#Identity Check API
Explore tagged Tumblr posts
Text
The Legal Effects of Employer Screening Without Using Criminal Record Lookup

In the modern workplace, employers must run extensive background checks on all new hires. This shields the business from possible legal repercussions while also assisting in ensuring worker safety. A Criminal Record Lookup is a vital component of background checks. We'll talk about the legal ramifications of not doing criminal record checks for hiring purposes in this blog article, as well as why it's so important for businesses to do so.
Let's first clarify what a criminal record check is. It is the procedure to obtain a person's criminal history that is accessible to the general public. Arrests, convictions, and sentences for both felonies and misdemeanors may be included in this data. Thanks to technological advancements, businesses may now obtain this data using Background Verification APIs, which improves the process' accuracy and efficiency.
Now, you might be wondering why running a criminal background check is so important. The possible legal repercussions of not doing so hold the key to the solution. Hiring someone with a criminal record exposes a firm to one of the biggest dangers, particularly if the illegal activity includes violence or fraud. The corporation may be held accountable for negligent hiring if a criminal history employee harms others or commits a crime there. A legal claim known as "negligent hiring" holds an employer accountable for the deeds of its workers if they knew or should have known about their risky inclinations.
On the other hand, running a Public Criminal Records check can also shield businesses from legal action. The employer won't be held accountable if a criminal recorded employee commits a crime outside of the workplace that has nothing to do with their duties. The criminal record check demonstrates that the business takes appropriate precautions to guarantee the security of its workers and clients.
Every company's hiring procedure has to include a criminal background check, since workplace safety and legal compliance are critical in today's society. To learn more call Authenticate at +1 833-283-7439 or visit:- www.authenticate.com!
#Background Checks for Landlords#Web API Identity Authentication#Identity Check API#Criminal Background Check#Background Check API Free
0 notes
Text
#kyc uk#kyc solution#kyc api#kyc software#background checks#background check companies#kyc aml solution#identity verification solution#background verification#kyc providers#fraud prevention
2 notes
·
View notes
Text
How Austrian Insurance Companies Are Strengthening Compliance with KYC Providers
Austria is a nation that is renowned for its stringent regulatory environment and commitment to financial stability. The insurance industry is a financial industry where regulatory compliance is not just a checkbox; it is a necessity of the business as the money laundering risks and identity fraud incidents are increasing rapidly in the financial industry. Compliance solution providers play a significant role in ensuring that insurance companies remain compliant with regulatory standards and prevent financial fraud.
#KYC providers in Austria#identity verification checks#compliance solutions#kyc providers#KYC API#AML API#AML solution#identity verification companies in Austria#KYC Providers For Austrian Insurance Companies#https://www.amlaustria.com
1 note
·
View note
Text
#kyc solution#kyc providers#kyc checks#kyc identity verification#kyc api#business#canada#kyc software#kyc in canada#background checks#kyc verification#fraud prevention
1 note
·
View note
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Note
I really should be studying physics right now but my mind is stuck in Brothers Ordeal AU and Biology right now 😭
So anyways, I have a theory/AU for BO and that is all the brothers are dead (excluding Daun) due to them not having one of the 7 signs of life. I'm not completely sure tho since I only skimmed through their lore (also because I was too focused on Cahaya and Daun haha)
Ok so let me cook
This all started with that one art of Angin in space being that judge figure (still need to read through that) and seeing Air taking care of his fusions in a fic (idk if you were the one who made it but I'll say it's canon) and I was like "I thought they're dead? Oh well I'll just roll with it" which got me thinking. Yes, they're dead but still act alive in some way.
The 7 signs of life are Movement, Respiratory, Sensitivity, Growth, Reproduction, Excretion, and Nutrition.
Angin lacks Respiratory, aka breathing, as seen with that one art of him in space, a place where oxygen is absent. Meaning Angin doesn't need to breath to sustain himself.
