#ISC2 CISSP
Explore tagged Tumblr posts
Text
CompTIA Certifications: Your Launchpad Into the globe of IT
The Computing Engineering Business Affiliation (CompTIA) delivers a number of the most identified certifications inside the IT business. From foundational competencies to Innovative specialties, CompTIA certifications empower professionals to build and advance their careers in info technologies.
Exactly what is CompTIA?
CompTIA is usually a non-financial gain trade Affiliation that's been delivering seller-neutral IT certifications due to the fact 1982. Its certifications cater to various skill levels and profession paths, making it a great choice for equally newbies and expert specialists.
Why Choose CompTIA Certifications?
Vendor-Neutral: CompTIA certifications concentrate on core IT competencies that are applicable throughout various platforms and technologies.
Commonly Regarded: Companies throughout industries worth CompTIA-certified industry experts.
Profession Versatility: Certifications cover A variety of IT disciplines, from networking and cybersecurity to task management.
youtube
Inexpensive Pathway: Compared to other certifications, CompTIA supplies an available entry level into IT careers.
Critical CompTIA Certifications
Below are a few of the most popular certifications supplied by CompTIA:
1. CompTIA A+
Who It’s For: Entry-degree IT gurus
What It Handles: Core hardware and program troubleshooting techniques
Why It’s Worthwhile: A+ certification is frequently considered the place to begin for the job in IT.
two. CompTIA Network+
Who It’s For: Networking experts
What It Covers: Community configuration, administration, and troubleshooting
Why It’s Important: Builds foundational techniques for roles like network administrator and methods engineer.
three. CompTIA Security+
Who It’s For: Cybersecurity gurus
What It Handles: Community protection, danger management, and menace mitigation
Why It’s Worthwhile: Security+ is extensively viewed as a baseline certification for cybersecurity roles.
4. CompTIA Cloud+
Who It’s For: Cloud computing specialists
What It Addresses: Cloud architecture, safety, and deployment
Why It’s Valuable: Demonstrates your ability to handle cloud infrastructure.
5. CompTIA Advanced Stability Practitioner (CASP+):
Who It’s For: Expert stability specialists
What It Handles: Innovative stability architecture and functions
Why It’s Useful: Ideal for anyone aiming for leadership roles in cybersecurity.
The way to Begin
Assess Your Plans: Select which certification aligns with the vocation aspirations.
Study Means: Leverage CompTIA’s official review products, follow tests, and on the net programs.
Get Fingers-On Knowledge: Useful knowledge reinforces theoretical information.
Plan the Exam: Select a tests Centre or go for an internet proctored exam.
Great things about CompTIA Certification
Career Development: Open doorways to new roles and responsibilities.
Aggressive Edge: Stick out inside of a crowded occupation marketplace.
Community Accessibility: Be a part of a global network of Accredited professionals.
Ultimate Feelings CompTIA certifications tend to be more than just qualifications; They are really stepping stones to An effective and gratifying career in IT. No matter if you’re just starting out or looking to boost your techniques, CompTIA offers a certification that fits your preferences. Take the first step nowadays and unlock your possible while in the ever-evolving globe of know-how.
Check out more details here: CompTIA
0 notes
Text
0 notes
Text



January 18th, 2024 18/366 Days of Growth
Very productive morning so far: ✔️ ISC2 classes done
✔️ CISSP Book reading ✔️ Duolingo (French) ✔️ Journaling ✔️ Walk for 30 minutes
About the flowers, I took pictures of them in Edinburgh... missing the city so much! I can't wait to come back there (๑╹ω╹๑ )☀️
#studyblr#study#study blog#daily life#study motivation#dailymotivation#studying#study space#productivity#study desk#cyber security#cybersecurity#edinburgh#flowers#codeblr#stemblr#certification
45 notes
·
View notes
Text
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk
New Post has been published on https://thedigitalinsider.com/deepfake-misuse-deepfake-detection-before-its-too-late-cybertalk/
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk


Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years in ICT, cyber security, emerging technology, and innovation. Micki’s focus is helping customers, system integrators, and service providers reduce risk through the adoption of emerging cyber security technologies. Micki is an ISC2 CISSP and holds a Master of Science in Technology Commercialization from the University of Texas at Austin, and an MBA with a global security concentration from East Carolina University.
