#Linux PAM Administration
Explore tagged Tumblr posts
Text
Why it is not recommended to merge the /etc/passwd and /etc/shadow files in Linux
Merging the /etc/passwd and /etc/shadow files in Linux is not recommended because these two files serve distinct purposes related to user account management, and merging them would compromise security and system functionality. Here are the main reasons why they should remain separate:
1. Separation of Concerns (Security and Privacy)
/etc/passwd: This file stores basic user information such as the username, user ID (UID), group ID (GID), full name, home directory, and login shell. Importantly, the passwd file used to store user passwords in older Unix systems, but this practice has been replaced with storing passwords in the /etc/shadow file.
/etc/shadow: This file specifically contains the hashed passwords for users and additional security-related data like password aging information. Only the root user has access to this file to ensure that the hashed passwords are protected from unauthorized access.
If these files were merged, the password hashes from /etc/shadow would become visible to all users who can read /etc/passwd, which would severely compromise the security of the system.
2. Security
Password Protection: The /etc/shadow file is designed to be readable only by the root user. This prevents non-privileged users from accessing sensitive data, like password hashes. If /etc/passwd and /etc/shadow were merged, this protection would be lost, exposing the hashed passwords to anyone who can read the file (e.g., users, processes running with lower privileges, etc.).
Hashing Algorithms: The passwords in /etc/shadow are stored in a hashed form using secure hashing algorithms like bcrypt, SHA-512, etc. Merging the files would expose these hashes unnecessarily, which could lead to attacks such as brute-forcing or rainbow table attacks.
3. System Integrity
File Permissions: By separating the files, system integrity is maintained. The /etc/passwd file typically needs to be world-readable to allow normal operation of many system processes and utilities. However, /etc/shadow requires restricted permissions to maintain the security of user credentials.
Authentication Process: Various services (like login, PAM, etc.) expect the password data to be in /etc/shadow to apply necessary access control and hashing operations securely. If both files were merged, it could interfere with the standard authentication mechanisms and might cause issues with login services, password management, and account auditing.
4. Audit and Management
Password Aging and Locking: The /etc/shadow file stores important data like password expiration, account expiration, and account locking information. This allows system administrators to manage password policies effectively without exposing sensitive data. Merging these files could lead to confusion and reduce the effectiveness of these features.
Account Management Tools: Many system tools (such as passwd, chage, vipw) rely on the separation of these files to manage user accounts. Merging them would require modifying all these tools and could break standard utilities that users and administrators rely on.
5. System Compatibility
Different distributions and Unix-like systems might handle these files differently. Merging /etc/passwd and /etc/shadow would create compatibility issues across different systems and might make it harder to migrate user data or integrate with external systems.
For example, other operating systems like BSD or certain older Unix systems may still depend on the distinction between these files for correct operation. Merging them could introduce interoperability problems.
Conclusion
The separation of /etc/passwd and /etc/shadow is a key design decision to ensure user security and system integrity. The passwd file contains basic, non-sensitive user information, while the shadow file contains sensitive password hashes and security-related data. Merging them would expose sensitive information and undermine the security mechanisms in place, making the system vulnerable to various attacks. Therefore, it's important to keep these files separate to protect user data and maintain the proper functioning of the system.
for more details please visit
www.qcsdclabs.com
www.hawkstack.com
0 notes
Text
Enhance Security with Linux Privileged Access Management Solutions
Linux Privileged Access Management (PAM) is essential for securing your Linux environment by controlling and monitoring privileged accounts and access. At Privilege Control, we specialize in offering robust solutions for Linux PAM to ensure that sensitive systems and data are protected against unauthorized access and potential breaches.
Our Linux PAM solutions provide comprehensive control over who can access critical system resources and perform administrative functions. By implementing strict access controls and rigorous auditing, we help organizations enforce the principle of least privilege, reducing the risk of insider threats and external attacks. Our tools facilitate granular access management, session recording, and real-time monitoring, enabling you to track and manage privileged activities efficiently.
With our Linux PAM solutions, you gain enhanced visibility into user actions, automated password management, and secure credential storage. This not only strengthens your security posture but also ensures compliance with industry regulations and best practices. Trust Privilege Control to deliver tailored Linux PAM solutions that align with your organization's needs, providing peace of mind and protecting your valuable assets from unauthorized access and cyber threats.
0 notes
Link
This Linux PAM Administration course will introduce the PAM (Pluggable Authentication Modules) in Linux. We are going to reassess the background and inner workings of PAM and so additionally show examples on a live system on a way to piece PAM.
