#Identity Server API Authentication
Explore tagged Tumblr posts
Text
Enhance Trust and Security with Seamless Background Check API
Background Check API are crucial as they enable businesses to seamlessly integrate background check functionalities into their systems. They provide valuable insights into an individual's history, helping to authenticate and establish trust, while enhancing security measures.

Are you looking to elevate trust, safety, and security within your business? Look no further than Authenticate! With our cutting-edge Background Check Integration API, you can unlock the power of background criminal checks and revolutionize your verification process.
Background checks have become an integral part of today's society, whether it's for employment, tenant screening, or partnership evaluations. The ability to authenticate an individual's background information has never been more crucial. That's where our Background Check API Integration comes into play, providing you with seamless access to comprehensive background check services, all within your existing system.
By incorporating our Background Check Integration API, you gain access to a wealth of information that can empower your decision-making process. From criminal records and employment history to education verification and reference checks, our API harnesses the latest technology to deliver accurate and up-to-date information in real-time. Say goodbye to manual processes and the potential for human error. With our API, you can automate the background check process and streamline your operations.
Why choose our Background Check Integration API? It's simple - we prioritize accuracy, security, and efficiency. Our API is designed to seamlessly integrate into your existing systems, providing a hassle-free experience. Whether you operate an HR platform, a rental management software, or a professional networking site, our API is flexible and customizable to fit your unique requirements.
By incorporating Background Criminal Check, you instill confidence and peace of mind in both your organization and your stakeholders. Trust is the cornerstone of any successful business relationship, and with our API, you can ensure that you are working with reliable individuals. From preventing fraud to protecting your brand reputation, our Background Check Integration API safeguards your interests.
Contact us today to explore the endless possibilities our Background Check Integration API has to offer. Our team of experts is ready to guide you through the integration process and help you unleash the power of background criminal checks. Together, we can elevate trust, security, and success in your business. For further info call us at +1 833-283-7439 or visit us at:- https://authenticate.com/!
#Background Check API#Background Criminal Check#Best Background Check#Check Your Criminal Record#Criminal Record Lookup#Id Verification API#Identity Check API#Identity Server API Authentication#Advanced Background Checks
0 notes
Text
What Are the Costs Associated with Fintech Software Development?

The fintech industry is experiencing exponential growth, driven by advancements in technology and increasing demand for innovative financial solutions. As organizations look to capitalize on this trend, understanding the costs associated with fintech software development becomes crucial. Developing robust and secure applications, especially for fintech payment solutions, requires significant investment in technology, expertise, and compliance measures. This article breaks down the key cost factors involved in fintech software development and how businesses can navigate these expenses effectively.
1. Development Team and Expertise
The development team is one of the most significant cost drivers in fintech software development. Hiring skilled professionals, such as software engineers, UI/UX designers, quality assurance specialists, and project managers, requires a substantial budget. The costs can vary depending on the team’s location, expertise, and experience level. For example:
In-house teams: Employing full-time staff provides better control but comes with recurring costs such as salaries, benefits, and training.
Outsourcing: Hiring external agencies or freelancers can reduce costs, especially if the development team is located in regions with lower labor costs.
2. Technology Stack
The choice of technology stack plays a significant role in the overall development cost. Building secure and scalable fintech payment solutions requires advanced tools, frameworks, and programming languages. Costs include:
Licenses and subscriptions: Some technologies require paid licenses or annual subscriptions.
Infrastructure: Cloud services, databases, and servers are essential for hosting and managing fintech applications.
Integration tools: APIs for payment processing, identity verification, and other functionalities often come with usage fees.
3. Security and Compliance
The fintech industry is heavily regulated, requiring adherence to strict security standards and legal compliance. Implementing these measures adds to the development cost but is essential to avoid potential fines and reputational damage. Key considerations include:
Data encryption: Robust encryption protocols like AES-256 to protect sensitive data.
Compliance certifications: Obtaining certifications such as PCI DSS, GDPR, and ISO/IEC 27001 can be costly but are mandatory for operating in many regions.
Security audits: Regular penetration testing and vulnerability assessments are necessary to ensure application security.
4. Customization and Features
The complexity of the application directly impacts the cost. Basic fintech solutions may have limited functionality, while advanced applications require more extensive development efforts. Common features that add to the cost include:
User authentication: Multi-factor authentication (MFA) and biometric verification.
Real-time processing: Handling high volumes of transactions with minimal latency.
Analytics and reporting: Providing users with detailed financial insights and dashboards.
Blockchain integration: Leveraging blockchain for enhanced security and transparency.
5. User Experience (UX) and Design
A seamless and intuitive user interface is critical for customer retention in the fintech industry. Investing in high-quality UI/UX design ensures that users can navigate the platform effortlessly. Costs in this category include:
Prototyping and wireframing.
Usability testing.
Responsive design for compatibility across devices.
6. Maintenance and Updates
Fintech applications require ongoing maintenance to remain secure and functional. Post-launch costs include:
Bug fixes and updates: Addressing issues and releasing new features.
Server costs: Maintaining and scaling infrastructure to accommodate user growth.
Monitoring tools: Real-time monitoring systems to track performance and security.
7. Marketing and Customer Acquisition
Once the fintech solution is developed, promoting it to the target audience incurs additional costs. Marketing strategies such as digital advertising, influencer partnerships, and content marketing require significant investment. Moreover, onboarding users and providing customer support also contribute to the total cost.
8. Geographic Factors
The cost of fintech software development varies significantly based on geographic factors. Development in North America and Western Europe tends to be more expensive compared to regions like Eastern Europe, South Asia, or Latin America. Businesses must weigh the trade-offs between cost savings and access to high-quality talent.
9. Partnering with Technology Providers
Collaborating with established technology providers can reduce development costs while ensuring top-notch quality. For instance, Xettle Technologies offers comprehensive fintech solutions, including secure APIs and compliance-ready tools, enabling businesses to streamline development processes and minimize risks. Partnering with such providers can save time and resources while enhancing the application's reliability.
Cost Estimates
While costs vary depending on the project's complexity, here are rough estimates:
Basic applications: $50,000 to $100,000.
Moderately complex solutions: $100,000 to $250,000.
Highly advanced platforms: $250,000 and above.
These figures include development, security measures, and initial marketing efforts but may rise with added features or broader scope.
Conclusion
Understanding the costs associated with fintech software development is vital for effective budgeting and project planning. From assembling a skilled team to ensuring compliance and security, each component contributes to the total investment. By leveraging advanced tools and partnering with experienced providers like Xettle Technologies, businesses can optimize costs while delivering high-quality fintech payment solutions. The investment, though significant, lays the foundation for long-term success in the competitive fintech industry.
2 notes
·
View notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
LiftMore Update 9.04.2023
I was posting updates on my Medium (see the pinned post), but lately I haven't had time to make a thorough post. Instead, I want to update on a few things in a more informal post here.
API Updates
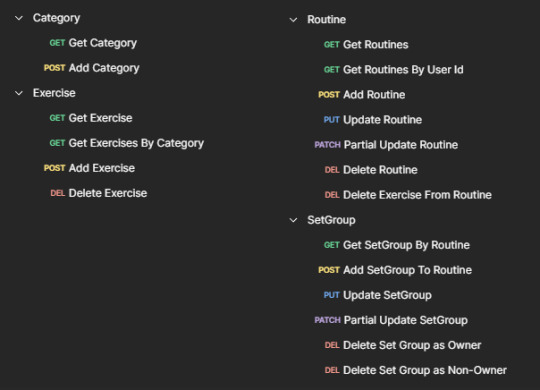
Finally went through and added all of the endpoints I'll need. There are a few endpoints on this list that I'm still in the process of refining permissions and making more secure.
