#LDAP Server
Explore tagged Tumblr posts
Text
Installing and Configuring an OpenLDAP Server on Linux: A Comprehensive Guide to Getting OpenLDAP Up and Running!
Are you ready to take control of your data and streamline your authentication and directory services? Look no further than our comprehensive guide on installing and configuring an OpenLDAP Server on Linux!
Introduction Are you ready to take control of your data and streamline your authentication and directory services? Look no further than our comprehensive guide on installing and configuring an OpenLDAP Server on Linux! OpenLDAP is a powerful, open-source solution that allows you to create and manage your own LDAP (Lightweight Directory Access Protocol) directory. With our step-by-step…

View On WordPress
0 notes
Text
(2025-01-02) “Merry And Happy” Vulnerable LDAP Nightmare
I woke up and was reading articles on my mobile phone until I saw this critical message about a very critical vulnerability in Windows LDAP Client. Well, game on, the “fun” has started already after 1 day in the new year! Still 364 days to go. OMG! Not a great way to start the year with an LDAP Nightmare, but it is the reality, unfortunately! This targets both Windows Clients and Servers,…

View On WordPress
#cybersecurity#domain controllers#LDAP Nightmare#Security#Vulnerability#Windows Client#windows servers
0 notes
Text
How to troubleshoot Active Directory Replication issues
#Active Directory#Active Directory Replication#Active Directory Replication Issues#ADREPLSTATUS#DCDiag#Download ADREPLSTATUS tool#LDAP connectivity#Microsoft Windows#RepAdmin.exe command-line tool#Windows#Windows Server#Windows Server 2012#Windows Server 2019#Windows Server 2022#Windows Server 2025
1 note
·
View note
Text
LDAP Nedir? Microsoft Exchange Ldap Entegrasyonu nasıl yapılır? Detaylı anlatımı makalede..
0 notes
Text
My work made me “””upgrade””” to win 11 and all my RSAT tools are gone so I’m having to install AD users and computers manually but the wizard isn’t working and I can’t query the LDAP server to see what port it’s running on I HATE YOU WINDOWS KILL YOURSELF BILL GATES
3 notes
·
View notes
Text
What is Argo CD? And When Was Argo CD Established?

What Is Argo CD?
Argo CD is declarative Kubernetes GitOps continuous delivery.
In DevOps, ArgoCD is a Continuous Delivery (CD) technology that has become well-liked for delivering applications to Kubernetes. It is based on the GitOps deployment methodology.
When was Argo CD Established?
Argo CD was created at Intuit and made publicly available following Applatix’s 2018 acquisition by Intuit. The founding developers of Applatix, Hong Wang, Jesse Suen, and Alexander Matyushentsev, made the Argo project open-source in 2017.
Why Argo CD?
Declarative and version-controlled application definitions, configurations, and environments are ideal. Automated, auditable, and easily comprehensible application deployment and lifecycle management are essential.
Getting Started
Quick Start
kubectl create namespace argocd kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
For some features, more user-friendly documentation is offered. Refer to the upgrade guide if you want to upgrade your Argo CD. Those interested in creating third-party connectors can access developer-oriented resources.
How it works
Argo CD defines the intended application state by employing Git repositories as the source of truth, in accordance with the GitOps pattern. There are various approaches to specify Kubernetes manifests:
Applications for Customization
Helm charts
JSONNET files
Simple YAML/JSON manifest directory
Any custom configuration management tool that is set up as a plugin
The deployment of the intended application states in the designated target settings is automated by Argo CD. Deployments of applications can monitor changes to branches, tags, or pinned to a particular manifest version at a Git commit.
Architecture
The implementation of Argo CD is a Kubernetes controller that continually observes active apps and contrasts their present, live state with the target state (as defined in the Git repository). Out Of Sync is the term used to describe a deployed application whose live state differs from the target state. In addition to reporting and visualizing the differences, Argo CD offers the ability to manually or automatically sync the current state back to the intended goal state. The designated target environments can automatically apply and reflect any changes made to the intended target state in the Git repository.
Components
API Server
The Web UI, CLI, and CI/CD systems use the API, which is exposed by the gRPC/REST server. Its duties include the following:
Status reporting and application management
Launching application functions (such as rollback, sync, and user-defined actions)
Cluster credential management and repository (k8s secrets)
RBAC enforcement
Authentication, and auth delegation to outside identity providers
Git webhook event listener/forwarder
Repository Server
An internal service called the repository server keeps a local cache of the Git repository containing the application manifests. When given the following inputs, it is in charge of creating and returning the Kubernetes manifests:
URL of the repository
Revision (tag, branch, commit)
Path of the application
Template-specific configurations: helm values.yaml, parameters
A Kubernetes controller known as the application controller keeps an eye on all active apps and contrasts their actual, live state with the intended target state as defined in the repository. When it identifies an Out Of Sync application state, it may take remedial action. It is in charge of calling any user-specified hooks for lifecycle events (Sync, PostSync, and PreSync).
Features
Applications are automatically deployed to designated target environments.
Multiple configuration management/templating tools (Kustomize, Helm, Jsonnet, and plain-YAML) are supported.
Capacity to oversee and implement across several clusters
Integration of SSO (OIDC, OAuth2, LDAP, SAML 2.0, Microsoft, LinkedIn, GitHub, GitLab)
RBAC and multi-tenancy authorization policies
Rollback/Roll-anywhere to any Git repository-committed application configuration
Analysis of the application resources’ health state
Automated visualization and detection of configuration drift
Applications can be synced manually or automatically to their desired state.
