#Norton installation error
Explore tagged Tumblr posts
Text
Suggestion on how to fix Doctor Who 15x6 - "The Interstellar Song Contest"
So, I think the core problem with the episode is just how two-dimensional and ill-conceived the writing is for the villain, 'Kid'. The way to fix this would be to basically rewrite him and reveal he isn't one, but have The Doctor still fall into the trap of assuming he is:
Phase 2 first The Doctor notices something odd about the air shield and goes exploring while Belinda continues watching the show. Meanwhile, Kid and Win take over the control room, uploading their code into the system and installing the Delta Wave. The Doctor meets Mike and Gary and Graham Norton in the history museum and eventually discovers the Hellian code that's taken control of the broadcast and the entire space station, triggering the deafening Delta Wave in the process. The Doctor fears the Hellians are going to transmit the wave out and kill trillions of viewers. Elsewhere, Mrs Flood tries to leave, but discovers the code is blocking off teleportation and stopping all exit or entry to the station. She heads for the control room to find out why.
Phase 1 Kid disables the air shield and the artificial 'mavity'. (Note, the bubble doesn't burst, he just seems to deactivate it). The Doctor watches helplessly from inside, as the crowd is sucked out into space, including Belinda and the TARDIS. (Note, as far as he can tell, they all just died and are gone. None of this 'oh, actually all 100,000 of them can still be saved, they're just in pseudo-cryogenic suspension' business). Understandably, The Doctor is grieving and on the warpath. He, Mike and Gary meet up with Cora and Len, who talk about the Hellians being terrorists and evil, despite the fact none of them have actually ever been to Hellia. Kid warns them over the intercom not to interfere and the Doctor threatens him. Cora reveals herself and explains the truth about Hellia, and her fear that Kid wants revenge. The Doctor does his hologram trick, but when Kid shoots at him, the blast passes through and hits Mrs Flood, seemingly killing her. Horrified, the Doctor destroys the Delta Wave device, and then begins torturing Kid. He does not realise the transmission is already locked in to broadcast at a specific point and can't be stopped now. Hellia Belinda wakes up disoriented on the barren plains of a desolate war-torn planet along with the other 100,000 people. She spots the TARDIS and makes her way through the crowd, who are confused, but mainly unharmed. With some trial and error, Belinda manages to get the TARDIS to return to the space station, and goes looking for the Doctor. A large projection screen activates above the crowd, showing the dress rehearsal being televised. Phase 3 The transmission begins, but it is not the Delta Wave being sent out. It is footage of Hellia before and after its destruction, with Kid's voice exposing proof of the Poppy Honey Corporation's crimes. Caught off guard, The Doctor stops torturing the genocide survivor, as Belinda comes through the door. Win explains that the plan was never to transmit the Delta Wave. They just needed it as a defense mechanism for the code to prevent anyone from interfering with their message going out. But knowing that even the footage wasn't enough to convince everyone watching, they also reconfigured the air shield to act as a giant teleport when the 'mavity' was turned off, thus sending 100,000 people to Hellia to see what had happened there with their own eyes, and hopefully spread the truth.
As Mike takes Kid to the hospital, Belinda confronts The Doctor about his actions, forcing him to admit his automatic assumptions about Kid being a terrorist out to kill everyone were aspersions he shouldn't have so readily accepted. Thinking The Doctor worked for Poppy Honey, Kid was willing to shoot him to stop any interference with the transmission, but any other threats were just him bluffing. With the message successfully transmitted, the regular broadcast is restored, but now shows Cora singing her song to an empty arena. The crowd watches in silence from the ruins of Hellia.
27 notes
·
View notes
Text
Before I begin, I’d like to apologize for missing the last couple days. Been pretty busy, and this post is the first of many detailed and [mostly] thorough rewrites, which has honestly taken me much longer than I anticipated.😅But anyway, here we go.
MCU Reimagined
Phase 1, pt 2
The Incredible Hulk. The reason I’ve chosen The Incredible Hulk for my second MCU film, is simply because I want to establish Marvel’s main 3 from the early 2000’s; Spider-Man, Hulk, and Wolverine. These were the three heroes that made up a large majority of Marvel’s marketing, so why not keep that running??
Now, in our main MCU Multiverse, we got 2 theatrical Hulk movies. Eric Bana’s Hulk from 2003, and Edward Norton’s The Incredible Hulk from 2008 (which was also the second installment in Feige’s MCU timeline). After that, Hulk has only ever showed up as a supporting role, from 2012’s The Avengers and beyond, and played by Mark Ruffalo. I plan to change that.
Now, there’s a lot that I liked about Eric Bana’s Hulk, and a lot more that I liked about Edward Norton’s. I really liked how they depicted that version of the Hulk. They did a great job at showing just how much of a beast he really is. He’s fast. He physically gets stronger the angrier he gets. And he’s literally a hulking beast. What I liked about Norton’s version, is the transformations. They really made just the IDEA of pissing Bruce Banner off a terrifying concept. They also did a good job at humanizing the Hulk, and I feel like Norton’s Hulk had more emotion. I also really liked the overall design they used for his Hulk, the emerald green eyes, the shade of green, all of it just looks perfect. But neither film alone, would I consider to be “perfect”.
Our version of The Incredible Hulk will draw inspiration from both of them, as well as set him up for a larger role than just a supporting role for future films. Now, as much as I liked the comic panel effects from the 2003 movie, I gotta admit…in hindsight, it’s a little bit too cringey, especially if we want audiences to take this new MCU seriously, so let’s go ahead and ditch those. We’re gonna keep the 2008 design and casting of Edward Norton here, because nothing against Ruffalo and his portrayal, but honestly, Edward Norton just looks more like how I’d imagine Bruce Banner looking. My only change in his character design would be the pants. I think Norton’s Hulk with purple pants would look great, except maybe not the super bright and vibrant pair that Betty tries offering him in the original movie:

Maybe something more like a washed dark, almost plum kind of purple, something like these:


That way, there’s enough shade to tell that they’re purple without looking completely and totally ridiculous.
Now, as for the story, obviously this will be an origin, but this time, it’s not going to revolve around the Super Soldier serum. I’m all for Easter eggs, references, and interconnectivity, and I’d definitely love to explore the global implications that the serum would have caused, but we don’t need to have our Hulks be a part of that. With that said, we open the movie to a dessert landscape. In the midst of the vast sandy ocean, sits a lone military base, where we find General Thaddeus “Thunderbolt” Ross overseeing tests for the military’s latest advanced weapons program…funded by Stark Industries, of course. Due to complications during the tests, however, they recruited Dr Bruce Banner, gamma expert and long time colleague/lover to Betty Ross (the General’s daughter), so they could safely handle the large amounts of gamma radiation that was being used in the production of these weapons.
Having completed his analysis and correcting the errors that were made, Banner’s role with the military is now finished, and they are quick to escort him off the base. As they’re driving him away, Banner notices something, off in the distance. A massive Multiple Rocket Launcher (MLR) that is being lifted seemingly out of the ground. And directly in its line of fire, a civilian dune buggy cruising by. Banner frantically tries to get the soldiers to call off the test sequence, but there’s nothing they can do. The radio signal doesn’t reach that far out from the base and they wouldn’t be able to get to him in time. Banner disagrees, though, as he wrestles the soldiers and pushes the two of them off the jeep.
Taking the wheel, Banner speeds towards the civilian, shouting, honking, doing everything he can to get the man’s attention. Finally, the civilian hears Dr Banner, but still unable to make out what he’s saying. He slows to a stop, staring curiously at Banner. He squints to see Bruce pointing out to the side, and follows his finger to find the missiles preparing to launch. The civilian is now frozen in fear of his seemingly pending doom, watching as the missiles begin their launch sequence. They fire, and time seems to slow down for the man. He stares into the sky, as the missiles rise higher, soaring closer and closer towards him. Suddenly, his gaze is interrupted as Dr Banner tackles him down to the ground.
Banner clambers back up to his feet, and practically drags the civilian behind him as he works to regain his footing.
As they run, Banner shouts at the man.
Banner: THERE’S A DITCH ABOUT 100 FEET AHEAD OF US!!! WE MIGHT JUST BE ABLE TO MAKE IT AND GET US AT LEAST SOME SORT OF COVER AND HOPEFULLY IT WILL BE ENOUGH FOR US TO SURVIVE THIS BLAST!!!
The two of them race to the ditch, running as fast as they possibly can. Just before they make it, the missiles blast the ground behind them, destroying the jeep and the dune buggy in a massive explosion of debris, dirt, and sand, creating a shockwave strong enough to fling Banner and the civilian over that final stretch and right into the ditch. Bruce then shielded the man as much as he could in an attempt to limit the man’s exposure to the gamma radiation.
Unfortunately for Bruce Banner, however, the blast changed him. As soon as it was over, Bruce Banner was gone, and in his place loomed…The Incredible Hulk. The man just did nothing but stare. Amazed, and grateful, yet terrified at this creature which used to be Bruce Banner, the man who had just saved his life. Then, a hoard of military vehicles approach the blast zone. The Hulk stands up, and pulls himself out of the ditch. Almost immediately, the troops begin attacking Hulk.
Hulk snarls, and leaps into the air, letting out a fierce, bellowing roar, leaving behind a small dent in the desert floor where he once stood. Everyone stops firing, as they all stare up at The Hulk, now a spec against the blistering sky, in disbelief that something so massive could leap so high. Suddenly, that spec starts to grow larger and greener as he comes crashing back down onto the convoy. The impact is so great that now, The Hulk stands in the center of a massive crater in the once flawless desert floor, tanks, jeeps, and soldiers flying seemingly weightlessly around him. The Hulk then charges at full speed towards the military base. Helicopters can be seen retreating as the base begins evacuations. But they are too late. It is only just as the 3rd helicopter begins its ascent that The Hulk grabs the chopper by its tail, and hammer throws it out and into the horizon.
The Hulk then leaps to the side of the base. He turns to face the 4th wall, and reaches out toward the audience. The audience’s screen then glitches out, and camera cuts to reveal that The Hulk had just destroyed one of the base’s security cameras. He turns back towards the base, and stomps over the garage door. The Hulk rips it free from its hinges and then crumples the door like it’s a sheet of paper, tossing it aside. He stoops to fit through the entry, as the camera lingers outside the base. All that is heard is gunshots, soldiers screaming, menacing grunts, and short roars as the inside of the base is torn apart, gunshots and human shouts becoming less and less frequent. Finally, there is a moment of silence as the camera slowly pans towards the front of the base, progressively zooming in closer.
