#Kernel security check failure
Explore tagged Tumblr posts
Text
Upgrade Your Steam Deck Experience with SteamOS 3.6.19

SteamOS 3.6.19 release with big update for Steam Deck support in a variety of areas, even games. Thanks to the Valve team and all the players who shared their feedback. Available for all owners via Steam. Good news, fellow Steam Deck users. SteamOS 3.6.19 has released with a whole range of updates, tweaks, and fixes to make our Deck experience even better. Let’s dive into what’s new, and I’ll keep it simple and to the point.
System Updates
First off, SteamOS 3.6.19 now runs on an updated Arch Linux base with the Linux kernel bumped up to version 6.5. What does that mean for us? It translates to better hardware compatibility, smoother performance, improved security, and a more stable system overall. If you’ve had any issues with random crashes or slow updates, those should be less of a problem now. Speaking of SteamOS 3.6.19 updates, they’ve made future OS updates quicker, which is always a win. Also, there are fixes for certain microSD cards, especially some SanDisk ones that were being misread by the Deck. Plus, session restarts should be faster, especially if your system glitches from GPU errors. If you’ve run into issues with long play sessions causing crashes (like the annoying ‘page allocation failure’). That’s has a patch too. And for those unlucky few who had corrupted Steam installations, recovery should now be smoother.
Wi-Fi and Connectivity Fixes
Steam Deck also fixed several Wi-Fi issues. You should have fewer connection problems, especially if you’re using WPA3 security or Wi-Fi 7 access points. Plus, Valve’s handheld should handle cursor alignment and performance overlay glitches more effectively. Which is also a nice touch.
SteamOS 3.6.19 Display and Performance
For anyone using the OLED model, display issues like weird refresh rates, gray lines during boot, or random screen blacks should be gone. There’s also better color balance and gamma uniformity, meaning the display should look crisper and less “greenish” in low brightness settings. VRR (Variable Refresh Rate) issues with external displays have also have a fix now. Due to make gaming on bigger screens a better experience.
Bluetooth and Controllers
Big win for Bluetooth users—there’s improved pairing for Apple AirPods, and new support for HFP and BAP Bluetooth profiles. They’ve made sure only certain Bluetooth devices (like controllers) wake up the system. So your Deck won’t suddenly power on when you don’t want it to. Some controller bugs have been fixed in SteamOS 3.6.19 too. Check out the gear that now has support through each link, so you can get exactly what you need. Especially for the DualShock 4 and DualSense controllers. Also, Steam Deck now officially supports the ASUS ROG Ally extra keys, Raikiri Pro controller, and Machenike G5 Pro controller, which is great for those who use these peripherals.
Desktop Mode and Docking
If you’re a fan of Desktop Mode, there are a few KDE Plasma updates (now at 5.27.10). SteamOS 3.6.19 also offers a bunch of fixes to ensure smoother switching between Desktop Mode and gaming. External display issues (like blank screens or crashes) should be fixed now too. For those using the Docking Station, there are new HDMI CEC features, meaning you can control things like waking up the TV or switching inputs with your Deck, which is pretty neat.
Battery Life and Power
Steam Deck LCD users will notice up to a 10% battery life improvement under light load situations, which is always welcome. There’s also better power management with fixes for things like random power LED blinking.
SteamOS 3.6.19 Game Fixes and More
A bunch of game-specific fixes are also apart of the changes. Titles like BlazBlue Centralfiction, Warriors All-Stars, ELDEN RING, and Disgaea 5 Complete should all run smoother without those annoying display glitches or crashes. Even game recording should work better with fixes for colors and capture issues.
Final Thoughts
Overall, this is full of useful upgrades, from better Bluetooth and controller support. Also, smoother display handling and more reliable updates. So, if you’ve been running into any of these issues. SteamOS 3.6.19 should make your Valve handheld that much better to play games. Time to get gaming and enjoy these fresh fixes. Available for all owners via Steam.
2 notes
·
View notes
Text
Check Point Certified Troubleshooting Expert 156-587 Practice Exam
In the ever-evolving world of cybersecurity, the ability to troubleshoot complex security issues is a highly sought-after skill. The Check Point Certified Troubleshooting Expert - R81.20 (CCTE) (156-587) certification is designed for security professionals aiming to excel in diagnosing and resolving advanced issues within Check Point security environments. This advanced-level credential validates expertise in managing and troubleshooting Check Point Security Management and Security Gateway systems, making it a valuable asset for network security professionals, engineers, and consultants. To help candidates prepare effectively, Cert007 offers a comprehensive Check Point CCTE R81.20 156-587 Practice Exam tailored to ensure success. This article explores the CCTE R81.20 certification, its benefits, structure, and how Cert007’s practice exams can pave the way to achieving this prestigious credential.
What is the Check Point CCTE R81.20 (156-587) Certification?
The Check Point CCTE R81.20 (156-587) certification is an advanced credential that equips security professionals with the skills to troubleshoot complex issues in Check Point security environments. It focuses on advanced troubleshooting techniques, including firewall kernel debugging, VPN diagnostics, log analysis, and performance optimization. This certification validates a candidate’s ability to maintain secure and resilient enterprise networks by resolving issues related to Check Point Security Management Architecture and Security Gateways.
This certification is ideal for:
Network Security Professionals managing Check Point security infrastructures.
Check Point Resellers and Consultants seeking to deepen their troubleshooting expertise.
IT Professionals aiming to specialize in advanced network security.
CCSE-Certified Individuals looking to enhance their skills in troubleshooting Check Point environments.
By earning the CCTE R81.20 certification, professionals demonstrate their ability to handle real-world cybersecurity challenges, positioning themselves as top-tier experts in the field.
Why Pursue the Check Point CCTE R81.20 Certification?
In today’s cybersecurity landscape, where threats are becoming more sophisticated, the demand for skilled troubleshooting experts is at an all-time high. The CCTE R81.20 certification offers numerous benefits, making it a worthwhile investment for career growth and professional development:
Master Advanced Troubleshooting TechniquesGain expertise in kernel debugging, VPN issue resolution, log event investigation, and security rule troubleshooting. Learn to analyze connection failures, rule misconfigurations, and policy errors with precision.
Boost Career OpportunitiesThe CCTE R81.20 certification sets you apart in the competitive cybersecurity job market, opening doors to high-paying roles such as network security administrator, security engineer, or consultant.
Develop Hands-On ExpertiseWork with real-world troubleshooting scenarios in Check Point environments, honing practical skills in performance analysis, debugging, and issue resolution.
Strengthen Security KnowledgeStay ahead of evolving cyber threats by mastering Check Point’s cutting-edge security technologies, ensuring enterprise networks remain secure and resilient.
Achieving the CCTE R81.20 certification not only validates your technical expertise but also enhances your credibility as a cybersecurity professional capable of tackling complex challenges.
Prerequisites for the CCTE R81.20 Exam
To succeed in the 156-587 Check Point CCTE R81.20 exam, candidates should have a solid foundation in the following areas:
Familiarity with UNIX and Windows Operating Systems: A working knowledge of these platforms is essential for understanding system-level troubleshooting.
Strong Networking Knowledge: Proficiency in TCP/IP fundamentals is critical for diagnosing network-related issues.
CCSE Training or Certification (Recommended): While not mandatory, having a Check Point Certified Security Expert (CCSE) certification or equivalent training provides a strong foundation.
Hands-On Experience with Check Point Security Products: Practical experience with Check Point Security Management and Gateway solutions is highly recommended.
These prerequisites ensure candidates are well-prepared to tackle the advanced troubleshooting topics covered in the exam.
Check Point CCTE R81.20 Exam Structure and Topics
The 156-587 CCTE R81.20 exam is a rigorous assessment of a candidate’s ability to troubleshoot complex security issues using Check Point’s debugging tools and methodologies. The exam consists of 75 multiple-choice questions, requires a passing score of 70%, and has a duration of 90 minutes (with an additional 15-minute extension for non-native English speakers). It is administered through Pearson VUE testing centers globally.
The exam covers the following key topics:
Introduction to Advanced Troubleshooting
Overview of Check Point Security Management Architecture.
Troubleshooting methodologies and best practices.
Key debugging tools for resolving complex issues.
Advanced Management Server Troubleshooting
Diagnosing Security Management Server failures.
Resolving SmartConsole and API-related issues.
Debugging management server crashes and performance bottlenecks.