Cahaya lacks Sensitivity, aka the ability to react to his environment. Every living being requires this sense to react to the dangers in their environment (like how venus fly traps close in on insects or how chameleons change colors to camouflage themselves from predators) and since Sensitivity comes from the emotion fear (which Cahaya lacks), Cahaya would not be able to react to his environment accordingly.
I'm assuming Tanah would be Nutrition. Assuming he can still breathe, move, and act like an alive person, he wouldn't be able to scavange for food without any help due to the lack of limbs (also last I saw he's chained up).
I'm guessing Api would be Growth, mainly due to the fact that everytime he dies he just revives himself and I'm assuming that revival includes deaging, keeping him in a child's body, not allowing him to grow like his brothers.
Air would most likely be Movement due to his inabillity to... well... move around and last I checked, he's basically paralyzed with how much sleep he needs. His body can still get nutrition one way or another but due to the amount of sleep he needs, movement is just not an option for him.
As for Petir, I'm not completely sure but I assigned him Excretion (yes, assigned) because I desperately wanted to make the whole "one brother, one sign lacked" thing to work out and made Daun lacking Reproduction since that is one thing that is required in every species to survive, but not in every individual so yeah there's that 😅
Uhh... hope you liked it? Ok it's time for me to focus on physics BYE! :3
- Shu
This does describe them definitely but i never thought of anything bout any 7 signs of life and them being dead
But they are kinda dead when you think about it, lost memories, new identities
And they probably died and just got resuscitated
But anyways, this theory/au is super interesting, im learning through this in a way
#xoshi asks#xoshi answers#boboiboy#bbb brother ordeal au#that fic is made by nerialter and yes that one is canon#i think this could give ideas too#shu anon
4 notes
·
View notes
Text
Whatsapp API
In the era of digital transformation marketers finding innovative solutions to engage their target audience, build brand identity and drive conversions. Despite other performance marketing tools available, Whatsapp Marketing strategies has its own advantages
Check out this blog and uncover the potential, Whatsapp API have for your business.
3 notes
·
View notes
Text
Process "File" Descriptors (PID FD)
Linux in recent years has fixed some of the biggest annoyances I had with the UNIX model, and I'm feeling rather happy about this. One example of this is with how you can refer to processes.
With traditional UNIX APIs, you can never signal a process without a PID reuse race condition. The problem is somewhat inherent to the model: a PID is just an integer reference to a kernel-level Thing, but crucially, that Thing is not being passed around between processes. If I tell you the PID 42, that's not qualitatively different from you randomly picking the number 42 - either way, you can try to signal whichever process currently has PID 42. You might not have permissions to signal the current resident of that PID for other reasons, but you don't need a prior relationship to signal it - you don't need to receive any capability object from anyone. I haven't given you something tied to any process, I just gave you a number, and in the traditional UNIX model there's nothing better (more intrinsically tied to a single process) to pass around.
Compare file descriptors. An FD is also "just" an integer, but having that integer is worthless unless you also have the kernel-level Thing shared with your process. Even if I give you the number 2, you can't write to my stderr - I have to share my stderr, for example by inheritance or by passing it through a UNIX domain socket.
This difference is subtle but technically crucial for eliminating race conditions: since an FD has to be shared from one process to another through the kernel, and the underlying "file" descriptor/description is managed and owned by the kernel, when you later use the FD in a system call, the kernel can always know a fully unambiguous identity of which Thing you were referring to. If you just told it 42 in some global ID space, well do you mean the thing currently at index 42? Or did you really think you were referring to a thing which existed some time ago at index 42? That information has been lost, or at least isn't being conveyed. But if you told it 42 in your file descriptor table, now that can hold more information, so it can remember precisely which thing your 42 was referring to when you last received or changed it.
So how did Linux fix this?
We now have "PID FDs", which are magic FDs referring to processes. Processes "as a file", in a more true and complete way than the older procfs stuff.