In this dynamic and insightful interview, Check Point expert Micki Boland discusses how deepfakes are evolving, why that matters for organizations, and how organizations can take action to protect themselves. Discover on-point analyses that could reshape your decisions, improving cyber security and business outcomes. Don’t miss this.
Can you explain how deepfake technology works?
Deepfakes involve simulated video, audio, and images to be delivered as content via online news, mobile applications, and through social media platforms. Deepfake videos are created with Generative Adversarial Networks (GAN), a type of Artificial Neural Network that uses Deep Learning to create synthetic content.
GANs sound cool, but technical. Could you break down how they operate?
GAN are a class of machine learning systems that have two neural network models; a generator and discriminator which game each other. Training data in the form of video, still images, and audio is fed to the generator, which then seeks to recreate it. The discriminator then tries to discern the training data from the recreated data produced by the generator.
The two artificial intelligence engines repeatedly game each other, getting iteratively better. The result is convincing, high quality synthetic video, images, or audio. A good example of GAN at work is NVIDIA GAN. Navigate to the website https://thispersondoesnotexist.com/ and you will see a composite image of a human face that was created by the NVIDIA GAN using faces on the internet. Refreshing the internet browser yields a new synthetic image of a human that does not exist.
What are some notable examples of deepfake tech’s misuse?
Most people are not even aware of deepfake technologies, although these have now been infamously utilized to conduct major financial fraud. Politicians have also used the technology against their political adversaries. Early in the war between Russia and Ukraine, Russia created and disseminated a deepfake video of Ukrainian President Volodymyr Zelenskyy advising Ukrainian soldiers to “lay down their arms” and surrender to Russia.
How was the crisis involving the Zelenskyy deepfake video managed?
The deepfake quality was poor and it was immediately identified as a deepfake video attributable to Russia. However, the technology is becoming so convincing and so real that soon it will be impossible for the regular human being to discern GenAI at work. And detection technologies, while have a tremendous amount of funding and support by big technology corporations, are lagging way behind.
What are some lesser-known uses of deepfake technology and what risks do they pose to organizations, if any?
Hollywood is using deepfake technologies in motion picture creation to recreate actor personas. One such example is Bruce Willis, who sold his persona to be used in movies without his acting due to his debilitating health issues. Voicefake technology (another type of deepfake) enabled an autistic college valedictorian to address her class at her graduation.
Yet, deepfakes pose a significant threat. Deepfakes are used to lure people to “click bait” for launching malware (bots, ransomware, malware), and to conduct financial fraud through CEO and CFO impersonation. More recently, deepfakes have been used by nation-state adversaries to infiltrate organizations via impersonation or fake jobs interviews over Zoom.
How are law enforcement agencies addressing the challenges posed by deepfake technology?
Europol has really been a leader in identifying GenAI and deepfake as a major issue. Europol supports the global law enforcement community in the Europol Innovation Lab, which aims to develop innovative solutions for EU Member States��� operational work. Already in Europe, there are laws against deepfake usage for non-consensual pornography and cyber criminal gangs’ use of deepfakes in financial fraud.
What should organizations consider when adopting Generative AI technologies, as these technologies have such incredible power and potential?
Every organization is seeking to adopt GenAI to help improve customer satisfaction, deliver new and innovative services, reduce administrative overhead and costs, scale rapidly, do more with less and do it more efficiently. In consideration of adopting GenAI, organizations should first understand the risks, rewards, and tradeoffs associated with adopting this technology. Additionally, organizations must be concerned with privacy and data protection, as well as potential copyright challenges.
What role do frameworks and guidelines, such as those from NIST and OWASP, play in the responsible adoption of AI technologies?
On January 26th, 2023, NIST released its forty-two page Artificial Intelligence Risk Management Framework (AI RMF 1.0) and AI Risk Management Playbook (NIST 2023). For any organization, this is a good place to start.
The primary goal of the NIST AI Risk Management Framework is to help organizations create AI-focused risk management programs, leading to the responsible development and adoption of AI platforms and systems.
The NIST AI Risk Management Framework will help any organization align organizational goals for and use cases for AI. Most importantly, this risk management framework is human centered. It includes social responsibility information, sustainability information and helps organizations closely focus on the potential or unintended consequences and impact of AI use.