Finally, another loud, bellowing roar escapes from The Hulk as he smashes through the front and leaps off frame. A distant voice over the radio can be heard from inside the base, as it says “Lee!? Lee, this is Ross, what’s your status?? LEE!?” And the camera fades to black, cuing the title reveal.
We cut back to the aftermath in the desert, where Banner had saved that man’s life. Several soldiers are lying dead, many more severely injured. As the medics continued to tend to the wounded and the FBI cleaned the mess, General Ross, who had escaped in the first of the helicopters, was off to the side, interrogating the man.
Ross: What’s your name, son?
Man: Rick. Rick Jones.
Ross: What in the hell were you doing way out here??? You realize this is a restricted area?? No civilians should be anywhere NEAR here!!!
Rick: It…it was a dare…sir.
Ross: A DARE!?!?! Are you out of your damn mind!!! You could have been killed! So you were DARED to trespass onto the testing grounds!?
Rick: Yes…yes sir. Yes sir, I was.
Ross: [Sighing] During the blast, what did you see?
Rick: Not much. Just that doctor that saved me, but…it all happened so fast…when the dust cleared, the doc was gone, but…that…that THING was standing exactly where the doc was…
Ross: What do you mean?
Rick: I think…I don’t know…just…the doc was there, but then he was gone, and the creature was in his place.
Ross: Well, now because of you, we have a rampaging beast on the loose and no idea where Dr Banner is! I hope you’re proud. [At another soldier] Take the kid home, we’ve got enough trouble on our plate.
Camera then cuts to a sky eye overview of an area isolated by civilization somewhere along the Colorado River. As the camera pans the landscape, we see a massive crater, not much different than the one left in the wake of the Hulk’s rampage at the base. The camera then cuts to the edge of the crater, in the far distance a silhouette of a man. The camera pans towards him, as we see massive footprints in the sand gradually getting smaller and smaller until they fit the size of a human. The camera catches up with the man, who turns out to be Dr Banner. His hair a mess, face pale and clammy, and he seems to have lost most of his clothes, save for the ripped and stretched pants he now struggles to keep from falling. He reaches the bank of the river, and collapses, a single thought seemingly evident through his face…What just happened? Finally, Banner passes out.
There’s a static shot of Banner’s face as he’s lying down, then after a beat, the shot immediately cuts to night and Banner wakes with a gasp. Regaining his senses, he realizes he’s no longer alone here. Next to him, a fresh pair of clothes sits folded. A plain white shirt and dark burgundy, almost plum colored pants.
Voice off frame: I hope those fit. But even if they don’t, they might be better than those pants you have on now…if you can even call them that anymore. [Suddenly, Banner realizes exactly who this person is. She sits across the way, glowing from the light of the fire she’s made, dressed in a tank top and jeans, with a red flannel shirt tied around her waist. Her glasses shine in the firelight, as she gazes at the river.] You’re lucky I found you, Bruce.
Bruce: Betty?
Betty: It’s been a while. What are you doing way out here? I thought you were helping my father with something?
Bruce: I…I’m not sure. They were experimenting with weapons using gamma, and needed me to help assess any probability for error and evaluate the gamma safety before they could test…soon as I was done, they went ahead and escorted me out. As we were driving off the base, though, there was this…this KID. Fresh out of high school, it seemed, and…he was driving out in the testing field. I tried telling the soldiers to call it off, but they wouldn’t even try to help. I ended up fighting them, and commandeered their jeep to help the kid. We were running towards a ditch not too far out to take cover, and then…everything was just a blur from there. I remember being…angry. Rage-full, even. I remember soldiers and helicopters, but that’s about it. And then next thing I knew, I was…here. What about you, what are you doing here? And…where exactly is here, anyway?
Betty: Near South Cove in Nevada. Roughly 20 miles east of Boulder City. I was on my way out here to conduct a study on the microbiological environment of the Colorado River. It’s going to be a part of my students’ lesson plan for next week. During my drive, though, I saw…well, I…how do I put this…Bruce, I saw YOU. But you weren’t….you. Get dressed. I need to show you something.
Bruce, clearly intrigued, gets up. Camera cuts to the crater, and Betty and Bruce are seen walking up to it.
Betty: Do you recognize this area at all?
Bruce: Not really, no.
Betty: This is where I found you…except…God, you’re going to think I’m crazy….you…you were huge. And I mean, HUGE. You were nearly 10 feet tall, and…and just this massive hulk of muscle…and…Bruce? Bruce, you were GREEN.
Bruce: Betty, I—
Betty: [interrupting] I KNOW how it sounds, Bruce, and I wouldn’t have believed it, either, but…I watched you turn back, Bruce. I watched your skin return to normal as you shrunk back down. I don’t know how it’s possible, but I SAW YOU, Bruce. I SAW you. And, if you need proof…look at the footprints.
Bruce: Betty. It’s ok. I believe you. I don’t know how it’s possible, either, but I believe you. We need to get to a lab. Run tests. Figure out what’s happened to me.
Betty: We will. But first…[kisses him deeply, then whispers] I’ve missed you, Bruce. It’s good to see you again.
Bruce: I’ve missed you, too.
The two walk back to the camp, and the screen fades to black.
From here, the two catch up, and they head back to Betty’s lab. Meanwhile, General Ross is obsessed with finding Banner, as new found evidence from the base has proven to show that Bruce Banner IS the Hulk. The General has tried several times to contact his daughter, Betty, to warn her about Banner, and to ensure that she stays away from him. Before, it was simply a matter of him not liking Bruce. He never liked him, and always thought that Betty settled for him when he knew she could do better. In fact, he was opposed to calling in Bruce to assist with the weapons test. He would have called in Betty, instead, knowing that she was just as knowledgeable in Gamma radiation as Banner, but they had spoken earlier about this trip she was taking, and knew she would be unavailable. But now, it was a matter of her own protection, and keeping The Hulk away from her. Hunting down and stopping The Hulk at all costs has now become priority number one.
Now, at this point, the 2008 movie showed Ross hunting down the Hulk, and used his military team as a bridge to connect Hulk to a secondary antagonist. Enter Emil Blonsky, aka, The Abomination. I like that they used the military hunting The Hulk to establish the connection between him and Abomination, but I have other plans for Blonsky. So we’re gonna put him on the back burner, and instead, we’re going to fill his original role with the character, Dirk Garthwaite.
For the most part, Garthwaite is going to be characterized similarly to how Blonsky was. Cocky, trigger happy, and “corrupted” essentially by his authoritative power. He will be leading Ross’s elite strike team, tasked with tracking down and eliminating The Hulk. With Garthwaite, comes two of his inseparable, ride or die, packaged deal soldiers, Henry Camp and Brian Calusky. Ross assigns the three of them a massive team with heavy weaponry, stealth gear, and anything else they might need to bring the Hulk down. Ross also assigns Eliot Franklin, a former Stark Industries employee who helped to pioneer the gamma-based weaponry that created the Hulk, to help the team track the Hulk’s gamma signature.
Throughout the remaining first half of the movie, Banner and Betty work to catch up, and discover how the Gamma radiation affected him and his DNA, all the while, being interrupted by Garthwaite and his team, and having to fight them off.
To start off the 3rd and final act, Garthwaite and his men have suffered yet another loss against the Hulk. Garthwaite decides that desperate times call for desperate measures. He leads Calusky, Camp, and Franklin to an undisclosed location in the woods, a shovel in hand as a storm starts brewing overhead. The crew keeps asking Garthwaite several questions about where they’re at, what they’re doing, and just voicing off overall concerns, but he just ignores them. He then stops, and starts digging.
Henry: Garth, cmon, what the hell are we doing out here, man? Ross is gonna have our asses if he finds out we’re not tracking Banner!
Dirk: [still digging, finally at his tolerance level of the men’s questioning] All right! All of you need to shut up, and listen. Years ago, during one of my earlier ops missions, there were…things that I saw. Things that I…can’t explain. And even if I could, y’all wouldn’t believe me. Hell, I wouldn’t have believed me. I swore never to speak of it again. To never go back. This mission, I planned to take to the grave with me. [Thunder claps in the distance, as it begins to rain and lightning] Not even my superiors from then know the details of that mission. I vowed never to return to it. [finally, he strikes something hard, and continues to clear the dirt, revealing an elongated case] The mission was to apprehend a high value target. Seemed as simple as that. But as it turned out, this target…wasn’t from around…Earth. I think she called herself something like an…Ass…Guard? Ass…Guardian???? I don’t know, some weird shit that didn’t sound like anywhere on Earth. But she had this…crowbar. [he pulls the case out the ground, and opens it, revealing the crowbar inside] But it’s not like your average crowbar. I don’t know how to explain it. But I took it from her on that mission, and I felt…different. Stronger. Powerful. I never would have imagined I’d need it. But if ANYTHING’S gonna take out the Hulk…it’s this baby.
Dirk lifts the crowbar in the air, high above his head. His crew just stares at each other for a moment before bursting into laughter at his nonsensical story. But their laughter is short lived, as they notice the crowbar beginning to shimmer in the lighting, runes glowing. Suddenly, the crowbar is struck by lightning and electricity arches out, striking the 4 men all at once. They all shout in agonizing pain and surprise as the camera zooms out, and the scene fades to black.
We cut to Ross, overseeing the repair and reconstruction of the desert base from The Hulk’s creation, who has just learned his four men charged with tracking The Hulk, have disappeared.
Ross: GONE!? What do you mean they’re GONE!? GONE WHERE!?
As though on cue, Dirk and his crew walk up to Ross.
Dirk: We’re right here, Boss.
Ross: [immediately turning on them] And where the hell have you four been!?!? And why aren’t you out there hunting down Banner?!?
Dirk: Needed some reinforcements. [Shows Ross his crowbar]
Ross: [laughing in disbelief] You went…to get a damn CROWBAR??? How the FUCK is that reinforcement?!? Have you lost your goddamn mind, soldier!?!?
Dirk: Maybe it’s best if you see just what we can do. You see that big ol missile launcher out there? [points with his crowbar] Watch this.
Dirk throws his crowbar, sending it flying straight for the MLR that created the Hulk just days before. The crowbar destroys the MLR, and then flies right back into Dirk’s hand. Ross just stares with his mouth open.
Dirk: But that ain’t all. [Calling out] Boys, give the man little demo!
His crew all nod simultaneously. Eliot makes his way to a line wrecking ball truck, gradually picking up speed as he begins running, leaps up, and lands on the wrecking ball. He then snaps the chain in half, and the wrecking ball thuds to the ground in a cloud of dust. Suddenly, it begins to move as Eliot lifts it off the ground. As he walks back to where Ross and Dirk are standing, he begins swinging the ball high over head like a mace.