Unit Testing ...ayup.. I came this far into the project without writing a single unit test. I really do want to strive for best TDD practices, but when there's no code at all in my application, it feels really unsatisfying to start working on tests before my code is capable of doing anything. Moving forward in the project, I will definitely strive to do TDD well.
Security Currently, the API just processes users via Basic Authentication. In this upcoming week, I'm planning on creating an identity server and using that server to issue my own OAuth2.0 tokens. I'm not sure yet how I want to set up my IDP service and OIDC Identity Providers.
Deployments Before moving onto the Front-End for this project, I want to make sure that my app is as secure and robust as possible. For this, I want to create 3 different environments (Development, Test, and Production), use a secret manager to inject secrets into the application, and have all of my deployments automated with GitHub Actions. In addition to all this, I want to make sure my application is set up properly between GitHub Actions and AWS so that I can manage dashboards and collect usage/cost information before having any users.
Finally, I'm happy to say that I've acquired the domain name "liftmore.app". After I get through some of the things I mentioned here, I'll push out a landing page and more information of LiftMore from a user perspective in case anybody wants to use it :)
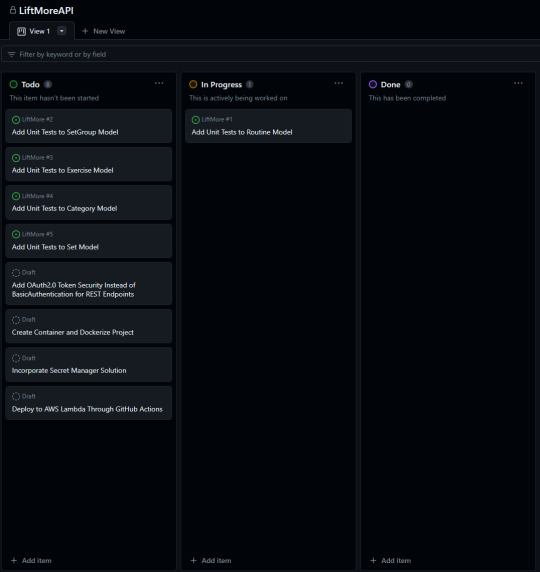
Lastly, little brief preview of my Project board in GitHub at the moment.
8 notes
·
View notes
Text
Top Challenges Web Development Companies Solve for Growing Brands
As your business grows, so do the expectations from your website. It’s no longer just a digital brochure—it’s your sales engine, lead generator, support channel, and brand identity rolled into one. Yet, as demands increase, many companies begin facing technical, design, and strategic roadblocks that can stall momentum.
This is where a Web Development Company becomes an essential partner. From handling complex integrations to future-proofing your platform, development agencies specialize in solving challenges that in-house teams may not be equipped to manage at scale.
1. Scaling Website Performance Under Growing Traffic
A major concern for any growing brand is website performance. As user traffic spikes, especially during product launches or campaigns, slow page loads or downtime can cost conversions and damage trust.
Professional development companies address this by:
Optimizing server architecture
Implementing caching strategies
Using CDNs for faster content delivery
Migrating to scalable cloud environments like AWS or Azure
These technical improvements ensure your site remains fast and available—no matter how quickly your business scales.
2. Managing Complex Integrations Across Systems
Growth brings more tools into your ecosystem—CRM platforms, inventory management, analytics tools, payment gateways, and marketing automation systems. The challenge is making all these systems communicate efficiently.
Web development companies build robust APIs and custom integrations that:
Sync data across platforms in real-time
Improve backend workflows
Enable personalized user experiences
Reduce manual errors
This level of technical harmony allows businesses to automate operations and focus more on growth strategies.
3. Ensuring Security and Compliance
As your brand attracts more users, it also becomes a bigger target for cyber threats. Ensuring data protection and regulatory compliance becomes non-negotiable.
A development agency strengthens your security through:
SSL implementation
Secure login and authentication systems
Regular vulnerability scanning
Compliance with global standards (like GDPR, CCPA, HIPAA)
With increasing customer expectations around data safety, proactive security is one of the most critical areas that expert developers address.
4. Creating Seamless Multi-Device User Experiences
Today’s users interact with your brand across desktops, tablets, and smartphones. An inconsistent experience on any of these devices can lead to lost engagement and sales.
Development companies apply responsive design principles and rigorous cross-browser testing to deliver:
Consistent UI/UX across all screen sizes
Intuitive navigation and interaction models
Faster mobile performance
This ensures that whether your customer is shopping, booking, or reading your blog—they enjoy a seamless experience every time.
5. Handling Content Management and Workflow Bottlenecks
Growing brands often struggle with content management. Outdated CMS platforms or poor backend architecture make publishing, editing, or localizing content a painful process.
A web development partner can:
Customize or migrate your CMS to a more scalable platform (like WordPress, Webflow, or headless CMSs)
Streamline your editorial workflows
Enable role-based access and approvals
This boosts content efficiency and lets your team stay focused on brand messaging instead of technical hurdles.
6. Maintaining Brand Consistency During Expansion
As businesses expand into new markets or launch new services, it becomes challenging to maintain brand consistency across all touchpoints.
Web development companies address this with:
Design systems and reusable components
Scalable style guides
Modular content blocks that adapt to new campaigns
This approach keeps your digital presence uniform while supporting the flexibility your marketing team needs.
7. Driving Continuous Optimization
Growth isn’t just about adding new features—it’s about refining what already exists. Development partners continuously test, monitor, and iterate to improve:
Conversion rates
Page performance
Funnel drop-offs
Technical SEO
By using tools like heatmaps, A/B testing platforms, and performance trackers, they help brands evolve based on real user behavior, not guesswork.
Conclusion
As your brand scales, so do the complexities of your digital infrastructure. A growing business needs more than a basic website—it requires a platform that evolves alongside it. Whether it’s integrating systems, securing customer data, optimizing for mobile, or scaling performance, these challenges can’t be left to chance.
That’s why partnering with a Web Development Company is not just helpful—it’s a strategic necessity. With deep technical knowledge and a forward-thinking approach, they ensure your website not only keeps up with growth but actively drives it.
0 notes
Text
What Comes Prebuilt in EasyLaunchpad: A Deep Dive into Features & Architecture

If you’re a .NET developer or startup founder, you’ve likely spent countless hours just getting the basics of your web app in place: login, admin dashboards, email systems, user roles, payments — the list goes on.
Now imagine you didn’t have to.
EasyLaunchpad is a complete .NET boilerplate��designed to help you skip the time-consuming setup phase and go straight to building your core application logic. But unlike generic templates, it’s not just a UI skin or a half-done framework. It’s a full production-grade starter kit with everything you need seamlessly working together.
In this blog, we’ll break down what actually comes prebuilt in EasyLaunchpad and how the architecture helps you launch scalable, maintainable apps faster than ever before.
🔧 Why Boilerplate? Why Now?
Before diving into the tech, let’s align on the problem EasyLaunchpad solves:
Every time you start a new project, you repeat:
Configuring authentication
Setting up admin panels
Managing users and roles
Handling emails and templates
Integrating payments
Adding job scheduling and logs
EasyLaunchpad does all of this for you — so you don’t have to start from scratch again.
⚙️ Core Technologies Behind the Boilerplate
EasyLaunchpad is built with a modern and stable tech stack designed for production:
Layer and Techbology used:
Backend Framework — .NET Core 8.0 (latest LTS)
Language — C#
UI — Razor Pages + Tailwind CSS + DaisyUI
ORM — Entity Framework Core
Dependency Injection — Autofac
Background Tasks — Hangfire
Logging — Serilog
Templating Engine — DotLiquid (for email templates)
This foundation ensures that your app is fast, secure, scalable, and easy to maintain.
