#RFID tag reader
Explore tagged Tumblr posts
Text
Voda IQ: Advanced Fish Farm Management Software with PIT Tag Reader Integration
In the dynamic world of aquaculture, efficiency and precision are crucial for success. As the demand for sustainable and productive fish farming grows, innovative technologies are reshaping the industry. Voda IQ, a leader in fish farm management software, offers a cutting-edge solution that integrates PIT tag reader technology, revolutionizing how fish farms operate and thrive.

The Importance of Advanced Fish Farm Management
Fish farming, or aquaculture, is a rapidly growing sector, providing nearly half of the global fish supply. However, managing a fish farm is no simple task. It involves monitoring water quality, feeding schedules, health assessments, and ensuring optimal growth conditions for the fish. Traditional methods can be labor-intensive and prone to errors, making advanced management tools essential.
Voda IQ addresses these challenges by offering a comprehensive fish farm management software designed to streamline operations, reduce costs, and enhance productivity. One of the standout features of Voda IQ is its integration with PIT tag readers, a technology that brings unparalleled precision and efficiency to fish tracking and management.
What is a PIT Tag Reader?
PIT (Passive Integrated Transponder) tags are small, electronic devices that can be implanted in fish to provide unique identification. These tags are read by PIT tag readers, which use radio frequency signals to detect and retrieve data from the tags. The use of PIT tags and readers in aquaculture allows for accurate tracking of individual fish, enabling better management of fish health, growth, and breeding programs.
Benefits of Integrating PIT Tag Readers with Voda IQ
Enhanced Tracking and Data Collection
With PIT tag reader integration, Voda IQ offers fish farmers a powerful tool to monitor individual fish throughout their lifecycle. This technology allows for real-time data collection on fish movements, growth rates, and health status. By having detailed records of each fish, farmers can make informed decisions to optimize their operations.
Improved Health Management
Disease outbreaks can devastate fish farms, leading to significant economic losses. Early detection and intervention are crucial. Voda IQ's software, combined with PIT tag readers, enables continuous health monitoring of fish. Any abnormalities or signs of illness can be detected early, allowing for prompt treatment and preventing the spread of disease.
Efficient Feeding Practices
Feeding is one of the most critical aspects of fish farming, directly impacting growth rates and overall farm productivity. Overfeeding can lead to wasted resources and poor water quality, while underfeeding can stunt fish growth. Voda IQ's software can analyze data from PIT tag readers to optimize feeding schedules, ensuring each fish receives the right amount of food based on its specific needs.
Streamlined Breeding Programs
Selective breeding is essential for improving fish stock quality and achieving desirable traits such as faster growth rates and disease resistance. By tracking genetic information and breeding histories using PIT tags, Voda IQ helps farmers implement effective breeding programs. This leads to higher quality fish and more efficient production cycles.
Voda IQ's Commitment to Sustainability
Sustainability is a core value at Voda IQ. By providing fish farmers with advanced tools to optimize their operations, Voda IQ contributes to more sustainable aquaculture practices. The use of PIT tag readers reduces waste, improves resource efficiency, and minimizes environmental impact. Furthermore, better health management and disease prevention lead to healthier fish stocks and more stable ecosystems.
Getting Started with Voda IQ
Adopting Voda IQ's fish farm management software with PIT tag reader integration is a straightforward process. Here are the steps to get started:
Assessment and Consultation: Voda IQ's team of experts will assess your farm's specific needs and provide a tailored solution.
Installation and Training: The software and PIT tag readers will be installed, and comprehensive training will be provided to ensure seamless integration into your existing operations.
Ongoing Support: Voda IQ offers continuous support and updates to keep your farm running smoothly and efficiently.
Conclusion
In the ever-evolving field of aquaculture, staying ahead requires embracing innovative technologies. Voda IQ's advanced fish farm management software, integrated with PIT tag reader technology, offers a game-changing solution for fish farmers. By enhancing tracking, health management, feeding practices, and breeding programs, Voda IQ empowers farmers to achieve greater efficiency, productivity, and sustainability.
0 notes
Text
RFID Tags: Revolutionizing Identification and Tracking