0 notes
Text
In this guide, we will cover the steps to install Webmin on Ubuntu 22.04|20.04|18.04 Linux distributions. Webmin is the leading open source web-based Linux/Unix system administration control panel. You can use Webmin to set up user accounts, manager Apache web server, DNS Server, samba and File configuration, email servers, package management, manage database servers e.t.c. Install Webmin on Ubuntu 22.04|20.04|18.04 We will install Webmin on Ubuntu 22.04|20.04|18.04 using the APT repository. Install required dependencies: sudo apt update sudo apt install vim apt-transport-https curl wget software-properties-common Once the repository is added, import GPG key used to sign packages in the repository: wget https://download.webmin.com/jcameron-key.asc cat jcameron-key.asc | gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/jcameron-key.gpg >/dev/null Add Webmin repository to Ubuntu22.04|20.04|18.04: sudo add-apt-repository "deb https://download.webmin.com/download/repository sarge contrib" Then update system and install Webmin package: sudo apt update sudo apt install webmin If the installation goes well, you should get output similar to below: Use 'sudo apt autoremove' to remove them. The following additional packages will be installed: libauthen-pam-perl libio-pty-perl The following NEW packages will be installed: libauthen-pam-perl libio-pty-perl webmin 0 upgraded, 3 newly installed, 0 to remove and 109 not upgraded. Need to get 28.7 MB of archives. After this operation, 306 MB of additional disk space will be used. Do you want to continue? [Y/n] y If you have an active UFW firewall service, allow port 10000: sudo ufw allow 10000 Access Webmin Interface Now that you have installed Webmin on Ubuntu22.04|20.04|18.04, open your server URL/IP address port 10000, e.g https://192.168.17.51:10000 Login with your server privileged user account to start administering your system from a web interface. Example of Webmin Modules: BIND DNS Server: Create and edit domains, DNS records, BIND options and views BSD Firewall : Configure a BSD firewall using IPFW, by creating and editing rules DHCP Server: Manage shared networks, subnets, hosts, and groups for ISC DHCPD CD Burner: Burn data CDs from ISO images or selected directories File Manager : View, edit and change permissions on files and directories on your system with a Windows-like file manager Dovecot IMAP/POP3 Server: Configure the Dovecot IMAP and POP3 mail retrieval server LDAP Server: Manage the OpenLDAP server and objects in its database All operating systems MySQL Database Server: Setup databases, tables, and permissions in your MySQL database server Linux RAID: Create RAID 0, 1, 4, 5, 6, 10 and linear devices on a Linux system SSL certificates: Let’s Encrypt SSL certificate requests IPsec VPN Configuration: Set up a client or server for an IPsec VPN using FreeSWAN Thanks for installing Webmin on Ubuntu 22.04|20.04|18.04 with our guide.
0 notes
Text
Learn Linux from scratch, and then learn how to get jobs in the field
Linux is 30 years old now, but is still so cool it went to Mars. So if you've always wished you could work in tech but didn't know where to start, you should definitely check out The 2022 Complete Linux Programming Certification Bundle because it lays out an entire career path from complete beginner to security expert. Best of all, there are even courses to help you actually get a job once you have the skills.
Total novices can start with "Linux Crash Course for Beginners (2022)" to learn how Linux works, how to use the command line efficiently, the basic Linux system administration and more. Then you can move right into networking in "Linux Network Administration" and become a Linux power user.
After you've got the fundamentals down, or if you already have Linux basics and want to move into security, "Guide to Security for Linux Systems" can teach you security measures for the Linux environment. This course can also help you pass the Redhat Certified Engineer exam (EX300), which should really make your resume stand out.
Courses on Pluggable Authentication Modules are rare, so "Linux PAM Administration" is truly valuable. It explains the importance of PAM, shows you live examples, demonstrates how to configure it and more. ซื้อฟรีสปิน
0 notes
Text
What is PRIVILEGED ACCESS MANAGEMENT (PAM)

What exactly is PAM?
Privileged Access Management (PAM) is an information security (infosec) system that protects identities with particular access or capabilities. PAM, like all other information security solutions, relies on a mix of people, processes, and technology.
Because of the risk they pose to the technical environment, we treat privileged accounts with extreme caution. For example, if the credentials of an administrator or service account fall into the wrong hands, the organization's systems and confidential data may be compromised.
What does it mean to have Privileged Access?
Privilege access is a term used in the technology world to describe accounts that have more power than regular users. In a Linux environment, for example, the root user can create, modify, and delete users, install and uninstall software, and access sections of the operating system that are forbidden to normal users. A similar security structure exists in Windows environments, however the root user is referred to as an administrator.
What is the importance of PAM?
Privileged Access Management is critical in every organization since privileged accounts are a major security risk. If a threat actor gains access to a regular user account, for example, they will only have access to that person's information. If they can compromise a privileged user, though, they will have significantly more access and, depending on the account, the capacity to damage systems.
Cybercriminals target privileged accounts because they can attack entire organizations rather than a single user because of their status and profile. With Forrester predicting that privileged accounts are involved in 80% of security breaches, safeguarding and monitoring these critical enterprise identities is critical. A PAM solution, for example, can address security flaws like many users accessing and knowing the same administrative password for a given service. It also reduces the danger of administrators not wanting to change long-standing static passwords for fear of causing an unforeseen outage.
0 notes
Text
Privileged Access Management (PAM) Solutions Market Research Report - Global Forecast to 2026
Privileged Access Management (PAM) Solutions Market Research Report - Global Forecast to 2026
Market Snapshot
According to MRFR analysis, the Global Privileged Access Management Solutions Market was valued at USD 1689.72 Million in 2019; it is expected to reach USD 12,067.50 Million by 2026, recording a CAGR of 32.67% during the forecast period, 2020–2026.
Regulatory compliance is enforced by several governments across the globe to ensure that business organizations follow and meet the standards applied to protect the sensitive information of consumers. For instance, the implementation of PAM solutions ensures compliance with GDPR and ISO/IEC 27001:2013 regulations. Some of these regulations include reinforcing the access to critical data, providing administrators with complete visibility over user actions, and helping define and enforce thorough security policies, records, and log activities of internal and external parties. Thus, the rising adoption due to government regulatory policies is expected to drive the global privileged access management solutions market during the forecast period.
With the increase in the number of internet users across the globe, there has been rapid growth in the number of cybercrimes in recent years. Additionally, the increasing number of smartphone owners and the availability of affordable mobile internet services have increased the number of unethical practices. The integration of IT services with cloud applications has been trending in businesses across several industrial verticals. Hackers are stealing valuable information stored in the organizations’ databases, with only a few security applications. For instance, the ransomware attack of the New Mexico County’s Government database, which resulted in an unknown number of electronic files and other important information being stolen. Thus, the increasing concerns over cyber threats are expected to drive the growth of the global privileged access management solutions market during the forecast period.