Let’s explore what comes ready-to-use as soon as you start your EasyLaunchpad project.
✅ Authentication (Email + Google + Captcha)
EasyLaunchpad includes secure login flows with:
Email-password authentication
Google OAuth integration
CAPTCHA validation during login/registration
You don’t need to spend days integrating Identity manually — just plug and play.
✅ Admin Panel (Built with Tailwind CSS + DaisyUI)
The admin panel is clean, responsive, and fully functional. It’s built using Razor views and styled with TailwindCSS and DaisyUI, giving you a modern UI that’s easy to extend.
Pre-integrated modules in the admin panel include:
User Management: View, add, deactivate users
Role Management: Basic role assignment and user filtering
Package Plans: Define product plans for sale
SMTP & Email Settings: Easily configure mail servers
Feature Settings: Enable or disable system options without touching code
✅ Email System with Templates (DotLiquid)
Forget the hassle of writing email logic from scratch. EasyLaunchpad includes:
Prebuilt transactional email templates (e.g., registration, password reset)
SMTP integration
Templating via DotLiquid, making it easy to insert variables and personalize content
All email dispatches are logged and tracked, so you never lose sight of what’s been sent.
✅ Queued Emails & Background Tasks (Hangfire)
Want to schedule tasks like email reminders or data syncs?
EasyLaunchpad uses Hangfire for:
Background job processing
Scheduled cron jobs
Retry logic for email dispatch and failed tasks
You can manage jobs through the Hangfire dashboard or extend it into your app logic.
✅ Logging with Serilog
Every serious app needs structured, searchable logs. EasyLaunchpad integrates Serilog for:
Real-time activity tracking
Error logging
Request/response data logging
This gives you full visibility into what’s happening in your app, both during development and in production.
✅ Stripe & Paddle Payment Integration
Monetizing your app? EasyLaunchpad includes out-of-the-box integration for:
Stripe
Paddle
You can configure:
Payment plans
One-time purchases
Trial periods
And manage all of it through the admin panel without coding custom APIs.
✅ Packages & Licensing Management
You can create, manage, and connect subscription packages via the admin dashboard.
Each package can be tied to payment providers and synced to your external website or product gateway, making EasyLaunchpad ideal for:
SaaS products
License-based tools
Tiered services
✅ Notifications System
Built-in support for system alerts and user notifications includes:
Inline admin messages
Success/failure alerts on actions
Extendable for real-time or email notifications
🧱 Architectural Design That Supports Growth
Beyond just features, the architecture of EasyLaunchpad is designed for maintainability, extensibility, and scalability.
🧩 Modular Structure
Each module (e.g., Auth, Payments, Email, Jobs) is built to be independently extendable or replaceable. This lets you:
Swap Stripe for PayPal
Replace DotLiquid with Razor templates
Add new modules like CRM or Analytics
📁 Clean Codebase Layout
plaintext
CopyEdit
/Controllers
/Services
/Repositories
/Views
/Models
The code is separated by responsibility, making it easy to onboard new developers or modify any layer.
🔌 Plug-and-Play Capabilities
Need to build your own modules? The boilerplate is interface-driven and uses Autofac for dependency injection, so you can override or extend any logic without rewriting core code.
🌐 Real Use Cases
Here are a few real-world examples of how EasyLaunchpad can be used:
🧠 AI Tools: Launch OpenAI-based chat tools with user plans & payments
💼 B2B SaaS: Create dashboards with multi-user access, logs, and subscriptions
🛠 Admin Systems: Quickly build portals for internal staff or clients
💸 Subscription Services: Monetize features via built-in plans & licensing
🧠 Final Thoughts
Most boilerplates are either too basic or too bloated. EasyLaunchpad hits the sweet spot — it’s production-ready, focused, and elegant.
Everything you’d normally spend 3–4 weeks building? Already done.
With the structure and flexibility of a custom-built project — but without the hassle — you’re free to build what really matters: your product, your logic, your innovation.
👉 Ready to dive in? Get your copy of EasyLaunchpad and start building today:🔗 https://easylaunchpad.com
0 notes
Text
What Your Firewall Isn’t Telling You: Hidden Security Gaps Modern Businesses Can’t Ignore

Introduction: Your Firewall Is Working… or Is It?
If you're reading this, you're probably confident that your business is protected by a firewall. Good news? Not quite. Because what if the very thing you trust the most — your firewall — is quietly allowing gaps that hackers are counting on?
In the age of advanced persistent threats, evolving malware, and human error, traditional firewall setups are like castles in a world of drones. They weren’t built for today’s fast-paced, cloud security, AI-powered cyber battlefield.
At EDSPL, we believe security isn’t about adding layers — it’s about understanding what those layers are missing.
Chapter 1: Firewalls Were Designed for a Simpler Time
Once upon a time, businesses ran on static IPs, limited ports, and in-house servers. Firewalls worked as gatekeepers. But things have changed:
SaaS apps now run critical functions
Remote teams access sensitive data from coffee shops
APIs connect everything from your CRM to your IoT devices
Your firewall didn’t sign up for this level of complexity.
Keyword Focus: network security, legacy firewall limitations, modern network threats, cybersecurity for cloud era
Chapter 2: The 5 Major Gaps Your Firewall Might Be Hiding
Even if you’ve configured everything right, these five threats might still slip through:
1. Encrypted Threats (SSL/TLS Blind Spots)
Hackers hide payloads in encrypted traffic. Basic firewalls don’t inspect encrypted traffic deeply — making it the perfect cover.
🔍 Solution: EDSPL’s Advanced Deep Packet Inspection services detect threats in real time—even within encrypted streams.
2. Shadow IT & Unsanctioned Apps
Employees use tools that IT doesn’t approve. Firewalls might miss these if they mimic normal traffic patterns.
🛠 Solution: With EDSPL’s Endpoint & Application Visibility tools, you see everything happening — even what isn’t officially “visible.”
3. East-West Movement Inside the Network
Firewalls protect the perimeter, but once inside, attackers can move freely.
🔒 Solution: Microsegmentation and Zero Trust from EDSPL stop lateral movement cold.
4. APIs – The Blindly Trusted Gateways
Firewalls aren’t built for API-level validation. An exposed or misconfigured API can open floodgates.
🌐 Solution: EDSPL’s application security solutions analyze behavior and stop exploits in real time.
5. BYOD and Remote Access Risks
Your firewall doesn’t know if that phone accessing your CRM is an employee’s or a thief’s.
🧠 Solution: Identity-aware access control and mobility architecture by EDSPL create context-aware defenses.
Chapter 3: Why Compliance Isn’t Protection
Passing a security audit ≠ being secure. Firewalls may meet compliance standards but still leave you vulnerable. Think of:
Zero-day threats bypassing known signature filters
Misconfigured rules or outdated firmware
Internal user negligence (accidental or intentional)
Keyword Focus: firewall security audit, cybersecurity compliance vs. real protection
Chapter 4: Real-World Incidents — Where Firewalls Failed
🚨 Case 1: A finance firm had a Next-Gen Firewall but still suffered data exfiltration via encrypted Dropbox sync. 🚨 Case 2: An e-commerce company had a properly configured firewall, but internal movement allowed attackers to infect backup servers.
These aren’t hypotheticals. These are the new normal — and proof that a firewall alone is not enough.