In today's fast-paced world, efficiency and accuracy are paramount. Radio Frequency Identification (RFID) tags have emerged as a game-changing technology, offering a streamlined and reliable solution for identification and tracking across a wide range of industries. These tiny tags, embedded with microchips and antennas, can store and transmit data wirelessly, enabling seamless tracking of assets, inventory, and personnel.
The Significance of RFID Tags
RFID tags have revolutionized various sectors due to their unique advantages:
Enhanced Efficiency: RFID tags eliminate the need for manual scanning or barcode reading, significantly reducing time and labor costs.
Improved Accuracy: RFID tags provide error-free identification, eliminating the potential for human error often associated with manual data entry.
Real-time Tracking: RFID tags allow for real-time tracking of assets, enabling businesses to monitor their inventory and optimize their supply chain.
Versatility: RFID tags can be attached to a wide range of objects, from clothing and electronics to livestock and vehicles, making them a versatile solution for various applications.
A World of Applications
RFID tags have permeated various industries, transforming operations and enhancing efficiency. Here are some notable examples:
Supply Chain Management: RFID tags streamline inventory management, enabling real-time tracking of goods throughout the supply chain, from manufacturing to distribution.
Access Control: RFID tags enable secure access control systems, granting authorized personnel access to restricted areas or buildings.
Asset Tracking: RFID tags are widely used to track valuable assets, such as medical equipment, library books, and industrial tools, preventing theft and loss.
Animal Tracking: RFID tags are employed for animal identification and tracking, providing valuable insights into livestock management, wildlife conservation, and research.
Retail: RFID tags enhance retail operations, enabling efficient inventory management, loss prevention, and personalized customer experiences.
SB Components: Your One-Stop Shop for RFID Tags
SB Components is a leading provider of high-quality RFID tags, catering to the diverse needs of businesses and individuals. Our extensive range of RFID tags includes a variety of frequencies, sizes, and functionalities to suit specific applications.
Whether you're looking to track inventory, manage access control, or enhance customer experiences, SB Components has the RFID tags that meet your requirements. Our expert team is always ready to assist you in selecting the right RFID tags for your unique needs.
Embrace the Future with RFID Technology
RFID tags have revolutionized identification and tracking, offering a powerful and versatile solution for businesses and individuals alike. As technology continues to advance, RFID tags are poised to play an even more significant role in streamlining operations, enhancing efficiency, and improving decision-making across industries.
To explore the vast potential of RFID tags, visit SB Components today and discover the innovative solutions that await you.
#rfid tags#rfid chip#rfid sticker#rfid nfc#rfid labels#rfid in iot#tag reader#rfid tag reader#rfid tag for car#rfid tag price#active rfid#rfid asset tracking#passive rfid tags#rfid tags for inventory#rfid decathlon#active rfid tag
0 notes
Text
Unlock productivity with POXO's advanced RFID technology for real-time tracking, more intelligent inventory management, and a more responsive supply chain.
Watch the full video here: https://www.youtube.com/embed/rIfYrLKvPS8
0 notes
Text
Revolutionizing Asset Tracking with RFID Long-Range Reader Technology

Fast-moving logistics operations and asset management depend on efficiency and precision. The RFID long range reader is one of the primary technological improvements enhancing these operational features. RFID (Radio Frequency Identification) scanning devices differ from standard barcodes through their capability to detect many tags from extended distances, thus enhancing tracking systems. The long-distance readers prove ideal for massive operations such as warehouses, shipping yards, and transportation fleets because they eliminate both time-intensive manual scanning and human scanning inaccuracies.
How RFID Enhances Efficiency
Through RFID technology, organizations can conduct real-time asset tracking that enhances inventory precision, reduces labour costs, and stops asset loss or thievery. The long-range capabilities of RFID readers give them the ability to scan numerous tags at once, regardless of whether assets remain unmoving or move between locations. The automated data flow stream allows businesses to achieve rapid and well-informed choices through this system. RFID systems benefit from seamless connectivity to enterprise software that generates asset-based data, including usage records, tracking information, and maintenance tracking.
Power of RFID Solar Tag
The most remarkable advancement in RFID technology is the RFID solar tag which employs solar power for self-powered tracking operations in external and distant applications. The tags operate using solar power, which enables them to continue functioning longer, thus becoming suitable for difficult battery replacement environments. The tracking system finds practical applications by following shipping containers, mining sites, and construction site equipment. The solar power function allows continuous operation and data transfer without regular maintenance to reduce operational breakdowns and expenses.
Applications across Industries
The RFID technology finds broad implementation in logistics, agriculture, retail and construction fields. Minimal human involvement enables this technology to track vehicles along with livestock and inventory while monitoring equipment through its fields. RFID systems demonstrate versatility by allowing organizations to organize procedures more efficiently and minimize human mistakes, together with productivity increases in multiple operational settings.
Bottom Line
Incorporating solar-powered tags with RFID technology brings a revolutionary change to the innovative and sustainable tracking systems that industries need. Real-time control over business assets is possible due to these systems, which provide exceptional reliability and adaptability. Successful implementation of advanced RFID technology can be done using the innovative solutions offered by Eco Track Systems to address current logistical requirements. As a creative and environmentally conscious company specializing in asset management solutions Eco Track Systems delivers trusted solutions to customers working toward more innovative inventory management systems. For Any inquiry visit at https://www.etsrfid.com/contact-us/
0 notes
Text


The CRUISE2 Industrial-Grade Mobile Terminal, powered by SureTrack by SureSolutions, is a rugged handheld device designed for seamless RFID tracking and inventory management. It runs on Android 14 and features Wi-Fi 6, an octa-core processor, fingerprint recognition, and AI + OCR technology for precise data capture. With IP68 protection and 1.5m drop resistance, it ensures durability in demanding environments. SureTrack by SureSolutions provides this cutting-edge device for fresh produce management, warehousing, and retail operations. Available in long-range (10m), Wi-Fi 6, and standard models, it enhances operational efficiency with real-time tracking and streamlined workflows. https://www.suresolutions.in/category/rfid/
#rfid#rfid technology#rfid solutions#rfid tags#rfid reader#rfid supply chain#rfid antenna#rfid technology solutions#rfid-tags-technology#SureTrack
0 notes
Text
How to Install & Optimize Your RFID Tag Reader System
Introduction
Radio Frequency Identification (RFID) technology has revolutionized asset tracking, inventory management, and supply chain operations. However, the efficiency of an RFID tag reader system depends on proper installation and optimization. In this comprehensive guide, we will walk you through the best practices for setting up and enhancing your RFID reader system to ensure maximum efficiency and accuracy.

