#ApplicationSecurity
Photo

Backend Developer Complete Roadmap😉⭐️ 👉Learn the fundamentals of software supply chain security with questions and answers 🌟🌟🌟 https://amzn.to/3Z3iFOg #applicationsecurity #cloudsecurity #iot #iotsecurity #dataprivacy #datasecurity #mobilesecurity #cognitivesecurity #automationsecurity #applicationsecuritytesting #portprotocol #datagovernance #smartcar ##networksecurityengineer #mobilesec #smartcarsecurity #pythonprogramming #pyhtonlearning #networksecurity #cybersecurityexpert #portsecurity #pythonprojects #datasecurityconsulting #blockchainprogramming #blockchaincybersecurity #bigdatasecurity #dataprivacyjobs #developerjobs #cybersecurityexpertcourses (at India) https://www.instagram.com/p/Cm1jNXPvraC/?igshid=NGJjMDIxMWI=
#applicationsecurity#cloudsecurity#iot#iotsecurity#dataprivacy#datasecurity#mobilesecurity#cognitivesecurity#automationsecurity#applicationsecuritytesting#portprotocol#datagovernance#smartcar#networksecurityengineer#mobilesec#smartcarsecurity#pythonprogramming#pyhtonlearning#networksecurity#cybersecurityexpert#portsecurity#pythonprojects#datasecurityconsulting#blockchainprogramming#blockchaincybersecurity#bigdatasecurity#dataprivacyjobs#developerjobs#cybersecurityexpertcourses
2 notes
·
View notes
Photo
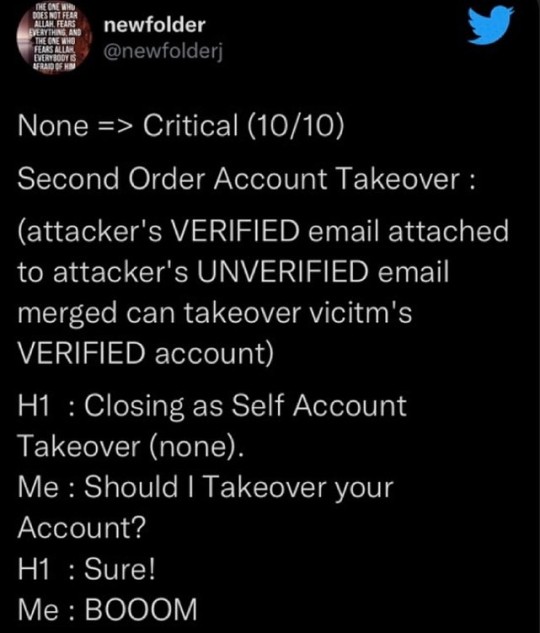
Daily Tweets. #tweets #tweetsfromtwitter #hackertweet #hackerinstagram #biohacking #applicationsecurity #lifehacks #mobilehacks #penetrationtesting #offensivesecurity https://www.instagram.com/p/ClRSbmVy0Mq/?igshid=NGJjMDIxMWI=
#tweets#tweetsfromtwitter#hackertweet#hackerinstagram#biohacking#applicationsecurity#lifehacks#mobilehacks#penetrationtesting#offensivesecurity
4 notes
·
View notes
Text

#cybersecurity#electronicinformationsecurity#informationtechnologysecurity#networksecurity#applicationsecurity#datasecurity#operationalsecurity#cloudsecurity
1 note
·
View note
Text

Looking for a holistic approach to security? At #RoundTheClockTechnologies, we deliver end-to-end testing that covers all aspects of the security framework. Our multi-layered defense strategies provide comprehensive protection for different organizations.
We customize our solutions to meet specific needs, addressing unique challenges and vulnerabilities. With our Security Testing Services, organizations benefit from a robust and resilient security posture that adapts to the ever-changing threat landscape.
Learn more about our security testing services at https://rtctek.com/security-testing-services
#rtctek#roundtheclocktechnologies#securitytesting#securitytestingservices#applicationsecurity#endtoendtesting#multilayereddefense#customisedsolutions
0 notes
Text