Unlike PIDs, which by design can only travel around like raw numbers divorced from the true identity information they gesture at, a PID FD can never lose track of the process it refers to: if that process dies, its PID FD will forever "know" that its dead even if the PID is reused (because when that process yields to or is preempted by the kernel for the last time, the kernel remembers that there's a PID FD for it which needs to be updated, and even if the kernel recycles the PID it knows not to update that PID FD to point to the new process).
And we now have a system calls which let us
create a new process (or thread!) and have that return a PID FD instead of a PID (or "TID" in the case of threads, but in the Linux kernel those are basically the same thing)
signal a PID FD instead of the traditional PID (or TID), and
wait on a PID FD (in fact, the FDs just plug into the normal poll, select, or epoll system calls, so waiting on process or thread status can just hook into all existing event loops).
The one crucial thing is that we must not forget that these guarantees only start once we've gotten the PID FD: in particular, if you get a PID FD from a PID instead of getting the PID FD directly, you still need to check once if the PID hasn't gotten invalidated between when you got the PID and when you got the PID FD. This is something you can only do as the direct parent or (sub)reaper of the PID in question, because then you can use the traditional "wait" system call on the PID after getting the PID FD - if getting the PID FD succeeded but then the wait reports that the PID exited, that means you could've gotten a PID reuse by the time you got the PID FD from the PID.
So ideally, we just don't deal in PIDs at all anymore. When we create a process, we can get its PID FD atomically with the creation. (If we can't do that, if we're creating the process and then getting the PID FD with a separate system call, we do the wait check described in the last paragraph after getting the PID.) Then we pass the PID FD around - this might superficially look like passing an integer around, for example if you need to use the FD number in a shell redirection or communicate it to a child process, but underneath that the actual FD would be getting passed around either by inheritance, UNIX domain sockets, or whatever other means are available.
I've been wanting this for years. I've spent a lot of mental cycles trying to figure out the most elegantly minimal and composable primitives which could work around various problems in service supervision and automatic restarts in the face of random processes dying or getting killed. Those edge cases are now much more simple to totally cover by using the PID FD stuff, at least so long as we're willing to lose compatibility with the BSDs and other Unix-y systems until they catch up. Which, honestly, is an increasingly appealing proposition as Linux has been adding good stuff like this lately.
P.S. On that note, another thing we now have, is the ability to reach into a process (if we have its PID FD and have the same relationship to it (or elevated privileges) that we'd need to hook into it with debugger system calls) and copy a file descriptor out of it. This means we no longer need a child process to have been coded to share it with us through a domain socket or by forking or exec-chaining into a process we specify. Accessing file descriptors in already-running processes enables some neat monkey-patching and composition, and it's simpler to implement than the UNIX domain socket trick. I remember being frustrated about 7 years ago by the lack of ability to do exactly this - reach down into a child process (for example into a shell script, which has no built-in ability to access the "ancillary data" of a socket) and pluck a file descriptor out of it.
6 notes
·
View notes
Text
Powering Secure & Instant B2B Payments with Gridlines
In today’s fast-paced digital economy, instant, secure, and verified payments are no longer a luxury—they’re a necessity. For fintechs, NBFCs, marketplaces, and enterprises, the ability to automate business payouts without compromising on compliance or risk is crucial. That’s where Gridlines steps in—powering secure payment workflows through its advanced business verification and compliance APIs.
The Problem: Trust & Compliance Gaps in B2B Payments
B2B payment workflows often face significant hurdles—verifying the legitimacy of a vendor or seller, ensuring that payouts reach the correct bank accounts, and managing fraud risks during disbursal. Traditional KYC and KYB methods are slow, manual, and fragmented. For high-volume platforms like lending startups, gig marketplaces, or vendor-heavy enterprises, these inefficiencies are costly and dangerous.
Gridlines’ Solution: Real-Time Business Identity Verification
Gridlines offers a comprehensive API suite that enables platforms to build fully automated and compliant payment workflows. Whether you're sending payouts to vendors, disbursing loans, or onboarding new merchants, you need to verify who you're paying—instantly.