Advanced Troubleshooting with Logs and Events
Investigating log collection and storage failures.
Debugging SmartEvent and Log Exporter issues.
Fixing log processing errors.
Advanced Gateway Troubleshooting
Resolving Security Gateway performance and connectivity issues.
Analyzing kernel logs for firewall debugging.
Diagnosing latency and connection drops.
Advanced Firewall Kernel Debugging
Understanding Check Point’s firewall kernel architecture.
Debugging inspection mechanisms and rule evaluation errors.
Analyzing kernel crash dumps and performance issues.
Advanced Access Control Troubleshooting
Resolving policy installation failures.
Debugging Access Control rules and security policies.
Investigating rule misconfigurations.
Advanced Identity Awareness Troubleshooting
Troubleshooting Active Directory, RADIUS, and LDAP integration.
Debugging Identity Collector and Captive Portal authentication issues.
Analyzing identity-based access control failures.
Advanced Site-to-Site VPN Troubleshooting
Diagnosing VPN tunnel establishment errors.
Debugging IKE and IPsec negotiation failures.
Resolving encryption and decryption issues.
Advanced Client-to-Site VPN Troubleshooting
Resolving remote access VPN connectivity problems.
Debugging VPN client authentication failures.
Troubleshooting SSL VPN portal and client errors.
These topics test a candidate’s ability to apply advanced troubleshooting techniques in real-world Check Point environments, ensuring they can maintain secure and efficient networks.
Tips for Preparing for the 156-587 CCTE R81.20 Exam
To maximize your chances of success, consider the following preparation strategies:
Enroll in Official Check Point Training: Attend the Check Point Certified Troubleshooting Expert (CCTE) R81.20 training course to gain in-depth knowledge of troubleshooting techniques.
Leverage Cert007 Practice Exams: Use Cert007’s 156-587 practice exams to familiarize yourself with the exam format and question types. Regular practice will help you identify weak areas and improve your performance.
Gain Hands-On Experience: Set up a Check Point lab or virtual appliance to practice troubleshooting real-world scenarios, such as VPN failures or policy misconfigurations.
Study Official Resources: Review Check Point’s official study guides and documentation available on the Check Point support portal and forums.
Join the Check Point Community: Engage with the Check Point CheckMates community to exchange tips, ask questions, and learn from experienced professionals.
Conclusion
The Check Point Certified Troubleshooting Expert - R81.20 (CCTE) (156-587) certification is a powerful credential that validates your ability to troubleshoot complex security issues in Check Point environments. By earning this certification, you position yourself as a highly skilled cybersecurity professional capable of ensuring the security and resilience of enterprise networks. With Cert007’s Check Point CCTE 156-587 Practice Exam, you gain access to a comprehensive, up-to-date, and realistic preparation tool that equips you with the knowledge and confidence to pass the exam on your first attempt. Invest in your career today by pursuing the CCTE R81.20 certification and leveraging Cert007’s practice exams to achieve your cybersecurity goals.
0 notes
Text
new computer's first BSOD security kernel check failure the classic windows probably broke some shit with that update last night is my guess
1 note
·
View note
Text
Unlocking Digital Success: From Linux OS Features to Website Ranking Insights
In today’s digital age, understanding both the tools you use and how your web presence performs is vital. Whether you're a developer choosing the right operating system or a business owner analyzing website performance, staying informed about technological essentials is crucial. Two core areas—operating systems like Linux and website ranking techniques—play pivotal roles in shaping the digital landscape. This blog dives into the dual worlds of operating systems and SEO to help you gain a competitive edge.
The Backbone of Digital Environments: Why Linux Matters
The operating system (OS) is the soul of any computing device. It manages hardware, software, files, and system resources. Among many options, Linux stands out as a highly favored OS, particularly in development environments, server management, and cybersecurity operations.
What Makes Linux So Powerful?
Linux is not just another OS—it’s a movement. Known for its open-source nature, Linux allows users to view, modify, and distribute its source code freely. This feature alone makes it ideal for customization and innovation, which is why it’s the OS of choice for developers and large enterprises alike.
Here are some standout features of the Linux operating system:
Open Source & Free: One of the biggest advantages is its cost-efficiency. Anyone can download and use it without licensing fees.
Stability & Performance: Linux systems can run for years without failure or the need for a reboot, making them excellent for servers.
Security: Linux is inherently secure. Its user privilege model, combined with active community support, makes it less prone to malware.
Customization: From the kernel to the user interface, Linux can be tailored to suit specific user needs.
Support for Programming: It supports almost all major programming languages and development tools.
If you're curious to explore more about the features of the Linux operating system, there’s a wealth of resources available to expand your understanding of why it continues to dominate the server and development space.
The Other Side of the Digital Coin: Your Website's Visibility
While having the right OS supports your backend operations, your digital presence—especially your website—needs to be discoverable. That’s where SEO and ranking tools come into play. The internet has billions of websites, but only a few make it to the first page of search engine results. So, how do you ensure your website doesn’t get lost in the crowd?
Why Website Ranking Matters
Website ranking refers to your site’s position in search engine results for a particular keyword or phrase. The higher your ranking, the more visibility and traffic you gain. This directly impacts brand credibility, lead generation, and conversions.
Several factors affect website ranking, including:
Keyword Optimization: Relevant keywords improve your chances of being found.
Page Speed: Fast-loading websites get better user engagement and rankings.
Mobile Friendliness: Google prioritizes mobile-optimized websites.
Backlinks: Quality backlinks from authoritative sources boost credibility.
Content Quality: Fresh, informative, and original content keeps users engaged.
Whether you’re a blogger, business owner, or digital marketer, knowing how to check a website ranking is key to tracking your SEO success and making informed decisions.
Tools to Check Website Rankings
There are various free and paid tools available that help you analyze your website’s performance on search engines. Here are some popular ones:
1. Google Search Console
This is a must-have tool for anyone who owns a website. It provides insights into search performance, including impressions, click-through rates (CTR), and keyword rankings.
2. SEMrush
Ideal for competitive analysis, SEMrush gives a detailed breakdown of keyword rankings, backlink profiles, and even your competitors’ strategies.
3. Ahrefs
Ahrefs is a favorite among SEO professionals. It helps track keyword performance, backlink audits, and content gaps.
4. Ubersuggest
A beginner-friendly tool by Neil Patel, Ubersuggest offers keyword tracking, site audit, and content suggestions.
5. Moz Pro
Moz offers a suite of SEO tools, including a keyword explorer and rank tracker that helps improve your online visibility.
6. SERPWatcher by Mangools
This tool allows you to monitor daily rankings and shows potential traffic impact, giving you a clear picture of your site's SEO performance.
Each tool provides a different perspective, but all aim to answer the same question: How well is your website performing in search results?
Bridging the Gap Between Performance and Visibility
Combining robust backend systems like Linux with smart digital marketing strategies creates a well-rounded, successful online presence. Here’s how the two worlds intersect:
1. Server Performance & SEO
Search engines consider page load time a critical ranking factor. A stable and fast Linux server ensures your site remains operational and loads quickly, improving both user experience and rankings.
2. Security Enhancements
Google has increasingly emphasized secure websites (HTTPS). Linux’s security features help you maintain a protected environment, reducing the risk of being penalized due to vulnerabilities.
3. Customization for Optimization
With Linux, you can fine-tune your server settings for caching, compression, and other performance metrics that impact SEO directly.
4. Open-Source Tools for SEO
Linux supports many open-source SEO tools that can be installed directly on your server, such as Screaming Frog, Matomo (an alternative to Google Analytics), and GIMP for image optimization.
Final Thoughts: Empower Your Digital Journey
Technology is ever-evolving, and to stay ahead, you need to harness both the power of a reliable system and the strategic insight of digital marketing. Whether you're setting up a new website or managing existing infrastructure, a dual focus on backend efficiency and frontend visibility is the key to success.
Start by strengthening your foundation with a powerful OS—Linux—and keep your finger on the pulse of your online presence by learning how to check a website ranking regularly. The combination of technical resilience and SEO strategy ensures your digital journey is both secure and successful.
By integrating these two essential aspects—features of the Linux operating system and practical SEO tactics—you build a digital strategy that’s both strong and smart. In the end, it’s not just about having a website—it’s about having a website that performs.