Web user interface that shows program activity in real time
CLI for CI integration and automation
Integration of webhooks (GitHub, BitBucket, GitLab)
Tokens of access for automation
Hooks for PreSync, Sync, and PostSync to facilitate intricate application rollouts (such as canary and blue/green upgrades)
Application event and API call audit trails
Prometheus measurements
To override helm parameters in Git, use parameter overrides.
Read more on Govindhtech.com
#ArgoCD#CD#GitOps#API#Kubernetes#Git#Argoproject#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
Privileged Access Management Market Driven by AI and Cloud Trends in 2032 Outlook
Privileged Access Management Market was valued at USD 2.69 billion in 2023 and is expected to reach USD 17.42 billion by 2032, growing at a CAGR of 23.13% from 2024-2032.
Privileged Access Management Market is undergoing rapid expansion as organizations face mounting cybersecurity threats targeting privileged credentials. With data breaches becoming more sophisticated, enterprises across critical sectors—including finance, healthcare, and government—are prioritizing PAM solutions to secure administrative access and enforce least-privilege policies.
U.S. Market Shows Aggressive Adoption in Response to Rising Cyber Threats
Privileged Access Management Market is increasingly recognized as a core component of modern cybersecurity frameworks. Companies are investing in PAM tools to enhance visibility, automate session monitoring, and mitigate internal risks. The demand is especially strong in compliance-heavy regions, where regulators emphasize secure access to sensitive systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6666
Market Keyplayers:
Fortinet (FortiPAM, FortiAuthenticator)
BeyondTrust (Password Safe, Privilege Management for Windows & Mac)
CyberArk (Privileged Access Manager, Endpoint Privilege Manager)
Broadcom (Symantec PAM, Symantec PAM Gateway)
Imprivata (OneSign, Privileged Access Management)
Optiv Security (Privileged Access Management Services, Identity & Access Management Solutions)
Okta (Okta Privileged Access, Okta Identity Governance)
IBM (Security Verify Privilege Vault, Security Identity Governance & Intelligence)
Micro Focus (OpenText) (NetIQ Privileged Account Manager, NetIQ Identity Governance)
ManageEngine (Zoho) (PAM360, Password Manager Pro)
HashiCorp (Vault, Boundary)
One Identity (Safeguard for Privileged Sessions, Safeguard for Privileged Passwords)
ARCON (Privileged Access Management, Session Monitoring & Recording)
Netwrix (Privileged Access Management, Auditor for Active Directory)
Delinea (Secret Server, Privilege Manager)
Wallix (Bastion, AdminBastion)
Saviynt (Saviynt for Privileged Access, Identity Governance Cloud)
Senhasegura (PAM Core, DevOps Secret Manager)
KronTech (Single Connect, Dynamic Password Controller)
miniOrange (PAM Solution, Identity Broker)
EmpowerID (Privileged Access Manager, Identity Governance Platform)
StrongDM (Infrastructure Access Platform, Admin UI)
CyberSolve (PAM Advisory, Identity & Access Consulting Services)
Opal Security (Access Review Automation, Just-in-Time Access)
Foxpass (PAM Solution, LDAP-as-a-Service)
Secureden (PAM Software, Remote Access Management)
RevBits (Privileged Access Management, Endpoint Security)
Silverfort (Unified Identity Protection, Secure Access for PAM)
IDM Technologies (IDM Privileged Access, Identity Governance Suite)
Market Analysis
The Privileged Access Management (PAM) market is being shaped by an urgent need to defend against identity-based attacks and insider threats. As businesses adopt hybrid cloud infrastructures and remote access models, managing privileged credentials becomes a top priority. Organizations are shifting from traditional perimeter security to identity-first security strategies that include PAM as a foundational layer. In the U.S., regulatory mandates like SOX, HIPAA, and FISMA are driving PAM implementation across enterprises, while in Europe, GDPR compliance and industry-specific norms continue to fuel adoption.
Market Trends
Growing demand for cloud-native and hybrid PAM solutions
Integration of AI and machine learning for threat detection and access analytics
Increased automation of access provisioning and de-provisioning
Rise in just-in-time (JIT) access and zero standing privileges
Expansion of PAM to DevOps and third-party vendor environments
Enhanced auditing and reporting features to meet compliance
Privileged session recording and real-time behavior analytics
Market Scope
The Privileged Access Management Market is not limited to large enterprises—it is increasingly essential for mid-sized businesses managing critical assets and data. With digital transformation accelerating, PAM is becoming a non-negotiable part of cybersecurity roadmaps.
Secure access to critical systems across cloud and on-prem
Real-time monitoring and auditing of privileged sessions
Identity-centric security aligned with zero-trust models
Vendor and third-party access governance
Scalable solutions for enterprises of all sizes
Policy enforcement and credential vaulting
Forecast Outlook
The future of the PAM market is marked by aggressive innovation, strategic investments, and global standardization. With threat actors constantly evolving, businesses are embracing dynamic, identity-focused security architectures. PAM solutions are expected to integrate more deeply with endpoint protection, identity governance, and broader zero-trust ecosystems. The market's trajectory points toward smarter, automated, and user-centric systems that deliver both protection and operational efficiency.