Another immense help for organizations that wish to further understand risk associated with GenAI Large Language Model adoption is the OWASP Top 10 LLM Risks list. OWASP released version 1.1 on October 16th, 2023. Through this list, organizations can better understand risks such as inject and data poisoning. These risks are especially critical to know about when bringing an LLM in house.
As organizations adopt GenAI, they need a solid framework through which to assess, monitor, and identify GenAI-centric attacks. MITRE has recently introduced ATLAS, a robust framework developed specifically for artificial intelligence and aligned to the MITRE ATT&CK framework.
For more of Check Point expert Micki Boland’s insights into deepfakes, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2023#adversaries#ai#AI platforms#amp#analyses#applications#Articles#artificial#Artificial Intelligence#audio#bots#browser#Business#CEO#CFO#Check Point#CISSP#college#Community#content#copyright#CTO#cyber#cyber attacks#cyber security#data#data poisoning#data protection#Deep Learning
2 notes
·
View notes
Text


















🤝Hand holding support is available with 100% passing assurance🎯 📣Please let me know if you or any of your contacts need any certificate📣 📝or training to get better job opportunities or promotion in current job📝 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.aisensy.com/uemtSK 💯Proxy available with 100% passing guarantee.📌 🎀 FIRST PASS AND THAN PAY 🎀 ISC2 : CISSP & CCSP Cisco- CCNA, CCNP, Specialty ITILv4 CompTIA - All exams Google-Google Cloud Associate & Google Cloud Professional People Cert- ITILv4 PMI-PMP, PMI-ACP, PMI-PBA, PMI-CAPM, PMI-RMP, etc. EC Counsil-CEH,CHFI AWS- Associate, Professional, Specialty Juniper- Associate, Professional, Specialty Oracle - All exams Microsoft - All exams SAFe- All exams Scrum- All Exams Azure & many more�� 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.aisensy.com/uemtSK
#ccna#ccnatraining#ccnacertification#cisco ccna#awscloud#aws course#devops#cybersecurity#salesforce#pmp certification#pmp training#pmp course#pmp exam
1 note
·
View note
Text
Finding the path
I am self-taught in many of my interests. I have poured hours and hours into reading, seeking inspiration, and putting hard work into my pursuits. This year, I have pushed myself to obtain Comptia Security+ certification, ISC2 CC “Certified in Cyber Security,” and I am diligently working on studying for their CISSP “Certified Information Systems Security Professional” with a goal to complete…
0 notes
Text
CISSP: certificação em cibersegurança pode impulsionar carreiras no Brasil
De acordo com Dario Caraponale, CEO da Strong Security Brasil, a certificação CISSP (Certified Information Systems Security Professional) tem se consolidado como um dos principais diferenciais para profissionais que desejam crescer na área de segurança da informação. Emitida pelo ISC2 e reconhecida internacionalmente, essa credencial atesta o domínio técnico e estratégico de especialistas — em um…
0 notes
Text
cissp sertifikası
CISSP Sertifikası: Nedir, Avantajları ve Nasıl Alınır? 1. CISSP Sertifikası Nedir? CISSP (Certified Information Systems Security Professional), siber güvenlik alanında dünya çapında tanınan ve prestijli bir sertifikadır. Bu sertifika, bilgi güvenliği profesyonellerinin bilgi güvenliği yönetimi ve uygulamaları konusundaki yetkinliklerini ve uzmanlıklarını kanıtlamak amacıyla ISC2 (International…
0 notes
Text
Cybersecurity Career Roadmap: How to Start and Succeed in This High-Demand Industry
Introduction
The field of cybersecurity is expanding rapidly, with an increasing demand for skilled professionals. According to industry research, the global cybersecurity market is expected to grow significantly, creating numerous job opportunities. With the rise in cyber threats, organizations are actively looking for professionals to safeguard their digital infrastructure. If you're interested in starting a career in cybersecurity, this guide provides a clear roadmap from beginner to expert.
Why Consider a Career in Cybersecurity?
High Demand: Millions of cybersecurity roles remain unfilled worldwide, highlighting the need for skilled experts.
Lucrative Salaries: Cybersecurity professionals earn competitive salaries, often exceeding industry averages.