REQUEST FREE SAMPLE REPORT@ https://www.marketresearchfuture.com/sample_request/10231
Key Developments
In May 2020, CyberArk announced the acquisition of IDaptive Holdings, Inc., a leading service provider of identity as a service. Through this acquisition, CyberArk can deliver modern identity solutions to its clients.
In April 2020, Thycotic and a leading IT service management provider entered into a partnership to solve workflow approvals that are handled by IT teams who manage privileged service accounts.
In March 2020, BeyondTrust Corporation announced a strategic partnership with XMS Solutions, a technology leader in system integration services. This helped enhance its global presence and cater to customers with broad product offerings, including security solutions.
In March 2020, Thycotic expanded its presence in Canada and began delivering cloud-based PAM solutions through its data center in Canada.
Market Segmentation
By Type: Software, Physical Appliance, and Virtual Appliance
By Application: Windows, Unix & Linux, Mac OS, and Infrastructure Devices and IoT
Regional Analysis
Global Privileged Access Management (PAM) Solutions Market has been analyzed across key geographies, namely, North America, Europe, Asia-Pacific, the Middle East & Africa, and South America. North America dominates the privileged access management (PAM) solutions market, followed by Europe. However, Asia-Pacific is the fastest-growing economy in the privileged access management (PAM) solutions market due to the growing number of SMEs and the high focus of enterprises on boosting the security for accessing sensitive information. The Middle East & Africa and South America markets are witnessing a steady growth in the demand for privileged access management (PAM) solutions. These regions have very few country-level markets for cloud-based infrastructure.
GET COMPLETE REPORT@ https://www.marketresearchfuture.com/reports/privileged-access-management-solutions-market-10231
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR),Half-Cooked Research Reports (HCRR), Raw Research Reports (3R),Continuous-Feed Research (CFR), and Market Research & Consulting Services.
Contact:
Market Research Future
Office No. 524/528, Amanora Chambers
Magarpatta Road, Hadapsar
Pune – 411028
Maharashtra, India
+1 646 845 9312
Email: [email protected]
0 notes
Text
Privileged Access Management Solutions Market–Challenges, Key Vendors, Drivers, Trends and Forecast to 2026
Market Highlights
According to MRFR analysis, the Global Privileged Access Management Solutions Market was valued at USD 1689.72 Million in 2019; it is expected to reach USD 12,067.50 Million by 2026, recording a CAGR of 32.67% during the forecast period, 2020–2026.
Regulatory compliance is enforced by several governments across the globe to ensure that business organizations follow and meet the standards applied to protect the sensitive information of consumers. For instance, the implementation of PAM solutions ensures compliance with GDPR and ISO/IEC 27001:2013 regulations. Some of these regulations include reinforcing the access to critical data, providing administrators with complete visibility over user actions, and helping define and enforce thorough security policies, records, and log activities of internal and external parties. Thus, the rising adoption due to government regulatory policies is expected to drive the global privileged access management solutions market during the forecast period.
Get Free Sample Copy Report of Virtual Fitness @ https://www.marketresearchfuture.com/sample_request/10231
Global Privileged Access Management (PAM) Solutions Market Segmentation
Global Privileged Access Management (PAM) Solutions Market has been segmented based on Type, Application, and Region.
Based on type, the global privileged access management (PAM) solutions market has been segmented into software, physical appliance, and virtual appliance. Among these, in 2019, the software segment accounted for the largest market share of 41.12%, with a market value of USD 694.77 million. The virtual appliance segment is projected to record the highest CAGR of 34.90% during the forecast period.
Based on application, the privileged access management (PAM) solutions market has been segmented into Windows, Unix & Linux, Mac OS, and infrastructure devices and IoT. Among these, in 2019, the Windows segment accounted for the largest market share of 37.57%. The infrastructure devices and IoT segment are projected to register the highest CAGR of 34.89% during the forecast period.
Prominent Players
Some of the Prominent Players in the Global Privileged Access Management (PAM) Solutions Market are CA Technologies, Wallix, CyberArk, Centrify, ManageEngine, ARCON, Hitachi ID Systems, Beyond Trust, Thycotic, Devolutions, and One Identity LLC.
Access Report Details @ https://www.marketresearchfuture.com/reports/privileged-access-management-solutions-market-10231
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Edibles. MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions. In order to stay updated with technology and work process of the industry, MRFR often plans & conducts meet with the industry experts and industrial visits for its research analyst members.
Contact: Market Research Future 528, Amanora Chambers, Magarpatta Road, Hadapsar Pune – 411028, Maharashtra, India Email: [email protected]
0 notes
Text
Linux Diagnostics And Troubleshooting

Linux Diagnostics And Troubleshooting. This course is aimed at senior system administrators who wish to learn more about troubleshooting.
Overview
The Red Hat Enterprise Linux Diagnostics and Troubleshooting course (RH342) provides system administrators with the tools and techniques they need to successfully diagnose, and fix, a variety of potential issues. Students will work through hands-on problems in various subsystems to diagnose and fix common issues.
Audience
The Red Hat Enterprise Linux Diagnostics and Troubleshooting course is aimed at senior system administrators who wish to learn more about troubleshooting.