Dirk: Yo, Brian! Get over here!
Brian trots over.
Dirk: [To Ross] Shoot him.
Ross is surprised Dirk would make such a callous request about his friend. Dirk sees this.
Dirk: It’s ok. You seen what me and Eliot can do. Trust me. Shoot Brian. As a matter of fact, shoot him a few times.
Ross, hesitantly decides to trust him. He pulls out his sidearm, and shoots Brian 5 times. Brian still stands there, unphased, as the bullets fall in the sand, not a scratch on him.
Dirk: And we got one more thing for ya to see, Boss. Brian, see that forklift? Pass it over to Henry for me.
Brian: On it!
Brian goes over to the forklift, and pushes it on its side.
Brian: Yo, Camp!!! Catch!!
Brian kicks the forklift with full force over to Henry, who braces for impact, taking stance, shifting his entire body weight forward, titling his head down, and lifting his shoulders up as the forklift flies toward him. Henry plows straight through it, completely unshaken as the forklift comes to a stop, with a hole ripped clean through the machinery where Henry stood. They all gather back around Ross and Dirk.
Dirk: General Ross. This here’s my Wrecking Crew. And we got us a Hulk to wreck.

The movie’s finale would be an epic city showdown between the Hulk and the Wrecking Crew, with Betty caught in the midst of the havoc. Ross and the military are there to provide air support for the Wrecking Crew as they fire down on the Hulk. Suddenly, debris falls from a building, with Betty directly in its path. Hulk breaks way from the battle, and shields her from the Debris. Ross orders his men to stop firing, in fear of accidentally hitting her. The Hulk then grabs Betty, and takes her away to a safe distance, Ross in close pursuit.
Cut away to a building a distance away from the carnage of the battleground, where Hulk lands, and gets Betty to safety. Ross’s helicopter levels out with the rooftop so Ross can step down. Hulk snarls at the sight of him, and steps forward, as if to protect Betty. But Betty grabs his arm, and looks up at him.
Betty: It’s ok. Thank you for wanting to protect me. But you have to stop them before they bring the whole city down. Watch over Banner for me, ok, Big Guy? [she kisses his hand, and walks away to the chopper]
Ross: [To Betty] I’ll be right there. [Approaches Hulk] I don’t like you. And I don’t like Banner. I never have, and I don’t think I ever will. But I can’t sit there and pretend like you didn’t just save my daughter down there, and for that, I thank you. We’ll leave you to deal with those idiots down there…I don’t need super powered FREAKS in my ranks. But we will be keeping our eye on you, and we will hunt you down if you show back up after this. And Banner. If you can hear me in there. Stay the hell away from my daughter. [walks away, back to the chopper]
Hulk, rolls his eyes as Ross’s chopper flies away, and turns back to face the damage. In the distance, the Wrecking Crew taunts The Hulk. He lets out a deafening roar, and leaps off frame. Camera cuts back to the streets, where the Wrecking Crew continues to wreak havoc. Dirk slams his crowbar into a police cruiser, sending it flying. Suddenly, The Hulk lands and catches the cruiser. He rips it in half, and fits the vehicle halves over his hands like gauntlets (Yes, I stole that right from the 2008 film, that was a badass scene, and I’d be crazy not to keep it.😂😂). The hulk smiles at them, about to enjoy this moment. He charges at the Wrecking Crew, and they all exchange a series of blows. The fight goes on for a few minutes until finally, Hulk unleashes his thunderclap, shouting, “HULK SMASH!!!!” This creates a shockwave so powerful it sends the Wrecking Crew flying, and causing Dirk to lose his crowbar in the wreckage. Without it, the four are powerless, and knocked unconscious from the blast. Then, several government agents swarm the area. Hulk snarls at them, but then a voice from behind calls out to him.
Voice: Stand down! We are not a threat!
Camera pans around to reveal the man speaking is none other than Nick Fury, director of SHIELD.
Fury: We’re merely here on clean up. But when you’ve calmed back down…we will definitely need to speak with Dr Banner. Coulson!
Agent Coulson comes up from behind Fury, standing next to him.
Coulson: Sir?
Fury: Grab that crowbar, and lock it up. We got some questions for Mr Garthwaite and company.
Coulson: Already on it, Sir.
The SHIELD agents arrest the wrecking crew, and contain Dirk’s crowbar. They all start clearing the area. Fury looks back at the Hulk, curiously before finally leaving the scene. The fight over, Hulk leaps away, bounding over buildings, and gains more and more air before leaving us with a final cinematic shot against the night sky. Cue credits.
Open to the mid credits scene:
Inside the SHIELD Helicarrier:
Maria Hill: Sir, a new report just came in, you might want to take a look at this.
Fury opens the file. It’s a single image, depicting a news paper, headlining:

Fury: Set course to New York. Seems like we got ourselves a Spider to catch.
Close scene with Danny Elfman’s Spider-Man theme.
It’s worth noting that along with Edward Norton reprising his role as Bruce Banner, William Hurt will still be General Ross, and Liv Tyler would still be Betty Ross. Now, I know Hurt had recently passed, and was recast by Harrison Ford, who did a great job in the role, but my thinking is that with my reimagining of the MCU, working under the concept that Marvel didn’t have to sell their rights, and how this Hulk movie would have come out earlier than the actual one, that would give us the wiggle room to give Hurt an opportunity to later shine as The Red Hulk before his eventual passing. As for Betty, I considered recasting her, but nobody else seemed to fit how I’d imagine her. I would also keep Clark Gregg as Agent Coulson and Sam Jackson as Nick Fury, as those roles seem irreplaceable to me. As for my Wrecking Crew, I would cast Arnold Vosloo for Dirk Garthwaite/Wrecker, Dominic Purcell as Henry Camp/Bulldozer, Ben Affleck as Brian Calusky/Piledriver, and finally, Terry Crews as Eliot Franklin/Thunderball.
Keep in mind, this concept for The Incredible Hulk is under the impression that it would have been released in 2002, and in this version of the MCU, rights are not a concern, as this is how the MCU could have looked had Marvel Comics not been in the financial crisis that they were in in the 90’s, and never had to sell off any filming rights. This would have left the Marvel Legacy films from before 2008 to one of two fates. They could be erased from history altogether, or, they could have all started the greater MCU, with Blade in 1998, rather than Iron Man in 2008. I’ve decided to start almost entirely from scratch, erasing most of those Marvel Legacy films from existence (as I have other plans for them later) while also keeping some of them and integrating them into my version of the MCU.
#marvel#mcu au#marvel comics#marvel community#mcu fandom#marvel fandom#marvel studios#incredible hulk#wrecking crew#marvel mcu#mcu#mcu rewrite
2 notes
·
View notes
Text

i made this for MY viewing pleasure but i thot id show you anyways. it is a flow chart discussing the hannibal lecter cinematic universe and i have some notes on it
first and foremost these movies are all based on books but for simplicity and because i havent read them, we're only going to reference them. this is for the movies and we're working chronologically.
we start with Hannibal Rising (2007), which despite being first chronologically was both released and in the case of the book published last. it is the root of all hannibal. Hannibal is played by both Gaspard Ulliel and Aaran Thomas (at different ages)
from Hannibal Rising (2007) you go to Red Dragon (2002) which follows Will Graham as he consults Hannibal on the case of a serial killer nicknamed the Tooth Fairy/Great Red Dragon. Will Graham is played by Edward Norton and Hannibal is played by Anthony Hopkins.
Red Dragon is followed by Silence of the Lambs (1991) in which FBI agent in training Clarice Starling consults with Hannibal Lecter to solve the case of a serial killer nicknamed Buffalo Bill. Will Graham is offhandedly mentioned in the past tense in the Silence of the Lambs novel, which places this movie here chronologically. Anthony Hopkins plays Hannibal and Jodie Foster plays Clarice Starling.
From Silence technically we go to Clarice (2021) but this is obviously a newer installation so i wouldnt be surprised if there were some continuity errors in the series. Clarice (2021) takes place 1 year after the events of Silence of the Lambs (1991) and it does not mention Hannibal Lecter whatsoever. Lol. Clarice is trying to get reacclimated to work after a break from the field. Clarice has been recast as Rebecca Breeds.
That means Hannibal (2001) is technically a sequel to Clarice (2021), despite having previously been a direct sequel to Silence (1991). It takes place 10 years after Silence of the Lambs (1991) or i suppose 9 years after Clarice (2021). Hannibal is trying to get back in contact with Clarice as he is hunted by a previous victim. Clarice has been recast as Julianne Moore, but Anthony Hopkins still plays Hannibal in this one.
There is also NBC Hannibal (2013-2015) which is really an island independent but adjacent to this flow chart but i thought i'd throw it in anyways. The show follows plot lines from all of the books, making it similar to all of the movies. Sometimes Will is substituted for Clarice, and it introduces new characters or adapts existing characters. Hannibal is played by Mads Mikkelsen and Will Graham is played by Hugh Dancy in the show.
There is also Manhunter (1981), is largely considered a FLOP movie. It follows the same plot as Red Dragon (2002), but Silence (1991) was not marketed as a sequel to Manhunter (1981), despite Silence the novel occurring chronologically after Red Dragon the novel. They're very different stylistically and according to many take place in different universes, hence it also being an island on the flowchart. Will Graham is played by William Petersen and Hannibal is played by Brian Cox.
Side note. you have no idea how pleasing it is to my brain that so many of these movies were released in a year that ends in 1. Red Dragon (2002) is forgiven cause it was a direct follow up to Hannibal (2001) so it couldnt possibly be released in a xxx1 year. but Hannibal Rising (2007) you have no excuse
#im not sure anyone cares but......uhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh..........................#one could argue that. hannibal rising could point to hannibal show and manhunter#but Bryan Fuller i believe had not seen or read Hannibal Rising at the time of making the show#and. idk if manhunter is not connected to silence it shouldnt be connected to hannibal rising either i think#but like#idk. i went back and forth. it is A hannibal origin story but not necessarily THE hannibal origin story? hypothetically? idk. you decide#ive remade the chart a few times deciding what connects where. feel free to discuss#<- again i say feel free to discuss as if anyone is going to read this#also idk if its necessary to continue putting the year after establishing what ur talking about but i think its funny to talk like that#so i did it anyways hehehe
28 notes
·
View notes
Text
How to fix installation issues with TurboTax on Windows 11?
Installing TurboTax on Windows 11 should be a smooth experience. However, technical issues can sometimes get in the way. If you're facing problems like TurboTax not installing, freezing, crashing, or displaying error messages on your Windows 11 device, you're not alone. This guide will walk you through all the proven ways to fix installation issues with TurboTax and get you back on track with your tax filing.