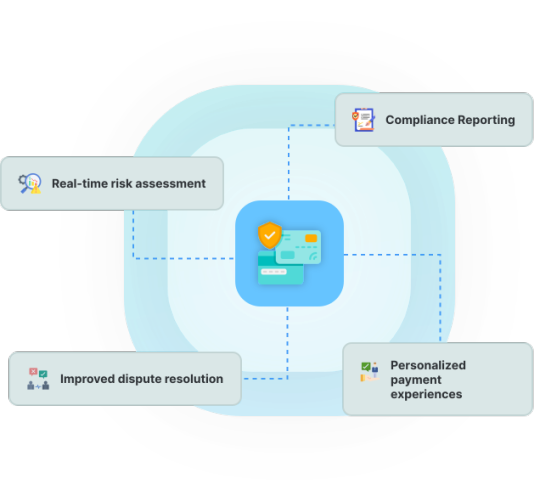
With Gridlines, you can:
Verify Udyam Registration Numbers to confirm MSME status
Cross-check PAN, GSTIN, and bank account ownership
Perform KYB (Know Your Business) checks in real-time
Ensure compliance with RBI and AML guidelines
All of this happens in seconds—giving you the confidence to release payments without manual intervention.
Key Benefits of Using Gridlines for Payments
Speed: Real-time APIs eliminate bottlenecks in disbursal.
Accuracy: Reduce payment errors and reversals with verified data.
Compliance: Stay audit-ready with in-built regulatory checks.
Scalability: Ideal for fintechs, gig platforms, and large enterprises handling bulk payouts.
Use Case Examples
NBFCs and Lending Startups: Automate business loan disbursals with verified KYB data.
Gig Marketplaces: Ensure the gig workers or vendors you pay are legitimate businesses.
E-commerce Platforms: Validate seller identity before enabling payouts.
Future-Proofing Your Payment Infrastructure
As regulatory norms tighten and fraud tactics evolve, having a future-proof and compliant payment infrastructure is a competitive advantage. Gridlines help you meet these demands while keeping the user experience frictionless.
By integrating Gridlines’ verification APIs, your platform ensures that every rupee disbursed is traceable, compliant, and secure—without slowing down operations.
Final Thoughts
Whether you're managing thousands of vendor payouts or offering instant working capital to SMEs, Gridlines is the API-first partner that enables safe, smart, and scalable payment operations. Get started with secure payment workflows that your business—and your regulators—can trust.
0 notes
Text
What is the Benefit of Using AVS?
Address Verification Service (AVS) is a critical component for any business that depends on the timely and accurate delivery of mail, packages, or services. AVS technologies cleanse, standardize, and verify mailing addresses in real time, ensuring that customer data is correct before sending out physical or digital communications. In this article, we delve into the myriad benefits of leveraging AVS, from cost savings and improved deliverability to fraud reduction and enhanced customer satisfaction.

1. Reduced Undeliverable Mail and Return Costs
Incorrect or incomplete addresses lead to undeliverable mail, which accrues return-to-sender fees and wastes printing, postage, and labor resources.
Cost Efficiency: AVS reduces return rates by up to 30%, slashing unnecessary postal expenses.
Operational Savings: Eliminating manual address correction tasks frees staff to focus on higher-value activities.
2. Improved Customer Experience and Satisfaction
Nothing frustrates a customer more than not receiving an order, invoice, or promotional offer.
Timely Deliveries: Verified addresses translate to on-time deliveries and happy recipients.
Professionalism: Clean address data enhances brand reputation by demonstrating attention to detail.
3. Enhanced Data Quality and Analytics
High-quality address data is a cornerstone of effective marketing analysis and business intelligence.
Accurate Segmentation: With standardized addresses, businesses can more effectively segment geographic markets and tailor campaigns.
Reliable Reporting: Clean data reduces statistical noise, yielding more trustworthy insights.