Step 1: Understanding RFID Components
Before installation, it’s crucial to understand the essential components of an RFID system:
RFID Tags: These contain embedded microchips and antennas that store data.
RFID Readers: Devices that emit radio waves to communicate with RFID tags.
Antennas: Transmit signals between the tags and the reader.
Middleware & Software: Process and interpret RFID data for integration with business systems.
Step 2: Selecting the Right RFID System
Choosing the right RFID system is critical for achieving optimal results. Consider the following factors:
Frequency Range: RFID operates in different frequency bands: Low Frequency (LF), High Frequency (HF), and Ultra High Frequency (UHF). Choose one based on your operational needs.
Read Range Requirements: Determine whether you need short-range or long-range reading capabilities.
Environmental Conditions: Harsh environments may require ruggedized RFID tags and readers.
Data Storage & Integration: Ensure the system can seamlessly integrate with your ERP or inventory management system.
Step 3: Planning RFID Reader Placement
Proper placement of RFID readers is crucial for ensuring accurate tag detection. Consider these best practices:
Minimize Interference: Avoid placing readers near metallic surfaces, electronic equipment, or sources of radio noise.
Optimize Read Zones: Position antennas strategically to maximize coverage and minimize blind spots.
Test Placement: Conduct a site survey to identify optimal reader locations before final installation.
Consider Orientation: The angle and distance between tags and readers affect read accuracy.
Step 4: Installing RFID Hardware
1. Setting Up RFID Readers & Antennas
Mount readers securely in designated locations.
Connect antennas to readers using RF coaxial cables.
Ensure antennas are aligned properly for maximum signal strength.
2. Deploying RFID Tags
Select Appropriate Tags: Choose tags based on application needs (passive, active, or semi-passive).
Ensure Proper Tag Placement: Place tags where they are easily scannable and not obstructed by materials that can interfere with radio signals.
Test Tag Readability: Before full deployment, test tags under real-world conditions to ensure they are readable from different angles and distances.
3. Connecting to the Network
Connect readers to the local network via Ethernet, Wi-Fi, or Bluetooth.
Configure IP addresses and establish communication with the central server.
Ensure adequate power supply to all components.
Step 5: Configuring & Optimizing the RFID System
After installation, fine-tuning the system ensures optimal performance.
1. Configuring RFID Reader Settings
Adjust read power settings to avoid interference and improve accuracy.
Set up data filtering to eliminate duplicate or incorrect tag reads.
Define read zones to control where and when tags are read.
2. Software Integration
Connect the RFID system to inventory management, asset tracking, or ERP software.
Implement automated data logging and reporting for streamlined operations.
Ensure real-time data synchronization with enterprise systems.
3. Conducting Performance Testing
Run benchmark tests to measure read rates and system efficiency.
Identify and troubleshoot weak signal areas or interference zones.
Conduct stress tests to determine system reliability under high workloads.
Step 6: Maintaining & Troubleshooting Your RFID System
Regular maintenance is essential to prevent downtime and performance issues.
1. Routine Inspections
Check for loose connections, damaged antennas, or misplaced readers.
Ensure RFID tags are intact and not obstructed by environmental factors.
2. System Performance Monitoring
Use RFID analytics tools to monitor tag reads and identify irregularities.
Regularly update firmware and software to keep the system up-to-date.
3. Troubleshooting Common Issues
Interference Problems: Reposition readers and reduce external RF noise sources.
Tag Read Failures: Adjust reader power settings and verify tag placement.
Connectivity Issues: Restart network connections and check system logs for errors.
Conclusion
Installing and optimizing an RFID tag reader system requires careful planning, proper hardware setup, and continuous performance monitoring. By following these best practices, businesses can achieve enhanced tracking efficiency, improved accuracy, and seamless data integration. Implementing these steps will ensure your RFID system operates at peak performance, leading to increased operational efficiency and cost savings.
0 notes
Text
UHF Reader Based on Pico W & ESP32 with 50 Tags/Second Reading within 1.5 Meter Range

A UHF Reader (Ultra High Frequency Reader) is a device that is used to read and write data from UHF RFID tags within the 860MHz-960MHz frequency range. It is a multi tags 50 tags/second reading/writing device within 1-1.5 meter range designed with cutting edge UHF technology. It is a compact, portable and easy to use device.
The UHF reader has 2 variants: one is UHF Reader by Pico W and another is UHF Reader by ESP32. The Pico W variant comes with RP2040 microcontroller with Wi-Fi and BLE support. It is compatible with MicroPython, CircuitPython and Arduino for programming. ESP32 variant comes with ESP32 S3 series microcontroller and has 2.4GHz & Bluetooth 5 (LE) support. It is compatible with Arduino and Espressif IDE for programming.
Key Features and Specifications:
UHF Reader Pico Variant:

Powered by Raspberry Pi Pico W
RP2040 microcontroller dual-core Arm Cortex M0+ microprocessor with 264kB RAM
Supports Wi-Fi and BLE
1.14” TFT display for better visualization
Multi-tone buzzer for audio alerts
Micro USB Support for programming & Type C support for power
3 programmable buttons and Reset button
SD card slot for data storage/transfer
LED Status for power and battery charging
Multipurpose GPIOs breakout for interfacing external peripherals
SWD pins breakout for serial debugging
Supports MicroPython, CircuitPython, and Arduino for programming
UHF Reader ESP32 Variant:

Powered by ESP32 S3 WROOM-1
Dual-core 32 bit LX7 microprocessor with Up to 8 MB PSRAM and up to 16 MB flash memory
Supports 2.4GHz (802.11b/g/n) Wi-Fi and Bluetooth 5 (LE)
1.14” TFT display with ST7789 display driver
Comes with a Read and Write UHF module.
Frequency range of 865.1MHz-867.9MHz (for EU/UK) and 902.25MHz-927.75MHz (for US)
Can Identify 50 tags/second up to the 1.5-meter range.
TTL UART communication interface and communication baud rates 115200bps-38400bps
output power 18-26dBm and output power accuracy +/- 1dB
operation current 180mA at 3.5V (26 dBm Output), 110mA at 3.5V (18 dBm Output)
Multi-tone buzzer for audio alerts
2 user programmable buttons, Boot and Reset buttons
For power and programming support, the Type C Interface
SD Card slot for data transfer/storage
LED status for power and charging
Multipurpose GPIOs breakout for interfacing external peripherals
Supports Arduino and Espressif IDE for programming
By using ESP32 and RP2040, you can build a UHF RFID reader for scan tags and data tracking. This UHF Reader with ESP32 and Pico by SB Components is suitable for applications like warehouses, retail stores, and many other applications where you want to track your inventory data accurately.
#technology#innovation#tech#iot#rfid#uhf#uhf reader#arduino#espressif#iot applications#raspberry pi#rp2040#esp32#projects#programming#ultra high frequency reader#rfid tags#data tracking#electronics
1 note
·
View note
Text
RFID Readers in Toll Collection: Benefits for Highways and Urban Infrastructure
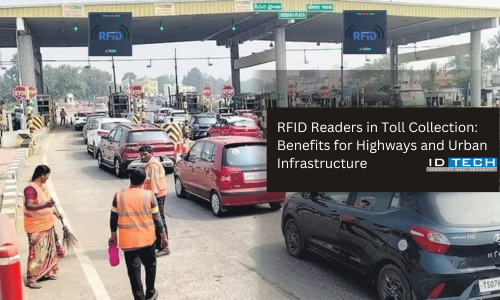
Efficient toll collection is essential to maintaining smooth traffic flow, generating revenue, and enhancing road infrastructure. With increasing vehicle numbers on highways and urban roads, traditional toll systems often struggle to keep pace, leading to congestion, delays, and costly maintenance. RFID (Radio-Frequency Identification) readers are changing the game by providing a seamless, automated approach to toll management, reducing both operational expenses and wait times for commuters.
RFID readers are essential for transforming toll collection and optimizing operations on highways and city roads, leading to greater efficiency and increased revenue for infrastructure authorities. ID Tech Solutions offers high-performance RFID systems tailored to the specific needs of toll collection, ensuring reliable solutions for both national highways and urban tolling points.
Understanding RFID Technology in Toll Collection
RFID technology in tolling works by utilizing RFID tags embedded in vehicles and RFID readers installed at toll plazas. These readers communicate with tags using radio waves to capture vehicle data such as identification number, time of entry, and account information, enabling automatic toll deductions without requiring vehicles to stop.
Types of RFID Systems in Tolling:
Active RFID: In this system, tags are battery-operated and can be read over longer distances. This is especially useful in high-speed highway tolling, where quick, long-range identification is needed.
Passive RFID: Passive tags depend on the reader for power and have a limited reading range. These are commonly used in urban or slower traffic scenarios, such as city toll plazas.
Benefits of RFID Toll Collection for Highways and Urban Infrastructure
1. Efficient Revenue Collection
Reduced Revenue Leakages: Traditional toll systems face challenges such as human errors and cash handling, leading to revenue leakages. RFID-based tolling automates toll collection, reducing the risk of human interference and ensuring accurate revenue collection.
Real-Time Data: RFID readers provide real-time data on vehicle movement and toll collection, enabling accurate and immediate reporting. This allows authorities to track revenue generated in real-time and make data-driven decisions for budgeting and resource allocation.
2. Reduced Maintenance and Operational Costs
Lower Labor Costs: Automated RFID tolling minimizes the need for toll operators, reducing labor costs and associated overhead. This also decreases the risk of fraud or mismanagement, leading to more secure revenue management.
Minimal Infrastructure Wear: RFID tolling reduces the need for physical toll booths and barriers, which are prone to frequent wear and tear. This ultimately results in lower maintenance expenses and longer-lasting infrastructure.
3. Enhanced Traffic Flow and Reduced Congestion
Faster Processing Speeds: RFID technology allows vehicles to pass through toll points without stopping, leading to smoother traffic flow, especially during peak hours. This is particularly beneficial on busy national highways and city roads, where bottlenecks can significantly disrupt travel times.
Reduced Vehicle Emissions: By eliminating stop-and-go traffic at toll booths, RFID tolling reduces vehicle idling time and fuel consumption, contributing to lower carbon emissions and improved air quality around toll plazas.
4. Enhanced Security and Data Protection
