#Rootkit detection
Explore tagged Tumblr posts
Text
SpyHunter
SpyHunter is a powerful tool for detecting and removing the latest spyware, trojans, rootkits, ransomware, keyloggers, and other malicious software on Windows PCs. Designed for everyday users, SpyHunter provides an effective solution for identifying and eliminating harmful threats. Developed by Enigma Software, SpyHunter specializes in detecting and removing various forms of malware, such as…
#anti malware#Custom malware fixes#Cybersecurity#Keyloggers#malware removal#ransomware protection#real-time protection#Rootkit detection#Software review#SpyHunter#Spyware protection#Technical support#Trojans#Windows Security
1 note
·
View note
Text
fuckin Valorant anti-cheat rootkit demands that you use secure boot if it detects that you're on Windows 11, fuck you fuck you fuck you. Secure Boot more like I'll make my boot secure in your ass. How do I convince my friends to play a less desperately annoying piece of software.
#video games#valorant#i do not feel like manually signing my Arch install and i dont want to fuck around in the BIOS just to play a video game
82 notes
·
View notes
Text
I'm no longer gonna be able to comfortably play my special interest, which fucking sucks. Rant under cut. It's about League of Legends and Riot's anti-cheat software, Vanguard, if you're interested.
Riot Vanguard (vgk) is a kernel-level software that scans all of a system's processes to detect cheat engines, which itself is fine - industry standard - except it boasts a particular effectiveness due to how it's run. Vgk runs on start-up so that it's running before a user has the chance to launch a cheat engine, and it can ID hardware so that if a player is caught cheating, they won't be able to play again on the same device. Unless it is disabled manually, it will run 24/7, whereas other AC software will start and stop in line with the game's execution.
It's more effective than other AC software, but it absolutely bricked some PCs back upon its initial release when Valorant dropped in 2020. This was a new game, fresh code, but the anti-cheat borders on a fucking rootkit - a term I'm using liberally, because vgk isn't malware, but it works in the same way on a systemic level. Equally as invasive, and can potentially be equally as destructive; one of those is intended, and the other is an unfortunate by-product of invasive software being developed by a video game company.
League of Legends is a 15 year old game with some pretty tragic code. If vgk caused people to bluescreen after exiting Valorant, then even more people are going to encounter issues with the shitshow that is LoL's code base.
Three weeks ago, an attempt to fix a bug regarding an in-client feature fucked over a far more significant API in several major servers. Every time a particular game-mode called "Clash" launches (every other month or so), it bricks the servers. This is currently a running gag in the community: that whenever the client acts up (embarrassingly often for such a well-funded game) Riot must be dropping Clash early. But when you introduce a bloody rootkit into the mix that runs in tandem with spaghetti code and beyond the closing of the game app, this is going to undoubtedly fuck some computers up.
I'm not someone who cheats at games, but I care about my system too much to risk this. Something that relies on the BIOS, that is known to have caused permanent damage to systems while running alongside a much better programmed game, that continuously scans your system while it's active (and always activates upon start-up until disabled) is obscenely risky. With a 24/7 invasive software, it can disable drivers regardless of what you're playing and when; the worst cases - plural - I've read about anecdotally were people's cooling systems being disabled erroneously by vgk, causing gpu melting. You bet any antivirus software you have installed is going to scan without pause because of it, which will cause more system-wide performance issues, too.
There's also the (albeit minor) risk of other scripts triggering the uh-oh alarm and leading to unfair account bans, and I've poured almost 7 years into this game. I mod some of my single-player games and write scripts. No thanks.
And while I'm lucky enough to have a decent system, the TPM 2.0 and secure boot requirement for Windows 11 users means that vgk will effectively - while the phrase is crude, I haven't seen a concise alternative - "class-ban" League players. Similar to the release of OW2, where a unique SIM was required for every account, including existing ones until that got changed after enough backlash - except buying a phone number is far cheaper than buying a laptop or PC. Even with the requirements, the performance issues will tank low-end systems, which would already be at higher risk of hardware fuckery from increased and extended cpu usage. And the game is currently designed to be comfortably playable on low-end rigs, so it will force-out a good number of players.
If you play League and intend to continue playing after vgk is made mandatory in Jan/Feb 2024, give it a few months after it goes live before you play. That's enough time for any catastrophic issues to unfold, because if the testing period was anything like it is for game features, it won't be sufficient, and the number of cases of system damage will be worse than it was for Valorant upon release.
This rant does read like I'm trying to dissuade people from playing post-vgk, and I'm not, but I am urging people to be cautious and informed on the legitimate controversies surrounding Vanguard, especially anything hardware related. Familiarise yourself with how the program works and assess whether your system will likely be affected, and how permanent any damage could be to your hardware. Read forums (that aren't moderated by Riot employees where possible) and verify the information you're reading. Including this. It's 3:30am and I'm writing this angrily, so my limited explanations of the software could stand to be more thorough.
I'm hoping that there will be enough of a reduction in League's ~200m monthly player-base to spark a reversal in the decision to implement vgk. Not out of consideration for people who don't want to install a rootkit for a video game, but because Riot would lose money and shit their corporate britches.