Ensure robust application security with Vulnerability Scanning, Penetration Testing, SAST, and DAST to identify, prevent, and address security threats in real-time.
#SecurityTesting#VulnerabilityScanning#PenetrationTesting#SAST#DAST#ApplicationSecurity#CyberSecurity#SecureApps
0 notes
Text
#ApplicationGateway#NetworkSecurity#TechSolutions#ApplicationSecurity#GatewayTechnology#CloudSecurity#NetworkInfrastructure#TechTrends#CyberSecurity#ApplicationManagement#GatewaySolutions#ITInfrastructure#NetworkManagement#SecureAccess#TechInnovation#CloudComputing#NetworkTech#ApplicationProtection#ITSecurity#SecuritySolutions
0 notes
Text
Critical .NET Security Updates Released for July 2024
Remote Code Execution Vulnerabilities in .NET 6.0 and 8.0
Denial of Service Vulnerabilities affecting .NET 8.0
As developers, it's crucial that we stay on top of these security patches to maintain the integrity and safety of our applications. Failing to update could leave our systems exposed to potential attacks.The .NET team has been hard at work to identify and resolve these issues, and we commend their commitment to keeping the framework secure. 👏If you haven't already, make sure to update your .NET 6.0 and 8.0 installations as soon as possible. The stability and protection of our applications depend on it!
Check out www.whiztekcorp.com
#.NETSecurity#CriticalUpdates#RemoteCodeExecution#DenialOfService#ApplicationSecurity#DeveloperSafety
1 note
·
View note
Text
OASIS Open's push for a software supply chain standard: All together now?

OSIM aims to build a unifying framework incorporating existing SBOM data models, including CSAF, CycloneDX, OpenVEX, and SPDX
https://tinyurl.com/38kjaf8b
0 notes
Text
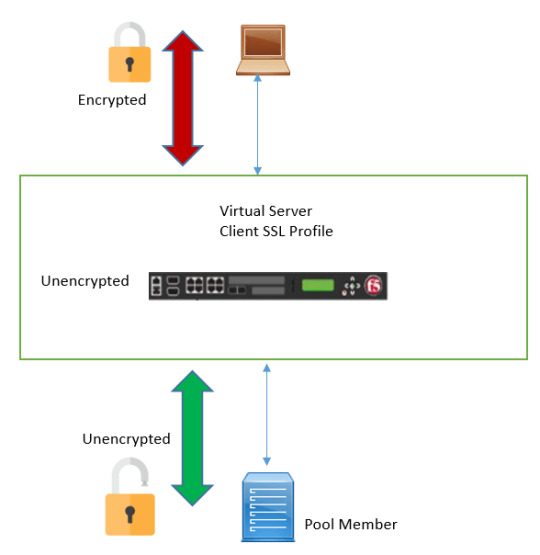
Master SSL traffic management and optimization techniques for secure and efficient data transmission. Ensure robust security and performance in your network infrastructure. https://www.dclessons.com/f5-ssl-traffic
#BIGIP#F5Networks#iRules#NetworkAutomation#ApplicationDelivery#LoadBalancing#NetworkManagement#ITInfrastructure#NetworkSecurity#ITTraining#TrafficManagement#NetworkEngineering#ApplicationSecurity
0 notes
Text
F5 Recognized As API Security Visionary By Enterprise Management Associates