Whether you're using a download version or installing from a CD/DVD, the tips below will help you troubleshoot errors effectively using www.installturbotax.com as a starting point.
Why TurboTax Installation Issues Happen on Windows 11
Before diving into solutions, it helps to understand why TurboTax may not install properly on Windows 11. Here are the most common reasons:
Incompatible Windows 11 system requirements
Incomplete or corrupted installation files
Conflicting antivirus or firewall settings
Pending Windows updates
Lack of administrator privileges
Corrupt .NET Framework components
The good news? Most of these issues can be resolved without technical support.
Prerequisites Before Installing TurboTax
To avoid installation errors from the beginning, ensure the following:
✅ Minimum System Requirements for TurboTax
OS: Windows 11 (64-bit)
Processor: 1 GHz or faster
RAM: 2 GB minimum
Disk Space: 1 GB free space for installation
Browser: Latest version of Microsoft Edge, Chrome, or Firefox
.NET Framework: Microsoft .NET Framework 4.7.2 or later
If you're missing any of the above, you may run into problems.
✅ Use www.installturbotax.com to Begin Installation
Go to www.installturbotax.com and log in with your Intuit credentials. This site provides the official and most updated version of TurboTax for downloading and installation.
Step-by-Step Guide to Fix TurboTax Installation Issues on Windows 11
Let’s walk through each solution to fix TurboTax not installing on Windows 11.
1. Run TurboTax as Administrator
One of the easiest ways to fix installation issues is to run the installer as an administrator.
Steps:
Download TurboTax from Turbo tax website
Right-click the installation file (e.g., setup.exe)
Select Run as administrator
Follow on-screen instructions
This ensures TurboTax has the necessary permissions to install and write files to your system.
2. Turn Off Antivirus and Firewall Temporarily
Some antivirus programs (like Avast, Norton, or Windows Defender) can mistakenly flag TurboTax as a threat, blocking installation.
Steps:
Go to your antivirus settings and temporarily disable real-time protection.
Disable Windows Firewall via:
Settings > Privacy & Security > Windows Security > Firewall & network protection
Restart the installer from www.installturbotax.com
Once installation completes, re-enable your antivirus and firewall.
3. Install the Latest Windows 11 Updates
Outdated system files may cause TurboTax to malfunction.
Steps:
Go to Settings > Windows Update
Click Check for updates
Install all pending updates
Restart your computer
Try running the TurboTax installer again from www.installturbotax.com.
4. Ensure Microsoft .NET Framework is Installed and Enabled
TurboTax depends on .NET Framework to run. If it’s missing or corrupted, installation may fail.
Steps to Enable .NET:
Press Windows + R > type optionalfeatures.exe
Check .NET Framework 3.5 and 4.8 Advanced Services
Click OK and let Windows install the necessary files
Restart your PC
Now, re-run the TurboTax installer using www.installturbotax.com.
5. Use TurboTax Cleanup Tool
Intuit offers a cleanup tool to remove previous corrupted TurboTax installations that may cause conflicts.
Steps:
Go to the official Intuit support site
Download the TurboTax Uninstall/Cleanup Tool
Run it to remove leftover files
Restart your computer
Download TurboTax fresh from www.installturbotax.com
This can resolve installer hang-ups, freezes, or crashing errors.
6. Clear Temp Files and Free Up Space
Low disk space or corrupted temporary files can block installations.
Steps:
Press Windows + R, type %temp% and hit Enter
Delete all files in the Temp folder
Empty the Recycle Bin
Make sure you have at least 1 GB of free disk space
Then retry installing TurboTax via www.installturbotax.com.
7. Use Compatibility Mode
If you're running a very new build of Windows 11, try running the TurboTax installer in Windows 10 compatibility mode.
Steps:
Right-click on the installer
Click Properties > Compatibility
Check Run this program in compatibility mode for: Windows 10
Click Apply and OK
Run the installer again
This trick resolves version-specific glitches.
8. Download a Fresh Copy from www.installturbotax.com
Corrupted download files are a common cause of errors. Instead of retrying the same installer:
Go to www.installturbotax.com
Delete the old file
Re-download the setup file
Run it as administrator
Fresh files from the official source often solve unexpected issues.
Common TurboTax Installation Errors and Fixes
Here are some specific errors you might see while installing TurboTax on Windows 11 and how to fix them:
Error Message
Fix
Error 1603
Run installer as admin and ensure .NET Framework is active
Installation freezes
Disable antivirus and download a fresh copy
Installer won't launch
Enable compatibility mode and check admin rights
Setup file missing
Re-download from www.installturbotax.com
“Installation Failed” message
Clear temp files and use the TurboTax cleanup tool
Final Thoughts
Running into installation problems while trying to install TurboTax on Windows 11 can be frustrating, especially during tax season. However, most of these issues can be easily fixed by following the steps in this guide.
Start by verifying system compatibility, using the official installer from www.installturbotax.com, and running it with administrator privileges. Disabling security software temporarily and updating your system can also solve many common issues.
https://www.rueanmaihom.net/forum/topic/20064/how-to-install-turbotax-on-windows-10-or-11?
0 notes
Text
Internet Security for Seniors: Staying Safe Online

The internet offers seniors a wealth of opportunities, from connecting with loved ones to managing finances and learning new skills. However, navigating the digital world also brings risks like scams, malware, and identity theft. For seniors, understanding and practicing internet security is crucial to enjoying a safe online experience.
This guide outlines essential tips and practices to help seniors stay secure and confident while using the internet.
Why Internet Security Is Important for Seniors
1. Protects Personal Information
Prevents unauthorized access to sensitive details like Social Security numbers, banking information, and medical records.
2. Reduces the Risk of Scams
Helps seniors recognize and avoid common online scams, such as phishing and tech support fraud.
3. Prevents Identity Theft
Minimizes exposure to cybercriminals who may misuse personal information for fraudulent purposes.
4. Builds Confidence Online
Empowers seniors to navigate the internet safely and independently.
Common Online Threats Targeting Seniors
1. Phishing Scams
Fraudulent emails or messages trick seniors into revealing personal or financial information.
2. Tech Support Scams
Scammers pose as technical support agents to gain remote access to devices or demand payment for fake services.
3. Malware and Ransomware
Malicious software infects devices, often leading to data loss or ransom demands.
4. Identity Theft
Cybercriminals steal personal information to commit financial fraud or open accounts in the victim's name.
5. Fake Online Stores
Fraudulent websites offer deals that seem too good to be true, taking payments without delivering goods.
Essential Internet Security Tips for Seniors
1. Use Strong and Unique Passwords
Create secure passwords to protect online accounts.
Tips for Strong Passwords:
Use at least 12 characters, including letters, numbers, and symbols.
Avoid using personal details like names or birthdays.
Use a password manager to store and manage passwords securely.
2. Enable Two-Factor Authentication (2FA)
Add an extra layer of security to online accounts.
How 2FA Works:
After entering your password, a secondary code (sent via text or app) is required to access the account.
3. Beware of Suspicious Emails and Messages
Be cautious of unsolicited communications asking for personal or financial information.
How to Spot a Scam Message:
Generic greetings like "Dear User."
Urgent requests to act immediately.
Spelling or grammar errors.
Tip: Never click on unknown links or download unexpected attachments.
4. Install Antivirus Software
Protect your devices from viruses, malware, and other online threats.
Recommended Antivirus Programs:
Norton 360
Malwarebytes
Bitdefender
Tip: Keep antivirus software updated to stay protected against the latest threats.
5. Use Secure Wi-Fi Connections
Avoid using public Wi-Fi for sensitive transactions like online banking.
How to Stay Secure Online:
Use a Virtual Private Network (VPN) to encrypt your connection.
Connect only to password-protected Wi-Fi networks.
6. Shop Safely Online
Ensure online purchases are made securely.
Tips for Safe Shopping:
Look for “https://” and a padlock icon in the website’s URL.
Use credit cards for online transactions instead of debit cards.
Avoid deals that seem too good to be true.
7. Keep Software and Devices Updated
Regular updates patch security vulnerabilities and improve performance.
What to Update:
Operating systems (Windows, macOS, iOS, Android).
Browsers (Chrome, Firefox, Edge).
Apps and antivirus software.
Tip: Enable automatic updates for convenience.
8. Be Cautious on Social Media
Protect your privacy and avoid sharing sensitive information.
Best Practices:
Set profiles to private and limit who can view your posts.
Avoid sharing personal details like your address or phone number.
Be cautious about accepting friend requests from strangers.
9. Back Up Important Data
Regularly back up files, photos, and documents to protect against data loss.
Backup Options:
External hard drives.
Cloud services like Google Drive, OneDrive, or iCloud.
10. Educate Yourself About Internet Safety
Stay informed about the latest online threats and how to avoid them.
How to Learn More:
Attend community workshops or webinars on internet security.
Follow trusted sources like the AARP Fraud Watch Network.
Creating a Safer Online Environment for Seniors
1. Use Simple Security Tools
Make use of tools that are easy to navigate, like:
Password managers.
Browsers with built-in privacy features, like Brave or Firefox.
2. Involve Family Members
Encourage family members to help set up devices and educate seniors about online safety.
3. Set Up Alerts
Enable account notifications to detect unusual activity, such as unrecognized logins or transactions.
4. Limit Access to Unnecessary Apps or Features
Simplify devices by uninstalling unused apps or disabling risky features, like location sharing.
What to Do If You Suspect a Scam
Stop Communication: Discontinue contact with the scammer immediately.
Change Passwords: Secure any affected accounts.
Run a Security Scan: Use antivirus software to check for malware.
Report the Scam: Notify local authorities or organizations like the Federal Trade Commission (FTC) or your bank.
Benefits of Internet Security for Seniors
Peace of Mind: Confidence in navigating the internet safely.
Enhanced Privacy: Protection of personal and financial information.
Empowerment: Independence in using online services for communication, shopping, and learning.
Conclusion
Internet security is crucial for seniors to enjoy the benefits of the online world without falling victim to cyber threats. By practicing good habits, using the right tools, and staying informed, seniors can navigate the digital landscape with confidence and peace of mind.
Start implementing these tips today to create a safer online environment for yourself or the seniors in your life.
FAQs
1. What is the safest browser for seniors? Browsers like Firefox or Brave offer strong privacy features and are easy to use.
2. How can seniors avoid tech support scams? Be cautious of unsolicited calls or pop-ups claiming to fix device issues. Contact trusted professionals for technical support.
3. Are public Wi-Fi networks safe for seniors? Public Wi-Fi should be avoided for sensitive activities unless paired with a VPN.
