#Ngrok
Explore tagged Tumblr posts
Text
If you're familiar with Ngrok, you'll know it allows secure tunnels to localhost. However, Localtonet offers a reliable Ngrok alternative with additional features. Localtonet provides easy setup and fast connectivity for developers needing HTTP reverse proxy services. Whether you're testing webhooks or accessing internal services, Localtonet can simplify your workflow. For anyone seeking a smooth, efficient, and secure connection, Localtonet stands as a strong contender. Plus, its affordable pricing makes it a practical choice for all developers. "Simplify your development with Localtonet – the secure alternative to Ngrok!"
0 notes
Text
Identifying the Best Development Tunnelling Tool: Ngrok vs. Localtunnel

Learning the power of Ngrok and Localtunnel will help you decide which platform to settle on when beginning your development path. Read More. https://www.sify.com/iot/identifying-the-best-development-tunnelling-tool-ngrok-vs-localtunnel/
0 notes
Link
看看網頁版全文 ⇨ Linux上讓Ngrok在背景執行 / Run Ngrok in Linux Background https://blog.pulipuli.info/2023/05/blog-post_27.html 改用「ngrok http 80 --log=stdout > /tmp/ngrok.log &」即可。 ---- # ngrok ngrok是一種讓本來只能在本機端連線的連結埠,轉換成可供網際網路連線的網址。 ngrok跟上次介紹的Telebit用法類似,但是知名很多,除了免費版有連線數量上的限制之外,目前使用上相當穩定,是我要測試網站的第一選擇。 想知道更多類似的服務,參考「Exposing localhost to the public Internet」這篇文章。 ngrok之所以很適合用來測試網站,是因為它會顯示現在連線的記錄,讓你明確知道客戶端現在連到了那個網址。 這對偵錯來說非常方便。 但這時候我們也只能看著ngrok的畫面,不能離開修改其他檔案,這樣也是挺困擾的。 # 讓Ngrok在背景運作 / Run ngrok in background。 https://stackoverflow.com/a/59756304。 所幸ngrok有提供「--log=stdout」的輸出模式,Kirill Malakhov更進一步把它整理成輸出到特定檔案。 我參考了大家的寫法,整理成以下腳本: [Code...] 如此一來,在ngrok開始運作之後,腳本會先列出 /tmp/ngrok.log 裡面包含Ngrok提供網址的資訊,讓我們確定測試時使用的網址。 後續連線的記錄則會保存在 /tmp/ngrok.log 之中,有需要的時候再 tail /tmp/ngrok.log 即可。 如果要讓ngrok停止,可以輸入以下指令:。 [Code...] # 腳本下載 / Download script。 為了方便大家使用,上述腳本可在以下網址下載:。 - https://pulipulichen.github.io/blog-pulipuli-info-data-2020-2025/23/05/ngrok.sh - https://ppt.cc/fWvyXx 下載後記得要給它執行權限。 在Linux指令列可以用以下指令下載,並且設定執行權限:。 [Code...] ---- 最後要來問的是,你有架設過伺服器嗎? 有架設過的朋友請再下面舉個手吧~ ---- 看看網頁版全文 ⇨ Linux上讓Ngrok在背景執行 / Run Ngrok in Linux Background https://blog.pulipuli.info/2023/05/blog-post_27.html
0 notes
Text
Akira Ransomware Breaches Over 250 Global Entities, Rakes in $42 Million
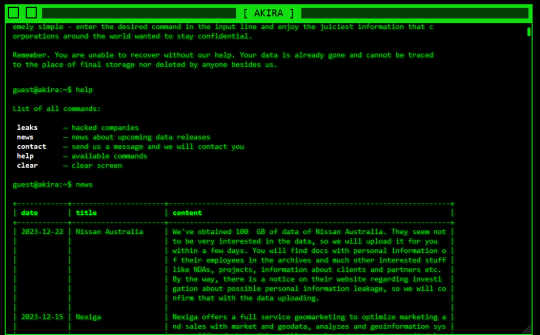