1 note
·
View note
Text
Effective Solutions for Common Windows Error Codes on Workstations

As a PC user, encountering error codes can be a frustrating experience that disrupts your workflow. These errors can stem from various issues, including software bugs and hardware failures. In this guide, we will explore some common Windows error codes, their causes, and effective troubleshooting methods. Additionally, we will highlight how utilizing advanced components like the AMD Ryzen AI processor can enhance your workstation's performance and reliability.
1. 0x00000124 (WHEA_UNCORRECTABLE_ERROR)
The 0x00000124 error, known as the WHEA_UNCORRECTABLE_ERROR, typically indicates a hardware malfunction. This error can result from issues with the CPU, RAM, motherboard, or power supply, leading to system crashes when it occurs.
Causes:
Defective hardware components such as CPU or RAM.
Overclocking issues, particularly with high-performance CPUs like AMD Ryzen AI processors.
Inadequate cooling causing overheating of system components.
Troubleshooting Steps:
Check Hardware Connections: Ensure all components are securely connected.
Reset BIOS Settings: Restore BIOS settings to default to address overclocking concerns.
Test Hardware: Use diagnostic tools to assess the health of RAM and CPU.
Update Drivers: Keep all system drivers up to date.
For workstations that demand high performance, an AMD Ryzen AI processor can help minimize the occurrence of these errors by providing enhanced stability when paired with compatible hardware.
2. 0x00000050 (PAGE_FAULT_IN_NONPAGED_AREA)
The 0x00000050 error arises from issues related to system memory (RAM), drivers, or corrupted files. It occurs when Windows attempts to access an invalid area of memory.
Causes:
Corrupted or incompatible drivers.
Faulty RAM or issues with memory slots.
Damaged system files or bad sectors on the hard drive.
Troubleshooting Steps:
Run Memory Diagnostic Tests: Utilize Windows Memory Diagnostic to identify RAM problems.
Check for Driver Conflicts: Update all drivers, especially chipset drivers.
Assess Hard Drive Health: Use disk check utilities to identify bad sectors.
Perform System Restore: Revert to a previous state if recent changes triggered the issue.
AMD Ryzen AI processors offer robust performance and reliability, making them ideal for workstations that require minimal downtime due to memory-related errors.
3. 0x0000001E (KMODE_EXCEPTION_NOT_HANDLED)
The 0x0000001E error, or KMODE_EXCEPTION_NOT_HANDLED, is a common blue screen error caused by unhandled exceptions in kernel mode. This often results from faulty drivers or software conflicts.
Causes:
Outdated or corrupt drivers, particularly for graphics or network devices.
Hardware malfunctions.
Conflicts with antivirus software or third-party applications.
Troubleshooting Steps:
Update Drivers: Ensure all drivers are current, focusing on graphics and network drivers.
Identify Software Conflicts: Disable or uninstall problematic third-party applications.
Conduct a System Scan: Run antivirus software to check for malware infections.
Review Event Viewer Logs: Check logs for detailed information about the error.
Workstations equipped with AMD Ryzen AI processors are designed to handle intensive tasks efficiently and come with strong driver support to reduce the likelihood of such errors.
4. 0x0000009F (DRIVER_POWER_STATE_FAILURE)
The 0x0000009F error indicates DRIVER_POWER_STATE_FAILURE and typically occurs during power state transitions like sleep mode.
Causes:
Incompatible or outdated device drivers, especially for USB or network devices.
Issues with Windows power settings.
Conflicts between hardware and drivers after a Windows upgrade.
Troubleshooting Steps:
Update Drivers: Look for updated drivers for graphics cards and USB controllers.
Optimize Power Settings: Adjust power settings for optimal performance on workstations.
Disconnect External Devices: Temporarily remove unnecessary peripherals to see if the issue resolves.
Perform a Clean Boot: Start Windows with minimal background programs to identify potential conflicts.
AMD Ryzen AI processors feature advanced power management capabilities that help prevent such errors, ensuring smooth transitions between power states.
Conclusion
Common Windows error codes like 0x00000124, 0x00000050, 0x0000001E, and 0x0000009F can significantly disrupt your work. Understanding their causes and following troubleshooting steps can help you resolve these issues effectively. When building or upgrading a workstation, consider the benefits of integrating an AMD Ryzen AI processor. With its cutting-edge technology and reliable performance, it provides an excellent foundation for demanding tasks while minimizing the risk of errors.By implementing these troubleshooting strategies and utilizing high-performance components like AMD Ryzen AI processors, you can achieve a more stable and efficient computing experience—whether you're gaming, working on projects, or creating content.
0 notes
Text
[ad_1] Microsoft Groups is majorly utilized by companies to assist create a neater workflow with straightforward collaboration or communication with others. Nonetheless, performing periodic backups of your Microsoft Groups knowledge could be very essential since there may be sudden circumstances of unintentional deletions, corruption of recordsdata, or safety breaches. The article discusses the completely different approaches for safeguarding your Microsoft Groups knowledge. Because the guide strategies present dependable backup choices, they don't seem to be efficient sufficient to fully retain the integrity and hierarchy of the information. For higher effectivity in your backup, you could look in direction of third-party options for Microsoft Groups chat backup, reminiscent of Kernel Microsoft Group Backup. This highly effective instrument gives a set of options that may ease the method of backup and restore for Microsoft Groups knowledge. Allow us to now check out the related insights on the Microsoft Groups backup. Why backup Microsoft Groups? To mitigate the rising threats with Microsoft Groups, common Groups backups turn out to be very important. Listed below are the advantages of Microsoft Groups backups: Defend knowledge from unintentional deletion, corruption, or unauthorized entry. Sooner knowledge loss restoration resulting from hardware failure, software program errors, and so on. Much less dependence on cloud storage by backing as much as a neighborhood system or secondary cloud atmosphere. Defend towards ransomware assaults, phishing, and different types of cyber threats. Safeguard knowledge from built-in apps with out affected by app-related issues that may trigger knowledge loss. Backup Microsoft Groups knowledge Microsoft Groups knowledge is principally saved in OneDrive, Alternate On-line and SharePoint On-line. We'll show you how to out with backup of information and defend unintentional deletion of information in MS Groups. Here's what you should know. Backup chats to textual content recordsdata One fundamental technique to again up Groups chat knowledge is to save lots of them as textual content recordsdata. It's good to spotlight the specified chats, copy them (Ctrl + C), and paste them right into a textual content editor like Microsoft Phrase or WordPad. Save the file to your required location. This method is simple, however it may be fairly time-consuming and liable to errors, particularly for big volumes of chats. Additionally, manually deciding on and copying every chat may be tedious and will result in knowledge loss. Defending private and channel chats Private and channel chats in Microsoft Groups are saved securely in Alternate On-line mailboxes. Nonetheless, these chats are situated in a hidden folder that can't be accessed straight. To guard these chats from unintentional deletion, it is strongly recommended to allow litigation maintain for the related mailboxes. This function retains deleted knowledge within the 'Deleted Gadgets' folder for a specified interval and permits for straightforward restoration. Furthermore, you'll be able to think about using third-party apps to migrate chats in Microsoft Groups. Steps to allow litigation maintain: Entry Workplace 365 Admin Heart. Navigate to the listing of mailboxes. Choose the mailbox containing the specified Groups chats. Go to the 'Others' tab and click on 'Handle litigation maintain.' Activate litigation maintain & set the specified retention interval. Save the settings. To get better deleted knowledge: Go to the eDiscovery heart within the Workplace 365 Admin Heart. Create a search case for Groups knowledge. By enabling litigation maintain and using eDiscovery, you'll be able to successfully defend and get better your Groups chats. Limiting unintentional deletion Whereas proscribing unintentional deletion does not straight again up your Groups chats, it may assist safeguard vital knowledge from being misplaced.