Prerequisites
Have earned a Red Hat Certified System Administrator (RHCSA) or have similar experienceIt is recommend that students have earned a Red Hat Certified Engineer (RHCE) or have similar experience Skill level: Intermediate Level Students: 398 Languages: EnglishCaptions: No Lectures: 81 Video: 10 hours
Introduction
What is troubleshooting?Troubleshooting a login issueCollecting InformationSystem JournalTroubleshoot a web server issue using the log filesUsing Red Hat ResourcesCollecting Information with SOSREPORTPractice Lab SessionTroubleshoot a FTP Connectivity Issue
Monitoring Systems
System Monitoring with CockpitPerformance Co-Pilot or pcpCentralized log server using rsyslogPractice Lab SessionIntrusion detection software to monitor changesAdvanced Intrusion Detection Environment (AIDE)Practice Lab SessionSystem Auditing with auditd
Identifying Hardware Issues
Identify various harwdare and their problemsHardware Error Reporting using mcelog and rasdaemonMemory Testing using memtest86+ packageManging Kernel ModulesLoading and unloading modulesManaging module optionsTroubleshooting to disable MSI-X interrupt handling in the driver
Troubleshooting Storage Issues
Overview of Linux Storage StackVirtual File SystemFilesystems & Device ManagerDevice Mapper MultipathRecovering from File System CorruptionChecking & Repairing ext3/ext4 fs using e2fsckChecking & Repairing xfs fs using xfs_repairRecovering LVM IssuesPractice Lab Session - using vgcfgrestoreMigrating a Volume Group from one system to anotherRecovering Metadata in LVMPractice Lab SessionConfiguration of Iscsi target & InitiatorPractice Lab Session on iscsi target & initiator - 1Practice Lab Session on iscsi target & initiator - 2 Troubleshooting RPM Issues Resolve package management dependency issuesIdentify & fix dependency issueRecover a corrupted RPM DatabaseWorking with transaction history using Yum commandReverting & repeating transaction using yum commandPractice Lab Session Troubleshooting a Network Issues Check Network ConnectivityScanning Network Ports using nmapCommunicating with a remote service using nc commandMonitoring Network traffic using iptraf-ngTroubleshooting a network issue (One network interface is not working properly)Troubleshooting tips related with device names of ethernet interfaceDisable consistent network device namingOverview NetworkManagerPractice Lab SessionCapturing Packets with tcpdumpPractice Lab Sessions Troubleshooting a Boot Issues Linux Boot processBooting of RHEL 7 with systemdOverview of Grub2Grub2 featuresBooting into Grub MenuProtect Grub by appying a passwordLab on Basic System Recovery (Initramfs file missing/Corrupted)Lab on Basic System Recovery (Grub related issues like grub is missing)Lab on Basic System Recovery (Master Boot Record missing/corrupted)Rescue Modue in RHEL 7Practice Lab SessionReset the root passwd using installation diskReset the root passwd using rd.break Troubleshooting a Security Issues Troubleshooting a SELinux IssueChanging SELinux contexttroubleshooting ftp connectivity issue using booleansSELinux Audit Logs & TroubleshootingOverview of PAM SecurityConcepts of PAMPAM Modules & ConfigurationsPAM Module GroupsControl Flags in PAMPAM Moduleslast lecture What you’ll learn Linux Diagnostics And TroubleshootingTo fix common issues on a Red Hat Enterprise Linux machine, using tools provided by the distribution.What is troubleshooting?Troubleshooting a login issueTroubleshoot a web server issue using the log filesTroubleshoot a FTP Connectivity IssueSystem Monitoring with CockpitCentralized log server using rsyslogAdvanced Intrusion Detection Environment (AIDE)System Auditing with auditdIdentify various harwdare and their problemsHardware Error Reporting using mcelog and rasdaemonManging Kernel ModulesTroubleshooting to disable MSI-X interrupt handling in the driverTroubleshooting Storage IssuesOverview about Filesystems, Device Manager & Device Mapper MultipathRecovering from File System CorruptionMigrating a Volume Group from one system to anotherConfiguration of Iscsi target & InitiatorTroubleshooting RPM IssuesRecover a corrupted RPM DatabaseWorking with transaction history using Yum commandTroubleshooting a Network IssuesScanning Network Ports using nmapnc & iptraf-ng commandsTroubleshooting a network issue (One network interface is not working properly)Troubleshooting a Boot IssuesLab on Basic System RecoveryReset the root passwd using installation disk or rd breakTroubleshooting a Security IssuesTroubleshooting a SELinux IssueSELinux Audit Logs & TroubleshootingOverview of PAM Security & Concepts of PAMVarious practice lab session Are there any course requirements or prerequisites? PC or Laptop with internet ConnectionA RHCSA/RHCE certification, or equivalent knowledge is required to successfully sit this course. Who this course is for: Linux Diagnostics and Troubleshooting course is aimed at senior system administrators who wish to learn more about troubleshooting. Read the full article
0 notes
Photo

Learn Linux PAM Administration with Certificate | Easyshiksha
This Linux PAM Administration course will introduce the PAM (Pluggable Authentication Modules) in Linux. We are going to reassess the background and inner workings of PAM and so additionally show examples on a live system on a way to piece PAM.
0 notes
Text
Using 7 Mysql Strategies Like The Pros
MySQL gives you Let to host lots of databases and it is named by you. Using MySQL and PHPMyAdmin ( my favorite management GUI ) has enabled me to insource numerous solutions we used to cover.
MySql is a database application of It is FREE on media and small scales business, it is supported on systems that were considered. Since 2009 Oracle buy Sun Microsystems ( such as MySQL ) to get 7.5 billons inducing user and programmers to start to debate the fate of their open - source database.
Almost any operating system and is operated in by mySQL Includes a controlled rate that is good I think it's the database manager together with all the rate of reaction to the procedures. Subqueries were one of the significant flaws of MySQL for quite a very long time; it had been notorious for dropping its way using a few degrees of sub-questions.
With MySQL, on the other hand, the Customer library is GPL, and that means you need to pay a commercial charge to Oracle or provide the source code of your program.PostgreSQL additionally supports data about data types, purposes and access methods from the system catalogs together with the typical information regarding databases, tables, and columns which relational databases maintain.

There are ways around the MySQL client library's licensing, the Route Atlassian decide to choose would be telling you where to get the JDBC connector out of for MySQL if you would like to join your Atlassian programs to a MySQL 38, and in which to drop the jar.