Improved Data Accuracy: RFID readers capture vehicle details accurately, minimizing the potential for human error. This provides more reliable data for tracking vehicle usage and toll revenue.
Encrypted Data: Many RFID systems incorporate encrypted data transfer, safeguarding sensitive information about vehicles and payments. Better security is really important for keeping user data safe and making sure the tolling system works properly.
5. Scalability for Growing Infrastructure Needs
Easy Integration with Existing Systems: RFID tolling systems are highly adaptable, allowing seamless integration with other toll management software and infrastructure, such as ANPR (Automatic Number Plate Recognition) and surveillance cameras.
Expandable for Urban and Rural Use: RFID readers can be easily installed across new tolling points, adapting to expanding infrastructure on highways and city roads without requiring significant additional investment.
How FAST Tags are Revolutionizing Toll Collection in India
One of the standout implementations of RFID technology in toll collection is India’s FAST Tags system, which has become synonymous with efficient, cashless tolling across the country. Launched by the National Highways Authority of India (NHAI) and the Ministry of Road Transport and Highways, FAST Tags enable RFID-based toll collection on highways, drastically reducing wait times and congestion at toll plazas.
What are FAST Tags?
FAST Tags are RFID-enabled stickers placed on a vehicle's windshield that allow toll payments to be automatically deducted from a linked prepaid or bank account. When a vehicle equipped with FAST Tags approaches a toll plaza, RFID readers installed at the toll booth scan the tag, authenticate the vehicle, and automatically deduct the toll fee. This seamless process eliminates the need for cash transactions and minimizes the time vehicles spend at toll gates.
Benefits of FAST Tags in Toll Collection:
Reduced Congestion and Wait Times: FAST Tags ensure that vehicles do not need to stop for toll payments, speeding up the tolling process significantly. This is especially advantageous on busy highways where toll queues can extend for kilometers, particularly during peak travel times.
Cashless Transactions for Increased Efficiency: FAST Tags connect straight to your bank or prepaid account, making it super easy to pay without cash. This means you won’t have to deal with the hassle of cash, plus it cuts down on mistakes and fraud that can happen with cash transactions.
Lower Fuel Consumption and Emissions: Vehicles with FAST Tags do not need to idle or accelerate multiple times while waiting in line at toll plazas, leading to less fuel usage and a reduction in emissions. This environmentally friendly benefit is especially impactful given the large volume of vehicles on national highways.
Enhanced Revenue Collection: FAST Tags improve revenue tracking by automating toll collections, reducing revenue leakages that may occur with manual toll handling. This efficiency directly benefits highway authorities, ensuring reliable and accurate revenue for road maintenance and expansion projects.
Integration with Smart Cities and Urban Infrastructure: FAST Tags have expanded beyond highways and are being integrated into parking lots, residential complexes, and other urban infrastructure. This broader application of RFID-based tolling systems shows how FAST Tags can contribute to a more streamlined and digitized city infrastructure.
ID Tech Solutions and FAST Tags-Ready RFID Systems
For toll operators looking to adopt or improve RFID toll collection systems, ID Tech Solutions provides cutting-edge RFID readers and FAST Tags-compatible technology. Our systems are specifically designed to handle the demands of high-speed, high-volume tolling on highways, ensuring accurate and seamless transactions. ID Tech Solutions offers:
Durable RFID Readers compatible with FAST Tags technology to withstand outdoor conditions and high-traffic environments.
High-speed processing capabilities, enabling efficient scanning and verification of FAST Tags stickers even at high vehicle speeds.
Reliable Data Transfer for accurate and secure toll deductions, minimizing the risk of data loss or transaction errors.
As toll collection continues to evolve, FAST Tags and RFID readers represent a shift toward efficient, eco-friendly, and digital tolling systems. ID TechSolutions is at the forefront, helping infrastructure authorities maximize the benefits of FAST Tags technology.
Conclusion
RFID readers and FAST Tags are transforming toll collection by bringing efficiency, reducing congestion, and ensuring a steady revenue stream for highways and city infrastructure. With solutions like ID Tech Solutions, tolling authorities have access to reliable and adaptable RFID technology that meets the unique challenges of modern tolling environments.
For government sectors, national highway authorities, and urban planners, RFID-based toll collection represents a leap forward in managing road infrastructure effectively. By investing in RFID readers and FAST Tags, agencies can streamline operations, reduce maintenance costs, and improve the experience for millions of commuters, all while driving greater revenue for infrastructure projects.
For more information about ID Tech Solutions’ RFID readers and how they can enhance toll collection for your road infrastructure, visit ID Solutions India.
#toll plaza#RFID Solutions for Toll Management#RFID Technology#RFID Tags#RFID Reader#rfid solutions#FAST Tags#FAST Tags for National Highways#RFID Readers for Toll Plazas#Benefits of RFID in Toll Collection
0 notes
Text