Having to say goodbye to my favourite game, a universe I love and one of the more significant outlets to socialisation in my life absolutely sucks, though. The actual season changes looked super cool too, and I was stoked about Ambessa coming to the game. I'll enjoy the game while I can, but yeah this feels like a bitter breakup lmao.
#enforcing a rootkit to ban a few xerath mains was not on my 2024 bingo card#i think i've encountered two cheaters in my 7 years of playing#rant post#league posting
8 notes
·
View notes
Text
Why does every multiplayer game need kernel-level anti-cheat now?!
Why does every multiplayer game need kernel-level anti-cheat now?! Is it just me worrying, or has it become literally impossible to play a multiplayer game these days without installing some shady kernel-level anti-cheat?I just wanted to play a few matches with friends, but nope — “please install our proprietary rootkit anti-cheat that runs 24/7 and has full access to your system.” Like seriously, what the hell? It’s not even one system — every damn game has its own flavor: Valorant uses Vanguard, Fortnite has Easy Anti-Cheat, Call of Duty uses Ricochet, and now even the smallest competitive indie games come bundled with invasive kernel drivers.So now I’ve got 3 or 4 different kernel modules from different companies running on my system, constantly pinging home, potentially clashing with each other, all because publishers are in a never-ending war against cheaters — and we, the legit players, are stuck in the crossfire.And don’t even get me started on the potential security risks. Am I supposed to just trust these third-party anti-cheats with full access to my machine? What happens when one of them gets exploited? Or falsely flags something and bricks my account?It's insane how normalized this has become. We went from "no cheat detection" to "you can't even launch the game without giving us ring-0 access" in a few short years.I miss the days when multiplayer games were fun and didn't come with a side order of system-level spyware. Submitted May 30, 2025 at 07:19PM by Chillzzzzz https://ift.tt/CfhYsIa via /r/gaming
0 notes
Text
APT41’s Actions Highlight the Need for Threat Monitoring

This blog post discusses malware attack chain technology, delivery tactics, and other APT41 operations. We also explain indications of compromise (IOCs) to help security professionals protect against similar attacks. GTIG used customised detection signatures, stopped attacker-controlled infrastructure, and strengthened Safe Browsing to defeat this attempt.
APT41
APT41, a Chinese cyber threat group, commits both commercial cybercrime and state-sponsored espionage. Group uses modern espionage software for its own gain. China promotes its economic interests through high-tech and healthcare strategic espionage and profits from video gaming. APT41 is skilled, persistent, and agile, using malware, supply chain breaches, and spear-phishing. Cybercrime and government are complex, as APT41's criminal acts may have government ties.
Chinese Cyber Group APT41 Blends Personal Crime with State Espionage
According to a detailed FireEye Intelligence study published on Google Cloud Blog, APT41, a well-known Chinese cyber threat cell, is purportedly conducting state-sponsored espionage and financially driven operations. This group is notable among China-based entities being watched because it appears to exploit private malware, generally used for espionage, for personal gain. Evidence suggests APT41 has been committing cybercrime and cyberespionage since 2014.
APT41's espionage targets match China's five-year economic growth goals. They have established key access to telecommunications, high-tech, and healthcare companies. Targeting telecom firms' call record data and targeting news/media corporations, travel agencies, and higher education institutions shows that the organisation tracks people and conducts surveillance. APT41 may have targeted a hotel's reservation systems before Chinese authorities came for security reconnaissance.
APT41 has targeted the video game sector with ransomware and virtual currency manipulation. They can switch between Linux and Windows to reach game production environments. The cryptographic certificates and source code needed to sign malware are taken from these settings. Importantly, it has used this access to put malicious code into trustworthy files and disseminate them to victim firms using supply chain breach techniques.
These supply chain compromises have defined APT41's most notorious espionage. APT41 restricts the deployment of follow-on malware in multi-stage operations by matching against unique system IDs, considerably obfuscating the intended targets and limiting delivery to only the targeted victims, notwithstanding the effort.
The malware families and tools used by APT41 include public utilities, shared malware with other Chinese espionage organisations, and unique tools. Spear-phishing emails with HTML attachments often compromise. After entering, they can utilise rootkits, credential stealers, keyloggers, and backdoors. APT41 sparingly uses rootkits and MBR bootkits to mask malware and maintain persistence on high-value targets. This adds stealth because the function runs before OS initialisation.
The group is fast and relentless. They quickly find and break intermediary systems to access network portions. In two weeks, they breached hundreds of systems across segments and regions. In addition, they are persistent and quick to adapt. After a victim company makes changes or users download infected attachments, APT41 can gather new malware, register new infrastructure, and re-establish itself in compromised systems across numerous locations within hours.
APT41 may be linked to Chinese-language forum users “Zhang Xuguang” and “Wolfzhi”. These people suggested publicising their skills and services to be hired.
Comparing online gaming goals to APT41's working hours, “Zhang Xuguang” recommended “moonlighting.” These individuals are suspected of espionage due to persona data, programming proficiency, and targeting of Chinese-market online games. Operational activity mapping since 2012 suggests APT41 conducts financially motivated operations outside of workdays.