Seasoned staff if You'd like competently Accessible on-call assistance without paying serious cash ( DB2 or Oracle - degree paying ) Percona ( and MySQL ) is the friend. Matt Aslett of 451 Research unites ScaleBase to talk: scaling - outside of your MySQL DB, high availability strategies that are fresh, smartly managing a MySQL environment that is dispersed.
Conclusion Scalability is a matter of a theoretical Number of nodes It is also about the capacity to provide predictable performance And also to do this without adding management sophistication, proliferation of cloud, and geo-dispersed programs are adding to the sophistication MySQL hasn't been under so much strain that the mixture of innovative clustering/load balancing and management technology provides a possible solution ( c ) 2013 from The 451 Group.
Flexibility: no need to oversupply Online data Redistribution No downtime Read / Write dividing Optimal for scaling read - intensive software Replication lag - established routing Enhances data consistency and isolation Read stickiness following writes Ensure consistent and dispersed database functioning 100% compatible MySQL proxy Software unmodified Standard MySQL interfaces and tools MySQL databases unmodified Info is protected within MySQL InnoDB / MyISAM / etc.
The dilemma is solved by database encryption, but Once the root accounts are compromised, it can't prevent access. You get rid of the ability of SQL, although application level encryption has become easily the most flexible and protected - it is pretty difficult to use columns in WHERE or JOIN clauses.
It is possible to incorporate with Hashicorp Vault server through A keyring_vault plugin, fitting ( and even expanding - binary log encryption ) the features available in Oracle's MySQL Enterprise version. Whichever MySQL taste you use, so long as it's a current version, you'd have choices to apply data at rest encryption through the database server, so ensuring your information is also secured.
Includes storage - engine frame that System administrators to configure the MySQL database for performance. Whether your system is Microsoft Linux, Macintosh or UNIX, MySQL is a solution that is comprehensive with self - handling features that automate all from configuration and space expansion to database management and information design.
By migrating database programs that are current to MySQL, businesses are currently enjoying substantial cost savings on jobs that are brand new. MySQL is an open source, multi-threaded, relational database management system ( RDBMS ) written in C and C++.
The server is Acceptable for assignment - Critical, heavy - load production systems in addition to for embedding into mass installed applications. MySQL is interactive and straightforward to use, in comparison to other DBMS applications and is protected with a data protection layer providing information with encryption.
MariaDB is a general - purpose DBMS engineered with extensible Structure to support a wide group of use cases through pluggable storage engines.MySQL users may get tens of thousands of metrics in the database, and so this guide we will concentrate on a small number of important metrics that will let you obtain real-time insight into your database wellbeing and functionality.
Users have a number of options for monitoring Latency, by taking advantage of MySQL's both built-in metrics and from querying the operation schema. The default storage engine, InnoDB of MySQL, utilizes an area of memory known as the buffer pool to indexes and tables.
Since program databases -- and information warehouses -- are Constructed on SQL databases, also because MySQL is among the most well-known flavors of SQL, we compiled a listing of the highest MySQL ETL tools that will assist you to transfer data in and from MySQL database programs. KETL is XML - based and operates with MySQL to develop and deploy complex ETL conversion projects which require scheduling.
Blendo's ETL - as - a - service product makes it Simple to get data From several data sources such as S3 buckets, CSVs, and also a massive selection of third - party information sources such as Google Analytics, MailChimp, Salesforce and many others.
In we, Seravo Migrated all our databases from MySQL into MariaDB in late 2013 and through 2014 we also migrated our client's systems to utilize MariaDB. Dynamic column service ( MariaDB just ) is interesting since it allows for NoSQL form performance, and thus a single database port may offer both SQL and" not just SQL" for varied software project requirements.
MariaDB as the Number of storage motors and in excels Other plugins it ships together: Link and Cassandra storage motors for NoSQL backends or rolling migrations from legacy databases, Spider such as sharding, TokuDB with fractal indexes, etc.
MySQL is a relational database - Standard information schema also is composed of columns, tables, views, procedures, triggers, cursors, etc. MariaDB, therefore, has exactly the database structure and indicator and, on the other hand, is a branch of MySQL. Everything -- from the information, table definitions, constructions, and APIs -- stays identical when updating from MySQL into MariaDB.
MariaDB has experienced an increase in terms of Security features such as internal password and security management, PAM and LDAP authentication, Kerberos, user functions, and robust encryption within tablespaces, logs, and tables. MySQL can not do hash link or sort merge join - it merely can perform nested loops method that demands a lot of index lookups which might be arbitrary.
In MySQL single question runs as only ribbon ( with exception Of MySQL Cluster ) and MySQL problems IO requests one for question implementation, so if only query execution time is the concern many hard drives and the large variety of CPUs won't help.
With table layout and application design, you Can build programs working with huge data collections according to MySQL.OPTIMIZE assists for specific issues - ie it types indexes themselves and removers row fragmentation ( all for MyISAM tables ).
Even though it's Booted up to 8 TB, MySQL can't operate effectively with a large database. Mysql continues to be my favorite database because I started programming, so it's simple to install, it is easy to obtain an application that links to the database and perform the management in a graphical manner, many articles supervisors and e-commerce stores utilize MySQL by default, and it has let me execute many projects, I enjoy that many hosting providers have MySQL tutorial service at no extra price.
Mysql is fast the setup, and light requirements Are minimal and with few tools, I've used it in Windows and Linux with no difficulty in either, but the server operating system hasn't been a restriction and that I utilize it in a Linux environment whenever it is potential.