Chapter 5: How EDSPL Closes These Gaps (The Right Way)
Let’s talk solutions. Here’s how EDSPL turns these weaknesses into strengths:
✅ Next-Gen Visibility
Our tools provide deep visibility across endpoints, APIs, and cloud apps.
✅ 24x7 SOC Monitoring
Our Managed and Maintenance Services detect and neutralize threats in real time — even those firewalls miss.
✅ Zero Trust Architecture
We don’t trust anything by default — not even internal traffic. Every connection is verified, authenticated, and monitored.
✅ SASE + ZTNA Integration
Move beyond hardware boundaries. EDSPL integrates identity, context, and data control into one seamless edge-to-cloud solution.
✅ Cloud-Native WAF & DDoS Protection
We defend your digital front doors at app and API levels — not just the perimeter.
Chapter 6: The Psychology of False Security
Many decision-makers stick with firewalls because it feels safe. It’s tangible. It's visible. But comfort isn’t protection.
Ask yourself:
Can your firewall detect behavior anomalies?
Does it understand your routing, switching, and compute environments?
Can it respond automatically to a breach?
If the answer is no, you’re not protected — you’re just hopeful.
Chapter 7: A Modern Security Blueprint – Built with EDSPL
Here’s a smarter architecture to replace blind firewall dependence:
Layered Detection (SIEM + SOAR)
User & Entity Behavior Analytics
Adaptive Access Controls
Threat Intelligence Integration
Endpoint + Network + Application Harmony
We include robust data center switching, storage, and backup frameworks in your enterprise blueprint.
At EDSPL, we design this blueprint around your real-world needs — not legacy models.
Conclusion: The Firewall Isn’t Dead. But It’s Not Enough.
Your firewall has served you well. But to protect your enterprise today, you need more than a wall — you need real-time visibility, behavioral intelligence, and automated response.
At EDSPL, we don’t just spot weaknesses — we rebuild security from the inside out.
Ready to see what your firewall isn’t telling you?
Call-to-Action
Book a Free Security Gap Assessment Let our experts assess your real-time firewall effectiveness and uncover blind spots before attackers do.
📞 9873117177 | 🌐 www.edspl.net | ✉️ [email protected] Reach Us or Get In Touch
Learn more about our vision
0 notes
Text
How APIs Power Modern Websites – A Think To Share IT Solutions Insight
Modern websites are no longer static brochures. They’re dynamic, data-driven platforms that interact with various services in real time. At the core of this interactivity lies a powerful and essential component: the API, or Application Programming Interface.
At Think To Share IT Solutions, we engineer websites that aren’t just visually compelling—they’re functionally superior, thanks to smart API integrations that enable real-time performance, seamless communication, and scalable features.
What is an API?
An API (Application Programming Interface) is a set of protocols and tools that allow software applications to communicate with each other. In web development, APIs act as bridges that connect your website to external or internal systems.
Instead of building every function from scratch, APIs allow developers to integrate existing, trusted services—making websites faster, more reliable, and more scalable.
How APIs Power Modern Websites
1. Dynamic Content Delivery
APIs allow websites to fetch and display real-time content from a database or CMS without refreshing the page. This improves performance and user experience.
Example: A blog or news portal pulling updated articles from a headless CMS like Strapi or WordPress via REST API.
2. User Authentication and Access Control
APIs handle secure user logins and permission-based access. Authentication services like Google OAuth or Auth0 rely entirely on API interactions.
Example: "Sign in with Google" uses an external API to verify the user's identity securely without storing sensitive data on your own servers.
3. Third-Party Service Integrations
APIs enable seamless integration with third-party platforms for added functionality.
Function
API Providers
Payments
Stripe, Razorpay, PayPal
Email Marketing
Mailchimp, SendGrid
Analytics
Google Analytics, Matomo
Customer Support
Zendesk, Intercom
Maps & Location
Google Maps API, Mapbox
These integrations enhance user experience without compromising performance or security.
4. Real-Time Features and Updates
Websites that support live chat, order tracking, or instant notifications use APIs to communicate with real-time databases.
Example: Firebase and Pusher APIs power real-time chat interfaces or live delivery status updates.
5. E-Commerce Functionality
Modern eCommerce websites rely on APIs to handle inventory updates, pricing changes, order processing, and shipping logistics.
What We Implement:
Cart management via REST or GraphQL APIs
Real-time pricing and availability updates
Shipment tracking using courier APIs (e.g., Delhivery, Shiprocket)
6. Headless Architecture
In a headless setup, APIs serve as the communication layer between the front-end and the back-end. This decoupling improves performance and allows for more flexible design and delivery across platforms.
Example: Using Next.js (for the front-end) and Strapi or Sanity (as the headless CMS), data is fetched via API endpoints and rendered statically or server-side for speed and SEO.
Benefits of API-Driven Web Development
Benefit
Explanation
Faster Deployment
Plug in pre-built services instead of coding everything from scratch
Scalability
Easily add new features or services without overhauling your system
Enhanced Security
Offload sensitive functions like payments to trusted platforms
Maintainability
Isolated services reduce complexity and ease troubleshooting
Cross-Platform
Share the same API with mobile apps, web apps, and IoT devices
How Think To Share Implements API-Driven Architecture
Our development process incorporates API planning from the very beginning:
Architecture Planning: Identify necessary APIs based on business goals
Security: Implement OAuth2, JWT tokens, and rate limiting for secure access
Performance: Use caching mechanisms (Redis, CDN) to reduce API load
Monitoring: Set up logging, error tracking, and fallback handling for resilience
Documentation: Provide detailed API docs using tools like Swagger or Postman
Final Thoughts: APIs Are the Backbone of Modern Websites
APIs have evolved from technical add-ons to mission-critical infrastructure for digital platforms. Whether you're running a website, mobile app, or enterprise software, APIs allow you to build faster, scale smarter, and connect deeper with users.
At Think To Share IT Solutions, we design and develop high-performance web systems that are modular, connected, and built for long-term growth—powered by reliable, secure, and well-integrated APIs.
0 notes
Text
Facing Compatibility Issues During Microsoft 365 Migration? Here's What You Need to Know
Microsoft 365 migration is never just a click-and-go process. Behind every successful move is a thorough compatibility check between systems, services, and user environments. If not done right, compatibility issues surface and disrupt everything from mailbox access to user authentication. These issues are more common than they should be, and they can derail your entire migration strategy.
Here’s a practical look at what causes these compatibility breakdowns and what steps you need to take to prevent them.

Legacy Systems That Don’t Meet Microsoft 365 Standards
Many organizations continue to operate with outdated infrastructure. Systems like Windows 7, older Outlook versions, or Exchange 2010 lack the protocols and security standards required by Microsoft 365. Without modernization, they create roadblocks during migration. For instance, a system that doesn’t support TLS 1.2 or Modern Authentication will fail to connect with Microsoft 365 services.
To prevent this, perform a full compatibility assessment of your OS, Exchange servers, and Outlook clients. Upgrade the environment or establish a hybrid setup that ensures continuity while you transition users.
Authentication Failures Due to Identity Conflicts
Identity and access management is a critical pillar in Microsoft 365. If your existing setup includes outdated AD FS configurations or incomplete Azure AD synchronization, users will face login failures, broken SSO, and token-related issues. Compatibility mismatches between your on-prem directory and cloud directory often go unnoticed until users can’t sign in after cutover.
Define your identity model well in advance. Whether you choose cloud-only, hybrid, or federated, validate it with pilot users. Ensure directory sync, UPN alignment, and conditional access policies are correctly applied.