APT41's originality, expertise, and resourcefulness are shown by their unique use of supply chain breaches, regular use of compromised digital certificates to sign malware, and infrequent use of bootkits among Chinese APT groups. Since 2015, APT41, like other Chinese espionage organisations, has shifted from direct intellectual property theft to strategic information gathering and access management, despite their continued financial interest in the video game sector. As their targeting and capabilities have grown, supply chain compromises in various industries may increase.
APT41 may receive safeguards to conduct for-profit operations or be ignored due to its linkages to state-sponsored and underground markets. They could have also avoided notice. These operations show a blurred line between government and crime, which threatens ecosystems and is exemplified by APT41.
For more details visit govindhtech.com
#APT41#supplychain#cybercrime#Chinesecyberthreat#MasterBootRecord#indicatorsofcompromise#technology#technews#technologynews#news#govindhtech
0 notes
Text
Cybersecurity Incident Response: 7 Steps to Reduce Damage

Cyberattacks are no longer a question of if, but when, with our increasingly hyperconnected world. Any organization—small business, school system, or global enterprise—is at risk of being a victim. With bad guys becoming more innovative each day, the true measure of an organization's cybersecurity resilience is not its defenses but how effectively it can respond to incidents as well.
This is where incident handling in cybersecurity comes in. It is a tested, future-oriented approach that acts on cyberattacks, reduces damage, and gets back to normalcy in the shortest time. Having a documented incident response plan (IRP) guarantees your team reacts instantly and efficiently when the attack strikes.
Let us discuss the seven incident handling steps required to reduce harm and provide business continuity.
1. Preparation: Building the Platform
Planning is the most crucial and initial step toward managing incidents. Planning puts the rest into action and will determine how well your organization fares under stress.
What It Covers:
Possessing an experienced Incident Response Team (IRT) of security professionals, IT professionals, lawyers, and communications leaders.
With cybersecurity tools such as firewalls, antivirus, and threat detection and prevention systems (IDS/IPS), and SIEM (Security Information and Event Management).
Practice and conduct dry runs so that your employees are prepared in case of a disaster.
Conduct and practice dry runs so that your employees are prepared in the event of a disaster.
Arrange for dry runs and prepare in advance so your team is prepared in case of a crisis.
Planning and conducting dry runs so that your team is ready in case of an incident.
Planning converts chaos into a systematized reaction. An effectively systematized team acts fast and quickly, with minimal downtime and little information loss.
2. Identification: Discovering What Occurred
In the event of an incident, the second of the crucial actions is to recognize that it actually occurred. Being aware of it on a timely basis can be the difference between minor deviation and total catastrophe.
Key Actions:
Regular system and network monitoring using automated software to detect abnormal or malicious activity.
Review IDS/IPS system, antivirus software, or SIEM system alerts.
Categorize the incident by type (e.g., malware, insider threat, DDoS attack) and severity.
The earlier a problem is recognized, the earlier it can be contained. Rapid detection stops intruders from digging deeper and causing widespread damage.
3. Containment: Stop the Spread
The instant you have isolated an event, contain it as your top priority. Containing an incident is separating vulnerable systems and eliminating the attacker's access.
Short-Term Containment:
Isolate vulnerable systems from the network.
Block malicious IP address space or domains.
Disable suspicious accounts.
Long-Term Containment
Apply short-term controls like security patches.
Password reset and access control.
Thoroughly search systems for persistence indicators.
A good containment stops the attacker from moving around laterally within your systems, minimizing damage and keeping evidence intact for forensics.
4. Eradication: Threat Removal
Having held off the threat, now it's time to eliminate it from your system. The emphasis here is on eliminating the presence of the attacker along with any malicious artifacts altogether.
Steps to Take:
Delete malware, rootkits, or unwanted software.
assistant
Exploit local vulnerabilities by patching and updating.
Rebuild or rebuild infected systems when necessary.
Conduct a detailed forensic search to establish the entry point of the intruder.
Eradication brings your systems to a clean and secure state once more before going back online. Skipping this process or rushing it can lead to reinfection.
5. Recovery: Back to Normal Operations
Once the threat has been removed, recovery is restoring your systems and services. Recovery needs to be done carefully so that no lingering threat remains.
Restore compromised systems from clean backups.
Monitor restored systems for malicious activity.
Restore systems gradually to the network.
Check for system integrity and operation.
Apply all patches and updates.
Set well-defined Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) to direct your actions. Recovery only occurs after operations are restarted and systems are guaranteed to be safe.
6. Lessons Learned: Analysis and Improvement
Every occurrence is a chance to learn and an opportunity to improve. The lessons learned step is the actual reviewing of what occurred, what worked well, and how to do it better.
Conduct a Post-Incident Review
Why did the occurrence occur?
How effective was the response?
Were roles and responsibilities established?
What failures or bottlenecks did occur?
How can processes or tools be improved?
Record these lessons in an incident report and revise your IRP, policies, or security infrastructure as a result. Sharing lessons with the rest of the team instills a culture of ongoing improvement.
7. Communication: Management of Information Flow
Good communication is the silent hero of incident response much too frequently.
Internal Communication:
Notify internal stakeholders, executives, and affected departments.
Provide regular updates to keep them informed.
External Communication:
Inform customers or users, as applicable, of the breach.
Inform external agencies like CERT-In (India) or GDPR officials (EU).