Access Complete Report: https://www.snsinsider.com/reports/privileged-access-management-market-6666
Conclusion
The Privileged Access Management Market is no longer a niche solution—it’s a strategic imperative. As U.S. and European enterprises adapt to a hyper-connected, threat-prone environment, PAM stands at the forefront of cyber resilience. With increasing attacks on administrative access, organizations that prioritize PAM will not only meet regulatory standards but will also build trust, reduce risk, and enable secure digital transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A experiences robust growth in Cloud Access Security Broker Market driven by data security priorities
U.S.A sees rising adoption of Voice Biometrics Market Size across banking and government sectors
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
The VPN connection between the on-site servers at our high school with the user home directories, mailboxes, LDAP (the inner workings of which I never did fully understand), the server for our thick-client Linux workstations, shell server for the students and various other sundries on them and the new co-located server with the website on it kept dropping for some unknown reason we never figured out so we implemented a cron job that would periodically run on both servers (I don't remember how frequently, maybe every 10 minutes?) to check the connection and restart the network interface if it was down.
0 notes
Text
Need a performance testing tool? We have short listed best load testing tools to perform automated testing. Load testing is a important part of measuring performance When we talk about performance testing tools, there are many available on the internet. Many of them are open source and many of them are paid. It is necessary for you to know every tool so that you can use them as per your requirement. This article features some of the most widely used performance testing tools that you can use to measure load stress capacity and web application performance. This article includes both open source and licensed performance testing tools. Apache JMeter This is a 100% pure Java open source application, which is designed to measure performance as well as load test functional behavior. It can be used on both dynamic and static resources and web dynamic languages. Grinder It is a load testing framework that runs on Java platform. This framework is easy to run a distributed test that can be done by using various load injector machines. It is available under BSD-style open-source license and is available for free. Gatling It is an open source load testing framework that is built based on Netty, Akka and Scala. It is a high-performance framework that offers ready-to-present HTTP reports. It offers scenario recorder and developer-friendly DSL. Tsung This is an open source load testing tool that runs on multiple protocols. It is a free software that is released under GPLv2 license. It can be used to stress WebDAV, HTTP, MySQL, LDAP and many other servers. LoadRunner This is a very common load testing tool, which gives you the perfect picture pertaining to end-to-end system performance. It is used to identify and rectify the issues prior to the application go live. WebLOAD When it comes to complicated process of performance testing WebLOAD is the name that makes the task easier. This is a flexible tool that builds load scenarios with any required logic and integration. Appvance When you are using Appvance you can be rest assured that you are with the technology leader in the segment. The drive response time for this tool is 500ms, which is faster than any other tool. NeoLoad This load testing software solution is designed to be used in both mobile as well as web applications. This is used to monitor infrastructure behavior and simulate the user activity in realistic manner. LoadUI This load tester enables the users to interactively redistribute, configure and create their load tests. This tester offers complete test coverage in a single test environment and it also supports all standard technologies and protocols. WAPT If you are looking for a cost-effective and easy-to-use stress and load testing tool there cannot be a better one than WAPT. It can test any website including mobile sites, business applications and web portals. Loadster This is the application whose aim to offer load testing for the users from anywhere. It is a fully featured load testing solution that can be used for web services, web apps and websites. It can handle cookies effortlessly and is built for real web apps. LoadImpact This is an on-demand and automated performance testing tool for DevOps. Whether it is API or mobile app or web app or website – this tool is equally effective for testing any protocol. Rational Performance Tester It is a load testing tool from IBM that offers code-free testing for the test data. It also offers root cause analysis tool along with real time reporting. It offers quick performance tests and analyzes impact of the load on your application. Testing Anywhere It is all-in-one easy-to-maintain automation testing software. This is scriptless single piece software that enables endless testing possibilities. It is built on patented SMART Automation Technology that brings built-in intelligence to testing. OpenSTA This distributed software testing framework is built around COBRA. The latest toolset is designed to perform heavy load tests for scripted HTTP and HTTPS along with measurement of performance from Win32 platforms.
QEngine (ManageEngine) It is a QEngine of Product End of Life Cycle announced by ManageEngine but is not available to purchase or active support. It offers services like Real Browser Monitor, HTTP URL Monitor and J2EE Web Transaction Monitor. Loadstorm This is a cost-effective and easy load testing tool that can be used for both mobile and web applications. This tool help you know the breaking points of your applications. CloudTest The best tool for faster load testing. This is a cloud based load testing tool. This tool fast tracks your load testing scenario and it performs with speed that is scalable and affordable. Httperf This tool can be used for measuring the performance of web server. It offers flexible facilities to generate different HTTP workloads and server performance measurement. It offers high performance and robust testing service. LoadComplete This is a desktop tool used for load testing of web applications along with their scalability, stress and performance. It works with both Rich Internet Application and HTML websites and uses modern web technologies like ASP.NET, AJAX, Flex, Flash etc. Loader This is a free and cloud-based load testing service, which offers tests of stress and load for your web apps and apps that have thousands of concurrent connections. It gives the output as stats and graphs. Allmon This is a system that collects and stores metrics that is used for monitoring the performance and availability along with quality, health and responses of the application. It also offers some data mining algorithms that is useful for further performance analysis. Databene Benerator It is a framework that supports in performing performance and load tests in real-time scenarios. It helps in generating high-volume realistic tests data for your system that is undergoing test. CLIF This is an open source load testing platform that includes load injector for generating traffic and probes for measuring the usage of the resources like network, memory and processor. ContiPerf 2 This is a light weight testing tool that enables users to leverage JUnit 4 test cases as performance tests easily. It uses Java annotations to define the test execution characteristics. Curl-loader This is an open source testing tool that is written on C language. It simulates application load and behavior of tens and thousands of FTP/FTPS and HTTP/HTTPS clients with their own source IP address. Linux Test Project This is a test project that is started by Bull, OSDL and SGI developed and maintained by Cisco, IBM, Oracle, Red Hat, SUSE, Fujitsu and many others. The aim is to deliver tests to the open source community. DBMonster This is a testing tool that randomly generates test data and places the same into the SQL database. It also helps in testing the capability of the application to deal with large database. Dieseltest This is an easy-to-use load testing tool that can be used to simulate hundreds or thousands of users on websites. This load tester has the ability to record the scripts and play them back again to show the results real time FunkLoad Like its name this is a functional and load testing tool written in Python script using the pyUnit framework. It enables functional testing of web projects and also regression testing. FWPTT This is a web application testing tool that is used for testing the loads on web applications. It has the capability of recording normal as well as AJAX requests and it also works with PHP, JSP and others. GrinderStone This is an Eclipse plug-in used to develop Grinder load testing scripts including support for debugging. It has the ability to create separate running configurations and is compatible with all latest versions of PyDev. HammerDB It is an open source benchmarking and load testing tool that can be used for variety of servers like SQL, Oracle, PostgreSQL, TimesTen, MySQL and many others. Fully automated functionality and advanced command-line is available in Autohammer extension. Http_load It tests the throughput of a web server by running multiple HTTP fetches in parallel.