Career Growth: The job market for cybersecurity roles is expected to grow substantially in the coming years.
Flexible Work Options: Many positions offer remote work and flexible schedules.
Step-by-Step Guide to Starting a Cybersecurity Career
1. Learn Cybersecurity Fundamentals
Before pursuing certifications or degrees, gaining a solid foundation in cybersecurity is essential. Key topics to explore include:
Common cyber threats and vulnerabilities
Basics of network security
Encryption and data protection techniques
Cybersecurity frameworks and compliance standards
Introduction to ethical hacking and penetration testing
2. Pursue Relevant Education
A formal degree is not always necessary, but it can provide a strong foundation. Consider these options:
Bachelor’s Degree: Fields like Computer Science, Cybersecurity, or Information Technology
Associate Degrees or Bootcamps: Short-term, skill-focused programs
Self-Learning: Utilize free courses from platforms like Coursera, Udemy, and Cybrary
3. Earn Cybersecurity Certifications
Certifications validate your skills and improve employability. Some top beginner-friendly options include:
CompTIA Security+ (Ideal for entry-level professionals)
Certified Ethical Hacker (CEH) (For penetration testing roles)
Cisco Certified CyberOps Associate (Focuses on network security)
Certified Information Systems Security Professional (CISSP) (Advanced-level certification)
4. Gain Practical Experience
Hands-on experience is key to building your expertise. Ways to gain experience include:
Internships: Look for cybersecurity internships at tech companies.
Capture The Flag (CTF) Challenges: Participate in platforms like Hack The Box and TryHackMe.
Bug Bounty Programs: Engage in ethical hacking through platforms like HackerOne and Bugcrowd.
5. Build a Strong Resume and Online Presence
Optimize Your LinkedIn Profile: Highlight skills, certifications, and projects.
Create a Personal Blog or Portfolio: Share insights and showcase security-related work.
Use GitHub for Coding Projects: Demonstrate programming and security skills.
Network with Industry Professionals: Join communities like OWASP, ISC2, and DEF CON.
6. Apply for Entry-Level Cybersecurity Jobs
Some common starting roles include:
Security Analyst
IT Support Specialist with a Cybersecurity Focus
Network Security Technician
Security Operations Center (SOC) Analyst
Leverage job portals such as LinkedIn, Indeed, and Glassdoor to find opportunities.
7. Advance Your Career with Specialization
Once you have experience, consider specializing in areas like:
Penetration Testing & Ethical Hacking
Cloud Security
Incident Response & Threat Hunting
Cybersecurity Leadership (CISO roles)
8. Stay Updated on Cybersecurity Trends
Cybersecurity is constantly evolving. Stay informed by:
Following security news websites like Dark Reading and Krebs on Security
Attending cybersecurity conferences such as Black Hat and DEF CON
Earning advanced certifications like CISM or OSCP
Conclusion
A career in cybersecurity provides exciting growth opportunities, job stability, and attractive salaries. By following this roadmap, job seekers can build a solid foundation, gain experience, and advance in this dynamic industry. Start today, stay curious, and continue learning!
To Know more: https://appliedtech.in/cybersecurity/appliedtech/2025/03/13/cybersecurity-career-roadmap-how-to-start-succeed/3267/

0 notes
Text

Get Certified Information Systems Security Professional (CISSP)
The CISSP certifies an information security professional's extensive technical, managerial, and engineering knowledge and expertise.