To forestall unintentional deletion: Entry the Microsoft Groups Admin Heart. Beneath 'Messaging,' choose 'Messaging insurance policies.' Click on the '+ Add' button. Create a brand new coverage and disable the next choices: 'Homeowners can delete despatched messages' 'Delete despatched messages' By disabling these choices, you will stop customers from by chance deleting essential messages out of your workforce's chat historical past. Utilizing skilled Microsoft Groups Chat backup instrument Whereas guide strategies can present a fundamental degree of backup, they might not totally protect knowledge integrity and hierarchy. For a extra environment friendly answer, think about using a third-party Microsoft Groups chat backup instrument like Kernel Microsoft Group Backup. This instrument permits you to simply again up all elements of Microsoft Groups, together with chats, channels, recordsdata, and extra. You may select your most popular backup location and shortly import bulk chat customers utilizing a CSV file. The instrument's search operate additionally makes it easy to seek out and again up particular customers or groups. For extra insights on the instrument, you too can check out the trial model at no cost. Conclusion Backing up your Microsoft Groups knowledge is essential to guard your precious info from unintentional deletion, knowledge corruption, and safety threats. We've mentioned the guide strategies that may present a fundamental degree of safety together with a devoted backup answer like Kernel Microsoft Group Backup, being an environment friendly backup method. With this instrument, you'll be able to automate the backup course of in order that your Groups knowledge is often backed up and simply recoverable. This instrument gives granular management over backup settings to customise the backup course of. Check out the trial model right this moment and search most advantages. [ad_2] Supply hyperlink
0 notes
Link
The Mystery Behind Kernel Security Check Failure Kernel security is a crucial aspect of computer systems as it ensures the stability and protection of the operating system against potential threats. One critical error that Windows users may encounter is the "kernel security check failure." This error can have a significant impact on system stability and the user experience, making it important to understand its causes, troubleshooting methods, and preventive measures. [caption id="attachment_63256" align="aligncenter" width="1280"] kernel security check failure[/caption] Understanding Kernel Security Check Failure Definition and Importance of Kernel Security The kernel is the core component of an operating system, responsible for managing hardware resources and providing essential services to other software components. Kernel security is vital as it safeguards the system from unauthorized access, malware, and other potential threats. A secure kernel ensures the overall stability and integrity of the operating system. Exploring Kernel Security Check Failure Kernel security check failure is an error that occurs in Windows systems, indicating a problem with the kernel's security mechanisms. Users may experience symptoms such as system crashes, frequent restarts, or the infamous "blue screen of death" (BSOD). Ignoring or neglecting this error can lead to further system instability, data loss, and potential security breaches. Causes of Kernel Security Check Failure Hardware Related Causes Several hardware-related issues can trigger kernel security check failure. Faulty RAM, incompatible drivers, or malfunctioning hardware components can compromise the kernel's integrity and cause this error to occur. It is important to ensure that all hardware components are functioning properly and compatible with the operating system to avoid such issues. Software Related Causes Software-related factors can also contribute to kernel security check failure. Outdated or incompatible drivers, corrupt system files, or malware infections can all undermine the security of the kernel. Regularly updating software, maintaining a clean system, and using reliable security software can help prevent these issues. Driver Related Causes Drivers play a critical role in the operation of the kernel. Outdated, incompatible, or conflicting drivers can lead to kernel security check failure. It is essential to keep drivers up to date and resolve any conflicts or errors that may occur. Regularly checking for driver updates and using reputable sources for driver installations can minimize the risk of encountering this error. Common Misconfigurations Common misconfigurations in system settings or security software can also contribute to kernel security check failure. Examples include improper firewall configurations, disabled automatic updates, or weak passwords. Ensuring proper system configurations and security settings can help prevent this error from occurring. Troubleshooting and Resolving Kernel Security Check Failure Basic Troubleshooting Steps When encountering kernel security check failure, there are some initial steps you can take to troubleshoot the issue. Try restarting your system and running built-in Windows diagnostics to identify any potential problems. It is also important to determine if any recent changes or installations triggered the error. Advanced Troubleshooting Methods If basic troubleshooting steps do not resolve the issue, you can proceed with advanced troubleshooting methods. These may include running system file checks to repair corrupt files, updating drivers to their latest versions, and performing malware scans to remove any infections. Additionally, there are specialized tools and software available that can diagnose and resolve kernel security check failures. Seeking Professional Help In some cases, resolving kernel security check failure may require the assistance of professional technicians or IT support. If you are unable to diagnose or fix the issue on your own, it is advisable to seek expert help. Professional technicians have the knowledge and experience to handle complex cases and provide appropriate solutions. Preventive Measures and Best Practices Regular System Maintenance Regular system maintenance is crucial for preventing kernel security check failure. This includes installing updates for the operating system and software, running regular antivirus scans, and optimizing system performance. By keeping your system updated and clean, you can minimize the risk of encountering kernel security check failure. Driver and Software Management Proper management of drivers and software is essential for maintaining kernel security. Regularly update drivers to their latest versions, as manufacturers often release updates to address security vulnerabilities. Use trusted sources for driver installations to avoid downloading malicious or incompatible drivers. Additionally, be cautious when installing software from unverified sources, as it can introduce security risks to your system. System Configurations and Security Settings Configuring your system settings and security options appropriately can help prevent kernel security check failure. Enable firewalls to protect against unauthorized access, enable automatic updates to ensure you have the latest security patches and use strong, unique passwords to protect your accounts. Regularly review and adjust security settings to stay proactive in safeguarding your system. Kernel security check failure is a critical error that can significantly impact the stability and security of your computer system. By understanding the causes, implementing troubleshooting methods, and adopting preventive measures, you can minimize the risk of encountering this error. Regular system maintenance, proper driver and software management, and appropriate system configurations are key to maintaining a secure kernel. Remember, seeking professional help is always an option if you are unable to resolve the issue on your own. By prioritizing kernel security, you can ensure a stable and protected computing experience.
#blue_screen_of_death#BSOD#bug_check#computer_error#device_driver#driver_issue#error_code#hardware_problem#kernel_mode#kernel_security_check_failure#memory_corruption#operating_system#software_conflict#system_analysis#system_crash#system_crash_dump#system_files#system_integrity#system_protection#system_recovery#system_stability#system_troubleshooting#system_vulnerability#Windows_10#Windows_error#Windows_update
0 notes
Text
BLIIoT Industrial PLC Edge Gateway BL110 Applied to Textile Machine Monitoring
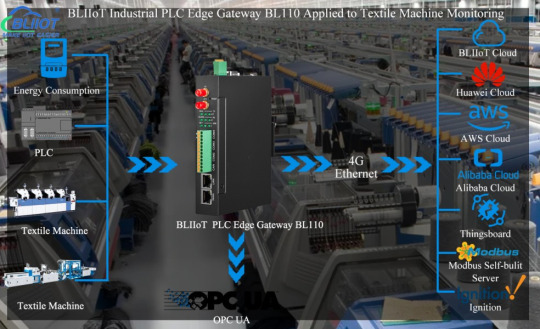
1. Foreword
With the continuous and rapid development of the textile industry, intelligent control technology, field bus technology and digital display technology have been widely used in textile equipment. In order to improve the management of small sample spinning equipment and improve the competitiveness of enterprises, textile equipment enterprises want to use advanced automation technology and information technology to carry out informatization transformation of equipment.
2. Textile Machine Remote Monitoring System
The entire system network is divided into 3 layers: management layer, control layer and equipment layer Spinning equipment mainly includes digital sample carding machine, sample draw frame, sample comber, sample roving frame, sample spinning frame and sample doubling machine , through the BLIIoT Industrial PLC Edge Gateway BL110 and the core controller of the textile machine equipment (such as PLC), combined with communication methods such as 4G, Wifi, Ethernet and GPRS, the data collected by each device includes the operating status of the equipment, output, efficiency, Process parameters, abnormal alarm information and other teaching data are transmitted to the server/cloud.
The system can use the BLIIoT Industrial PLC Edge Gateway BL110 to collect meter data, and the online monitoring module can monitor the voltage, current, power, power factor, energy consumption and other indicators of the host and auxiliary equipment in real time, and can realize the following functions: compare the energy consumption of different machines Data, check abnormal data in a timely manner; reproduce the power change trend of the machine in the last 24, 48, and 72 hours, and find equipment problems in time; count the total power consumption of the machine, process, variety, etc., and the data of power consumption per ton of yarn to form various Class reports, visually compare and display devices with abnormal power consumption, and provide targeted improvement suggestions.