It runs in a single process, which is unlikely for other applications. Hence there is no chance of bogging down client machine. Iperf It is a modern alternative that can be used for measuring maximum UDP and TCP bandwidth performance and it allows tuning of different UDP characteristics and parameters. It has the capability to report bandwidth, datagram loss and delay jitter. IxoraRMS If you want to visualize and gather the monitoring data IxoraRMS is the tool that you can use. It has a Swing GUI and is developed under Java platform. It is an open source platform released on Apache License. J-Hawk This is a performance testing tool and is a Java based open source framework. This tool can execute the module in two ways – property mode and script mode. The scripting language is developed in a easy-to-learn method for the developers. JChav This is a method to see the changes in performance of the web applications that you are using over time. It does so by running a benchmark test for every build produced by you. This tool is available under Apache License. JCrawler This is an open source tool that is used for testing the stress for your web applications. This is named as Crawler because of its crawling or exploratory feature. The load parameters in this tool are configurable. MessAdmin It is a non-intrusive and light-weight tool that is used for monitoring the interaction with Java HTTP session. It can easily be attached to any Java EE application that too with no changes to the monitored application. Mstone This is a multi-protocol performance and stress testing tool that has the capacity to simultaneously test multiple protocols like SMTP, POP etc. along with the performance measurement of every transaction. Multi-Mechanize This is an open source framework based on Python script, which is used for load and performance testing. It can run on concurrent Python scripts to generate load against a remote service or a site. NGrinder This is a stress testing platform that also has the capacity to simultaneously execute various functions like test execution, script creation, monitoring and generating result report. It provides integrated environments and eliminates inconveniences making it easy for running the test. OpenSTA It is a software testing architecture that is available in distributed mode. This is designed around COBRA. It offers the modern tool sets that have the ability to perform scripted HTP and HTTPS heavy load tests. OpenWebLoad This is a tool that is used for testing load and stress on web applications. It offers near real time performance measurements of the applications that are under test. This tool is useful when you are doing some optimization of your tools. Ostinato It is a cross-platform network packet crafter or traffic generator and analyzer with friendly GUI. It is an open source system that can craft and send packets of many streams with various protocols at different rates. P-unit It is an open source framework that can be used for performance benchmark and unit tests. It can run same tests with single as well as multi threads. It also has the capability to track memory and time consumption along with generating reports in text, image or PDF format. Postal This program is written with the aim to benchmark SMTP servers. The aim of writing this program was to see which server can give the best result with more than 1,000,000 users at a time. Pylot It is a free and open source tool that is used for testing scalability and performance of web services. It runs HTTP tests that are useful to test the load for capacity planning, analysis, system tuning and benchmarking. Raw Load Tester It is an open source free tool that is used for testing the load on websites. Though it does not have many features it can be useful where there is a need to use a more comprehensive load testing tool. Seagull It is an open source multi-protocol traffic generator tool used for testing. This tool was primarily aimed at IMS protocols but ultimately has become a powerful tool for traffic generation.