Cooperate with law enforcement if there is a crime.
Predefined communications and procedures that can be implemented will be a world of difference, with the additional advantage of reducing stress at the time of an event happening.
Equifax was the victim of a 2017 hack that revealed the personal data of over 147 million people. While the attack began with an unpatched vulnerability, the resulting damage was exacerbated by
Lack of preparedness and detection
Delayed responses
Effective public communications
This incident points to the importance of having a clearly defined, proactive incident response procedure.
Final Thoughts
Cyberattacks are inevitable—but being in no position to retaliate is not. It can be a phishing message, ransomware, or insider attack—whichever, the result is in your response.
With a formal seven-step incident response methodology, you can make a potential disaster into a manageable problem:
Preparation
Identification
Containment
Eradication
Recovery
Lessons Learned
Communication
1 note
·
View note
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Detects & Removes Malicious Threats: Blocks Viruses, Spyware, Adware, Trojans, Worms, Ransomware, Hijackers, Parasites, Rootkits, KeyLoggers, and many more. Stops Ransomware In Its Tracks: Protects your files and prevents hackers from holding them hostage. Proprietary Definitions Database & Daily Updates A dedicated threat research team scours the web and analyzes thousands of possible threats, focusing on the hard-to-find ones. The database is updated 8-14 times a day. Multi-Dimensional Scanning A next-generation scanning system that goes beyond the typical rules-based methods. It detects existing threats and analyzes general characteristics and code patterns to identify future threats. Analyzes Your System In-Depth: System Investigator identifies spoofed and malicious files. Easy to Use: Receive notifications when product and database updates are available Stay informed: Review detailed scan logs about detected and removed threats and their locations. USB Data Loss Prevention Data Loss Prevention – Mass Storage toward your data theft, denying access to unauthorized devices. Speedo scanner repair Infected USB’s in minutes and recovers the files which got hidden by virus attacks Intel or AMD x32 / x64 Minimum RAM – : 1 GB Free Disk Space – : 800 MB Windows Xp SP3, Windows Vista, Windows 7, Windows 8, Windows 10 Internet Connection is must for License activation [ad_2]
0 notes
Text
Unlock Powerful Hosting with cPanel Server Management by CloudMinister Technologies
In a digital environment where speed, security, and uptime determine the success of websites and online platforms, effective server management is critical. cPanel Server Management provides a robust foundation for web hosting, but it's the experience and expertise of a professional team that elevates server performance to enterprise-grade reliability.
This is where CloudMinister Technologies steps in—a company known for its dedicated focus on Linux server management, particularly for environments using cPanel and WHM (Web Host Manager). Let’s explore how CloudMinister helps organizations gain maximum value from their cPanel servers.
What is cPanel Server Management?
cPanel is a web hosting control panel that provides a graphical user interface (GUI) and automation tools designed to simplify the process of hosting a website. It allows users to manage files, databases, email accounts, domains, backups, and more—all from a central dashboard.
cPanel Server Management, however, goes far beyond what the software provides out of the box. It involves the continuous monitoring, configuration, optimization, securing, and troubleshooting of servers running cPanel. This ensures the hosting environment remains stable, secure, and high-performing at all times.
About CloudMinister Technologies
CloudMinister Technologies is an India-based IT services company specializing in server management, hosting solutions, and cloud infrastructure. With deep expertise in Linux environments, their team provides managed cPanel services to businesses of all sizes, ranging from solo web developers to enterprise-level organizations.
CloudMinister is recognized for combining technical excellence with responsive customer support, making it a preferred partner for businesses seeking reliable server management.
Key Features of CloudMinister’s cPanel Server Management Services
1. Advanced Security Implementation
Security is a top concern for any server exposed to the internet.CloudMinister applies multiple layers of protection to prevent unauthorized access, malware infections, and denial-of-service attacks.
Their security setup typically includes:
Configuring firewalls like CSF (ConfigServer Security & Firewall)
Installing and tuning ModSecurity (a web application firewall)
Enabling brute-force attack detection via tools like cPHulk
Scanning the server regularly for malware or rootkits
Disabling unused ports and services
Keeping software and kernel versions up to date with patches
This approach significantly reduces vulnerability and helps maintain compliance with security best practices.
2. Server Optimization and Speed Tuning
Out-of-the-box server configurations often aren't optimized for specific workloads or traffic levels. CloudMinister evaluates your server environment and implements performance enhancements tailored to your needs.
This may include:
Tuning Apache, NGINX, or LiteSpeed web servers for faster content delivery
Adjusting MySQL settings for better database response times
Implementing caching mechanisms like Memcached, Redis, or OPcache
Managing PHP versions and optimizing handlers like PHP-FPM
Monitoring resource consumption and load balancing, where necessary
These efforts ensure faster website load times, improved user experience, and better search engine performance.
3. Continuous Monitoring and Alerts
Downtime and service interruptions can affect user trust and business revenue. CloudMinister deploys monitoring tools that check the health of your server and its key services 24/7.
Their monitoring system tracks:
Server uptime and load averages
Web and database service availability
Disk usage and memory consumption
Suspicious activity or spikes in traffic
If any issue is detected, alerts are automatically generated, and their support team takes immediate action, often resolving problems before clients are even aware of them.