4. What should seniors do if they receive a suspicious email? Delete the email without clicking on any links or downloading attachments.
5. How can families help seniors with internet security? Assist with setting up devices, explaining online threats, and providing easy-to-use security tools.
0 notes
Text
why does norton vpn turn off automatically
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
why does norton vpn turn off automatically
Norton VPN auto-disable causes
Title: Understanding Norton VPN Auto-Disable Causes
Norton VPN is a popular choice for individuals seeking to safeguard their online privacy and security. However, some users may encounter instances where the VPN unexpectedly disables itself, leaving them vulnerable to potential threats. Understanding the reasons behind Norton VPN auto-disable can help users mitigate these issues and ensure uninterrupted protection.
One common cause of Norton VPN auto-disable is software conflicts. Certain programs or applications installed on the device may interfere with the VPN's functionality, leading to automatic shutdowns. Users should review their installed software and identify any potential conflicts, such as antivirus programs or firewall settings, to resolve this issue.
Another factor contributing to Norton VPN auto-disable is outdated software. It's essential to keep both the Norton VPN application and the operating system up to date to ensure compatibility and stability. Regularly checking for updates and installing them promptly can help prevent unexpected disruptions in VPN service.
Additionally, network connectivity issues can trigger Norton VPN auto-disable. Fluctuations in internet connectivity, network congestion, or router malfunctions may cause the VPN connection to drop unexpectedly. Users should troubleshoot their network connection and address any underlying issues to maintain a stable VPN connection.
Furthermore, user settings and configurations can impact Norton VPN's behavior. Incorrect settings or misconfigurations may inadvertently trigger auto-disable features within the application. Users should review their VPN settings and ensure they are configured correctly to avoid unintentional disruptions in service.
In conclusion, Norton VPN auto-disable can occur due to various factors, including software conflicts, outdated software, network issues, and user configurations. By addressing these potential causes and implementing preventive measures, users can enjoy uninterrupted protection and peace of mind while browsing the internet with Norton VPN.
Troubleshooting Norton VPN automatic shutdown
Troubleshooting Norton VPN Automatic Shutdown
Norton VPN is a popular choice for users seeking online privacy and security. However, encountering automatic shutdowns can be frustrating, disrupting your browsing experience and potentially leaving your connection vulnerable. Understanding and troubleshooting this issue is crucial to maintaining a seamless VPN experience.
One common reason for Norton VPN automatic shutdowns is conflicting software. Certain antivirus programs or firewall settings may interfere with Norton's operation, causing it to unexpectedly close. To address this, try disabling any conflicting software temporarily and see if the issue persists. If the problem resolves, you may need to adjust settings or seek alternatives to conflicting programs.
Another possibility is outdated software or system components. Ensure both Norton VPN and your operating system are up to date with the latest patches and updates. Outdated software can contain bugs or compatibility issues that may trigger automatic shutdowns. Regularly checking for updates and installing them promptly can help prevent such issues.
Additionally, network instability or configuration errors may contribute to Norton VPN shutdowns. Poor internet connectivity, network congestion, or misconfigured VPN settings can all impact VPN performance. To troubleshoot network-related issues, try switching to a different network, restarting your router, or adjusting VPN settings such as protocol or server location.
Lastly, if none of the above solutions resolve the problem, reaching out to Norton support can provide further assistance. They can offer personalized troubleshooting steps based on your specific setup and circumstances.
In conclusion, troubleshooting Norton VPN automatic shutdowns requires identifying and addressing potential causes such as conflicting software, outdated components, network issues, or configuration errors. By following these steps and seeking appropriate support when needed, users can resolve issues and enjoy a stable and secure VPN connection.
Norton VPN auto-disconnect root causes
Norton VPN auto-disconnect issues can be frustrating for users seeking a secure and seamless online experience. There are several common root causes for the automatic disconnection problem with Norton VPN that you should be aware of.
One of the main reasons for Norton VPN auto-disconnects is unstable internet connectivity. If your network connection is weak or experiencing frequent interruptions, the VPN might disconnect to protect your data integrity. It is essential to ensure a stable and strong internet connection to avoid these disruptions.
Another possible cause of Norton VPN auto-disconnects is outdated VPN software. Regularly updating your Norton VPN application ensures that you have the latest bug fixes and security patches, reducing the chances of automatic disconnections.
Moreover, conflicting applications or settings on your device can also lead to Norton VPN auto-disconnects. Certain third-party software or firewall settings may interfere with the VPN connection, causing it to disconnect unexpectedly. It is advisable to check for any conflicting programs and adjust your settings accordingly.
Lastly, server overload or maintenance on Norton's end can also result in automatic disconnections. During peak hours or server maintenance periods, the VPN service may disconnect users to manage server load efficiently.
In conclusion, understanding the root causes of Norton VPN auto-disconnects can help you troubleshoot and resolve the issue effectively. By addressing issues such as internet connectivity, software updates, conflicting applications, and server status, you can enjoy a stable and uninterrupted VPN connection with Norton.
Preventing Norton VPN auto-turnoff
Are you tired of experiencing sudden auto-turnoffs while using Norton VPN? This common issue can be frustrating and compromise your online security and privacy. Luckily, there are several steps you can take to prevent Norton VPN from automatically turning off.
Firstly, ensure that your Norton VPN software is up to date. Outdated software can often cause technical glitches and malfunctions, including auto-turnoffs. By regularly updating your Norton VPN, you can benefit from the latest bug fixes and security patches that can help prevent auto-turnoffs.
Secondly, check your device's power settings. Sometimes, devices are programmed to enter sleep or hibernate mode after a certain period of inactivity, which can trigger Norton VPN to turn off automatically. Adjusting your device's power settings to prevent it from going to sleep can help maintain a stable connection with Norton VPN.
Additionally, review your network settings and configurations. Poor network connectivity or unstable internet connections can also lead to Norton VPN auto-turnoffs. Ensure that you are using a reliable internet connection and try switching between different network protocols to see if that resolves the issue.
By following these preventative measures, you can minimize the occurrence of Norton VPN auto-turnoffs and enjoy uninterrupted online protection and privacy. Remember to regularly update your software, adjust your device's power settings, and optimize your network configuration to maintain a seamless and secure VPN experience.
Understanding Norton VPN auto-off triggers
Norton VPN is a reliable software that provides users with secure and private internet connections. One of the features that users may encounter while using Norton VPN is the auto-off trigger. Understanding Norton VPN auto-off triggers is essential for ensuring the effective use of the software and maintaining your online security and privacy.
Norton VPN auto-off triggers are designed to deactivate the VPN connection under specific circumstances. These triggers are programmed to ensure that the VPN connection is enabled only when it is safe and necessary to do so. One common trigger is when the VPN detects an unstable network connection or a sudden drop in internet speed. In such cases, the VPN automatically switches off to prevent any disruptions in your online activities.
Another common trigger for Norton VPN auto-off is when the software identifies that a particular website or application does not support VPN connections. This feature helps prevent compatibility issues and ensures that you can access all online content seamlessly without any restrictions.
Understanding how Norton VPN auto-off triggers work is crucial for users to avoid any vulnerabilities in their online security. By being aware of the situations that can trigger the VPN to turn off, users can take necessary precautions to protect their sensitive information and browsing activities.
In conclusion, Norton VPN auto-off triggers are important mechanisms that contribute to the overall performance and effectiveness of the software. By understanding these triggers, users can enhance their online security and privacy while enjoying a seamless browsing experience.
0 notes
Text
did i install norton vpn properly
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
did i install norton vpn properly
Norton VPN setup guide
Title: The Complete Norton VPN Setup Guide: Protect Your Online Privacy with Ease
In today's digital age, securing your online privacy is more important than ever. With cyber threats lurking around every corner, safeguarding your personal data has become a top priority for internet users worldwide. One effective solution to enhance your online security is using a Virtual Private Network (VPN), such as Norton VPN. This guide will walk you through the steps to set up Norton VPN and start browsing the web securely.
Step 1: Subscription and Installation The first step is to subscribe to Norton VPN and download the software onto your device. You can easily find Norton VPN on the official Norton website or through reputable app stores.
Step 2: Sign In or Create an Account After installing the software, launch the Norton VPN application. If you already have a Norton account, sign in using your credentials. Otherwise, you'll need to create a new account to proceed.
Step 3: Choose Your Subscription Plan Norton VPN offers various subscription plans to cater to different user needs. Select the plan that best fits your requirements and budget.
Step 4: Connect to a Server Once you've signed in or created an account and selected your subscription plan, you can now connect to a VPN server. Norton VPN has servers located worldwide, allowing you to choose the location that suits you best.
Step 5: Enjoy Secure Browsing Congratulations! You're now connected to Norton VPN and can enjoy secure and private browsing. Whether you're accessing sensitive information, streaming content, or simply surfing the web, Norton VPN will encrypt your data and protect your online privacy.
In conclusion, setting up Norton VPN is quick and straightforward, providing you with peace of mind knowing that your online activities are safe from prying eyes. Take control of your digital security today with Norton VPN.
Troubleshooting Norton VPN installation
Troubleshooting Norton VPN Installation
Norton VPN is a popular choice for users seeking to protect their online privacy and security. However, sometimes users may encounter issues during the installation process. Here are some common troubleshooting steps to help you resolve any installation problems with Norton VPN.
Check System Requirements: Before installing Norton VPN, make sure your device meets the minimum system requirements. Ensure that your operating system is up to date and compatible with the software.
Internet Connection: A stable internet connection is essential for a successful installation. Make sure you are connected to the internet and that there are no disruptions that could hinder the installation process.
Disable Antivirus/Firewall: Sometimes, security software like antivirus programs or firewalls can interfere with the installation of Norton VPN. Temporarily disable any such software before installing Norton VPN to see if it resolves the issue.
Download from Official Source: Ensure you are downloading Norton VPN from the official website to avoid any potential issues with third-party sources.
Clear Cache and Cookies: Clearing your browser's cache and cookies can sometimes resolve installation issues by removing any stored data that may be conflicting with the installation process.
Reinstall the Application: If all else fails, try uninstalling Norton VPN and then reinstalling it. This can help resolve any corrupted files or errors that may be causing the installation problem.
By following these troubleshooting steps, you should be able to address common issues that may arise during the installation of Norton VPN. If you continue to experience problems, reaching out to Norton's customer support for further assistance is recommended. Remember, protecting your online privacy is important, so don't hesitate to seek help in ensuring that your Norton VPN installation is successful.
Norton VPN configuration tips
Configuring a Norton VPN is essential for ensuring your online privacy and security. Here are some tips to help you set it up effectively.