WhatsApp https://wa.me/18175597620
CISSP #Certification from #CISSP #ISC2. #High #Pass Rate, #Best #Price Offer. In-House #services online
0 notes
Text









🤝Hand holding support is available with 100% passing assurance🎯 📣Please let me know if you or any of your contacts need any certificate📣 📝or training to get better job opportunities or promotion in current job📝 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.link/sihgby 💯Proxy available with 100% passing guarantee.📌 🎀 FIRST PASS AND THAN PAY 🎀 ISC2 : CISSP & CCSP Cisco- CCNA, CCNP, Specialty ITILv4 CompTIA - All exams Google-Google Cloud Associate & Google Cloud Professional People Cert- ITILv4 PMI-PMP, PMI-ACP, PMI-PBA, PMI-CAPM, PMI-RMP, etc. EC Counsil-CEH,CHFI AWS- Associate, Professional, Specialty Juniper- Associate, Professional, Specialty Oracle - All exams Microsoft - All exams SAFe- All exams Scrum- All Exams Azure & many more… 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.link/sihgby
Thanks & Regards,… Krishna Sinha (Subnetting Guru) Intact Technology & Consultant Contact : +1-8176686697 (USA) & +91-9674277941 (India)
0 notes
Text












🤝Hand holding support is available with 100% passing assurance🎯 📣Please let me know if you or any of your contacts need any certificate📣 📝or training to get better job opportunities or promotion in current job📝 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.link/ymcu0i 💯Proxy available with 100% passing guarantee.📌 🎀 FIRST PASS AND THAN PAY 🎀 ISC2 : CISSP & CCSP Cisco- CCNA, CCNP, Specialty ITILv4 CompTIA - All exams Google-Google Cloud Associate & Google Cloud Professional People Cert- ITILv4 PMI-PMP, PMI-ACP, PMI-PBA, PMI-CAPM, PMI-RMP, etc. EC Counsil-CEH,CHFI AWS- Associate, Professional, Specialty Juniper- Associate, Professional, Specialty Oracle - All exams Microsoft - All exams SAFe- All exams Scrum- All Exams Azure & many more… 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- https://wa.link/ymcu0i
#microsoft#software#azure#devops#aws#family#cisco#pmp#pmp training#pmp course#pmp certification#pmp exam
0 notes
Text
This International Women’s Day, meet a true technology trailblazer… - CyberTalk
New Post has been published on https://thedigitalinsider.com/this-international-womens-day-meet-a-true-technology-trailblazer-cybertalk/
This International Women’s Day, meet a true technology trailblazer… - CyberTalk


Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years in ICT, cyber security, emerging technology, and innovation. Micki’s focus is helping customers, system integrators, and service providers reduce risk through the adoption of emerging cyber security technologies. Micki is an ISC2 CISSP and holds a Master of Science in Technology Commercialization from the University of Texas at Austin, and an MBA with a global security concentration from East Carolina University.
In this incredible interview, Check Point Evangelist Micki Boland discusses her career, mentoring the next generation of women in cyber and so much more. This interview will make you feel inspired, enlightened and energized. Don’t miss this!
What inspired you to pursue a career in cyber security?
Great question… it was on my mind for a long time. I had been in IT and emerging technologies for years. I worked in electronics and electrical engineering for the U.S. Army and eventually designed, architected, deployed and managed IT and communications systems for Kaiser Permanente and Sprint.
Before there was a formalized career in cyber security, most techies “hacked” things, took things apart and rebuilt and fixed them. Many of the people who eventually became hackers started in telecommunications.
I began my MBA with a global security concentration (political science), and included national security policy, evolution of terrorism, counterterrorism, and public safety strategy.
I mashed this up with my passion for emerging technology in my Master of Science Commercializing Emerging Technology degree while I was an HQ engineer at Nortel. After much consideration, I made the jump to cyber security.
I had a lot of supporters along the way, which I am so very grateful for and, as I can never thank those folks enough, I have tried to pay it forward.
I wanted to start my own business. I did a lot of planning and advice seeking from trusted entrepreneurs, and I also needed also to develop myself in advanced pen testing, ethical hacking, and digital forensic investigation and response.
Then, I made a huge leap to starting my own digital forensics investigation firm: a woman veteran-owned firm with an excellent management team, in Texas — a state that requires you to be licensed private investigators. We did get licensed.
Many adventures were had and hurdles overcome. My firm spent most of our time doing machine learning for attack path graphing and top down security assessments. We had a big goal of working on specialized forensics and investigations (non-exploitation). We were constrained primarily to enterprise and law firm work. Later on, a family friend who was at Check Point encouraged me to come to Check Point. I joined up with the Global System Integrator team here and I love Check Point Software’s entrepreneurial spirit and culture!
Have you always been very interested in building things, systems and STEM?
Yes, as a kiddo I loved all science, technology, and math, how things are connected and how things work. I had a real aptitude for breaking, building and fixing things.
What career accomplishments are you most proud of?