MySQL provides its code Beneath the GPL and gives the choice of Non - GPL commercial supply in the kind of MySQL Enterprise. MariaDB also supplies motor - separate table numbers to enhance the optimizer's functionality, speeding up query processing and data evaluation on the dimensions and arrangement of their tables.
Utilization in MySQL is sub - InnoDB and Optimum tables eventually become fragmented over time, undermining functionality. Shifting from MySQL into MariaDB is relatively simple and is a slice of cake for most systems administrators.
For program, Example Hosts ( even though they need to be okay with attaining MySQL via proxies ), the proxy layer, and perhaps a management host. You ought to check of the logs and settings files and confirm that they're not readable by others.
Data may be moved between MySQL servers, For instance via MySQL replication that is regular or inside a Galera cluster. Flexibility is incorporating the features your company needs, although pushing arbitrary JSON seems elastic.
Among those enterprise qualities, Informix relational Databases, recently launched a new variant ( v12.10. XC2 ) which supports JSON / BSON info as a native from inside the relational database frame and fully supports each the MongoDB APIs so that any program is composed to the MongoDB, protocol may just be pointed in the Informix server and it'll just work.
On top of the IBM Engineers ( Informix Is currently an IBM product ) extended the JSON kind to encourage files Up to 2 GB in size ( MongoDB limitations files to 16 MB). In MySQL and Oracle, working memory Is shared links because links Are serviced by a single procedure.
Noted Also :⇒ Use Of Quit SEO In 5 Days
0 notes
Text
New User Creation / Add new user

Create a new user in Linux
Table of Contents: Adding new user Changing Password User Login Switch User Granting Admin Privileges User Aliases Reloading Aliases Testing Conclusion >Adding new user:Creating new user with the name "testuser" shown as below. # useradd testuser

> Changing Password:Creating password for newly created user ( ie., testuser )# passwd testuserChanging password for user testuser. New UNIX password: # set passwordRetype new UNIX password: # confirmpasswd: all authentication tokens updated successfully.
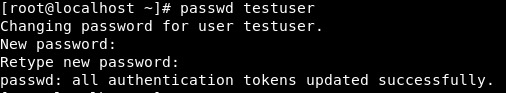
> User Login:Login with newly created user ( ie., testuser ). localhost login: testuser # Enter user-name .password: # Enter testuser password ( Password will not be display ) Then press Enter.

> Switch user:We can switch between users by using 'su' command. the below example is switch to root user.su - l $ su -l root # switch user to root , if we did not type any username then it will take root user by default . ie., we can login to root by using 'su - ' as well.Password: # Enter root password# # we have logged into root user. the '#' indicates that we are now using root user.

>Granting Administrative Privileges:Assigning administrative privileges to a user to execute root commands without switching to root user. ( ie., testuser ) # usermod -G wheel testuserEdit '/etc/pam.d/su' file. the file looks like as below.# vi /etc/pam.d/su#%PAM-1.0 auth sufficient pam_rootok.so # Uncomment the following line to implicitly trust users in the "wheel" group. #auth sufficient pam_wheel.so trust use_uid # Uncomment the following line to require a user to be in the "wheel" group. #auth required pam_wheel.so use_uid auth substack system-auth auth include postlogin account sufficient pam_succeed_if.so uid = 0 use_uid quiet account include system-auth password include system-auth session include system-auth session include postlogin session optional pam_xauth.so

Un Comment the below lines from the file."auth sufficient pam_wheel.so trust use_uid" "auth required pam_wheel.so use_uid"The file will be looks like below.# vi /etc/pam.d/su#%PAM-1.0 auth sufficient pam_rootok.so # Uncomment the following line to implicitly trust users in the "wheel" group. auth sufficient pam_wheel.so trust use_uid # Uncomment the following line to require a user to be in the "wheel" group. auth required pam_wheel.so use_uid auth substack system-auth auth include postlogin account sufficient pam_succeed_if.so uid = 0 use_uid quiet account include system-auth password include system-auth session include system-auth session include postlogin session optional pam_xauth.so

> User aliases: Creating an alias for the root user and forwarding all root user emails another user. ( ie., testuser ) # vi /etc/aliasesuncomment the last line and enter the username as shown below.root: testuser

> Reloading aliases: # newaliases

> Testing:Try to login to root user from testuser. in general, it should ask for the password. but testuser having root privileges so that we can login without entering any password like a root user.$ su -l root #

> Conclusion:We have learned user creation, password creation, User login, Switching user using 'su' command, Assigning administrative privileges to a normal user in this article and tested successfully.Any questions please make a comment.Thankyou Read the full article
0 notes
Text
PAM Mastery - Michael W. Lucas
PAM Mastery Michael W. Lucas Genre: Operating Systems Price: $9.99 Publish Date: September 19, 2016 Publisher: Tilted Windmill Press Seller: Tilted Windmill Press LLC Pluggable Authentication Modules: Threat or Menace? PAM is one of the most misunderstood parts of systems administration. Many sysadmins live with authentication problems rather than risk making them worse. PAM’s very nature makes it unlike any other Unix access control system. If you have PAM misery or PAM mysteries, you need PAM Mastery! With PAM Mastery, you’ll understand: the different versions of PAM the intricacies of Linux-PAM and OpenPAM how PAM policies make decisions how to debug PAM the most frequently seen PAM modules Linux-PAM extended controls and substacks time-based one-time passwords using SSH keys for more than SSH password quality testing policies from CentOS, Debian, and FreeBSD and more! Transform PAM from a headache to an ally with PAM Mastery! http://bit.ly/2EIFYG1
0 notes
Text
Privileged Identity Management Market 2019 Global Analysis with Focus on Opportunities, Development Strategy, Future Plans, Competitive Landscape and Trends by Forecast 2023 | Corona-Virus Analysis
Market Highlights
Privileged identity management (PIM) is the process to monitor top-level user accounts in an organization. These top-level users include CIOs, CEOs, and database administrators who have access to the organization's most sensitive information. In such condition where vulnerabilities of numerous systems are exposed which is a major identity management security issue.