JoeDog Software This is a tool to generate traffic. The JoeDog software is a useful tool that helps you generate traffic through blogs rather than any other aspects of the website. This is basically open source software. SIPp This is a free open source test tool or traffic generator that is used for SIP protocol. This tool has UAS and UAC that are basic SipStone user agent scenarios. It also has the ability to read custom XML scenarios. Soap-Stone This is a network benchmark application that conducts automatic recording and benchmark activities by placing your network under load. This tool is delivered to you as a single Java JAR archive. Stress Driver It is a general purpose strexs test tool for testing the loads on your website. This is not a free open source tool and is available under license distribution. This effective tool is best for your business website. PushToTest: This open source test tool surfaces any type of functional issues and performance bottlenecks. You can build and test web, AJAX, BPM and SOA applications in a cloud or grid environment. TPTEST The aim of this tool is to offer the users to measure the speed of their internet connection in a simple and easy possible way. It offers measurement of the throughput speed to and from many reference servers over the internet. Valgrind This is an instrumentation framework that can be used for making dynamic analysis tools. There are many Valgrind tools that have the capability to detect many memory management and threading bugs automatically. LoadSim It is load simulator for web application that allows you to create simulations and run them against your web servers. This web simulator is fairly complex and offers you the accurate information Web Polygraph This is a performance testing tool that is available freely. This testing tool is useful for caching proxies, test the origin server accelerators, content filters, L4/7 switches and many other web intermediaries. WebLOAD WebLOAD: This a testing tool that can create tests in easy fashion with intuitive record and playback controls. This tool enables user to easily turn the recorded script into an execution-ready test with the help of automatic identification. Bees With Machine Guns This is an utility that can help you creating many bees or micro EC2 instances that can load test the web applications. This has the dependencies towards Python 2.6, Boto and Paramiko. Ab – Apache This is a benchmarking tool for your Apache HTTP server. This tool is designed in such a way that it can give you impression on how is the performance of your current Apache installation. Now that you have a fair idea of the performance testing tools available on the net, it is up to you to take the decision of choosing the one that is suitable for your requirement. Some offer the standard testing tools while some others provide you premium features, but at a price. Start using them to test the performance of your websites and web servers
0 notes
Text
Appian Senior Developer ACD201 Practice Exam For Success
Becoming an Appian Certified Senior Developer (ACD201) is a significant milestone for professionals looking to validate their expertise in designing and delivering high-performing, scalable Appian applications. To help candidates prepare, Cert007 offers the latest Appian Senior Developer ACD201 Practice Exam, designed to closely simulate the actual test environment. This practice exam covers all major exam objectives, ensuring that you gain the practical knowledge and confidence needed to pass the ACD201 exam with ease. By familiarizing yourself with real exam scenarios, troubleshooting techniques, and Appian best practices, you can increase your chances of success and advance your career in the low-code automation field.
Who Should Take the ACD201 Exam?
The Appian Certified Senior Developer exam is tailored for professionals with at least 12 months of hands-on experience in Appian project implementation. Candidates should be proficient in:
Converting complex business requirements into functional applications with minimal guidance.
Understanding Appian’s platform architecture and leveraging it for building scalable applications.
Designing and implementing relational data models to support process automation.
Senior Developers are expected to work independently on complex projects, making design decisions that ensure scalability, security, and efficiency. Additionally, they should be comfortable with mentoring junior developers, conducting code reviews, and collaborating with DevOps and QA teams throughout the application lifecycle.
Core Skills Tested in the ACD201 Appian Certified Senior Developer Exam
The ACD201 exam evaluates a broad range of skills, ensuring that certified developers can handle real-world Appian application development. The major areas tested include:
1. Platform and Application Management (12%)
Candidates must be skilled in:
Configuring the Administration Console to manage system performance.
Using logs, dashboards, and health check tools to troubleshoot application issues.
Deploying applications across multiple environments while ensuring quality through technical reviews and performance testing.
2. Data Management (20%)
Data is at the heart of any Appian application. Candidates must demonstrate their ability to:
Design complex relational data models that align with business objectives.
Implement and maintain Appian records, views, and stored procedures for efficient data management.
Optimize data queries and transformations to enhance application performance.
3. Application Design and Development (28%)
As the most weighted section of the exam, candidates should be proficient in:
Building complete Appian applications using the platform’s core components.
Applying security best practices to manage access control at the object and application levels.
Following UX design principles to create intuitive user interfaces.
4. Advanced Appian Concepts (18%)
Senior Developers must have an academic understanding of advanced features, including:
Configuring authentication options such as SAML and LDAP for Single Sign-On (SSO).
Integrating external systems via web APIs and connected systems.
Leveraging smart services and plug-ins while assessing their potential risks and challenges.
5. Performance & Scalability (22%)
To ensure optimal performance, candidates should be skilled in:
Designing memory-efficient process models and minimizing system resource consumption.
Conducting load testing and using automated testing tools for performance analysis.
Identifying and resolving performance bottlenecks using server logs and monitoring tools.
How to Prepare for the Appian Senior Developer ACD201 Exam
To succeed in the exam, candidates should:
✅ Take the Cert007 ACD201 Practice Exam to familiarize themselves with real test scenarios.
✅ Study the Appian documentation and developer guides to understand best practices.
✅ Engage with the Appian Community to stay updated on the latest platform features and enhancements.
✅ Work on real-world Appian projects to reinforce theoretical knowledge with hands-on experience.
Boost Your Career with the ACD201 Certification
Earning the Appian Certified Senior Developer (ACD201) certification enhances your credibility and career prospects in the low-code automation industry. It proves that you have the expertise to design, build, and manage enterprise-grade Appian applications, making you a valuable asset to any organization. By leveraging resources like Cert007’s practice exam, you can streamline your preparation process and maximize your chances of success.
Ready to take your Appian development skills to the next level? Start preparing today and unlock new career opportunities!
0 notes
Text
Installing and Configuring an OpenLDAP Server on Linux: A Comprehensive Guide to Getting OpenLDAP Up and Running!
Are you ready to take control of your data and streamline your authentication and directory services? Look no further than our comprehensive guide on installing and configuring an OpenLDAP Server on Linux!
Introduction Are you ready to take control of your data and streamline your authentication and directory services? Look no further than our comprehensive guide on installing and configuring an OpenLDAP Server on Linux! OpenLDAP is a powerful, open-source solution that allows you to create and manage your own LDAP (Lightweight Directory Access Protocol) directory. With our step-by-step…

View On WordPress
0 notes
Text
How Symfony Software Development Enhances Web Performance and Security?