I am humble and do not really like to talk much about myself. If I think about it though, I will have to say starting my own investigations firm was gutsy. It is one thing to create enterprise, study the market, develop “services”, build proformas, get funded and launch, and entirely different to sustain and grow this enterprise. Sales and marketing and acquiring and delighting new customers is everything! I encourage any woman wanting to start her own businesses to proceed with due diligence, bootstrap and do it, as it is simply an amazing experience.
As a woman in the cyber security industry, what challenges have you faced and how have you overcome them?
I think the challenges for me have been largely of my own making, in terms of insatiable curiosity, learning, growing, and continuous seeking of new challenges and adventures. I get bored easily and like to do new things.
On one hand, cyber security has fed my seeking behavior, as it is hugely dynamic. The industry is rapidly evolving, the threat landscape is ever changing; new and emerging technologies are being developed and rolled out that need to be protected, threat actors are honing their skills, as are defenders. It is never boring. On the other hand, my continuous seeking has limited my opportunities for senior leadership positions, as I do not seek to spend time in grade and/or wait for someone else to age out to get opportunities. This is a good thing. I would rather be an intrapreneur and leader, teaming, adapting, improvising, and overcoming challenges while continuously getting better and craftier.
That said, I think that, in cyber security, we should actively campaign for women, veterans, and people of all walks and backgrounds to join the cyber security field. We can provide development opportunities to gain skills and experience. We must not let opportunities constrain people that do not have 10 out of 10 skills and/or X years of experience, as frequently required within job descriptions. It is often said that women will not “fake it ‘till they make it” and will not go after roles that they feel they do not have 100% of the skills and experience required for.
Do not hesitate. If you want the role, you have to go for it. Plan and learn, get help if you need advice or a mentor, fill your gaps while you are in the job and in the field. If you want a career in cyber security grab the bull by the horns and get there!
What kinds of cyber security projects are you involved in at the moment that might inspire our readers?
Generative AI (all algorithmic machine learning) and computational intelligence (artificial neural networks ANN) have been my quest since starting my Master of Science at the University of Texas at Austin in 2009-2010. In my cohort were some of the most amazing and brilliant people.
Having been active in IEEE, I joined the Society for Design and Process Science and worked with a most talented Dr. Cristiane Gattaz, and her father (also Ph.D.) from Brazil, both of whom worked on ANN in the aerospace industry. I also got to meet Dr. Chittoor V. Ramamoorthy, Professor of Electrical Engineering and Computer Science, Emeritus, U.C. Berkeley (may he rest in peace) in Sao Paulo and Berlin, Dr. Robert Metcalfe, the inventor of Ethernet (Metcalfe’s Law), and founder of 3Com.
I met Gary Hoover, the founder of Hoover’s Business, which later became Dunn and Bradstreet. He is also the founder of Bookstop, which later became Barnes and Noble. All of these amazing people work in computational intelligence and nothing has been more exciting to me than neural networks, swarm intelligence, generative AI and large language models.
With emerging technologies, there are many perspectives: how organizations adopt these technologies without incurring additional risk; how the defenders (including Check Point with 50+ AI engines to deliver 99.7% confidence threat intelligence) are using these technologies to protect data, networks, people and devices; and the way the adversaries are utilizing these technologies to attack organizations. It does not get more fun than that!
And lastly, I will mention that these technologies have been utilized to create deepfake videos, voice clones, fake images and fake news. It will be increasingly important for humans to use a zero trust approach with the online content they consume and to also understand the uses of these technologies for manipulation, destabilization, disruption, distrust, to sway public opinion, and to foment violence.
How can we encourage more women to pursue careers in cyber security?
Check Point has an employee resource group called FIRE, an acronym that stands for Females In Roles Everywhere. I think this is a great place to start. In this organization, there is outreach to women within Check Point, among our partners and among customers. There are sponsored events, including those for females in leadership roles and the C-suite. There are mentoring and STEM initiatives. This is a great way to lead the charge in terms of attracting women to pursue careers in cyber security.
We can also get into K-12 schools and higher education — talking with students help them see the opportunities available in cyber security, with careers ranging from technical support, to coding, to threat hunting, to incident response, to architects, to engineers, to technical sales, and management.
In your opinion, what role does mentorship play in fostering the next generation of cyber security professionals?