Implementation of PIM ensures efficient management of those top-level users, creating a policy that specifies how top-level user accounts should be managed and their access reach. In PIM, these privileged accounts are also regularly audited. This policy-based centralization of user identity management is also known as identity governance.
PIM supports IT security and helps maintain regulatory compliance and thus, allows organizations orchestrate, reviewing the policy with compliance regulations by auditing user access. Resultantly, implementations of the privileged identity management are increasing across growing verticals such as government & defense, healthcare, manufacturing, energy & utilities, it & telecommunication, and retail, among others. It has been noted that enterprises face serious threats when privileged account users share their privileged identity with another person, which in turn, leads to easy access to critical applications. This situation gives rise to need for advanced user activity monitoring solutions in enterprises, such as privileged identity management system. This system helps these companies to record all activities, identify any suspicious activity and take appropriate action to mitigate risks. MRFR’s report identifies the accelerating cases of insider threats to be one of the main drivers for the global privileged identity management market growth till 2023. Also, these cases have motivated many vendors to provide a facility where enterprises can limit the access to Active Directories, and Linux, Windows, and UNIX systems.
Acknowledging the vast accruals, the market is garnering currently, Market Research Future (MRFR) asserts that the global privileged identity management market would reach approximately USD 6,200 MN by 2023, registering a whopping 32% CAGR throughout the assessment period (2017 and 2023).
Factors bolstering the growth of the market include increased cyber-attacks and malware and increased adoption of bringing your own device (BYOD) policies in enterprises. The wide adoption of this technology to ensure security is a key driving force behind the growth of the privileged identity management market. Augmented demand for PIM across government sectors (eGovernance usages) is boosting the market growth.
Factors such as spurting digitization, usage of the internet, and the trend of digital database management systems, fuel the growth of the privileged identity management market. Rising security concerns in banking activities are one of the key growth propellers.
Despite ensuring a broad uptake, privileged identity management still lacks substantial technological breakthroughs which are highly dependent on the skills of technicians. This acts as a major drawback restricting the growth of the market. However, the expected technological advancements in the recent future would give some relief promising a good fortune for the global privileged identity management market.
Get a Free Sample @ https://www.marketresearchfuture.com/sample_request/3233
Segmentation:
For a better understanding, the report has been segmented into seven key dynamics:
By Solution: Identity Management, Access Management, And Session Monitoring & Management, among others.
By Service: Professional Services, Implementation and Integration, Consulting, Education & Training, Support and maintenance, and Managed Services, among others.
By Installation Type: Agent-based and Appliance based
By Deployment Type: Cloud and On-Premise.
By Organization Size: Small & Medium Enterprises and Large enterprises.
By Vertical: Government & Defense, Healthcare, Manufacturing, Energy & Utilities, IT & Telecommunication, and Retail, among others.
By Regions: Asia Pacific, North America, Europe, and the Rest-of-the-World.
Regional Analysis:
The global privileged identity management market share is geographically segmented on the basis of Asia Pacific, North America, Europe and Rest of the World.
Among all regions, North America region is anticipated to account for the largest market share owing to elevated adoption of bring your own device (BYOD) technology and growing malicious attacks on sensitive information. Moreover, there is an increased adoption of solution such as session monitoring and management and identity management in order to curb such threats in several enterprises across the region.
Asia-Pacific region, on the other hand, is estimated to grow at the highest CAGR due to increasing information technology (IT) infrastructure and increasing cases of cyber-attacks. Furthermore, growing investments by government organizations in PIM solutions has led to the positive outlook of the market in the region.
The Europe market is exhibiting massive potential due to various mergers and acquisition and collaborations between market players. The companies are constantly indulging in various strategic activities along with technological innovations that enhance the product performance. These factors have led to increase in demand for PIM systems in a vast array of organizations in the region, wanting to make optimum use of the benefits offered by the system.
Global Privileged Identity Management Market – Competitive Analysis
Highly competitive, the privileged identity management market appears to be fragmented due to the presence of numerous well-established players. Innovation, mergers & acquisitions, and brand reinforcement remain the key trends for these players. The market will witness intensified competition with an increase in R&D innovations and M&A.
Major Players:
Players leading the global privileged identity management market include Balabit (Hungary), ARCON (India), BeyondTrust (US), CA, Inc. (US), Bomgar Corporation (US), Centrify (US), Cyberark (US), Core Security (US), Hitachi-ID (Canada), and IBM Corporation (US), among others.
Industry/ Innovation/ Related News:
June 26, 2019 --- Saviynt Inc. (the US), a leading company enabling enterprises to secure applications, data, and infrastructure in a single platform for cloud and enterprise, launched Cloud PAM to provide Privileged Access Management for cloud workloads and hybrid apps.
The new Cloud PAM is the latest addition to Saviynt’s core IGA platform that also offers Application Access Governance for critical applications and Cloud Security, seamlessly extending the power of intelligent identity to Privileged Access Management.
This unique SaaS offering enables organizations to govern and administer privileged access with integrated security analytics and segregation of duty violation verification, thereby allowing the enterprises to stay compliant.