4. Compliance with Postal and Data Privacy Regulations
Postal authorities often mandate standardized addressing formats to ensure mail processing efficiency. Meanwhile, data protection regulations impose strict requirements on personal data handling.
Postal Certification: Many AVS providers are USPS’s Certified Commercial Mail Service Providers, ensuring official compliance.
GDPR and CCPA Alignment: Secure AVS solutions protect personal data and maintain audit logs for regulatory reporting.
5. Fraud Prevention and Risk Management
Address verification is a first line of defense against fraudulent transactions in e-commerce and financial services.
Identity Verification: Matching customer-provided addresses against authoritative postal databases helps spot stolen identities.
Chargeback Reduction: Financial institutions use AVS results to validate billing addresses, reducing credit card fraud and chargebacks.
6. Seamless Integration and Automation
Modern AVS solutions integrate via RESTful APIs, batch processing, or connectors with leading CRMs and e-commerce platforms.
Real-Time Verification: Front-end form validation prevents bad data from entering your systems.
Batch Cleansing: Periodic cleansing of legacy databases ensures ongoing data integrity.
Workflow Automation: Tools like Zapier, Make, and native plugins for Salesforce, Shopify, and Magento streamline address hygiene within existing business processes.
7. Scalability for Growing Businesses
From startups sending a handful of shipments to enterprises dispatching millions of parcels, AVS services scale effortlessly.
Pay-As-You-Go Pricing: Many providers offer usage-based billing, allowing businesses to pay only for verifications performed.
Flexible Deployment: Cloud-based AVS can handle sudden spikes in verification volume during peak seasons.
8. Additional Value-Add Features
Beyond basic address checks, AVS platforms often offer:
Geocoding: Latitude/longitude data attached to addresses for location-based analytics and route optimization.
Postal Intelligence: Insights into mail carrier performance, delivery windows, and service levels.
International Formatting: Support for local postal formats in over 200 countries, reducing international shipping errors.
9. Return on Investment (ROI) Analysis
Quantifying the benefits of AVS helps secure budget and stakeholder buy-in.
Cost Savings Calculation: Compare the total cost of undeliverable mail (returns, reprints, labor) against AVS subscription fees.
Revenue Uplift: Improved delivery rates can boost repeat purchases and positive word-of-mouth referrals.
Conclusion
In today’s data-driven and customer-centric marketplace, Address Verification Service is no longer a nicety but a necessity. By ensuring that every piece of mail and package reaches its intended destination, AVS drives cost efficiencies, elevates customer satisfaction, enhances data quality, and fortifies fraud defenses. Investing in a scalable, compliant, and feature-rich AVS solution empowers businesses to operate confidently, knowing that their address data is accurate and their communications are effective
youtube
SITES WE SUPPORT
Tips To Send Direct Mail – Wix
1 note
·
View note
Text
Enhance Trust and Security with Seamless Background Check API
Background Check API are crucial as they enable businesses to seamlessly integrate background check functionalities into their systems. They provide valuable insights into an individual's history, helping to authenticate and establish trust, while enhancing security measures.

Are you looking to elevate trust, safety, and security within your business? Look no further than Authenticate! With our cutting-edge Background Check Integration API, you can unlock the power of background criminal checks and revolutionize your verification process.
Background checks have become an integral part of today's society, whether it's for employment, tenant screening, or partnership evaluations. The ability to authenticate an individual's background information has never been more crucial. That's where our Background Check API Integration comes into play, providing you with seamless access to comprehensive background check services, all within your existing system.
By incorporating our Background Check Integration API, you gain access to a wealth of information that can empower your decision-making process. From criminal records and employment history to education verification and reference checks, our API harnesses the latest technology to deliver accurate and up-to-date information in real-time. Say goodbye to manual processes and the potential for human error. With our API, you can automate the background check process and streamline your operations.