4. Automated and Manual Backups
Reliable data backup strategies are essential for disaster recovery and business continuity. CloudMinister sets up both automated and manual backups to safeguard your critical data.
Backup services include:
Daily, weekly, or monthly automated backups to local or remote locations
Snapshot-based backups for entire file systems or virtual machines
Backup integrity checks to confirm recoverability
Disaster recovery support for fast data restoration in case of failure
Clients can request custom backup schedules based on their operational needs.
5. 24/7 Technical Support
CloudMinister offers round-the-clock technical support, including holidays and weekends. Whether the issue is routine or critical, their support team responds promptly to resolve it.
Support includes:
Assistance with DNS, email, FTP, and database issues
Troubleshooting site errors, load problems, and misconfigurations
Help with third-party application installation or integration
Guidance on cPanel and WHM usage for non-technical users
Their support system is designed for fast response and resolution, helping minimize downtime and stress for business owners.
6. Software Installation and Upgrades
In many cases, users need to add new tools or features to their servers. CloudMinister handles software installations, compatibility checks, and upgrades as part of its managed service offerings.
Common installations include:
Content management systems like WordPress, Joomla, and Drupal
E-commerce platforms such as Magento or PrestaShop
Server-side enhancements like ImageMagick, FFmpeg, or GIT
Secure protocol support, including Let’s Encrypt SSL and SSH hardening
Upgrading PHP, MySQL, cPanel, or the operating system when necessary
Each installation is tested to ensure compatibility and optimal performance.
Who Benefits from CloudMinister’s cPanel Server Management?
CloudMinister’s services are suitable for a wide range of users and industries:
Web Hosting Providers benefit from white-label server management and reduced support workload.
Digital Agencies can offer hosting to clients without hiring in-house server administrators.
E-commerce companies enjoy improved performance and secure transactions during peak times.
Startups and Developers get technical expertise without the need for full-time staff.
Large Enterprises can ensure compliance, uptime, and scalable infrastructure with proactive support.
Why Choose CloudMinister Technologies?
The advantages of working with CloudMinister Technologies include:
Certified Expertise: Their team consists of Linux and cPanel-certified professionals with years of experience.
Cost Efficiency: Competitive pricing makes enterprise-grade support accessible to small businesses.
Scalability: Their solutions grow with your business, from shared servers to dedicated infrastructure.
Client-Centric Approach: Support plans are tailored to your actual needs—nothing more, nothing less.
Transparent Reporting: Regular performance and security reports give you insight and peace of mind.
Conclusion
Managing a cPanel server is more than just setting up hosting—it’s about ensuring consistent performance, hardened security, regular updates, and quick support when issues arise. With CloudMinister Technologies, your server is not just managed—it’s optimized, protected, and monitored by experts.
If you're looking for a trusted partner to handle your cPanel Server Management, CloudMinister offers a proven solution that allows you to focus on your business while they handle the backend.
Get in touch with CloudMinister Technologies today and experience professional, worry-free server management.
For More Visit:- www.cloudminister.com
#cloudminister technologies#servers#technology#hosting#information technology#cPanel Server Management
0 notes
Text
PoC rootkit Curing evades traditional Linux detection systems
http://i.securitythinkingcap.com/TKQKzd
0 notes
Text
15 Types of Malware Everyone Should Know About
In today’s digital world, our devices are more connected than ever. While this makes life easier, it also means more opportunities for cybercriminals to attack. One of the biggest online threats is malware. But what is malware? And how can you stay safe from it?
In this blog, we’ll explain 15 different types of malware in simple terms. We’ll also show you how using tools like CoverMeVPN can help protect your personal information and keep you safe online.
What Is Malware?
Malware is short for malicious software. It’s any program or file created to harm your computer, steal your information, or take control of your device without your permission. Cybercriminals use malware to cause problems for people, businesses, and even governments.
Let’s look at the most common types of malware you should watch out for.
The 15 Main Types of Malware
1. Virus
A virus attaches itself to a file or program. When you open that file, the virus spreads to other files on your device. Viruses can damage data, slow down your system, or even delete important files.
Example: A harmful file downloaded from a suspicious email.
Worm
A worm spreads by itself through a network. It doesn't need you to open a file or click a link. Worms often slow down computers and networks by using up resources.
Example: A worm might spread through email contacts and send copies of itself to others.
Trojan Horse
A Trojan horse, or Trojan, looks like a normal file or app. But when you open it, it installs malware secretly. Trojans are often used to steal personal data or give hackers control of your device.
Example: A free online game that secretly steals your passwords.
Ransomware
Ransomware locks your files and demands money to unlock them. It usually asks for payment in cryptocurrency, like Bitcoin.
Example: The famous WannaCry ransomware attack in 2017 affected thousands of companies around the world.
Spyware
Spyware secretly gathers information about you. It can track your keystrokes, watch the websites you visit, and record your passwords.
Example: A program that steals your online banking details while you type.
Adware
Adware shows unwanted ads on your screen. Some adware also collects information about your browsing habits without your permission.
Example: Pop-up ads that appear even when you’re not using your browser.
Rootkit
A rootkit hides deep in your system and allows hackers to control your computer remotely. It’s very hard to detect.