3. BLIIoT Industrial PLC Edge Gateway BL110
◆ Using 4G wireless network and Ethernet redundant data upload method, stable and reliable;
◆ Embedded ARM9 32-bit Linux kernel real-time operating system and watchdog function;
◆ Wide working voltage design with anti-reverse protection design;
◆ Supports Mitsubishi, Siemens, Delta, Schneider, ABB, Huichuan, Omron, Panasonic, Hollysys and other PLC protocols;
◆ 4 serial ports support modbus master-slave protocol, support modbus / mqtt / private custom protocol upload;
◆ All 4 serial ports support transparent transmission, and the CAN port supports data of CAN communication equipment, such as server;
◆ It can collect the data of the network port PLC or other network port equipment through the Ethernet interface;
◆ Support OPC client function, can read data provided by OPC server of other manufacturers;
◆ Support multiple data storage functions according to cycle, change, condition, etc .;
◆ Support multi-level data security rights management function;
◆ Support multiple alarm conditions, such as alarm conditions, urgency, confirmation rules, push rules, and SMS push;
◆ Support power failure alarm function; (optional)
◆ Support remote PLC download programming and remote collection of PLC equipment, set conditions to stop PLC operation;
◆ Support routing function and access video surveillance camera;
◆ Support mainstream public cloud platforms such as Alibaba Cloud and AWS Cloud;
◆ Support third-party manufacturers custom development, provide hardware and SDK interface
◆ Support BLRMS;
◆ Embedded TCP / IP protocol stack, support TCP, UDP protocol, TCP Server and TCP Client services;
4. Summarize
By connecting the textile equipment and PLC to BLIIoT Industrial PLC Edge Gateway BL110, real-time data collection is carried out on the equipment, and the equipment operation status and fault alarm information are fed back to the management personnel in a timely manner, so that the equipment can be checked online and offline, operation failure and other information anytime and anywhere, and with the help of the equipment maintenance express line Realize operations such as remote uploading and downloading of programs, remote programming and debugging.
The data collection of intelligent instruments on the textile factory site can realize real-time monitoring of production environment and energy consumption, monitoring of environmental temperature and humidity, gas and energy consumption data, can feed back accurate and reliable data to the staff, and take timely measures for management and control. It plays an important role in equipment and personal safety as well as energy saving optimization.
More information about BLIIoT Industrial PLC Edge Gateway BL110: https://gateway-iot.com/industrial-iot-edge-gateway-p00272p1.html
#iot devices#smartcities#iot solutions#industrial automation#industrial iot#datacollection#Textile Machine Monitoring
0 notes
Text
So, for some time, FreeBSD had something vaguely similar: you called the "pdfork" system call, which gave you a "process descriptor" ("PD") - also a magic file descriptor to a process.
The FreeBSD stuff was more focused on solving problems in the other direction. It has more of a "structured concurrency" shape. If a PD was closed (and no other copies of the PD, such as from dup system calls or forking, were still open), the process was automatically killed, unless you had explicitly given it permission to outlive the parent. This means that you can properly "contain" child processes "within" parent processes, so that if the parent dies, the child also dies. Do this recursively, and you eliminate a lot of design challenges in handling edge cases since now there's more guarantees of robust and complete cleanup if the process you're relying on to detect other failures itself fails or is artificially taken down.
You see this problem in the runit/daemontools model - it's a really elegant model, a few simple and efficient primitives which end up being recursively composable into a supervision tree which can drop privileges as it goes leafwards and so on... buuut if for some reason a SIGKILL hits a "runsvdir", that whole branch of the supervision tree is orphaned. Unless those processes are written to check if their parent died and die with it, the revived runsvdir will come up to an unclean state that it doesn't know about. (Trying to solve this while keeping the composable-LEGO-brick elegance of that model is why I have written before trying to lay out what a minimal init system must have, why I have an unusually high pre-occupation/awareness about orphaned process re-parenting/reaping and the Linux subreapers feature, and so on....)
So in some ways the FreeBSD thing is better, because if you want to decompose your program into processes, you can do so and you keep proper encapsulation and cleanup out-of-the-box, without needing any additional coordination with your ancestor or descendant processes. You just call "pdfork" instead of "fork" and (unless you go out of your way to disable it) your child processes will go down with you. My understanding is that FreeBSD's Capsicum lets you impose this recursively on all your descendent processes, and it's a bit of a shame that Capsicum is this obscure thing billed as primarily focused on security when this is just proper structured concurrency at the process level. (UNIX process groups and sessions almost provided this, even back then you could see that people were being drawn to the inevitably helpful design of structuring their concurrency into a hierarchical tree... but UNIX didn't quite get there because it let any process just branch-break out of that hierarchical tree by starting a new process group or session, so you didn't get the rock-solid invariant.)
But on the flip side: BSD PDs can't be used for much else. Linux PID FDs can be used to reach into a process in other ways. As described at the end of the original post, they can be used to grab a file descriptor from another process. They can also refer to threads rather than just processes (since Linux threads and Linux processes are implemented as basically the same thing, just some of the kernel-side resources are shared rather than being copied and isolated during creation), which means that we can get some of the race-condition eliminating benefits down among threads too. More generally, it seems that Linux is moving in the direction of using the PID FD as a way to pass around the capabilities to do things with a process that you would normally only have if you are that process, or its direct parent, or its (sub)reaper, or in one of its namespaces, and so on. For example, you can use the
Both Linux PID FDs and BSD PDs can be used to send signals without being inherently vulnerable to PID reuse races. They can also both be used to check/wait for the process ending, including in ways that can hook into event loops build on the portable poll or the less portable but more modern/versatile/scalable epoll/kqueue.
I wasn't really
Process "File" Descriptors (PID FD)
Linux in recent years has fixed some of the biggest annoyances I had with the UNIX model, and I'm feeling rather happy about this. One example of this is with how you can refer to processes.
With traditional UNIX APIs, you can never signal a process without a PID reuse race condition. The problem is somewhat inherent to the model: a PID is just an integer reference to a kernel-level Thing, but crucially, that Thing is not being passed around between processes. If I tell you the PID 42, that's not qualitatively different from you randomly picking the number 42 - either way, you can try to signal whichever process currently has PID 42. You might not have permissions to signal the current resident of that PID for other reasons, but you don't need a prior relationship to signal it - you don't need to receive any capability object from anyone. I haven't given you something tied to any process, I just gave you a number, and in the traditional UNIX model there's nothing better (more intrinsically tied to a single process) to pass around.
Compare file descriptors. An FD is also "just" an integer, but having that integer is worthless unless you also have the kernel-level Thing shared with your process. Even if I give you the number 2, you can't write to my stderr - I have to share my stderr, for example by inheritance or by passing it through a UNIX domain socket.
This difference is subtle but technically crucial for eliminating race conditions: since an FD has to be shared from one process to another thought the kernel, and the underlying "file" descriptor/description is managed and owned by the kernel, when you later use the FD in a system call, the kernel can always know a fully unambiguous identity of which Thing you were referring to. If you just told it 42 in some global ID space, well do you mean the thing currently at index 42? Or did you really think you were referring to a thing which existed some time ago at index 42? That information has been lost, or at least isn't being conveyed. But if you told it 42 in your file descriptor table, now that can hold more information, so it can remember precisely which thing your 42 was referring to when you last received or changed it.
So how did Linux fix this?
We now have "PID FDs", which are magic FDs referring to processes. Processes "as a file", in a more true and complete way than the older procfs stuff.
Unlike PIDs, which by design can only travel around like raw numbers divorced from the true identity information they gesture at, a PID FD can never lose track of the process it refers to: if that process dies, its PID FD will forever "know" that its dead even if the PID is reused (because when that process yields to or is preempted by the kernel for the last time, the kernel remembers that there's a PID FD for it which needs to be updated, and even if the kernel recycles the PID it knows not to update that PID FD to point to the new process).
And we now have a system calls which let us
create a new process (or thread!) and have that return a PID FD instead of a PID (or "TID" in the case of threads, but in the Linux kernel those are basically the same thing)
signal a PID FD instead of the traditional PID (or TID), and
wait on a PID FD (in fact, the FDs just plug into the normal poll, select, or epoll system calls, so waiting on process or thread status can just hook into all existing event loops).
The one crucial thing is that we must not forget that these guarantees only start once we've gotten the PID FD: in particular, if you get a PID FD from a PID instead of getting the PID FD directly, you still need to check once if the PID hasn't gotten invalidated between when you got the PID and when you got the PID FD. This is something you can only do as the direct parent or (sub)reaper of the PID in question, because then you can use the traditional "wait" system call on the PID after getting the PID FD - if getting the PID FD succeeded but then the wait reports that the PID exited, that means you could've gotten a PID reuse by the time you got the PID FD from the PID.