A joint cybersecurity advisory issued by CISA, FBI, Europol, and the Dutch NCSC-NL has uncovered the staggering scale of the Akira ransomware campaign. Since early 2023, the nefarious Akira operators have compromised more than 250 organizations worldwide, extorting a whopping $42 million in ransom payments. Akira's Prolific Targeting Across Industries The Akira ransomware group has been actively infiltrating entities across diverse sectors, including education, finance, and real estate. Staying true to the double extortion playbook, the threat actors exfiltrate sensitive data before encrypting the victims' systems, amplifying the pressure for a ransom payment. Early Akira versions, coded in C++, appended the .akira extension to encrypted files. However, from August 2023 onward, certain attacks deployed Megazord, a Rust-based variant that encrypts data with the .powerranges extension. Investigations reveal the perpetrators interchangeably using both Akira and Megazord, including the updated Akira_v2. Initial Access and Privilege Escalation The cybercriminals exploit various entry points, such as unprotected VPNs, Cisco vulnerabilities (CVE-2020-3259 and CVE-2023-20269), RDP exposures, spear phishing, and stolen credentials. Post-compromise, they create rogue domain accounts, like itadm, to elevate privileges, leveraging techniques like Kerberoasting and credential scraping with Mimikatz and LaZagne. Disabling Security Controls and Lateral Movement To evade detection and facilitate lateral movement, Akira operators disable security software using tools like PowerTool to terminate antivirus processes and exploit vulnerabilities. They employ various tools for reconnaissance, data exfiltration (FileZilla, WinRAR, WinSCP, RClone), and C2 communication (AnyDesk, Cloudflare Tunnel, RustDesk, Ngrok). Sophisticated Encryption The advisory highlights Akira's "sophisticated hybrid encryption scheme" combining ChaCha20 stream cipher with RSA public-key cryptography for efficient and secure encryption tailored to file types and sizes. As the Akira ransomware campaign continues to wreak havoc, the joint advisory provides crucial indicators of compromise (IoCs) to help organizations bolster their defenses against this formidable threat. Read the full article
2 notes
·
View notes
Text
Gophish Setup Guide: Launching Phishing Campaigns
Phishing Scenario : CASE 1 - Breaking news
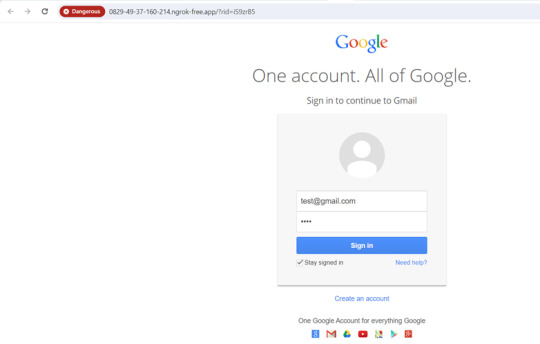
Objective: The objective of this phishing campaign is to lure employees into clicking a malicious link disguised as breaking news from the company. The landing page masqueraded as a Gmail sign-in page, prompting users to enter their login credentials. This page was designed to steal users' email account credentials.
Install Gophish framework
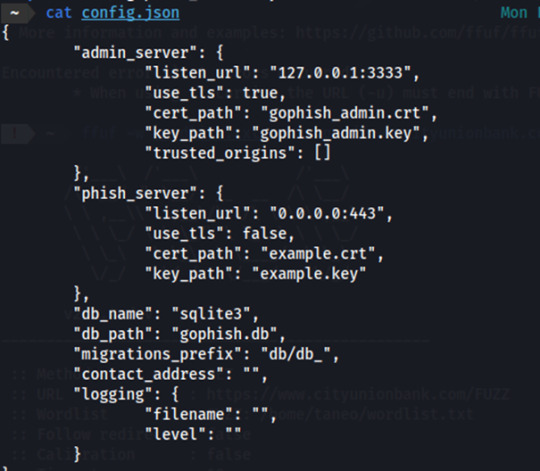
Make the required changes in the config.json file
Launch Gophish and our first step would be to set up the sending profile by which we will send out phishing emails.