Unsupported Add-ins and Custom Applications
Custom Outlook add-ins, CRM connectors, or VBA-based automations are often built around legacy environments. These integrations may fail in Microsoft 365 because they rely on outdated APIs or local server paths. Post-migration, users report missing features or broken workflows, which is not a mailbox problem but a compatibility one.
Catalog all active plugins and applications. Check vendor documentation for Microsoft 365 support. Transition to updated versions or re-develop legacy tools using supported APIs like Microsoft Graph.
PST and Archive Data That Can’t Be Imported
PST files from end-user systems or public folder archives frequently carry hidden corruption, non-compliant data formats, or unusually large attachments. These can cause import failures or lead to incomplete data availability after migration.
To avoid surprises, pre-scan PST files using tools that verify integrity. Break large PSTs into manageable sizes. Use modern utilities that support direct PST import with accurate folder mapping and duplicate prevention.
Email Clients and Mobile App Incompatibility
Not all email clients are built to support Microsoft 365. Legacy Android apps, IMAP clients, or older iOS Mail apps often lack support for OAuth or Modern Authentication. Once migrated, users might encounter repeated login prompts or full access loss.
Standardize supported apps in advance. Recommend and configure Outlook for mobile. Use device management policies to enforce security compliance. Disable access for non-compliant clients using conditional access in Microsoft 365 admin settings.
Loss of Mailbox Permissions and Calendar Access
Access issues post-migration are common when shared mailbox permissions or calendar delegation rights aren’t migrated properly. Users may suddenly lose visibility into shared mailboxes or receive errors when trying to access team calendars.
Before migrating, document all mailbox and folder-level permissions. After migration, reapply them using PowerShell scripts or a tool that automates permission preservation. Always validate shared access functionality with test users before expanding the migration to all users.
Conclusion
Compatibility issues don’t happen randomly during Microsoft 365 migrations. They are the result of incomplete planning or assumptions that legacy systems will integrate seamlessly with modern cloud environments. The only way to mitigate them is through comprehensive discovery, pre-validation, and the right migration tooling.
If you want to reduce risk and accelerate your migration with minimal disruption, consider using EdbMails Office 365 migration tool. It simplifies complex moves, retains all mailbox properties and permissions, supports hybrid and tenant-to-tenant scenarios, and ensures seamless migration across environments. It’s a trusted choice for IT teams who need control, flexibility, and reliability.
Additional links:
👉 Export Microsoft 365 Mailbox to PST
👉 Move public folders to office 365
#edbmails#office 365 migration software#incremental migration#office 365 migration#artificial intelligence#coding
0 notes
Text
Beyond Firewalls: What True End-to-End Cybersecurity Looks Like Today

In a world where digital transformation is no longer optional, cybersecurity has become the backbone of any successful business. And yet, many companies still approach it like a patchwork a firewall here, some antivirus software there, and a few compliance checkboxes ticked. But today’s threat landscape is far too complex for that kind of fragmented thinking.
At NetObjex, we believe cybersecurity must be built into the DNA of your digital operations not added as an afterthought. That’s what true end-to-end cybersecurity is all about. It’s not just about stopping threats at the door; it’s about securing every layer of your digital ecosystem, from edge devices to the cloud.
What Does “End-to-End” Really Mean?
“End-to-end” means comprehensive. It means you're not only protecting what’s visible — like your company’s website or internal server — but also what’s often overlooked: connected devices, APIs, mobile endpoints, backend data flows, and third-party integrations.
Let’s break that down:
Endpoint Protection: Every laptop, mobile device, or IoT sensor is a potential entry point for attackers. Securing these ensures that threats are blocked at the source.
Network Security: From VPNs to firewalls and intrusion detection systems, your internal communications should be monitored and encrypted.
Cloud Security: As more businesses move their data and apps to the cloud, secure configurations, identity access management, and encryption protocols become crucial.
Application Security: Vulnerabilities in your codebase — whether web or mobile — can be exploited if not rigorously tested and updated.
Data Protection: Whether data is at rest, in transit, or being processed, it should remain encrypted and inaccessible to unauthorized eyes.
Each layer must not only be secured but also intelligently connected — so that if something suspicious happens in one part of your system, the rest can respond in real time.
The Problem With the Old Way of Thinking
For years, businesses were instructed to "secure the perimeter." Firewalls were the initial and sometimes sole point of defense. But now, the perimeter no longer exists. Due to remote work, mobile devices, and cloud services, your data's everywhere — so are the threats.
Attackers are smarter, faster, and more relentless. Social engineering, phishing, ransomware, and advanced persistent threats don’t always knock at the front door. They find the weakest link — often a human one — and work inward.
That’s why relying solely on firewalls or antivirus software is like installing a steel door on a house with no windows.
How NetObjex Delivers True End-to-End Security
At NetObjex, we approach cybersecurity as a holistic system, not a toolkit. Here’s how we put that philosophy into action:
1. Edge-Level Protection with Smart Devices
Our IoT infrastructure ensures that devices are authenticated, data is encrypted at the edge, and firmware is continuously monitored. Whether it’s a smart parking sensor or a manufacturing robot, we secure every point where data originates.
2. Integrated AI & Machine Learning
We don’t just react to threats — we predict and prevent them. Our AI models identify unusual patterns, flag anomalies in real time, and adapt continuously. This assists in minimizing false positives while keeping incident response quicker.
3. Blockchain for Data Integrity
To secure transactional data, NetObjex leverages blockchain technology. Immutable, decentralized records prevent tampering and create a trustworthy audit trail. This is especially powerful in supply chains and smart city ecosystems.
4. Cloud-to-Device Encryption
We protect data streams from device to cloud, and vice versa. With our hybrid architecture, sensitive data is never left vulnerable — even in high-speed transfers between systems.
5. Fractional CISO Services
Not every business can hire a full-time cybersecurity executive and that’s okay. Our Fractional CISO offering ensures that even startups and SMEs have access to expert-level security leadership, risk assessments, and compliance guidance without stretching their budget.
A Real-World Example: Securing Smart Parking
Let’s take one of our own deployments — a smart parking system in a city environment. Here’s how end-to-end security comes into play:
The parking sensor at the edge is encrypted and authenticated.
The data it collects (availability, vehicle ID, payment info) is securely transmitted.
AI monitors for anomalies — such as spoofed devices or unusual patterns.
Blockchain records each transaction, creating trust in a public infrastructure.
The cloud dashboard used by the municipality is secured via role-based access and two-factor authentication.
This isn’t just “good IT hygiene.” It’s a proactive, multi-layered approach that prevents fraud, ensures citizen safety, and builds digital trust.
Why This Matters More Than Ever
In 2025 and beyond, cybersecurity is not just a technical concern it’s a business enabler. Customers demand privacy. Partners expect compliance. Investors look for risk mitigation. And regulators are tightening their grip.
Businesses that treat cybersecurity as a core competency not an add-on will gain the trust, scalability, and resilience they need to thrive.
Ready to Go Beyond the Basics?
If you’re still relying on firewalls and antivirus to protect your digital assets, it’s time to rethink your strategy. At NetObjex, we help businesses of all sizes design and deploy true end-to-end cybersecurity solutions that adapt, learn, and scale with you.
Discuss how we can future-proof your organization.
Get in touch with us today
#Managed Security Operations Center#Cybersecurity Risk Assessment and Audit#24/7 Threat Monitoring Services#Compliance and Vulnerability Management#End-to-End Cybersecurity Solutions#Fractional CISO
0 notes
Text
How to Use an API Key for Your ChatGPT Clone
Building a ChatGPT clone can be a game-changer for your business, product, or app. At the heart of this process lies one critical component — the API key. In this blog, you’ll learn what an API key is, how to get one, and how to use it effectively to power your custom chatbot solution.