Related Reports:
https://ehteshampeerzade.wixsite.com/website/post/vr-headsets-market-strategy-future-plans-competitive-landscape-and-trends-by-forecast-2022
https://ehteshampeerzade.wixsite.com/website/post/iot-platform-market-2018-global-expected-to-grow-at-cagr-of-28-5-and-forecast-to-2023-1
https://ehteshampeerzade.wixsite.com/website/post/mobile-application-market-growth-factors-and-global-industry-overlook-during-forecast-period
https://ehteshampeerzade.wixsite.com/website/post/iot-analytics-market-statistics-competitor-landscape-trends-and-forecasts-corona-virus-analysis
https://ehteshampeerzade.wixsite.com/website/post/enterprise-asset-management-market-gross-margin-research-report-and-trends-by-forecast-2022
https://ehteshampeerzade.wixsite.com/website/post/high-performance-data-analytics-hpda-market-gross-margin-and-competition-forecast-to-2022
0 notes
Text
Privileged Access Management (PAM) Solutions Market Research Report - Global Forecast to 2026
Privileged Access Management (PAM) Solutions Market Research Report - Global Forecast to 2026
Market Snapshot
According to MRFR analysis, the Global Privileged Access Management Solutions Market was valued at USD 1689.72 Million in 2019; it is expected to reach USD 12,067.50 Million by 2026, recording a CAGR of 32.67% during the forecast period, 2020–2026.
Regulatory compliance is enforced by several governments across the globe to ensure that business organizations follow and meet the standards applied to protect the sensitive information of consumers. For instance, the implementation of PAM solutions ensures compliance with GDPR and ISO/IEC 27001:2013 regulations. Some of these regulations include reinforcing the access to critical data, providing administrators with complete visibility over user actions, and helping define and enforce thorough security policies, records, and log activities of internal and external parties. Thus, the rising adoption due to government regulatory policies is expected to drive the global privileged access management solutions market during the forecast period.
With the increase in the number of internet users across the globe, there has been rapid growth in the number of cybercrimes in recent years. Additionally, the increasing number of smartphone owners and the availability of affordable mobile internet services have increased the number of unethical practices. The integration of IT services with cloud applications has been trending in businesses across several industrial verticals. Hackers are stealing valuable information stored in the organizations’ databases, with only a few security applications. For instance, the ransomware attack of the New Mexico County’s Government database, which resulted in an unknown number of electronic files and other important information being stolen. Thus, the increasing concerns over cyber threats are expected to drive the growth of the global privileged access management solutions market during the forecast period.
REQUEST FREE SAMPLE REPORT@ https://www.marketresearchfuture.com/sample_request/10231
Key Developments
In May 2020, CyberArk announced the acquisition of IDaptive Holdings, Inc., a leading service provider of identity as a service. Through this acquisition, CyberArk can deliver modern identity solutions to its clients.
In April 2020, Thycotic and a leading IT service management provider entered into a partnership to solve workflow approvals that are handled by IT teams who manage privileged service accounts.
In March 2020, BeyondTrust Corporation announced a strategic partnership with XMS Solutions, a technology leader in system integration services. This helped enhance its global presence and cater to customers with broad product offerings, including security solutions.
In March 2020, Thycotic expanded its presence in Canada and began delivering cloud-based PAM solutions through its data center in Canada.
Market Segmentation
By Type: Software, Physical Appliance, and Virtual Appliance
By Application: Windows, Unix & Linux, Mac OS, and Infrastructure Devices and IoT
Regional Analysis
Global Privileged Access Management (PAM) Solutions Market has been analyzed across key geographies, namely, North America, Europe, Asia-Pacific, the Middle East & Africa, and South America. North America dominates the privileged access management (PAM) solutions market, followed by Europe. However, Asia-Pacific is the fastest-growing economy in the privileged access management (PAM) solutions market due to the growing number of SMEs and the high focus of enterprises on boosting the security for accessing sensitive information. The Middle East & Africa and South America markets are witnessing a steady growth in the demand for privileged access management (PAM) solutions. These regions have very few country-level markets for cloud-based infrastructure.
GET COMPLETE REPORT@ https://www.marketresearchfuture.com/reports/privileged-access-management-solutions-market-10231
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR),Half-Cooked Research Reports (HCRR), Raw Research Reports (3R),Continuous-Feed Research (CFR), and Market Research & Consulting Services.
Contact:
Market Research Future
Office No. 524/528, Amanora Chambers
Magarpatta Road, Hadapsar
Pune – 411028
Maharashtra, India
+1 646 845 9312
Email: [email protected]
0 notes
Text
SECURITY FEATURES IN ICTCONTACT
Following are the security features provided by ICTContact :
Fail2Ban Fail2ban support is added for asterisk and ssh. It scans log files (e.g. /var/log/apache/error_log) and bans IPs that show the malicious signs such as too many password failures, seeking for exploits, etc . Generally Fail2Ban is then used to update firewall rules to reject the IP addresses for a specified amount of time. Contact Centre
Linux Operating System Linux is the most secure operating system as it offers the following security features: Contact Centre Software
ExecshieldExecShield is designed to prevent security breaches caused by software programs written to crawl through the Internet
SElinux (Security Enhanced Linux) is an implementation of a flexible mandatory access control architecture in the Linux operating system. Call Center Software
IPtables is used to set up, maintain, and inspect the tables of IP packet filter rules in the Linux kernel.
PAM (Pluggable Authentication Modules)Linux-PAM is a system of libraries that handle the authentication tasks of applications (services) on the system. Progressive Dialer
AuditThe 2.6 Linux kernel has the ability to log events such as system calls and file access. These logs can then be reviewed by the administrator to determine possible security breaches such as failed login attempts or a user failing to access system files.
Firewall A firewall is a network security system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented as both hardware and software, or a combination of both. Network firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet. Cloud Contact Center
Multi tenant This Multi tenant System provides full security of your data. Any other user can not access or manipulate data entered by Admin. Cloud Call Center
ICTContact software developed using standard security practices and it has fine grade permission and role system
ICTContact does not allow user sip accounts to make outbound calls themselves , only they can run campaigns through ICTContact interface with proper credentials and authentication
0 notes