In today’s digital era, businesses need web applications that are not only feature-rich but also high-performing and secure. Symfony, a leading PHP framework, has become a preferred choice for web application development due to its robust architecture, performance optimization features, and advanced security mechanisms. Let’s explore how Symfony software development enhances web performance and security.
Performance Optimization with Symfony
1. Efficient Caching Mechanism
Symfony’s built-in caching system ensures that web applications load faster and use fewer server resources. It supports multiple caching methods such as HTTP caching, application caching, and OPcache integration, reducing redundant computations and improving response times.
2. Code Reusability and Modularity
Symfony is designed around reusable components and a modular architecture. This reduces the need for redundant code, making the application lightweight and improving execution speed. Developers can integrate only the necessary components, ensuring optimized performance.
3. Autoloading and Dependency Injection
Symfony uses an efficient autoloading system that eliminates the need to manually include files. Additionally, its powerful dependency injection container reduces memory consumption, allowing applications to run faster with fewer resources.
4. Database Optimization
Symfony’s Doctrine ORM (Object-Relational Mapping) optimizes database queries by reducing unnecessary calls and enabling query caching. This ensures faster data retrieval and better database performance.
5. Built-in Debugging and Profiling Tools
Symfony’s debugging tools, such as the Web Debug Toolbar and Profiler, help developers identify performance bottlenecks. By optimizing slow queries and refining application logic, Symfony ensures enhanced application speed and efficiency.
Enhancing Security with Symfony
1. Secure Authentication and Authorization
Symfony offers a built-in security system that provides robust authentication and authorization mechanisms. It supports multi-factor authentication, OAuth, JWT, and LDAP integrations, ensuring secure user access and preventing unauthorized logins.
2. Protection Against Common Web Threats
Symfony is designed to protect applications from common security threats, including:
Cross-Site Scripting (XSS): It automatically escapes output to prevent malicious script injections.
Cross-Site Request Forgery (CSRF): Symfony includes built-in CSRF protection to safeguard forms from unauthorized requests.
SQL Injection Prevention: By using Doctrine ORM, Symfony prevents direct SQL injections by implementing parameterized queries.
3. Secure Data Encryption
Symfony supports data encryption mechanisms such as bcrypt and Argon2 hashing for password storage. It also enables secure transmission of sensitive data using SSL/TLS protocols.
4. Regular Security Updates and Community Support
Symfony has an active community and a dedicated security team that continuously monitors vulnerabilities and releases regular updates and patches. This ensures applications remain secure against evolving cyber threats.
Conclusion
Symfony software development is an excellent choice for businesses looking to build high-performing and secure web applications. With its powerful caching mechanisms, optimized database queries, and security-focused architecture, Symfony ensures enhanced web performance and protection against cyber threats. By leveraging Symfony’s capabilities, businesses can deliver fast, scalable, and secure web applications, ensuring a seamless user experience.
0 notes
Text
Preventing LDAP Injection Vulnerabilities in Laravel
Introduction
In today’s cybersecurity landscape, web applications are frequently targeted by malicious actors using various injection techniques. One of the most dangerous is LDAP injection, which can allow attackers to manipulate Lightweight Directory Access Protocol (LDAP) queries, potentially compromising sensitive data. If you are developing applications with Laravel, it’s essential to be aware of this vulnerability and implement the necessary safeguards.

In this blog post, we will discuss what LDAP injection is, how to prevent it in Laravel applications, and how our free tool can help to check website vulnerability and secure your website.
What is LDAP Injection?
LDAP injection is a form of attack where the attacker injects malicious code into an LDAP query to manipulate the results returned by the server. The attack typically occurs when user input is improperly sanitized, allowing the attacker to alter the structure of the LDAP query.
For example, consider an authentication mechanism where the user submits a username and password. If the input is not sanitized, an attacker could manipulate the query to authenticate as any user.
How LDAP Injection Works
Here’s a simple example of an LDAP query in Laravel that could be vulnerable to injection:
$ldapConnection = ldap_connect("ldap://localhost"); $dn = "uid=$username,dc=example,dc=com"; $filter = "(uid=$username)"; $search = ldap_search($ldapConnection, $dn, $filter);
If an attacker provides input like admin)(&(|(password=password, the $filter string will become:
$filter = "(uid=admin)(&(|(password=password)";
This could result in unintended behavior, such as returning all records in the LDAP database.
How to Prevent LDAP Injection in Laravel
To secure your Laravel application against LDAP injection, you should follow these best practices:
Sanitize User Input: Always sanitize user input before passing it to LDAP queries. You can use Laravel’s built-in validation and sanitization features.
Use Prepared Statements: Prepared statements ensure that the user input is treated as data rather than executable code. Laravel’s query builder and Eloquent ORM can help mitigate these risks in other contexts, but for LDAP, it’s essential to sanitize properly.
Limit User Input Length: Restrict the length of input fields like usernames and passwords to prevent overflows or other attack vectors.
Use Strong Authentication: Implement multi-factor authentication (MFA) to add an additional layer of security, even if LDAP injection is successful.
Monitor Logs for Unusual Activity: Regularly check the logs for any suspicious activity related to LDAP queries, such as unexpected characters or patterns in the username.