Let’s assume that the target company is using Gmail server
(When setting up the sending profile in Gophish using a Gmail account, you have to enable 2FA and give app access to Gophish)
Since our target company is using Gmail server, we will use Gmail email on our phishing campaign so we have set host as smtp.gmail.com:587. After creating the sending profile, we have to test if the sending profile works by sending a test email.
We're using the email address [email protected] as our designated Gmail account for sending phishing emails. Make sure to include the password that was generated when granting Gophish access to this Gmail account. After configuring the sending profile, we can test it by sending a test mail.

This is what the test mail will look like:

Email Template
The next step involves integrating an email template for the phishing campaign. We can opt for a pre-made template, for example, here we use a Breaking News email template, for initial testing. We can incorporate a tracking image within the emails to monitor various engagement metrics, including email opens, clicks, and receipt statuses. It also has an option where we can add a link which will redirect the victim to the landing page. On the landing page we can proceed to request for more valuable information from the user.

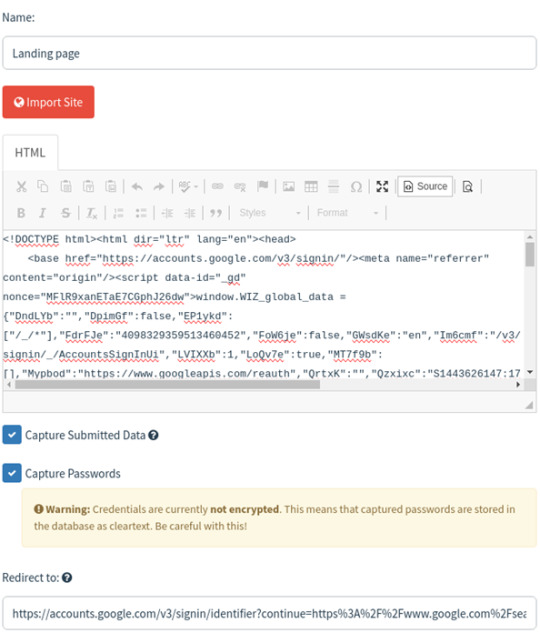
Landing Page
In the third step, set up a landing page where targets will be directed after clicking a link in the email. This landing page plays a crucial role in the phishing campaign, as it's where you can capture sensitive information like passwords. Gophish defaults to using http://0.0.0.0:80 for the landing page, but we can customize it to look like a legitimate login page or other enticing content to attract targets. We'll need to specify a redirect page where users will be sent after submitting their credentials.
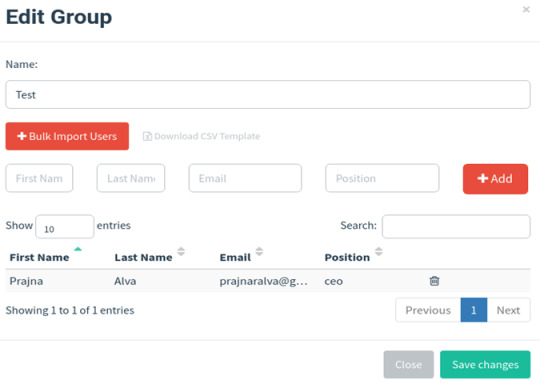
In the User & Groups section, you'll need to input the email addresses of your targets. Gophish framework requires you to provide the first name, last name, email address, and the rank of each target individual on the user groups page. You can also upload target details from a CSV file stored on your local system using import feature.