Example: A hacker secretly turning on your webcam.
Keylogger
A keylogger records every key you press. It captures passwords, messages, and credit card numbers.
Example: A hidden program that sends everything you type to a hacker.
Botnet
A botnet is a group of infected computers controlled by a hacker. These computers, called bots, work together to perform tasks like sending spam emails or attacking websites.
Example: A hacker using thousands of infected computers to crash a website.
Fileless Malware
Fileless malware doesn’t install any files. It uses existing programs on your computer to perform harmful tasks, making it hard for antivirus programs to find.
Example: Malware that uses system tools like PowerShell to steal data.
Logic Bomb
A logic bomb is hidden in a program and only activates when certain conditions are met, like a specific date or event.
Example: A malicious code set to delete files on April 1st.
Mobile Malware
Mobile malware attacks smartphones and tablets. It can steal data, track your location, or send premium-rate messages.
Example: A fake mobile app that quietly spies on you.
Scareware
Scareware tricks you by displaying fake virus warnings. It tries to scare you into buying fake software or services.
Example: A pop-up claiming “Your system is infected! Download now!”
Rogue Security Software
A form of scareware, rogue security software pretends to be a real antivirus program. It shows fake alerts and asks you to pay for a solution to problems that don’t exist.
Example: A program claiming you have 500 viruses when your device is clean.
Malvertising
Malvertising uses online ads to spread malware. Even trusted websites can display infected ads without knowing it.
Example: Clicking an ad promising a free prize, which installs malware.
How to Stay Safe from Malware
Staying safe online doesn’t have to be complicated. A few simple habits can protect you from most malware threats:
Always keep your software updated.
Don’t click on suspicious links or attachments.
Use strong, unique passwords for every account.
Backup your important files regularly.
Install reliable antivirus software.
Avoid downloading apps or files from unknown sources.
And here’s a powerful tool to add to your defense:
🌐 Protect Your Privacy with CoverMeVPN
One of the best ways to stay safe online is by using a VPN (Virtual Private Network). A VPN hides your IP address and encrypts your internet connection, making it much harder for hackers to target you.
We recommend CoverMeVPN, a trusted and secure VPN service that shields your online activity from prying eyes. It prevents malware from tracking your location and protects your personal information, especially when using public Wi-Fi networks.
Whether you’re working from home, traveling, or just browsing at a coffee shop, CoverMeVPN adds an extra layer of safety between you and the internet.
Why CoverMeVPN?
Keeps your identity and data private.
Protects you on public Wi-Fi.
Blocks dangerous websites.
Easy to use and fast.
Final Thoughts
Malware comes in many forms, and it’s more common than most people realize. From viruses and worms to ransomware and spyware, these digital threats can cause serious problems. The good news is that by learning about malware and taking simple steps to stay safe, you can avoid most attacks.
Make sure to use strong passwords, avoid suspicious links, and always keep your devices up to date. And for even stronger protection, consider using a VPN like CoverMeVPN to keep your online life private and secure.
By being careful and staying informed, you can enjoy the internet safely without falling victim to malware.
0 notes
Text
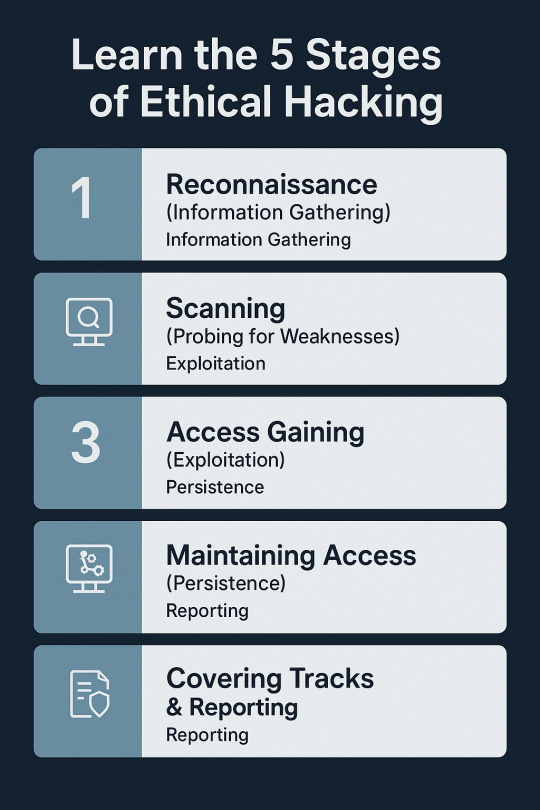
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Certified Ethical Hacker V13 (CEH): The Ultimate Guide to Mastering Ethical Hacking

CEH V13 is among the most sought-after and respected certifications available in the domain of cybersecurity. Introduced and updated by the EC-Council, CEH V13 has been crafted to give IT professionals the skills and information required to recognize, analyze, and eliminate security threats like those posed by malicious hackers. Nevertheless, unlike malicious hackers, certified ethical hackers are taught to utilize their skills legally and ethically in an effort to protect networks and systems.
CEH is popular because it is hands-on, exposing the candidates to real-world environments and a diverse array of hacking tools. The newest version, CEH V13, offers new content with the most current trends in cyber attacks and countermeasures. These include more emphasis on malware analysis, cloud security, incorporating artificial intelligence (AI), and IoT (Internet of Things) security.