Table of Contents
What is an API Key?
Why You Need an API Key for a ChatGPT Clone
How to Get an API Key from OpenAI
How to Use the API Key in Your ChatGPT Clone
Securing Your API Key
Alternatives to Manual Setup
Final Thoughts
Keyword Ideas
What is an API Key?
An API key is a unique code used to authenticate and interact with APIs. In the context of a GPT chatbot, this key allows your app to access and use the capabilities of the OpenAI language model, such as generating human-like responses or processing queries in natural language.
Why You Need an API Key for a ChatGPT Clone
When creating a ChatGPT clone, your backend will communicate with the GPT engine via API calls. Every request made to OpenAI's servers must be authenticated using a valid API key. Without it, your chatbot won’t be able to generate responses.
If you're using a ready-to-go ChatGPT clone, the platform might include API integration options that make the process even easier.
How to Get an API Key from OpenAI
Here’s a quick guide to obtaining your API key:
Create an OpenAI account at https://platform.openai.com
Verify your email and identity, if required
Navigate to your API Keys dashboard
Click on “Create new secret key”
Copy and save the key securely — it won’t be shown again
Note: Some usage may incur costs, depending on how much you use the API.
How to Use the API Key in Your ChatGPT Clone
Once you have the key, you can integrate it into your code. Here's an example in JavaScript using fetch():
javascript
CopyEdit
const response = await fetch("https://api.openai.com/v1/chat/completions", {
method: "POST",
headers: {
"Content-Type": "application/json",
"Authorization": "Bearer YOUR_API_KEY"
},
body: JSON.stringify({
model: "gpt-3.5-turbo",
messages: [{ role: "user", content: "Hello!" }]
})
});
Replace "YOUR_API_KEY" with your actual API key. You can do the same in Python, Node.js, or any language that supports HTTP requests.
Securing Your API Key
Never expose your API key in frontend code, public repositories, or browser-based scripts. Use environment variables or a secure backend to store and access the key. If compromised, someone could use your key and rack up charges on your account.
Alternatives to Manual Setup
Not comfortable with coding? No problem. Use platforms that offer pre-built solutions. A customizable ChatGPT clone comes with built-in API integration and features like chat UI, admin panel, and user authentication — all without the need to build from scratch.
Final Thoughts
Using an API key is a simple but crucial step when developing a ChatGPT clone. Whether you’re building a chatbot for customer service, productivity, or just experimenting with AI, securing and integrating your API key ensures your application runs smoothly. For a faster start, consider using a complete ChatGPT clone solution designed to work out of the box.
Reach out to the Miracuves team to start the conversation:
Website: https://miracuves.com Email: [email protected] Contact (US): +15162023950, (India): +91–983000–9649
0 notes
Text
Microsoft PQC ML-KEM, ML-DSA algorithms for windows & Linux

Microsoft has made significant progress in post-quantum cryptography (PQC) with SymCrypt-OpenSSL version 1.9.0 for Linux and Windows Insiders (Canary Channel Build 27852 and higher). This modification allows customers to test PQC algorithms like ML-KEM and ML-DSA in actual operational situations. Linux and Windows Insiders Get Quantum-Resistant Cryptography.
Due to quantum computing, modern cryptography faces significant challenges. Microsoft is providing early access to PQC capabilities to help organisations evaluate the performance, interoperability, and integration of these novel algorithms with current security infrastructure. This pragmatic approach helps security teams identify challenges, refine implementation strategies, and ease the transition when industry standards evolve. Early adoption also helps prevent new vulnerabilities and protect private data from quantum threats.
Next-generation cryptography API update
Cryptography API: Next Generation (CNG) enhancements are crucial to this Windows edition. CryptoAPI will be superseded forever by CNG. It is extendable and cryptography-independent. Programmers designing programs that allow safe data production and sharing, especially across insecure channels like the Internet, use CNG. CNG developers should know C, C++, and Windows, though it's not required. Cryptography and security knowledge are also advised.
Developers designing CNG cryptographic algorithm or key storage providers must download Microsoft's Cryptographic Provider Development Kit. First to support CNG are Windows Server 2008 and Vista. The latest PQC upgrades use encrypted communications, CNG libraries, and certificates.
New Windows PQC Algorithms
Microsoft is providing ML-KEM and ML-DSA, two NIST-standardized algorithms, to Windows Insiders via CNG updates.
Developers can now try ML-KEM for public key encapsulation and key exchange. This helps prepare for the “harvest now, decrypt later” scenario, in which hackers store encrypted data now to use a quantum computer to decipher it tomorrow. Microsoft proposes a hybrid method that combines ML-KEM with RSA or ECDH for defence in depth throughout the transition, ideally with NIST security level 3 or higher.
By incorporating ML-DSA in CNG, developers can evaluate PQC algorithms for digital signature verification of identity, integrity, or authenticity. Microsoft recommends a hybrid approach, using ML-DSA alongside RSA or ECDSA throughout the transition.
Size and performance will affect these new algorithms, according to preliminary research. Customers should analyse these consequences on their environment and apps early.
Customers can test installing, importing, and exporting ML-DSA certificates to and from the certificate store and CNG and PQC updates using the Windows certificate API interface win crypt. PQ certificate chains and trust status can be verified.
PQC Linux Features
Microsoft is releasing PQC upgrades in the SymCrypt provider for OpenSSL 3 because Linux customers expect them. The provider allows Linux programmers to use OpenSSL's API surface, which uses SymCrypt cryptographic procedures.
The latest IETF internet draft recommends SymCrypt-OpenSSL 1.9.0 for TLS hybrid key exchange testing. This lets you prepare for “harvest now, decrypt later” risks early. This feature allows for a full study of how hybrid PQC algorithms affect handshake message length, TLS handshake delay, and connection efficiency. Such research are needed to understand PQC's actual trade-offs.
It is important to remember that SymCrypt-OpenSSL will be updated when standards change to ensure compliance and compatibility, and that Linux updates are based on draft specifications.
What Next?
PQC's Linux and Windows Insider integration must be described first.
Plans call for more features and improvements:
Upcoming efforts include adding SLH-DSA to SymCrypt, CNG, and SymCrypt-OpenSSL.
Add new algorithms to assure broad compatibility as PQC standards expand, improve security, and comply with international law.
Working with industry partners on X.509 standardisations for the IETF's LAMPS working group's broad use of ML-DSA algorithm, composite ML-DSA, SLH-DSA, ML-KEM, and LMS/XMSS. These efforts will involve PKI use cases and signature approaches for firmware and software signing.
TLS hybrid key exchange for Windows users is being implemented using the Windows TLS stack (Schannel).
Develop and standardise quantum-safe authentication methods for TLS and other IETF protocols including SLH-DSA, Composite ML-DSA, and pure ML-DSA with the IETF. SymCrypt for OpenSSL, Windows TLS stack (Schannel), and Linux Rust Wrapper will deliver standards as they are established.
Active Directory Certificate Services actively supports PQC. Customers setting up a Certification Authority (CA) can use ML-DSA-based CA certificates. PQC algorithms sign CA-issued CRLs for customers who enrol in end-entity certificates. We'll support all ADCS role services.
Supporting PQC certificates in Microsoft Intune's Certificate Connector lets endpoints and mobile devices sign up for quantum-safe credentials. This will unlock SCEP & PKCS #12 scenarios for on-premises CAs utilising ADCS.
TLS 1.3 is essential for PQC. Microsoft strongly advises customers to abandon older TLS protocols.
