. He had made some phoney excuse to his mom about how he needed to study something with Aggie, and would be at hers for the evening.
‘Well, my Stanley taking an interest in school-work? I never thought I’d see the day.’
‘Guess I’m turnin’ over a new leaf ma.’
He goes out into the corridor, and nods inconspicuously at her, before looking up and down the length of it, as though there might be people listening in. He wasn’t exactly sure what he would do if there was anyone doing that, but from the pre-war spy movies he had watched in preparation, there was usually some kind of shoot-out. Cognisant that he might need to protect himself and Aggie, and given firearms in the vault were safely kept under lock and key, he had brought a butter knife he had stolen from the canteen. He had tried to sharpen it with a whetstone in the family’s general store, but looking at it now had probably only managed to just scuff up the surface. The satchel slung around his shoulder also contained half a sweet-roll, the Pines family camera (for taking evidence photos) and a spare holotape.
“You ready Aggie?” Stan asked as they started walking off in the direction of the Science Wing. “I gotta be honest with you, I’m pretty scared here. What will happen if we get caught?”
Memories of terrible pre-war films where the dreaded communist spies get their just desserts in the end. He and Aggie were a bit like those spies. Did that in fact make Aggie’s dad the hero?
They needed to walk back towards the atrium, then cross over into another corridor that led to the Science Wing. Thankfully around this time of day they probably wouldn’t bump into anyone, as all adults on day shift remained there until 6pm. However it did mean they would only have a short time to get in and find what they needed. He hoped that they didn’t get lost.
After passing through the atrium (same intercom announcements, same banners, same scowl from Agnes) they arrive at the corridor leading down towards the Science Wing.
“Do you wanna do the honours then?” Stan says, eyeing the keycard in Aggie’s hands.
#**I actually wrote this reply like two days ago but tumblr ate ir.#**finally redid it today#**atom bomb baby
10 notes
·
View notes