So ideally, we just don't deal in PIDs at all anymore. When we create a process, we can get its PID FD atomically with the creation. (If we can't do that, if we're creating the process and then getting the PID FD with a separate system call, we do the wait check described in the last paragraph after getting the PID.) Then we pass the PID FD around - this might superficially look like passing an integer around, for example if you need to use the FD number in a shell redirection or communicate it to a child process, but underneath that the actual FD would be getting passed around either by inheritance, UNIX domain sockets, or whatever other means are available.
I've been wanting this for years. I've spent a lot of mental cycles trying to figure out the most elegantly minimal and composable primitives which could work around various problems in service supervision and automatic restarts in the face of random processes dying or getting killed. Those edge cases are now much more simple to totally cover by using the PID FD stuff, at least so long as we're willing to lose compatibility with the BSDs and other Unix-y systems until they catch up. Which, honestly, is an increasingly appealing proposition as Linux has been adding good stuff like this lately.
P.S. On that note, another thing we now have, is the ability to reach into a process (if we have its PID FD and have the same relationship to it (or elevated privileges) that we'd need to hook into it with debugger system calls) and copy a file descriptor out of it. This means we no longer need a child process to be written to share it with us through a domain socket or by forking or exec-chaining into a process we specify. Accessing file descriptors in already-running processes enables some some neat monkey-patching and composition, and it's simpler to implement than the UNIX domain socket trick. I remember being frustrated by the lack of ability to do exactly this - reach down into a child process (for example a shell script, which doesn't even have access to the "auxiliary" and get a file descriptor out of it, like 7 years ago, and minimal and composable systems like S6 which can compete with Systemd on features like socket activation might be able to achieve a simpler API now that we have this.
6 notes
·
View notes
Text
The Way to Fix One Kernel_Security_Check_Failure In Windows 10?
With WinDbg to Evaluate The Performance
Assess The design Of The File-systems Properly, certainly one of many explanations for prevent code kernel security test collapse is obsolete device drivers. Our solution is utilizing the most recent version of drivers such as controls, GPU, and motherboard. To accomplish this, buy the application form with a respectable seller. If you're a newcomer in this subject, it's much far better to ask other IT pros for trusted vendors available on the industry. For users that really don't wish to re set the operating platform, we urge them to boot up their computer with all the safemode. This manner will assess whether there's a computer difficulty linked to the specific function or maybe not. In the event the challenge isn't suggested, then your malfunction is rooted within a program. Therefore, all you've got to accomplish this would be re install the debatable applications. At the next area, we'll direct you on what best to mend this technical matter. Assessing the document system The Most Important Thing! Assess RAM
Issues with Unified Extensible Firmware port
After you Find a Note Pop up in your own display saying Regarding the documents neglected Throughout integrating or harmonious procedures, attempt one of the following approaches: From date version of the motorist We'd revived the device if kernel security check failure windows 10 had been happening. Because of this, it functioned very nicely. But, you will find attributes that you Want to Focus on before implementing this technique: This process ought to be used while the kernel error arises after installing new applications as it will help you to erase the discretionary software. The complete Windows operating system is going to be flashed through and have mended later. Apart from assessing the disk, providing a glimpse at the RAM will be able to allow one to mention the memory conditions that cause this malfunction. Whether there are lots of memory segments, then you definitely must test one before conducting diagnostics for that entire memory usefulness. With this evaluation, you are able to test the instrument such as the image below:
kernel_security_check_failure
Un-install Overclocking Computer Software In the event you do not need all files to evaporate, be sure to store them before conducting the alternative! Kernel mistake frequently appears on the screen background in ordinary blue colour. Lately, over clocking computers can also result in this Windows 10 kernel security check failure issue. Really, when you face such a mistake, place your computer back into its default setup. You can find over clocking apps running which want one to uninstall too. Finally, restart your own computer to find out perhaps the problem becomes repaired. May 10, 2021Tagged cease code kernel safety check collapse, Windows-10 kernel security test collapse Windows-10 Kernel Security Check Struggling -- Assess the Tough Drive One of many ordinary data corruption issues is kernel_security_check_failure. Lots of you could think this can be a mistake due to viruses, however it isn't. This issue generated data corruption over the Windows os. If you enter in to trouble using this particular specific issue, then this guide is right for you. Here we'll provide you available techniques of how you can correct the mistake. Let us kick in! Kernel Security Verify Failure is among those mistakes that typically arise within your Windows operating procedure. It displayed like an email on the gloomy background when the files shifting process collapsed. Based on the pros, the common causes of windows prevent code kernel safety assess collapse are: Up Date The BIOS This technical dilemma can just take place within the neglected motorist or network component. Utilizing a multi purpose debugger is among those complete tactics to determine the original mistake because this tool permits users to investigate the wreck within the memory card disk drive. The kernel_security_check_failure may happen at any moment to anybody, that induces users to fight with using their computers. This article aimed to provide you basic solutions with this particular mistake, and we trust it had been helpful for you personally. When you've got additional methods of fixing this matter, do not be afraid to talk around! Superior luck!Assess the Hard Disk DriveHandling the pliersThe restoration option within Windows-10 helps people to manually delete the system.In our experience, the ethics of these document systems additionally can make kernel errors. We recommend you mend this issue using the scanning control or BSOD kernel security test collapse solution.Difficulties with hardware partsRun The Safe-modeOur ultimate answer for you personally is re setting the simple input/output procedure by copying the computer system. With this approach, you might need to ascertain today's firmware version . Then assess if there are always a couple variants of this on the motherboard! From then on, upgrade the most recent version following manufacturer's guidelines.Fixing the machineWindows-10 Kernel Security Assess FailureUp Date the Unit Display
#kernel_security_check_failure#windows 10 kernel security check failure issue#kernel security check failure windows 10
1 note
·
View note
Text
How to Fix a Kernel Security Check Failure BSOD

In a world wherein get right of entry to to a laptop is more essential than ever, a blue display of death (BSOD) errors on a Windows PC can bring that get right of entry to to a grinding halt. Unfortunately, not unusual BSOD mistakes like an unexpected kernel mode trap or vital method died save you your PC from working until you repair the underlying problem.
Another commonplace BSOD errors which can seem, depending on the circumstances, is a “stop code: kernel security check failure” BSOD. This trouble is generally due to corrupted system documents, however it could additionally be due to faulty hardware or old drivers. If you want to restore a kernel security check failure BSOD, right here’s what you’ll want to do.
What Causes a Kernel Security Check Failure BSOD Error on Windows 10?
Some BSOD errors are tough to research, however with a kernel protection take a look at failure BSOD, you may commonly anticipate that it points to certainly one of two things: a hardware trouble or corrupt (or outdated) system documents.
These troubles can reason your PC to attempt to get entry to the Windows kernel incorrectly in a few way. As the most protected of all gadget services, illegal access to the machine kernel reasons an integrity check to fail, together with your PC crashing and showing a BSOD mistakes like this one.
If your gadget documents are corrupted or outdated, you can commonly resolve the difficulty with the aid of jogging Windows Update. This will set up any to be had gadget updates, which include device motive force updates. You may additionally want to run different renovation gear, consisting of System File Checker (SFC) and chkdsk, the use of Windows PowerShell.
Hardware problems, such as defective machine memory, could also be in the back of the hassle. You may also need to check your hardware, and in case you discover faults, recollect changing it. If that doesn’t work, greater drastic movement (which includes resetting Windows) may be your most effective option.
Check for System and Driver Updates
In many instances, a Windows stop code “kernel safety test failure” message is resulting from an old machine with lacking (and necessary) computer virus fixes. To solve the hassle, you’ll need to test Windows Update for brand new device and driver updates.
To begin, proper-click on the Start menu and pick Settings.
In the Settings menu, pick Update & Security > Windows Update and pick Check for Updates to scan for new updates. If any updates are available, choose Download (or Download and Install) to begin the set up process. After installing any to be had updates, restart your PC to complete the process.
While updated drivers must remedy this difficulty, you could locate that new drivers also are at the back of a kernel safety check failure on Windows 10. You can also want to roll back a motive force in case you see this mistake after you’ve currently up to date your tool drivers, either manually or thru Windows Update.
Run the System File Checker and Chkdsk Tools
If Windows machine documents are compromised or corrupted, Windows will forestall running properly. You can help to fix the problem via checking the integrity of your device files and your difficult force’s report machine the use of the System File Checker (SFC) and chkdsk tools.