These new features will be available to Windows Insiders and development channels for real-world testing. Microsoft can make incremental modifications before release by getting feedback on usability, security, and compatibility. Microsoft will distribute dependable and compatible solutions to supported platforms using a flexible and adaptable approach after standards are finalised. Working with standards organisations and industry partners will ensure features fit global regulatory framework and ecosystem needs.
Future challenges and prospects
Due to their youth, PQC algorithms are an emerging field. This shows how important “Crypto Agility” is in building solutions that can use different algorithms or be modified when standards change.
Microsoft recommends hybrid PQ and crypto-agile solutions for PQC deployment. Composite certificates and TLS hybrid key exchange use PQ and RSA or ECDHE algorithms. Pure PQ implementations should increase as algorithms and standards improve.
Despite integration being a turning point, PQC algorithms' performance, interoperability with current systems, and acceptance remain issues.
Performance: PQC algorithms often require more processing power than standard algorithms. Its efficient implementation without affecting system performance is a big hurdle. Technology for hardware acceleration and optimisation is essential. Keccak is utilised in many PQ algorithms, and hardware acceleration is needed to boost its performance for PQC cryptography.
Larger key encapsulation and digital signatures, especially in hybrid mode, may increase TLS round-trip time. Although signatures cannot be compressed, IETF proposals are examining certificate compression and TLS key sharing prediction. These effects should be assessed on applications and surroundings.
Adoption and Compatibility: PQC requires upgrading and replacing cryptographic infrastructure. Developers, hardware manufacturers, and service providers must collaborate to ensure legacy system compatibility and broad acceptance. Education and awareness campaigns and government-mandated compliance deadlines will boost adoption.
In conclusion
PQC incorporation into Linux and Windows Insiders is a major quantum future preparation step. Microsoft is proactively fixing cryptographic security flaws to help create a digital future that uses quantum computing and reduces security risks. PQC is needed to protect data, communications, and digital infrastructure as quantum computing evolves. Cooperation and security are needed to build stronger systems.
#MLDSAalgorithm#CryptographyAPI#PQCAlgorithms#MLKEM#MLDSA#PQalgorithms#MLKEMalgorithms#technology#technews#technologynews#news#govindhtech
0 notes
Text
From Concept to Launch: How Full Stack Developers Drive End-to-End Product Development
In today’s fast-paced digital world, where innovation and time-to-market can define the success of a product, having the right team is everything. Among the most vital players in any tech-driven project is the Full Stack Developer—the unsung hero who bridges the gap between vision and reality.
From concept to launch: how Full Stack Developers drive end-to-end product development is not just a technical journey—it's a collaborative, creative, and strategic one. Let’s dive into how these multifaceted professionals play a pivotal role in turning ideas into fully functional products.
Who is a Full Stack Developer?
A Full Stack Developer is a tech professional skilled in both front-end (what the user sees) and back-end (the server, database, and application logic) development. Think of them as the architects who not only design the house but also build the plumbing, electrical system, and interiors.
These developers wear many hats, often acting as problem solvers, strategists, and even project managers in smaller teams. They are well-versed in multiple technologies, frameworks, and tools, allowing them to handle every stage of the development lifecycle.
Why Full Stack Developers Are the Backbone of Product Development
When you’re launching a digital product—be it a mobile app, website, or SaaS platform—each phase of development requires agility, communication, and technical depth. Here’s how Full Stack Developers drive end-to-end product development:
1. Turning Ideas into Blueprints
Collaborate with stakeholders to understand the vision and goals.
Help define technical feasibility and suggest solutions.
Break down product concepts into actionable development tasks.
2. Designing the User Experience
Build interactive, intuitive, and accessible user interfaces using HTML, CSS, JavaScript, React, or Angular.
Ensure the product’s front-end aligns with brand identity and user needs.
Create responsive designs that work across devices.
3. Building a Strong Foundation
Develop robust backend systems using languages like Node.js, Python, Ruby, or PHP.
Integrate APIs, databases (like MongoDB or MySQL), and authentication systems.
Manage data flow and ensure application logic is efficient and secure.
4. End-to-End Integration
Seamlessly connect the front-end and back-end.
Ensure data consistency and real-time communication between different components.
Run tests across the full stack to identify and fix issues early.
5. Deployment and Launch
Set up server environments, cloud infrastructure (like AWS or Azure), and CI/CD pipelines.
Monitor system performance and scalability.
Assist in launching the product to live users and quickly iterate based on feedback.
The Human Side of Full Stack Development
It’s easy to get lost in the code, but being a Full Stack Developer isn’t just about programming. It’s about empathy, collaboration, and a deep understanding of the user. Many Full Stack Developers are passionate creators—they don’t just build software, they bring ideas to life.
Whether working in a startup or a large corporation, they:
Communicate closely with designers, marketers, and product owners.
Provide strategic input during planning and ideation.
Help teams pivot quickly when market demands change.
Benefits of Having a Full Stack Developer on Your Team
Faster Development Cycles: No need to coordinate between separate front-end and back-end teams.
Cost Efficiency: One skilled developer can handle multiple roles.
Holistic Problem Solving: They understand how all parts of the system interact.
Better Collaboration: They bridge communication gaps between technical and non-technical stakeholders.
Real-World Scenario: A Startup Success Story
Imagine a small startup aiming to build a fitness tracking app. With limited resources, hiring separate developers for every task isn't feasible. Enter the Full Stack Developer—within months, the MVP (Minimum Viable Product) is designed, developed, tested, and launched.
Not only did the developer write the code, but they also worked closely with the founders, gave input on features, helped with user onboarding flows, and made the app scalable for growth. This is how Full Stack Developers drive end-to-end product development—by becoming the glue that holds the entire product journey together.
Conclusion
From concept to launch: how Full Stack Developers drive end-to-end product development is more than a buzzworthy phrase—it's a testament to their versatility and value. In a digital landscape that demands speed, adaptability, and innovation, Full Stack Developers provide a holistic approach to building powerful, user-focused products.
Whether you’re launching your next startup or scaling a global platform, having a Full Stack Developer on your team could be the smartest decision you make.
0 notes
Text
What a Full-Stack Web Development Company Really Offers
In today’s fast-moving digital ecosystem, businesses don’t just need a website—they need a comprehensive digital solution that’s fast, functional, secure, and scalable. That’s where a Full-Stack Web Development Company comes in. From the moment your project is conceptualized to the final stages of deployment and beyond, a full-stack agency delivers an all-in-one solution for both the front-end and back-end of your digital presence.
Whether you’re launching a startup or scaling an enterprise product, understanding what these companies actually offer can help you make smarter, long-term decisions.
Front-End Development: Your Digital First Impression
The front end is what your users see and interact with—buttons, navigation, layouts, animations, and forms. A full-stack web development company ensures that your front end is not just beautiful but also functional across devices and browsers.
They work with technologies like:
HTML, CSS, JavaScript
Frameworks such as React, Angular, or Vue.js
UI/UX best practices for intuitive and accessible design
Beyond just building interfaces, they align your visual identity with usability. You get interfaces that convert, retain users, and reflect your brand story effectively.
Back-End Development: The Engine Behind the Experience
Behind every user action is a set of processes that connect your website to a server, database, or third-party service. That’s the back end, and it’s where a full-stack team shines.
They handle:
Server setup and database design
APIs and system integrations
Authentication and security layers
Logic for handling business operations (e.g., shopping carts, booking systems, dashboards)
By using powerful languages and frameworks like Node.js, Django, Laravel, Ruby on Rails, or .NET, full-stack developers ensure that your application is fast, secure, and scalable from day one.