RFID READER AND TAG | Tomson Electronics
Unlock the potential of RFID technology - Buy RFID readers and tags online at Tomson Electronics. Explore our selection for efficient and secure data management solutions. Shop now for innovation in connectivity.
0 notes
Text
RFID Technology
The Pervasive Use of RFID Technology: Convenience at a Cost

What is RFID Technology?
RFID technology automatically recognizes and tracks tags affixed to things using electromagnetic fields. These tags can be found as close as a few millimeters or as far away as several meters away from RFID readers, which can read the electrically stored information on them. RFID tags are much more flexible for a variety of applications than barcodes since they may be read without a direct line of sight.
RFID tags come in two primary varieties: passive and active. While active RFID tags have their own power source and can communicate data over greater distances, passive RFID tags depend on the energy from the RFID reader to power the tag and transfer data. RFID is widely utilized in the retail, transportation, logistics, healthcare, and even personal identity systems such as credit cards and passports.
The Convenience of RFID Technology
Unquestionably, RFID technology has improved convenience in a lot of areas of life. RFID tags, for example, facilitate faster checkout times and more effective inventory control in the retail industry. Stock levels can be automatically monitored by stores, which lowers the possibility of out-of-stock merchandise and improves inventory forecasting. On the other hand, customers gain from quicker transactions and shorter checkout lines.
RFID technology is essential for controlling toll collection, operating public transit, and even tracking automobiles for fleet management in the transportation industry. For instance, RFID tags put to vehicles enable automated toll collection, saving drivers from having to pull over and make the payment by hand. In addition to saving time, this lessens traffic jams.
Another industry where RFID technology has shown to be quite beneficial is healthcare. RFID tags are utilized in pharmaceutical inventory management, patient monitoring, and medical equipment tracking. RFID technology lowers the possibility of mistakes in hospitals, such as giving the wrong prescription or misplacing vital medical equipment. This increases overall healthcare facility efficiency while simultaneously improving patient safety.
To Get RFID Technology:JOIN NOW
The Dark Side of RFID Technology
Despite the obvious advantages of RFID technology, there are drawbacks to its extensive application, especially in terms of security and privacy. The same ease of use that draws so many people to RFID technology also renders it vulnerable to abuse and exploitation.
Privacy Concerns
The possibility of illegal access to personal data is one of the biggest issues with RFID technology. RFID tags are frequently incorporated into everyday objects that individuals carry with them, including credit cards, passports, and even clothes. There is a chance that nefarious actors could obtain private information as RFID tags can be read from a distance without the owner’s knowledge or consent.
Think of a situation at a busy mall, for instance. Without your knowledge, someone using a covert RFID reader at the mall may be able to scan the RFID tags on your passport or credit cards and obtain personal information. Fraud or identity theft could then be perpetrated using this information. While RFID tags usually have a restricted range, technological advancements have allowed some RFID readers to read data at longer ranges, which raises the possibility of unwanted access.
Furthermore, there are other applications for RFID technology that people might not even be aware of. For example, retailers employ RFID tags to monitor customer activity, such as the length of time a customer spends in a specific area of the store or the products they pick up and inspect. Although this information is useful for marketing, the collecting and analysis of personal data without express agreement creates serious privacy concerns.
Security Risks
RFID technology poses a number of security vulnerabilities in addition to privacy issues. Among the most well-known is the risk of RFID tag spoofing or cloning. RFID tags use wireless technology to transfer data, which makes it feasible for a malevolent actor to intercept and copy the signal, producing a cloned tag that can be used fraudulently.
For example, if a credit card includes RFID capabilities, it is possible for an attacker to copy the RFID tag on the card and use it to make fraudulent payments. Similar to this, an attacker may copy an RFID badge in an access control system and enter restricted areas without authorization. Attacks of this nature have serious repercussions, especially in places like financial institutions and government buildings where security is vital.
The possibility of denial-of-service (DoS) attacks is another security concern connected to RFID technology. A denial-of-service (DoS) assault occurs when a malevolent party floods an RFID system with signals, preventing it from operating as intended. This might cause serious delays or even put lives in danger by interfering with vital operations in industries like transportation and healthcare.
Mitigating the Risks of RFID Technology
Although RFID technology carries some risks, people and organizations can take a number of precautions to lessen these risks and safeguard their security and privacy.
Enhancing Privacy
The adoption of RFID-blocking materials is one of the best ways to handle privacy concerns. Wallets, sleeves, and bags that block RFID signals are made to prevent unwanted RFID tag scanning. These goods are made of a unique substance that obstructs the radio frequencies needed to read RFID tags, stopping unwanted access to private data.
Apart from adopting physical security measures, people can also reduce the quantity of personal data that is kept on RFID-capable gadgets. To lower the possibility of unwanted access, certain credit card firms, for instance, provide customers the choice to turn off the RFID feature on their cards. Personal privacy can also be greatly enhanced by being aware of the RFID technology incorporated into commonplace objects and by adopting the necessary safety measures.
On the other hand, businesses should put in place stringent data privacy guidelines and make sure that any data collected using RFID technology is done so openly and with the participants’ consent. Retailers and other companies must to educate clients in a straightforward manner about how their data is being used, and if at all feasible, allow them the opportunity to opt out.
Strengthening Security
Investing in encryption and authentication measures is recommended for enterprises to mitigate the security risks connected with RFID technology. The data transmitted by RFID tags is protected from illegal access via encryption, and only authorized RFID readers can access the data thanks to authentication measures.
The use of RFID kill codes is a crucial additional security measure. An RFID tag can be rendered unreadable by permanently deactivating it using a kill code. When there is a chance of unwanted entry or when an RFID tag is no longer required, this can be helpful.
Companies should regularly evaluate the security of their RFID systems in order to find and fix any flaws. This entails making sure that all RFID systems and devices are up to date with the most recent security patches and testing for popular attack vectors like cloning and spoofing.
To Get RFID Technology:JOIN NOW
The Future of RFID Technology
RFID applications are expected to grow much more as the technology develops, posing both new possibilities and difficulties. RFID technology is anticipated to be important in the development of the Internet of Things (IoT), which will allow common things to connect and communicate with each other effortlessly.
But as RFID technology becomes more widely used, strong privacy and security safeguards will also become more important. Like with any technology, the secret is to take a balanced strategy that takes into account both the possible expenses and the convenience of RFID in order to maximize its benefits while limiting its hazards.
Conclusion
Without a doubt, RFID technology has changed many facets of our life and provided unmatched convenience in a variety of sectors, including healthcare and retail. But there is a price for this convenience, especially when it comes to security and privacy. As RFID technology spreads, it is critical to maintain vigilance and take the necessary precautions to guard against potential risks.
We may continue to reap the rewards of this useful tool while protecting our security and personal data by being aware of the hazards connected with RFID technology and putting mitigation measures in place. In an increasingly connected world, it is imperative that we strike a balance between adopting new technologies and preserving the security and privacy that are fundamental to our well-being.
To Get RFID Technology:JOIN NOW
1 note
·
View note
Text
Understanding RFID Protectors: A Comprehensive Guide to Safeguarding Your Personal Information
It is more important than ever to protect our personal information in today’s increasingly digital environment. The risk of unwanted access to our private information has increased with the popularity of contactless payment cards, electronic passports, and other products based on RFID (Radio Frequency Identification) technology. This is the situation in which RFID shields are useful. These straightforward yet powerful gadgets are becoming necessary tools for everyone trying to protect their data from online dangers. We’ll discuss what RFID protectors are, how they function, and why you might need one in this post.
What is RFID Technology?
RFID, or radio frequency identification, is a technology that automatically recognizes and tracks tags affixed to items using electromagnetic fields. These tags have the capacity to hold a variety of data, including your credit card number, passport information, and even health information. RFID is a common technology found in numerous products, such as:
Credit and Debit Cards: A lot of cards now have RFID chips installed, enabling contactless transactions.
Passports: More recent passports come with inbuilt RFID chips that hold biometric and personal data.
Access Cards: To regulate access, a lot of offices and structures employ RFID-enabled access cards.
RFID technology carries some concerns even though it is convenient. Since RFID tags may be read without physical contact, your information could be accessed without your knowledge by someone with the appropriate tools.
Note: Secure your data with a simple shield — because in today’s world, peace of mind is priceless.