To do that, open a new Windows PowerShell window by way of proper-clicking the Start menu and choosing the Windows PowerShell (Admin) alternative.
In the PowerShell window, kind sfc /scannow to run the System File Checker device. You’ll want to look ahead to SFC to complete the test of your machine files and, wherein feasible, repair them.
With the SFC tool complete, type chkdsk C: /f to test your machine force’s record gadget integrity. Windows will ask you to time table this to your next reboot, allowing a boot level experiment of your pressure to complete. Type Y and pick the Enter key to verify this, then restart your PC.
Test Your System Memory
Should the SFC and chkdsk gear provide no decision to a kernel safety take a look at failure on Windows 10, you may want to appearance greater intently on the health of your hardware. For instance, memory problems ought to without delay reason a kernel exception message along with this one.
To take a look at the fitness of your machine reminiscence, you’ll need to check it. You can try this the usage of the built-in Windows Memory Diagnostic tool. Start by way of proper-clicking the Start menu and deciding on Run.
In the Run box, type mdsched.Exe and choose OK.
In the Windows Memory Diagnostic window, Windows will ask you for permission to restart. Select Restart now and test for issues to do that without delay or choose Check for issues the next time I begin my computer to delay this until your next restart.
The Memory Diagnostic device will run a stress take a look at of your gadget reminiscence to ensure it’s working effectively. If any troubles are detected, you’ll need to keep in mind replacing your gadget memory to remedy it.
Fixing a Kernel Security Check Failure BSOD Error
The steps above ought to help you fix a windows 10 kernel error , in addition to avoid them in destiny. You have to take a look at your PC’s overall performance regularly to preserve a watch on any similarly issues, keeping your machine up to date to make certain you have the latest worm and protection fixes, and checking for malware regularly.
A PC is only as exact as the hardware it runs on, but. If you’re seeing BSOD mistakes seem at an alarming charge, it can factor to hardware troubles that you could’t resolve. It can be time to improve your PC with new hardware or keep in mind building or buying a brand new PC rather.
0 notes
Text
We deal with this, “fiction is reality” shit EVERY. GENERATION.
And I mean it comes back among authoritarians playing to sheep EVERY fucking generation on different pretenses.
It always boils down to a bunch of people that are insecure about the effects of culture and media on other people, and as a flimsy pretense/pretext to restrict access to things to other people “in society” for their own safety and sense of security.
And when it comes to, “obscene literature” or illustrations, the source is always jealousy, insecurity and an attempt to reduce other people down to a demographic statistic. Whether it’s reducing black people to a caricature and acting like hip-hop just turns the kids into violent, drug abusing, psychotic felons, or imagining pornography is what turns people into horny fucking do-nothings, it’s always about control.
And we’ve put it off for so long. We’ve put off the conversation about just what demographic these people play to in order to get traction and followers and staying power and warm bodies for their movements. They’re the demographic that makes antis- work, the demographic that screams for censorship because illustrations “hurt them personally,” or “cause men to hurt them.”
I’m talking about women. Particularly, cis women, as trans women are not in numbers enough to affect anything, and it is EXPLICITLY IMPORTANT that the source of the offense and complaint come from the population that are the gateway through which the next generation is born and brought up.
Individual men may be so clueless as to assume the way degeneration works is a person is left improperly or negligently nurtured, and so just make bad decisions because, “they were never taught better.” They embrace the idea that people only do bad shit because, “the society,” isn’t paying attention, or that individual people are just blank slates beholden to the righteousness and morality of the cultural hivemind of said society. That Society is an objective effect, and if bad people exist, it’s proof to them that there’s something wrong with said society.
But individual men know that the bad actions of other men are not caused solely by “male culture,” or the absence of it, or shitty “role models.” They see the shitty natural inborn attitudes of other men, and despite being raised in shitty conditions, naturally develop a good head on their shoulders, and despise actions like that. As men you can’t HELP but grow up watching boys around you make shitty decisions based on shitty impulse control and, no matter how often they’re punished, how much they’re loved, how much they’re compassionately talked to, STILL act the fool and wind up as terrible, stealing, violent adults. As men you can’t do anything BUT reconcile that some people are just fucking shitheads, and the idea as a man YOU should be punished or treated like the “association” of men itself is at fault, smacks of sexism. The same sort of sexism women’s lib supposedly is against- at least, when it happens to women.
Women, however, are not men, are not privy to the thoughts and feelings of men. Men are abstracts to these women, many of whom are so solipsistic or gynocentrist that they just see men as a class of monsters in a videogame. Just a pattern of individuals that surely must all get their code and culture from “society.” Clearly, when there’s bad men about, it’s proof this “society” isn’t doing everything it can to mollify and gentrify those horrible beastly men to make them safe and not dangerous and productive.
These women that see men like living aggregates for society, imagine that in order to “keep men working properly,” they need to not have “bad moral influences,” treating pornography and access to drugs and literature like a cleaning lady treats dirt on linen. They imagine that the only reason rape or murder or theft by men occurs is because “there’s a problem with men, thinking that is okay.” Like the only reason your average man isn’t running around violently raping people or killing them is because they sang enough hymns at church- by force. Or because they were prevented from, “getting deranged by wrongthink.”
So with this in mind, how do they imagine porn affects men, male minds, and this big abstract-turned-monolithic-concept called, “society?”
Well, they imagine fiction is reality. That if “people of lesser intellect” read a thing, then they’ll inherently believe it, because, “it presents itself as factual and reality.” When.. no. That’s not how it works. They believe, absolutely, that without some mechanism there to go, “BUT WE’RE JUST PRETENDING THO, IT’S NOT REAL!” that will inherently make people, whom all have tenuous and toddler-like grasps of reality and object permanence, think a thing in fiction is real and applies to reality.
And naturally, they see men as people of lesser intellect. So they reason, those dangerous statistical anomalies are just men that haven’t been browbeaten, and whom are subject to any given negative influence or writing or opinion or culture that preaches values and ideas incongruent with their preferences, as women. Therefore, they conclude, fiction that does not preach their “good values” is in fact advocating bad ones, bad habits, bad moral character, bad mental health- call it whatever you want based on your generation. It’s ALL THE SAME SHIT. All the same knee-jerk moralism based on justifying societal and institutional use of force to restrict and arbitrate and judiciously enforce and justify dictating censorship and good-think. It’s just a question of where that basis comes from.
And theres’ ultimately no reasoning with that culture of women when they grasp hold of a thing that appeals to them, flatters and justifies their prejudices and biases. You can sit there colorfully or dryly explaining the ways in which this shitty point of view is wrong, much as you can try to walk back a persons beliefs in their homophobia that they base on religious purism or use the purism to validate their homophobia, but you cannot just get them individually to give up those nice, comfortable beliefs.
And when grouped together for mutual support and validation, it becomes this negative-thought, field of fucking SHEEP braying “Nuuuh-uuuh!” and arguing for restriction of content and sanitation and disbarrment from certain subject matter to be in consumable porn or literature or even just art. The only thing keeping them in check being the consequences for vandalism, and the ability for a community or institution to police out the bias usurpers that would seek to enter their foundations and run them on behalf of the values of these easily upset, insecure sheep.
every FUCKING generation, it manifests in some manner. Be they from church ladies, to radical feminists, to intersectional feminists. If you capture the imaginations, insecurities, jealousies, foster and sanction them, interpret them, get young women believing them, participating in the romance that tells them the way to change the bad things or take the edge off the bad men is to foster and enable authoritarianism (be it regional social, regional institutional, or federal institutional) then you have this neverending avalanche of unending support for it. Be it from dictators, or just from pure ideology from a doctrine. They’ll do it. And stubbornly and obstinately believe in whatever compliments their biases, to the contradiction of everything.
And while you can remove a man and his influences on the next gen from the home, from the social radius of the next generation to be a significant source of culture and how they relate to young people, removing women from the equation, from whom the next generation comes from, is virtually impossible. So a male zealot, already susceptible to scrutiny and punishment for being so wild and zealous with their beliefs, can be retaliated against, muted, beaten and removed from relevance until they censor themselves or change their tune.
But you cannot do that to a female human, or women/mothers as a sex, without both women AND men taking it as an attack on humanity at their most prime and kernel. It has to be done with disproportionate authoritarian state power that does not fear mass dissent and violent retaliation, or it isn’t done at all.