Why Get the Certified Ethical Hacker V13 (CEH) Certification?
Increased cybercrime has developed a growing need for professional ethical hackers to assist organizations in defending themselves against data breaches, ransomware, and other security threats. The Certified Ethical Hacker V13 (CEH) certification is the standard for experts who wish to establish a career in cybersecurity.
Through CEH, V13 certification, professionals establish that they are well aware of the five stages of ethical hacking: Reconnaissance, Scanning, Gaining Access, Maintaining Access, and Covering Tracks. By such deep knowledge, certified ethical hackers are able to foretell and prevent hacking activities from being executed, thus making them highly valuable assets to any organization.
Key Features and Changes in Certified Ethical Hacker V13 (CEH)
1. Malware Advanced Threats and Analysis
CEH V13 provides greater insights into new malware threats, such as ransomware, trojans, and rootkits. The course teaches how to detect and neutralize these threats with the use of specialized tools and techniques.
2. Cloud and IoT Security
As the use of cloud services and IoT devices increases, CEH V13 now specifically has modules that cover securing cloud infrastructure and exploiting vulnerabilities in Internet of Things devices. This positions ethical hackers to better resist threats of this era on IoT networks and cloud infrastructures.
3. AI and Machine Learning in Cybersecurity
CEH V13 also integrates AI and machine learning capabilities for advanced threat detection and response. Future CEH V13s are trained on how AI products can automate the process of threat analysis and offer better response times in complex security infrastructures.
4. Practicing with Cyber Range
CEH V13 provides experiential learning by way of simulated Cyber Range, where individuals are provided with a chance to hone skills in real-life situations. Practice is converted into application and theory becomes grounded as it helps in making candidate readiness guarantee solution of real-world problems.
5. Emerging Threats
CEH V13 educates current threats to cybersecurity, such as social engineering, phishing, and insider threats. The course educates identifying and managing threats before causing data breaches.
How to Prepare for Certified Ethical Hacker V13 (CEH)
1. Official CEH Training
The official training sessions are provided by the EC-Council, such as instructor-led, online, and self-study. Attending an official course ensures you learn everything about the exam topics and have hands-on practice.
2. Hands-on with Ethical Hacking Tools
CEH V13 training covers learning more than 350 ethical hacking tools, such as Nmap, Wireshark, Metasploit, and John the Ripper. You will learn these tools and enhance your hands-on skills to be more confident and solid during the exam.
3. Play Capture the Flag (CTF) Challenges
Most aspiring CEHs refine their skills via CTF challenges and hackathons. They mimic actual hacking settings, and you get to apply what you know in a competitive setup.
4. Engage Cybersecurity Communities
Exchange information with other ethical hackers on forums, web forums, and social media groups. Knowing others and exchanging information will expose you to current trends and methods.
Advantages of Being a Certified Ethical Hacker V13 (CEH)
1. More Job Opportunities
Companies all over the world are looking for ethical hackers to improve their security stance. Being certified with CEH V13 can lead to job opportunities as a Penetration Tester, Security Analyst, Network Security Engineer, and Cybersecurity Consultant.
2. Greater Salary Potential
Certified ethical hackers are in great demand, and that equates to good pay. CEH holders are said to earn between $90,000 and $120,000 annually, with higher pay for experienced personnel.
3. Credits and Respect
The CEH V13 certification is well recognized throughout the world and holds a great deal of respect. It testifies to your professional skill in ethical hacking and enhances your esteem as a cyber security expert.
4. Contributing to Cybersecurity Defense
Ethical hackers are the backbone of protectors of the company against cyber attacks. They help you in the greater cause of defending cyberspace for all.
Conclusion
The Certified Ethical Hacker V13 (CEH) certification is essential for anyone who wishes to pursue a good career in cybersecurity. Its strong curriculum, practical training approach, and focus on emerging threats make it the most highly sought-after certificate across the globe. Whether you are going to build a career in cybersecurity or want to upgrade your skills, CEH V13 will provide you with the knowledge to make your career a success in the ever-changing world of cybersecurity.
#certified ethical hacker v12#certified ethical hacker v13#ethical hacking certification#Certified Ethical Hacker V13 (CEH)
0 notes
Text
GlarySoft Malware Hunter Pro with Crack 2025 Download [Latest]
DOWNLOAD LINK
GlarySoft Malware Hunter is a security software designed 2025 to detect and remove malware, including viruses, Trojans, spyware, adware, and other potentially harmful software from your computer. Developed by Glarysoft, it aims to provide users with an extra layer of protection against malicious threats, ensuring that their system runs smoothly and securely. Malware Hunter is known for being easy to use, with a user-friendly interface, and it operates alongside existing antivirus software to enhance your system's overall security.
Key Features of GlarySoft Malware Hunter:
Comprehensive Malware Detection and Removal:
Malware Hunter is capable of detecting various types of malicious software, such as viruses, Trojans, worms, rootkits, spyware, and adware. It scans your system for threats and removes them to ensure your computer remains safe from infection.