The Risks of RFID Technology
The possibility of “skimming,” or unauthorized access to your data, is the main concern connected with RFID technology. Skimming is the process of using a gadget to intercept an RFID chip’s signal and obtain the data that is stored on it. This might result in:
Identity Theft: Your name, address, social security number, and other personal information may be taken and used to open phony accounts.
Financial Theft: Should someone manage to obtain your credit card details, they may use them to make fraudulent transactions or even take money out of your account.
Privacy Invasion: You run the risk of having sensitive information, like medical records or trip itinerary, obtained and exploited against you from RFID-enabled products.
Because of these dangers, it’s critical to keep your RFID-enabled products safe from harm.
What is an RFID Protector?
An RFID protector, sometimes referred to as an RFID blocking card, wallet, or sleeve, is a tool made to stop unwanted access to your data by blocking the electromagnetic fields utilized in RFID technology. The materials used to make these guards put an obstruction between the RFID chip and any possible skimming equipment. Typical varieties of RFID shields consist of:
RFID Blocking Wallets: Wallets with integrated RFID blocking technology are known as RFID blocking wallets. They have an additional layer of security but still look and work like standard wallets.
RFID sleeves: You can slip your passports or credit cards into these slender, protective sleeves. They are simple to carry and small in weight.
RFID blocking cards: You can carry these cards in your wallet with your regular cards. By emitting a signal that interferes with RFID signals, they prevent skimmers from accessing your personal information.