Example: Secure LDAP Query in Laravel
Below is an example of a more secure way to handle LDAP queries in Laravel using proper input validation:
use Illuminate\Support\Facades\Validator; public function authenticate(Request $request) { $validator = Validator::make($request->all(), [ 'username' => 'required|string|max:255', 'password' => 'required|string|min:8', ]); if ($validator->fails()) { return response()->json(['error' => 'Invalid input'], 400); } $username = htmlspecialchars($request->input('username')); $password = $request->input('password'); $ldapConnection = ldap_connect("ldap://localhost"); $dn = "uid=$username,dc=example,dc=com"; $filter = "(uid=" . ldap_escape($username, "", LDAP_ESCAPE_FILTER) . ")"; $search = ldap_search($ldapConnection, $dn, $filter); // Further LDAP authentication code }
In this example, we use htmlspecialchars() to sanitize the username and ldap_escape() to ensure the username is properly encoded before being included in the LDAP query.
How Our Free Tool Can Help
To help identify LDAP injection vulnerabilities in your website, we have a Free Website Security Scanner. Our tool performs a detailed security audit and can detect potential LDAP injection vulnerabilities, along with other common issues like SQL injection, cross-site scripting (XSS), and more.
Here’s a screenshot of the tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Vulnerability Assessment Report
After scanning your website with our tool for a website security test, you’ll receive a detailed vulnerability assessment report. This will include findings on LDAP injection risks, along with suggestions for remediation. Here’s a sample report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
LDAP injection can be a significant threat to your Laravel applications if left unaddressed. By understanding how the attack works and implementing secure coding practices, you can protect your applications from this dangerous vulnerability. Additionally, our free Website Security Checker can help you identify and resolve LDAP injection issues, ensuring your website stays secure.
For more detailed cybersecurity insights and best practices, visit our blog at Pentest Testing Corp Blog.
1 note
·
View note
Text
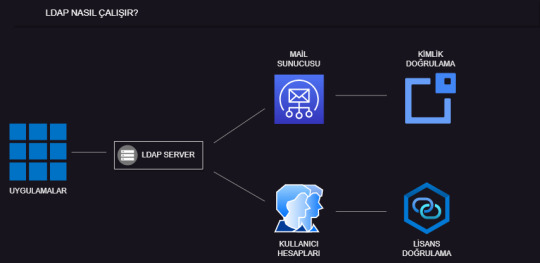
LDAP Nedir? Bir Örnek Üzerinden Anlatalım.
LDAP'ın kurumsal bir e-posta sistemi için uygulamalı örneğini genel hatlarıyla anlattım. Keyifli Okumalar.
Örnek LDAP Nedir Senaryosu Bir şirket, tüm çalışanlarının e-posta hesaplarını yönetmek için LDAP kullanmaya karar vermiştir. Şirketin IT departmanı, çalışanların kullanıcı adlarını, şifrelerini ve e-posta adreslerini LDAP sunucusunda merkezi olarak yönetmek istemektedir. Bu örnekleme LDAP Protokolüne genel bir bakış sergilemektedir. Bununla beraber detaylı anlatım ile alakalı video ilerleyen…

View On WordPress
0 notes
Text
Optimizing IT Operations Using Red Hat Satellite
In today's rapidly evolving IT landscape, efficiency and scalability are paramount. As organizations grow, managing complex infrastructure and ensuring the availability of critical systems becomes a challenge. This is where Red Hat Satellite comes into play. A robust and comprehensive systems management platform, Red Hat Satellite helps businesses optimize their IT operations by simplifying administration, improving system consistency, and increasing overall operational efficiency.
What is Red Hat Satellite?
Red Hat Satellite is an open-source system management tool designed to help organizations manage their Red Hat-based environments. It provides a centralized platform for provisioning, patching, and managing systems, ensuring that they are always up to date, secure, and running efficiently. Satellite integrates seamlessly with Red Hat Enterprise Linux (RHEL) and other Red Hat offerings to provide a unified and scalable solution for managing large fleets of Linux systems.
The primary goals of Red Hat Satellite are:
Automation: Automate routine IT tasks like provisioning, patching, and configuration management.
Compliance: Ensure that systems are configured in line with security and operational standards.
Visibility: Gain insights into system performance, security posture, and patching status.
Efficiency: Reduce manual interventions, streamline workflows, and improve overall productivity.
Key Benefits of Red Hat Satellite for IT Operations
1. Simplified System Provisioning
Provisioning new systems manually can be time-consuming and error-prone. Red Hat Satellite provides a powerful set of automation tools that allow you to quickly deploy new systems, applications, and services. Using predefined system templates, IT teams can automate the process of configuring servers with the necessary packages, configurations, and security settings. This not only speeds up the provisioning process but also ensures consistency across all systems.
With Satellite, administrators can:
Automate system installations and configurations.
Integrate with external systems like LDAP or Active Directory for user management.
Use PXE (Preboot Execution Environment) and Kickstart for automated OS installations.
2. Efficient Patching and Software Management
Keeping systems up-to-date with the latest security patches and software updates is crucial for maintaining a secure IT environment. Red Hat Satellite streamlines the process by allowing you to manage patches and updates across a wide range of systems from a central location. The tool ensures that patches are deployed consistently, minimizing the risk of security vulnerabilities due to outdated software.
Key features include:
Patch Management: Easily schedule and deploy patches to systems at scale.
Lifecycle Management: Manage system lifecycles, including development, testing, and production environments.