Database Management: Organizing Your Digital Assets
Databases are essential for storing and retrieving user data, product information, analytics, and more. A full-stack web development company is adept at choosing and managing the right type of database for your project—whether it’s a relational database like PostgreSQL and MySQL or a NoSQL solution like MongoDB.
They not only build your data architecture but also manage:
Query optimization
Data backup and recovery
Scalable solutions for growing user traffic
This ensures your digital infrastructure remains agile and responsive even as your user base expands.
DevOps and Deployment: Going Live Smoothly
Launching a website isn’t as simple as clicking a button. A full-stack company also manages:
Continuous Integration/Continuous Deployment (CI/CD)
Server provisioning
Cloud hosting on AWS, Azure, or Google Cloud
Monitoring tools for uptime and performance
They streamline the process so your site not only launches smoothly but stays stable and updated post-launch.
Security & Compliance: Protecting What Matters
Security breaches can cost brands not just financially but reputationally. Full-stack web development companies implement proactive security measures:
SSL encryption
OWASP-compliant practices
Secure user authentication
GDPR and data protection compliance
With regular audits and automated security checks, they help you protect user data and avoid potential liabilities.
Maintenance & Scaling: Supporting Growth
Once the site is live, you’ll still need support. A professional full-stack company doesn’t walk away after deployment. Instead, it offers:
Ongoing performance monitoring
Bug fixes and upgrades
Server scaling
Feature enhancements
Whether you want to add a new product line, launch in a new country, or optimize your existing site’s speed, they’re your long-term partners in success.
End-to-End Consultation and Strategy
Beyond technical skills, what sets apart a true full-stack web development company is its ability to align tech with business strategy. They help you:
Define user personas
Map digital journeys
Prioritize features
Choose the right tools for your budget and scale
From MVP to enterprise product, your web partner acts as a digital co-pilot—helping you stay relevant in an ever-changing digital economy.
Conclusion
In essence, a Full-Stack Web Development Company offers far more than coding skills. It offers a strategic, end-to-end partnership to build, run, and grow your digital presence. From intuitive front-end experiences to robust back-end systems, database architecture, DevOps, and ongoing maintenance, a full-stack partner ensures that every layer of your website is aligned with performance and business outcomes.
If you're looking to build a resilient, future-proof digital platform, partnering with a Web Development Company that covers the full stack is one of the smartest investments you can make.
0 notes
Text
What Are the Challenges of Scaling a Fintech Application?

Scaling a fintech application is no small feat. What starts as a minimal viable product (MVP) quickly becomes a complex digital ecosystem that must support thousands—or even millions—of users. As financial technology continues to disrupt traditional banking and investment models, the pressure to scale efficiently, securely, and reliably has never been greater.
Whether you're offering digital wallets, lending platforms, or investment tools, successful fintech software development requires more than just technical expertise. It demands a deep understanding of regulatory compliance, user behavior, security, and system architecture. As Fintech Services expand, so too do the challenges of maintaining performance and trust at scale.
Below are the key challenges companies face when scaling a fintech application.
1. Regulatory Compliance Across Regions
One of the biggest hurdles in scaling a fintech product is adapting to varying financial regulations across different markets. While your application may be fully compliant in your home country, entering a new region might introduce requirements like additional identity verification, data localization laws, or different transaction monitoring protocols.
Scaling means compliance must be baked into your infrastructure. Your tech stack must allow for modular integration of different compliance protocols based on regional needs. Failing to do so not only risks penalties but also erodes user trust—something that's critical for any company offering Fintech Services.
2. Maintaining Data Security at Scale
Security becomes exponentially more complex as the number of users grows. More users mean more data, more access points, and more potential vulnerabilities. While encryption and multi-factor authentication are baseline requirements, scaling applications must go further with role-based access control (RBAC), real-time threat detection, and zero-trust architecture.
In fintech software development, a single breach can be catastrophic, affecting not only financial data but also brand reputation. Ensuring that your security architecture scales alongside user growth is essential.
3. System Performance and Reliability
As usage grows, so do demands on your servers, databases, and APIs. Fintech users expect fast, seamless transactions—delays or downtimes can directly affect business operations and customer satisfaction.
Building a highly available and resilient system often involves using microservices, container orchestration tools like Kubernetes, and distributed databases. Load balancing, horizontal scaling, and real-time monitoring must be in place to ensure consistent performance under pressure.
4. Complexity of Integrations
Fintech applications typically rely on multiple third-party integrations—payment processors, banking APIs, KYC/AML services, and more. As the application scales, managing these integrations becomes increasingly complex. Each new integration adds potential points of failure and requires monitoring, updates, and compliance reviews.
Furthermore, integrating with legacy banking systems, which may not support modern protocols or cloud infrastructure, adds another layer of difficulty.
5. User Experience and Onboarding
Scaling is not just about infrastructure—it’s about people. A growing user base means more diverse needs, devices, and technical competencies. Ensuring that onboarding remains simple, intuitive, and compliant can be a challenge.
If users face friction during onboarding—like lengthy KYC processes or difficult navigation—they may abandon the application altogether. As your audience expands globally, you may also need to support multiple languages, currencies, and localization preferences, all of which add complexity to your frontend development.
6. Data Management and Analytics
Fintech applications generate vast amounts of transactional, behavioral, and compliance data. Scaling means implementing robust data infrastructure that can collect, store, and analyze this data in real-time. You’ll need to ensure that your analytics pipeline can handle increasing data volumes without latency or errors.
Moreover, actionable insights from data become critical for fraud detection, user engagement strategies, and personalization. Your data stack should evolve from basic reporting to real-time analytics, machine learning, and predictive modeling.
7. Team and Process Scalability
As your application scales, so must your team and internal processes. Engineering teams must adopt agile methodologies and DevOps practices to keep pace with rapid iteration. Communication overhead increases, and maintaining product quality while shipping faster becomes a balancing act.
Documentation, version control, and automated testing become non-negotiable components of scalable development. Without them, technical debt grows quickly and future scalability is compromised.
8. Cost Management
Finally, scaling often leads to ballooning infrastructure and operational costs. Cloud services, third-party integrations, and security tools can become increasingly expensive. Without proper monitoring, you might find yourself with an unsustainable burn rate.
Cost-efficient scaling requires regular performance audits, architecture optimization, and intelligent use of auto-scaling and serverless technologies.
Real-World Perspective
A practical example of tackling these challenges can be seen in the approach used by Xettle Technologies, which emphasizes modular architecture, automated compliance workflows, and real-time analytics to support scaling without sacrificing security or performance. Their strategy demonstrates how thoughtful planning and the right tools can ease the complexities of scale in fintech ecosystems.
Conclusion
Scaling a fintech application is a multifaceted challenge that touches every part of your business—from backend systems to regulatory frameworks. It's not just about growing bigger, but about growing smarter. The demands of fintech software development extend far beyond coding; they encompass strategic planning, regulatory foresight, and deep customer empathy.
Companies that invest early in scalable architecture, robust security, and user-centric design are more likely to thrive in the competitive world of Fintech Services. By anticipating these challenges and addressing them proactively, you set a foundation for sustainable growth and long-term success.
0 notes
Text
Is AEPS Safe? Understanding the Security Behind It
Security is at the heart of AEPS. It leverages biometric authentication and Aadhaar validation — significantly reducing the risk of fraud, identity theft, or unauthorized transactions. Because it bypasses cards and PINs, it eliminates common vulnerabilities found in traditional banking.
Paysprint’s AEPS API builds on this foundation, offering end-to-end encryption, secure server communication, and real-time monitoring — ensuring every transaction is both fast and fraud-proof.
0 notes