0 notes
Text
Kaspersky Rescue Disk Crack 2025 + Serial Key
Kaspersky Rescue Disk is a powerful tool designed by Kaspersky Lab to help users detect and remove malware and other security threats from infected computers. It is a bootable disk image that can be used to run a system scan and clean up a machine that may be compromised by viruses, trojans, rootkits, and other types of malicious software. Kaspersky Rescue Disk is especially useful when the operating system has become unresponsive or the infection is severe enough that traditional antivirus software cannot be run in the infected environment.
Download Now
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Detects & Removes Malicious Threats: Blocks Viruses, Spyware, Adware, Trojans, Worms, Ransomware, Hijackers, Parasites, Rootkits, KeyLoggers, and many more. Stops Ransomware In Its Tracks: Protects your files and prevents hackers from holding them hostage. Proprietary Definitions Database & Daily Updates A dedicated threat research team scours the web and analyzes thousands of possible threats, focusing on the hard-to-find ones. The database is updated 8-14 times a day. Multi-Dimensional Scanning A next-generation scanning system that goes beyond the typical rules-based methods. It detects existing threats and analyzes general characteristics and code patterns to identify future threats. Analyzes Your System In-Depth: System Investigator identifies spoofed and malicious files. Easy to Use: Receive notifications when product and database updates are available Stay informed: Review detailed scan logs about detected and removed threats and their locations. USB Data Loss Prevention Data Loss Prevention – Mass Storage toward your data theft, denying access to unauthorized devices. Speedo scanner repair Infected USB’s in minutes and recovers the files which got hidden by virus attacks Intel or AMD x32 / x64 Minimum RAM – : 1 GB Free Disk Space – : 800 MB Windows Xp SP3, Windows Vista, Windows 7, Windows 8, Windows 10 Internet Connection is must for License activation [ad_2]
0 notes
Text
Obțineți o licență gratuită pentru UnHackMe 16.50. Programul vă permite să identificați și să eliminați orice tip de malware, precum și să monitorizeze instantaneu codul rău intenționat din sistem UnHackMe este un instrument de detecție rootkit extrem de eficient, care este proiectat pentru a detecta și elimina programele rootkit ce se ascund in sistemele de operare Windows. Rootkit-urile sunt o nouă clasă de amenințări: pachete software rău intenționat concepute pentru a menține clandestin controlul asupra calculatoarelor țintă, în timp ce se sustrage de la detectarea antivirus. Astfel de rootkit-uri sunt utilizate direct de către hackeri (persoane fizice malware) sau sunt folosite ca blocuri pentru viruși sofisticate de creatorii de virusi. UnHackMe identifică pozitiv a rootkit-urilor și oferă opțiunea de a le scoate, inclusiv intrări registru asociate, procese și fișiere. Nume produs: UnHackMe 16.50 Pagina oficiala: https://greatis.com/unhackme/ Pagina promotionala: N /A Valabilitate licenta: pe viata (versiune promotionala, vine cu unele limitari) Sistem de operare: Windows 11 / 10 / Windows 8.1 și 8 / Windows 7 / Windows Vista (x32/x64) [wpsm_ads1] In primul rand descarcam si instalam aplicatia accesand acest link ( sau din link-ul oferit in sectiunea ”Detalii promotie”. Pentru inregistrare apasam butonul din bara de sus ”Register” si introducem serialul furnizat mai sus. Anti-Rootkit. Anti-malware, Anti-Troian, Anti-Bot. Anti-adware, Anti-Spy. Caracteristici cheie ale UnHackMe 16.50: Detectare și Eliminare Rootkit: UnHackMe este specializat în detectarea și eliminarea rootkit-urilor, care sunt programe malware ce încearcă să obțină acces neautorizat la un computer și să ascundă prezența altor programe malițioase. Protecție Anti-Malware: Programul oferă protecție împotriva diverselor tipuri de malware, inclusiv troieni, viruși, viermi și spyware. Scanare Rapidă și Completă: UnHackMe permite utilizatorilor să efectueze scanări rapide pentru detectarea rapidă a amenințărilor, precum și scanări complete pentru o verificare mai amănunțită a sistemului. Monitorizare în Timp Real: Programul monitorizează sistemul în timp real pentru a detecta activitățile suspecte și a preveni atacurile înainte ca acestea să se producă. Eliminare Programe Potențial Nedorite (PUP): UnHackMe poate identifica și elimina programele potențial nedorite care pot încetini performanța computerului sau pot cauza alte probleme. Interfață Ușor de Utilizat: Interfața intuitivă a programului permite utilizatorilor de toate nivelurile să navigheze și să utilizeze eficient funcțiile software-ului. Compatibilitate cu Alte Software-uri de Securitate: UnHackMe poate fi utilizat alături de alte soluții de securitate fără a cauza conflicte, oferind un strat suplimentar de protecție. Actualizări Regulate: Programul beneficiază de actualizări regulate pentru a asigura protecția împotriva celor mai recente amenințări cibernetice. Raportare și Jurnalizare: UnHackMe oferă funcții de raportare și jurnalizare detaliată pentru a ajuta utilizatorii să urmărească și să analizeze activitățile și amenințările detectate. Suport Tehnic: Utilizatorii au acces la suport tehnic pentru a primi asistență în rezolvarea problemelor legate de securitatea computerului.
0 notes