Mentoring is extremely important in fostering the next generation of cyber security professionals. At all stages of our careers in this industry, we are all continuously learning. We have to keep learning. No one has more expertise and real world experience than the people on the ground working with customers every day; those helping them solve their cyber security challenges, responding to security incidents and securing their corporate assets and finances.
As we celebrate International Women’s Day, what message would you like to share with younger women who are thinking of pursuing a role in cyber security?
Be bold. Come and join the cyber security warriors. We need you and you are indeed very welcome! If this is the career you want, I assure you, you will love it. Never let obstacles stand in the way of achieving your goals. If you do not know how to proceed, reach out and get a sherpa to help you with your strategy. Over, under, around or through the mountain!
#IWD2024#adversaries#Advice#aerospace#aerospace industry#ai#AI engines#amazing#approach#Aptitude#artificial#artificial neural networks#assets#Behavior#berlin#Bootstrap#Brazil#Building#Business#C-suite#career#Careers#careers in cyber security#Check Point#Check Point Software#CISSP#coding#communications#computer#Computer Science
0 notes
Text
ISC2 CGRC Exam Highlights
NIST RMF (Source: NIST) With 20 study hours or so, I passed the ISC2 CGRC (formerly known as CAP) exam today (Jan 9, 2024). As a CISSP, I was reluctant to pursue the entry-level exam CC and US government-specific CGRC/CAP because CISSP covers job practices well enough. However, as a CISSP instructor, I must wear the same shoes to prove to my students that CC is a fantastic starter and a…
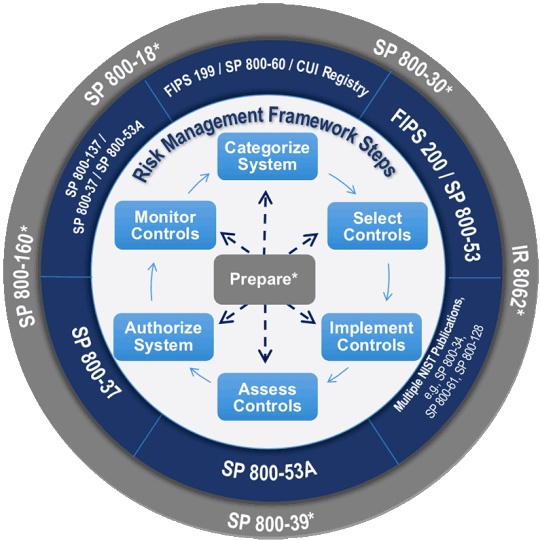
View On WordPress
0 notes
Text
🤝Hand holding support is available with 100% passing assurance🎯 📣Please let me know if you or any of your contacts need any certificate📣 📝or training to get better job opportunities or promotion in current job📝 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : Interested people can whatsapp me directly ✅WhatsApp :- WhatsApp https://wa.link/tq2u7b 💯Proxy available with 100% passing guarantee.📌 🎀 FIRST PASS AND THAN PAY 🎀 ISC2 : CISSP & CCSP Cisco- CCNA, CCNP, Specialty ITILv4 CompTIA - All exams Google-Google Cloud Associate & Google Cloud Professional People Cert- ITILv4 PMI-PMP, PMI-ACP, PMI-PBA, PMI-CAPM, PMI-RMP, etc. EC Counsil-CEH,CHFI AWS- Associate, Professional, Specialty Juniper- Associate, Professional, Specialty Oracle - All exams Microsoft - All exams SAFe- All exams Scrum- All Exams Azure & many more… 📲𝗖𝗼𝗻𝘁𝗮𝗰𝘁 𝗨𝘀 : If you interested in any of the IT #Certification #Trainig & #Dumps Please Ping me for further details WhatsApp https://wa.link/tq2u7b
0 notes
Text

How do I Buy #CISSP Certified Information Systems Security Professional Certification Exam?
You can purchase a CISSP (Certified Information Systems Security Professional) certification through the #ISC2 website or other online resources. Contact us via Skype id=(Jacob JB)
Buy CISSP Certified #Information #Systems #Security #Professional certification Exam
CLICK ON THE LINK BELOW TO MESSAGE US ON WHATSAPP 👇🏽👇🏽👇🏽👇🏽👇🏽👇🏽👇🏽👇🏽
0 notes