Download the Norton VPN App: Start by downloading the Norton VPN app from a trusted source. You can find the app on the official Norton website or app store.
Install and Launch the App: Once the app is downloaded, install it on your device and launch the application. Follow the on-screen instructions to set up your account and log in.
Choose Server Location: Norton VPN allows you to choose from different server locations. Select a server location that is closer to you for better speed and performance.
Enable Kill Switch: The kill switch feature is crucial as it disconnects your internet connection if the VPN connection drops. Enable this feature in the settings menu for added security.
Automatic Connection: To ensure continuous protection, enable the automatic connection feature. This will automatically connect your device to the VPN whenever you go online.
Customize Settings: Explore the app's settings menu to customize your VPN preferences. You can adjust security levels, protocols, and other settings according to your needs.
Regular Updates: Keep your Norton VPN app updated to ensure you have the latest security features and bug fixes.
By following these configuration tips, you can maximize the effectiveness of your Norton VPN and enjoy a secure and private browsing experience. Remember to stay informed about VPN best practices to stay safe online.
Verifying Norton VPN installation
Verifying Norton VPN Installation
Once you have installed Norton VPN on your device, it is essential to verify that the installation was successful to ensure your online privacy and security. Verifying the installation of Norton VPN is a simple process that can give you peace of mind knowing that your internet connection is encrypted and your data is protected.
To verify the Norton VPN installation, follow these steps:
Open the Norton VPN application on your device. You should see the Norton Secure VPN interface with options to connect to different servers around the world.
Select a server location and click on the "Connect" button. This will initiate the VPN connection, and you should see a notification confirming that you are now connected to the VPN server.
Visit a website that displays your IP address, such as whatismyipaddress.com, to check if your IP address has been changed. If the displayed IP address is different from your actual IP address, it means that the VPN is working correctly.
You can also run an online privacy test to ensure that your internet connection is secure and your data is encrypted. There are various websites available that can perform these tests and provide you with detailed information about your online privacy status.
By following these simple steps to verify the Norton VPN installation, you can guarantee that your online activities are protected and your data remains confidential. Remember to regularly check and verify your VPN connection to stay safe and secure while browsing the internet.
Common Norton VPN installation mistakes
When it comes to installing Norton VPN, there are common mistakes that users may encounter that could impact the performance and effectiveness of the VPN service. By being aware of these potential pitfalls, users can ensure a smooth and successful installation process.
One common mistake when installing Norton VPN is not properly following the installation instructions provided by the provider. Skipping important steps or overlooking certain requirements can lead to connectivity issues or a compromised security setup. It is essential to read through the instructions carefully and follow them step by step to avoid any mishaps.
Another mistake is not updating the software before installation. Ensuring that both the operating system and the VPN software are up to date can prevent compatibility issues and security vulnerabilities. It is recommended to check for updates regularly and install them before setting up the VPN.
Choosing the wrong subscription plan can also be a mistake that users make during the installation process. Opting for a plan that does not meet your needs in terms of the number of devices supported or the level of security offered can result in dissatisfaction with the service. It is crucial to assess your requirements and choose a plan that aligns with them.
Finally, neglecting to test the VPN connection after installation is a mistake that can go unnoticed but have serious ramifications. Testing the connection ensures that the VPN is functioning correctly and that your online activities are secure and private.
By being mindful of these common mistakes and taking the necessary precautions, users can optimize their Norton VPN installation experience and enjoy the benefits of a reliable and secure VPN service.
0 notes
Text
How To Easily Solve the Norton Installation Error On Your PC
Norton security antivirus application is the most used antivirus software at this time. This antivirus is also the most popular protection application that its users utilize to protect their devices from various types of viruses, malware, phishing sites, etc
Do you want to know how to easily solve the Norton installation error on your system in a few simple steps? Read this blog to get detailed information about it
0 notes
Text
Norton Security Deluxe Full Review with Pros and Cons
Norton antivirus is an enemy of malware programming item planned by Symantec Corporation. The product has been in the business for 30 long a very long time at this point yet was simply patched up by the engineers in April 2019. Its Norton Security Deluxe bundle is one of its very good quality and lead security programming that has been making malware location simpler for the average person. Norton's security special bundle has been set apart as the 'most ideal decision' by numerous experts fundamentally because of its simple establishment from Norton page, high recognition scores, an enormous determination of safety highlights and the general incentive for cash that it gives.
Malware Detection
Norton's security grand accompanies a 97 percent malware and infection identification rate which is quite high. Regardless of whether the product can't prevent an infection from entering your framework, it is ultimately identified in the customary framework filters that are booked dependent on the client's inclination. When recognized, the tainted records are forever hindered.
Norton Security Deluxe
Aside from this, with regards to hindering and recognizing dangers from the web, the fancy bundle works really hard. When contrasted with other enemy of infection programming like Trend Micro and BitDefender, Norton's Deluxe bundle dominated the race. While associated with the web, Norton profits by the online data set of malware that expands the general infection and malware identification capacity.
Similarity
When contrasted with its Norton standard security, the Norton security select accompanies various client licenses and is additionally viable with cell phones which makes it ideal for people that need to keep every one of the gadgets at home ensured. Once purchased, Norton setup can be introduced on a limit of three or five gadgets including PCs, cell phones, workstations, and tablets. The quantity of gadgets relies upon the bundle you purchase.
Firewall and Software Updates
The framework accompanies an individual firewall that incorporates various apparatuses to check the texts, messages and USB drives on every one of the viable gadgets, delivering any infections of malware pointless. The best element of the choice bundle is a distant association with your PC. On the off chance that, your gadget is undermined, the product can interface with your framework distantly to reestablish it.
Aside from this, the counter infection program keeps a mind all the introduced programming on your PC. Obsolete programming can make your gadget helpless against programmers and payoff product. Henceforth, the product separated from keeping itself refreshed keeps other programming in the framework refreshed also.
Masters:
It tends to be utilized to get more than one gadget which adds to the client's comfort.
You can Install Norton on different gadgets with same item key.
Has an individual firewall that can associate with the online malware data set.
Can get to PCs distantly on the off chance that they are undermined.
Cons:
Since it runs on the gadget all day, every day, a lot of RAM should be distributed to it.
Last Verdict
Because of the individual firewall and added parental controls this enemy of infection programming is ideal for families who need to keep every one of their gadgets shielded from the consistently expanding number of malware.
#Norton#how to#Norton setup#endpoint security#error fix#reinstall#Norton virus scan#Norton virus scan installation issues#Norton.com/setup
1 note
·
View note
Text
How to choose best antivirus Software for K7 Security
1) Assess your requirements: Consider what you need from an antivirus software. Are you looking for basic protection or advanced features like parental controls, firewall protection, or secure online banking? Make a list of the features you require.
2) Research and compare: Look for reputable antivirus software providers and compare their offerings. Visit their websites, read product descriptions, and compare features, pricing, and user reviews. Pay attention to independent antivirus testing organizations like AV-Test or AV-Comparatives, which evaluate software for effectiveness and performance.
3) Compatibility: Ensure that the antivirus software you choose is compatible with your operating system (Windows, mac OS, Android, etc.) and any other devices you want to protect.
4) Real-time protection: Check if the antivirus software provides real-time protection. This feature actively scans files, emails, downloads, and websites for malware and other threats as you use your computer.
5) Malware detection and removal: Look for software that has a high detection rate for known and unknown malware. It should also offer robust malware removal capabilities.
6) System impact: Consider the impact the antivirus software has on your system's performance. Look for software that is lightweight and doesn't slow down your computer significantly.
7) User interface: Ensure the software has an intuitive and user-friendly interface. It should be easy to navigate and configure.
8) Customer support: Check the available customer support options such as email, phone, or live chat. Look for software that offers timely and helpful support in case you encounter any issues.
9) Additional features: Consider any additional features you may need, such as a VPN, password manager, or backup capabilities. Some antivirus software providers offer these features as part of their packages.
10) Pricing: Compare the pricing options, including subscription plans and the number of devices covered. Look for any trial versions or money-back guarantees that allow you to test the software before committing. Reputation and trustworthiness: Research the reputation of the antivirus software provider. Look for their track record in the industry and their commitment to regular updates and security patches.
How can activate best antivirus Software for K7 Security?
Purchase or download: Purchase the K7 Security software or download it from the official website or a reputable source.
1) System requirements: Ensure that your computer meets the system requirements specified by K7 Security. This may include the operating system version, available disk space, and RAM.
2) Disable conflicting software: If you have any other antivirus or security software installed, it's recommended to uninstall or disable them before installing K7 Security. Having multiple antivirus programs can cause conflicts and affect performance.
3) Run the installer: Locate the downloaded installer file and double-click on it to run the installation wizard. Follow the on-screen instructions provided by K7 Security.
4) Activate the license: During the installation process or after it, you may be prompted to enter a license key or activate your product. Enter the required information accurately to activate K7 Security.
5) Configure settings: Once installed, open K7 Security and navigate through the settings. Set your preferences for scanning options, real-time protection, scheduled scans, and any additional features you want to enable.
6) Update the software: Check for updates within the K7 Security interface. Keeping your antivirus software up to date is crucial to ensure it can detect and protect against the latest threats.
7) Perform a full system scan: Initiate a full system scan with K7 Security to scan your entire computer for existing malware or potential threats. This initial scan may take some time to complete.
8) Customize further: Explore the additional features and settings provided by K7 Security to tailor the software to your specific needs. This may include configuring web protection, email scanning, firewall settings, or any other available options.
What locations can I find a K7 Security?
1) Purchase or download: Purchase the K7 Security software from the official website or a reputable retailer. Alternatively, download it from the official K7 Security website.
2) Locate the installer: If you downloaded the software, locate the installer file on your computer. It is usually saved in the default download location or the folder you selected during the download process.
3) Run the installer: Double-click on the installer file to start the installation process. You may need to grant administrative privileges or provide your account password to proceed.
4) Installation wizard: The installation wizard will guide you through the installation process. Follow the on-screen instructions, including accepting the license agreement and choosing the installation location (or using the default location).
5) Activation: Once the installation is complete, you may be prompted to activate your K7 Security software. Enter the license key or any required information accurately to activate the product. This key is usually provided with your purchase or in the email confirmation if you downloaded the software.
6) Initial setup: After activation, you may be prompted to configure initial settings for K7 Security. This may include options for real-time protection, scheduled scans, automatic updates, and other preferences. Set these according to your preferences.
7) Update the software: It's crucial to update K7 Security to ensure it has the latest virus definitions and security updates. Look for an update option within the software interface and follow the prompts to update it to the latest version.