F5 is a top player in keeping cloud applications secure and delivering them. They were recently named a visionary in API security by Enterprise Management Associates (EMA) in their Vendor Vision 2024 report. F5's Distributed Cloud Web App and API Protection (WAAP) solution was singled out as a must-see security solution at the RSA Conference 2024 in San Francisco.
The report commends F5 for their thorough approach to API and application security, which means customers don't have to juggle different API security solutions. F5 is recognized for leading the way in API security, developing, promoting, and continuously enhancing API security to make the security world take notice.
API security is a big challenge for companies as they use AI and offer more AI-powered services. APIs, which link modern applications, are now prime targets for cybercriminals. In fact, 81% of the attacks stopped by F5 Distributed Cloud Services in the first quarter of 2024 were aimed at APIs.
Chuck Herrin, Field CTO for API Security at F5, stresses the importance of making API security simpler, quicker, and more accessible for customers. He highlights the need for end-to-end solutions that can keep pace with the rapid development of AI without needing complex deployment and management processes.
Read More - https://www.techdogs.com/tech-news/business-wire/f5-recognized-as-api-security-visionary-by-enterprise-management-associates
0 notes
Link
0 notes
Text
Unlocking Business Potential: A Guide to Cloud Application Development Services
In the rapidly evolving landscape of technology, businesses are constantly seeking innovative solutions to stay competitive and foster growth. One of the key enablers of this transformation is the adoption of Cloud Application Development Services. In this comprehensive guide, we'll explore how these services can unlock the full potential of your business.
Understanding Cloud Application Development
1. The Basics of Cloud Application Development
Discover the fundamental concepts behind cloud application development, including the shift from traditional on-premises solutions to scalable and flexible cloud-based architectures.
2. Advantages of Cloud Application Development Services
Explore the myriad benefits, from cost efficiency to improved collaboration, that businesses can gain by leveraging cloud application development services.
Choosing the Right Cloud Platform
3. Navigating Cloud Platforms: AWS, Azure, Google Cloud
An in-depth comparison of major cloud platforms to help you make an informed decision on selecting the one that aligns with your business goals and requirements.
4. Cloud-Native Development Strategies
Learn about the principles of cloud-native development and how they contribute to increased agility, scalability, and overall business efficiency.
Best Practices for Successful Implementation
5. Security in Cloud Application Development
A guide to implementing robust security measures, addressing common concerns, and ensuring the confidentiality and integrity of your applications and data.
6. Achieving Cost Optimization
Explore strategies for optimizing costs in cloud application development, including resource allocation, monitoring, and adopting serverless architectures.
Realizing Business Impact
7. Case Studies: Success Stories in Cloud Application Development
Dive into real-world examples of businesses that have successfully harnessed cloud application development services to achieve transformative results.
8. Future Trends and Innovations
Stay ahead of the curve by exploring emerging trends and innovations in cloud application development, such as edge computing, artificial intelligence integration, and more.
Conclusion
As businesses strive to unlock their full potential, embracing cloud application development services becomes not just a choice but a strategic necessity. This guide aims to provide you with the insights and knowledge needed to embark on this transformative journey, ensuring that your business remains agile, scalable, and ready for the challenges of the future.
#CloudApplicationDevelopment#BusinessTransformation#CloudServices#TechInnovation#DigitalTransformation#CloudPlatforms#TechGuide#CloudSecurity#CostOptimization#CloudNativeDevelopment#BusinessSuccess#CaseStudies#FutureTech#AgileBusiness#InnovationInTech#CloudComputing#TechTrends#ApplicationSecurity#BusinessEfficiency#DigitalStrategy
1 note
·
View note
Text
0 notes
Text
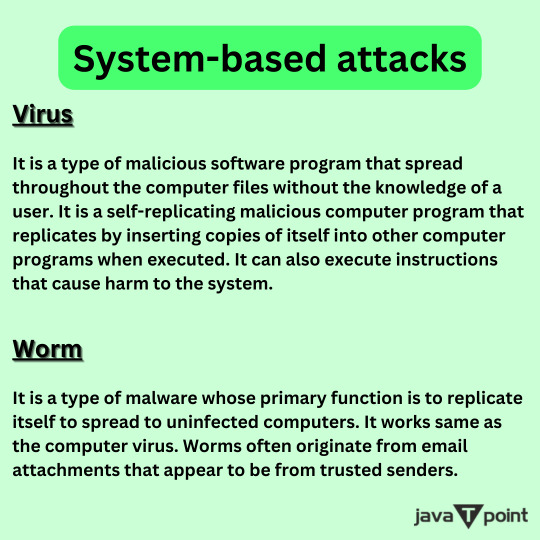
System-based attacks
.
.
.
.
for more information and tutorial
https://bit.ly/3iNHzkd
check the above link
#cybersecurity#mobilesecurity#dnsattack#romancescam#dridexmalware#webbasedattck#systembasedattacks#applicationsecurity#databse#dbms#computerscience#computerengineering#javatpoint
0 notes
Text