Compliance and Audit Trails: Track patch statuses and ensure systems remain compliant with internal security policies and external regulations.
3. Configuration Management with Puppet and Ansible
Red Hat Satellite supports integration with popular configuration management tools such as Puppet and Ansible. This integration enables IT teams to automate and standardize configurations across the entire infrastructure. Whether you're managing a few systems or thousands, automation ensures that systems are configured consistently and correctly every time.
With Puppet and Ansible, administrators can:
Automate configuration updates, reducing human errors.
Apply configurations consistently across different environments (dev, test, production).
Scale configurations easily as the infrastructure grows.
4. Enhanced Security and Compliance
In today’s world, security is more critical than ever. Red Hat Satellite includes built-in tools for enforcing security best practices and ensuring that your systems are compliant with industry standards, such as PCI-DSS, HIPAA, or GDPR. The system offers features like automated security patching, configuration baselines, and compliance reporting, making it easier for teams to manage security across their environments.
Some notable security features include:
Security Hardening: Configure and enforce security policies on all systems.
Compliance Reporting: Generate reports to track compliance with security frameworks.
Role-based Access Control (RBAC): Define granular permissions for users to ensure that only authorized personnel can make changes.
5. Centralized System Monitoring and Reporting
One of the most important aspects of IT operations is ensuring systems are running smoothly. Red Hat Satellite provides centralized monitoring and reporting, giving IT teams valuable insights into system performance, patching status, and overall health. This enables proactive issue resolution and minimizes downtime.
Red Hat Satellite offers:
System Health Dashboards: View the status of all managed systems from a central dashboard.
Automated Notifications: Receive alerts when systems require attention or are out of compliance.
Reporting: Generate detailed reports on system performance, patching activities, and compliance.
6. Scalability and Flexibility
As organizations scale, their IT infrastructure becomes increasingly complex. Red Hat Satellite is designed to handle large-scale environments, supporting thousands of systems across multiple data centers and geographies. With Satellite, you can manage vast numbers of systems while ensuring optimal performance and minimal administrative overhead.
Satellite offers:
High Availability: Redundant configurations to ensure that the Satellite server remains operational even in case of failures.
Remote Management: Manage remote systems securely, regardless of location.
Dynamic Content Views: Customize software repositories and updates to meet specific needs based on system roles or requirements.
Integrating Red Hat Satellite with Other Tools
Red Hat Satellite is not just a standalone solution; it integrates well with other tools in the Red Hat ecosystem and beyond. For instance, it works seamlessly with:
Red Hat Insights: For proactive identification and resolution of system vulnerabilities and performance issues.
Red Hat CloudForms: For hybrid cloud management and orchestration.
Red Hat OpenShift: For managing containerized applications and Kubernetes clusters.
Conclusion
Optimizing IT operations is a critical aspect of any organization's success, and Red Hat Satellite is an invaluable tool in this process. By automating routine tasks, ensuring system compliance, and improving visibility across your infrastructure, Satellite empowers IT teams to manage complex environments more efficiently and effectively. Whether you are managing a handful of systems or thousands, Red Hat Satellite helps streamline your operations, reduce risks, and ultimately drive greater business value.
If you're looking to enhance your IT management processes and improve system performance, Red Hat Satellite provides the comprehensive, scalable, and secure solution you need to stay ahead in today’s competitive landscape.
For more details visit
hawkstack.com
qcsdclabs.com
0 notes
Text
⚙️ cURL là gì ? Cách sử dụng cURL
-- cURL viết tắt của client URL là một công cụ dòng lệnh (command-line tool) vô cùng hữu ích, cho phép bạn truyền dữ liệu qua nhiều giao thức khác nhau. Nó được sử dụng rộng rãi trong việc tương tác với các máy chủ, tải xuống dữ liệu, thực hiện các yêu cầu HTTP và nhiều tác vụ khác.
🔰Giao thức được hỗ trợ trong cURL Command
cURL Command có thể hỗ trợ các giao thức (protocol) sau: HTTP, HTTPS, IMAP, IMAPS, SMB, MBS, SFTP, GOPHER, LDAP, LDAPS, SCP, FTP, FTPS, TELNET, POP3, POP3S, SMTP, SMTPS.
cURL có nhiều giao thức được hỗ trợ khác nhau. Tuy nhiên, cURL sẽ sử dụng giao thức HTTP theo mặc định nếu không có giao thức nào được cung cấp.
🔰Tại sao sử dụng curl?
Vậy tại sao bạn nên sử dụng cURL? Hãy xem xét những lợi ích sau của công cụ này:
Nó có tính di động cao. Nó tương thích với hầu hết mọi hệ điều hành và thiết bị được kết nối.
Nó hữu ích khi thử nghiệm các điểm cuối để kiểm tra xem chúng có hoạt động hay không.
Nó có thể dài dòng, cung cấp thông tin chi tiết về những gì đã được gửi/nhận, điều này hữu ích cho việc gỡ lỗi.
Có chức năng ghi lại lỗi tốt.
Có thể giới hạn tốc độ.
🔰Chức năng của cURL
Chức năng của cURL là giúp người dùng tải xuống một trang web hoặc hình ảnh trên mạng Internet. Ngoài ra, nó cũng hỗ trợ người dùng vận chuyển tập tin, dữ liệu, hình ảnh, hoặc truyền dữ liệu đến và đi từ server. Bên cạnh đó, cURL cho phép bạn kiểm tra Cookie được tải trên URL.
0 notes