8) Customize settings: Explore the settings and configuration options within K7 Security to customize it according to your needs. You can adjust scanning options, enable additional features, configure exclusions, and fine-tune other settings based on your requirements.
9) Perform a scan: After the initial setup, it's recommended to perform a full system scan to check for any existing malware or potential threats. Initiate a scan from within the K7 Security interface and let it scan your entire system.
10) Ongoing maintenance: Keep K7 Security running in the background to ensure real-time protection. Regularly update the software, perform scheduled scans, and follow safe browsing habits to maintain optimal security.
Having issues without K7 security applications: Installation of McAfee Secure Again
1) Uninstall previous security software: If you have any existing antivirus or security software installed on your computer, it's important to uninstall it before installing McAfee Secure Again. Having multiple security applications can cause conflicts. To uninstall the previous software, go to the Control Panel (Windows) or the Applications folder (Mac) and locate the security software. Follow the provided uninstallation instructions.
2) Download from official source: Ensure you are downloading McAfee Secure Again from the official McAfee website or a trusted source. This will help ensure you are getting the legitimate software without any modifications or malware.
3) Check system requirements: Verify that your computer meets the system requirements specified by McAfee Secure Again. Check for the supported operating systems, available disk space, and RAM requirements. If your computer doesn't meet the requirements, you may need to upgrade your hardware or consider an alternative security solution.
4) Disable conflicting software: Temporarily disable any firewall, antivirus, or security software installed on your computer during the installation process. These applications can interfere with the installation of McAfee Secure Again. Consult the documentation of the conflicting software to learn how to disable it temporarily.
5) Run the installer as administrator: Right-click on the McAfee Secure Again installer file and select "Run as administrator" to give it the necessary permissions to make changes to your system. This can help overcome any permission-related issues during the installation process.
6) Check for software conflicts: If you have any other software running in the background that could potentially interfere with the installation, temporarily disable or close them. This includes software such as VPN clients, system optimization tools
Reinstall K7 Security Anywhere with assistance from Best Antivirus Software
1) Uninstall previous version: If you have a previous version of K7 Security installed, it's recommended to uninstall it before reinstalling. Go to the Control Panel (Windows) or the Applications folder (Mac), locate K7 Security, and follow the provided uninstallation instructions.
2) Download the latest version: Visit the official K7 Security website or a trusted source to download the latest version of K7 Security. Ensure you are downloading it from a reputable source to avoid any potential risks.
3) Run the installer: Locate the downloaded installer file and double-click on it to run the installation wizard. If prompted, grant the necessary permissions to the installer.
4) Follow the on-screen instructions: The installation wizard will guide you through the installation process. Follow the on-screen instructions, such as accepting the license agreement and choosing the installation location. You may also be prompted to enter a license key or activate the software, so have that information ready.
5) Configure settings: Once the installation is complete, open K7 Security and configure the settings according to your preferences. This may include setting up real-time protection, scheduled scans, or other security options. Take some time to review and adjust the settings as per your requirements.
6) Update the software: It's important to update K7 Security to ensure it has the latest virus definitions and security patches. Look for an update option within the K7 Security interface and follow the prompts to update the software to the latest version.
7) Perform a scan: After the installation and updates, initiate a full system scan with K7 Security to check for any existing malware or potential threats. This initial scan may take some time to complete, but it helps ensure your system is protected.
8) Ongoing maintenance: Keep K7 Security running in the background and regularly perform scans to maintain continuous protection. Stay vigilant with software updates, enable automatic updates if available, and follow safe browsing practices.
Contact Us: 800-834-6919
0 notes
Note
...........
Error, error.
Nortan Anti-Virus compromised.
Error, uninstalling Norton Anti-Virus.
Installing Black Mesa Sweet Voice.
.......
Installation complete!
Hello Chara!
Uh hi?
2 notes
·
View notes
Text
Family Cybersecurity Practices: Protecting Your Loved Ones Online

In today’s connected world, families face numerous online threats, from phishing scams and malware to identity theft and cyberbullying. Practicing good cybersecurity as a family is essential to ensuring everyone stays safe while using the internet. By setting up proper safeguards and fostering awareness, you can protect your loved ones from digital dangers.
This guide provides actionable tips for implementing effective family cybersecurity practices.
Why Family Cybersecurity Is Important
1. Protects Personal Data
Safeguards sensitive information like names, addresses, and financial details from theft.
2. Prevents Cyber Threats
Stops malware, phishing attacks, and hacking attempts before they cause harm.
3. Educates Family Members
Builds awareness about online risks, empowering everyone to use the internet responsibly.
4. Creates a Safer Online Environment
Minimizes exposure to inappropriate content and harmful interactions.
Key Family Cybersecurity Practices
1. Set Up Strong Passwords
Ensure every family member uses unique, strong passwords for their accounts.
Password Tips:
At least 12 characters with a mix of letters, numbers, and symbols.
Avoid using personal details like birthdays or pet names.
Use a password manager to securely store and generate passwords.
2. Enable Two-Factor Authentication (2FA)
Add an extra layer of protection to important accounts like email, social media, and online banking.
How 2FA Works:
Requires a password and a secondary method of verification, such as a code or biometric scan.
Prevents unauthorized access even if a password is compromised.
3. Educate About Phishing Scams
Teach family members how to identify and avoid phishing attempts.
What to Watch For:
Emails or messages asking for personal information.
Unfamiliar links or attachments.
Spelling errors and generic greetings like “Dear User.”
Tip: Encourage them to verify suspicious messages with you before responding.
4. Use Parental Controls and Content Filters
Set up tools to restrict access to inappropriate content and monitor online activity.
Recommended Tools:
For Browsers: Google SafeSearch, Microsoft Family Safety.
For Devices: Apple Screen Time, Android Family Link.
For Networks: Configure your router’s parental control settings.
5. Keep Devices Updated
Ensure all devices have the latest security updates and software versions installed.
Why Updates Matter:
Fixes security vulnerabilities that hackers could exploit.
Enhances device performance and stability.
Tip: Enable automatic updates where possible.
6. Install Reliable Antivirus Software
Protect devices from malware, spyware, and viruses.
Recommended Antivirus Programs:
Norton 360
Bitdefender
Kaspersky
Tip: Schedule regular system scans for additional protection.
7. Secure Your Home Wi-Fi Network
Make your home network a fortress against potential cyber intrusions.
Best Practices:
Use a strong, unique password for your Wi-Fi.
Enable WPA3 encryption for better security.
Set up a guest network for visitors and IoT devices.
8. Limit Screen Time
Encourage a healthy balance between online and offline activities for family members.
Tips for Managing Screen Time:
Set daily limits on device usage.
Designate tech-free zones, such as bedrooms or dining areas.
Use apps like Qustodio or OurPact to manage screen time.
9. Monitor Online Activities
Stay aware of what your family members, especially children, are doing online.
How to Monitor Safely:
Check browsing history and app usage periodically.
Discuss online behavior openly to build trust.
Use family-friendly monitoring apps like Bark or Net Nanny.
10. Discuss Social Media Safety
Help family members use social media responsibly and securely.
Key Tips:
Set profiles to private to limit visibility.
Avoid oversharing personal information, like vacation plans.
Be cautious about accepting friend requests from strangers.
11. Back Up Important Data
Regularly back up files and photos to protect against data loss due to cyberattacks or device failure.
Backup Options:
External hard drives.
Cloud services like Google Drive, iCloud, or OneDrive.
Tip: Use encrypted backups for added security.
12. Practice Safe Online Shopping
Teach family members to shop safely and securely online.
Tips for Safe Shopping:
Use credit cards instead of debit cards for better fraud protection.
Shop only on websites with “https://” in the URL.
Avoid saving payment information on websites.
Creating a Family Cybersecurity Plan
Host Regular Discussions: Talk about online safety rules and address any concerns.
Establish Clear Guidelines: Set rules for internet use, such as time limits and approved websites.
Role-Model Good Habits: Demonstrate safe practices like using strong passwords and avoiding suspicious links.
Create an Emergency Response Plan: Decide how to handle cyber incidents, such as phishing or hacked accounts.
Benefits of Practicing Family Cybersecurity
Peace of Mind: Ensures the safety of your loved ones and their data.
Improved Digital Literacy: Helps family members navigate the online world confidently.
Reduced Risk of Cyber Incidents: Prevents threats before they happen.
Conclusion
Family cybersecurity is about more than just tools—it’s about fostering awareness, communication, and good habits. By taking proactive steps to secure devices, educate family members, and set boundaries, you can create a safer online environment for everyone.
Start implementing these practices today to protect your loved ones from the ever-evolving landscape of cyber threats.
FAQs
1. How often should I review family cybersecurity practices? Review your practices every 6–12 months or when new threats or technologies arise.
2. Are parental controls enough to keep children safe online? Parental controls are helpful but should be combined with open discussions about online behavior.
3. Can antivirus software protect all devices in my home? Yes, many antivirus programs offer multi-device protection for computers, smartphones, and tablets.
4. How can I teach young children about cybersecurity? Use age-appropriate language and examples, and consider educational apps or games.
5. What should I do if a family member falls for a scam? Act quickly: change affected passwords, monitor accounts for suspicious activity, and report the scam to relevant authorities.
0 notes
Text
November 16, 2020: 2:59 pm:
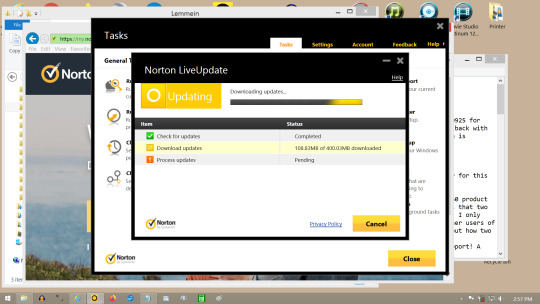
Centurylink Shane Welsh; Zachary White; Stephen Bell terror scenario playing out today, is a repeating, scripted screenplay of a terror scenario: The activity begins with Centurlylink terror operatives using the Symantec norton product to erase itself from the computer with a variety of computer headaches that take several hours to remedy. The hack installs a second norton product, one conflicts with the other, the computer is said to have no internet security at all, the message from norton says there are a number of “Errors” and the manual diagnostics must be done, a re-installation of the norton product, and a system restore is necessary after figuring out what the problem is. I am re-installing the update to the most recent version now as a result of that computer hack attack.
So, there is more. The other part to this computer attack is the dangerous part.
I have played this game before, always the same people, same props, same place, same activity, same, same, same, all over again... the same shit on a different day at one year intervals or so.
The other part to the attack is a physical one. While I am busy fixing the computer, the thing needs time to load the program, do the diagnostic, etc, so that is a good time to take a walk while the spinning curser is doing it’s thing.