Why choose our Background Check Integration API? It's simple - we prioritize accuracy, security, and efficiency. Our API is designed to seamlessly integrate into your existing systems, providing a hassle-free experience. Whether you operate an HR platform, a rental management software, or a professional networking site, our API is flexible and customizable to fit your unique requirements.
By incorporating Background Criminal Check, you instill confidence and peace of mind in both your organization and your stakeholders. Trust is the cornerstone of any successful business relationship, and with our API, you can ensure that you are working with reliable individuals. From preventing fraud to protecting your brand reputation, our Background Check Integration API safeguards your interests.
Contact us today to explore the endless possibilities our Background Check Integration API has to offer. Our team of experts is ready to guide you through the integration process and help you unleash the power of background criminal checks. Together, we can elevate trust, security, and success in your business. For further info call us at +1 833-283-7439 or visit us at:- https://authenticate.com/!
#Background Check API#Background Criminal Check#Best Background Check#Check Your Criminal Record#Criminal Record Lookup#Id Verification API#Identity Check API#Identity Server API Authentication#Advanced Background Checks
0 notes
Text
#background checks#fraud prevention#identity verification solutions#KYC API#kyc solution#kyc uk#fintech#banks#finance#identity verification system
2 notes
·
View notes
Text
The Role of KYC Companies in Austria: From Background Checks to Compliance Solutions
Compliance solutions are strategic needs for banks, financial institutions, insurance, fintech, forex, trading, and other non-financial businesses like healthcare, real estate, e-commerce, telecom, age-restricted products, and services-based businesses such as alcohol, pharmaceutical, online gaming, dating, vaping, tobacco, lottery, and adult-only industry business. KYC Companies in Austria play a considerable role in conducting KYC checks to ensure the customer’s identity and Know Your Customer (KYC) compliance for financial and non-financial businesses.
#kyc solutions#kyc checks#identity verification solutions#kyc api#aml solution#fraud prevention#kyc solution providers#kyc service providers#age verification solution#id verification solution#kyc platform#kyc companies#aml Austria
1 note
·
View note
Text
#KYC Services Provider#Background Checks in Canada#KYC service providers in Canada#KYC API#KYC solution#AML solution#identity verification system#identity verification solutions
1 note
·
View note
Text
Beyond KYC: How Identity Verification is Evolving for Modern Businesses
In today's fast-paced digital economy, traditional Know Your Customer (KYC) processes are no longer enough to verify identities or prevent fraud. Businesses are now adopting more sophisticated identity verification technologies that go beyond KYC, enhancing security, streamlining onboarding, and improving compliance. But what exactly is driving this shift, and how can your business benefit?
The Limitations of Traditional KYC
KYC was primarily designed for financial institutions to prevent money laundering and financial fraud. While it laid the groundwork for identity verification, it often relies on static documents and manual checks that are time-consuming and vulnerable to tampering.
With the explosion of digital services—from banking and fintech to gig platforms and healthcare—companies need more robust, real-time solutions to onboard users safely and at scale.
The Rise of Smart Identity Verification
Modern businesses are now embracing advanced identity verification methods powered by artificial intelligence (AI), machine learning (ML), biometrics, and access to real-time government databases. These tools offer several advantages:
Real-Time Verification: Instantly validate PAN, Aadhaar, Udyam Registration, GST, and other official documents through secure APIs.
Biometric Authentication: Facial recognition and liveness checks reduce impersonation risks.
Ongoing Monitoring: Continuous background screening and risk alerts help businesses stay compliant even after onboarding.
Platforms like OnGrid have been at the forefront of this transformation, offering digital identity verification solutions that go beyond basic KYC. These systems are designed not just for regulatory compliance, but also to establish trust and efficiency across sectors.
Benefits for Businesses
Whether you're in lending, insurance, workforce management, or gig economy platforms, adopting smart identity verification brings tangible advantages:
Faster Onboarding: Eliminate delays caused by manual document checks.
Reduced Fraud: Prevent synthetic identities and document forgery with AI-based validation.
Enhanced User Experience: Offer a seamless and secure onboarding journey.