Install and set up Ngrok:
Install ngrok via Apt with the following command:
curl -s https://ngrok-agent.s3.amazonaws.com/ngrok.asc \
| sudo tee /etc/apt/trusted.gpg.d/ngrok.asc >/dev/null && echo "deb https://ngrok-agent.s3.amazonaws.com buster main" \
| sudo tee /etc/apt/sources.list.d/ngrok.list && sudo apt update && sudo apt install ngrok
Run the following command to add your authtoken to the default ngrok.yml configuration file.
ngrok config add-authtoken 2crm6P5lWlbTm4rwoGqn0QSHhPA_6nf7WmMJFKXVSD2SgBohF
Create an index.html page for the landing page and launch python http server in the port 8001
• python3 -m http.server 8001
Note: Verify in the browser if it's actually accessible.
We can also use other login page cloning techniques like built in gophish cloner, or Github projects (we used), Custom or by using third party clones (ex-goclone).
If it's a php file use the following command instead:
• php -S localhost:8001 -t .
Launch ngrok :
ngrok http http://localhost:8001/

Use the URL under forwarding and paste it on the Gophish URL section in the campaign page shown below:
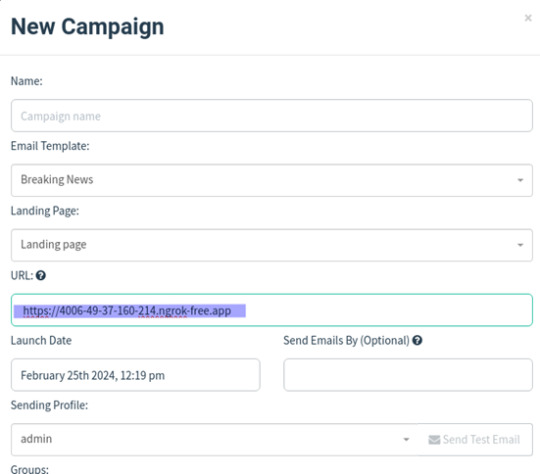
Creating Gophish Campaign:
Go to the Campaigns section.
Choose the right email and landing page templates.
Enter the landing page server URL.
Select the target group.
Start the campaign and monitor its progress.

Once we click on the link we are directed to the landing page, where we can enter our credentials.
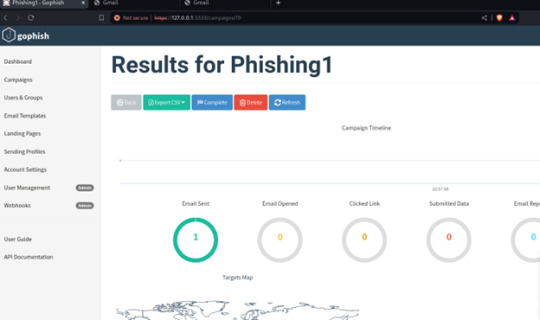
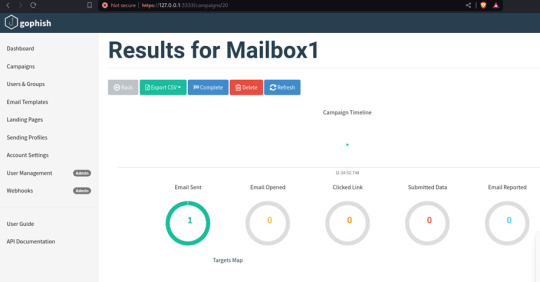
You can find all the phishing reports related to a specific campaign on the Dashboard in the Gophish framework. Here, you can see details such as sent emails, opened emails, clicked links, submitted data, and any emails reported as phishing by the targets. This page provides a comprehensive overview of the ongoing phishing campaign.
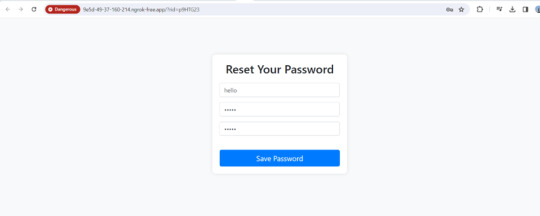
Phishing scenario: Case 2 - Password Reset Campaign
The aim of this phishing campaign is to trick users into divulging their login credentials by pretending to offer account protection in response to a fake mailbox compromise.