While walking, I encounter an expecially geeky looking fellow at the neighbors house. He is always carrying the same broken computer with wires sticking out all over the place... clearly, the man is a computer wizard, and can help me fix my computer (the one he attacked from Centurylink). Of course, in the past, I have fallen for the computer geek at the neighbor before, so, I already know who he is... he is part of the Green Jello Centurylink Shane Welsh/Zack White attack team. If I say: “Hey, you look like a friendly sort of SDA computer geek who can help me repair this nasty bug that just happened”, then, he will be like Johnny on the spot, ready to go, has a pouch filled with thumb drives and diagnostic software, and, he is already carrying around a broken computer with wires all hanging out of it so I can clearly see it as I walk by. They wait there for me to walk by, so they can carry the broken computer with wires all sticking out for me to see.
The physical attack happens after you invite the geek into the house to look at the bug he put on your computer. There is also a Hot Chick who is there to be mysteriously just barely out of view, so, that is another reason to start a conversation with the friendly SDA Green Jello terror computer geek, maybe have a look at a Hot Chick who is clearly not a computer geek oriented woman.
So, that’s all i have on that, but, the point here is more about the repetitive, planned, scripted attack scenario that is invasive into your personal computer to unknown extent, designed to fool a victim into asking for some help, as a lure for a private, physical attack behind closed doors at the victims home.
I pay $45 per month for Internet service. I pay more than $100 annually for the Symantec norton product. That won‘t keep Centurylink out of my computer or personal information, nor will it protect me from being throttled from reaching FBI and other national Security offices.
One more interesting Symantec note, is that in about twenty years of annual renewals to the norton product, it has never found any issues of computer bugs, ever, when I do a scan. The product is fake. It only does what Centurylink wants it to. The need the information I share online, so, they don‘t completely wipe pout my computer like they could do. Instead, the install keystroke recorder software, and other spyware, so that the information I explain can be stolen, changed enough to suit the needs of Centurylink, and ultimately used as a lure to get federal agents to go to the wrong addresses, and walk directly into the traps that are set for them.
End terror report: 3:37 pm.
7 notes
·
View notes
Text
How To Turn Off Norton Firewall Temporarily If Needed
Norton antivirus security is the name of the main programming in this advanced world, and gives solid protection against different online dangers like malware and infections which are prowling on the gadgets to get monitory advantages. In this situation, it has ended up being a huge assignment for the clients to save individual information, character, and gadgets since every one of these things are getting increasingly more helpless against these assaults by cybercriminals or intruders. Norton Setup accompanies the most complex highlights to ensure gadgets and individual data. In this post, we will talks about on the best way to kill on or turn the Norton firewall so this errand don't fall in your manner to shielding your gadgets or different resources from these online hunters.
Crafted by a firewall is to screen the In-and-out traffic of your PC, and it shields your gadgets from outside dangers. On the off chance that you turn off the firewall of your framework, you can't shield your gadgets from online dangers that are prepared to assault. For a particular reason, you can kill the fire divider, after that it is turned on consequently. Norton accompanies numerous items that are empowered with firewall. Perhaps the most noticeable items is Norton 360 that is accessible on Norton com setup enter product key product key site. Sometimes, it gets important to impair this firewall to introduce the necessary program. A portion of the business programs don't permit the firewall on and it ought to be killed and later on it very well may be turned on.
To figure out how to kill on or the Norton firewall, here are the means which clients need to continue to finish this undertaking:
The initial step is to double tap on "Open" of the Norton control board. And afterward look down till you find and select "Impair Smart Firewall", and afterward you will discover the alternative to kill the firewall. You will be incited to clarify how long you need to handicap the firewall.
The subsequent stage is to tap on the "Settings" to open the settings window, and afterward it is fitting to tap on "network" alternative to see the firewall settings.
Presently, you will be incited to tap the "Shrewd Firewall" tab in the overall setting choice. Furthermore, presently move to the on/off, according to your need you can tap on the "Off" alternative to kill the firewall.
From that point, click on the "Apply" and later on "select the span" of killing the firewall, and afterward, you will be encouraged to drop down the rundown from the "security solicitation" and window which is accessible to open.
Presently, click on "Alright" from that point 'near' total the setting window.
It gets important to figure out how to turn on or off Norton firewall so this safeguard against online dangers doesn't transform into a hindrance in your work. As a portion of the projects don't need a functioning firewall since it isn't viable. This post will be a decent instructional exercise to fix this issue. In the event that there is an issue that is by all accounts strange, you can facilitate with the professional who can fix it inside a moment.
#Norton#how to#Norton setup#endpoint security#error fix#reinstall#Norton virus scan#Norton virus scan installation issues#Norton.com/setup
1 note
·
View note
Text
Norton Antivirus Stuck on Update
Norton antivirus software shields the PC framework against cyber threats like viruses, malware, spyware, and Trojans. It is famously known for its advanced features and functions across the globe. It blocks the malicious activities that harm your system and keep your personal and professional information safe.
And it is also true that Norton keeps updating its software for better performance and protection. And users need to keep updating the Norton antivirus software to the latest version to keep the system data in safety and security. But sometimes, due to some new bugs and unknown threats, the methods get interrupted, and users face the Norton antivirus stuck on update Error.
A user needs to fix the error in due course to keep the software updated and for the safety of the system from the bugs and threats.
Some methods to fix the Norton antivirus stuck on update Error
A user can simply go through the given methods to get rid of the issue. One can without much effort, follow the given strategies.
Method 1: Norton Remove and Reinstall tool
1. To download the tool, visit Norton's main page.
2. Here, you need to download the latest version of the software.
3. And then save the downloaded file in your system.
4. Now, go to the file and run the file.
5. Once the download process completes, you need to install the software.
6. At last, you need to restart your system.
Also See - Norton Server Error
Method 2: Disable windows firewall
Your firewall setting is one of the reasons for the update stuck error, and, in that case, users need to disable the window firewall for updating the software without having any issue.
1. To start the process, a user is required to go to the Control Panel
2. Here, a user is required to select system and security
3. Now, a user needs to choose the Windows Firewall option.
4. After that, a user needs to disable the firewall.
We wish the article is helpful for the users to eradicate the Norton antivirus stuck on update Error. But users still having any difficulty and issues, then they can contact the Norton Antivirus support desk. Here users will get the best and simple solutions for all the Norton antivirus related issues and errors. And the executives will help the users to get the best benefit of the Norton antivirus software.
1 note
·
View note
Text
How to Solve the Error Code 5 Issue in Driver Installation?
In some cases, users may come across the error code 5 issue when installing Huion driver on Windows. In this article, we will guide you on how to fix this issue.
Situation 1. When you encounter the issue shown below, please adhere to the following steps to fix it.
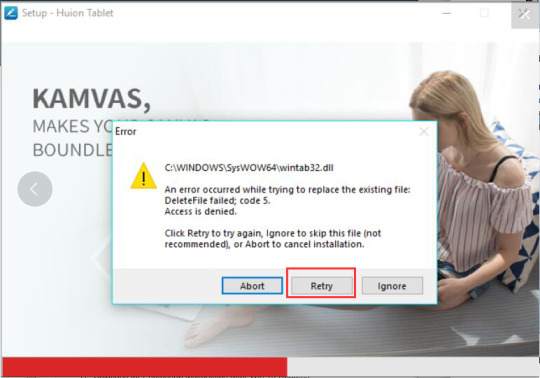
Step 1. Click Local Disk (C:) > find the Huion Tablet file.
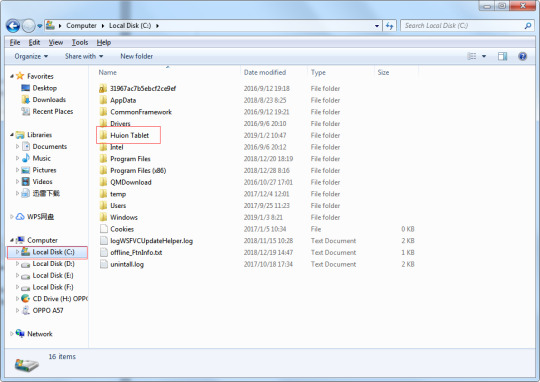
Step 2. Find the checkWintab32.bat in Huion Tablet file and then double-click to launch the checkWintab32.bat file.
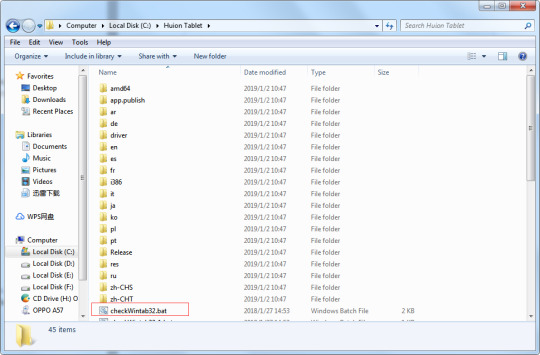
Step 3. Please click the Abort or Retry button, then you can install the driver normally. Remember, please do not click the Ignore button, otherwise, you will be unable to install the driver.

Situation 2. When you come across such an issue shown in the picture below, you can follow the steps below to fix it.
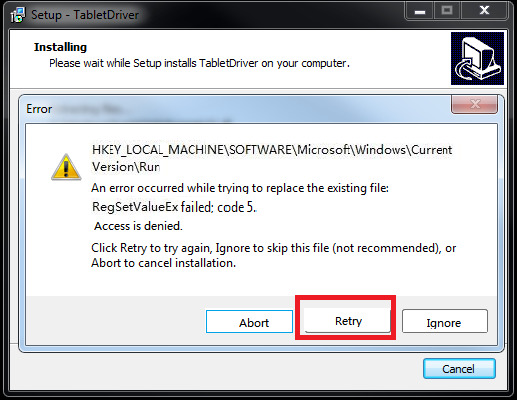
Step 1. Check if Norton or any other anti-virus software is running. If necessary, exit or quit the anti-virus software.
Method to quit the anti-virus software (Take Norton as an example):
Click Start >Type Norton and search > Click Uninstall Norton
Step 2. Click Local Disk (C:) > find the Huion Tablet file.

Step 3. Find the checkWintab32.bat in Huion Tablet file and double-click to open the checkWintab32.bat file.

Step 4. Please click the Retry button to install the driver. Remember please do not click the Ignore button, otherwise, you will be unable to install the driver.

If the issue still persists after trying the above mentioned methods, please try to reinstall the driver and follow the steps mentioned above again to see if it can help.
6 notes
·
View notes