Regulatory Compliance: Stay ahead of evolving norms like CKYC, eKYC, and KYB with modular APIs.
Looking Ahead: Identity as a Trust Layer
Identity verification is no longer just a regulatory checkbox—it has become the foundation of digital trust. The evolution from KYC to a dynamic, data-driven identity ecosystem reflects a broader trend in how businesses interact with customers and partners. In a world of rising fraud and digital risks, investing in robust identity infrastructure is no longer optional.
Solutions like OnGrid’s plug-and-play APIs and comprehensive identity verification tools are helping businesses scale securely, comply confidently, and grow faster.
#BeyondKYC#IdentityVerification#DigitalOnboarding#AIinCompliance#BusinessSecurity#OnboardingSolutions#KYC#KYB#FraudPrevention#OnGrid#eKYC#RegTech#DigitalTrust#BiometricVerification
0 notes
Text
Google developers OAuth 2.0 playground And OpenID Connect

Google Auth Platform usability and security updates
Millions of developers authenticate users and access hundreds of APIs using Google's identity platform. One of the largest implementations of the Google developers OAuth 2.0 playground protocol and OpenID Connect standard in the world provides developers with a reliable, secure, and easy method to interact. Google is pleased to announce significant platform usability and security improvements.
Google engineers' OAuth 2.0 playground
Simple OAuth setting in Google Cloud Console
Developers that use Google Sign-in for authentication or user consent to use Google APIs must register their applications and websites to generate client credentials. Developers utilising Google Cloud Console previously found OAuth setup pages under APIs & Services. Separate navigation for Google Auth Platform is added to these sites.
This version speeds up app configuration updates, simplifies project registration, and improves developer advice. Upcoming improvements include an improved onboarding wizard, simpler OAuth scope management, and faster, more transparent app verification.
Developers using other consoles for OAuth have the same Firebase or Apps Script experience.
OAuth client secret presentation change
Some OAuth clients require a “secret” for authorisation and authentication. Since the client secret operates like a website or application password, protecting these strings is crucial to user account and data security.
Developers could previously download client secrets from Google Cloud Console, Firebase Console, and other Google developer tools. OAuth secrets will be hidden in Google Cloud Console client administrative pages in June. Developer consoles will show the last few characters to help identify them.
OAuth client secrets must be downloaded and handled securely by developers. For this, most developers utilise Google Cloud Platform's Secret Manager. The client secret won't appear when the creation screen closes.
Never reveal OAuth client secrets that provide access to user data or other production systems online or in version control systems. If secrets leak, change them immediately and cycle them often.
Automatic deactivation of unused OAuth clients
Starting in June, OAuth clients inactive for six months will be automatically terminated to prevent credential theft and misuse. When token exchanges end, the six-month period begins.
When inactive clients are erased, developers will be notified and can recover them for 30 days.
A great experience for you and your customers
These upgrades and more planned for later this year make your experience smoother and safer, giving you more time to build great applications and websites for your consumers.
Accessing Google APIs with OAuth 2.0
Simple acts
Every Google API-accessing app utilising OAuth 2.0 follows a pattern. You take five stages typically:
The Google API Console gives OAuth 2.0 credentials.
Get an access token from Google Authorisation Server.
Review user-granted access scopes.
Give an API the access token.
Update the access token if needed.
Google APIs authorise and authenticate using OAuth 2.0. Google supports OAuth 2.0 applications for web servers, client-side, installation, and limited-input devices.
Get OAuth 2.0 client credentials from Google API Console to begin. After that, your client app requests an access token from the Google Authorisation Server, extracts it, and sends it to the Google API you want to use. Check out the OAuth 2.0 Playground for an interactive Google OAuth 2.0 demonstration using your own client credentials.
#technology#technews#govindhtech#news#technologynews#Google developers OAuth 2.0 playground#Google developers OAuth#OAuth 2.0#OAuth clients#OAuth 2.0 playground#OAuth
0 notes