How Does an RFID Protector Work?
Materials that can obstruct or jumble the electromagnetic fields needed to read RFID tags are utilized in RFID protectors. These substances, which are frequently composed of metals like copper or aluminum, enclose the RFID chip in a Faraday cage. A Faraday cage is a device that, by dispersing charge throughout the cage, blocks electromagnetic fields and keeps them from reaching the objects inside.
An RFID protector will cover an RFID-enabled device, like a credit card, from external electromagnetic fields when the protector is placed within it. This implies that your information will be protected even if someone tries to access it by using a skimming device to scan your card.
Why You Might Need an RFID Protector
While not necessary for everyone, an RFID protector can offer additional security and peace of mind for some. The following are some explanations on why you should use an RFID shield:
1. Frequent Traveler
If you travel a lot, especially abroad, you probably have an RFID chip in your passport. Your personal and travel information can be protected from unwanted access with an RFID protector, which is especially crucial in crowded places like train stations and airports.
2. Concerned About Identity Theft
An RFID protector can offer an additional degree of protection if identity theft is a worry. Your driver’s license, credit cards, and any other RFID-enabled objects you carry with you can all be better protected.
3. Regular Use of Contactless Payment Cards
Use of contactless payment cards increases your vulnerability to skimming. Your financial information is protected and fraudulent transactions can be avoided with the use of an RFID protector.
4. Carrying Sensitive Information
An RFID protector can help keep sensitive information safe if you carry any things containing RFID chips that hold data, such as access cards or medical records.
Types of RFID Protectors
There are various kinds of RFID protectors available, and each has benefits of its own. Here are a few of the most well-liked choices:
1. RFID Blocking Wallets
These wallets are available in a variety of designs and materials, including as leather and synthetic fabrics, and have integrated RFID-blocking technology. Because they combine the features of a standard wallet with the extra security of RFID protection, RFID-blocking wallets are practical.
2. RFID Sleeves
RFID sleeves are thin, light covers that fit over individual credit cards and identification cards. For those who wish to safeguard particular goods without changing their entire wallet, they are perfect. RFID sleeves are simple to use and reasonably priced.
Note: Secure your data with a simple shield — because in today’s world, peace of mind is priceless.
3. RFID Blocking Cards
The purpose of RFID blocking cards is to fit them in your wallet with your other cards. Any attempt to scan your cards is interfered with by a signal they generate. If you want to maintain the security of RFID blocking but still want to use your existing wallet, these cards are a suitable choice.
4. RFID Blocking Purses and Bags

How to Choose the Right RFID Protector
How to Choose the Right RFID Protector
Take into account the following elements while selecting an RFID protector:
1. Quality of Material
The RFID protector’s material quality is very important. Seek for shields composed of premium metals such as copper or aluminum, which are renowned for their potent electromagnetic shielding capabilities.
2. Size and Compatibility
Make sure the items you wish to protect are the proper size for the RFID protection. For example, seek for an RFID wallet or sleeve made specifically to handle passports if you need to protect one.
3. Style and Design
RFID guards are available in a range of shapes and sizes, from beautiful and traditional to sleek and contemporary. Select the option that best fits your tastes and style.
4. Durability
It’s critical to select an RFID protector that is robust and resistant to normal wear and tear because you will be utilizing it on a regular basis.
5. Brand Reputation

Common Myths About RFID Protectors
There are a number of false beliefs and misunderstandings regarding RFID shields that could be confusing. Let’s address a few of the most prevalent ones:
1. Myth: Only Expensive RFID Protectors Work
Factual statement: Efficacy cannot always be determined by price. Numerous reasonably priced RFID protectors are equally effective as more costly ones. The secret is to seek excellent content and reviews.
2. Myth: RFID Skimming is Extremely Common
Factual statement: RFID skimming is not as frequent as some people think, yet it is still a possible hazard. But there is still a chance, particularly for frequent travelers and those who use contactless transactions.
3. Myth: All RFID Chips Are Vulnerable to Skimming
Factual statement: Not every RFID chip is susceptible to skimming. Modern technologies employ encrypted transmissions, which are considerably more difficult to intercept. Many older RFID chips are still susceptible, though.
4. Myth: You Can Use Any Metal Object as an RFID Protector

Final Thoughts
RFID protectors provide a quick and easy solution to protect our data in a time when unlawful access to our personal information is becoming more common. An RFID protector can give you extra security and peace of mind whether you’re worried about identity theft, travel frequently, or use contactless payment cards on a regular basis. To make sure the RFID protector you select suits your demands, take into account the product’s type, quality, and durability. Even while RFID skimming isn’t the most frequent type of data theft, it’s still a risk that should be avoided, particularly as RFID technology spreads. Purchasing a trustworthy RFID protector is a simple action that can significantly impact the security of your personal data. By remaining knowledgeable, When exercising prudence, you can take advantage of RFID technology’s convenience without having to worry about possible risks.

1 note
·
View note
Text
0 notes
Text
5 Facts You Need To Know About Active RFID Readers

In the rapidly evolving world of RFID technology, Active RFID readers stand out for their exceptional capabilities. Whether you’re new to RFID or looking to upgrade your system, understanding the benefits and features of active RFID readers can help you make informed decisions. Here are five essential facts about Active RFID readers that you need to know.
0 notes
Text
#alphatechsusa#cafeteria keypads#cafeteria pin pads#school cafeteria keypads#school lunch keypads#school cafeteria pin pads#alphatechs usa#keypads#cafeteria keypad#custom keypads#rfid#rfid tags#rfid technology#rfid reader#rfid solutions
0 notes
Text
How Does RFID Work?
RFID relies upon three main elements to function efficiently: 1. RFID Tags: Attached to the item or asset to be tracked. Tags are available in two types:
Passive tags: Powered by the reader's signal.
Active Tags: Self-powered, so they can be read over larger distances for viewing.
2. RFID Readers: These send out radio waves, which can interrogate the data stored on the RFID tag. The readers can be handheld or permanently placed at such points as turnstiles or conveyor belts. 3. Middleware/Software RFID: Reader captures data and middleware processes it to interface with databases or software applications to manage, store, and analyze the RFID.

#rfid#rfid tags#rfid technology#rfid reader#rfid supply chain#rfid technology solutions#rfid teg technology#rfid system#rfid market
1 note
·
View note