Users received an urgent email claiming their mailbox was compromised. They were directed to a phishing landing page disguised as a password reset portal.
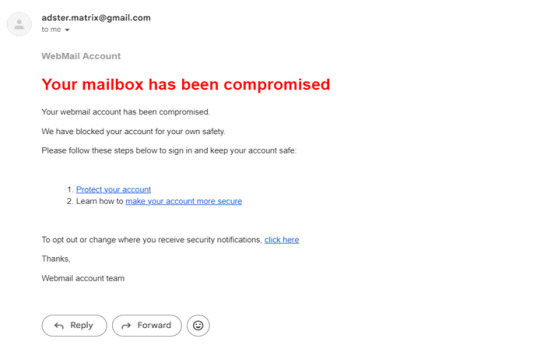
Upon clicking the link, Users were redirected to a fake password reset page resembling the email service provider's design, where they were prompted to enter their login credentials.
3 notes
·
View notes
Text
En Kolay Port Açma Yöntemi: Ngrok ile Ücretsiz Port Açma
Oyun sunucusu açma, bilgisayarınızdaki projeleri dışarıdan kullanılabilir hâle getirme ya da en basitinden bilgisayarınıza dışarıdan bağlanabilmek içi...#Genel #ngrok #ngrokalternatifleri #ngrokkomutları #ngrokkurulumu #ngroknasılkullanılır #ngrokportaçma #portyönlendirme #statikip #ücretsizportaçma
0 notes
Text
dev: Ngrok + open-webui + ollama
What a great setup, you can nearly duplicate all the stuff that requires the cloud on your local machine. While open-webui really likes using docker, I have to say that the overhead is pretty big particularly when all that is really going on is the need to isolate python environments. So instead of that I’ve been using the miracles of pipx install to accomplish all that and not have to lose all…
0 notes
Link
0 notes
Text
Looking for an Ngrok alternative? Localtonet offers all the features of Ngrok, plus more. With Localtonet, developers enjoy HTTP reverse proxy, mobile proxy, and 4G proxy services all under one roof. Its user-friendly interface and enhanced security options make it a practical alternative to Ngrok. Plus, Localtonet is more affordable and scalable, making it the perfect choice for businesses or individual developers who need seamless local-to-remote connections. "Step up your development game with Localtonet – the smart alternative to Ngrok."
0 notes
Text
----
Adding NGROK to #dotnet #aspire so you can develop against external services and webhooks is as easy as...
0 notes
Text
How we built ngrok's data platform
https://ngrok.com/blog-post/how-we-built-ngroks-data-platform
0 notes
Text
Tiny C# code to test webhooks with NGrok
TL;DR; Here is the github repo: https://github.com/infiniteloopltd/MiniServer/If you need to test webhooks, it can be sometimes awkward, since you have to deploy your webhook handling code to a server, and once there, you can’t debug it. Running it on localhost, then the remote service can’t reach it. This is where NGrok comes in handy, you can use it to expose (Temporarily) a local website –…

View On WordPress
0 notes
Text
DS3 Term Project Escape Room Update (#8)
This sprint, we finished our presentation slides for Beta and presented it. After Beta, we started to work on the rest of our game. I am currently working on the Rotary dial artifact.
Here is a screenshot of what I have got so far for it:
One of the challenges we ran into this week was circles taking a long time to load right before our presentation time. We tried to use a new ngrok account and it did not seem to help.
One of the successes was being able to solve the problem of circles taking too long to load by loading every room beforehand. That seemed to have cut down the amount of time it took enough to have it not slow down our presentation.
I spent 8 hours on this sprint.
I plan on spending 12 hours on the next sprint.
0 notes