So these zealous Karens that embrace wholly these ideas enabling authoritarianism under a banner they approve of, are allowed to propagate unchallenged, and even if challenged, cannot be subdued or subverted. Their own little cliques and echo chambers and lack of desire to even consider their positions are wrong. Any attempt to point the fingers at this very real, disproportionate and characteristic, objective power female humans have just on the basis of their sex and how that relates among them socially, can and will be trash binned arbitrarily as, “sexism.” Despite the fact, it’s absolutely true.
So long as women that believe “society” is an objective, monolithic thing from which, “that other sex” and other women get their marching orders on how to BE what they are, and don’t see them as billions of individuals with their own ambitions, instincts, inborn personality and character flaws, independent of “society’s failures,” believing those people can be saved or corrected IF ONLY WE CENSOR EVERYTHING or make all media “good thing,” we’re just going to have people with illiberal beliefs asserting their dominance and insisting it’s for the soul of the species, society and the planet.
I mean yeah there are male antis and shit, but honestly. Tell me honestly. How many fucking deranged fandom people that are doing shit like mailing cookies with sewing needles backed into them are male gendered or male sexed, either? As uncomfortable as it may be to acknowledge or consider this might have a sexual grounding, I’m sorry. Not acknowledging it is simply rejecting reality.
3 notes
·
View notes
Text
How To Fix Kernel Security Check Failure {Windows Blue Screen Error}
Kernel Security Check Failureor Blue Screen Of Death (BSoD Error) is one of several errors that can cause sudden interruption to access your computer. There might be one or more of your data files that are corrupted or have failed a compatibility check. As said, there are many reasons for this error occurrence, like incompatible memory, virus infections, or other problems. The most common reason…
View On WordPress
#antivirus check#blue screen of death error#bsod error#driver update#hard disk scan#Kernel Security Check#Kernel Security Check Failure#ransomware check#windows update
0 notes
Text
How to Easily Fix Kernel Security Check Errors in Windows 10
Do you dread getting a BSoD or Blue Screen of Death? You’re not alone. It isn’t very pleasant. Unfortunately, kernel security check failure is one of these “serious” errors that cause a BSoD. Kernel Security Check Failure is a Blue Screen of Death (BSoD) problem, which is why you are reading this article. Many users who updated to Windows 10 from an earlier operating system have encountered the…

View On WordPress
0 notes
Link
The Mystery Behind Kernel Security Check Failure Kernel security check failure is a critical error that can occur in computer systems, causing system crashes, data loss, and compromised security. Understanding this error is crucial for maintaining a stable and secure computing environment. [caption id="attachment_62844" align="aligncenter" width="1280"] kernel security check failure[/caption] Understanding Kernel Security Check Failure The kernel is a fundamental part of an operating system that acts as a bridge between hardware and software. It manages various tasks, such as memory management, process scheduling, and device driver communication. Its role is vital in ensuring the smooth operation of the system. Kernel security check failure refers to an error that occurs when the kernel detects a security violation during its routine checks. This violation can be caused by various factors, such as memory issues, outdated drivers, or malware infections. Resolving this error is essential to prevent system instability and potential security breaches. Common Causes of Kernel Security Check Failure Memory issues Faulty RAM or incompatible drivers can trigger kernel security check failure. When the kernel accesses faulty memory addresses or encounters issues with drivers, it may result in this error. It is important to ensure that the RAM is functioning properly and that the drivers are compatible with the operating system. Outdated drivers Outdated or incompatible drivers can also lead to kernel security check failure. When the kernel interacts with drivers that are not up to date or designed for the specific hardware configuration, it may encounter compatibility issues, resulting in this error. Regularly updating drivers is crucial to prevent such problems. Malware infections Malicious software can exploit vulnerabilities in the kernel, leading to kernel security check failure. Malware can compromise the integrity of the kernel and cause it to malfunction, resulting in system crashes and potential data breaches. Having robust antivirus software and regularly scanning for malware is essential to protect the kernel from such attacks. Resolving Kernel Security Check Failure Resolving kernel security check failure requires identifying and addressing the underlying causes. Here are some steps to help resolve this error: A step-by-step guide to updating drivers and resolving compatibility issues 1. Identify the drivers causing the issue by checking the error message or using diagnostic tools. 2. Visit the manufacturer's website or use a reliable driver update software to obtain the latest drivers for your hardware. 3. Uninstall the outdated or incompatible drivers from the Device Manager. 4. Install the updated drivers and restart the system. 5. Verify if the kernel security check failure error persists. Techniques for diagnosing and addressing memory-related problems 1. Run a memory diagnostic tool, such as Windows Memory Diagnostic, to identify any issues with your RAM. 2. If faulty RAM is detected, replace it with a new one. 3. Ensure that the RAM modules are properly seated in their slots. 4. Check for any bent pins or physical damage on the RAM slots. 5. Update the motherboard's BIOS to the latest version to ensure compatibility with the RAM. Best practices for detecting and removing malware to safeguard the kernel 1. Use a reputable antivirus software and keep it updated with the latest virus definitions. 2. Perform regular system scans to detect and remove any malware. 3. Avoid downloading files or software from untrusted sources. 4. Be cautious of suspicious emails, links, or attachments that may contain malware. 5. Enable automatic updates for your operating system and other software to patch security vulnerabilities. Preventing Kernel Security Check Failure Prevention is key to maintaining a healthy and secure kernel. Here are some tips to minimize the risk of kernel security check failure: Importance of regular system updates and patches Regularly update your operating system, drivers, and software to ensure you have the latest security patches. These updates often address vulnerabilities that can be exploited by malware, reducing the risk of kernel security check failure. Tips for maintaining a healthy and secure kernel 1. Avoid installing unnecessary or untrusted software that can potentially introduce vulnerabilities to your system. 2. Keep your system clean by regularly removing temporary files and unused applications. 3. Use a firewall to control incoming and outgoing network traffic, adding an extra layer of protection to your kernel Educating users about safe browsing habits and avoiding suspicious downloads Users should be educated about safe browsing practices, such as avoiding clicking on suspicious links or downloading files from untrusted sources. This can help prevent malware infections that could compromise the kernel's security. Frequently Asked Questions What is the difference between the kernel and the operating system? The kernel is a core component of the operating system that manages hardware and software interactions, while the operating system includes additional components such as user interfaces and system utilities. Can a single faulty driver cause kernel security check failure? Yes, a single faulty driver can cause kernel security check failure if it triggers a security violation during the kernel's checks. How can I determine if my system is infected with malware? Look out for signs such as slow system performance, unexpected pop-ups, unresponsive applications, or unauthorized changes to files. Running a reputable antivirus scan can also help detect malware. Is it possible to recover data after a kernel security check failure? In some cases, data recovery may be possible after a kernel security check failure. It is recommended to consult a professional data recovery service for assistance. Are there any specific tools or software to help diagnose kernel-related issues? Yes, there are various diagnostic tools available, such as Windows Memory Diagnostic for memory-related issues and driver update software to identify and update outdated drivers. Should I be concerned if I encounter this error only once? If you encounter the kernel security check failure error only once and your system functions normally afterward, it may not be a cause for immediate concern. However, if the error persists or occurs frequently, it is advisable to investigate and address the underlying issue. Can a kernel security check failure be caused by hardware problems? Yes, hardware problems such as faulty RAM or incompatible drivers can cause kernel security check failure. It is important to ensure that your hardware is functioning properly and compatible with your system. What precautions can I take to minimize the risk of kernel security check failure? To minimize the risk of kernel security check failure, follow these precautions: Keep your operating system, drivers, and software up to date with the latest patches. Use reputable antivirus software and perform regular system scans. Avoid downloading files or software from untrusted sources. Practice safe browsing habits and be cautious of suspicious links or attachments. Maintain a clean system by removing temporary files and unnecessary applications. Conclusion: Kernel security check failure is a critical error that can disrupt the stability and security of computer systems. By understanding the causes and implementing the steps to resolve and prevent this error, users can maintain a reliable and secure computing experience. Regular updates, driver maintenance, and malware protection are essential in safeguarding the kernel and ensuring the smooth operation of the system.
#blue_screen_of_death#computer_error#driver_issue#error_message#hardware_issue#kernal_security_check_failure#software_conflict#system_crash#system_failure#system_protection#System_Security#system_stability#system_vulnerability#troubleshooting#Windows_error#Windows_kernel
0 notes