Wondering how to detect and neutralize advanced threats? At #RoundTheClockTechnologies, we deliver advanced threat detection services that leverage AI-driven tools.
Our real-time alerts inform organizations of suspicious activity, allowing for swift action. By adopting a proactive defense approach, we anticipate potential threats and neutralize them before they cause harm.
Our commitment to using the latest technology ensures that the organization remains protected against even the most sophisticated cyber threats.
With our #SecurityTestingServices, organizations can rest assured that their digital assets are in safe hands.
Learn more about our Security testing services at https://rtctek.com/security-testing-services
#rtctek#roundtheclocktechnologies#securitytesting#cybersecurity#applicationsecurity#pentesting#vulnerabilityassessment
0 notes
Text
In the code section, we are performing password hashing and verification using the SHA-256 algorithm. Let's go through the comments added to the code and understand their purpose:
/* * © 3:03pm/Tue/Oct/17/2023 Your Raymond Sedrick Leslie II * All rights reserved. * This code is released under the MIT License. * *𝖈𝖔𝖒.𝖘𝖆𝖋𝖙𝖞𝕱𝖎𝖗𝖘-𝖕𝖗𝖔𝖉𝖚𝖈𝖙𝖎𝖔𝖓𝖘 * * 𝕿𝖍𝖊 𝖕𝖚𝖗𝖕𝖔𝖘𝖊 𝖔𝖋 𝖙𝖍𝖎𝖘 𝖈𝖔𝖉𝖊 𝖎𝖘 𝖙𝖔 𝖒𝖆𝖐𝖊-𝖘𝖔𝖈𝖎𝖆𝖑-𝖒𝖊𝖉𝖎𝖆-𝖘𝖆𝖋𝖊-𝖆𝖘-𝖘𝖍𝖔𝖚𝖑𝖉-𝖇𝖊-𝖘𝖔-𝖚𝖘𝖊𝖗𝖘-𝖆𝖈𝖗𝖔𝖘𝖘-𝖙𝖍𝖊-𝖌𝖑𝖔𝖇-𝖈𝖆𝖓-𝖘𝖆𝖋𝖑𝖞-𝖒𝖊𝖊𝖙-𝖓𝖊𝖜-𝖋𝖗𝖎𝖊𝖓𝖉𝖘-𝖜𝖎𝖙𝖍-𝖓𝖔-𝖜𝖔𝖗𝖗𝖎𝖊𝖘-𝖔𝖋-𝖋𝖆𝖐𝖊-𝖘𝖈𝖆��𝕬𝖗𝖙𝖎𝖘𝖙𝖊𝖘𝖙.*/ i
mport org.mindrot.jbcrypt.BCrypt; class PasswordUtils { public static…
View On WordPress
#3reddit9.wordpress.com#InvocationHandler#AIInnovation#android#ApplicationSecurity#BlockingIPinJava#bullies#BullyingPrevention#ChildProtection#Coding#Coding Programming#computerScience#Cybersecurity#Cybersecurity JavaDevelopment#DataScience#DataSecurity#DevSecOps#EmailBlocker#Errors#highSpeed#InformationRetrieval#infoSec#IPAddressBlocking#IPBlocker#IPBlocking#IPFiltering JavaProgramming#java#JavaApplication#javaCode#JavaDevelopment
0 notes